L2l AAS behind router
Can an ASA initiate a VPN L2L on NAT - T behind a router?
The VPN can be established successfully, when our third party start the connection, but not when we leave it to our end.
Many providers do not support this scenario, I would like to know if Cisco do.
Yes it will work. The SAA can be behind a NAT as an originater IPSec as an IPSec responder. Of course As NAT is configured correctly if the ASA's answering machine.
--
Don't stop once you have upgraded your network! Improve the world by lending money to low-income workers:
http://www.Kiva.org/invitedBy/karsteni
Tags: Cisco Security
Similar Questions
-
Termination of VPN on Pix behind router IOS with private subnet
OK, basically, I wonder if it is possible to terminate a VPN connection on a Pix 506 Firewall which is behind a router IOS. The public interface of the Pix 506 have a private on a 29 ip address will IOS within the interface. Network is configured as follows:
Internet as 10Base T
| (5 public - X.X.X.34. 38)
| (In WIC-1ENET)
| (.34 assigned to interface)
Cisco 1760
| (Pomp) | (WIC-4PORTSWITCH)
| | (10.0.0.1 29 on 1760)
Net private Pix 506
(192.168.1.0) (10.0.0.2 29 on Pix)
Now, two internal interfaces of the 1760 are configured to PAT on the IP of the interface of the 1760 and all internet traffic goes perfectly. None of the access lists are currently applied anywhere on the 1760 and a static translation on the 1760 is configured pour.35 to 10.0.0.2 ('public' ip pix). RDP and other services authorized in the pix access list work perfectly well from the outside world when you enter a.35, but if I try to terminate a VPN from a pix 501 for the pix 506 offsite using the Intellectuelle.35 property, it does not work.
Is it possible to do this type of work setting.
I realize I could put an external switch to 1760 and run the public subnet directly and individually in the 1760 and Pix 506, however, I really would prefer not no need to do so if it is possible to avoid it.
Remove the crypto map to the interface on the PIX and reapply.
-
The managed behind router switch remote access?
What is the best way to access remotely to a switch behind a router? I will use a switch SF300, and there is no server.
For points of access (PA) behind a router, I give each a diffferent LAN address and port number. In router I have forward TCP traffic with the single port/LAN IP. Then using the port numbers with the address of the static router, the browser can remote access to the router or the attached AP. But where do I put the managed switch LAN port number? Assume default is port 80 and I would change to 8001 to switch #1; 8002 to switch #2; etc. Could not find this info in the manual of configurtion.
Hello
At this point, I would recommend a call to the Cisco Small Business Centre at 1-866-606-1866 support so that action can be taken and your configuration can be reviewed.
I have reproduced the concern here and I am able to remotely manage my switch SF300 with an RV082 as the router.
My rule in the RV082 are as follows:
Creating a custom topic UPnP service. Create SF300 application name (it is a basic text field and can be any name), 8001 an external port and internal port 80. I send to the address IP internal SF300 switch and click the check box. From there on, I select Add to the list. Once it appears in my list, I then click Save settings at the bottom of the page.
Thank you!
Dave
-
L2l multiple rays routing traffic
I have a problem I hope you can shed some light on this. I have all 3 sites connected with VPN/IPsec ikev2 tunnels using ASA 5505 and 5510 with 8.4 + code. Please see the image below for more details on my installation. All VPN tunnels are up and send traffic across the immediate neighbor, the problem is that I can't ping or access the ASA2 subnet ASA3 subnet or ASA2 of ASA3, that I'm missing in my setup? Please see below and thank you in advance for any help you can provide this.

