RV120W - cannot access static IP via VPN devices
Hello
I have a RV120W used to provide VPN access to several industrial devices. Some of these devices are assigned via DHCP from the router IP address. Can not do DHCP, so there a self-determined static IP.
The VPN works well for all devices that are affected intellectual property. However, it does allow me to connect to the device that has a static IP address. I can connect to it very well when I'm on the LAN or WLAN, but it cannot ping via the VPN.
Help!
Thank you-
Bailey
Hi Bailey, it seems that the static device has no default gateway are entrusted to him.
-Tom
Please mark replied messages useful
Tags: Cisco Support
Similar Questions
-
Cannot access remote network via VPN
Hello
I'm trying to set up a router vpn access to my office network. The router is connected to the Internet through using pppoe vdsl.
There is also a public oriented Web server in the office which must be accessible.I can access the Web server from the Internet and the vpn connects successfully. I can also ping the LAN Gateway, however, I can't access all the local machines.
I'm quite puzzled as to why it does not work. Please could someone help.
The results of tests and the router configuration are listed below. Please let me know if you need additional information.
Thank you and best regards,
Simon1. routing on the router table
Router #sh ip route
Gateway of last resort is ggg.hhh.125.34 to network 0.0.0.0
xxx.yyy.zzz.0/29 is divided into subnets, subnets 1
C XXX.yyy.zzz.192 is directly connected, Vlan10
GGG.hhh.125.0/32 is divided into subnets, subnets 1
C GGG.HHH.125.34 is directly connected, Dialer0
172.16.0.0/32 is divided into subnets, subnets 1
S 172.16.100.50 [1/0] via mmm.nnn.ppp.sss
S * 0.0.0.0/0 [1/0] via ggg.hhh.125.342. ping PC remotely (172.16.100.50) local GW (172.16.100.1) successful
> ping 172.16.100.1
Ping 172.16.100.1 with 32 bytes of data:
Response to 172.16.100.1: bytes = 32 time = 24ms TTL = 255
Response to 172.16.100.1: bytes = 32 time = 10ms TTL = 255
Response to 172.16.100.1: bytes = 32 time = 10ms TTL = 255
Response to 172.16.100.1: bytes = 32 time = 11ms TTL = 2553. ping PC remotely (172.16.100.50) to the local server (172.16.100.10) failure
> ping 172.16.100.10
Ping 172.16.100.10 with 32 bytes of data:
Request timed out.
Request timed out.
Request timed out.
Request timed out.4. ping the router to the successful local server
router #ping 172.16.100.10
Type to abort escape sequence.
Send 5, echoes ICMP 100 bytes to 172.16.100.10, wait time is 2 seconds:
!!!!!
Success rate is 100 per cent (5/5), round-trip min/avg/max = 1/1/4 ms5 see the version
Cisco IOS software, software of C181X (C181X-ADVIPSERVICESK9-M), Version 12.4 (15) T1, VERSION of the SOFTWARE (fc2)
ROM: System Bootstrap, Version 12.3 YH6 (8r), RELEASE SOFTWARE (fc1)
the availability of router is 1 hour, 9 minutes
System image file is "flash: c181x-advipservicesk9 - mz.124 - 15.T1.bin".
Cisco 1812-J (MPC8500) processor (revision 0 x 300) with 118784K / 12288K bytes of memory.
10 FastEthernet interfaces
1 ISDN basic rate interface
Configuration register is 0 x 21026. router Config
AAA authentication login default local
connection of local AAA VPN authentication.
AAA authorization exec default local
local authorization AAA VPN network
!
!
AAA - the id of the joint session
!
!
!
!
crypto ISAKMP policy 1
BA 3des
preshared authentication
Group 2
!
Configuration group customer isakmp crypto ASI_Group
key mykey
DNS aaa.bbb.cccc.ddd
domain mydomain.com
pool VPN_Pool
ACL VPN_ACL
!
!
Crypto ipsec transform-set esp-3des esp-sha-hmac TS1
!
crypto dynamic-map 10 DYNMAP
game of transformation-TS1
market arriere-route
!
!
list of authentication of VPN client VPN crypto card
card crypto VPN VPN isakmp authorization list
crypto map VPN client configuration address respond
card crypto 10 VPN ipsec-isakmp dynamic DYNMAP
!
!
!
IP cef
!
!
!
Authenticated MultiLink bundle-name Panel
!
!
username admin privilege 15 password mypassword
Archives
The config log
hidekeys
!
!
!
!
!
interface FastEthernet0
WAN description
no ip address
no ip redirection
no ip unreachable
no ip proxy-arp
no ip mroute-cache
automatic duplex
automatic speed
PPPoE enable global group
PPPoE-client dial-pool-number 1
!
interface FastEthernet2
Description Public_LAN_Interface
switchport access vlan 10
full duplex
Speed 100
!
FastEthernet6 interface
Description Private_LAN_Interface
switchport access vlan 100
full duplex
Speed 100
!
interface Vlan1
no ip address
!
interface Vlan10
Public description
IP address xxx.yyy.zzz.193 255.255.255.248
no ip redirection
no ip unreachable
no ip proxy-arp
no ip mroute-cache
!
interface Vlan100
172.16.100.1 IP address 255.255.255.0
no ip redirection
no ip unreachable
no ip proxy-arp
no ip mroute-cache
!
interface Dialer0
IP unnumbered Vlan10
no ip unreachable
IP mtu 1452
IP virtual-reassembly
encapsulation ppp
no ip mroute-cache
Dialer pool 1
Dialer-Group 1
Authentication callin PPP chap Protocol
PPP chap hostname myhostname
PPP chap password mychappassword
PPP ipcp dns request accept
failure to track PPP ipcp
PPP ipcp address accept
VPN crypto card
!
IP pool local VPN_Pool 172.16.100.50 172.16.100.60
!
!
no ip address of the http server
no ip http secure server
!
VPN_ACL extended IP access list
IP 172.16.100.0 allow 0.0.0.255 any
!
Dialer-list 1 ip protocol allow
not run cdp
!
!Simon,
Basically when you connect through a VPN Client PC routing table is updated automatically as soon as the connection is established. If you do not need to manually add routes. You can check this by doing a "route print" once you are connected.
Ideally, you need to put your pool of VPN on subnet that does not exist on your physical network, the router would be to route traffic between the IP pool and internal subnet.
Now, you said that you have a web server with a public IP address that you need to access through the VPN, that host also as a private IP addresses on the 172.16.100.0? If it isn't then the ACL that I proposed should work. If she only has a public IP then your ACL VPN address must have something like
IP 172.16.100.0 allow 0.0.0.255 192.168.100.0 0.0.0.255
219.xxx.yyy.192 ip 0.0.0.7 permit 192.168.100.0 0.0.0.255
Who says the router and the client to encrypt all traffic between the subnets behind your router and your VPN pool.
I hope this helps.
Luis Raga
-
Cannot access static nat address via vpn.
I have an asa5510 where I
a static nat from one interface to the other.
I also have a VPN connection to the asa...
On the other side of the vpn connection, I can not access this static NAT.
192.168.170.x is the vpn network.
Is it not possible to access the static NAT over vpn?
the DM_INLINE_NETWORK_16 object-group network
object-network 192.168.0.0 255.255.255.0
object-network vxtron 255.255.255.0
object-network dmz_zone 255.255.255.0
object-network 192.168.170.0 255.255.255.0MPLS_nat0_outbound list extended access deny host ip 172.26.1.5 all
Access extensive list ip 172.26.0.0 MPLS_nat0_outbound allow 255.255.252.0 object-group DM_INLINE_NETWORK_16
pnat1 list extended access permit ip host 172.26.1.5 all
static (MPLS, inside) 192.168.0.199 access list pnat1
NAT (MPLS) 0-list of access MPLS_nat0_outbound
NAT (MPLS) 1 172.26.0.0 255.255.252.0
static (MPLS, inside) 172.26.1.5 MPLS_nat_static access listRené, happy you including yourself this one! If you could, please mark the post as solved so that we know that it is not need more attention
-
Cannot access the videos via USB more
Nice day
I have a HDR-SR10. I can't access the videos via USB more. drive appears blank in windows 8. Videos can be played through the screen of the device. Help, please
Yes. Tried 2 usb ports with no luck.
