OR Spy: ibwrta
Hello
With NEITHER spy, I am only interested in the lines of ibwrta. I planned to export the captured data in a text file, then write a script to extract these lines, but is there a better way? My choice of the API are NOR-488. 2 and NI-VISA. (Also, is there a depth of maximum call history?)
Thank you very much!
Hi JenT,
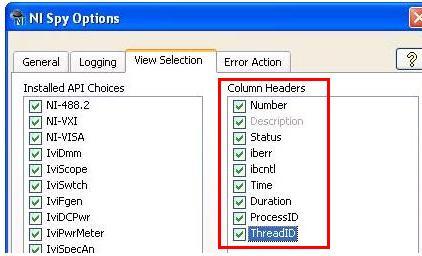
Only filtering options you have in OR-SPY can be found in the NI SPY options on the display tab. As you can see ibwrta figure does not therefore, by using a script to extract the desired code can be your best bet. Theoretically, the depth of the call history maximum is really only limited by available memory, although I would not making much larger that you need advice, advances because it will slow down your system.
Thank you
Scott M
Tags: NI Hardware
Similar Questions
-
How do I find and disable webroot spy sweeper?
I'm trying to get rid of the "inadmissible scripts" that freeze to my computer. Makes me crazy! I'm not very knowledgeable computer, so telling me to disable webroot spy sweeper does not help. I have no idea what it is, where to find it, or how to do it. Help!
Hello cypressmd, as the link in the second answer of John99 said, the problem is probably an installed extension, try Firefox Safe Mode to see if the problem goes away. Safe mode is a troubleshooting mode, which disables most of the modules.
(If you use it, switch to the default theme).
- You can open Firefox 4.0 + in Safe Mode holding the key SHIFT key when you open the desktop Firefox or shortcut in the start menu.
- Or open the Help menu and click on the restart with the disabled... modules menu item while Firefox is running.
Once you get the pop-up, simply select "" boot mode safe. "
If the issue is not present in Firefox Safe Mode, your problem is probably caused by an extension, and you need to understand that one. To do this, please follow article Troubleshooting extensions, themes and problems of hardware acceleration to resolve common Firefox problems .
To exit safe mode of Firefox, simply close Firefox and wait a few seconds before you open Firefox for normal use again.
When find you what is causing your problems, please let us know. It might help others who have the same problem.
Thank you.
-
How to remove Trojan - Spy.Win32.Banker.aiw
How to remove Trojan - Spy.Win32.Banker.aiw
It's a false alarm or a Windows malware attachment in email (a common occurrence for most users of e-mail). No one can hurt you, and you don't need to do anything. Just do not pass to someone else.
You have no need to do is get rid of the software "anti-virus" (AV). All these software are worse than useless.
Malware Windows is so widespread that you must assume that it is in each attachment until proof to the contrary. If you are just curious to know if a file is recognized as malware by the AV engines, you can download it from the "VirusTotal" site, where it will be tested against most of them. I do not recommend doing this with a file that may contain private information. A negative result is no evidence of anything either, because the AV software is not reliable.
Never leave any AV software remove or 'quarantine' send messages or attachments. This will damage the messaging database.
-
How we can know if my iphone already install spy app (like myspy, webwatcher) by someone?
Dear Hei
Please give know how to check my iphone's record or not to spy app like myspy, webwatcher
TL; DR: having backups, use TLS everywhere, choose passwords secure, use codes to six digits or (better) passwords, etc.
Well, since you are clearly concerned about the safety... First, go get yourself good and current backups and maintain and recreate with the some schedule, like a lot of people here who are concerned about safety have these backups, or not to encrypt these backups. Backups are a central part of the security, because they are the path to your data after the loss of the unit, damage or theft or such. Although iCloud backups are possible, I prefer to use iTunes for this.
Then determine if you have installed a software who ran security iOS - a process called jailbreaking - or whether you are a target of interest for an individual entity, organization or nation State with a lot of time and money and to access intentionally. Since you ask this question here, you are most likely not. Most people are simply not worth the risk of inherent exposure. If you are, then formal assistance - an iOS device is that the tip of what is involved.
