Timed CSA rules
Hello
Does anyone know how to create a rule that runs for a period of time say 5 minutes
You can create rules to add and remove processes for specified time intervals.
Look at homelessness - module of rule VPN to 5.2 CSA for an example.
Tom
Tags: Cisco Security
Similar Questions
-
I am running APF on a number of jobs in direct mode, but I wanted to give some users a privileged access (Tech) so I created a group of States with these users user and when users log into a machine with the CSA, they are able to see the interface user and turn csa to install applications. For other users of that rule of the user interface is not enabled so not visible on their desktop. It seems to work, but the user interface often disappears if I make it a rule to change or create a new rule. It's a good way or I'm hacking in a way that should not be used. Now technicians need to reboot the machine and relog in their accounts to see the icon of the CSA client. Seems to me that there should be a better way.
Sounds like a good way. Don't forget there is no other User Agent interface control rules that could be walking on the one you have created.
In addition, the User Agent interface will disappear if there is no User Agent applied to the host interface control rule.
Tom
-
Best way to change the default rule in CSA
People,
Could someone guide me please how best to change the default rules on the CSA MC. I would like to address some of the rules and I do not know how to change the default rules, can be copied and change them and increase the priority?
Thank you
Use the wizard to create the exception. The default value is that it will create an exception to the policy by creating a new module of rule and assign to politics. Then, you can see how the exception works and you can change the exception rather than the rule. This keeps unchanged Moose rules but allows you to make all the necessary changes to get your apps to work.
Tom S
-
Management Center for Security Agents Cisco v4.0 - 1 build 544
Configuration--> policies--> quarantine network--> rules to change Module--> of network access control
Then, you delete by mistake a rule... YIKERS... but you have not clicked on generate rules--> generate again.
Is it possible to revisit this rule?
What bring the default set of rules?
More curious than anything whatsoever. The a doc I've read don't develop much. You are welcome to send me links to documents on the Cisco site. I have access to most of it.
Thank you
Jeff
Not that I know of. You could do a restore configuration (if you set it to automatically back up), but it looks like you just make the rule. You will lose all changes made since the backup well.
A best practice, in my opinion, is to clone all the policies that you will work with and make changes to them rather than the default ones. This way you always have the default policies to watch. Unfortunately he is unable to help you...
-
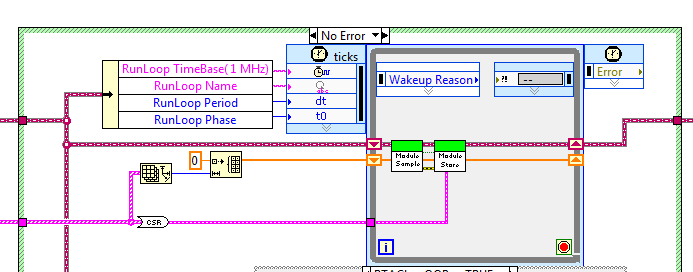
Abandonment of a loop timed - what happens?
LV2013, LVRT 2013
I'm not clear on what happens when you STOP a timed loop, STOP TIMED STRUCTURE vi.
The help says:
"If you try to interrupt a timed running the timed immediately loop loop runs the current iteration and returns ABORTED in the output of the REASON for the data node left."
Given the following loop:
I can abandon this loop, by name, by the way.
This cancellation occurs at any time, regardless of this loop is where its cycle.
This loop runs at 10 Hz and takes 1 to 2 mSec per iteration.
1... what happens if the cancellation occurs during the delay? I guess that he wakes up with the reason set to ABORTED. It executes the code inside, or not?
2... Suppose that the loop has already run the vi of the SAMPLE, but not the vi STORE, when comes the demolition. It don't...
( ) 2A... An abortion without running the STORE?
( ) 2B... Run the STORE, browse again with REASON = INTERRUPTED, and then runs the SAMPLE and STORE again?
( ) 2C... Run the STORE, browse again with REASON = INTERRUPTED, then popping out without running again?
3... assume that the loop is located in the middle of the vi of the SAMPLE. What is this VI partially abandoned through?
What throws me is help text: "immediately runs the current iteration and returns ABORTED."
If she abandoned after he woke up normally, then the REASON is already set, so he can't tell me that it's been abandoned. But if she should set the REASON, then it must finish executing the code, browse AGAIN, and then run the code AGAIN, isn't?
Anyone know the rules for this?
I have not tested, I guess based on a combination of documentation and experience in similar situations. It should still run once with the reason set to ABORTED to give the code inside a chance to do a cleaning. If you are in the middle of an iteration, it will end this iteration, then run again immediately. If cancellation is received during the wait, the loop is executed immediately once (stops pending). The last execution will always be reason set to ABORTED, and you never have a situation where the code is suddenly stopped in the middle of execution.