ASA 3 VPN Config:
protocol esp integrity sha-1
crypto ipsec security-association pmtu-aging infinite
crypto map crypto_map 1 match address AS3_ACL
crypto map crypto_map 1 set peer 1.1.1.1
crypto map crypto_map 1 set ikev2 ipsec-proposal aes_256
crypto map crypto_map interface outside
crypto ca trustpool policy
crypto ikev2 policy 1
encryption aes-256
integrity sha256
group 2
prf sha256
lifetime seconds 86400
tunnel-group 1.1.1.1 type ipsec-l2l
tunnel-group 1.1.1.1 general-attributes
default-group-policy ipsec_group_policy
tunnel-group 1.1.1.1 ipsec-attributes
ikev2 remote-authentication pre-shared-key *****
ikev2 local-authentication pre-shared-key *****
vpn-idle-timeout 6000
vpn-session-timeout none
vpn-tunnel-protocol ikev2
nat (inside,outside) source static all_inside_networks all_inside_networks destination static all_outside_networks all_outside_networks no-proxy-arp route-lookup
object-group network all_inside_networks
network-object 10.0.1.0 255.255.255.0
object-group network all_outside_networks
network-object 10.0.0.0 255.255.255.0
network-object 10.0.18.0 255.255.255.0
access-list ASA3_ACL extended permit ip object-group all_inside_networks object-group all_outside_networks
Hello
Seems to me that your ASA1 missing certain rules in the 'card crypto' ACL
ASA3_ACL list extended access permitted ip object-group objects ASA3 ASA2-group
ASA2_ACL list extended access permitted ip object-ASA3 group ASA2 object
You miss also the "nat" command I mentioned
public static ASA2 ASA2 destination NAT (outside, outside) static source ASA3 ASA3
You do not have a second order of "nat" because this must match the connection management training is the
Hope this helps
-Jouni
-
Hello
I have ASA 5505 behind a router, which is also a dmvpn (the router), on my ASA RADIUS I configured a remote access vpn.
But when I try to forward the VPN ports to my asa, I get problems with stability, with my talk about vpn on the router.
Is it possible to have a dmvpn to the router and vpn for remote access to my ASA?
I have attached the running configuration.
Thank you
Joelle,
The problem here is that your router and the ASA want to use udp port 500 and udp port 4500. Of course if you forward incoming ports then the dmvpn is not going to work and vice versa. What you can try to have your ezvpn use ipsec-over-tcp on port 10000 and that transmits to the place.
On the SAA configure "crypto isakmp ipsec-over-tcp port 10000.
On the change of the client connection information, click the transport tab and select ipsec-over-tcp.
On the router port forward tcp 10000 to the ASA.
Hope that helps.
-Jay
-
Hi all
We just bought a 570W ISA. I have a router in 1921 that we use for our DSL connection. Basic configuration on 1921 only for the DSL connection and pass-through. How do you get the NATTING on ISA to allow internal users internet. External interface on the ISA will be IP private inside the interface on 1921, so I know you do a NAT static external interface of the ISA, but not familiar with GUI CÉP. Someone, can someone help me?
Thank you
Mike
A few final things to check on the ISA
- Make sure that the changes above do not affect the routing table.
- Networks--> routing--> routing table, make sure there is still a 0.0.0.0 0.0.0.0 for gateway 10.255.0.1
- If it is gone, you can add it in back via the static routing in networks--> routing
- Networks--> routing--> routing table, make sure there is still a 0.0.0.0 0.0.0.0 for gateway 10.255.0.1
- You can also try to change the Mode of WAN/LAN routing on IT.
- Go to networks--> routing--> routing Mode
- I don't think this is necessary, but read the description, I could see where it might be. I think it's more like SHEEP bridge
- Go to networks--> routing--> routing Mode
Still, I don't think you need to perform one of these, but thought I would mention them as you go over there to help expedite your resolution.
- Make sure that the changes above do not affect the routing table.
-
VPN problem - "C1712 behind router Linksys ' connection to PIX515e
Hi all
I have a question about VPN (lan-to-lan).
My setup is the following:
10.1.20.x-[PIX515e_central site VPN concetrator]-(( ISP ))-[LINKSYS BEFSX41 router]-[Cisco1712_branch] - 192.168.14.x
I would like to create tunnel VPN between C1712 and PIX515 (lan-to-lan), so users of 192.168.14.x would be able to connect to servers located on a central site in network 10.1.20.x.
NAT - T is manually enabled on PIX and 'IPsec passtrough' is enabled on the Linksys router. Then what should I do now to create a VPN tunnel?
What is the basic C1712 and PIX515e configuration to make it work?
All other industries (8) work, but they are directly connected to the internet via C1712, so without router Linksys in front of him. Thus, PIX is already properly configured for this configuration.
I guess that the installer with Linksys router does not work because of PAT.
6.3 (4) version PIX
C1712 Version 12.4
Please advise!
Thank you very much in advance!
This line is incorrect on the router configuration:
IP nat inside source list 6 interface FastEthernet0 overload
Please, remove it and have her take:
overload of IP nat inside source list 101 interface FastEthernet0
Hope that solves this problem.
