Statements of NAT
We have a new ASA 5510. We are not sure of the basic configurations. We want to use the ASA as a firewall and VPN. For VPN, we go to the configuration for VPN client group policies. There is a router between the ASA and internal networks. Here is the basic configuration. Do you see something wrong? Is there something else that we need the facility regarding the routing?
1. the external IP address is 66.102.7.17, netmask 255.255.255.248 gateway 66.102.7.22. Is that what we would go into the outside interface?
interface Ethernet0/0
nameif outside
security-level 0
IP 66.102.7.17 255.255.255.0
2. we want NAT IP address private to each public IP address. Public IP addresses are 209.145.25.1 - 209.145.25.62, subnet mask 255.255.255.192. Here are the correct declarations of NAT?
static (inside, outside) 209.145.25.1 192.168.100.1 netmask 255.255.255.255
static (inside, outside) 209.145.25.2 192.168.100.2 netmask 255.255.255.255
static (inside, outside) 209.145.25.3 192.168.100.3 netmask 255.255.255.255
static (inside, outside) 209.145.25.4 192.168.100.4 netmask 255.255.255.255
static (inside, outside) 209.145.25.5 192.168.100.5 netmask 255.255.255.255
3. This is the instruction to the road outside. Is it correct? The 66.102.7.22 IP address is the default gateway of 66.102.7.17, which is the external interface of the ASA
Route outside 0.0.0.0 0.0.0.0 66.102.7.22 1
3. given that the external of the ASA interface and public IP addresses are on different networks, we need another statement of course?
Thank you.
Diane
Diane,
Everything is OK with these exceptions:
1. change the mask
interface e0/0
no ip add
IP 66.102.7.17 255.255.255.248
2. as public IP addresses are on a different subnet of the IP outside the ASA, you must ensure that the ISP knows how to send
the ASA traffic intended for these IPs.
Hoping to help.
Federico.
Tags: Cisco Security
Similar Questions
-
statements of nat on my PIX 520
I have the following two statements on the config of my PIX 520:
NAT (inside) - 0 100 access list
NAT (inside) 1 0.0.0.0 0.0.0.0 0 0
I understand that my predecessor built our Access-list 100 as tunnels for our VPN to our customers. But I don't know what is the purpose of the 2nd NAT.
Pls help...
Education of a nat 0 specifies addresses that will not be translated.
The nat statement 1 by 0 all indicates that any address will lead to a global address. (with the exception of nat 0)
Access-list 100 should be your networking source and destination for the vpn.
-
Several statement list Access NAT (DMZ) 0
Hello
IM I have problems with remote VPN. The scenario is as follows:
I have I have few clients who will connect remotely via VPN. Until today, one of them needed to enter my DMZ. But now I want a different profile (the cause is a new client) to access one of my server in the DMZ.
So I said all of the VPN, the ACL settings, but when I want to declare the nat 2 access-list newclient (dmz) it does not work. But if I declare the nat 0 access-list newclient (dmz), it works, BUT it removes the previous 0 having my other client nat. Is there a way to create several access list statement 0 - nat (dmz)?. If this is not the case, how could I solve this problem?
This is my config:
vpnashi list extended access allowed host ip 192.168.16.28 192.168.125.0 255.255.255.0
access extensive list ip 192.168.125.0 vpnashi allow 255.255.255.0 host 192.168.16.28
vpnlati list extended access allowed host ip 192.168.16.50 192.168.125.0 255.255.255.0
access extensive list ip 192.168.125.0 vpnlati allow 255.255.255.0 host 192.168.16.50
IP local pool ippool 192.168.125.10 - 192.168.125.254Global 1 interface (outside)Global 2 200.32.97.254 (outside)NAT (outside) 1 192.168.125.0 255.255.255.0NAT (inside) 0-list of access vpnasNAT (inside) 2 access list ACL-NAT-LIMNAT (inside) 3 access-list vpnwipNAT (inside) 4 access-list vpnashiNAT (inside) 5-list of access vpnlatiNAT (inside) 1 0.0.0.0 0.0.0.0NAT (wifi) 2 0.0.0.0 0.0.0.0NAT (dmz) 0-list of access vpnashiNAT (dmz) 1 192.168.16.0 255.255.255.0NAT (dmz) 2 access-list vpnlatiinternal group RA-ASHI strategyattributes of RA-ASHI-group policyServer DNS 172.16.1.100 valueVPN-idle-timeout 30VPN-filter value vpnashiProtocol-tunnel-VPN IPSec l2tp ipsec webvpnSplit-tunnel-policy tunnelspecifiedinternal strategy of RA-LATI groupattributes of RA-LATI-group policyServer DNS 172.16.1.100 valueVPN-idle-timeout 30VPN-filter value vpnlatiProtocol-tunnel-VPN IPSec l2tp ipsec webvpnSplit-tunnel-policy tunnelspecifiedtunnel-group RA-ASHI type remote accesstunnel-group RA-ASHI-global attributesippool address poolauthentication-server-group (outside partnerauth)Group Policy - by default-RA-ASHItunnel-group RA-ASHI ipsec-attributespre-shared-key *.tunnel-group RA-LVL type remote accesstunnel-group RA-LATI-global attributesippool address poolauthentication-server-group (outside partnerauth)Group Policy - by default-RA-LATItunnel-group RA-LATI ipsec-attributespre-shared-key *.André,
You can have as a NAT exempt list of access by interface (nat rule 0). I understand what you are trying to accomplish. You use the vpnashi and vpnlati access list to control access to devices for different customers through VPN group policies.