In fact. I downloaded the latest version of PMB and was able to import videos from cam. Once imported, I formatted the drive, then it pops up on the desktop as usual.
For me, it wa weird experience and have no logical explanation. -
Windows 2003 cannot access remote network via Cisco VPN
I have two computers at home, an XP Pro SP2 and another is Windows 2003 server SP1. If I set Cisco VPN XP (version 4.6) the Office (ASA 5510), I can access the office network resources. However, if I set the Cisco VPN on 2003, can I? t do the same thing. After studying the two routing tables, I think XP has this road: 192.168.0.0 255.255.0.0 192.168.101.5 192.168.101.5 1, but the 2003 doesn't? t. If I add this route manually (rou? add 192.168.0.0 mask 255.255.255.0 192.168.101.3) 2003, then I can access resources. Why?
tale of 2003 routing.
Active routes:
Network Destination gateway metric Interface subnet mask
0.0.0.0 0.0.0.0 192.168.10.1 192.168.10.3 40
x.x.x.37 255.255.255.255 192.168.10.1 192.168.10.3 1
127.0.0.0 255.0.0.0 127.0.0.1 127.0.0.1 1
192.168.10.0 255.255.255.0 192.168.10.3 192.168.10.3 40
192.168.10.3 255.255.255.255 127.0.0.1 127.0.0.1 40
192.168.10.255 255.255.255.255 192.168.10.3 192.168.10.3 40
192.168.101.0 255.255.255.0 192.168.101.3 192.168.101.3 10
192.168.101.3 255.255.255.255 127.0.0.1 127.0.0.1 10
192.168.101.255 255.255.255.255 192.168.101.3 192.168.101.3 10
224.0.0.0 240.0.0.0 192.168.10.3 192.168.10.3 40
224.0.0.0 240.0.0.0 192.168.101.3 192.168.101.3 10
255.255.255.255 255.255.255.255 192.168.10.3 192.168.10.3 1
255.255.255.255 255.255.255.255 192.168.101.3 192.168.101.3 1
Default gateway: 192.168.10.1
===========================================================================
Persistent routes:
None
VPN client has not been tested on Win2003. Customer requirements are described here:
http://www.Cisco.com/univercd/CC/TD/doc/product/VPN/client/4_6/relnt/4604cln.htm#wp1024664
and the show to competition of WinXP is supported.
-
I have a question to give a static IP address to the VPN clients. I have a Cisco ASA 5510 11 laptops that will be connected via a VPN (Cisco or Microsoft PPTP). For business reasons, I need each laptop to be assigned the same IP every time that it connects. What would be the best way to accomplish this task?
It is certainly possible, but it does not require that you add an IP address to each user name in the configuration. ASA leans on the username entered by the remote user and checks if it has an IP address that is configured with his user name.
You can find the configuration option in the ASDM here: Configuration-> VPN-> General-> users. Editing a user and click the VPN Policy tab, you will find the 'IP address' option at the bottom of the page.
If you want to configure this via the console/telnet/ssh: access the configuration mode and type the following:
name of user attributes
VPN-framed-ip-address
Make sure that the subnet matches the subnet of your already configured ip pool! If you use 192.168.10.0/24 as ip pool, your configuration should look like this:
user testuser name attributes
VPN-framed-ip-address 192.168.10.1 255.255.255.0
The address 192.168.10.1 should now always be attributed to the user "testuser".
I hope that this post helps, please rate if she does!
Kind regards
Michael
-
Cannot ping inner network via VPN site-2-site
I have the following Setup of the site 2 site VPN.

The pain I feel is host 172.168.88.3 in site A is not able to ping 172.168.200.3 in site B and vice versa. Think I've added static routes and lists ACLs correctly on 3560 switches (acting as an access point) and the two PIX to access internal networks. 172.168.9.3 host can ping 172.168.200.3 very well. All advice is appreciated.
Thank you very much.
My configs are as follows:
PIX HAS
8.0 (3) version PIX
!
PIX - A host name
activate u18hqwudty78klk9s encrypted password
names of
!
interface Ethernet0
Speed 100
full duplex
nameif outside
security-level 0
IP address x.x.x.250 255.255.255.240
!
interface Ethernet1
nameif inside
security-level 100
IP 172.168.9.1 255.255.255.0
!
uh78mklh78yMs encrypted passwd
connection of the banner it is a private network. Unauthorized access is prohibited!
Banner motd this is a private network. Unauthorized access is prohibited!
passive FTP mode
clock timezone GMT/UTC 0
summer time clock GMT/BST recurring 1 Sun Mar 01:00 last Sun Oct 02:00
DNS domain-lookup outside
DNS server-group Ext_DNS
Server name 82.72.6.57
Server name 63.73.82.242
the LOCAL_LAN object-group network
object-network 172.168.9.0 255.255.255.0
object-network 172.168.88.0 255.255.255.0
Internet_Services tcp service object-group
port-object eq www
area of port-object eq
EQ object of the https port
port-object eq ftp
EQ object of port 8080
EQ port ssh object
port-object eq telnet
the WAN_Network object-group network
object-network 172.168.200.0 255.255.255.0
ACLOUT list extended access allowed object-group LOCAL_LAN udp any eq log field
ACLOUT list extended access allow icmp object-group LOCAL_LAN no matter what paper
ACLOUT list extended access permitted tcp object-group LOCAL_LAN connect to any object-group Internet_Services
Access extensive list ip 172.168.88.0 ACLOUT allow 255.255.255.0 172.168.200.0 255.255.255.0 connect
access-list extended ACLIN all permit icmp any what newspaper echo-reply
access-list extended ACLIN all permit icmp any how inaccessible journal
access-list extended ACLIN allowed icmp no matter what newspaper has exceeded the time
IP 172.168.200.0 allow Access - list extended ACLIN 255.255.255.0 172.168.9.0 255.255.255.0 connect
standard access list split_tunnel_list allow 172.168.9.0 255.255.255.0
Access log list split_tunnel_list note LOCAL_LAN
access-list extended SHEEP allowed ip object-group LOCAL_LAN 172.168.100.0 255.255.255.0 connect
access extensive list ip 172.168.9.0 inside_nat0_outbound allow 255.255.255.0 172.168.200.0 255.255.255.0 connect
access extensive list ip 172.168.9.0 outside_cryptomap_20 allow 255.255.255.0 172.168.200.0 255.255.255.0 connect
pager lines 24
Enable logging
logging buffered information
logging trap information
host of logging inside the 172.168.88.3
Outside 1500 MTU
Within 1500 MTU
IP local pool testvpn 172.168.100.1 - 192.168.100.99
no failover
ICMP unreachable rate-limit 1 burst-size 1
ASDM image Flash: / pdm
don't allow no asdm history
ARP timeout 14400
Global 1 interface (outside)
NAT (inside) 0-list of access inside_nat0_outbound
NAT (inside) 1 0.0.0.0 0.0.0.0
Access-group ACLIN in interface outside
ACLOUT access to the interface inside group
Route outside 0.0.0.0 0.0.0.0 x.x.x.45 1
Route inside 172.168.88.0 255.255.255.0 172.168.88.254 1
Route inside 172.168.199.0 255.255.255.0 172.168.199.254 1
Route outside 172.168.200.0 255.255.255.0 172.168.9.1 1
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout, uauth 0:05:00 absolute
dynamic-access-policy-registration DfltAccessPolicy
Enable http server
http 172.168.9.1 255.255.255.255 inside
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Crypto ipsec transform-set esp-3des esp-md5-hmac Set_1
Crypto ipsec transform-set ESP-AES-256-SHA 256 - aes - esp esp-sha-hmac
Crypto dynamic-map outside_dyn_map 1 set of transformation-Set_1
Crypto dynamic-map outside_dyn_map 1 the value reverse-road
outside_map 1 card crypto ipsec-isakmp dynamic outside_dyn_map
card crypto outside_map 20 match address outside_cryptomap_20
card crypto outside_map 20 peers set x.x.x.253
outside_map crypto 20 card value transform-set ESP-AES-256-SHA
outside_map interface card crypto outside
crypto ISAKMP allow outside
crypto ISAKMP policy 1
preshared authentication
3des encryption
md5 hash
Group 2
life 86400
crypto ISAKMP policy 10
preshared authentication
aes-256 encryption
sha hash
Group 5
life 86400
No encryption isakmp nat-traversal
Telnet 0.0.0.0 0.0.0.0 inside
Telnet timeout 5
SSH timeout 5
Console timeout 0
a basic threat threat detection
Statistics-list of access threat detection
NTP server 130.88.203.12 prefer external source
internal testvpn group policy
attributes of the strategy of group testvpn
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list split_tunnel_list
Viv ZdlkjGlOTGf7dqdb encrypted user name password
type tunnel-group testvpn remote access
tunnel-group testvpn General-attributes
address testvpn pool
Group Policy - by default-testvpn
testvpn group of tunnel ipsec-attributes
pre-shared-key *.