-
Standard Gmail view does not work behind the router WRT110
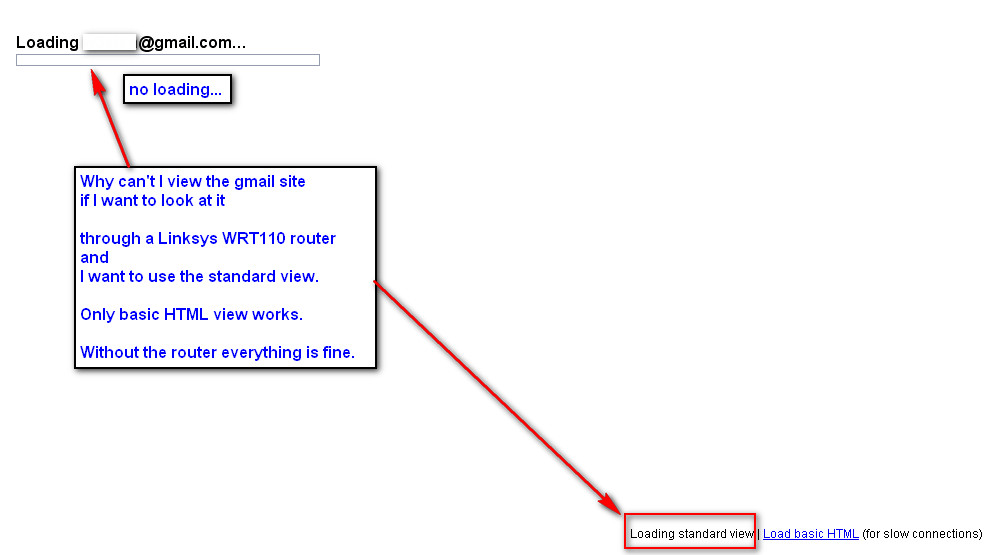
I use the gmail webmail site.
Behind router wrt110 and in standard gmail view, I can't read my emails
because the site stops loading in.
The problem only occurs in the browser Firefox 3.5.7.
In Internet Explorer 8, everything seems fine.
Help, pls.
Problem solved.
NoScript Firefox addon was guilty.
It automatically blocks goole.com scripts.
After the activation of google in noscript standard display GMail works again.
-
Router dual-band only invited E3200 access works
Hello, I am looking for help on my router. Today my main band has stopped working and I can not connect. I tried to change the password and am still unable to connect, and can't even get an option to enter the new password to other devices, even if the signal is recognized. My guest access works very well. Can anyone help?
Yes, the router behind router can be a bit confusing, but I think you're in luck because the E3200 supports bridge mode.
Simply follow the instructions to configure your E3200 in Bridge mode.
The alternative if you want to use your E3200 as the main router is to set your modem in Bridge mode, if it is able.
-
Very strange Vista problem when behind a switch
I bought the router WRT610N along a LINKSYS EG008W 10/100/1000Mbps Gigabit Workgroup Switch. In my small office (4 closed offices and an area central + kitchen + room + storage + a bowl of chocolate for my pregnant wife), we were using our ISP (Bell) modem/router (Wi - Fi + 4 ports RJ-45) with switch 8 old ports. There are 3 Mackintosh a XP and a Vista workstations and a D - Link DNS-323 NAS on the local network, + XP/Vista/Mac laptop wireless now and then. I wanted to update our stuff for a flow rate of localized Gigabyte (still looking autour to build a Xeon server + file server), with Wireless N Dual-Band, and the following configuration has worked right away without installing anything same software-wise, nor the need to reset - restart a computer or device: all records shared Internet connection was available immediately which was very satisfying. I even bought Cisco Network Magic Pro 5.5 and I'm glad I did, this is a really well done and intuitive graphic interface to manage small business networks (one license for PC stations up to 8 + 8 Mac stations), if not the best out there for its target market niche and prices vary.
However, there is a confused about Vista glitch: I have to fix directly on one of the ports on the WRT610N, it won't work if I try behind a switch box (although it works for all other operating systems), using the following network configuration:
- all the workstations are connected to the switch, focused on one of the ports of WRT610N
- The Internet WRT610N port Bell's DSL modem
- SIN D - Link DNS - 323 and the port 3 WRT610N
- EG008W Switch 4 port WRT610N 1 port
- Workstation to the switch EG008W 2 Vista port
- Workstation XP and switch EG008W 3 port
- Workstations Mac to switch EG008W ports 1, 5, and 6
From the XP desktop, I see Macs and access the NAS. From a Mac, I can see + access the XP and the NAS. Vista station connects any behind the switch EG008W: I * must * plug into the router, WRT610N, something I don't want to because the switch is there to serve as a wall mounted RJ45 plugs into each office (where the Mac XP and Vista workstations are located)... Any help or link to a relevant reference would be greatly appreciated.