What I do is the following:
Create an ACL for the VPN client (that you have, with vpnashi and vpnlati)
Create an ACL for NAT exemption for the interface (inside sheep, sheep-dmz, etc.).Create the ACEs within the exempt ACL of NAT that corresponds to your VPN client access-list.
It is allowed to have multiple statements within a NAT exempt list to access. This will not have a client VPN access to things, it shouldn't.
For example:
access-list sheep-dmz allowed extended host ip 192.168.16.28 192.168.125.0 255.255.255.0
192.168.125.0 IP Access-list extended dmz sheep 255.255.255.0 allow host 192.168.16.28
NAT 0 access-list sheep-dmz (dmz)
-
Split of static traffic between the VPN and NAT
Hi all
We have a VPN from Site to Site that secures all traffic to and from 10.160.8.0/24 to/from 10.0.0.0/8. It's for everything - including Internet traffic. However, there is one exception (of course)...
The part that I can't make it work is if traffic comes from the VPN (10.0.0.0/8) of 10.160.8.5 (on 80 or 443), then the return traffic must go back through the VPN. BUT, if traffic 80 or 443 comes from anywhere else (Internet via X.X.X.X which translates to 10.160.8.5), so there need to be translated réécrirait Internet via Gig2.
I have the following Setup (tried to have just the neccessarry lines)...
interface GigabitEthernet2
address IP Y.Y.Y.Y 255.255.255.0! the X.X.X.X and Y.Y.Y.Y are in the same subnet
address IP X.X.X.X 255.255.255.0 secondary
NAT outside IP
card crypto ipsec-map-S2S
interface GigabitEthernet4.2020
Description 2020
encapsulation dot1Q 2020
IP 10.160.8.1 255.255.255.0
IP nat inside
IP virtual-reassembly
IP nat inside source list interface NAT-output GigabitEthernet2 overload
IP nat inside source static tcp 10.160.8.5 80 80 X.X.X.X map route No. - NAT extensible
IP nat inside source static tcp 10.160.8.5 443 443 X.X.X.X map route No. - NAT extensible
NAT-outgoing extended IP access list
refuse 10.160.8.5 tcp host 10.0.0.0 0.0.0.255 eq www
refuse 10.160.8.5 tcp host 10.0.0.0 0.0.0.255 eq 443
permit tcp host 10.160.8.5 all eq www
permit tcp host 10.160.8.5 any eq 443
No. - NAT extended IP access list
refuse 10.160.8.5 tcp host 10.0.0.0 0.0.0.255 eq www
refuse 10.160.8.5 tcp host 10.0.0.0 0.0.0.255 eq 443
allow an ip
route No. - NAT allowed 10 map
corresponds to the IP no. - NAT
With the above configuration, we can get to the Internet 10.160.8.5, but cannot cross it over the VPN tunnel (from 10.200.0.0/16). If I remove the two commands «ip nat inside source static...» ', then the opposite that happens - I can get then to 10.160.8.5 it VPN tunnel but I now can't get to it from the Internet.
How can I get both? It seems that when I hit the first NAT instruction (overload Gig2) that 'decline' in the list of ACL-NAT-outgoing punts me out of this statement of NAT. It can process the following statement of NAT (one of the 'ip nat inside source static... ") but does not seem to"deny"it in the NON - NAT ACL me punt out of this statement of NAT. That's my theory anyway (maybe something is happening?)
If this work like that or I understand something correctly? It's on a router Cisco's Cloud Services (CSR 1000v).
Thank you!
Your netmask is bad for your 10.0.0.0/8. I worry not about the port/protocol or since that can screw you up. A better way to do it would be to deny all IP vpn traffic.
NAT-outgoing extended IP access list
deny ip 10.160.8.0 0.0.0.0.255 10.0.0.0 0.255.255.255
...
No. - NAT extended IP access list
deny ip 10.160.8.0 0.0.0.0.255 10.0.0.0 0.255.255.255
allow an ip
Doc:
Router to router IPSec with NAT and Cisco Secure VPN Client overload
Thank you
Brendan
-
I have a Nat problem that is confounding me.
Today, in our lab, I have a video server that is on the subnet 10.16. 42.91/26
This subnet is managed by a L3 with L3 routing switch to the rest of the network.
I need this test server on a WAN access emulated to validate the performance of the Executive Office.
