Help of the chain
I'm counting the words real in my thong so I can tell my for how many times to execute in a loop. Is there a way to do this?
We have already done here:
http://forums.NI.com/NI/board/message?board.ID=170&thread.ID=491463
But if you don't like this method, you can ensure 100% of the time that each word will be separated by a space, you can:
(1) clear spaces around the string.
(2) moving through the search and replace the string function and replace all spaces with something
-the number of seats + 1 = number of words.
As I said in the other thread, this only works if you are dealing with WORDS.
If you try to convert the sentence 'it has 10 cows' pig Latin, your function can handle.
He can't handle the text speaks as "R U coming round 2nite."
(Note that it is the addition of a character at the beginning of a word that is causing a problem here. "It was bad (very bad), so bad...". ' is not managed well by your VI. I maintain my old code.)
James
Tags: NI Software
Similar Questions
-
The chain is be ignored and need help with why?
Hi all.
I hope again with help from the community.
There is a chain created (code below) and it runs with success - at least she built MOST of the tables.
The problem is: the last three tables all rely on the same condition and only two of them pass.
The code below, step 4, steps 5 and 6 are all dependent on the success of step 3.
When work for this string is executed, all stages of execution fails with the exception of step 5.
The interesting thing (to me at least), is that regardless of the generation of the table is step 5 fails. For example, in the code below prog_Y is attributed to step 5 and it fails. If I swap prog_Y to step_4 and prog_X to step_5, step_5 still does not work. Same result if prog_Z is listed as step 5. While steps 4 and 6 to run correctly.
Further info in job run lists of details: table or view does not exist. However, I confirmed the procs behind programs every summer executed successfully and the tables exist.
I tried several things to get more information: change the numbers.dropping/redefining step leaving down the chain and redefine, retype the steps and rules.
Help, please. Suggestions of why this step 5 may be at fault or where to find more information is super useful.
Thank you very much
Fritz
When the string is executed partially
/* 1. Create the string * /.
BEGIN
() dbms_scheduler.create_chain
CHAIN_NAME = > 'dgr_cmpl_chain ',.
RULE_SET_NAME = > null,
EVALUATION_INTERVAL = > null,
Comments = > 'Chain that loads tables of degree completion.');
END;
/* 2. Define the steps of the string * /.
BEGIN
DBMS_SCHEDULER. () DEFINE_CHAIN_STEP
chain_name = > 'dgr_cmpl_chain ',.
step_name = > "step_1".
program name = > 'prog_intrmdt_1');
DBMS_SCHEDULER. () DEFINE_CHAIN_STEP
chain_name = > 'dgr_cmpl_chain ',.
step_name = > "step_2"
program name = > 'prog_intrmdt_2');
DBMS_SCHEDULER. () DEFINE_CHAIN_STEP
chain_name = > 'dgr_cmpl_chain ',.
step_name = > "step_3"
program name = > 'prog_base');
DBMS_SCHEDULER. () DEFINE_CHAIN_STEP
chain_name = > 'dgr_cmpl_chain ',.
step_name = > "step_4"
program name = > 'prog_X');
DBMS_SCHEDULER. () DEFINE_CHAIN_STEP
chain_name = > 'dgr_cmpl_chain ',.
step_name = > "step_5"
program name = > 'prog_Y');
DBMS_SCHEDULER. () DEFINE_CHAIN_STEP
chain_name = > 'dgr_cmpl_chain ',.
step_name = > "step_6"
program name = > 'prog_Z');
END;
/* 3. Add rules * /.
BEGIN
DBMS_SCHEDULER. () DEFINE_CHAIN_RULE
chain_name = > 'dgr_cmpl_chain ',.
State = > 'TRUE ',.
action = > 'START step_1. "
nom_regle = > 'rule_1. "
Comments = > 'String degree start.');
DBMS_SCHEDULER. () DEFINE_CHAIN_RULE
chain_name = > 'dgr_cmpl_chain ',.
State = > "step_1 succeeded."
action = > 'START step_2. "
nom_regle = > "rule_2");
DBMS_SCHEDULER. () DEFINE_CHAIN_RULE
chain_name = > 'dgr_cmpl_chain ',.
State = > "step_2 succeeded."
action = > 'START step_3 ',.
nom_regle = > 'rule_3');
DBMS_SCHEDULER. () DEFINE_CHAIN_RULE
chain_name = > 'dgr_cmpl_chain ',.
State = > "step_3 succeeded."
action = > 'START step_4 ',.
nom_regle = > 'rule_4');
DBMS_SCHEDULER. () DEFINE_CHAIN_RULE
chain_name = > 'dgr_cmpl_chain ',.
State = > "step_3 succeeded."
action = > 'START step_5 ',.
nom_regle = > 'rule_5');
DBMS_SCHEDULER. () DEFINE_CHAIN_RULE
chain_name = > 'dgr_cmpl_chain ',.