-
Structure of the timed real-time event loop does not work
I'm a new user for LabVIEW. And I've encountered a problem that frastre really me! Hope someone can help out me. Thanks in advance!
I just want to use the structure of the event under timed loop, which is important in my extrmely design.
However, this works very well in my computer (without connecting to the FPGA).
Once I connect it to the FPGA, then I can still run but there is no response!
My file is attached. Please someone help me!
Looking forward to your answers!
The FPGA runs headless. Structures of the event won't work. What you need to do is to have an application on your host computer when the user presses a button, changes a value, etc.. This event should send a message via TCP/IP for code that runs in real-time environment. Then the real time environment should attribute to the desired value a control on the FPGA.
As a general rule, programming real-time with FPGA has several layers.
(1) host-> handles interactions with the user code and communicates the code in real-time via TCP, UDP, etc.. Displays the user sent by RT controller data.
(2) code in real-time-> tracks headlessly. Manages host code messages, processes the data of FPGA, communicates with FPGA much as the host code communicates with the code in real-time
(3) FPGA-> no acquistion and passes through PEP in the RT
The first thing you need to do is to understand the architecture and how all these pieces of the puzzle work together before you throw things down on a diagram.
-
Rule for access to documents on a server
Hello
How to create a rule that allows recovering files .xls and .doc for an internal intranet site and still block extraction of files from another server to Internet Explorer.
At the present time CSA keeps popping up asking you want to allow this?
"The process"C:\Program may Explorer\iexplore.exe"(as user XXX\admin) tried the open/create file"C:\Documents and admin Settings\Temporary Internet Files\Content.IE5\WTRRRTQZ\CompanyExpensesForm[1].xls"and the user was questioned. The user responded by choosing "Yes to all". "
This is section 321
Thanks for any help
Do not know the pickiness issue but it seems that the rule of module Office 321 allows downloads.
If you have the DAC to work, you could add the desktop module and change the 321 rule to deny file access control.
Which could serve as the corresponding deny rule, that I mentioned earlier. It seems that the rule of module Office 321 replaces your DAC and allows downloads.
-
CSA 5.1 (Classification of the untrusted content Module)
Hi Experts,
I'm under CSA in my driver and his kind of stable now and working Fine.I need to know one thing I hv disabled 'Module of Classification content unreliable' according to the classification of the Application policy makes part of all the Windows Group.I hv disable this module, because there are more than 1000 applications runing in my body and will add more new applications that cannot be tested in my Test harness.
I want to know the level of security tht I hv compromised by disabling this module on my ASC.
No, it monitors just apps and ranks them according to the rules. A bit like protection of the core rules. It can also be useful in the investigation of the Application.
You must test with real outside your if possible laboratory stations, but you don't need this rule to do.
-
We are deploying CSA ver5.0 in our society. I read 2 books for Cisco Press but wanted to get an idea of what real companies use as their groups. We have all the windows, all Types of desktop computers, remote desktop or Mobile and CTA. Everyone thinks it is exaggerated or under the protection of a starting point?
The only problem we encountered so far is that the IBM portable computer touchpad driver is detected as an untrusted root kit. If someone met what I'd like to hear about your solution. TAC still works with us on this to create an exception that works.
Thank you
Dvergau,
I think it is maybe too kill to a pilot group. That is where I hope you intend to start. You want to import a little, you decide what is a little, then slowly adjust and Add. What I mean is that you need to adjust these rules that block the operation. Then add a little more political and other.
Many people have several ways of doing things. Some suggest simply use the wizard for all, many will tell you to clone all groups and modify those that don't. Cloning is a pretty smart way to keep a reference point. Yet once again, I suggest you start small and build up to the reference level.
Regarding the rootkit, it's tough. The only way to allow the rootkits are to use the wizard. The wizard will make the hashes and application and the exception. I found a similar problem with Symantec. Leaving me the only option to disable the notification, or to add hashes on the fly.
Hope this helps, if you need just to all creation information and politics rule. I'll help you better than I can.
Kind regards
Christopher
-
What is the best way to grant CSA 5.0 so that the changes you make to a group do not affect the rules of another group?
Is there a way to create a rule for a group? where I could say still allow this class access application run?
Or will I have to create clones of all the rules and have each group point to its rules cloned?
Any help is greatly appreciated.
Thank you.
A rule must belong to a module and as a policy, so the answer is no.
You should not need to have all the cloned rules, just as the exception rules applies to a single group.
A separate policy for this group with just the exceptions in a module of rule would probably work better for this.
Tom
-
What is the default action of the CSA?
Hi all
I'm a newcomer to the CSA. I have a few questions as follows. Could you please clarify it for me?
