Cisco Nexus 1000V Virtual Switch Module investment series in the Cisco Unified Computing System
Hi all
I read an article by Cisco entitled "Best practices in Deploying Cisco Nexus 1000V Switches Cisco UCS B and C Series series Cisco UCS Manager servers" http://www.cisco.com/en/US/prod/collateral/switches/ps9441/ps9902/white_paper_c11-558242.html
A lot of excellent information, but the section that intrigues me, has to do with the implementation of module of the VSM in the UCS. The article lists 4 options in order of preference, but does not provide details or the reasons underlying the recommendations. The options are the following:
============================================================================================================================================================
Option 1: VSM external to the Cisco Unified Computing System on the Cisco Nexus 1010
In this scenario, the virtual environment management operations is accomplished in a method identical to existing environments not virtualized. With multiple instances on the Nexus 1010 VSM, multiple vCenter data centers can be supported.
============================================================================================================================================================
Option 2: VSM outside the Cisco Unified Computing System on the Cisco Nexus 1000V series MEC
This model allows to centralize the management of virtual infrastructure, and proved to be very stable...
============================================================================================================================================================
Option 3: VSM Outside the Cisco Unified Computing System on the VMware vSwitch
This model allows to isolate managed devices, and it migrates to the model of the device of the unit of Services virtual Cisco Nexus 1010. A possible concern here is the management and the operational model of the network between the MSM and VEM devices links.
============================================================================================================================================================
Option 4: VSM Inside the Cisco Unified Computing System on the VMware vSwitch
This model was also stable in test deployments. A possible concern here is the management and the operational model of the network links between the MSM and VEM devices and switching infrastructure have doubles in your Cisco Unified Computing System.
============================================================================================================================================================
As a beginner for both 100V Nexus and UCS, I hope someone can help me understand the configuration of these options and equally important to provide a more detailed explanation of each of the options and the resoning behind preferences (pro advantages and disadvantages).
Thank you
Pradeep
No, they are different products. vASA will be a virtual version of our ASA device.
ASA is a complete recommended firewall.
Tags: Cisco DataCenter
Similar Questions
-
Cisco Unified Computing System - Play Smart expiration
Dear friends,
I have quoted the part number "UCS-SPL-5108-AC2" to one of our customers, and it has been profitable since we presented the lowest bid because of the selection of smartplay.
I need to know the validity of this Smartplay Promotion, when it will expire, since we are in the bidding process and it can take a long time to close.
Here's the BOQ.
UCS-SPL-5108-AC2 UCS SP select 5108 chassis w/2208 IO AC2, 4 x SFP cable 3 m 1 CAB-BS1363-C19-UK BS 1363 to IEC - C19 14 ft UK 4 SFP-H10GB-CU3M 10GBase-CU SFP + cable 3 meters 4 UCS-IOM-2208XP UCS 2208XP Module IO (8, 32 Ports external internal 10Gb) 2 N01-UAC1 Power supply single-phase AC for UCS 5108 1 N20 - CAK Accessory Kit for UCS 5108 blade server chassis 1 N20-CBLKB1 Blade cutting sign slot slot UCS 5108/single 8 N20-FAN5 Module breakdown for UCS 5108 8 N20-FW012 Server chassis package blade UCS FW 2.2 1 UCSB-5108-PKG-HW UCS 5108 packaging for blades width chassis. 1 UCSB-PSU-2500ACDV Hot Plug 2500W power Platinum AC - DV 4 UCSB-B200-M4-U UCS B200 M4 w/o CPU, mem, Berry drive, HDD, mezz (UPG) 8 UCS-UC-E52695D 2.30 GHz E5-2695 v3/120W 14 c / 35 MB Cache/DDR4 2133 MHz 16 UCS-MR-1X162RU-A 16 GB DDR4-2133-MHz RDIMMS/PC4-17000/dual rank/x4/1.2v 64 UCS-MR-1X081RU-A 8 GB DDR4-2133-MHz RDIMMS/PC4-17000/single rank/x4/1.2v 64 UCSB-MLOM - 40G - 03 Cisco UCS VIC 1340 modular LOM Server blades 8 UCSB-LSTOR-BK FlexStorage panels without controller, w/o bays-caches 16 UCSB-HS-EP-M4-F Heat sink for CPU to M4 M4/B420 UCS B200 (front) 8 UCSB-HS-EP-M4-R Heat sink for CPU to M4 M4/B420 UCS B200 (rear) 8 C1UCS-OPT-OUT Calculation of data center Cisco ONE Opt option 8 CON-3SNT-SL6508A2 3 yr SMARTNET 8X5XNBD, UCS B 5108 SP AC2 chassis 1 CON-3SNT-B200M4U 3 YR SMARTNET 8X5XNBDUCS B200 M4 w/o m, Dr. b, CPU, HDD, m (UPG) 8 Kind regards
Farhan.