Kevj, thanks for answer you, I came here to close the topic because I put the finger on the problem and it is resolved: the problem lies elsewhere, it is not the calbling or some other hardware problem. I have replace the Vista box by a mobile XP, using the same wiring right and everything worked well, he wasn't a wiring problem... Note that the workstation is a Dell Studio which comes with a Realteck Gigabit controller box (so I guess that many other models/brands also provide this same controller, which means that many other users can know this problem).
Here's what I did:
- I got rid of Vista by installing Windows 7 and everything worked fine!
- I then published an update of Windows from the Microsoft site, which offered a patch for the familly Realteck GBE (among other patches) controller
- After restarting the computer, the network was not accessible more while the Win7 box is behind the Swithcher: it behaved exactly as when it was Vista (indicating that the adapter was unplugged when behind the selector and then giving access while behind router WRT)!
- So I restored the last just restore point prior to the update of the controller and got everything back to normal; I then did another session of MS Windows Update without the Realteck driver patch, and everything worked well.
Conclusion: DO NOT update your controller driver Realteck GBE from Microsoft, whether for Vista or Windows 7, it has a bug which takes place whenever your Vista/Win7 box is behind a DMZ sub-segment of LAN using a blender (switch-router-router/DSL-ISP).
Note: the WRT610N works like a charm! It is plugged with a RAID0 of DNS-323 1 TB NAS, one 8-port Gigabit switch power supply 3 macs, 1 XP and 1 Windows 7, Wi - FI works well enough (G mode, while the band n is open - I don't have a camera of 5 GHz yet so I can't say for this FREQUENCY range) and I left the own DSL access available Point. Which means that there are 3 Access Points: one directly on the DSL router that leaves the LAN in a DMZ (cannot be seen or accessed from the mobile) and 2 more on the WRT610N dual band access not only to the Internet but also for shared resources). Blue color for the port connected to the dwitcher, which means a Gigabit local LAN, and green port for the DNS-323 whitch works to 100 MB (unfortunately they still do not have a Gigabit NAS). I am very happy with the product, more when combined with Network Magic Pro.
-
I get the error message on debugging ipsec-l2l tunnel
Hello
Can someone help me understand the debug message?
I get the error message on debugging ipsec-l2l tunnelI tried to configure an ASA5520 with an ipsec-l2l to ios router 1721
= 1721 router =.
Cisco 1721 (flash: c1700-k9o3sy7 - mz.123 - 2.XC2.bin)
80.89.47.102 outside
inside 10.100.110.1 255.255.255.0Debug crypto ipsec
Debug crypto ISAKMP-config-
crypto ISAKMP policy 1
BA 3des
md5 hash
preshared authentication
Group 2
0 1234567890 128.39.189.10 crypto isakmp key address
!
!
Crypto ipsec transform-set esp-3des pix-series
!
ASA 10 ipsec-isakmp crypto map
defined by peer 128.39.189.10
transform-set pix - Set
match address 101
!
!
interface FastEthernet0Outside-interface description
IP 80.89.47.102 255.255.255.252
NAT outside IP
card crypto asa
!
interface Vlan10
Inside description
IP 10.100.110.1 255.255.255.0
IP nat inside!
!
IP nat inside source overload map route interface FastEthernet0 sheep
!
access-list 101 permit ip 10.100.110.0 0.0.0.255 10.100.4.0 0.0.3.255
!
access-list 110 deny ip 10.100.110.0 0.0.0.255 10.100.4.0 0.0.3.255
access-list 110 permit ip 10.100.110.0 0.0.0.255 any
!
sheep allowed 10 route map
corresponds to the IP 110
!= Config ASA =.
Cisco 5520 ASA Version 8.2 (1)
128.39.189.10 outside
inside 10.100.4.255 255.255.252.0Debug crypto ipsec
Debug crypto ISAKMP-Config-
!
