single interface
Hello
I was wondering if there is a way to combine the views of modules (a couple of State displays and a few slider control modules) in a single user interface. I know that this feature is available in labview, but haven't be able to find instructions or make reference to it in dasylab.
Also, I am currious to see if there was a way to protect a worksheet (optionally password protect), ultimately what I would be hoping to accomplish, is to create a spreadsheet to run an experiment, and then create a unique user interface so that anyone can run the test being able to set the values of a couple on the slides , but without the power to change logical paths.
Thanks for the help.
DASYLab offers the opportunity to password protect the worksheet as well as the ability to create page layouts.
Page layouts are full screens that you can use to create custom interfaces by integrating modules to display, create text fields and display the VAR and TEXT.
I would say the Full version or Pro if it is the way you want to go.
Tags: NI Products
Similar Questions
-
XNET multiple sessions on a single interface
Hello guys,.
I use XNET to communicate with our equipment CAN. In my project, I created 3 Sessions: session to an image of writing/sending frames to the device, a frame off session to receive the response from the device to the back and another frame in session for you connect all frames transmitted and received.
As part of the session, I do the property "echo of the transmitted frames" option ture, so that transmitted frames also appear as "read" frames and I can connect every image that I expected. Goal, if I, in another frame in a session also transmitted frames appear as frames 'read', even if I do the property "echo transmitted frames" option in this session to False. How can I do a session read all the frames transmitted and received, but the other is not? Thx a lot!
I don't think you can. Unfortunately, some of the properties of a session, are actually a property of the interface. XNet has also of resistance internal CDN, you can turn on and off. You do this by using the session reference and turn it on. Now, even if you have two sessions on an interface you have only a single interface and so you don't have a single property for if the resistance is on or off. If you turn it on in one sitting, it will be because he shares the same interface on the other.
I believe that the same is true when it comes to the echo. In most transceiver CAN echo is a feature of the transmitter/receiver and is a feature of the hardware, not software (similar to the example of resistance). So when you turn on the echo of the session, you really turn on echo for this interface, and I do not think that you will be able to turn on the echo of a session, but not all of them on the same interface.
-
Multiple Crypto cards on a single Interface of ASA
Hello
I work with a TAC support engineer, and while troubleshooting it suggests to assign two different cryptographic cards on a single interface.
It is technically possible to have multiple Crypto maps on a single Interface ASA?
PS: I know have several sequences in a single encryption card would work, but it is a case that I must address multiple Crypto maps on a single ASA.
Hi Ali,
The rule is by interface, a single card encryption is supported. You cannot assign more than one encryption on a single interface card.
Documentation: -.
"You can only assign a single encryption card defined on an interface. If multiple crypto map entries with the same name of card but a sequence number different, they are part of the same series and are applied to the interface. ASA first assesses the entry card crypto with sequence number low. »http://www.Cisco.com/c/en/us/TD/docs/security/ASA/ASA-command-reference/A-H/cmdref1/C6.html
Kind regards
Dinesh MoudgilPS Please rate helpful messages.
-
Dynamic and static map crypto on a single interface
I must apply encryption static and dynamic map to a single interface. is this possible?
crypto ISAKMP policy 10
md5 hash
preshared authentication
!
crypto ISAKMP policy 11
BA 3des
md5 hash
preshared authentication
Group 5
ISAKMP crypto key hronov address 50.76.65.124
address of pardubice key crypto isakmp 0.0.0.0 0.0.0.0
!
!
Crypto ipsec transform-set esp-3des esp-md5-hmac DYN - TS
Crypto ipsec transform-set esp-3des esp-md5-hmac ESP_3DES_MD5
transport mode
!
crypto dynamic-map 10 DYN
game of transformation-DYN-TS
!
!
!
card crypto IPSEC 10-isakmp dynamic ipsec DYN
!
GRE_AND_IPSEC 11 ipsec-isakmp crypto map
defined by peer 50.76.65.124
game of transformation-ESP_3DES_MD5
match address WILLYes. Slightly modified.