Smartplay you on what plans we have many, select currently SP9 or Smartplay is the currently running program. Citing the expiry for January 23, 2016, and the expiry of the order would be February 27, 2016.
Does that answer your question?
-
Cannot install hp 1300 series on the Windows 7 operating system
I just got a new laptop with Windows 7. The installation disc contains the operating system is not compatible and that's why it cannot install it.
I tried to change the compatibility by changing the request of Vista installation file. Still will not work.
I tried to install directly from the laptop but my printer is not - he is online and says he cannot access at this time. Try again. (I tried again and again)
I searched for HP PSC 1300 series all-in-one on the HP website and it is not found.
Help, please. I don't want to buy another printer when this one works very well (well, he did on my old computer)
Thank you
Use the link below to download the software for Windows 7:
Download and save the driver on desktop screen. Make sure that the USB cable is not connected to the port on the computer before you start the installation of s/w. If the same error on the subject not compatible operating system, press on and hold down the CTRL + SHIFT keys on the keyboard and click CANCEL on the error message.
It ignores the error and we will install the s/w.
-
Hi, I have 2 questions about the Switch Cisco Nexus 1000v.
First of all, why use it rather than the standard vswitch distributed?
Second, if an environment currently works using distributed vswitches, what are the impacts and the problems likely to introduce a Switch Cisco Nexus 1000v? Is there a process for the upgrade?
See you soon
Here is a comparison for the most up-to-date between the optioins network:
http://www.Cisco.com/en/us/prod/collateral/switches/ps9441/ps9902/solution_overview_c22-526262.PDF
The great driver with most of the people running the 1000v I talked to is give visibility to the network team and streamlining changes made to the virtual network environment. In a great organazation with a network operations team, they will create an IVR to route a new VLAN, and then create the new VLAN on all switches distribution and access in the area of layer 2, just 1000v allows them to move forward and it create on the hypervisor using a set of commands that they already know.
-
Hello
Thanks for reading.
I have a virtual (VM1) connected to a Nexus 1000V distributed switch. The willing 1000V of a connection to our DMZ (physically, an interface on our Cisco ASA 5520) which has 3 other virtual machines that are used successfully to the top in the demilitarized zone. The problem is that a SHOW on the SAA ARP shows the other VM addresses MAC but not VM1.
The properties for all the VMS (including VM1) participating in the demilitarized zone are the same:
- Tag network
- VLAN ID
- Port group
- State - link up
- DirectPath i/o - inactive "path Direct I/O has been explicitly disabled for this port.
The only important difference between VM1 and the others is that they are multihomed agents and have one foot in our private network. I think that the absence of a private IP VM1 is not the source of the problem. All virtual machines recognized as directly connected to the ASA (except VM1).
Have you ever seen this kind of thing before?
Thanks again for reading!
Bob
The systems team:
- Rebuilt the virtual machine
- Moved to another cluster
- Configured for DMZ interface
Something that they got the visible VM to the FW.
-
What does Nexus 1000v Version number Say
Can any body provide long Nexus 1000v version number, for example 5.2 (1) SV3 (1.15)
And what does SV mean in the version number.
Thank you
SV is the abbreviation of "Swiched VMware"
See below for a detailed explanation:
http://www.Cisco.com/c/en/us/about/Security-Center/iOS-NX-OS-reference-g...
The Cisco NX - OS dialing software
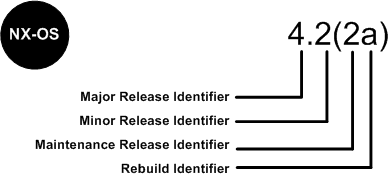
Software Cisco NX - OS is a data-center-class operating system that provides a high thanks to a modular design availability. The Cisco NX - OS software is software-based Cisco MDS 9000 SAN - OS and it supports the Cisco Nexus series switch Cisco MDS 9000 series multilayer. The Cisco NX - OS software contains a boot kick image and an image of the system, the two images contain an identifier of major version, minor version identifier and a maintenance release identifier, and they may also contain an identifier of reconstruction, which can also be referred to as a Patch to support. (See Figure 6).