tunnel-group x.x.x.253 type ipsec-l2l
x.x.x.253 group of tunnel ipsec-attributes
pre-shared-key *.
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the rsh
inspect the rtsp
inspect esmtp
inspect sqlnet
inspect the skinny
inspect sunrpc
inspect xdmcp
inspect the sip
inspect the netbios
inspect the tftp
inspect the icmp
!
global service-policy global_policy
context of prompt hostname
Cryptochecksum:bb6ead3350227b3745c14b9ba340b84a
: end
B PIX
8.0 (3) version PIX
!
hostname PIX - B
enable password ul; encrypted jk89A89hNC0Ms
names of
!
interface Ethernet0
Speed 100
full duplex
nameif outside
security-level 0
IP address x.x.x.253 255.255.255.240
!
interface Ethernet1
nameif inside
security-level 100
IP 172.168.200.1 255.255.255.0
!
interface Ethernet2
Shutdown
No nameif
no level of security
no ip address
!
2ljio897hFB.88fU encrypted passwd
Banner motd this is a private network. Unauthorized access is prohibited!
passive FTP mode
DNS domain-lookup outside
DNS server-group Ext_DNS
Server name x.x.x.57
Server name x.x.x.242
the LOCAL_LAN object-group network
object-network 172.168.200.0 255.255.255.0
Internet_Services tcp service object-group
port-object eq www
area of port-object eq
EQ object of the https port
port-object eq ftp
EQ object of port 8080
the WAN_Network object-group network
networks WAN Description
object-network 172.168.88.0 255.255.255.0
ACLOUT list extended access allowed object-group LOCAL_LAN udp any eq field
ACLOUT list extended access allow icmp object-group LOCAL_LAN all
ACLOUT list extended access permitted tcp object-group LOCAL_LAN any Internet_Services object-group
access-list extended ACLIN allow all unreachable icmp
access-list extended ACLIN permit icmp any one time exceed
access-list extended ACLIN permit icmp any any echo response
IP 172.168.88.0 allow Access - list extended ACLIN 255.255.255.0 172.168.200.0 255.255.255.0
IP 172.168.9.0 allow Access - list extended ACLIN 255.255.255.0 172.168.200.0 255.255.255.0
IP 172.168.199.0 allow Access - list extended ACLIN 255.255.255.0 172.168.200.0 255.255.255.0
access extensive list ip 172.168.200.0 inside_nat0_outbound allow 255.255.255.0 172.168.9.0 255.255.255.0
access extensive list ip 172.168.200.0 outside_cryptomap_20 allow 255.255.255.0 172.168.9.0 255.255.255.0
pager lines 24
Enable logging
monitor debug logging
debug logging in buffered memory
logging trap information
Outside 1500 MTU
Within 1500 MTU
no failover
ICMP unreachable rate-limit 1 burst-size 1
don't allow no asdm history
ARP timeout 14400
Global 1 interface (outside)
NAT (inside) 0-list of access inside_nat0_outbound
NAT (inside) 1 0.0.0.0 0.0.0.0
Access-group ACLIN in interface outside
ACLOUT access to the interface inside group
Route outside 0.0.0.0 0.0.0.0 x.x.x.253 1
Route outside 172.168.88.0 255.255.255.0 172.168.200.1 1
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout, uauth 0:05:00 absolute
dynamic-access-policy-registration DfltAccessPolicy
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Crypto ipsec transform-set ESP-AES-256-SHA 256 - aes - esp esp-sha-hmac
card crypto outside_map 20 match address outside_cryptomap_20
card crypto outside_map 20 peers set x.x.x.250
outside_map crypto 20 card value transform-set ESP-AES-256-SHA
outside_map interface card crypto outside
crypto ISAKMP allow outside
crypto ISAKMP policy 10
preshared authentication
aes-256 encryption
sha hash
Group 5
life 86400
No encryption isakmp nat-traversal
Telnet timeout 5
SSH timeout 5
Console timeout 0
management-access inside
a basic threat threat detection
Statistics-list of access threat detection
tunnel-group x.x.x.250 type ipsec-l2l
x.x.x.250 Group of tunnel ipsec-attributes
pre-shared-key *.
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the rsh
inspect the rtsp
inspect esmtp
inspect sqlnet
inspect the skinny
inspect sunrpc
inspect xdmcp
inspect the sip
inspect the netbios
inspect the tftp
inspect the icmp
!
global service-policy global_policy
context of prompt hostname
Cryptochecksum:ccb8392ce529a21c071b85d9afcfdb30
: end
3560 G/W
version 12.2
no service button
horodateurs service debug uptime
Log service timestamps uptime
no password encryption service
!
hostname 3560_GW
!
enable secret 5 $1$ cOB4$ Uklj8978/jgWv? TSSP
!
No aaa new-model
mtu 1500 routing system
IP subnet zero
IP routing
!
!
!
!
No file verify auto
pvst spanning-tree mode
spanning tree extend id-system
!
internal allocation policy of VLAN ascendant
!
interface GigabitEthernet0/1
!
interface GigabitEthernet0/2
uplink Description to Cisco_ASA
switchport access vlan 9
!
interface GigabitEthernet0/3
!
interface GigabitEthernet0/4
!
interface GigabitEthernet0/5
!
interface GigabitEthernet0/6
!
interface GigabitEthernet0/7
!
interface GigabitEthernet0/8
!
interface GigabitEthernet0/9
!
interface GigabitEthernet0/10
!
interface GigabitEthernet0/11
!
interface GigabitEthernet0/12
!
interface GigabitEthernet0/13
!
interface GigabitEthernet0/14
!
interface GigabitEthernet0/15
!
interface GigabitEthernet0/6
!
interface GigabitEthernet0/7
!
interface GigabitEthernet0/8
!
interface GigabitEthernet0/9
!
interface GigabitEthernet0/10
!
interface GigabitEthernet0/11
!
interface GigabitEthernet0/12
!
interface GigabitEthernet0/13
!
interface GigabitEthernet0/14
!
interface GigabitEthernet0/15
!
interface GigabitEthernet0/16
!
interface GigabitEthernet0/17
!
interface GigabitEthernet0/18
!
interface GigabitEthernet0/19
!
interface GigabitEthernet0/20
!
interface GigabitEthernet0/21
!
interface GigabitEthernet0/22
!
interface GigabitEthernet0/23
switchport access vlan 88
switchport mode access
spanning tree portfast
!
interface GigabitEthernet0/24
switchport access vlan 9
switchport mode access
spanning tree portfast
!
interface GigabitEthernet0/25
trunk of the description and the port of A_2950_88 1
switchport trunk encapsulation dot1q
!
interface GigabitEthernet0/26
!
interface GigabitEthernet0/27
trunk of the description and the port of A_2950_112 1
switchport trunk encapsulation dot1q
Shutdown
!
interface GigabitEthernet0/28
!
interface Vlan1
no ip address
Shutdown
!
interface Vlan9
IP 172.168.9.2 255.255.255.0
!
interface Vlan88
IP 172.168.88.254 255.255.255.0
!
interface Vlan199
IP 172.168.199.254 255.255.255.0
!