State = > "step_3 succeeded."
action = > 'START step_6 ',.
nom_regle = > 'rule_6');
DBMS_SCHEDULER. () DEFINE_CHAIN_RULE
chain_name = > 'dgr_cmpl_chain ',.
State = > ' completed and full of step_5 step_4 and end step_6 "
action = > "END."
nom_regle = > 'rule_7');
END;
/*
*/
/* 4. Select the string * /.
BEGIN
DBMS_SCHEDULER. SELECT ("dgr_cmpl_chain");
END;
/* 5. Create a job that points to the string. */
/ * Wizard of work used to create jobs * /.
Thanks a lot for your suggestions. Very grateful.
Looks like this may have been a self-inflicted error.
There were a few other errors which confuse this explanation. But today, this seems to be the most likely case.
The END condition was initially step completed 6. Turns, then step 3 successful, all the steps 4, 5 and 6 began at the same time. Well, step 6 was shorter than the 5 step execution time. So step 6 would end, and the end to trigger the end of the string before step 5.
This worked constantly since the END condition has been updated in order to assess the steps, 4, 5 and 6.
Fritz
-
Hello
I have a control over the chain on my UI and I would like to make the difference between mouse different events, that is to say, to be able to differentiate a click on the outline or the label of the controller vs right-clicking on the Center (between the control in "edit" mode)
The reason is that sometimes if the user does click not in the Center but in the scope of control, Labview fires the mouse event down but the typed keys are not registered...
Is it possible to distinguish the two?
Thanks a lot for your help
Set the string "update as you type" and use instead a "changed value" event Now, the event fires whenever a new character is entered.
-
Changing a property of an indicator of the chain in a cluster with a sub - VI
I know that the issue of the update of an indicator on a first level VI of a Subvi has been requested before on the discussion Forum, but my question is slightly different, because I want to update the property of an indicator, not necessarily its value.
In my first level VI, I have a group that contains some indicators of the chain. The cluster is a typedef.
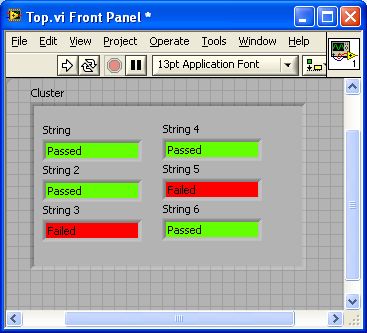
I want to change the background color of the indicator for red or green of my sub - VI string so that it looks like this:
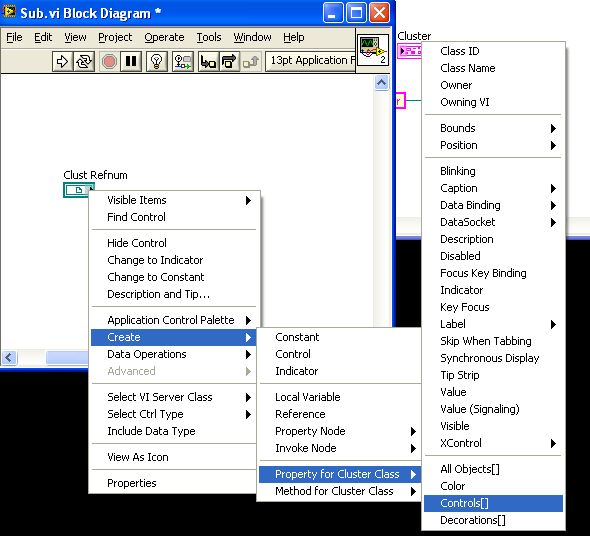
Creating a reference to the cluster and move to the Subvi do not seem to work. I'm not able to see the Text.BGColor property to change the background color of the string indicators:
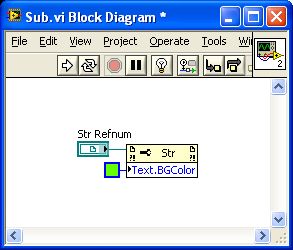
It seems that the creation of a reference to a string indicator and switch to the Subvi might work like this:
Is there a way to better/more elegant to do this? Do I have to create a reference of string for each string in my cluster and send it to my sub - VI?
I've messed around with global variables, but not luck.
Plese help.
You have the right idea. The cluster reference has a property called [orders]. Which returns an array of references to all the controls in your cluster. Indexing of those who have properties BGColor, that you need.
-
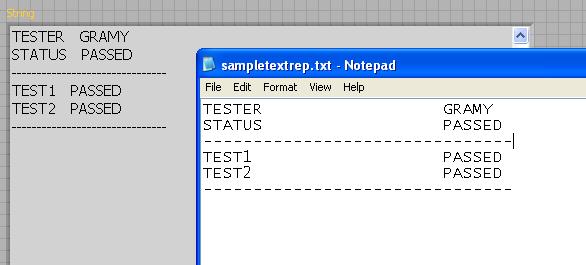
Display the contents of a text file in the control of the chain without changing the format
Hi all
I need your help!
