Attack and Release in Compression
Good, rather than as one problem, another one of my academic discussions 'how it works '.
On another forum, I debated the meaning of 'attack' and 'release' in compression. My thesis is that the attack time is how long it takes to reach the set level of gain reduction once the signal passes through the threshod... level and liberation is the opposite: reduction, once again the time it takes to come back or not gain levels once to cross the threshold down.
Another poster, who usually knows what he's talking about, the content as time attack and release are triggered, not levels reaching the threshold, but rather simply by the compressor, a level upward or downward change detection.
As evidence, he has published a test of Soundforge: a tone that made the transition between - 12 and - 3 dB at intervals 300ms. He then applied with the threshold set at-16 compression (so everything should be compressed) and, indeed, the waveform shows the effect of the attack and communicated to each transition even if the test set should be compressed.
I tried the same thing at the hearing and, although things are not as noticeable as Sound forge, you can see the pumping on the waveform.
I don't see that the attack and release can be quite skilled to respond to each change in level (especially on a real signal, not his test) so I have to assume that the cause is a bit more basic.
Here is a picture of the original file that I made:
And here is the same file compressed with an attack of 2ms and 5ms release and a threshold of - 15dB, i.e. less than what anyone in the clip.
As you can see, you can see where the attack and release happens (I do not post a picture but, with attack and release to zero, you can not see any transition) so if someone can explain that you will cure my curiosity!
Want to know how to work the compressors?
Well, I wouldn't trust in Wikipedia - especially when he's wrong!
We must look at the history of the compression, and how this was done by conventional electronic means before having any kind of idea of how it works really - and then we must keep in mind that even if software compression can move some of the apparent problems, it is not necessarily a good thing to do.
The initial problems with compression were double, when it came to the electronic traditional compressors. First, they took the time to analyze the incoming signals; Second, they took even more time to respond to the changes. It is usually because the element doing the control signal (and there were several different methods) also had a finite response time. Usually the response of the control element has been physically forced, and ultimately limited the attack time - even if you can detect a more rapid change, you could not apply it more quickly - you could not delay the release, that needed to be addressed in real time. The response of the detector is essentially based on the amplitude - if the first half cycle exceeds the amplitude threshold, then theoretically a corresponding signal is sent to the control element. The detector, but always follows the the envelope amplitude of the received signal, and this is what determines, by the controls, the compression ratio. The decay time depended entirely on controls of that - at the time wherever the envelope of the signal is less than the threshold, the rate of decay sets in. If the signal rises to the top, then decay stops - after another attack of time spent.
The threshold setting determines the point at which the control starts, and report control determines the rate of Exchange used at that time - and that's why Wikipedia quote is bad, because the absolute level has not been determined at all - just the rate to which the control signal is going in this direction. It may be supplanted by a change of the signal level.
In any case, it is this that compressors software were essentially try to imitate. I have never designed a software, but I designed and built a couple of material ones - that's why I know not how they work!
But what is that software that can compensate for certain aspects of the behavior of compressor, because they have not primarily to work in real time. This means that it is possible to use ' to come'. If you do this, then theoretically you can do a good job the same catch the first half cycle of a waveform that exceeds your threshold - because you have already made the detection. And because you control software of the final amplitude rather than a hardware device, you can cause instant changes unfold. But as everyone experiences a software compressor soon realizes, most of the things that are possible not - happen devices are designed more along the lines of the original material, because that's what people really want! They do not want instant attack, because that gets rid of transients, and that's where a lot of crucial information in a signal. Also, for other timed titles of pumping is called for - and that requires a system with a known time response, not one where the rate of change of the input signal is determined and used in any way.
The other thing that you should keep in mind is that we create a signal envelope. And to do this, we need to make some money. What we are doing is technically known as integration - we are calculating the area under a curve and for that we need a period of integration. With Audition and Cool Edit dynamic controller we get options here to control this. And it's in the section Attack/Release to get you all the clues. First, note that it says that it is the amplitude is determined, not the rate of change, and secondly, you can determine (because it has more options than most of the compressors) how the amplitude envelope is determined in the detector - peak values, which means that the integration time is actually the same as the frequency of sampling, or RMS values. It does not say what is the RMS integration time, but dare I say that it would be too difficult to determine.