IP classless
IP route 0.0.0.0 0.0.0.0 172.168.9.1
IP route 172.168.88.0 255.255.255.0 172.168.9.1
IP route 172.168.100.0 255.255.255.0 172.168.9.1
IP route 172.168.200.0 255.255.255.0 172.168.9.1
IP http server
!
!
control plan
!
Banner motd ^ C is a private network. ^ C
!
Line con 0
line vty 0 4
opening of session
line vty 5 15
opening of session
!
end
Hi Robert,.
I went through the configuration on both the PIX firewall and see that trafficking is not defined for 172.168.88.0/24-->172.168.200.0/24.
If you check the card crypto a PIX configuration, it says:
address for correspondence outside_map 20 card crypto outside_cryptomap_20<--This acl="" defines="" interesting="">
and the outside_cryptomap_20 of the acl says:
access extensive list ip 172.168.9.0 outside_cryptomap_20 allow 255.255.255.0 172.168.200.0 255.255.255.0 connect
Is the same on the PIX B:
address for correspondence outside_map 20 card crypto outside_cryptomap_20
access extensive list ip 172.168.200.0 outside_cryptomap_20 allow 255.255.255.0 172.168.9.0 255.255.255.0
To allow users to talk to each other, apply to these commands:
On the PIX:
access extensive list ip 172.168.88.0 outside_cryptomap_20 allow 255.255.255.0 172.168.200.0 255.255.255.0
access extensive list ip 172.168.88.0 inside_nat0_outbound allow 255.255.255.0 172.168.200.0 255.255.255.0
and PIX B:
IP 172.168.200.0 allow access-list extended outside_cryptomap_20 255.255.255.0 172.168.88.0 255.255.255.0
access extensive list ip 172.168.200.0 inside_nat0_outbound allow 255.255.255.0 172.168.88.0 255.255.255.0
Let me know if it helps.
Thank you
Vishnu Sharma
-
Cannot access remote network by VPN Site to Site ASA
Hello everyone
First of all I must say that I have configured the VPN site-to site a million times before. Stuck with it. First of all I can't ping outside the interface of my ASA remote. Secondly, VPN is in place, but no connectivity between local networks
ASA local:
hostname gyd - asa
domain bct.az
activate the encrypted password of XeY1QWHKPK75Y48j
XeY1QWHKPK75Y48j encrypted passwd
names of
DNS-guard
!
interface GigabitEthernet0/0
Shutdown
nameif vpnswc
security-level 0
IP 10.254.17.41 255.255.255.248
!
interface GigabitEthernet0/1
Vpn-turan-Baku description
nameif outside Baku
security-level 0
IP 10.254.17.9 255.255.255.248
!
interface GigabitEthernet0/2
Vpn-ganja description
nameif outside-Ganja
security-level 0
IP 10.254.17.17 255.255.255.248
!
interface GigabitEthernet0/2.30
Description remote access
VLAN 30
nameif remote access
security-level 0
IP 85.*. *. * 255.255.255.0
!
interface GigabitEthernet0/3
Description BCT_Inside
nameif inside-Bct
security-level 100
IP 10.40.50.65 255.255.255.252
!
interface Management0/0
nameif management
security-level 100
IP 192.168.251.1 255.255.255.0
management only
!
boot system Disk0: / asa823 - k8.bin
passive FTP mode
DNS server-group DefaultDNS
name-server 192.168.1.3
domain bct.az
permit same-security-traffic intra-interface
object-group network obj - 192.168.121.0
object-group network obj - 10.40.60.0
object-group network obj - 10.40.50.0
object-group network obj - 192.168.0.0
object-group network obj - 172.26.0.0
object-group network obj - 10.254.17.0
object-group network obj - 192.168.122.0
object-group service obj-tcp-eq-22
object-group network obj - 10.254.17.18
object-group network obj - 10.254.17.10
object-group network obj - 10.254.17.26
access-list 110 scope ip allow a whole
NAT list extended access permit tcp any host 10.254.17.10 eq ssh
NAT list extended access permit tcp any host 10.254.17.26 eq ssh
access-list extended ip allowed any one sheep
icmp_inside list extended access permit icmp any one
icmp_inside of access allowed any ip an extended list
access list nat-ganja extended permit tcp any host 10.254.17.18 eq ssh
RDP list extended access permit tcp any host 192.168.45.3 eq 3389
rdp extended permitted any one ip access list
sheep-vpn access-list extended permits all ip 192.168.121.0 255.255.255.0
NAT-vpn-internet access-list extended ip 192.168.121.0 allow 255.255.255.0 any
NAT-vpn-internet access-list extended ip 172.26.0.0 allow 255.255.255.0 any
NAT-vpn-internet access-list extended ip 192.168.122.0 allow 255.255.255.0 any
access-list sheep-vpn-city scope ip 192.168.121.0 allow 255.255.255.0 10.40.60.0 255.255.255.0
access-list sheep-vpn-city scope ip 192.168.121.0 allow 255.255.255.0 10.40.50.0 255.255.255.0
access-list sheep-vpn-city scope ip 192.168.121.0 allow 255.255.255.0 192.168.0.0 255.255.0.0
access-list sheep-vpn-city scope ip 192.168.121.0 allow 255.255.255.0 172.26.0.0 255.255.255.0
access-list sheep-vpn-city scope ip 192.168.121.0 allow 255.255.255.0 10.254.17.0 255.255.255.0
GHC-ganja-internet access-list extended ip 192.168.45.0 allow 255.255.255.0 any
Standard access list Split_Tunnel_List allow 192.168.16.0 255.255.255.0
azans 192.168.69.0 ip extended access-list allow 255.255.255.0 any
permit inside_nat0_outbound to access extended list ip 192.168.0.0 255.255.0.0 192.168.121.0 255.255.255.0
permit inside_nat0_outbound to access extended list ip 192.168.0.0 255.255.0.0 192.168.80.0 255.255.255.0
pager lines 24
Enable logging
emblem of logging
recording of debug console
recording of debug trap
asdm of logging of information
Interior-Bct 192.168.1.27 host connection
flow-export destination inside-Bct 192.168.1.27 9996
vpnswc MTU 1500
outside Baku MTU 1500
outside-Ganja MTU 1500
MTU 1500 remote access
Interior-Bct MTU 1500
management of MTU 1500
IP local pool raccess 192.168.121.60 - 192.168.121.120 mask 255.255.255.0
IP local pool ssl 192.168.121.130 - 192.168.121.200 mask 255.255.255.0
no failover
ICMP unreachable rate-limit 1 burst-size 1
ICMP allow any outside Baku
ICMP allow access remotely
ICMP allow any interior-Bct
ASDM image disk0: / asdm - 621.bin
don't allow no asdm history
ARP timeout 14400
global (outside-Baku) 1 interface
global (outside-Ganja) interface 2
3 overall (RAS) interface
azans access-list NAT 3 (outside-Ganja)
NAT (remote access) 0 access-list sheep-vpn-city
NAT 3 list nat-vpn-internet access (remote access)
NAT (inside-Bct) 0-list of access inside_nat0_outbound
NAT (inside-Bct) 2-nat-ganja access list
NAT (inside-Bct) 1 access list nat
Access-group rdp on interface outside-Ganja
!