The WAn emulator is all set up and works fine
Now I would like to extend this slow acess outside the laboratory, so that everyone can test the slow lane of their office.
Do this, I added a 2nd router between subnet of video server and the rest of the network
I want to NAT the 10.16.42.91 address to 10.16. .91 44,
Such as... anyone 10.16.44.91 SEO through the slow lane, and anyone using 10.16.42.91 through the GigE
The NAting router is a 881 running 15.3
Should be hide nat return traffic would be routed through the NAT router
I tried several nat configs, but remain confused.
Diagram below... Would appreciate any suggestions
Thanks in advance

Wes
You need two things-
(1) for the return shipping back to the 881 you need for NAT overload all users IPS to the 10.16.42.x on the 881 interface IP. You have the Interior facing users that makes it a lot easier if-
access-list 101 permit ip 10.0.0.0 0.0.0.255 host 10.16.44.91
IP nat inside source list 101 interface overload<- where="" is="" the="" one="" facing="" the="">
Note that I'm not entirely sure the exact order of treatment regarding two statements of NAT, so in the acl above where you have the 10.16.44.91 host, you might need to change it to the real server IP. Try the above first.
(2) a NAT for server-
source 10.16.42.91 IP NAT outside static 10.16.44.91 netmask 255.255.255.255
Edit - I'm assuing you have already assigned 'ip nat inside' to the interface on the 881 to users and the 'ip nat outside' on the interface to the server.
Jon
-
Hello
I just want to understand this syntaxs. How is it from outside to outside outside the demilitarized zone?
NAT (outside, DMZ1) static source everything any destination FW11_NAT one-way static obj-server1
NAT (outside, outside) static source DM_INLINE_NETWORK_34 DM_INLINE_NETWORK_34 DM_INLINE_NETWORK_90 DM_INLINE_NETWORK_90 non-proxy-arp-search of route static destination
Hello Tahir,
The first statement of nat is used to allow any user to the source (outside) translates to himself (nat exemption) while the destination (on dmz) is translated from server1-obj in FW11_NAT.
The second statement of nat is a declaration of exemption nat to allow of translates auto to himself so that the destination is dm_inline_network_90 (also on the outside interface) translates both traffic (coming soon on the external interface) DM_INLINE_NETWORK_34.The second nat is used when you want to allow traffic to a counterpart of VPN tunnel to connect to one another homologue of VPN tunnel traffic, allowing the user to communicate with another user VPN VPN tunnel gold peers/SSL SSL VPN.
I hope this helps.
Kind regards
Dinesh MoudgilPS Please rate helpful messages.
-
For statement: isakmp nat - t
What is it, or in what circumstances, should it be used?
Thank you for helping.
Scott
the command "isakmp nat-traversal" should be applied to the vpn server when the vpn client is behind a nat/pat device.
the reason being nat/pat on the client side will result in the ip original source to the IP (public) own peripheral nat/pat. When the vpn server receives, decrypts, and analysis package, it's going to come back with a mistake as the original source ip does not correspond to the
for example
Remote vpn client implements a remote vpn router and the client remote vpn is behind a nat/pat device, such as a router or pix.
-
NAT subnet in the network object group
Can someone help me please? I'm rusty with VPN and Natting.
Scenario: I need to share my internal-tunnel network. Traffic to 192.168.88.0/24 192.168.0.0/24 NAT when establishing a VPN connection for the objects that I defined in one group of objects specific network (Group1Servers). Internet traffic does not get this NAT 88, even by default.
ASA5506-X, 7.5 ASDM, ASA 9.5
Hello
You can configure a static strategy of nat to translate 192.168.0.0/24 to 192.168.88.0/24 when the destination is Group1Servers, the CLI command:
Create objects for 192.168.0.0/24 and 192.168.88.0/24
network object obj - 192.168.0.0
192.168.0.0 subnet 255.255.255.0network object obj - 192.168.88.0
192.168.88.0 subnet 255.255.255.0Statement by NAT:
NAT obj destination - source (indoor, outdoor) 192.168.88.0 obj - 192.168.0.0 static static Group1Servers Group1Servers
You can view this documentation to setup NAT:
https://supportforums.Cisco.com/document/33921/ASA-pre-83-83-NAT-CONFIGU...
Given that this traffic goes through a tunnel of site to site do not forget interesting traffic must be configured with the translated '192.168.88.0/24' not the real network, which is a common error just keep in mind
Best regards, please rate.
-
Hello
I'm new to configurations of ASA and who need help with Setup on an execution code 8.6 X 5555. I need allow network several ip address ranges from my inside several subnets outside the network so that external systems only see traffic entering an ip address and may not be the ip address of the external interface. I was able to do this with a box and statements IOS nat-based firewall but difficult to do the same in the bones of the ASA.
Hello
Sound is fairly simple and fast, for your condition, you should use.