Make the key of a site to so it can't be used for xauth (aka the authentication of the client).
crypto isakmp key hronov address 50.76.65.124 no-xauth
Make the specific card crypto site site come first (priority 10 in this case).crypto map IPSEC 10 ipsec-isakmp set peer 50.76.65.124 set transform-set ESP_3DES_MD5 match address GRE
Do in this case priority low dynamic (60000) map.crypto map IPSEC 60000 ipsec-isakmp dynamic DYN
-
SSL vpn, single interface acting as outside/inside
Hi all
I'm trying to implement a VPN SSL (not without customer) with a cisco ASA 5510, but I'm a bit stuck since for testing the vpn will be in the same subnet as the destination to reach and so there is only a single interfaces connected to the network that would deal with internal and external traffic. I have attached a diagram of what I'm trying to do and the configuration of my ASA, hope this would be useful.
The entire network is for historical reasons on routed public ip addresses. There are ACL to block traffic from the internet on the workstation on our network that is 8.8.36.0/24.
As I am not responsible for management of this network, I would like to test vpn in several steps.
(1) the first step is to test this vpn from inside to inside
(2) second step would be to test this vpn from outside the internet inside network
(3) and the final step would be to put this vpn in one vlan separate
For the first step, I tried to connect to the vpn with the anyconnect client server, no problem with the creation of vpn, and I correctly get an ip address from the pool (for example: 8.8.36.181) but I can't contact the internal workstation on the 8.8.36.0/24 network.
I' I'm sure I'm missing something in the configuration, it would be possible to help me?
Thanks in advance,
1. Please use a different subnet as pool other than your network vpn client internal 8.8.36/24
2. given that traffic will turn back on ASA, you need the following command.
permit same-security-traffic intra-interface
-
Mutiple target in a single interface using ODI11g
Hello
I heard that we can place tables of mutiple to the target data source into a single interface with ODI 11 g.
According to my knowledge, we can place several tables in the data source source and target the unique to the data source table into a single interface.
Please can someone help me on this.
Thank you
PhaniHey Brad,
I don't think so.
Always ODI holding the concept of target one single interface.
No where I found this new feature. Take a look,
http://www.Oracle.com/us/products/middleware/data-integration/odi11g-newfeatures-WP-168152.PDF
Thank you
Guru -
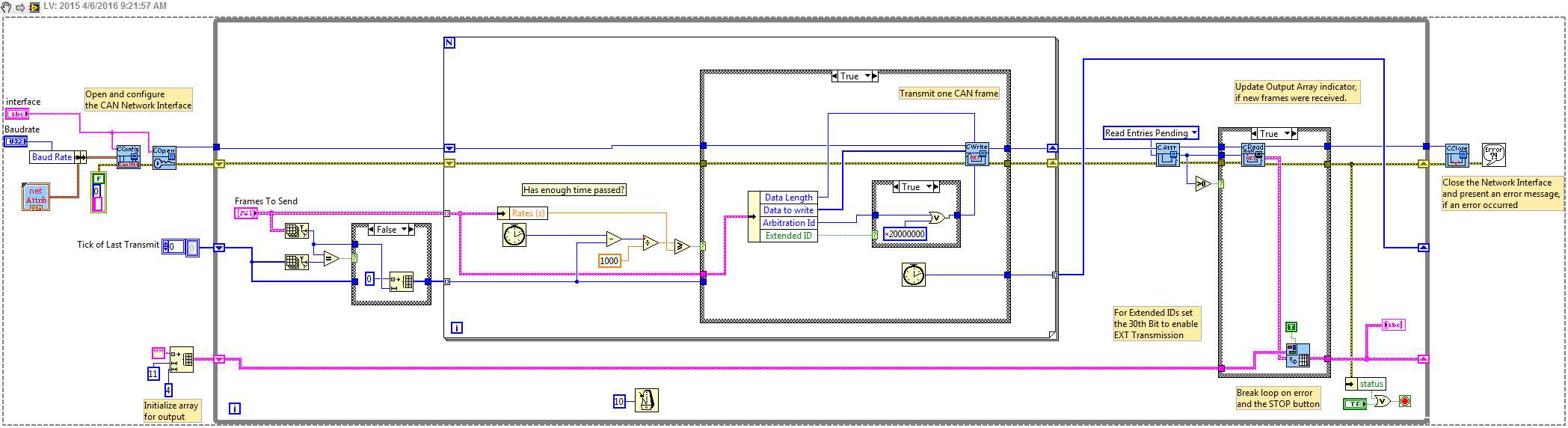
Is it possible to send several messages with IDS of different arbitration periodically (messages can have different periods) by simple CAN interface?