Router eigrp 2008
No Auto-resume
neighbor 10.254.17.10 interface outside Baku
neighbor 10.40.50.66 Interior-Bct interface
Network 10.40.50.64 255.255.255.252
Network 10.250.25.0 255.255.255.0
Network 10.254.17.8 255.255.255.248
Network 10.254.17.16 255.255.255.248
redistribute static
!
Access remote 0.0.0.0 0.0.0.0 85.*. *. * 1
Outside-Baku route 10.0.11.0 255.255.255.0 10.254.17.10 1
Outside-Baku route 10.0.33.0 255.255.255.0 10.254.17.10 1
Outside-Baku route 10.0.150.0 255.255.255.0 10.254.17.10 1
Outside-Baku route 10.0.170.0 255.255.255.0 10.254.17.10 1
Route outside Baku 10.254.17.24 255.255.255.248 10.254.17.10 1
Route outside Baku 10.254.17.32 255.255.255.248 10.254.17.10 1
Route outside Baku 192.1.1.0 255.255.255.0 10.254.17.10 1
Outside-Baku route 192.168.27.0 255.255.255.0 10.254.17.10 1
Outside-Baku route 192.168.39.0 255.255.255.0 10.254.17.10 1
Route outside-Ganja 192.168.45.0 255.255.255.0 10.254.17.18 1
Route outside-Ganja 192.168.66.0 255.255.255.0 10.254.17.18 1
Route outside-Ganja 192.168.69.0 255.255.255.0 10.254.17.18 1
Outside-Baku route 192.168.80.0 255.255.255.0 10.254.17.11 1
Access remote 192.168.121.0 255.255.255.0 85.132.43.1 1
Route outside-Ganja 192.168.184.0 255.255.255.0 10.254.17.18 1
Route outside Baku 192.168.208.16 255.255.255.240 10.254.17.10 1
Route outside-Ganja 192.168.208.112 255.255.255.240 10.254.17.18 1
Route inside-Bct 192.168.254.0 255.255.255.0 10.40.50.66 1
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-registration DfltAccessPolicy
AAA-server protocol Ganymede GANYMEDE +.
AAA-server GANYMEDE (Interior-Bct) 192.168.1.8
key *.
AAA-server GANYMEDE (Interior-Bct) 192.168.22.46
key *.
RADIUS protocol AAA-server TACACS1
AAA-server TACACS1 (Interior-Bct) host 192.168.1.8
key *.
AAA-server TACACS1 (Interior-Bct) host 192.168.22.46
key *.
authentication AAA ssh console LOCAL GANYMEDE
Console to enable AAA authentication RADIUS LOCAL
Console Telnet AAA authentication RADIUS LOCAL
AAA accounting ssh console GANYMEDE
Console Telnet accounting AAA GANYMEDE
Enable http server
http 192.168.1.0 255.255.255.0 management
http 192.168.1.0 255.255.255.0 Interior-Bct
http 192.168.139.0 255.255.255.0 Interior-Bct
http 192.168.0.0 255.255.255.0 Interior-Bct
Survey community SNMP-server host inside-Bct 192.168.1.27
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Crypto ipsec transform-set esp-3des esp-md5-hmac RIGHT
Crypto ipsec transform-set newset aes - esp esp-md5-hmac
Crypto ipsec transform-set esp-3des esp-sha-hmac myset2
Crypto ipsec transform-set esp-3des esp-md5-hmac raccess
Crypto ipsec transform-set esp-3des esp-sha-hmac vpnclienttrans
Crypto ipsec transform-set vpnclienttrans transport mode
life crypto ipsec security association seconds 2147483646
Crypto ipsec kilobytes of life security-association 2147483646
raccess 1 set transform-set vpnclienttrans crypto dyn1 dynamic-map
correspondence address card crypto mymap 10 110
card crypto mymap 10 peers set 10.254.17.10
card crypto mymap 10 transform-set RIGHT
correspondence address card crypto mymap 20 110
card crypto mymap 20 peers set 10.254.17.11
mymap 20 transform-set myset2 crypto card
card crypto mymap interface outside Baku
correspondence address card crypto ganja 10 110
10 ganja crypto map peer set 10.254.17.18
card crypto ganja 10 transform-set RIGHT
card crypto interface outside-Ganja ganja
correspondence address card crypto vpntest 20 110
peer set card crypto vpntest 20 10.250.25.1
newset vpntest 20 transform-set card crypto
card crypto vpntest interface vpnswc
vpnclientmap 30 card crypto ipsec-isakmp dynamic dyn1
card crypto interface for remote access vpnclientmap
Crypto ca trustpoint ASDM_TrustPoint0
registration auto
name of the object CN = gyd - asa .az .bct
sslvpnkeypair key pair
Configure CRL
map of crypto DefaultCertificateMap 10 ca certificatecrypto isakmp identity address
ISAKMP crypto enable vpnswc
ISAKMP crypto enable outside-Baku
ISAKMP crypto enable outside-Ganja
crypto ISAKMP enable remote access
ISAKMP crypto enable Interior-Bct
crypto ISAKMP policy 10
preshared authentication
3des encryption
md5 hash
Group 2
life 86400
crypto ISAKMP policy 20
preshared authentication
aes encryption
md5 hash
Group 2
life 86400
crypto ISAKMP policy 30
preshared authentication
3des encryption
sha hash
Group 2
life 86400
crypto ISAKMP policy 40
preshared authentication
aes encryption
sha hash
Group 2
life 86400
Crypto isakmp nat-traversal 30
No vpn-addr-assign aaa
Telnet timeout 5
SSH 192.168.0.0 255.255.255.0 Interior-Bct
SSH timeout 35
Console timeout 0
priority queue outside Baku
queue-limit 2046
TX-ring-limit 254
a basic threat threat detection
Statistics-list of access threat detection
no statistical threat detection tcp-interception
Server NTP 192.168.1.3
SSL encryption, 3des-sha1 rc4 - md5 aes128-sha1 sha1-aes256
SSL-trust point ASDM_TrustPoint0 to vpnlb-ip remote access
SSL-trust ASDM_TrustPoint0 remote access point
WebVPN
turn on remote access
SVC disk0:/anyconnect-win-2.4.1012-k9.pkg 1 image
enable SVC
tunnel-group-list activate
attributes of Group Policy DfltGrpPolicy
Protocol-tunnel-VPN IPSec l2tp ipsec svc webvpn
internal group ssl policy
attributes of group ssl policy
banner welcome to SW value
value of DNS-server 192.168.1.3
Protocol-tunnel-VPN IPSec l2tp ipsec svc webvpn
group-lock value SSL
WebVPN
value of the SPS URL-list
internal vpn group policy
attributes of vpn group policy
value of DNS-server 192.168.1.3
Protocol-tunnel-VPN IPSec l2tp ipsec
disable the PFS
BCT.AZ value by default-field
ssl VPN-group-strategy
WebVPN
value of the SPS URL-list
IPSec-attributes tunnel-group DefaultL2LGroup
ISAKMP retry threshold 20 keepalive 5
attributes global-tunnel-group DefaultRAGroup
raccess address pool
Group-RADIUS authentication server
Group Policy - by default-vpn
IPSec-attributes tunnel-group DefaultRAGroup
pre-shared key *.
ISAKMP retry threshold 20 keepalive 5
IPSec-attributes tunnel-group DefaultWEBVPNGroup
ISAKMP retry threshold 20 keepalive 5
tunnel-group 10.254.17.10 type ipsec-l2l
IPSec-attributes tunnel-group 10.254.17.10
pre-shared key *.
ISAKMP retry threshold 20 keepalive 5
type SSL tunnel-group remote access
attributes global-group-tunnel SSL
ssl address pool
Authentication (remote access) LOCAL servers group
Group Policy - by default-ssl
certificate-use-set-name username
Group-tunnel SSL webvpn-attributes
enable SSL group-alias
Group-url https://85. *. *. * / activate
tunnel-group 10.254.17.18 type ipsec-l2l
IPSec-attributes tunnel-group 10.254.17.18
pre-shared key *.
