How to initialize variables when instanciating new interface fxml
Good afternoonI have a small javaFX application,
during the passage of the authentication of the welcome interface interface I want to transfer user connection and other attributes and their use in the initialize method of the fxml welcome but I get them null?
This is the main class
the initialization of the variables is in the function loginOK()
public class MainGeoTrack extends Application{
/**
* @param args the command line arguments
*/
private Stage stage;
private Controller loggedController;
private final double MINIMUM_WINDOW_WIDTH = 390.0;
private final double MINIMUM_WINDOW_HEIGHT = 500.0;
private String addIP;
private String portService;
private String portGPS;
/**
* @param args the command line arguments
*/
public static void main(String[] args) {
Application.launch(MainGeoTrack.class, (java.lang.String[])null);
}
@Override
public void start(Stage primaryStage) throws Exception {
stage = primaryStage;
stage.setMinWidth(MINIMUM_WINDOW_WIDTH);
stage.setMinHeight(MINIMUM_WINDOW_HEIGHT);
gotoLogin();
primaryStage.show();
}
public void setAddIP(String addIP) {
this.addIP = addIP;
}
public void setPortService(String portService) {
this.portService = portService;
}
public String getAddIP() {
return addIP;
}
public String getPortService() {
return portService;
}
private void gotoLogin() {
try {
LoginController login = (LoginController) replaceSceneContent("Login.fxml");
login.setApp(this);
} catch (Exception ex) {
Logger.getLogger(Main.class.getName()).log(Level.SEVERE, null, ex);
}
}
public void loginOK(String loginController, String addIP, String portService, String portGPS) {
try {
WelcomeController welcome = (WelcomeController) replaceSceneContent("welcome.fxml");
stage.setMinHeight(768);
stage.setMinWidth(1024);
stage.centerOnScreen();
welcome.setControllerLogin(loginController);
this.setAddIP(addIP);
this.setPortService(portService);
welcome.setApp(this);
} catch (Exception ex) {
Logger.getLogger(Main.class.getName()).log(Level.SEVERE, null, ex);
}
}
private Initializable replaceSceneContent(String fxml) throws Exception {
FXMLLoader loader = new FXMLLoader();
InputStream in = Main.class.getResourceAsStream(fxml);
loader.setBuilderFactory(new JavaFXBuilderFactory());
loader.setLocation(Main.class.getResource(fxml));
AnchorPane page;
try {
page = (AnchorPane) loader.load(in);
} finally {
in.close();
}
// Store the stage width and height in case the user has resized the window
double stageWidth = stage.getWidth();
if (!Double.isNaN(stageWidth)) {
stageWidth -= (stage.getWidth() - stage.getScene().getWidth());
}
double stageHeight = stage.getHeight();
if (!Double.isNaN(stageHeight)) {
stageHeight -= (stage.getHeight() - stage.getScene().getHeight());
}
Scene scene = new Scene(page);
if (!Double.isNaN(stageWidth)) {
page.setPrefWidth(stageWidth);
}
if (!Double.isNaN(stageHeight)) {
page.setPrefHeight(stageHeight);
}
stage.setScene(scene);
stage.sizeToScene();
return (Initializable) loader.getController();
}
}public class WelcomeController implements Initializable {
@FXML
private AnchorPane principalAnchor;
MainGeoTrack app;
public String controllerLogin;
@FXML
private TreeView treeViewCar;
private Client client;
private Service service;
private List<CheckBoxTreeItem<String>> treeItems;
private int controllerId;
@FXML
private Button buttonGeolocalisation;
String addIP;
String portService;
public void setAddIP(String addIP) {
this.addIP = addIP;
}
public void setPortService(String portService) {
this.portService = portService;
}
public void setApp(MainGeoTrack app) {
this.app = app;
}
public void setControllerLogin(String controllerLogin) {
this.controllerLogin = controllerLogin;
}
/**
* Initializes the controller class.
*/
@Override
public void initialize(URL url, ResourceBundle rb) {
//this var is null
System.out.println("login" + controllerLogin);
}
@FXML
private void buttonGeolocalisationOnAction(ActionEvent event) {
//System.out.println("add ip : " + app.getAddIP());
}
}Thank you
I think the problem is that the initialize (...) method in your controller welcome is called during FXMLLoader.load (...) method. before setting the value of the variable that you want to access there is.