I use CAN frame API 2.7.5.
Not any material support retransmit material timed, so I usually stick with software programmed if calendar is not super critical. An improved version that works with an array of broadcast signals is attached. Each rate is assessed at the same time, and then this frame is sent, if enough time has passed.
-
OfficeJet 4500 and 6380: problem with all in a single interface
I have 2 HP laptops, as well as my work computer (a laptop HP also) and my Dell desktop computer girlfriends, air conditioned and have Windows installed 10.
I have a HP Officejet 4500 Wireless (G510n-z) All in One installed on my 2 HP notebooks and Dell Office girlfriends. My HP work laptop has an all-in-one printer HP Photosmart C6380 (CD028A) that is installed.
I know that the Dell itself will not be addressed here, but then it is still under warranty anyway.
My problem is:
Microsoft has released the update of security for Internet Explorer Flash Player for Windows 10 Version 1511 for x 64 systems (KB3132372). (My older HP laptop is 32-bit, but he got a 32-bit update for the same.)
It seems that this update of Adobe Flash Player ruined two all in software interfaces. (Both my 4500 Officejet AND Photosmart C6380 work).
When I try to open one of their interfaces, the initial screen flashes on the monitor but just going backwards.
My question is: HP has a file to download to fix them both all in software interfaces?
Thanks for any help.
Jeff Wohnsiedler
Hi @Jeff17866,
The question seems to appear in the last days of 2-3 due to the specific update.
He is currently under investigation by HP and Microsoft, these things take time, however.
Because now I suggest you uninstall the update of KB3132372 of programs and features > uninstall a program.
Then follow this troubleshooting to hide this update at the moment:
https://support.Microsoft.com/en-us/KB/3073930
Kind regards
Shlomi
-
More than 1 VPN using a single interface
I need to set up a VPN with four routers each router has different configurations but the main router has only one interface connected to the internet. Whenever I try to put in place more than a VPN on the same interface, it gives me an error that you have a VPN running on this interface, and it can be done, without taking into account this error will cost me VPN downwards from the previous site.
You must use the same card encryption, with the values of different priority (10 for the site-to-site first, 20 for the second), as the only card encryption can be applied on a given interface.
Please rate if this helped.
Kind regards
Daniel
-
VPN site2site & VPN client dailin on the question of a single interface
Hello dear colleagues,
First of all, the question of information subsequently:
Setup
C2801 race
(C2801-ADVENTERPRISEK9-M), Version 12.4 (25f)
---------- ----------
| Central | Di1 IP:80.153.xxx.xxx | DISTANCE | IP: 91.218.xxx.xxx
| Router | <-----------------------------------------> | Router |
-IPsec via GRE Tu1 - works | Debian |
^ | |
| ----------
| does not work
|---------------------------------------->-------------------
| Cisco VPN | Intellectual property: all
| Customer |
-------------------
!
AAA authentication login default local activate
AAA authentication login local VPN_Users
RADIUS group AAA authorization network default authenticated if
AAA authorization VPN_Users LAN
!
AAA - the id of the joint session
iomem 20 memory size
clock timezone THIS 1
clock summer-time EST recurring last Sun Mar 02:00 last Sun Oct 03:00
IP cef
!
username myVPN secret 5
!