Allow Access-list extended sheep 255.255.252.0 IP 10.100.4.0 10.100.110.0 255.255.255.0
!
access extensive list ip 10.100.4.0 outside110 allow 255.255.252.0 10.100.110.0 255.255.255.0
!Crypto ipsec transform-set ESP-3DES-MD5-esp-3des esp-md5-hmac
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
86400 seconds, duration of life crypto ipsec security association
Crypto ipsec kilobytes of life - safety 4608000 association
card crypto outside_map 11 match address outside110
peer set card crypto outside_map 11 80.89.47.102
card crypto outside_map 11 game of transformation-ESP-3DES-MD5
outside_map interface card crypto outside
crypto ISAKMP allow outside
crypto ISAKMP policy 10
preshared authentication
3des encryption
md5 hash
Group 2
life 86400!
attributes of Group Policy DfltGrpPolicy
VPN-idle-timeout no
Protocol-tunnel-VPN IPSec!
tunnel-group 80.89.47.102 type ipsec-l2l
IPSec-attributes tunnel-group 80.89.47.102
pre-shared key 1234567890Concerning
TorYou have a transformation defined on the SAA named ESP-3DES-MD5? Your crypto card refers to that but I don't see it listed in the config you have posted. I don't have much experience with routers, but is MD5 hashing algoritm (and why it is not)?
James
-
VPN router to the problem of the ASA
Hello world.
I am doing a VPN between a router and a series of ASA5500 and difficulties.
The router part is 100% correct because it is a daily task, but miss me something on the side of the ASA of the things.
The ASA also has remote via IPsec tunnels clients as you'll see below, so I have to make sure that continues to work!
It is a fairly urgent question. So any help or advice can be provided, it would be very appreciated!
Here is the router part:
!
crypto ISAKMP policy 1
BA 3des
preshared authentication
Group 2
isakmp encryption key * ASA-PUBLIC-IP address
ISAKMP crypto keepalive 100
!
!
Crypto ipsec transform-set transform-set esp-3des esp-md5-hmac
!
10 customers map ipsec-isakmp crypto
defined ASA-PUBLIC-IP peer
transform-set transform-Set
match address 102
QoS before filing
!
!
Access-list 100 remark [== NAT control ==]
access-list 100 deny ip 192.168.2.0 0.0.0.255 10.1.1.0 0.0.0.255
access-list 100 permit ip 192.168.2.0 0.0.0.255 any
Access-list 102 remark == [VPN access LISTS] ==
access-list 102 permit ip 192.168.2.0 0.0.0.255 10.1.1.0 0.0.0.255
Access-list 102 remark
(Crypto card has been applied to the corresponding interface)
SIDE OF THE ASA:
permit inside_nat0_outbound to access extended list ip 10.1.1.0 255.255.255.0 10.1.1.192 255.255.255.224
prevpn_splitTunnelAcl list standard access allowed 10.1.1.0 255.255.255.0
access-list Interior-access-in extended permit ip 10.1.1.0 255.255.255.0 any
access-list Interior-access-in extended permit icmp 10.1.1.0 255.255.255.0 any
access list for distance-extended permitted ip network 10.1.1.0 255.255.255.0 192.168.2.0 255.255.255.0
Global (outside) 1 ASA-PUBLIC-IP
NAT (inside) 0-list of access inside_nat0_outbound
NAT (inside) 1 10.1.1.0 255.255.255.0
NAT (inside) 0 192.168.2.0 255.255.255.0
Crypto ipsec transform-set ESP-3DES-MD5-esp-3des esp-md5-hmac
Crypto-map dynamic outside_dyn_map 20 the transform-set ESP-3DES-MD5 value
card crypto outside_map 40 match remote-network address
card crypto outside_map 40 game peers REMOTE-router-IP
outside_map card crypto 40 the transform-set ESP-3DES-MD5 value
map outside_map 65535-isakmp ipsec crypto dynamic outside_dyn_map
outside_map interface card crypto outside
ISAKMP allows outside
part of pre authentication ISAKMP policy 10
ISAKMP policy 10 3des encryption
ISAKMP policy 10 md5 hash
10 2 ISAKMP policy group
ISAKMP life duration strategy 10 86400
tunnel-group prevpn type ipsec-ra
tunnel-group prevpn General-attributes
address pool VPN-pool
Group Policy - by default-prevpn
prevpn group of tunnel ipsec-attributes
pre-shared-key *.
tunnel-group REMOTE-router-IP type ipsec-l2l
REMOTE-router-IP tunnel-group ipsec-attributes
pre-shared-key *.