When I need to share data between the controllers like that, I usually create a class that encapsulates the shared data and pass the same instance of it to the constructor of each controller. You must either set the controller in the Java code (and not specify it in the FXML), or define a custom for the FXML charger controller factory that instantiates the controllers with a reference to the shared data. The first way is usually more convenient, unless for some reason you cannot change the fx:controller attribute in your file FXML.
The basic structure looks like this:
public class GeoTrackDataModel {
private final StringProperty addIP ;
private final StringProperty portService ;
private final StringProperty portGPS ;
private final BooleanProperty loggedIn ;
public GeoTrackDataModel() {
addIP = new SimpleStringProperty(this, "addIP", "");
// etc
}
// usual getXXX/setXXX/xxxProperty methods
}
public class WelcomeController {
private final GeoTrackDataModel model ;
public WelcomeController(GeoTrackDataModel model) {
this.model = model ;
}
...
public void setPortService(String portService) {
model.setPortService(portService);
}
...
}
// Similarly for LoginController
public class MainGeoTrack extends Application {
private GeoTrackDataModel model ;
...
@Override
public void start(final Stage primaryStage) {
model = new GeoTrackDataModel();
// load welcome page when logged in:
model.loggedInProperty().addListener(new ChangeListener() {
@Override
public void changed(ObservableValue obs, Boolean oldValue, Boolean newValue) {
if (newValue) {
loginOK(primaryStage) ;
}
}
});
gotoLogin(primaryStage);
primaryStage.show();
}
private void gotoLogin(Stage stage) {
LoginController loginController = new LoginController(model);
FXMLLoader loader = new FXMLLoader();
loader.setController(loginController);
loader.setLocation(getClass().getResource("Login.fxml"));
Parent page = (Parent) loader.load();
stage.setScene(new Scene(page));
}
private void loginOK(Stage stage) {
WelcomeController welcomeController = new WelcomeController(model);
FXMLLoader loader = new FXMLLoader();
loader.setController(welcomeController);
loader.setLocation(getClass().getResource("Welcome.fxml"));
Parent page = (Parent) loader.load();
// your stage size preserving trick here, if needed.
stage.setScene(new Scene(page));
}
}
Update your LoginController so it sets the values of data in the model rather than directly in the controller class itself. Now your welcome controller can retrieve these values from the model. Don't forget to update Login.fxml and Welcome.fxml to remove the attributes of fx:controller (otherwise you will get a nice runtime error saying that the control is already set).
Notice that the I put in a property for 'connected' in the data model. The intention is that your connection controller must set it to true when the user is connected (instead of hanging at the main application and call the loginOK() method directly). Your main application class can listen to this and load the home page when it changes. This means that your connection controller does not need a reference to the application class, making separation much more own responsibility (you can now use your connection controller and the controller welcome in another application if necessary).
Edited by: James_D 26 May 2013 12:10
Tags: Java
Similar Questions
-
How can you tell when your new tablet was first actervated
I bought a HP Omni 10 of 8.1 tablet model window (a final) and told me he never lit, when I first turned it on windows has been activated and the tablet was running and I don't have to put something in place.
My question is, is there a place on my tablet which recorded the time it has been activated.
Lewis of the Australia.
- OEM Activation 3.0 (OA3) at the factory. A digital product key (DPK) is installed on the motherboard BIOS during the manufacturing process. Windows 8 will be ignited automatically the first time that the computer is connected to the Internet. With systems activated by OA3, most of the computer's hardware can be replaced without the need to reactivate the software from Microsoft.
-
How will I know when I need a new computer?
How will I know when I need a new computer?
When you want to do something and your current cannot do, or can't do effectively and efficiently.
-
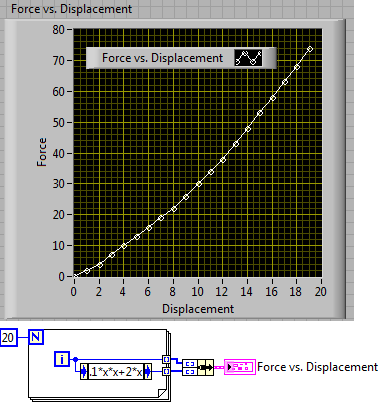
How to plot two variables when neither are expressed in time?
I know how to trace a variable against time, but how to plot two variables when neither one of them are time against each other. For example if I want to draw Let's force against remote what is the best approach to use?
Thank you.