!
crypto ISAKMP policy 1
BA 3des
preshared authentication
Group 2
life 3600
address
key crypto isakmp xauth No. 91.218.xxx.xxx ISAKMP crypto nat keepalive 20
!
Configuration group customer isakmp crypto VPN_dialin
key
DNS 192.168.198.4
domain example.com
pool VPN
ACL VPN
Crypto isakmp VPNclient profile
match of group identity VPN_dialin
client authentication list VPN_Users
ISAKMP authorization list VPN_Users
client configuration address respond
!
Crypto ipsec security association idle time 3600
!
Crypto ipsec transform-set esp-3des esp-sha-hmac hostb-transform
transport mode
Crypto ipsec transform-set ESP-AES-128-SHA aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-SHA-LZS, hmac-sha-esp esp - aes comp-lzs
!
!
crypto dynamic-map vpn-dynamic-map 10
game of transformation-ESP ESP-AES-128-SHA-AES-128-SHA-LZS
Define VPNclient isakmp-profile
!
!
!
HostB-cryptomap 1 ipsec-isakmp crypto map
the value of 91.218.xxx.xxx peer
the transform-set hostb-transform value
PFS group2 Set
corresponds to hostb-address list
!
dynamic map crypto hostb-crytomap 65535-isakmp ipsec vpn-dynamic-map
!
!
!
!
!
!
Tunnel1 interface
bandwidth 100000
IP vrf forwarding vl199
IP 10.0.201.2 255.255.255.0
IP 1400 MTU
IP nat inside
IP virtual-reassembly
IP ospf network point
source of Dialer1 tunnel
destination 91.218.xxx.xxx tunnel
bandwidth tunnel pass 10000
bandwidth tunnel receive 50000
!
interface Dialer1
Description # PPPoE T-Online.
MTU 1492
bandwidth 50000
IP ddns update hostname it-s - dd.dyndns.org
IP ddns update it-s-dd_dyndns_org
the negotiated IP address
NAT outside IP
IP virtual-reassembly max-pumping 512
encapsulation ppp
IP tcp adjust-mss 1452
no ip mroute-cache
Dialer pool 1
Dialer idle-timeout 0
persistent Dialer
KeepAlive 20
No cdp enable
Authentication callin PPP chap Protocol
PPP chap hostname
PPP chap password 7
PPP pap sent-username
password 7 PPP ipcp dns request
card crypto hostb-cryptomap
Crypto ipsec fragmentation after encryption
!
!
local pool IP VPN 192.168.196.30 192.168.196.60
IP forward-Protocol ND
IP route 0.0.0.0 0.0.0.0 Dialer1 track 1
IP route 0.0.0.0 0.0.0.0 Tunnel1 20 Track3
IP route 0.0.0.0 0.0.0.0 Dialer1 254
IP route vrf vl199 0.0.0.0 0.0.0.0 192.168.1.251
IP route vrf vl99 0.0.0.0 0.0.0.0 192.168.3.1
!
The dns server IP
!
no ip address of the http server
no ip http secure server
TCP-time translation nat IP 3600
translation of nat IP udp-timeout 600
IP nat Pat_for_192.168.198.4 192.168.198.4 pool 192.168.198.4 netmask 255.255.255.0 type
IP nat Pat_for_192.168.200.50 192.168.200.50 pool 192.168.200.50 netmask 255.255.255.0 type
IP nat inside source static 5060 udp interface 192.168.200.50 Dialer1 5060
IP nat inside source static tcp 192.168.200.51 3389 3389 Dialer1 interface
IP nat inside source static tcp 192.168.198.4 3389 interface Dialer1 3390
IP nat inside source static tcp 192.168.198.9 interface 5000 Dialer1 5000
IP nat inside source overload map route dialer1 interface Dialer1
IP nat inside interface 13001 static udp 192.168.199.3 source Dialer1 13001
IP nat inside interface 32768 static udp 192.168.179.2 source Dialer1 32768
IP nat inside source static udp 192.168.179.2 Dialer1 49152 49152 interface
IP nat inside interface 64206 static udp 192.168.179.2 source Dialer1 64206
IP nat inside source static udp 192.168.179.2 interface 7597 Dialer1 7597
IP nat inside source static tcp 192.168.179.2 9998 interface Dialer1 9998
IP nat inside source static tcp 192.168.179.2 7597 interface Dialer1 7597
IP nat inside source static tcp 192.168.179.2 64206 interface Dialer1 64206
IP nat inside source static tcp 192.168.179.2 Dialer1 49152 49152 interface
IP nat inside source static tcp 192.168.179.2 Dialer1 32768 32768 interface
IP nat inside source static tcp 192.168.198.4 interface 443 443 Dialer1
IP nat inside destination list Pat_for_192.168.198.4 pool Pat_for_192.168.198.4
IP nat inside destination list Pat_for_192.168.200.50 pool Pat_for_192.168.200.50
!