Software NX - OS Cisco Nexus 7000 Series and MDS 9000 series switches use the numbering scheme that is illustrated in Figure 6.
Figure 6. Switches of the series Cisco IOS dial for Cisco Nexus 7000 and MDS 9000 NX - OS
For the other members of the family, software Cisco NX - OS uses a combination of systems independent of the platform and is dependent on the platform as shown in Figure 6a.
Figure 6 a. software Cisco IOS NX - OS numbering for the link between 4000 and 5000 Series and Nexus 1000 switches virtual
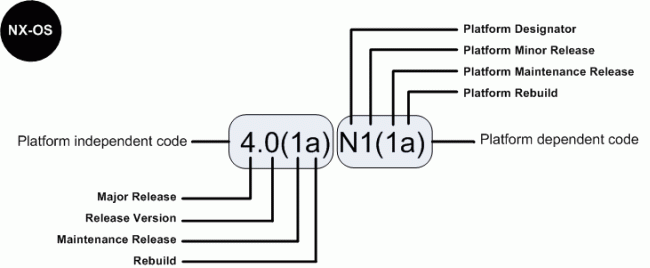
The indicator of the platform is N for switches of the 5000 series Nexus, E for the switches of the series 4000 Nexus and S for the Nexus 1000 series switches. In addition, Nexus 1000 virtual switch uses a designation of two letters platform where the second letter indicates the hypervisor vendor that the virtual switch is compatible with, for example V for VMware. Features there are patches in the platform-independent code and features are present in the version of the platform-dependent Figure 6 a above, there is place of bugs in the version of the software Cisco NX - OS 4.0(1a) are present in the version 4.0(1a) N1(1a).
-
Hey guys,.
Hope this is the right place to post.
IM currently working on a design legacy to put in an ESXi 5 with Nexus 1000v solution and a back-end of a Cisco UCS 5180.
I have a few questions to ask about what people do in the real world about this type of package upward:
In oder to use the Nexus 1000v - should I vCenter? The reason why I ask, is there no was included on the initial list of the Kit. I would say to HA and vMotion virtual Center, but the clients wants to know if I can see what we have for now and licenses to implement vCenter at a later date.
Ive done some reading about the Nexus 1000v as Ive never designed a soluton with that of before. Cisco is recommended 2 VSM be implemented for redundancy. Is this correct? Do need me a license for each VSM? I also suppose to meet this best practice I need HA and vMoton and, therefore, vCenter?
The virtual machine for the VSM, can they sit inside the cluster?
Thanks in advance for any help.
In oder to use the Nexus 1000v - should I vCenter?
Yes - the Nexus 1000v is a type of switch developed virtual and it requires vcenetr
Ive done some reading about the Nexus 1000v as Ive never designed a soluton with that of before. Cisco is recommended 2 VSM be implemented for redundancy. Is this correct? Do need me a license for each VSM? I also suppose to meet this best practice I need HA and vMoton and, therefore, vCenter?
I'm not sure the VSMs but yes HA and vMotion are required as part of best practices
The virtual machine for the VSM, can they sit inside the cluster?
Yes they cane xist within the cluster.
-
Nexus 1000v, UCS, and Microsoft NETWORK load balancing
Hi all
I have a client that implements a new Exchange 2010 environment. They have an obligation to configure load balancing for Client Access servers. The environment consists of VMware vShpere running on top of Cisco UCS blades with the Nexus 1000v dvSwitch.
Everything I've read so far indicates that I must do the following:
1 configure MS in Multicast mode load balancing (by selecting the IGMP protocol option).
2. create a static ARP entry for the address of virtual cluster on the router for the subnet of the server.
3. (maybe) configure a static MAC table entry on the router for the subnet of the server.
3. (maybe) to disable the IGMP snooping on the VLAN appropriate in the Nexus 1000v.
My questions are:
1. any person running successfully a similar configuration?
2 are there missing steps in the list above, or I shouldn't do?
3. If I am disabling the snooping IGMP on the Nexus 1000v should I also disable it on the fabric of UCS interconnections and router?
Thanks a lot for your time,.
Aaron
Aaron,
The steps above you are correct, you need steps 1-4 to operate correctly. Normally people will create a VLAN separate to their interfaces NLB/subnet, to prevent floods mcast uncessisary frameworks within the network.