Use an XY Chart. Use context-sensitive help to see the expected data type and refer to the examples. Consider what follows, don't forget to rename the scale labels and name:
-
How to configure Outlook for me a beep when a new message arrives
How to configure Outlook for me a beep when a new message arrives
Barry
Hotmail, or Outlook supports email notification any longer. Sorry
-
Anyone who has a problem with the system crashes when importing using the new interface to import
Anyone who has a problem with the system crashes when importing using the new interface to import
Can specify you what Adobe program you use so that we do that your post is in the right forum?
-
I bought Lightroom 5 of B & H Photo a few months ago and since then have now upgraded computers. This new computer doesn't have a hard drive and I can't figure out how to download it on my new computer. I must not have created an Adobe account when I initially purchased and downloaded on my other computer. How can I still download it if the serial number does not appear in my plans and products page? I still have the drive and everything that came with it.
Hello
Please download the Lightroom 5 application from the link below.
http://prodesigntools.com/Lightroom-5-DDL-comparison-vs-LR4.html
Serial number - please visit https://helpx.adobe.com/x-productkb/global/find-your-serial-number.html
Let us know if this helps!
Kind regards
Vivet
-
How to stop flickering / refreshing newtab-page when opening new tabs by ctrl-click on the pictures?
Often when opening new tabs of pages newtab miniatures (topic: newtab) newtab - full page refreshes or otherwise falters. This sometimes causes some tabs are not open when ctrl-click on several thumbnails in a row. Page newtab recalculates after each click what thumbnails it should show, and this could cause the flickering effect? (Although I don't see changes in miniature order.)
Hi FFanatic,
Please upgrade to the 32 version to see if it still happens. Go to Firefox and click on the update button. -
How to remove add it on to google search when the new tab is selected.
The location of the default cursor is in the search box that is displayed when a new tab is selected. It's a firefox add-on. I would remove that add on. So that the cursor will move to the browser when a new tab is selected.
Hi cor - el
Who did the trick. Now, I own empty screens when I open my home page or open a new tab. I like the simplicity - I don't want to see ads or irrelevant guff loads when I use internet. I like a clear workspace, it makes me more relaxed and more productive. I am now very happy!
Thanks a lot for your help to solve my problems.
And thanks to Monez01 to start the discussion.
All the best wishes, FriedEgg (keeping my Sunny Side Up!)
-
How to program the shift register to play only when a new user is detected user?
Hello
I'm currently developing a program of position control in labview. The program is quite simple, in which case the user will enter the distance on which he wants the table in the labview program and labview will send the signal to move a motor that will turn a ball screw to move a table horizontally to the targeted position. The criterion is that the profile of the engine depends on the distance to move, if a biphase (acceleration and deceleration) or three phase (acceleration, steady speed, deceleration) to reach the position of the target.
The problem occurs when the user wants to enter a new entry second position) for the table, as the input by the user is the position that the table should be, but the necessary input to determine what profile the engine follows depends on the distance that the table moves to the target position. Therefore, I need a function to save the entry by the user temporarily and reminds that when a new user input is detected. Hereby, I would be able to use the difference of the input (input [n + 1] [n] input) and animal feed to determine what profile the engine follows and the entry by the user can be kept in the position he wants to the table to get (to compare with encoder).
I thought to use for shift registers do, but I am not able to perform the deduction ([n + 1] - [n]) only when it detects a new entry. When I try to use registry to offset, it moves to the target location, and we only reached it will go to the original position. For example, when a user entry 90, this means that the table must be moved to the point 90. The shift register is initialized to 0, it will move to the point 90 (90-0 = 90), but arriving at 90, the shift register sends a signal of 90 (90-90 = 0) and the table back to its original position.
Is it possible that I can delay the reading of the shift register only when a new entry is detected or there at - it another way for me to achieve what I want?
I tried searching the forum site and neither discussion but could not find similar problems. Thank you for your help in advance.
As I understand it, the use of shift registers with a structure of the event (to detect a user event when the user enters a new value) should solve the problem. Do not forget to post your request (or a version of it that isolates the issue) when you arrive at the lab, if we can get a clear visual of the issue you are facing.
-
Get the current value of the variable when reaching CNVCreateSubscriber
I use CNVCreateSubscriber () to create a subscription read to a network Variable: whenever the value of the variable changes, the DataCallback is called and I'm able to get the new value of the variable.