Planning the content of the text report file in labview control chain of the GI.
When I read the text file and update the chain control, alignment of text was not appropriate.
but when I open the same text file in Notepad, alignment looks good.
How to solve this problem of text alignment?
Gramy
You experience the same problem before.
Just use a .net textbox control to display text, instead of the string of LabVIEW.
There is NO need to re - format the string.
-
Using a control of the chain with the Enter key, return * and * allowing repeated identical entry
Hi all
There must be a simple solution for this, but it's Friday afternoon, and my brain is not cooperating.
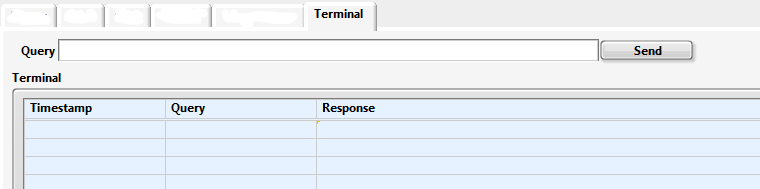
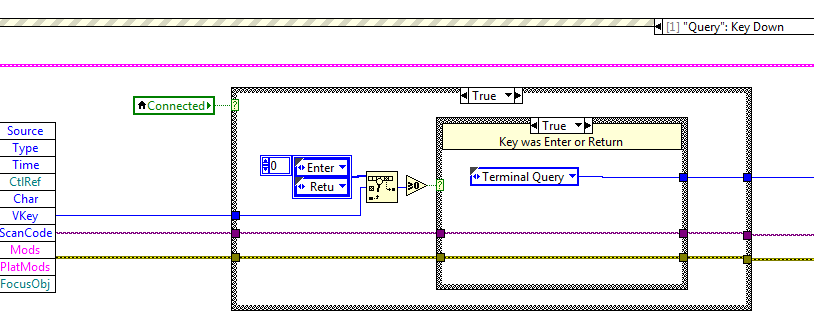
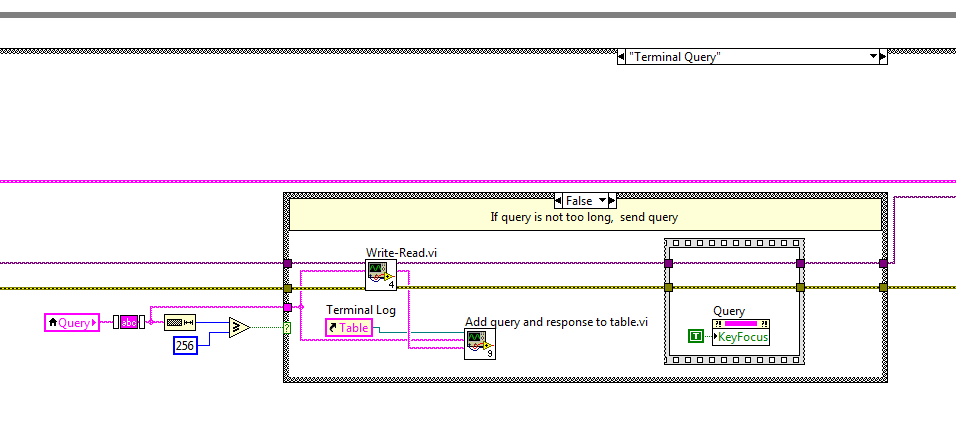
I create a simple terminal through which a user can interact with an instrument. My question is about the only query string control. The button send and the Terminal Table are here for reference.
Here is my desired behavior:
(a) the user types a command in the field of the query, tape input or return. An event is triggered, and the request is sent to the instrument. The focus remains on the field in the query.
(b) with any other action the interface user, the user types Enter or return again and again, by triggering an event that sends the request to the instrument every time Enter or return is typed. The focus remains on the field in the query.