But the dynamics of hearing controller is a good example of how the software can imitate - and also to overcome the limits of the - a hardware compressor. The characteristics of the sensor and the controller can be determined separately, and look forward can also be specified. I'm not 100% convinced that reflects the output always exactly what you set, but it's close enough. But just because you can overcome how works a compressor equipment, it does not usually pay to do unless you have a very good reason to do.
Tags: Audition
Similar Questions
-
If I leave my desktop computer all the time, my computer open to attack and or infection?
I am concerned about leaving my computer all the time. If I leave all the time open the computer to attack and or infection?
Thanks for the information.
-
I have microsoft net framework SP2 2.o... and sp2... msnf3.0 and msnf3.5 sp 1... and the microsoft compression client pack 1.0 for windows... should I all of this on my computer?
See:
What is the .NET Framework, and I need all these versions?
http://ask-Leo.com/what_is_the_net_framework_and_do_i_need_all_these_versions.html -
When can we expect Windows 8, at least his version of beta and release candidate.
original title: Windows Vista and its support
When can we expect Windows 8, at least his version of beta and release candidate.
Its really unfair if Windows Vista Home Basic/Home Premum / Ultimate will be no supported from April 10, 2012 and Windows 8 is not yet released.
Of course with the release of Windows 8, Microsoft will ask to get Windows 8 and stop promoting Windows 7.
So why not get Windows 8, directly after the end of Windows Vista - of - support. I heard the final version will come on October 12, at that time customers that Windows Vista will we do. We have no option rather than getting Windows 7 or Windows Vista Business, which will be only Windows Vista available for consumers in general.
If Windows 8 Beta or RC is available at the time, not all consumers will get it.
Microsoft needs to review their plans so that consumers can make the best, its illogical to buy Windows 7 in April and then new version will be released in the coming months.
Windows Vista can get the extension until the release of WIndows 8. What I guess that happened both Windows Vista, not Windows 98 support June ' 2006, most of the consumers got new Windows XP computers and therefore din't find buy affordable Windows Vista at this time. This may be the reason why Windows Vista has suffered.
Once again, more expensive version of Windows Vista Ultimate that is for which pay us Rs 15 000 +, is the only support achievement of 5 years, rather than 10 000-12 000 companies varied is given 10 years of support.
Some politicians really need review
Hello
Windows 8 has not been released as yet to verify this information.
Connect - there is no Windows beta 8 again
http://connect.Microsoft.com/directory/Overview of Windows 8 developers
http://msdn.Microsoft.com/en-us/Windows/br229518Windows 8 News
http://Windows.Microsoft.com/en-us/Windows-8/PreviewOverview of Windows 8
http://Windows.Microsoft.com/en-GB/Windows-8/PreviewI hope this helps.
Rob Brown - Microsoft MVP<- profile="" -="" windows="" expert="" -="" consumer="" :="" bicycle=""><- mark="" twain="" said="" it="">
-
Windows Vista security alert sending indicating virus attack and does not allow me to get security alerts. How to bypass or disable? I have another anti-spyware (Kapersky) program that manages all aspects and indicates no virus found.
I want to disable Vista, but it won't let me and the only solution it says is to download a update for a cost. Help, please.
The 'alert' is not from Vista. Your computer is infected by a rogue security program. It's called "thugs" because he pretended to be a good guy but is really bad. Don't pay them!
Bleeping Computer has the removal of many variants of thieves here steps - http://www.bleepingcomputer.com/virus-removal/remove-antivirus-vista-2010
You can also check for the stages of removal at these links:Bleeping computer removal how - to - http://www.bleepingcomputer.com/forums/forum55.html
Malwarebytes malware removal guide - http://tinyurl.com/5xrpftMalwarebytes' Anti-malware (MBAM) or SuperAntiSpyware will often do the job. Both have free versions and you don't need to buy these programs.