Pat_for_192.168.198.4 extended IP access list
Note = Pat_for_192.168.198.4 =-
permit tcp any any eq www
permit tcp any any eq 987
permit tcp any any eq 143
permit tcp any any eq 993
permit tcp any any eq pop3
permit tcp any any eq 995
permit tcp any any eq 587
permit tcp any any eq ftp
permit tcp any any eq ftp - data
permit tcp any any eq smtp
Pat_for_192.168.200.50 extended IP access list
Note = Pat_for_192.168.200.50 =-
allow udp everything any 10000 20000 Beach
permit tcp everything any 5222 5223 Beach
allow udp any any eq 4569
permit any any eq 5060 udp
list of IP - VPN access scope
IP 192.168.198.0 allow 0.0.0.255 192.168.196.0 0.0.0.255
permit ip host 80.153.xxx.xxx 192.168.196.0 0.0.0.255
list hostb extended IP access list
permit ip host 91.218.xxx.xxx host 80.153.xxx.xxx
permit ip host 80.153.xxx.xxx host 91.218.xxx.xxx
permit ip host 10.0.201.2 10.0.201.1
!
!
access-list 10 permit 192.168.200.6
access-list 100 permit ip 192.168.0.0 0.0.255.255 everything
access-list 100 permit ip 10.1.0.0 0.0.255.255 everything
access-list 100 permit ip 10.0.0.0 0.0.255.255 everything
access-list 101 permit ip 192.168.199.3 host everything
access-list 101 permit ip 192.168.199.4 host everything
access-list 101 permit ip 192.168.199.13 host everything
access-list 101 permit ip 192.168.199.14 host everything
access list 101 ip allow any host 204.13.162.123
access-list 103 allow ip 10.0.1.0 0.0.0.255 any
!
dialer1 allowed 10 route map
corresponds to the IP 100
match interface Dialer1
!
!
####################################################################################################
SH crypto isakmp his:
status of DST CBC State conn-id slot
91.218.xxx.xxx 80.153.xxx.xxx QM_IDLE 7 0 ACTIVE
80.153.248.167
QM_IDLE 12 0 ASSETS ######################################################################################
SH encryption session
Current state of the session crypto
Interface: Virtual-Access5
The session state: down
Peer: port of 91.218.xxx.xxx 500
FLOW IPSEC: allowed ip host 10.0.201.2 10.0.201.1
Active sAs: 0, origin: card crypto
FLOW IPSEC: allowed ip host 80.153.xxx.xxx host 91.218.xxx.xxx
Active sAs: 0, origin: card crypto
FLOW IPSEC: allowed ip host 91.218.xxx.xxx host 80.153.xxx.xxx
Active sAs: 0, origin: card crypto
Interface: Dialer1
The session state: UP-NO-IKE
Peer: port of 91.218.xxx.xxx 500
IKE SA: local 80.153.xxx.xxx/500 remote 91.218.xxx.xxx/500 inactive
FLOW IPSEC: allowed ip host 10.0.201.2 10.0.201.1
Active sAs: 0, origin: card crypto
FLOW IPSEC: allowed ip host 80.153.xxx.xxx host 91.218.xxx.xxx
Active sAs: 4, origin: card crypto
FLOW IPSEC: allowed ip host 91.218.xxx.xxx host 80.153.xxx.xxx
Active sAs: 0, origin: card crypto
Interface: Dialer1
The session state: IDLE-UP
Peer: port of
55033 ITS IKE: local 80.153.xxx.xxx/4500 distance
55033 Active ################################################################################################################################
Error message:
020932: 2 Oct 21:55:14.459 CEST: IPSEC (validate_transform_proposal): No IPSEC cryptomap is to address local 80.153.xxx.xxx
020933: 2 Oct 21:55:14.459 CEST: IPSEC (validate_proposal_request): part #1 of the proposal
(Eng. msg key.) Local INCOMING = 80.153.xxx.xxx, distance =
,. local_proxy = 0.0.0.0/0.0.0.0/0/0 (type = 4),
remote_proxy = 192.168.196.32/255.255.255.255/0/0 (type = 1),
Protocol = ESP, transform = esp - esp-md5-hmac (Tunnel-UDP).