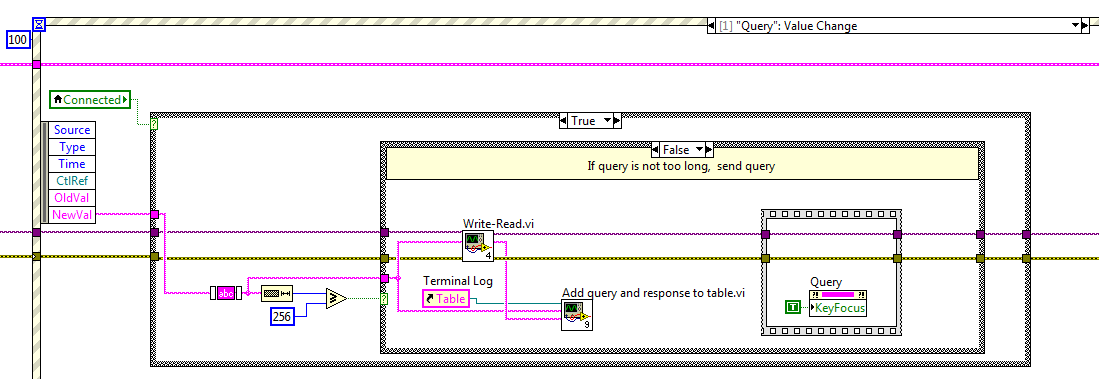
Here's what I have:
This allows for one), but fails to b). The reason is, because the value of the field in the query has not changed, change value event does not fire when the user starts to spam keys enter or return. There is a way around this, as suggested by this post. Here is the solution in a few words:
Instead of looking for the change in the value of the query command, the event fires for each key event to the bottom of the control and resembles a pressure of enter key or return. What attracts the user action, even if the content of the field of the request have not changed. The problem with this approach is that, when this event fires, I need to read the value of the query string order and send it to the instrument, but the value I get via the local Variable query is the old value, probably because the key down event fires before the value of query is saved as changed. Is there a way to programatically "enter" the contents of the control channel so it is recorded as a change in value, until I have the question via a local Variable? Is there a different way I should go about it? I'd rather not do anything that bound the input keys or return to this particular area, since I have many other UI elements that need these keys in my program.
If not, is there a way to make the control of the fire 'Change of value' query string event when the user presses enter or return even if the value has not changed?
Thank you for your comments!
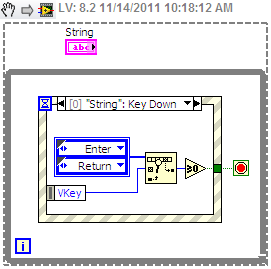
I thought about it.
(1) control of the string (query) a value of update while typing.
(2) save the key event down to the control of the chain. If the entry or return was pressed, send the state machine to the State 'send request '.
(3) in the application 'send' State read control channel via the local Variable value.
This is the desired behavior to allow the user repeatedly hit entry or return to regularly send a command, and the user can also type in a new order and send it by pressing enter or return.
Thanks to all who have helped me this something to think about!
-
menu bar popup not working if the focus is on the control of the chain
Dear all,
I wonder if this is the behavior expected or if I'm doing something wrong:
On a Panel, I have a control of the chain; on double click, I opened a file selection box to select a file, then the file name on this control of the chain. After this action, this string is the active control, indicated by the gray frame.
I also have a menu with some defined keyboard shortcuts bar for example F2. It seems that F2 is not functional, long as the focus is on the control of the chain. It's embarrassing because the typical user action is selects a file and then pressing on Fx. To resolve this problem, the user should click somewhere on the Panel to move the focus to another control. Of course this could be done programmatically, but the extra effort is not to say necessary for controls ring or digital controls. Also in digital controls, I can change the numbers, but even if a digital control is the active control due to the edition of the F2 value works immediately.
Help is appreciated.
Thank you
Wolfgang
I think what is happening here is that left double click is also used to highlight the text. So when you trigger the EVENT_LEFT_DOUBLE_CLICK, you're placing the text in the control of the chain and then also accentuating. It seems to be behaving strangely when the two of them occurs at the same time because of the order of the events. You can see that the mouse around when, returning from the file select popup causes the region highlighting to drag over the text. In this highlight mode, you cannot use the shortcuts for the menu. I was able to solve this problem by swallowing the EVENT_LEFT_DOUBLE_CLICK after you set the value of the control.
-
floating point No. the chain with the same precision
I use "format string" to convert floating point No. to a string. Most of the numbers have a single decimal digit, so I use '%^0.1f' in the format in the connection string. But for our whole. like 150, it gets converted to 150,0. I want to avoid this, such that the chain looks exactly like the No.... What should I change?
Use %#0.1f as your format string.
Read the help file on the format codes. The sign # told him to truncate the zeros.
-
Need help with the configuration of the Site with crossed on Cisco ASA5510 8.2 IPSec VPN Client (1)
Need urgent help in the configuration of the Client VPN IPSec Site with crossed on Cisco ASA5510 - 8.2 (1).
Here is the presentation:

There are two leased lines for Internet access - a route 1.1.1.1 and 2.2.2.2, the latter being the default Standard, old East for backup.
I was able to configure the Client VPN IPSec Site
(1) with access to the outside so that the internal network (172.16.0.0/24) behind the asa
(2) with Split tunnel with simultaneous assess internal LAN and Internet on the outside.
But I was not able to make the tradiotional model Hairpinng to work in this scenario.
I followed every possible suggestions made on this subject in many topics of Discussion but still no luck. Can someone help me here please?