These can work for you, and all can be good. However, in many cases the computer will also infected with other horses of Trojan and protected by a rootkit. These machines are extremely difficult to clean. If your machine is one of these cases, either the interactive assistance to one of the specialty forums listed in the link below, OR take your machine to a professional on the local computer OR backup your data and do a clean install of Windows. It's your choice. I do not recommend using BigComputerStore/GeekSquad types of places.
http://www.elephantboycomputers.com/page2.html#HJT-links MS - MVP - Elephant Boy computers - don't panic!
-
There are invisible files of > 100 GB C:\Users\B folder... \AppData\Local\Microsoft\Windows: how to remove and release this space?
Explore it has been configured to show hidden files. Files can come from files continuously from the satellite receiver via WiFi with windows media player.Windows 7 premium 64-bit, protection against viruses,... with microsoft.To study disk space, use download and install Treesize (freeware).
https://www.Jam-software.de/customers/downloadTrial.php?ARTICLE_NO=80&language=en&PHPSESSID=6odgempt76un9q9nkj7luf5be0Information about Treesize
http://www.Jam-software.com/treesize_free/
When you open Treesize scan select in the Menu and you will see a list of drives. Click on C and it will generate a list of files. Display names and 6 larger files sizes and the total at the top of the list.
-
If I run the calc script to aggregate a BSO cube, it blocks and release each block in a few seconds?
Hello
If I run the calc script to aggregate a BSO cube, it blocks and release each block in a few seconds? Or is it keep held locked blocks even after aggregation for this block is over?
For example if I correct sparse dimensions Forecast, FY15, dec. and my accounts dimension is only dense, after calc has my senior level members in the accounts, it it will issue after updating (i.e. in fractions of seconds) or is agg keep it held in a lock?
I ask because I want to run scripts tot., but there is the update of our cube users. I never had a problem to start agg, while users are updating. But maybe I am lucky. If a user updates a closed block, they will receive an error message that I think. They may try to update again after a few seconds, I hope.
Thank you.
Locking behavior for BSO Essbase is described in the database administrator's Guide: http://docs.oracle.com/cd/E57185_01/epm.1112/essbase_db/dstinteg.html
It is certainly theoretically possible that a user can obtain a lock because of a calc, although I can't say I saw him be a problem in real-world applications (perhaps because access uncommitted is the default).
-
When you use the pen tool when I click and create an anchor point and release the mouse button the pen tool emerges from the anchor and allow me to go and select a new anchor point. The right pen tool keeps adding lines that I move the mouse. How can I get the pen tool to release the anchor
Try this.go in the menus. Select cc illustrator > preferences > display selection & anchor > then make sure the box "activate the rubber band for" the pen tool is not selected. Then press OK. It should work.
-
Adobe Folio billing and releases of Apple
I am currently unemployed and looking to change my background in the creation of freelance publications annual reports, etc. - for the non-profit sector here in the United Kingdom.
Being short of money I am considering investments in the annual Adobe Cloud subscription (including editing simple user DPS, with creations unlimited app?) which is currently testing and soon to expire.
I tested the workflow of the designs and happy with the results so far. I feel a workflow perspective that I can move forward in this area of development. However I have a few questions, I would be grateful for entries with.
One
I'm confused about Folios and billing issues. I read reports that Adobe free Folio downloads and I'm sure I read this out of context, but that it wishes to receive clarification. If I create a showcase App, show what is possible in DPS, promotion bonus publication to e-devices and demonstrate my creativity, I hope to be able to attract some potential work. I want to do a marketing campaign on my service and invite interested parties to download the App to showcase.
In creating this binary application for the apple store in DPS, I just assume it's the end of the participation of the Adobes in this process? I would not that surprises, if there was a good acceptance of freedom download from the app store and receive an invoice from Adobe.
I would be grateful if someone could clarify this point.
Two
My second question relates to the Apple. I am aware that it is a forum for Adobe, but I would assess the knowledge of users and experiences from apple on this point. Which relates to the policy of apples and releases. I start to become wary about apple rejecting apps and are unwilling to invest to see rejected. I am also aware that it will be difficult to answer to this question since one saw the publication, so I don't rely on the experiences of users and knowledge of the procedure.