ISAKMP retry threshold 20 keepalive 5
tunnel-group 10.254.17.11 type ipsec-l2l
IPSec-attributes tunnel-group 10.254.17.11
pre-shared key *.
ISAKMP retry threshold 20 keepalive 5
type tunnel-group DefaultSWITGroup remote access
attributes global-tunnel-group DefaultSWITGroup
raccess address pool
Group-RADIUS authentication server
Group Policy - by default-vpn
IPSec-attributes tunnel-group DefaultSWITGroup
pre-shared key *.
!
type of policy-card inspect dns migrated_dns_map_1
parameters
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the migrated_dns_map_1 dns
inspect the rsh
inspect the rtsp
inspect sqlnet
inspect sunrpc
inspect xdmcp
inspect the netbios
Review the ip options
class flow_export_cl
flow-export-type of event all the destination 192.168.1.27
class class by default
flow-export-type of event all the destination 192.168.1.27
Policy-map Voicepolicy
class voice
priority
The class data
police release 80000000
!
global service-policy global_policy
service-policy interface outside Baku Voicepolicy
context of prompt hostnameCryptochecksum:4f35f975ba7a0c11f7f46dfd541d266f
: end
GYD - asa #.ASA remote:
ASA Version 8.2 (3)
!
ciscoasa hostname
activate the encrypted password of XeY1QWHKPK75Y48j
2KFQnbNIdI.2KYOU encrypted passwd
names of
DNS-guard
!
interface Ethernet0/0
nameif inside
security-level 100
IP 192.168.80.14 255.255.255.0
!
interface Ethernet0/1
nameif outside
security-level 0
IP 10.254.17.11 255.255.255.248
!
interface Ethernet0/2
Shutdown
No nameif
no level of security
no ip address
!
interface Ethernet0/3
Shutdown
No nameif
no level of security
no ip address
!
interface Management0/0
Shutdown
nameif management
security-level 100
no ip address
management only
!
boot system Disk0: / asa823 - k8.bin
passive FTP mode
access-list 110 scope ip allow a whole
192.168.80.0 IP Access-list extended sheep 255.255.255.0 allow 192.168.0.0 255.255.0.0
pager lines 24
Enable logging
asdm of logging of information
Outside 1500 MTU
management of MTU 1500
Within 1500 MTU
no failover
ICMP unreachable rate-limit 1 burst-size 1
ICMP allow all outside
ICMP allow any inside
ASDM image disk0: / asdm - 621.bin
don't allow no asdm history
ARP timeout 14400
NAT (inside) 0 access-list sheep
Route outside 0.0.0.0 0.0.0.0 10.254.17.9 1
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-registration DfltAccessPolicy
Enable http server
http 192.168.1.0 255.255.255.0 management
http 192.168.80.0 255.255.255.0 inside
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Crypto ipsec transform-set esp-3des esp-md5-hmac RIGHT
Crypto ipsec transform-set newset aes - esp esp-md5-hmac
Crypto ipsec transform-set esp-3des esp-sha-hmac myset2
life crypto ipsec security association seconds 2147483646
Crypto ipsec kilobytes of life security-association 2147483646
correspondence address card crypto mymap 10 110
card crypto mymap 10 peers set 10.254.17.9
mymap 10 transform-set myset2 crypto card
mymap outside crypto map interface
crypto ISAKMP allow outside
crypto ISAKMP policy 10
preshared authentication
3des encryption
md5 hash
Group 2
life 86400
crypto ISAKMP policy 20
preshared authentication
aes encryption
md5 hash
Group 2
life 86400
crypto ISAKMP policy 30
preshared authentication
3des encryption
sha hash
Group 2
life 86400
crypto ISAKMP policy 40
preshared authentication
aes encryption
sha hash
Group 2
life 86400
Telnet timeout 5
SSH timeout 5
Console timeout 0
a basic threat threat detection
Statistics-list of access threat detection
no statistical threat detection tcp-interception
WebVPNtunnel-group 10.254.17.9 type ipsec-l2l
IPSec-attributes tunnel-group 10.254.17.9
pre-shared key *.
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns migrated_dns_map_1
parameters
maximum message length automatic of customer
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the migrated_dns_map_1 dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the rsh
inspect the rtsp
inspect esmtp
inspect sqlnet
inspect the skinny
inspect sunrpc
inspect xdmcp
inspect the sip
inspect the netbios
inspect the tftp
Review the ip options
!
global service-policy global_policy
context of prompt hostnameCryptochecksum:1c1ac60e2fb84f65269d15d53f27c21b
: end
ciscoasa # $Still, I can't ping ASA remote outside from outside of the Local interface. And there is no connectivity between the 192.168.80.0 distance and local don't say 192.168.1.0. I have run out of ideas
Would appreciate any help. Thank you in advance...
If the tunnel is up (phase 1), but no traffic passing the best test is the following:
Add order management-access to the Interior , and then try to PING the intellectual property inside ASA counterpart.
inside x.x.x.x ping --> x.x.x.x is the IP of the ASA peer inside
The test above shows if the traffic passes through the tunnel (check encrypted/decrypted packets of sh cry ips its).
Test on both directions.
Please post the results.
Federico.
-
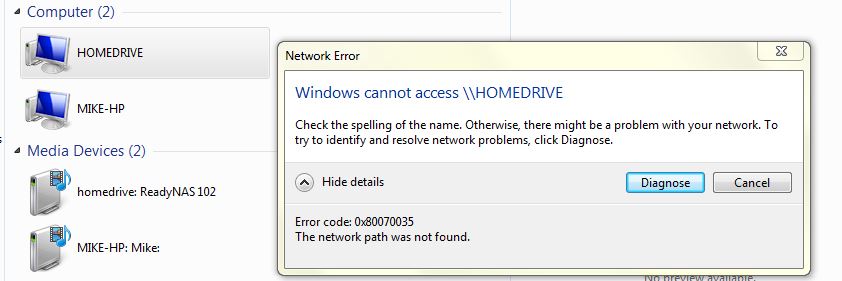
Cannot access the readynas via the network of windows 7 since the 65.5 update
I have a readynas 102 fixed by a switch to a windows 7 computer pro.
Before the update, to 65.5 I could still access the files on my readynas 102 (name: homedrive) by selecting it under Network > homedrive
Since the update, it still appears in 'network', but clicking on does not give me access more :-(
I found that I can open the homedrive ready nas using the IP (\\192.***.*.***) in a new window of Solution Explorer. The media unit also works very well to access music. But why can't access through the 'network' - and why he always appears without giving me access...
I guessed that maybe it's to do with the new credentials of connection (since the change of a name of the EBU to an e-mail address), but how to change it in my windows pc network?
Any help would be great and simple steps please! Thank you very much.
Thanks to your inspiration I solved it my changing the password of the network connection of the former username of pre update for the new updated post e-mail deal as username via windows credentials... thank you everyone :-)
-
RVL200 and Windows 2000 Server - can not access network resources via VPN
I am new to the VPN, and I feel I'm missing something very basic in my configuration. I just installed a RVL200 as the gateway for my corporate network router. The network includes a Windows 2000 Server that acts as server DHCP and several PC and a printer. I was able to "establish a SSL VPN tunnel" home connection to the router, but after recording in everything I see is the screen of virtual Passage - one with lock icons - otherwise I am inside the router. The statement shows that I am connected. Once the tunnel is established, what am I supposed to do to get computers to the computers on my network? I can ping all computers on the network using their LAN address. I'm supposed to see a choice of network resources to get to this point? I put the router as a trusted site in the server and even tried to disable all firewalls, but I see that the VPN screen with icons. I don't know how to proceed from here because I don't know what I'm supposed to see. Thanks for any help that you can give to a newbie!
The SSL connection is only for the VPN router. To access the computer, you can use Windows Remote Desktop connection. So that you can access to remote computers on the network, or you could look for 3 third-party software for remote access
Hope this helps
-
Cannot access the internet via Blackberry 10 Simulator...