But how to get the value of the variable when a subscription is created?
I read in the help CNVCreateBufferedSubscriber () returns this information, but I wonder if using CNVGetDataFromBuffer () in a polling loop has the same performance as the approach to DataCallback of CNVCreateSubscriber ().
In addition, the dataStatus (CNVGetDataFromBuffer) parameter is different for different Subscribers? (that is if I have multiple subscribers, CNVStaleData is related to the specific Subscriber or is a global property of the variable)?
CNVData data;
CNVGetConnectionAttribute (customer, CNVMostRecentDataAttribute, &data);)
-
How about a readme for the new signing of RVS - 4000 IPS: 1.42 in firmware 1.3.2
Hello
How about a readme for the new Signature IPS 1.42 inside the new firmware to version 1.3.2 RVS-4000?
Or am I just too fast and it comes out in a bit?
Thank you
Bruce
Bruce,
You are right. He left this time by mistake. We will solve it. In the meantime, here's what it will be:
RVS4000/WRVS4400N IPS Signature Release Note
Version: 1.42 rules Total: 1097
In this signature, we talked about the exploits/vulnerabilities and applications
as below:Supported P2P application called BitTorrent up to version 5.0.8.
Supported P2P application named uTorrent up to version 1.7.2.Version: 1.41 rules Total: 1098
In this signature, we talked about the exploits/vulnerabilities and applications
as below:-EXPLOIT the MS video control ActiveX Stack Buffer Overflow
A buffer overflow vulnerability exists in Microsoft DirectShow.
The defect is due to the way Microsoft Video ActiveX Control parses image files.
An attacker can convince the user target to open a malicious web page to exploit
This vulnerability.-EXPLOIT the Injection SQL Oracle database Workspace Manager
Multiple SQL injection vulnerabilities exist in Oracle database server product.
The vulnerabilities are due to inadequate sanitation of input parameters
in the Oracle Workspace Manager component. A remote attacker with user valid
credentials can exploit these vulnerabilities to inject and execute SQL code
with lift is SYS or privilegesof WMSYS.Supported P2P application named uTorrent up to version 1.7.2.
Content signature for 1.41
========================================================================
Added new signature:
1053635 video MS stack buffer overflow EXPLOIT control ActiveX-1
1053636 video MS stack buffer overflow EXPLOIT control ActiveX-2
1053632 EXPLOIT Oracle database Workspace Manager SQL Injection-1
1053633 EXPLOIT Oracle database Workspace Manager-2 SQL Injection
1053634 EXPLOIT Oracle database Workspace Manager SQL Injection-3Updated the signature:
1051783 P2P Gnutella Connect
1051212-P2P Gnutella Get file
1051785 P2P Gnutella UDP PING 2
1051997 P2P Gnutella Bearshare with UDP file transfer
1052039 P2P Gnutella OK
Get Foxy P2P file 1052637Signature removed:
1050521 Worm.Klez.E1 - 1
1050522 Worm.Klez.E1 - 2
1050523 Worm.Klez.E1 - 3
1050524 Worm.Klez.E2 - 1
1050525 Worm.Klez.E2 - 2
1050526 ¡v Worm.Klez.E2 3
1050536 Worm.Blaster.B - 1
1050537 Worm.Blaster.B - 2
1050538 Worm.Blaster.B - 3
1050539 Worm.Blaster.C - 1
1050540 Worm.Blaster.C - 2
1050541 Worm.Blaster.C - 3Number of rules in each category:
========================================================================
Back/DDoS 51
Buffer overflow: 241
Access control: 92
Scan: 41
Trojan horse: 62
Misc: 3
P2P: 40
Instant Messaging: 121
VRU/worm: 410
Web attacks: 37Version: 1.40 rules Total: 1091
In this signature, we talked about the exploits/vulnerabilities and applications
as below:1053406 FEAT MS IE HTML Embed Tag Stack Buffer Overflow (CVE-2008-4261)
An error of border during the processing of a too long file name extension specified
inside a "EMBED" tag can be exploited to cause a stack-based buffer overflow.1053421 USE MS IE XML Handling Remote Code Execution (CVE-2008-4844)
The vulnerability is due to a use-after-free error when composed
HTML elements are related to the same data source. This can be exploited to
dereference of a pointer released by a specially designed HTML document memoryVersion 1.38
In this signature, we addressed the following exploits/vulnerabilities and
applications:1. support for P2P, BitTorrent and eMule applications.