Information on PAT Dynamics
Dynamic PAT translates multiple real addresses to a single IP address mapped by translating the port real, address and source, the mapped address and a unique port. If necessary, the actual source port number is used for the mapped port. However, if the actual port is not available, by default mapped ports are selected in the same range of ports than the real port number: 0 to 511, 512 to 1023 and 1024 to 65535. Therefore, ports below 1024 have only a small PAT pool that can be used. (8.4 (3) and later, not including 8.5 (1) or 8.6 (1)) If you have a lot of traffic that uses the lower ranges of port, you can now specify a flat range of ports to use instead of the three levels of unequal size.
Each connection requires a separate translation session because the source port is different for each connection. For example, 10.1.1.1:1025 requires a separate 10.1.1.1:1026 translation.
Figure 27-10 illustrates a typical scenario of PAT dynamic. Only real hosts can create a session of NAT, who answered the questionnaire of traffic is allowed to return. The mapped address is the same for each translation, but the port is assigned dynamically.
Figure 27-10 dynamic PAT
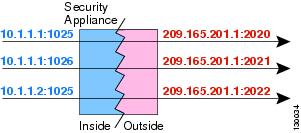
After the expiry of the connection port forwarding expires after 30 seconds of inactivity. The timeout is not configurable. The destination network users may not reliably initiate a connection to a host that uses PAT (even if the connection is allowed by an access rule).
Understanding of NAT
Let me know if you need help on this, you can do PAT with additional IP addresses that are available on outside interface. You must have appropriate for the additional ip address routing
HTH
Sandy. -
Hi all
How can I get NAT my internal to the range of IP addresses different before reaching destination LAN network
Hello
No, you no longer have need of NAT0 and actully, it is mandatory to remove it as NAT0 prevails over the other statements of NAT.
You should translate all subnet to a single IP address in NAT rules-based help
NAT (inside) 10-list of access VPN - NAT
overall 10 172.16.20.1 (outside)
access VPN - NAT ip 192.168.10.0 list allow 255.255.255.255 192.50.100.32 255.255.255.240
The card crypto access list:
host ip 172.16.20.1 allowed VPN access list 192.50.100.32 255.255.255.240
To check the NAT:
SH xlate
To test the complete configuration use the command "packet - trace", which generates a bunch of fake with the features you want and spends the entire process internal SAA and shows you the result.
Please rate if this helped.
Kind regards
Daniel
-
NAT VPN tunnel and still access Internet traffic
Hello
Thank you in advance for any help you can provide.
I have a server with the IP 192.168.1.9 that needs to access a subnet remote from 192.168.50.0/24, through the Internet. However, before the server can access the remote subnet, the server IP must be NAT'ed to 10.1.0.1 because the VPN gateway remote (which is not under my control) allows access to other customers who have the same subnet address that we do on our local network.
We have a 2801 Cisco (running c2801-advsecurityk9 - mz.124 - 15.T9.bin) set up to make the NAT. It is the only gateway on our network.
I have configured the Cisco 2801 with the following statements of NAT and the relevant access lists:
access-list 106 allow host ip 192.168.1.9 192.168.50.0 0.0.0.255
NAT extended IP access list
refuse the host ip 192.168.1.9 192.168.50.0 0.0.0.255
deny ip 192.168.1.0 0.0.0.255 192.168.3.0 0.0.0.255
ip permit 192.168.1.0 0.0.0.255 anyroute allowed ISP 10 map
corresponds to the IP NATIP nat EMDVPN 10.1.0.1 pool 10.1.0.1 netmask 255.255.255.0
IP nat inside source list 106 pool EMDVPN
IP nat inside source map route ISP interface FastEthernet0/1 overloadWhen the server (192.168.1.9) attempts to ping on the subnet of 192.168.50.0/24 devices, the VPN tunnel is established successfully. However, after that, the server is no longer able to access the Internet because the NAT translation for 192.168.1.9 has changed since the external IP address of the router (FastEthernet0/1) at 10.1.0.1.
The documentation I've seen on the site of Cisco says that this type of Setup allows only host subnet communication. Internet access is not possible. However, maybe I missed something, or one of you experts can help me. Is it possible to configure the NAT router traffic destined to the VPN tunnel and still access the Internet by using the dynamic NAT on FastEthernet0/1?
Once again, thank you for any help you can give.
Alex
Hello
Rather than use a pool for NAT
192.168.1.9 - 10.1.0.1 > 192.168.50.x
ACL 102 permit ip 192.168.1.9 host 192.168.50.0 0.0.0.255
RM-STATIC-NAT route map permit 10
corresponds to the IP 102IP nat inside source static 192.168.1.9 10.1.0.1 card expandable RM-STATIC-NAT route
ACL 101 deny host ip 192.168.1.9 192.168.50.0 0.0.0.255
ACL 101 by ip 192.168.1.0 0.0.0.255 any
overload of IP nat inside source list 101 interface FastEthernet0/1VPN access list will use the source as 10.1.0.1... *.