In fact, I'm in the workplace...
There are a lot of restrictions are there... every time that I'm trying to access internet from the blackberry browser 10 Simulator...
He rasises an error which is unavailable to the network (proxy is enabled).
When I connect the pc even to open the network while I am able to browse internet Simulator itself...
then I came to know that the proxy server is not bypassing the url generated from the Simulator...
can someone suggest a good answer to work with...
10 BlackBerry Simulator does not support connections via a proxy server. This looks like what you see.
-
Cannot access network resources - Cisco VPN client
Please see attached the network topology.
I can connect using the Cisco VPN client and access to all resources of the 192.168.3.0 network
I can't ping / access to all hosts on the network 192.168.5.0.
Any ideas?
Thanks for the help in advance
AD
Quite correct.
Please add has the access list:
CPA list standard access allowed 192.168.5.0 255.255.255.0
-
Unable to access company LAN via VPN
Hello
I have an ASA 5505 that I used to test run them the IPSec VPN connection after having studied the different configs and crossing the ASDM I get the same question that I can not receive any traffic.
The company LAN is on a 10.8.0.0 255.255.0.0 network, I placed the VPN clients in 192.168.10.0 255.255.255.0 network, 192 clients may not speak on the 10.8 network.
On the Cisco VPN client, I see a lot of packets sent but no receipt.
I think it could be to do with NAT, but the examples I've seen I think it should work.
I have attached the complete running-config, I might well have missed something.
Thanks a lot for all the help on this...
FWBKH (config) # show running-config
: Saved
:
ASA Version 8.2 (2)
!
hostname FWBKH
test.local domain name
activate the encrypted password of XXXXXXXXXXXXXXX
passwd encrypted XXXXXXXXXXXXXXXX
names of
name 9.9.9.9 zscaler-uk-network
name 10.8.50.0 Interior-network-it
Interior-nameservers 10.8.112.0
name 17.7.9.10 fwbkh-output
name 10.8.127.200 fwbkh - in
name 192.168.10.0 bkh-vpn-pool
!
interface Vlan1
nameif inside
security-level 100
IP fwbkh 255.255.0.0
!
interface Vlan2
nameif outside
security-level 0
IP fwbkh-out 255.255.255.248
!
interface Vlan3
nameif vpn
security-level 100
IP 192.168.10.1 255.255.255.0
!
interface Ethernet0/0
!
interface Ethernet0/1
switchport access vlan 2
!
interface Ethernet0/2
Shutdown
!
interface Ethernet0/3
Shutdown
!
interface Ethernet0/4
Shutdown
!
interface Ethernet0/5
Shutdown
!
interface Ethernet0/6
Shutdown
!
interface Ethernet0/7
Shutdown
!
banner intruder connection will be shot, survivors will be prosecuted!
Banner motd intruder will be Shot, survivors will be prosecuted!
banner intruder asdm will be Shot, survivors will be prosecuted!
boot system Disk0: / asa822 - k8.bin
passive FTP mode
DNS server-group DefaultDNS
test.local domain name
DM_INLINE_TCP_2 tcp service object-group
port-object eq www
EQ object of the https port
DM_INLINE_UDP_1 udp service object-group
port-object eq 4500
port-object eq isakmp
object-group Protocol DM_INLINE_PROTOCOL_1
ip protocol object
icmp protocol object
object-protocol udp
inside_access_in list extended access permitted tcp 10.8.0.0 255.255.0.0 any object-group DM_INLINE_TCP_2 journal of inactive warnings
inside_access_in list allowed extended access computer-network-inside ip 255.255.255.0 any idle state
inside_access_in list extended access permitted tcp 10.8.0.0 255.255.0.0 host zscaler-uk-network eq www
inside_access_in list extended access allowed inside-servers ip 255.255.255.0 log warnings
list of access USER-ACL extended permitted tcp 10.8.0.0 255.255.0.0 any eq www
list of access USER-ACL extended permitted tcp 10.8.0.0 255.255.0.0 any https eq
outside_nat0_outbound list allowed extended access bkh-vpn-pool ip 255.255.255.0 10.8.0.0 255.255.0.0
outside_access_in list extended access permit udp any host fwbkh-out object-group DM_INLINE_UDP_1 errors in the inactive log
inside_nat0_outbound list extended access allowed object-group DM_INLINE_PROTOCOL_1 10.8.0.0 255.255.0.0 any
inside_nat0_outbound_1 to access extended list ip 10.8.0.0 allow 255.255.0.0 255.255.255.0 bkh-vpn-pool
UK-VPN-USERS_splitTunnel of the access list extended ip 10.8.0.0 allow 255.255.0.0 255.255.255.0 bkh-vpn-pool
UK-VPN-USERS_splitTunnel to the list of allowed extensive access inside-servers 255.255.255.0 bkh-vpn-pool ip 255.255.255.0
pager lines 24
Enable logging
asdm of logging of information
Within 1500 MTU
Outside 1500 MTU
MTU 1500 VPN
mask UK-VPN-POOL 192.168.10.10 - 192.168.10.60 255.255.255.0 IP local pool
no failover
ICMP unreachable rate-limit 1 burst-size 1
ASDM image disk0: / asdm - 631.bin
don't allow no asdm history
ARP timeout 14400
NAT-control
Global (inside) 1 interface
Global 1 interface (outside)
NAT (inside) 0-list of access inside_nat0_outbound_1
NAT (inside) 1 10.8.0.0 255.255.0.0 dns
NAT (0 outside_nat0_outbound list of outdoor outdoor access)
inside_access_in access to the interface inside group
Access-group outside_access_in in interface outside
Route outside 0.0.0.0 0.0.0.0 17.7.9.10 1
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-registration DfltAccessPolicy
the ssh LOCAL console AAA authentication
Enable http server
http 10.8.0.0 255.255.0.0 inside
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
Crypto ipsec transform-set ESP-DES-SHA esp - esp-sha-hmac
Crypto ipsec transform-set ESP-DES-MD5 esp - esp-md5-hmac
Crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
Crypto ipsec transform-set ESP-3DES-MD5-esp-3des esp-md5-hmac
Crypto ipsec transform-set ESP-AES-256-SHA 256 - aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-SHA aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-MD5-esp - aes esp-md5-hmac
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 pfs Group1 set
Crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 value transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA MD5-ESP-3DES ESP-DES-SHA ESP-DES-MD5
outside_map card crypto 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
outside_map interface card crypto outside
Crypto ca trustpoint BKHFW
registration auto
name of the object CN = FWBKH
Configure CRL
encryption BKHFW ca certificate chain
certificate fc968750
308201dd a0030201 30820146 020204fc 96875030 0d06092a 864886f7 0d 010105
310e300c b 05003033 06035504 03130546 57424, 48 3121301f 06092 has 86 4886f70d
ccc6f3cb 977029d 5 df42515f d35c0d96 798350bf 7472725c fb8cd64d 514dc9cb
7f05ffb9 b3336388 d55576cc a3d308e1 88e14c1e 8bcb13e5 c58225ff 67144c 53 f2
quit smoking
crypto ISAKMP allow outside
crypto ISAKMP policy 10
preshared authentication
aes-256 encryption
sha hash
Group 2
life 86400
crypto ISAKMP policy 30
preshared authentication
3des encryption
sha hash
Group 2
life 86400
Telnet timeout 5
SSH 10.8.0.0 255.255.0.0 inside
SSH timeout 30
SSH version 2
Console timeout 0
dhcpd outside auto_config
!
a basic threat threat detection
Statistics-list of access threat detection
no statistical threat detection tcp-interception
WebVPN
strategy of UK-VPN-USERS group internal
UK-VPN-USERS group policy attributes
value of 10.8.112.1 DNS server 10.8.112.2
Protocol-tunnel-VPN IPSec svc
Split-tunnel-policy tunnelspecified
Split-tunnel-network-list value UK-VPN-USERS_splitTunnel
test.local value by default-field
the address value UK-VPN-POOL pools
attributes of Group Policy DfltGrpPolicy
VPN-tunnel-Protocol webvpn
username admin encrypted XXXXXXXXXXXXXXXXX privilege 15 password
karl encrypted XXXXXXXXXXXXXXX privilege 15 password username
type tunnel-group UK-VPN-USERS remote access
attributes global-tunnel-group UK-VPN-USERS
Address UK-VPN-POOL-pool
Group Policy - by default-UK-VPN-USERS
tunnel-group USERS of the UK VPN-ipsec-attributes
pre-shared key *.
type tunnel-group IT - VPN remote access
General attributes of IT - VPN Tunnel-group
Address UK-VPN-POOL-pool
Group Policy - by default-UK-VPN-USERS
tunnel-group IT - VPN ipsec-attributes
pre-shared key *.