Does anyone know of a contact email where I can contact apple and ask for clarification on the specific approval process. What is likely to get a rejection, and what is the pro - forma they check, just so that it's not a secret to me. If anyone has the url to guidelines, I would be grateful, that I have a developer account registered app so happy for contact by e-mail and open to suggestions.
I noticed that the House already has an app in the app store called Adobe & DTS in the title of the company, which has been approved. The intention is that my application is similar modelled on the application Adobe and DTS, except my own storefront and be a unique app promotion available for free without a subscription. However, I would like to somehow capture the Subscriber information so that I can stay in touch with interested parties.
I am grateful for the readers with this one, I really want to do my research and not to surprising obstacles if I finish the purchase of the subscription for one year, which I won't be able to return once committed.
With best wishes,
Michael Beaumont
London - United Kingdom
1. single Edition is turned off. It is the entire folio group within an application
and that's all. You are proposing is that Apple and Adobe is done with you. The
I like to use the analogy is simple editing is like a hard cover book, while
multi-Folio apps are like three ring binders.
2. when it comes with Apple, you take the good with the bad. There is none
way to 100% sure your application is accepted, but you must ensure
have a lot of interactivity to minimize the risk of rejection.
Bob
-
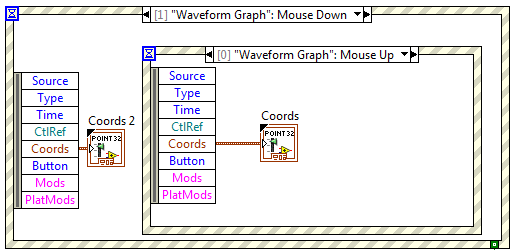
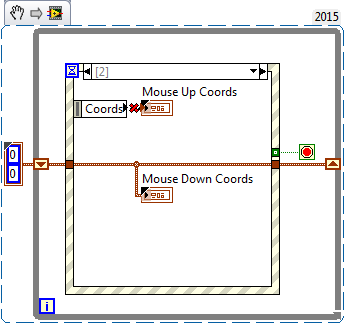
Press and release the mouse coordinates
Hello, I am currently working on a frequency counter with simple sound recorder. I want to implement by selecting a fragment of recorded waveform by dragging pressed the mouse over it. I did a VI that would do, but it requires the mouse down and coordinates the mouse upwards. So far I have only came to the top with a double event Structure as in the attached screenshot (outter structure has enabled the front panel) and well, it works, but when one of the conditions is not met (i.e. mouse has been pressed on the inside and then released outside the area of the graph of a waveform or vice versa) the façade will freeze I believe that there must be a more elegant solution. Any ideas how can I make infallible?
You don't want to put event inside the other two structures... technically it might work if configure you event not to lock the Panel and you do an event of compensation, but this isn't the easiest way in the end. You'll find yourself with a queue of mouse events inside and it would be a mouse event instantly each time after you click once on the structure.
Create two tests in the exterior structure of the event, and then use a cluster of data to store information you need from the mouse to the bottom of the event. Then, in mice an event handle drag and drop contact information accordingly.
You end up with something like this:
Ignore the cut wire, it's just something in the way that LabVIEW exports the code snippet. The mouse down event happening just the contact information for the DataSet.
-
I discovered that when I export-> release build, I have signed bar file - good, but when I manually deploy on Playbook he won't start. Apparently, the problem is that arguments need Qt app '-blackberry platform ' runs correctly. When I packed up and sign the same command-line application using blackberry-nativepackager with arg-blackberry - arg platform I could start this signed request the Playbook.
So, questions:
(1) when I build device-Relase and once run from NDK it is pushed to the Playbook and stays there. I can easily then click the icon to start the application. How the application knows everything - blackberry platform (which I said when I ran the project in the "Arguments" section.
((2) why 1) does not happen with signed app?
(3) what/where should we indicate in NDK to export-> release Qt application?
Thank you
Evgeny.