If your phone was not jailbroken and if all of your passwords are well chosen through a mail server Apple ID and all services used, then the iOS platform default security will prevent all known shenanigans - outside interfaces designated, iOS security Apple seeks to block all applications to access all the other apps unrelated. It is also why you do not see the anti-virus or anti-malware packages available on iOS.
If your phone was jailbroken, then this is very probably wide open. This process intentionally disables the security of the platform. The jailbreak software that has been available is would have been extremely questionable itself, too.
Now that you can do which connects out of the appliance - connections not secure network for mail or web, websites were opened, including networks Wi - Fi and cellular towers you have been close, etc. - can be monitored, but it is no different from any other computer in the network. Make sure that you use TLS security everywhere and decent passwords. At least the people of Mspy, is a known password iCloud allowing him to listen to (some) traffic to the iOS device.
Apple Remote Desktop software - where this issue has been published, is completely different to your question, FWIW.
-
After the recent upgrade, my favorite app, the chumby spy cam has stopped working. He is always in my main channel on the web, but is no longer present on the channel on the dashboard. I tried to remove and add the dashboard as well as power cycling. I also noticed that he is more listed as an application available to add. It is still available for the chumby. What gives?
Thank you
This application has been added
-
Hi guys,.
I have develop a controller to communicate with the instrument using gpib. We can see that all called 488 functions that has been used in the controller by spy application, nor is there a way to stop the spies or listening because we do not want others know how our controller? Thank you!!!
OK, the answer is probably 'no '. The only solution I can think of is do not use NI-VISA (as is the pilot VISA itself which refers to the Trace of e/s).
However, there could be a solution that would allow you to detect if there is an e/s running tracing session:
(edit: no error should be dialogue,-303201 indicates no current session trace, ignore the other codes?)
Monitoring IO API allows you to send personalized events, but it only works if a trace session is active - it returns error-303201 if it is not a valid tracing session.
In any case-, the argument is useless, because it is so easy to see/inspect communications by other means. Protect your software by offering features and first class customer support is always up to you!
-
DAQmx 9.0, OR spy, and Measurement Studio
Hello
The NOR-Spy has with DAQmx 9.x working with applications written in c# or VB?
Curt
Hi Curt,.
Please let us know your interest about this feature.
From the next 9.1 NEITHER-DAQmx (and for all its minor and maintenance versions), NOR the Spy is not supported for the .NET API of NOR-DAQmx. We do not have a specific target version when we implement this feature. However, we are considering adding the support of the spy OR in future versions of the .NET API of NOR-DAQmx.
Anzurio Parra
National Instruments
-
My screen for NI Spy and Bird ibwrt is abbreviated. I have for example with the help of a Manager to get
ibwrt (UD1, "BINON:00000000...",44(0x2C)) printed
When I expect to
ibwrt (UD1, "BINON:00000000,00000000,00000000,000000A0;",44(0x2C))
In the options, I chose great buffer and extended details of the buffer.
How can I get the entire string printed?
I figured this out: RMC on the control and select Properties-> buffer. This allows to display the entire string. I guess it's useful to read the online help.
-
NEITHER Spy works only in the development environment?
NEITHER Spy works on LabView (executables) stand-alone applications deployed (using VISA vi), or NI Spy works only in the development environment? It might be useful for debugging of deployed applications.
If the answer is Yes (which I doubt), OR would have to create an installer for it since currently it is no longer available as an add-on.
Thank you
Ed
Edjsch,
You can install VISA as a standalone w/o LabVIEW. Spy is not a stand-alone installer because it does nothing in itself. That's why we always package it with a driver or application software.
-
Spy ++ will be able to read label VB controls
Spy ++ will be able to read label VB controls. We try to read the version number on the box about our Vb app using spy ++. But we have not managed to bring this fact.
Hello
Your question is more advanced is usually asked to Microsoft Community.