Version 1.33
In this signature, we addressed the following exploits/vulnerabilities and
applications:1. support application IM named AIM (http://dashboard.aim.com/aim) until
version 6.5.2. support application IM called MSN (http://get.live.com/messenger) until
version 8.1.3 PcShare is a Trojan tool that can remotely administer an attacked computer.
4-CVE-2007-3039: the vulnerability is due to an error of limit in the
Microsoft Message Queuing (MSMQ) service during the treatment of MSMQ messages.
This can be exploited to cause a buffer overflow by sending specially
packages designed for the MSMQ service.Version 1.32
In this signature, we addressed the following peer-to-peer applications:
1. named IM application PURPOSE up to version 6.5 support.
2. press the request of IM named MSN until version 8.1.Version 1.31
In this signature, we addressed the following peer-to-peer applications:
1 P2P application called BitTorrent up to version 5.0.8 support.
2. support the P2P application named uTorrent up to version 1.7.2.
Version 1.30
In this version, we have addressed the following vulnerabilities in Microsoft
applications:1 SUBMISSION-24462: dereference of a pointer Null vulnerability exists in some versions
Microsoft Office. Remote attackers can trick users into visiting a
specially designed web page. The symptom includes a denial of
condition of service for the process in question.2 Microsoft Security Bulletin MS07-027: Microsoft Windows support
Services NMSA Session Description object ActiveX control does not reach
restrict access to dangerous methods. This vulnerability could allow
a remote attacker to execute arbitrary code on an affected system.Version 1.29
In this version, we have addressed the following exploits/vulnerabilities and
peer-to-peer applications:1 Microsoft Security Advisory (935423): there is one based on the stack
in Microsoft Windows buffer overflow. The vulnerability is due
for insufficient format validation when handling incorrect ANI
file cursor or icon. A remote attacker can exploit this
vulnerability of prompting grace target user to visit a malicious
Web site by using Internet Explorer. A successful operation would be
allow the execution of arbitrary code with the privileges of the
currently logged in.2. support a named QQ instant messaging application blocking until the
2007 Beta1 and Beta2 version.Version 1.28
In this signature, we address the following exploits/vulnerabilities:
Microsoft Security Bulletin MS07-014: there is a buffer overflow
vulnerability in Microsoft Word. The vulnerability is created due to
a flaw in the Table entry of the Section within the structure of Table data flow.
An attacker could exploit this vulnerability by tricking a user to open
a designed Word file. Exploitation of the vulnerability may result
injection and execution of arbitrary code in the security context
the user target.Microsoft Security Bulletin MS07-016: there is an alteration of the memory
vulnerability in Microsoft Internet Explorer. The flaw is due to a bad
posting lines of response in the responses from the FTP server. By persuading a user
to visit a malicious website, an attacker could run arbitrary on code
the target system with the privileges of the currently logged in user.Version 1.26
In this signature, we addressed the following exploits/vulnerabilities:
CVE-2006-5559: there is a memory corruption vulnerability in
the ADODB. Connection ActiveX control in Microsoft Internet Explorer.
The flaw is due to improper validation of the data provided to the
Execute method. By persuading target the user to visit a malicious
Web site, an attacker can cause the application process
to terminate or possibly divert its flow of execution to arbitrary
code.Version 1.25
In this signature, we addressed the following exploits/vulnerabilities:
Microsoft MS06-070 security bulletin: MS Windows 2000 Workstation
Service (WKSSVC. (DLL) has a remote code execution vulnerability. One
unauthenticated attacker could exploit this vulnerability to run
arbitrary code with the privileges of the level system on Windows 2000 and
Windows XP computers.Version 1.24
In this signature, we addressed the following exploits/vulnerabilities:
1 Microsoft Data Access Components (MDAC) has a remote code execution
vulnerability in the RDS object. DataSpace ActiveX control. A remote attacker
could create a specially designed and host the malicious file on a
Web site or send it to the victim through e-mail. When the file is opened,
the attacker can run arbitrary code on the victim's system.2. control WMI Object Broker ActiveX (WmiScriptUtils.dll) in Microsoft
Visual Studio 2005 has a vulnerability that could allow a remote
attacker to execute arbitrary code.3 Microsoft Internet Explorer has a type of heap buffer overflow vulnerability.