To answer your questions
(1) I saw multiple clients run this configuration
(2) the steps you are correct
(3) you can't toggle the on UCS IGMP snooping. It is enabled by default and not a configurable option. There is no need to change anything within the UCS regarding MS NLB with the above procedure. FYI - the ability to disable/enable the snooping IGMP on UCS is scheduled for a next version 2.1.
This is the correct method untill the time we have the option of configuring static multicast mac entries on
the Nexus 1000v. If this is a feature you'd like, please open a TAC case and request for bug CSCtb93725 to be linked to your SR.This will give more "push" to our develpment team to prioritize this request.
Hopefully some other customers can share their experience.
Regards,
Robert
-
Can not pass traffic with label of vmware virtual switch fabric 10 GB
Hello
I need to understand how to move traffic labeled VMware VST to these virtual Fabric switch. Blades IBM HS22 connecting internally to the virtual switch between ports 1 to 14. I use 2 external ports (17-18), one connects to the Netgear switch and another to the other switch to virtual fabric. Did the same on the other virtual fabric switch. My Synology rackstation is configured with LUN iscsi that connect to the Netgear switch and I would like to connect my HS 22 rackstation blades. My main concern is that I can't ping the IP of netgear on the same interface vlan. I can ping my Synology diskstation to the netgear which are in the same vlan. NETGEAR and BNT switches are connected by cables DAC SFP +.
Even VLAN is also configured on Netgear switch. The default pvid is set as 1 on all interfaces, can I disable this? Do I need to use tagpvid-penetration on all interfaces.
SH run
Current configuration:
!
version "7.8.7.
switch type "IBM Networking OS virtual fabric 10 Gb Switch Module for IBM BladeCenter"
iscli-new
!
timezone system 295
! Europe/Denmark
Advanced System
!SNMP-name of the server "BNT01".
!
hostname "BNT01".
!
!
enable access userbbi
!
INT1 interface port
switchport trunk allowed vlan 1, 16-50, 3998-4000, 4095
output
!
INT2 interface port
switchport trunk allowed vlan 1, 16-50, 3998-4000, 4095
output
!
INT3 interface port
switchport trunk allowed vlan 1, 16-50, 3998-4000, 4095
output
!
INT4 interface port
switchport trunk allowed vlan 1, 16-50, 3998-4000, 4095
output
!
INT5 interface port
switchport trunk allowed vlan 1, 16-50, 3998-4000, 4095
output
!
INT6 interface port
switchport trunk allowed vlan 1, 16-50, 3998-4000, 4095
output
!
INT7 interface port
switchport trunk allowed vlan 1, 16-50, 3998-4000, 4095
output
!INT8 interface port
switchport trunk allowed vlan 1, 16-50, 3998-4000, 4095
output
!
INT9 interface port
switchport trunk allowed vlan 1, 16-50, 3998-4000, 4095
output
!
INT10 interface port
switchport trunk allowed vlan 1, 16-50, 3998-4000, 4095
output
!
INT11 interface port
switchport trunk allowed vlan 1, 16-50, 3998-4000, 4095
output
!INT12 interface port
switchport trunk allowed vlan 1, 16-50, 3998-4000, 4095
output
!
INT13 interface port
switchport trunk allowed vlan 1, 16-50, 3998-4000, 4095
output
!
interface INT14 port
switchport trunk allowed vlan 1, 16-50, 3998-4000, 4095
output
!
EXT1 interface port
switchport mode trunk
switchport trunk allowed vlan 1, 16-50, 3998-4000
output
!
EXT2 interface port
switchport mode trunk
switchport trunk allowed vlan 1, 16-50, 3998-4000
output
!!
VLAN 1
the name "Default".
!
VLAN 16
name "VLAN16".
!
VLAN 17
name "VLAN17".
!
VLAN 18
name "VLAN18".
!
VLAN 19
name "VLAN19".
!
VLAN 20
name "VLAN20.
!.
.
.
.
.
.
..
VLAN 46
name "VLAN46".
!
VLAN 47
name "VLAN47".
!
VLAN 48
name "VLAN48".
!
VLAN 49
name "VLAN49".
!
VLAN 50
name "VLAN50".
!
VLAN 3998
name "iscsi".
!
VLAN 3999
name "vmotion".
!
VLAN 4000
name "mgmt".
!
!
!
spanning tree mst configuration
lethosting-name "region1".
revision 2
output
!
spanning tree mst mode
!
spanning tree mst configuration
example of 1 vlan 16-50
instance 2 vlan 3997,4000
example 3 vlan 3998-3999
outputThe configuration is for Teddy. I donno what I'm missing here? Any ideas would be very appreciated.