Let me know if it works.
Concerning
M
-
RA VPN VPN L2L via NAT strategy
Scenario: we have remote access VPN users who need to access a VPN L2L by ASA even outside the interface. This particular VPN L2L is a partner that requires us to NAT (192.168.x.x) addresses to another private address (172.20.x.x). We also access VPN L2L to internal hosts. NATing to the partner is accomplished through a NAT policy.
Our remote VPN users cannot access the L2L VPN. It seems that the host address VPN (assigned through RADIUS) is not in THAT NAT would not, even if it is in the range object.
"Group" is configured and works for the other VPN.
NO - NAT ACL does not seem to be involved (which it shouldn't), as the address of the internal host (192.168.60.x) is not NAT to be the public address.
Internal hosts that can access the VPN tunnel very well.
Here are the relevant config:
permit same-security-traffic intra-interface
the OURHosts object-group network
host 192.168.1.x network-object
host 192.168.2.x network-object
object-network 192.168.60.0 255.255.255.0
the PartnerHosts object-group network
network-host 10.2.32.a object
network-host 10.2.32.b object
network-host 10.2.32.c object
access-list extended NAT2 allowed ip object-group OURHosts-group of objects PartnerHosts
Global (OUTSIDE) 2 172.20.x.x
NAT (INSIDE) 2-list of access NAT2
The syslog error we receive:
% ASA-4-402117: IPSEC: received a package not IPSec (Protocol = ICMP) 10.2.32.a to 192.168.60.x
Yes. According to the config that you posted, there is no command currently in no place in vpn nat clients the RA to the hairpin above the tunnel.
The inside of our customers work due to "nat (INSIDE) 2 NAT2 access-list. But because your VPN RA customers coming from "OUTSIDE", this statement by nat would have no effect on them.
-
Remote access ASA, VPN and NAT
Hello
I try to get access to remote VPN work using a Cisco VPN client and ASA with no split tunneling. The VPN works a little, I can access devices inside when I connect, but I can't access the Internet. I don't see any errors in the log ASA except these:
1 Jul 04:59:15 % ASA-3-305006 gatekeeper: failed to create translation portmap for udp src outside:192.168.47.200/137 dst outside:192.168.47.255/137
1 Jul 04:59:15 % ASA-3-305006 gatekeeper: failed to create translation portmap for udp src outside:192.168.47.200/54918 dst outsidexx.xxx.xxx.xxx/53There is only one address public IP that is assigned to the external interface of DHCP. The Interior is 192.168.1.0/24 network which is PAT'ed to the external interface and the VPN network is 192.168.47.X.
I think my problem is that the net.47 is not NAT'ed out properly and I don't know how to put in place exactly. I can't understand how this is supposed to work since the net VPN technically provenance from the outside already.
Here are all the relevant config:
list of vpn access extended permits all ip 192.168.47.0 255.255.255.0
Within 1500 MTU
Outside 1500 MTU
IP local pool vpnpool 192.168.47.200 - 192.168.47.220 mask 255.255.255.0
IP verify reverse path to the outside interface
IP audit info alarm drop action
IP audit attack alarm drop action
ICMP unreachable rate-limit 1 burst-size 1
ICMP allow all outside
Global interface (2 inside)
Global 1 interface (outside)
NAT (inside) 0-list of access vpn
NAT (inside) 1 0.0.0.0 0.0.0.0
NAT (outside) 2 192.168.47.0 255.255.255.0 outside
static (inside, outside) tcp 3074 XBOX360 3074 netmask 255.255.255.255 interface
static (inside, outside) udp 3074 XBOX360 3074 netmask 255.255.255.255 interface
public static (inside, outside) udp interface 88 88 XBOX360 netmask 255.255.255.255
public static tcp (indoor, outdoor) https someids netmask 255.255.255.255 https interfaceI can post more of the configuration if necessary.
Change ' nat (outside) 2 192.168.47.0 255.255.255.0 apart ' "NAT (2-list of vpn access outdoors outside)" gives these:
1 Jul 06:18:35 % gatekeeper ASA-3-305005: no group of translation not found for udp src outside:192.168.47.200/56003 dst outside:66.174.95.44/53
So, how I do right NAT VPN traffic so it can access the Internet?
A few things that needs to be changed:
(1) NAT exemption what ACL must be modified to be more specific while the traffic between the internal subnets and subnet pool vpn is not coordinated. NAT exemption takes precedence over all other statements of NAT, so your internet traffic from the vpn does not work.
This ACL:
list of vpn access extended permits all ip 192.168.47.0 255.255.255.0
Should be changed to:
extensive list of access vpn ip 192.168.47.0 255.255.255.0 allow
(2) you don't need statement "overall (inside) 2. Here's what to be configured:
no nat (outside) 2 192.168.47.0 255.255.255.0 outside
no global interface (2 inside)
NAT (outside) 1 192.168.47.0 255.255.255.0
(3) and finally, you must activate the following allow traffic back on the external interface:
permit same-security-traffic intra-interface
And don't forget to clear xlate after the changes described above and connect to your VPN.