Here is the race-Conf with Normal Client to Site IPSec VPN configured with no access boarding:
LIMITATION: Cannot boot into any other image ios for unavoidable reasons, must use 8.2 (1)
race-conf - Site VPN Customer normal work without internet access/split tunnel
:
ASA Version 8.2 (1)
!
ciscoasa hostname
domain cisco.campus.com
enable the encrypted password xxxxxxxxxxxxxx
XXXXXXXXXXXXXX encrypted passwd
names of
!
interface GigabitEthernet0/0
nameif outside internet1
security-level 0
IP 1.1.1.1 255.255.255.240
!
interface GigabitEthernet0/1
nameif outside internet2
security-level 0
IP address 2.2.2.2 255.255.255.224
!
interface GigabitEthernet0/2
nameif dmz interface
security-level 0
IP 10.0.1.1 255.255.255.0
!
interface GigabitEthernet0/3
nameif campus-lan
security-level 0
IP 172.16.0.1 255.255.0.0
!
interface Management0/0
nameif CSC-MGMT
security-level 100
the IP 10.0.0.4 address 255.255.255.0
!
boot system Disk0: / asa821 - k8.bin
boot system Disk0: / asa843 - k8.bin
passive FTP mode
DNS server-group DefaultDNS
domain cisco.campus.com
permit same-security-traffic inter-interface
permit same-security-traffic intra-interface
object-group network cmps-lan
the object-group CSC - ip network
object-group network www-Interior
object-group network www-outside
object-group service tcp-80
object-group service udp-53
object-group service https
object-group service pop3
object-group service smtp
object-group service tcp80
object-group service http-s
object-group service pop3-110
object-group service smtp25
object-group service udp53
object-group service ssh
object-group service tcp-port
port udp-object-group service
object-group service ftp
object-group service ftp - data
object-group network csc1-ip
object-group service all-tcp-udp
access list INTERNET1-IN extended permit ip host 1.2.2.2 2.2.2.3
access-list extended SCC-OUT permit ip host 10.0.0.5 everything
list of access CAMPUS-LAN extended permitted tcp 172.16.0.0 255.255.0.0 any eq www
list of access CAMPUS-LAN extended permitted tcp 172.16.0.0 255.255.0.0 any https eq
list of access CAMPUS-LAN extended permitted tcp 172.16.0.0 255.255.0.0 any eq ssh
list of access CAMPUS-LAN extended permitted tcp 172.16.0.0 255.255.0.0 no matter what eq ftp
list of access CAMPUS-LAN extended permitted udp 172.16.0.0 255.255.0.0 no matter what eq field
list of access CAMPUS-LAN extended permitted tcp 172.16.0.0 255.255.0.0 any eq smtp
list of access CAMPUS-LAN extended permitted tcp 172.16.0.0 255.255.0.0 any eq pop3
access CAMPUS-wide LAN ip allowed list a whole
access-list CSC - acl note scan web and mail traffic
access-list CSC - acl extended permit tcp any any eq smtp
access-list CSC - acl extended permit tcp any any eq pop3
access-list CSC - acl note scan web and mail traffic
access-list extended INTERNET2-IN permit tcp any host 1.1.1.2 eq 993
access-list extended INTERNET2-IN permit tcp any host 1.1.1.2 eq imap4
access-list extended INTERNET2-IN permit tcp any host 1.1.1.2 eq 465
access-list extended INTERNET2-IN permit tcp any host 1.1.1.2 eq www
access-list extended INTERNET2-IN permit tcp any host 1.1.1.2 eq https
access-list extended INTERNET2-IN permit tcp any host 1.1.1.2 eq smtp
access-list extended INTERNET2-IN permit tcp any host 1.1.1.2 eq pop3
access-list extended INTERNET2-IN permit ip any host 1.1.1.2
access-list sheep extended ip 172.16.0.0 allow 255.255.0.0 172.16.0.0 255.255.0.0
access list DNS-inspect extended permit tcp any any eq field
access list DNS-inspect extended permit udp any any eq field
access-list extended capin permit ip host 172.16.1.234 all
access-list extended capin permit ip host 172.16.1.52 all
access-list extended capin permit ip any host 172.16.1.52
Capin list extended access permit ip host 172.16.0.82 172.16.0.61
Capin list extended access permit ip host 172.16.0.61 172.16.0.82
access-list extended capout permit ip host 2.2.2.2 everything
access-list extended capout permit ip any host 2.2.2.2
Access campus-lan_nat0_outbound extended ip 172.16.0.0 list allow 255.255.0.0 192.168.150.0 255.255.255.0
pager lines 24
Enable logging
debug logging in buffered memory
asdm of logging of information
Internet1-outside of MTU 1500
Internet2-outside of MTU 1500
interface-dmz MTU 1500
Campus-lan of MTU 1500
MTU 1500 CSC-MGMT
IP local pool 192.168.150.2 - 192.168.150.250 mask 255.255.255.0 vpnpool1
IP check path reverse interface internet2-outside
IP check path reverse interface interface-dmz
IP check path opposite campus-lan interface
IP check path reverse interface CSC-MGMT
no failover
ICMP unreachable rate-limit 1 burst-size 1
ASDM image disk0: / asdm - 621.bin
don't allow no asdm history
ARP timeout 14400
interface of global (internet1-outside) 1
interface of global (internet2-outside) 1
NAT (campus-lan) 0-campus-lan_nat0_outbound access list
NAT (campus-lan) 1 0.0.0.0 0.0.0.0