A remote attacker could create a malicious web page containing COM objects
Daxctle.OCX HTML when instantiated as an ActiveX control and the thing the
victim to open the web page. By this attack, the attacker to execute
arbitrary code on the victim's browser.Version 1.23
In this version, we have addressed the following exploits/vulnerabilities:
The vulnerability lies in some of the engines in Microsoft XML core
Windows. It is the result of the failure of the engine to properly manage the
bad arguments passed to one of the methods associated with the XML
purpose of the request.Version 1.22
In this version, we discussed the exploits/vulnerabilities as follows:
Vagaa is a P2P that supports the network BitTorrent and eDonkey software.
It can be downloaded from the two network. The software is mainly used in people's Republic of CHINA.
There are some problems with this software because it didn't follow the official eMule Protocol.
The question can be referenced on the wiki (http://en.wikipedia.org/wiki/Vagaa).
Classify us Vagaa as eDonkey2000 program and allow admin users to disable in the user Web interface.Version: 1.21
In this version, we have addressed vulnerabilities exploits as below:
Microsoft Internet Explorer WebViewFolderIcon has a buffer overflow
Vulnerability. A remote attacker could create a malicious Web page and
trick the victim to open. By this attack, the attacker could cause buffer
Overflow and crash the browser of the victim.Version: 1.20
In this version, we discussed the exploits/vulnerabilities and applications
as below:1 foxy is a P2P application that can search and download music and movies.
Foxy follows most public Gnutella P2P protocol but still has its own
signature under certain conditions. After the inclusion of the file Get Foxy P2P
rule, we can perfectly detect and block the Foxy and it will be detected as Gnutella.
Foxy can be blocked by deactivating Gnutella.2 Microsoft Internet Explorer 6.0 and 6.0SP1 have impaired memory
vulnerability in the ActiveX component. A remote attacker can create a
malicious Web page and trick the victim to open the web page. By this attack.
the attacker could cause the crash of the browser of the victim or to execute arbitrary code.3 Microsoft Internet Explorer has heap buffer overflow vulnerabilities
Vector Markup Language (VML). A remote attacker can create a malicious Web site
page and the thing the victim to open the web page. By this attack, the attacker
could cause the buffer overflow and execute arbitrary code on the victim's browser.Version: 1.19
In this version, we have added a rule to meet cross-domain redirect
Microsoft Internet Explorer vulnerability (MS06-042). The vulnerability
is caused by the inappropriate use of URL redirection by the object.documentElement.outer
HTML property. A remote attacker could create a malicious web page and
trick the victim to open the web page. With this attack, the attacker could
run arbitrary code on the victim's browser and get sensitive information.Version: 1.18
In this version, we have added the 6 rules to facilitate the blocking of QQ, the most
popular instant Messenger in China. There are several versions of QQ on the
official download site. Currently, we can detect and block QQ until the
Version 2006 Sp3 beta 2.Version: 1.17
In this version, we discussed the exploits/vulnerabilities below:
1. the Server Service in Microsoft Windows 2000 SP4, XP SP1 and SP2, server
2003 and SP1 have a buffer overflow vulnerability. A remote attacker
could exploit a server response designed to cause the buffer overflow and run
arbitrary code on the victim's system.2 hyperlink Object Library in Microsoft Windows 2000 SP4, XP SP1 and SP2,
Server 2003 and SP1 have a code execution vulnerability. A remote control
attacker could send a malicious Office document containing a
specially designed hyperlink to a victim in an email or host the file on
a web site. When the operator successfully this vulnerability, a remote control
attacker to execute arbitrary code with the privileges of the victim.3 Microsoft Word XP and Word 2003 have a remote code execution vulnerability.
A remote attacker could host a DOC file on a Web site. If successfully
exploiting this vulnerability, remote attacker could execute arbitrary code
with the privilege of the victim.Version: 1.16
In this version, we discussed the exploits/vulnerabilities below:
1 Microsoft Excel 2000, XP and 2003 Excel have a remote code execution
vulnerability, due to an error in Excel when incorrect URL handling
channels. A remote attacker could send a malicious .xls file of a victim
in an email or host the file on a web site. When the operator successfully this
vulnerability, a remote attacker to execute arbitrary code with the victim
privileges.2 hyperlink Object Library in Microsoft Windows 2000 SP4, XP SP1 and SP2,
Server 2003 and SP1 have a code execution vulnerability. A remote control
attacker could send a malicious Office document containing a
specially designed hyperlink to a victim in an email or host the file on
a web site. When the operator successfully this vulnerability, a remote control
attacker to execute arbitrary code with the privileges of the victim.3 Microsoft Windows XP/NT/2000/2003 have a denial of service vulnerability.