lifedur = 0 and 0kb in
SPI = 0 x 0 (0), id_conn = 0, keysize = 0, flags = 0 x 400
020934: 2 Oct 21:55:14.459 CEST: IPSEC (validate_transform_proposal): No IPSEC cryptomap is to address local 80.153.xxx.xxx
020935: 2 Oct 21:55:14.459 CEST: IPSEC (validate_proposal_request): part #1 of the proposal
(Eng. msg key.) Local INCOMING = 80.153.xxx.xxx, distance =
,. local_proxy = 0.0.0.0/0.0.0.0/0/0 (type = 4),
remote_proxy = 192.168.196.32/255.255.255.255/0/0 (type = 1),
Protocol = ESP, transform = null esp esp-md5-hmac (Tunnel-UDP).
lifedur = 0 and 0kb in
SPI = 0 x 0 (0), id_conn = 0, keysize = 0, flags = 0 x 400
#################################################################################################
I tried to understand where is my mistake, can someone help me find it?
Thank you very much
concerning
crypto map hostb-crytomap 65535 ipsec-isakmp dynamic vpn-dynamic-map
is the fault of typing in the name as in your original config?
--
Don't stop once you have upgraded your network! Improve the world by lending money to low-income workers:
http://www.Kiva.org/invitedBy/karsteni -
TimeMachine and two Ethernet interfaces
OS version 6.4.2 OS X 10.11.3 (El Cap).
That ReadyNAS has two ethernet interfaces, which I had connected without adherence to the network.
All Mac on the network would be fix and update the sparsebundle on the ReadyNAS for some time (two days for example) and then each machine would begin to complain that the destination does not exist. One solution would be to reboot the NAS and things would work for a while.
How I solved this problem is to simply unplug one of the NAS ethernet ports and run on a single interface.
I guess that there is a conflict in the NAS with Hello or other discovery services and some confusion about the interface gets introduced to the network. This seems to change with the times.
I could possibly get a switch that supports the binding, but for now I would like to be able to run both interfaces if possible (I pay for them after all)
Hi rawb1,
Concerning the use of multiple network cards or adapters ethernet in your ReadyNAS system, here are some useful articles from NETGEAR that you can watch.
ReadyNAS OS 6: Set up cards under customs
ReadyNAS - collage/team and how should I use?
I hope this helps!
Kind regards
BrianL
NETGEAR community team -
number of dynamic interfaces in a group of interfaces regarding 8510 controllers
I have a controller 8510, is it possible to club 130 dynamic interfaces in a single interface group?
I guess a single interface group can have 64 dynamic interfaces, if there is a way to club 130 dynamic interfaces in a group unique interface, please suggest.