NAT (CSC-MGMT) 1 10.0.0.5 255.255.255.255
static (CSC-MGMT, internet2-outside) 2.2.2.3 10.0.0.5 netmask 255.255.255.255
Access-group INTERNET2-IN interface internet1-outside
group-access INTERNET1-IN interface internet2-outside
group-access CAMPUS-LAN in campus-lan interface
CSC-OUT access-group in SCC-MGMT interface
Internet2-outside route 0.0.0.0 0.0.0.0 2.2.2.5 1
Route internet1-outside 0.0.0.0 0.0.0.0 1.1.1.5 2
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-registration DfltAccessPolicy
the ssh LOCAL console AAA authentication
AAA authentication enable LOCAL console
Enable http server
http 10.0.0.2 255.255.255.255 CSC-MGMT
http 10.0.0.8 255.255.255.255 CSC-MGMT
HTTP 1.2.2.2 255.255.255.255 internet2-outside
HTTP 1.2.2.2 255.255.255.255 internet1-outside
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
Crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
Crypto ipsec transform-set ESP-DES-SHA esp - esp-sha-hmac
Crypto ipsec transform-set ESP-DES-MD5 esp - esp-md5-hmac
Crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
Crypto ipsec transform-set ESP-3DES-MD5-esp-3des esp-md5-hmac
Crypto ipsec transform-set ESP-AES-256-SHA 256 - aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-SHA aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-MD5-esp - aes esp-md5-hmac
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 pfs set group5
Crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 value transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA MD5-ESP-3DES ESP-DES-SHA ESP-DES-MD5
Crypto map internet2-outside_map 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
crypto internet2-outside_map outside internet2 network interface card
Crypto ca trustpoint _SmartCallHome_ServerCA
Configure CRL
Crypto ca certificate chain _SmartCallHome_ServerCA
certificate ca xyzxyzxyzyxzxyzxyzxyzxxyzyxzyxzy
a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as
a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as
a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as
a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as
a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as
a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as
a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as
a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as
a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as
a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as
a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as
a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as
a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as
a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as a67a897as
a67a897as a67a897as a67a897as a67a897as a67a897as
quit smoking
ISAKMP crypto enable internet2-outside
crypto ISAKMP policy 10
preshared authentication
aes encryption
md5 hash
Group 2
life 86400
Telnet 10.0.0.2 255.255.255.255 CSC-MGMT
Telnet 10.0.0.8 255.255.255.255 CSC-MGMT
Telnet timeout 5
SSH 1.2.3.3 255.255.255.240 internet1-outside
SSH 1.2.2.2 255.255.255.255 internet1-outside
SSH 1.2.2.2 255.255.255.255 internet2-outside
SSH timeout 5
Console timeout 0
a basic threat threat detection
Statistics-list of access threat detection
no statistical threat detection tcp-interception
WebVPN
internal VPN_TG_1 group policy
VPN_TG_1 group policy attributes
Protocol-tunnel-VPN IPSec
username ssochelpdesk encrypted password privilege 15 xxxxxxxxxxxxxx
privilege of encrypted password username administrator 15 xxxxxxxxxxxxxx
username vpnuser1 encrypted password privilege 0 xxxxxxxxxxxxxx
username vpnuser1 attributes
VPN-group-policy VPN_TG_1
type tunnel-group VPN_TG_1 remote access
attributes global-tunnel-group VPN_TG_1
address vpnpool1 pool
Group Policy - by default-VPN_TG_1
IPSec-attributes tunnel-group VPN_TG_1
pre-shared-key *.
!
class-map cmap-DNS
matches the access list DNS-inspect
CCS-class class-map
corresponds to the CSC - acl access list
!
!
type of policy-card inspect dns preset_dns_map
parameters
message-length maximum 512
Policy-map global_policy
CCS category
CSC help
cmap-DNS class
inspect the preset_dns_map dns
!
global service-policy global_policy
context of prompt hostname
Cryptochecksum: y0y0y0y0y0y0y0y0y0y0y0y0y0y
: end
Adding dynamic NAT for 192.168.150.0/24 on the external interface works, or works the sysopt connection permit VPN
Please tell what to do here, to pin all of the traffic Internet from VPN Clients.
That is, that I need clients connected via VPN tunnel, when connected to the internet, should have their addresses IP NAT'ted against the address of outside internet2 network 2.2.2.2 interface, as it happens for the customers of Campus (172.16.0.0/16)
I am well aware of all involved in here, so please be elaborative in your answers. Please let me know if you need more information about this configuration to respond to my request.