Hope that helps.
-
On the Question of VPN S2S source NAT
Currently we have a number of implementation of VPN with various clients. We are NAT'ing range them at a 24 in our network to keep simple routing, but we seek to NAT Source our resources due to security problems. It is an example of a current virtual private network that we have configured:
outside_map crypto card 5 corresponds to the address SAMPLE_cryptomap
outside_map 5 peer set 99.99.99.99 crypto card
card crypto outside_map 5 set ikev1 transform-set ESP-3DES-MD5 SHA-ESP-3DES
card crypto outside_map 5 the value reverse-road
SAMPLE_cryptomap list extended access permitted ip object-group APP_CLIENT_Hosts-group of objects CLIENT_Hosts
NAT (inside, outside) static source APP_CLIENT_Hosts APP_CLIENT_Hosts CLIENT_Host_1_NAT CLIENT_Host_1 non-proxy-arp-search of route static destination
NAT (inside, outside) static source APP_CLIENT_Hosts APP_CLIENT_Hosts CLIENT_Host_2_NAT CLIENT_Host_2 non-proxy-arp-search of route static destination
NAT (inside, outside) static source APP_CLIENT_Hosts APP_CLIENT_Hosts CLIENT_Host_3_NAT CLIENT_Host_3 non-proxy-arp-search of route static destination
the APP_CLIENT_Hosts object-group network
network-object, object SITE1_APP_JCAPS_Dev_VIP
network-object, object SITE1_APP_JCAPS_Prod_VIP
network-object, object SITE2_APP_JCAPS_Dev_Host
network-object, object SITE2_APP_JCAPS_Prod_VIP
network-object, object SITE1_APP_PACS_Primary
network of the SITE1_APP_JCAPS_Dev_VIP object
Home 10.200.125.32
network of the SITE1_APP_JCAPS_Prod_VIP object
Home 10.200.120.32
network of the SITE2_APP_JCAPS_Dev_Host object
Home 10.30.15.30
network of the SITE2_APP_JCAPS_Prod_VIP object
Home 10.30.10.32
network of the SITE1_APP_PACS_Primary object
Home 10.200.10.75
network of the CLIENT_Host_1 object
host of the object-Network 192.168.15.100
network of the CLIENT_Host_2 object
host of the object-Network 192.168.15.130
network of the CLIENT_Host_3 object
host of the object-Network 192.168.15.15
network of the CLIENT_Host_1_NAT object
host of the object-Network 10.200.192.31
network of the CLIENT_Host_2_NAT object
host of the object-Network 10.200.192.32
network of the CLIENT_Host_3_NAT object
host of the object-Network 10.200.192.33
My question revolves around the Source NAT configuration. If I understand correctly, I have to configure 3 statements of NAT per NAT Source since there are three different destinations that are NAT' ed. I think I would need to add this:
network of the SITE1_APP_JCAPS_Dev_VIP_NAT object
Home 88.88.88.81
network of the SITE1_APP_JCAPS_Prod_VIP_NAT object
Home 88.88.88.82
network of the SITE2_APP_JCAPS_Dev_Host_NAT object
Home 88.88.88.83
network of the SITE2_APP_JCAPS_Prod_VIP_NAT object
Home 88.88.88.84
network of the SITE1_APP_PACS_Primary_NAT object
Home 88.88.88.85
NAT (inside, outside) static source SITE1_APP_JCAPS_Dev_VIP SITE1_APP_JCAPS_Dev_VIP_NAT CLIENT_Host_1_NAT CLIENT_Host_1 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE1_APP_JCAPS_Dev_VIP SITE1_APP_JCAPS_Dev_VIP_NAT CLIENT_Host_2_NAT CLIENT_Host_2 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE1_APP_JCAPS_Dev_VIP SITE1_APP_JCAPS_Dev_VIP_NAT CLIENT_Host_3_NAT CLIENT_Host_3 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE1_APP_JCAPS_Prod_VIP SITE1_APP_JCAPS_Prod_VIP_NAT CLIENT_Host_1_NAT CLIENT_Host_1 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE1_APP_JCAPS_Prod_VIP SITE1_APP_JCAPS_Prod_VIP_NAT CLIENT_Host_2_NAT CLIENT_Host_2 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE1_APP_JCAPS_Prod_VIP SITE1_APP_JCAPS_Prod_VIP_NAT CLIENT_Host_3_NAT CLIENT_Host_3 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE2_APP_JCAPS_Dev_Host SITE2_APP_JCAPS_Dev_Host_NAT CLIENT_Host_1_NAT CLIENT_Host_1 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE2_APP_JCAPS_Dev_Host SITE2_APP_JCAPS_Dev_Host_NAT CLIENT_Host_2_NAT CLIENT_Host_2 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE2_APP_JCAPS_Dev_Host SITE2_APP_JCAPS_Dev_Host_NAT CLIENT_Host_3_NAT CLIENT_Host_3 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE2_APP_JCAPS_Prod_VIP SITE2_APP_JCAPS_Prod_VIP_NAT CLIENT_Host_1_NAT CLIENT_Host_1 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE2_APP_JCAPS_Prod_VIP SITE2_APP_JCAPS_Prod_VIP_NAT CLIENT_Host_2_NAT CLIENT_Host_2 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE2_APP_JCAPS_Prod_VIP SITE2_APP_JCAPS_Prod_VIP_NAT CLIENT_Host_3_NAT CLIENT_Host_3 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE1_APP_PACS_Primary SITE1_APP_PACS_Primary_NAT CLIENT_Host_1_NAT CLIENT_Host_1 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE1_APP_PACS_Primary SITE1_APP_PACS_Primary_NAT CLIENT_Host_2_NAT CLIENT_Host_2 non-proxy-arp-search of route static destination
NAT (inside, outside) static source SITE1_APP_PACS_Primary SITE1_APP_PACS_Primary_NAT CLIENT_Host_3_NAT CLIENT_Host_3 non-proxy-arp-search of route static destination
Is that correct, or is at - it an easier way to do this without having to add all statements of NAT? Moreover, any change would be to do on the access list?