I suggested to my client to create two interface group, a dynamic group of 64 can interfaces each, but he suggested the following
- If the interface of several groups to be created, rules of correspondence ACS must make the same number (access policies ACS allowing only 1 name of Air Interface [interface group] in line with the strategy)
- Having several access policy for the Group of users even identify unknown factors in the distribution of access requests between two or more access policies where they the same group of service users
Hello
Yes, you just... you can have a max 64 interface in a group of interfaces:
Here is the reference (table 2): http://www.cisco.com/c/en/us/td/docs/wireless/controller/technotes/8-1/8...
So you cannot combine all the 130 dynamic interface in a group.
According to my experience: one solution is to use 2 SSIDS and each ssid must have a group of interfaces (64 interfaces).
Concerning
Remember messages useful rates
-
Area-based-Firewall: card crypto / tunnel interface / area?
Hello
We use a router CISCO1921-SEC. On the side "WAN", we have 1 public IP assigned by DHCP address.
At present, we use the WAN Interface with a crypto-map as endpoint of some IPSec connections. We have created a zone - fire-with area "WAN" and "LAN". In this configuration, all IPSec parameters are on a single Interface - connection to the 'LAN' box can be managed through rulesets. What about the connections between IPSec connections and the area "self."
We would like to finish each IPSec connection in a separate area. Is this a good idea?
How can this be configured?
Each of them on a "inetface tunnel" with binding "tunnel source...". » ?
Please give us a clue... Thank you!!
Message geändert durch NISITNETC
When the tunnels are completed on the router, which is the area free, by default, all traffic is allowed, if you want to restrict access, you must create a free zone and add a pair of WAN area to auto.
Hope this link will help you,
-
With an interface easy VPN client only
Hi guys,.
I have an ASA 5505 configuration as simple Client VPN. Current configuration uses two interfaces: inside and outside. I tested the connection to the server and works very well.
For reasons of site specific I'm limited to a single interface, you can call it inside, lan, whatever. So I need to connect clients to the remote site behind this interface and also use it to reach the easy VPN server. Is it possible in the first place?
Of course, I will put the default route through the Interior of interface and another router will provide the Internet connection.
It's so hard to make it work you should consider the answer is no.
Specifically, you need to have one inside and outside interface or EasyVPN will not come to the top.
-
Dynamic interfaces, VIRTUAL, multiple physical interfaces LAN?
Hello
We're just starting with a WLC 5508 and WCS. We can already see that it is a big improvement on our installation current with autonomus AP we are also implementing some 11n AP is in this framework.
I think I understand the multiple interfaces AP-Manager and balance the load of the average AP in these. But I do not understand what customer traffic should be load-balanced.
The goal is to have a WLAN. When I create this I select a dynamic interface (and so a VLAN for the customers). But this VLAN is bound to a physical port (with a port of relief). So my understandig of the wil of customer traffic from the AP to the controller on several interfaces, but then goes out to the servers in a single interface?
It's not what I want - I'd like to that traffic on him VLAN on the servers to be distributed on several ports. How do I do that? I then use LAG?
Kind regards
Kaj
OK, if you don't have that a WLAN you would probably a dynamic interface, unless you use AP group VLAN.
Maybe you are looking for
-
Default size of paper in the print preview
Mode legal print preview, I changed the format of paper and now it is the default value. How can I get the default back to letter format and keep so I don't have to change each time I print? Here also the predefined default settings for ink black & w
-
When I access the net with firefox, a new tab opens on a specific page. How can I block access to this site or stop firefox from loading? Here is the site in question: http://AdultFriendFinder.com/go/g1110961-PMOnot once have I ever accessed this sit
-
completely remove a partition of the HD
I had my iMac a few weeks now and created a partition to put things that I wanted to keep away from the main road. Now, I decided to install windows 7 and possibly upgrade to windows 10. Problem! When I try to use Bootcamp to install it guard refuse
-
Hello world According to the statement, NOR for the verification of the Pxi4330 procedure, I need "Disable calibration shunt for the channel by using the property node DAQmx Channel, you can find custom I/O" DAQmx - data palette purchase LabVIEW. "'"
-
create folders in Windows live mail on my iPad 2 Air
Can I create folders in Windows live mail on my iPad 2 Air. I need folders to organize my email to come.