Thank you & best regards
MAXS
Hello
If possible, I'd like to see that a TCP connection attempt (e.g. http://www.google.com) in the ASDM logging of the VPN Client when you set up the dynamic NAT for the VPN Pool also.
I'll try also the command "packet - trace" on the SAA, while the VPN Client is connected to the ASA.
The command format is
packet-tracer intput tcp
That should tell what the SAA for this kind of package entering its "input" interface
Still can not see something wrong with the configuration (other than the statement of "nat" missing Dynamics PAT)
-Jouni
-
How to stop the chain of management based on the description in Oracle 11 g BPM
Hi all
Need your help in the understanding of the possible implementation under the scenario:
We have a chain of management where he must be stopped once the instance they are assigned to a user with specific indication of the genre (say HOD).
We are unsure of the number of levels in which it will reach to user with the designation as HOD.
It may be 2, perhaps 3 or 4 is perhaps.
When I looked at the options available, we have the ability to define the best participant "by title" (Manager, Director, CEO the values available)
So my concerns here are:
(a) If this title is mapped to the user of designation as a Manager, Director or CEO?
(b) can we add other titles down to the bottom.
Secondly, we have the possibility of using XPath, but here I do not know how to achieve this using XPath use cases.
Please guide if there is another way to handle this.
Let me know if my problem statement is not clear.
Kind regards
Bodet
For your condition, you should be able to type the name directly in the title field:
You can use XPath to determine the top Participant at run time. For example, according to the applicant, if the participant at the top of the page is different. You can determine the value of participating in the execution, put it in a variable of the payload and then use it here.
-
Need help on the regular expressions and query
Hi guru s, I hope that you all made great!
I have a scenario where I need to insert data into the table.
I have three scenarios:
What I want is now.select 'Kodali,Raj,S' str from dual union select 'Alex Romano' from dual union select 'ppppp' from dual Alex Romano Kodali,Raj,S ppppp
1 Alex Romano
is there space between the chain and then I want to insert in the last name and first name columns
2 Xavier, Raj, S
If there is a comma between the chain and I want to insert in the last name, first name and middle name
3. If there is one channel then insert even in first name and last name.
I wrote the request more early to manage only by commas and now I'm trying but not able to use this all scenarios
Can you please help me.
Currently I put a b and c if its null value.WITH t AS ( select 'Kodali,Raj,S' str from dual union select 'Alex Romano' from dual union select 'ppppp' from dual ) select DECODE(trim(a),NULL,'a',trim(a)),DECODE(trim(b),NULL,'b',trim(b)),decode(trim(c),NULL,'c' ,trim(c)) from ( SELECT max(decode(level,1,regexp_substr(str,'[^,]+',1,level))) a --INTO lFNAME , max(decode(level,2,regexp_substr(str,'[^,]+',1,level))) b --INTO lLNAME , max(decode(level,3,regexp_substr(str,'[^,]+',1,level))) c --INTO lMNAME FROM t CONNECT BY regexp_substr(str,'[^,]+',1,level) IS NOT NULL GROUP BY str ) ;
Thanks in advance!Hello
You can do what you asked for in pure SQL like this:WITH got_pos AS ( SELECT str , INSTR (str, ',') AS comma_pos , INSTR (str, ' ') AS space_pos FROM t ) SELECT str , CASE WHEN comma_pos > 0 THEN REGEXP_SUBSTR (str, '\w+', 1, 2) WHEN space_pos > 0 THEN SUBSTR (str, 1, space_pos - 1) ELSE str END AS fname , CASE WHEN comma_pos > 0 THEN REGEXP_SUBSTR (str, '\w+', 1, 3) ELSE TRIM (REGEXP_SUBSTR (str, ' \w+ ')) END AS mname , CASE WHEN comma_pos > 0 THEN SUBSTR (str, 1, comma_pos - 1) ELSE REGEXP_SUBSTR (str, '\w+$') END AS lname FROM got_pos ORDER BY str ;But look how it is difficult, even for this simple example of data.
I suggest you write a PL/SQL function to analyze the name. It will be much easier to deal with a combination of spaces and commas, the names of more than 3 words, etc.
-
How can I know because of what table in database, causing the chaining line
Hello
Please help me that how can I know because of what table in database, causing the chaining line?Hello
hope that you have already created the table utlchain. Or otherwise create as below.
SQL > @?/rdbms/admin/utlchain.sql
And try to run the script again.
I tried with the following example in the following link.
http://psoug.org/reference/chained_rows.html
His works very well and it will list the tables.
Or try the row chaining and Migration of line [ID 122020.1]
It has all the necessary steps to do so.
Thank you
Rognard -
the chained rows vs migrate lines
Hi guys,.
Anyone know the diff between lines chained and migrated rows?