A remote attacker can send a malicious SMB packet causes the victim computers
Crash. -
Creating a new interface on the Pix 516F
I've created and activated a new interface (DMZ) on a 516F Pix. In the MDP a default outbound rule was automatically created for this interface. I could get out to the internet without any problem. However, I need to open some ports in the DMZ to the inside interface. When I add a new access rule, the outbound rule disappears and I can no longer to the internet. I tried to recreate a similar rule to allow all tcp traffic to the external interface of the demilitarized zone. The MDP has accepted the rule, but when I went back to look at it, the rule has been changed from the outside to the inside.
How can I maintain the default outbound rule and always open ports inside?
Thank you
Nick
In General:
allow access to your internal network (web servers, printers, regardless.) (BE SPECIFIC!)
deny all access to your internal network (deny ip no matter what subnet)
allow an ip
-
Error in the new interface consultation documents
Hello
I created a new type of document and I use script idoc for certain metadata are
autofilled and can perform the download of the documents of the new interface, but when I see the documents
I have an error: System error has occurred. Contact your site administrator.
This problem occurs only in the new interface in the native interface can access the documents.
Someone knows how to help?
Thank you
Hello
Thank you all, I am now managing read documents
After you change a type of metadata that were incorrect.
Thank you
-
How do I know when I make a createInsert?
How do I know when I make a createInsert, this is to hide a button when you do this, I use a workflow.
my version of jdeveloper is 12 c
Hello
If you use the createInsert as a method of appeal in the workflow. This is your form/table will come new lines and you want to disable a button.
Your workflow can be as below
CreateInsert---> Page.
To do
Properties to 1.) your method call and bind the method property to a method in a bean (bean stored in a larger scope or the workflow with extended view)
(2) call the create programmatically insert operation in this method.
(3) and in this method after the createinsert, set a Boolean variable in pageFlowScope.
(4) to this variable in the property to disable or the visible property of the button you wabt to hide/devil.
for example:
public void doCreateInserOperation() {}
try {}
Call programmatically CreateInsert
Links DCBindingContainer = (DCBindingContainer) getBindingContainer ();
bindings.getOperationBinding("CreateInsert").execute ();
Set a variable in the extended flow page
AdfFacesContext.getCurrentInstance () .getPageFlowScope () .put ("disableButton", true)
} catch (Exception e) {}
e.printStackTrace ();
}
}
public BindingContainer {} getBindingContainer()
FacesContext facesContext = getFacesContext();
Application app = facesContext.getApplication ();
ExpressionFactory elFactory = app.getExpressionFactory ();
ELContext elContext = facesContext.getELContext ();
ValueExpression valueExp = elFactory.createValueExpression (elContext, "#{bindings}", Object.class);
return (BindingContainer) valueExp.getValue (elContext);
}
You can access this variable in EL expression # {pageFlowScope.disableButton}. So, when your page showing he will be in mode CreateInsert and the button is disabled/hidden.
I hope this will help you.
With respect,
Gijith.
Maybe you are looking for
-
Toshiba 40L5441DG - Led shows red and green light
My Toshiba 40L5441DG were now waiting for 72hrs, and the Led is showing red and green lights.I just bought 3 weeks ago... I need help pls.
-
Satellite L500-19Z - limited WIFI access
Hello. Last week I had real problems with my laptop, access to the Wifi network. We have many other devices that can still use the internet on our wifi but my laptop seems to be difficult to access. While booting, the laptop connects to the network,
-
my desktop icon is now working... "If I try to open any application a messege always apper" open with "a list of program... when I try to open the Control Panel control panel open, but when I try to open Add / Remove program error appear c:\windows\s
-
a flash 7 premature front of shutter
Recently, I had a flash for my Sony a7. The flash pass seconds before the shutter making useless flash. Is there a setting I changed that it would cause? Or should I not configuration flash correctly? Thanks in advance.
-
Printer keeps printing a blank cover page - don't want
My printer is a HP LJ 3050 all in one. "In the preferences of the printer, the" Paper/quality"tab shows that under"special pages", I ask"covers"so many pages printed on different paper." I don't know how these choices got there, don't want and can'