Yes. Finally managed to do work. Tagged traffic now connects blades with ESXI 5.5 U2 to the Synology rackstation.
It was the same thing we had. ESXi 6.0 is not supported by this adapter emulex. Also ESXi 5.5 does not I think with the iSCSI driver. So I have updated drivers using esxcli.
VMware
Updated network driver
/ tmp # software esxcli vib install v - /tmp/elxnet-10.0.575.9-1OEM.550.0.0.1331820.x86_64.vib
Result of the installation
Message: The update completed successfully, but the system must be restarted for the changes to be effective.
Restart required: true
VIBs installed: Emulex_bootbank_elxnet_10.0.575.9 - 1OEM.550.0.0.1331820
VIBs removed: VMware_bootbank_elxnet_10.0.100.0v - 1vmw.550.0.0.1331820
VIBs ignored:ISCSI driver update
/ tmp # software esxcli vib install v - /tmp/scsi-be2iscsi-4.6.261.0-1OEM.550.0.0.1198611.x86_64.vib
Result of the installation
Message: The update completed successfully, but the system must be restarted for the changes to be effective.
Restart required: true
VIBs installed: Emulex_bootbank_scsi - be2iscsi_4.6.261.0 - 1OEM.550.0.0.1198611
VIBs deleted:
VIBs ignored:
/ tmp # software esxcli vib install v - /tmp/ima-be2iscsi-4.6.261.0-1OEM.550.0.0.1198611.i386.vib
Result of the installation
Message: The update completed successfully, but the system must be restarted for the changes to be effective.
Restart required: true
VIBs installed: Emulex_bootbank_ima - be2iscsi_4.6.261.0 - 1OEM.550.0.0.1198611
VIBs deleted:
VIBs ignored:esxcli system set to true EI maintenanceMode
esxcli system shutdown reboot - r = driverupdate d = 10After that, I created iSCSI vmkernel ports with the grouping. Ping has started working and now I can connect to the storage
-
Nexus 1000v VSM compatibility with older versions of VEM?
Hello everyone.
I would like to upgrade our Nexus 1000v VSM 4.2 (1) SV1 (5.1) to 4.2 (1) SV2(2.1a) because we are heading of ESXi 5.0 update 3 to 5.5 ESXi in the near future. I was not able to find a list of compatibility for the new version when it comes to versions VEM, I was wondering if the new VSM supports older versions VEM, we are running, so I must not be upgraded all at once. I know that it supports two versions of our ESXi.
Best regards
Pete
You found documentation, transfer of the station from 1.5 to latest code is supported in a VSM perspective. Which is not documented is the small one on the MEC. In general, the VSM is backward compatible with the old VEM (to a degree, the degree of which is not published). Although it is not documented (AFAIK), verbal comprehension is that MEC can be a version or two behind, but you should try to minimize the time that you run in this configuration.
If you plan to run mixed versions VEM when getting your upgraded hosts (totally fine that's how I do mine), it is better to move to this enhanced version of VEM as you upgrade the hypervisor. Since you go ESXi 5.0 5.5, you create an ISO that contains the Cisco VIBs, your favorite driver async (if any), and the image of ESXi 5.5 all grouped together so the upgrade for a given host is all of a sudden. You probably already have this cold technique, but the links generated by the Cisco tool below will show you how to proceed. It also gives some URLS handy to share with each person performing functions on this upgrade. Here is the link:
Nexus 1000V and ESX upgrade utility
PS - the new thing takes clones your VSMs offline. Even if they are fairly easy to recover, having a real pure clone will save some sauce secret that otherwise you may lose in a failure scenario. Just turn off a VSM, then right click and clone. Turn on again this MSM and failover pair HA, then take to the bottom of it and get a clone of it. So as a security measure, this upgrade, get your clones currently out of the current 1.5 VSMs, then some time after your upgrade some clones offline, saved from the new version.
-
Nexus 1000v and vmkernel ports
What is the best practice to put on the nexus 1000v vmkernel ports? Is it a good idea to put all the ports of vms and vmkernel on nexus 1000v? switch or dvs or some vmkernel as management ports must be on a standard? If something happens to the 1000v, all management and vms will be unreachable.
any tips?
Yep, that's correct. Port system profiles don't require any communication between the MEC and VSM.