1. If all the rules do not match the event, what measures will it take place? Allow or deny?
2. If the first answer is allow, how it can protect the system from the zero-day attack?
Thank you very much
Nitass
Nitass,
You are right that if no rules are triggered, CSA does not interfere with the application. But to answer the second half of your original question, CSA protects attacks zero-day monitoring of behavior rather than signatures. In other words, it doesn't matter what the attack code looks like, no matter what he does. For example, if you get attacked by a new virus, not have a signature for your anti-virus software to detect. But if she tries to install a copy on your computer, or tries to install a rootkit, or open a port for listening or scans for other vulnerable hosts, CSA detects these actions and block them.
-
I have a problem with the CsA and print the screen, if the workstation is in the test mode print screen, alt print screen works very well. However, when the machine is in application mode the user is unable to use this feature. Worse still there is no generated logs. Has anyone seen this behavior before and well more to the point what is the cause.
You have a 'Clipboard' access control rule applied to users?
If you have (if its allowing or refusing the application) will be disabled the print-screen feature.
See below for reference
+++++++++++++++++++++++++++++++++
NOTE: If you use the Clipboard rule to limit applications to access data from the Clipboard, print screen feature system is also automatically disabled.
++++++++++++++++++++++++++++++++++
------Naman
-
Anyone know if it is possible prevent users to connect to networks without wire for the connection of the ethernet adapter? I have create a strategy and used rule Module included in CSA (prevent if wireless Active Ethernet) and it allows me to connect to wireless networks.
Any info would be greatly appreciated.
I think that they create them then they are there if needed and you don't have to create them from scratch.
You can associate the module existing rule to a new wireless policy and who join your groups.
If you clone and modify the copies or change the original is a personal preference.
In any event, it should work and there are people who prefer one over the other for various reasons.
Tom
-
Hello
I have a case where a customer needs me to build a custom strategy for about 250 pc with users of developer on them, of the Eclipse RAD to the developers of Prolog and some Mainframe people as well and everything in between really.
Usually I give up from the start, since these types of people work in the more lawless ways and with most of the time no systematic way to use their system... at least that's my experience.
Maybe someone has an another experince with the implementation of CSA policies for this type of user?
At CSA, you can apply modules based on the statements of the user. Make sure that you run CSA 4.5.0 573 or the latest version of the CSA 4.5.1 616 since 4.5.0 565 contained many bugs that did not have the rules of the user state to run accordingly. You can find documentation for the user States to:
http://www.Cisco.com/en/us/docs/security/CSA/csa45/user_guide/Chap4.html
-
After the 6.0.1 update 6.0.2 start some systems with CSA impossible.
If manually remove agent (in safe mode) - ok again.
A few butable systems, but the Treaty officer takes more then 90% CPU resourses.
Logs on CSA MC are clean
Any ideas? Manual uninstall agent on hungreds little workstaitions is unreal...
There was a recent bug discovered with interaction of the APF and Windows 7 guests where access control rule files that implements digital suignature control can cause a system to 'hang' after you have entered identifying information. The bug is CSCtg98849. The following workaround is provided in the bug:
Edit the "Base - Digital Signing of Downloaded Executables" rule module and disable the file access control "Send downloaded executables for scanning if opened for read".
Save the change.
Generate rules and deploy to affected hosts.
[Wrap text] [Edit this forum]
Support Note: added the 2010-05-25 06:26:54 by scfringe
[Unwrap text] [Edit this forum]
Support Note: added the 2010-05-25 06:26:54 by scfringe
Maybe you are looking for
-
iMac A1311 does not start, due to no HARD drive
I have an iMac A1311 that has no HARD drive, so I have a disk HARD of Windows and OS X 10.6.1 discs. Can I use my PC to format the HARD drive and install OS X on the HDD using my PC? iMac will not start cuz no HARD drive
-
Need to connect by Satellite U945-S4110 to the VGA-IN of the external monitor port
I need to configure my laptop Toshiba U945-S4110 to be connected to the VGA input of a display screen.What do I need? Is this enough for this HDMI to VGA Converter active http://www.Amazon.com/1080p-female-video-converter-adapter/DP/B008279OJ6/ref=sr
-
Outlook 2010: Cannot open the mail files
Hello! Help me stop Outlook 2010 error message: "Cannot open your default e-mail folders. The information store could not be opened. » Thanks in advance.
-
Remove the scientific notation in report
I am calculating a number and put it in a box of comments on a report. It works very well, but one of the numbers has decided to display in scientific notation (1.52666667e - 3). The problem is that the comment box is not large enough to display scie
-
Even if I put new ink cartridges in the windo continues to show low ink I can do to fix this?
How can I change the view of low ink even though I put new cartridges in?