Hello
To my knowledge you should not create several new instructions from NAT. You should be well just create a new Group 'object' for new addresses your source address NAT.
To better explain, take a look at your current ' object-group ' that defines your source addresses
the APP_CLIENT_Hosts object-group network
network-object, object SITE1_APP_JCAPS_Dev_VIP
network-object, object SITE1_APP_JCAPS_Prod_VIP
network-object, object SITE2_APP_JCAPS_Dev_Host
network-object, object SITE2_APP_JCAPS_Prod_VIP
network-object, object SITE1_APP_PACS_Primary
Now you can do this sets up a "object-group" that contains a NAT IP address for each of the IP addresses inside the ' object-group ' and 'object' used above. The IMPORTANT thing is that the ' object-group ' that contains the NAT IP addresses is in the SAME ORDER as the actual source addresses.
I mean, this is the first IP address is in most object - group ' will correspond to the first IP address in the newly created "object-group" for the IP NAT addresses.
As above, you can simply have the same "nat" configurations 3 as before but you change/add in the newly created "object-group"
For example, you might do the following
network of the SITE1_APP_JCAPS_Dev_VIP_NAT object
Home 88.88.88.81
network of the SITE1_APP_JCAPS_Prod_VIP_NAT object
Home 88.88.88.82
network of the SITE2_APP_JCAPS_Dev_Host_NAT object
Home 88.88.88.83
network of the SITE2_APP_JCAPS_Prod_VIP_NAT object
Home 88.88.88.84
network of the SITE1_APP_PACS_Primary_NAT object
Home 88.88.88.85
the APP_CLIENT_Hosts_NAT object-group network
network-object, object SITE1_APP_JCAPS_Dev_VIP_NAT
network-object, object SITE1_APP_JCAPS_Prod_VIP_NAT
network-object, object SITE2_APP_JCAPS_Dev_Host_NAT
network-object, object SITE2_APP_JCAPS_Prod_VIP_NAT
network-object, object SITE1_APP_PACS_Primary_NAT
Then you add the following configurations of "nat"
NAT (inside, outside) 1 static source APP_CLIENT_Hosts APP_CLIENT_Hosts_NAT CLIENT_Host_1_NAT CLIENT_Host_1 non-proxy-arp-search of route static destination
Static NAT APP_CLIENT_Hosts APP_CLIENT_Hosts_NAT static destination CLIENT_Host_2_NAT CLIENT_Host_2 non-proxy-arp-search of source route 2 (inside, outside)
NAT 3 (indoor, outdoor) static source APP_CLIENT_Hosts APP_CLIENT_Hosts_NAT CLIENT_Host_3_NAT CLIENT_Host_3 non-proxy-arp-search of route static destination
Note line numbers, we added the above commands. This allows them to enter the upper part of the ASAs NAT rules, and therefore, they will become active immediately. Without line numbers that they will only be used after when you remove the old lines.
Then you can remove the "old"
no nat source (indoor, outdoor) public static APP_CLIENT_Hosts APP_CLIENT_Hosts CLIENT_Host_1_NAT CLIENT_Host_1 non-proxy-arp-search of route static destination
no nat source (indoor, outdoor) public static APP_CLIENT_Hosts APP_CLIENT_Hosts CLIENT_Host_2_NAT CLIENT_Host_2 non-proxy-arp-search of route static destination
no nat source (indoor, outdoor) public static APP_CLIENT_Hosts APP_CLIENT_Hosts CLIENT_Host_3_NAT CLIENT_Host_3 non-proxy-arp-search of route static destination
This should leave you with 3 configurations "nat" who made the NAT source addresses and destination.