Try an appropriate MSDN forum:
http://social.msdn.Microsoft.com/forums/en-us/category/VisualStudio
Don
-
Webroot Spy Sweeper just put up-to-date. Now, my laptop says that I don't have spyware. When I open Webroot it says I'm covered! What is happening with this?
Also, I had a lot of recent Java fatal errors. Errors are listed on my desk. Something about access happens. Also noticed my system is slow to come and moving from one site to the other. Could you please provide me with the help?
I am a member of Club Pogo (pogo.com) and I wonder if it is a question, even if I got it for a few years now.
I'm really at a loss. Could you please help me with the questions listed above, or point me in the right direction to get the resolution?
Thank you!
Evie
Please specify your problem, if Webroot is said to have no spyware, you should be good.
About Java, try to reinstall it.
-
Spy never support the command line options or have an API?
The latest version of Spy, 2.7, contains a LabVIEW API, which allows to start and stop the capture. You can get it by installing VISA 4.6.
-
How can I set up Vista so that the PC does not switch to another window (for example the Spy Sweeper alerts) while I am playing a game?
Vista is not in control of this technique. Spy Sweeper needs to have an option to control that. If this isn't the case, then it is badly programmed. Flight of focus (go to another window) when it is actually needed is a big no-no for the design. I find this option, if I were you :)
-
A spam spy/hard ware removal program has inserted itself next to the msft Update button and I am unable to remove it. It appears constantly. I'm unable to identify in the Add/Remove software control panel section.
I use a sony with vista desktop computer
Hi jtbgradywhite,
Thank you for using answers Forum.
You can download the Windows Malicious Software Removal Tool here:
You can also find software third party malware removal and protection of search with your favorite search engine.
Please let us know if that helps. Chris
Microsoft Answers Support Engineer
Visit our Microsoft answers feedback Forum and let us know what you think. -
duplicate name exists on the network: can spy on me
I get this error message on an existing when duplicate name that I start.I read the patches for this, but what I'm wondering is...Assuming that the name "duplicate" is another computer, we are related in any way other thanby name and network? I want to know if Name2 (the other) is aware of name1 (me) regardinglike keystrokes, passwords, navigation, etc. ? What is the possibility exists for a name'spy' on the other? -I'm on a wireless home network.Because the error messages began, an oddity came with them... many times I have toClick a button a second time, then wait for 1-2 seconds, whereas before, a simple left clickhas brought an immediate response. Are us bogged down each other?Let us know if the issue of the double name reappears; It should not.
I suspect that your mouse is having mechanical problems. Are you using the left button of the mouse much (for example, in games)? Or there may be a foreign substance (dirt) in the switch.
If you have another mouse, you can try for a while to see if the problem persists with another mouse. You can also go in Control Panel > mouse and (temporarily) the right switch and buttons to the left of the mouse - but this is not something you want to probably keep for any significant amount of time and if the problem occurs only intermittently, you may not be able to definitively determine that it does not occur when you use the right button to the usual left button functions.
Maybe you are looking for
-
cannot import a vcard file attached to the email
When you receive an e-mail when someone transfers a .vcf contact to me I see a text file in the body of the e-mailI can open a card, but he wants to add it to windows instead of thunderbird contacts How can I fix this
-
After you have installed windows 8 may not display bookmarks
I would like to have the bookmarks displayed on a sidebar, but since installing windows 8 on my new Pc, I can't find the sidebar display bookmarks in menus on the final instillation of Firefox.
-
COMPAQ AMD 64-BIT DESPERATE...
My mother has a computer is a compaq amd 64-bit with windows media center 2005. This computer comes with an HP monitor and she had to if for bout a year. nothing else you need to know I can't tell you because I don't know much about the system. What
-
Hello! I bought a laptop Dell Inspiron 14R in October and because the premium Windows 7 OS has been pre installed I don't mind on the product key so far here. But now since I want to upgrade to windows 8 (using the offer of Rs: 699 dell) I need to gi
-
Guest user can access the system tools?
Start menu > all programs > Accessories > system tools This allows the user access to computer, control panel (and running and same command prompt), although I selected "don't display this item" through properties > Start Menu > customize. Is there s