PS: also the same question on env variable LD_LIBRARY_PATH - how is it implemented when the application is running? the same for all applications or there is a possibility to change this var?
In all cases, the '-blackberry platform "part goes in the MANIFESTO. MF file in the context of the invocation of the main executable.
The problem with the export Release Wizard, is that you have to tell him to pass these arguments along at the Packer in a certain way.
You can do it on the last page of the wizard in the settings of packaging-> Advanced tab using «- arg - arg - blackberry platform»
-
Resolution - difference between Dev Alpha and released screen device
Hi guys
I read on one blog that the Alpha of Dev and the real device which will be released at the end of January should have different screen resolutions. (1,280 x 768, 1,280 x 720)
You know nothing about it?
Thank you guys. In the meantime, I got a link to blog useful Kamel Lajili (@KLajili) - http://devblog.blackberry.com/2012/08/blackberry-10-screen-resolutions/
-
SIP spam attack and MCU and vcs - e call
as far as I know sip call spam attacks is done against the videoconference, connected with a public ip address, I disabled the sip but im not sure if my mcu and vcs - e with sound are vulnerable to them? they pose no threat to security for them? and if so, how? and what can we do about it?
It is a well known problem and it affects H.323 and SIP, take a look at the below threads:
https://supportforums.Cisco.com/discussion/12340591/nuisance-h323-calls-SX20
https://supportforums.Cisco.com/discussion/12336591/sourceh323idcisco-incomingcalls
https://supportforums.Cisco.com/discussion/12508641/Cisco-source-spam-calls-stepped-complexity
https://supportforums.Cisco.com/discussion/12613681/attack-vcse
There are many more discussions on this issue, the above, this is just a small selection. :)
You do not need to disable SIP on the VCS-E, all you need to do is turn SIP UDP unless you need it for voice services.
You can protect yourself by using a CPL on the VCS-E who will avoid calls to go through your MCU, or anything else you have sitting behind the VCS-E. This is assuming that you are using a combo of VCS-C/VCS-E, with the VCS - C behind a firewall and the VCS-E outside the firewall, for example in the demilitarized zone.
Having just trouble ask points of termination or MCU sitting in nature with public IP addresses.
These scans, moreover, mainly looking for systems that will allow them to make free international calls.
/Jens
Please evaluate the answers and makr as 'answered' questions as appropriate.
-
Licenses and releasing a derivative under creative commons license
Hello
I hope someone can help me with this,
We have a standard license for Club Photo Dollar images.With the standard or extended licensing, derivative works, we create can be released under a license creative commons share the same ?
If this isn't the case, under what license do we need to release them, and what are the conditions of it?Thank you
Hi Scott,.
There is no license that will allow this type of use. You can view license standard for Dollar Club of Photo at this link: Dollar Club Photo - photo galleries free high quality royalty and vectors - Club picture Dollar
Kind regards
Mat Hayward
-
Month 20141 Dreamweaver and released 2014.1.1?
Months were released 20141 and 2014.1.1 Dreamweaver?
Hello
Please see the link below which has all versions of Dreamweaver release dates.
https://helpx.Adobe.com/Dreamweaver/Dreamweaver-releasenotes.html
Concerning
Vivek
Maybe you are looking for
-
iMac Photo app smart album settings files: stored in this directory?
Nobody knows... On the iMac, in which directory is 'photo app Smart Album settings files' stored? I am running OS X El Capitan, version 10.11.4
-
http://imgur.com/av4aa.PNG On the left is FF 4 b 5, with a slightly blurry text on Lifehacker. On the right is Chrome 6.0.472.59 beta, without the blurry text. I must emphasize that the fuzzy text was not a problem in FF 4 b 4 or an earlier version.
-
Why safari quit/crash when I select the address bar?
Whenever I select the address bar type in an address, once I run Safari, the application closes automatically.
-
Mail software by default continuous change Parallels shared Internet Applications tool
My default mail software continues to reset to Parallels Shared Internet Applications tool even if I have not installed more than Parallels. Is there anything else that might be given to zero this?
-
I can't connect to the e-mail account on my other computer, keeps saying my mapi or outlook express, do not set up