Naturally while you perform this change you will also have to change the ACL Crypto to match the new source NAT. This is because as all NAT is done before any VPN on the ASA. So the destination addresses are Nations United for before VPN and source addresses are translated before VPN.
If you do not want to make the changes without affecting the connections too so I suggest
- Add rules to the ACL Crypto for new addresses (NAT) source. Of course, this must be done on both sides of the VPN L2L. You would still be leaving the original configurations to the Crypto ACL does not not the functioning of the L2L VPN.
- Add new configurations of "nat" above without the line numbers I mentioned who mean you that they wont be used until you remove the "old".
- When you are ready to be migrated to use the new IP addresses, simply remove the original "nat" configurations and the ASA will start the corresponding traffic for new "nat" configurations. Provided of course that there is no other "nat" configuration before the nine that could mess things up. This should be verified by the person making the changes.
Of course if you can afford a small cut when then changing the order in which you do things should not matter that much. In my work, that connections are usually not that critical that you can't make these changes almost at any point as it is a matter of minutes what it takes to make changes.
Hope this made sense and helped
Remember to mark a reply as the answer if it answered your question.
Feel free to ask more if necessary.
-Jouni
-
Public static political static NAT in conflict with NAT VPN
I have a situation where I need to create a VPN site-to site between an ASA 5505 using IOS 7.2 and a Sonicwall NSA4500. The problem arises where the LAN behind the Cisco ASA has the same subnet an existing VPN currently created on the Sonicwall. Since the Sonicwall cannot have two VPN both run on the same subnet, the solution is to use policy NAT on the SAA as well as for the Sonicwall, the new VPN seems to have a different subnet.
The current subnet behind the ASA is 192.168.10.0/24 (The Sonicwall already has a private network virtual created for another customer with the same subnet). I try to translate it to 192.168.24.0/24. The peer LAN (behind the Sonicwall) is 10.159.0.0/24. The ASA relevant configuration is:
interface Vlan1
IP 192.168.10.1 255.255.255.0
access extensive list ip 192.168.24.0 outside_1_cryptomap allow 255.255.255.0 10.159.0.0 255.255.255.0
list of access VPN extended permit ip 192.168.10.0 255.255.255.0 10.159.0.0 255.255.255.0
public static 192.168.24.0 (inside, outside) - list of VPN access
card crypto outside_map 1 match address outside_1_cryptomap
In addition, there are other static NAT instructions and their associated ACLs that allow certain traffic through the firewall on the server, for example:
public static tcp (indoor, outdoor) interface smtp SERVER smtp netmask 255.255.255.255
The problem is this: when I enter the static strategy statement NAT, I get the message ' WARNING: real-address conflict with existing static "and then it refers to each of the static NAT statements reflecting the external address to the server. I've thought about it, and it seemed to me that the problem was that policy NAT statement must be the first statement of NAT (it is the last one) so that it is run first and all traffic destined to the VPN to the Sonicwall (destination 10.159.0.0/24) tunnel would be properly treated. If I left him as the last statement, then the other static NAT statements would prevent a part of the 10.159.0.0/24 network-bound traffic to be correctly routed through the VPN.
So, I tried first to my stated policy NAT upward in the ASDM GUI interface. However, moving the declaration was not allowed. Then I tried to delete the five static NAT statements that point to the server (an example is above) and then recreate them, hoping that would then move up the policy statement NAT. This also failed.
What Miss me?
Hello
I assumed that we could have changed the order of the 'static' , the original orders, but as it did not work for some reason any then it seems to me that you suggested or change, that I proposed should work.
I guess that your purpose was to set up static political PAT for the VPN for some these services, then static PAT of public network access, then static NAT to policy for the rest of the network in-house.
I guess you could choose any way seems best for you.
Let me know if get you it working. I always find it strange that the original configuration did not work.
Remember to mark a reply as the answer if it answered your question.
Feel free to ask more if necessary
-Jouni
Maybe you are looking for
-
Said that my ID apple does not allow to unlock
-
migration assistant crushes apps on the new computer?
I've migrated user accounts to a new mac from an old mac. I want to migrate applications as well, but do not want to replace the existing applications on the new computer. How can I avoid this?
-
MBPro Mid 2015 GPU diode 0 high temperature
I recently got a new MBPro 15 "mid-2015 (16 GB of Ram with Iris Pro). I use temperature indicator 4.1 and get sometimes a message saying WHAT GPU Diode 0 received at 98 ° C for a short time. Is this normal?
-
Flight Simulator 2004 (Fs9.1) runs on Windows 8?
Flight Simulator 2004 (Fs9.1) run Windows 8?
-
I need the BIOS for my gateway T - 63 Lap Top series.
I have a gateway T - 63 Lap Top series. The part of the motherboard is #: ACEH-40GAB1700-F605.The serial number is: V94DM03707. I tried to contact the bridge, but the information (serial number) that the system is requested to attend my request are s