!
ALLOW-USER-CLASS of the class-map
corresponds to the USER-ACL access list
type of class-card inspect all http ALLOW-URL-CLASS match
match without the regex ZSGATEWAY ALLOW request headers
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
maximum message length automatic of customer
message-length maximum 512
type of policy-card inspect http ALLOW-URL-POLICY
parameters
ALLOW-URL-class
drop connection
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the netbios
inspect the rsh
inspect the rtsp
inspect the skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect the tftp
inspect the sip
inspect xdmcp
Review the ip options
Policy-map ALLOW-USER-URL-POLICY
ALLOW-USER-class
inspect the http
!
global service-policy global_policy
USER-URL-POLICY-ALLOW service-policy inside interface
context of prompt hostname
call-home
Profile of CiscoTAC-1
no active account
http https://tools.cisco.com/its/service/oddce/services/DDCEService destination address
email address of destination [email protected] / * /
destination-mode http transport
Subscribe to alert-group diagnosis
Subscribe to alert-group environment
Subscribe to alert-group monthly periodic inventory
monthly periodicals to subscribe to alert-group configuration
daily periodic subscribe to alert-group telemetry
Cryptochecksum:00725d3158adc23e6a2664addb24fce1
: end
Hi Karl,
Please, make the following changes:
local IP VPN_POOL_UK_USERS 192.168.254.1 pool - 192.168.254.254
access extensive list 10.8.0.0 ip inside_nat0_outbound_1 255.255.0.0 allow 192.168.254.0 255.255.255.0
!
no nat (0 outside_nat0_outbound list of outdoor outdoor access)
!
UK-VPN-USERS_SPLIT of the allowed access list 10.8.0.0 255.255.0.0
!
UK-VPN-USERS group policy attributes
Split-tunnel-network-list value UK-VPN-USERS_SPLIT
!
No UK-VPN-USERS_splitTunnel scope 10.8.0.0 ip access list do not allow 255.255.0.0 255.255.255.0 bkh-vpn-pool
No list of UK-VPN-USERS_splitTunnel extended access not allowed inside-servers 255.255.255.0 bkh-vpn-pool ip 255.255.255.0
!
inside_access_in to access extended list ip 10.8.0.0 allow 255.255.255.0 192.168.254.0 255.255.255.0
!
management-access inside
******'
As you can see, I have create a new pool, since you already have an interface in the 192.168.10.0/24 network, which affects VPN clients.
Once you have finished, connect the client and try:
Ping 10.8.127.200
It work?
Try to ping so another internal IP.
Let me know how it goes.
Portu.
Please note all useful posts
Post edited by: Javier Portuguez
-
Cannot access remote resources - Cisco VPN Client
I'm having a problem with my Cisco VPN Client. I am new to VPN configuration, so this is probably something easy I'm missing. I have a my internet gateway for my LAN 2611XM router and my VPN server. I do all my tests of a society with a high card laptop mobile broadband. VPN connects, but anytime I ping anything in the network Cabinet, he returned with the public IP address of the external interface. I have NAT overload configured so any network can access the internet, inside which it looks like may be causing my problem. I don't know how to fix it. My config running is attatched. No one knows what might happen.
Oh, almost forgot to add. When I remove the nat overload on my interface fa0/1, the vpn will connect to any resource on the inside.
Your nat configuration seems to be the origin of the problem. If you are using an ACL to match the source for NAT, then it will be necessary to add the line 1A refuse for the local ip pool for your vpn clients to one only. try that to see how it goes.
Sent by Cisco Support technique iPhone App
-
Cannot access ESXi server via network
Hello world!
We have a HP C7000 Encolosure with 4 BL460c Gen 8 blades in front size of it. Back size of the C7000, we have 2 SAN Switch, 2 switch HP BLc GbE2c layer 2/3 and 2 Onboard Administrator Module.
Everything is working fine with IP addresses like this:
OA active:
IP address: 172.16.0.253
STANBY OA:
IP address: 172.16.0.254
Server Blade BL460c Bay 1:
The IP address of the ILO: 172.16.0.10
Server Blade BL460c Bay 2:
The ILO IP address: 172.16.0.11
BL460c blade Bay 9:
The ILO IP address: 172.16.0.19
Server Blade BL460c Bay 10:
The ILO IP address: 172.16.0.20
We can ping pc that connected to the port of ILO on Onboard Administrator (OA) IP addresses above. (I can it call PC MANAGE?)
Continue, we access OA via Web https://172.16.0.253 use of , then Console integrated to control 4 Server blades. We have mounted image ESXi 5.1 U1 and successfully installed on 4 servers blade.
We manually config IP address on each ESXi Server (like this):
BL460c Server Blade on Bay 1 as server ESXi 1:
IP address: 10.0.0.11
BL460c Server Blade on Bay 2 as server ESXi 2:
IP address: 10.0.0.12
BL460c Server Blade on Bay 9 as a server ESXi 9:
IP address: 10.0.0.19
BL460c Server Blade on 10 Bay as a server ESXi 10:
IP address: 10.0.0.20
Now we can ping server to another server ESXi ESXi 1. I mean 4 Blade Server can ping together.
BUT:
-We can not ping servers to blade PC of manage (that PC connect to the port of ILO on OSTEOARTHRITIS. In this scene, MANAGE PCs has the IP 172.16.0.100/16)
-We unplug the network cable from the port of iLO, then connect it to the port number 24 on HP BLc GbE2c LY 2/3 switch, then address IP of the PC to MANAGE the 10.0.0.100/24 value. Always the same, can only access servers
Can someone explain to me how to access this server (ping, http, etc...). Do we have to config switch HP BLc GbE2c LY 2/3? We read many many guide on the HP website, but they have not mentioned about routing or switch to configure
Thanks in advance!
It's my mistake!
My servers have 2 connections FlexLOM. That a connection has been enabled for 'network management' in ESXi. I do not understand, then I activated 2 connections. That cause outside the network can not access them.
I just disabled a single connection and everything works perfectly.
I thank everyone!
Maybe you are looking for
-
Portege M200 - weird display with docking station problem
Hello I use a Portege M200 with MS Windows Vista and the Toshiba docking station. Whenever I connected the system closed down it will start with low light and different screen resolution. The brightness can then be adjusted in Vista. To solve the pro
-
Qosmio G20 - its Media Center does not work properly
I do not often use the TV tuner, but when I went to save a program of the week last I found that I was getting loud hissing and sound distortion. Although I could play back a few straight recorded music. I ran the TV Tuner, settings and which seemed
-
I can't sign on my icloud account, saying: "check failed and an unknown error has occurred."
-
There every time. I don't know even how to stop to try every day. Any help will be greatly appreciated. I'm not very computer savy, so I don't have much technical knowledge or programming.Thank you.
-
We have a range of R730xd servers with 2 x controllers RAID H730P, each with a 8 x 6 GB/s SSD attached. Servers are sold as servers '12 + 12' drive, and the chassis has bays for 4 more disks per controller. When I read the H730P specification, I see