The query below is the lines chained after analyzing:
SELECT the table table_name, num_rows, owner, chain_cnt
Round(chain_cnt/num_rows*100,2) pct_chained,
avg_row_len, pct_free, pct_used
FROM dba_tables
where chain_cnt <>0
and num_rows <>0
How about migrated lines?
Thank you!If you are not careful following the basic rules is a good way to end up making unnecessary work.
Since by definition that a linked line is a line that is too large to fit in a single block the reorganization of a table database has no effect on the number of lines chained in a table only migrated lines will be eliminated. The required referenced threads listing chained then lines feteching in fact the lines then statistical verification, which is a lot of work.
Another approach or help reduce the number of tables of interest after analysis your paintings would be to filter the list of tables to consider choosing a percentage value where values below this level are regarded as not of interest: dba_tables.chain_cnt / dba_tables.num_rows. After all you care if one person out of 1000 10 thousand, or 200 e / s to get a line via an index reading requires a second IO? You can follow the link referenced at this stage for the identified tables or more based on statistics an analysis of eye-ball.
Consider the pctfree, the amount of data exists on insert and avg_row_len. Short rows would not be the string so a chain_cnt > 0 in this case probably would be migrated rows. A line length average larger than the size of the block would require chaining and you could estimate how many blocks N number of lines should take and comapre for your chain_cnt. It's tables with medium-sized lines that are the most difficult to understand given that the avg_row_len could hide some very large rows that have the chain and where to capture the chained rows and retrieve can be useful.
Now make a quick estimate of the number of blocks needed to contain num_rows * avg_row_len * overhead_factor / the_oracle_block size and compare that to dbatables.blocks.
If the space used is substantially higher than the calculated space so this table can be a canidate for reorganization for the purpose of management of space, if you really need to look at the DML model space may soon be rehabilitated. A history of use of space by the heads of line object can be beneficial to determine whether the table is a State of equilibrium (essentially static in size) or still growing. If you go to the trouble to re-organize a table you must keep a record the before and after results, including the number of lines and the number of blocks used for use on the line to determine if the execution of this task again on the same object is worth.
If a table turns have migrated lines then most likely you need to adjust the pctfree factor in order to ensure a suitable available space exists in the block at the time of insertion to allow future expansion line so that you don't have to re-organize the table again in a few months.
HTH - Mark D Powell.
-
With the help of the links related to the Garland in an LMS... Help!
I worked on a module of training locally on the server of our company. I used the chaining to connect separate projects and it seems to work very well in our workspace. When uploaded to the LMS the Garland does not work. All we see is a gray loading screen as if the module is trying to find the specified project file. Does anyone know a solution to this problem? Help, please! Thanks in advance!
For the output of the LMS, value options end of project module just stop Project, not open URL or file. Do not use narrow project because it would sometimes make the window of LMS SCORM player to quit smoking. Project is the best.
More good LMS have an option called something like Auto continue or reading continues, which means that when a module ends the following in the table of contents is open and read automatically. Look for this option in your LMS and use it for your daisy chaining effect.
-
Hello
I want you to help because the phone ask me for becoming a frequent and annoying password to calculate the icloud, and I do not know because I bought a phone from someone else is not new Hama is on the phone (*) No. account. IMEI (*) Please help me soon thank you
< post branched out by host >
< personal information under the direction of the host >
Robert Odamat says:
Hello
I want you to help because the phone ask me for becoming a frequent and annoying password to calculate the icloud, and I do not know because I bought a phone from someone else is not new Hama is on the phone (*) No. account. IMEI (*) Please help me soon thank you
< post branched out by host >
< personal information under the direction of the host >
Find my iPhone Activation Lock - Apple Support
There is nothing you can do to get around activation icloud blocking without recovering the former owners information.
Communicate with the person that you bought the phone.
Maybe you are looking for
-
just changed after the last update of firefox. It's very embarrassing because the address bar and search bar are two different entities.
-
Tecra 8100: the wrong processor speed?
I just bought a Tecra 8100 opportunity and told me the cpu speed to 800 MHz. This excerpt with the technical spec that I downloaded form the Support from Toshiba site. However, there is a program called Belarc advisor installed that the cpu is a P3 2
-
Lenovo X 1 20A Carbo 8 left side
If rest my left hand on the left side of the carbon X 1 sound is cut, but for a rattling sound. Someone at - it this?
-
Dual booting - problem with the disk when trying to start windows
original title: problems with dual boot. Windows does not play well with others. Hello I have Windows Vista Home Premium 64-bit included with the computer. I installed Fedorah and it works on my computer. When I installed it, but I had my hard dri
-
T410 - question external displayport monitor
HelloI have problem with my T410. I connected external monitor (HP LP2475w) on displayport. All right until I wake my NB to suspend. After I wake up, I have to move the mouse (or press a key) to get an image (like the monitor has been turned off). Bu