Hi Chris
first on the router make this change to littil than u ned to add md5 as hashing whil employees u th in the asa and the router u did not, so the default is sha!
do
crypto ISAKMP policy 1
md5 hash
now on the SAA as I see that there is a problem in nat0 you line l2l tunnel
so that you need to look like:
permit inside_nat0_outbound to access extended list ip 10.1.1.0 255.255.255.0 192.168.2.0 255.255.255.0
You also need a permit for the ipsec traffic, the following command will allow all ipsec traffic if you want to filter traffic not to use this command and use rather ACLs on the external interface, but following that to allow all traffic to your L2L and remote vpn access:
Permitted connection ipsec sysopt
so, please:
clear xlate and reload the ASA then attempt to leave the expmtion NAT new effects
Good luck
If useful rates
-
Recently, I have raised a ticket with my ISP to tell don't reach is not my bamdwith contraxt. I have 120 MB of up and down. On speed tests I have abt 55 scope consistentluly to the top and 150 down. It seems that my wrt1900ac is the culprit:
-all tests must be carried out by cat6 cable
-a test when it is connected directly to the modem/vocations ISPs give you 150 upstairs and downstairs
-If I put my pc behind my linksys (which is the router behind router of the Internet service provider), I get aforentioned low download
-copy of files in my local network (nas to pc) gives 700 MB
-all switches are linksys gigabit switchesWhat's happening here? Is it normal that my traffic loses speed so just browsing through my router side wan side lan?
Enable the prioritization of media and configure it correctly:
Activate the Support WMM
The maximum value that your ISP provides you with the value Downstream\Bandwidth. # x 1024 = # value to enter the area downstream.
http://www.Linksys.com/us/support-article?articleNum=138353
http://www.Linksys.com/us/support-article?articleNum=156271 -
Hello
I'm trying to implement a subnet 2 with two routers RV042. A router will act as a bridge and the two WAN ports will be used by two different isp connection. The first router (gateway) IP LAN will be 192.168.0.1/24.
I also want to set up another router behind router modem with different subnet 192.168.1.X/24. And I would that the customers of the 192.168.1.x subnet that you want to use the internet through the gateway router and the 192.168.0.x subnet clients to access resources on the 192.168.1.x subnet. I am able to do it with two RV042?
Hello.
These products are processed by the Cisco Small Business Support Community.
* If my post answered your question, please mark it as "acceptable Solution".
Thank you!
-
Loopback Interface client endpoint VPN Site
My project consists of 871 router connected to the router soho 3845 network head on the MPLS network unencrypted for data communication. For the Client PC behind router 871 on remote site, they need activate the Cisco VPN client and connect to headend 3845 so that they can access information behind the main switch 6506.
To reduce to a minimum the installation, I would like to prepare a unique VPN profile for all remote controls. So, I plan on using lo0 int for the VPN endpoint. However, I have found that when the VPN connection is in place on the int lo0, the remote client computer can 'ping' lo0 only, but can not 'ping' all other IP addresses. However, when I set up the connection to the IP address on router 3845, the connection is ok.
I have attached my config for the VPN and the diagram. Can anyone help?
Hello
You need to change your ACL split tunnel:
FEHD_VPN extended IP access list
Note * outbound VPN client traffic *.
IP 10.0.0.0 allow 0.255.255.255 10.65.215.0 0.0.0.255
Note: Do not know what is the purpose of "allowed host ip host 0.0.0.0 0.0.0.0.
Maybe you are looking for
-
Re: Thinkpad Yoga S1 touchpad two finger Scroll switch Direction Bug
Update: I was able to recreate the running direction reversed when 'Sense switch' is deselected in the tab scrolling - mouse - ThinkPad - Advanced - Control Panel and perform then two fingers scrolling on (Internet Explorer) desktop applications from
-
How to install windows 8 in freedos?
Hey, I bought a HP 15 g009ax of flipkart with FREE DOS as the operating system, I do not know how to use freedos and install windows 8. Its just sitting there without being used. How to install windows? Please advice or help the guy?
-
Hello I have a HP620 and I need emergency assistance in the start-up of windows 7 from USB because I can't access the START menu, either the BIOS settings. What can I do, thank you.
-
It is possible to upgrade my hp xw station 8400 base unit of work 32-bit to 64-bit works sysytem?
It is possible to upgrade my hp xw station 8400 base unit of work 32-bit to 64-bit works sysytem? Also is it useful? Or should I buy a new computer, I'm currently under XP and want to up grade to Windows 7.
-
Accidentally uninstall Roxio. I don't have the media to re - install. How can I get it back?
removal of Roxio I did the right thing and thought it was one of those LabelMaker discs that come with the package of the label. Oops, my system now wants for re - install, but can't find it. What can I do? Systen recovery did not work.