-
Migrating from a distributed virtual switch pass
I have a cluster that is approved for business-more. I would like the host to a distributed switch. The configuration of the virtual switch is as follows:
4 NICs connected to a host, the NIC are part of an EtherChannel. The network adapters are teamed up with ip route based on the hash of the IP. All network adapters are connected to the same vSwitch with port groups created for access to the different VLANS
I did the following to try to migrate to the new distributed switch: I broke the EtherChannel and removed three network adapters on the virtual switch and assigns them to the distributed switch. At the same time grouping NETWORK adapters on the virtual channel switch based on the originating virtual, we changed the port ID. I then migrated the service console more for the new switch successfully distributed. I have created groups of ports on the virtual switch.
The question is when I re - create the EtherChannel falls hosts on the network. I have noted the following: "see attachment".
Anyone using EtherChannel with distributed switches?
Any help would be appreciated...
How to configure etherchannel on your Cisco switch? You may not use LACP or PAgP. You must use "channel-group mode on.
-
NSX 6.1.5 - distribute Firewall rules are not applied to the empty virtual switches
Hi all
We have a big problem since we have improved the NSX to version 6.1.3 to 6.1.5.
I get a bug following this procedure:
. In vSphere Client--> NSX, create a new virtual switch
. Distribuer distribute the firewall, create a rule to deny traffic between two survey periods. Example: source: all, destination: all, service: all, Action: reject, applies: the new virtual switch
. Connect two VMS to the virtual switch and you can test the other (this is false due to the firewall rule)
. Publish ANY changes on the firewall distribute (could not be related to our rule. Example to change its name to another rule), and the rule starts to operate.
Additional steps:
. Remove the firewall rule
. Identify the virtual machines in the virtual switch
. Re-create the firewall with applies rule: the virtual switch (still empty)
. Connect the virtual machines and ping between them. Yet once, the rule does not work.
. Publish ANY changes on distributed firewalls and the rule starts to operate.
NSX version 6.1.3 and 6.2.0 both work correctly. But I can't downgrade to 6.1.3 or upgrade to 6.2.0. 6.2.1 upgrade involves the upgrade of several other components.
I use the following versions:
. NSX 6.1.5
. vCenter Version 5.5.0 Build 2414847
. ESXi, 5.5.0, 2718055
Please, any ideas?
Thank you very much
D.
She seems to be a bug in 6.1.5 NSX and there is no solution for this yet. There are workarounds, but none of them apply to my "fully automated" environment
We need to wait for a fix or upgrade to NSX 6.2.1 requiring an upgrade of several components as well.
D.
-
Will there be an updated version of the Nexus 1000V for vSphere 4.1, or is the last compatible version?
Current is compatible and included for vSphere 4.1 Ent more.
---
MCSA, MCTS Hyper-V, VCP 3/4, VMware vExpert
-
Update Virtual Center 5.0 to 5.1 (using Cisco Nexus 1000V)
Need advice on upgrading production please.
current environment
Race of Virtual Center 5.0 as a virtual machine to connect to oracle VM DB
3 groups
1: 8 blades of ESXI 5.0 IBM cluster, CLuster 2: 5 IBM 3850 x 5
2 cisco Nexus 1000v of which cluster only 1 use.
I know that the procedure of upgrading to 5.1
1. create DB SSO, SSO of installation
2 upgrading VC to 5.1
3. install WEB CLient set up AD authentication
IT IS:
I have problems with the Nexus 1000? I hope the upgrade will treat them as he would a distributed switch and I should have no problem.
He wj, treat the Nexus as a dVS.
Maybe you are looking for
-
lock the images (how it happened)
Hi guys,. I just use app to find my images in doubles, from there, I just don't see that I have a lot of images that I have; are the lock. How this happen? I don't know that I'm not done it. TQ
-
Vista - Error Code: C80003FA (cannot install will want to)
You'll never have any problems with the automatic update of my Vista. 3 days ago, no update occurred. Just search for the new update & C80003FA of Code error received. Please help as soon as possible. Thank you
-
Any time I turn on my computer, I see a message saying (files which are required for Windows to run properly have been replaced by unrecognized versions.) To maintain the stability of the system Windows must restore the original versions of these fil
-
CreateProcess failed; code 740. The requested operation requires a rise. This game is SNIPER ELITE REBELLION V2 Please help me if you can, I want to play this game, please help me, are any developer here?
-
The logo design for application
Hello I have a request I want to load on my Blackberry. I also want to add a logo for this application when it is loaded on the device. Can someone tell me how this is done? Thank youSaket
