ASA ACL problem
Hello
I try to put an ACL on a group policy on my VPN Ipsec Lan to Lan.
My LCD does not work and blocking all traffic.
Since it does not work with the ACLs on group policy, I put an ACL on the interface inside but do not match.
To match, I must decline any all a put before a permit.
Thank you
Hello
The main problem when the configuration of IPSec filters is that people set up a descendant. You must specify the inbound traffic you want to allow or deny.
Here is the document that explains how to configure filters. Take a look and if you have any problems please contact your VPN configuration.
Have fun.
Raga
Tags: Cisco Security
Similar Questions
-
Need of the ACL kung fu for VPN from Site to Site ACL problem
Group,
Have a little problem I know is related to ACL. I wanted to have a few experts to take a look at my config please. Here's the question:
Attempt to create a site between two offices, but for some reason any that they cannot ping each other. It is a strange thing.
97.XX.231.22 <-->71.xx.160.123
I can ping both firewalls from the outside using a computer to another, but from the internal firewall utilities, they cannot ping each other. At the same time I can ping to their respective gateways.
Secondly, I did an interior outside translation as you can see here for 80 & 443 preventing me from browsing http and https via VPN for Remote LAN, can it be modified to allow access? I can access when I dial in via VPN client but not via permanent VPN tunnel. Here is the config.
no ip nat service sip 5060 udp port
IP nat inside source map route SDM_RMAP_1 interface GigabitEthernet0/0 overload
IP nat inside source static tcp 10.41.14.103 80 71.xx.160.123 80 extensible
IP nat inside source static tcp 10.41.14.103 71.xx.160.123 expandable 443 443
IP route 0.0.0.0 0.0.0.0 71.xx.160.121
IP route 10.67.188.32 255.255.255.224 10.41.14.99 6 permanent
IP route 10.67.188.96 255.255.255.224 10.41.14.99 8 permanent
IP route 10.200.107.0 255.255.255.0 10.41.14.99 9 permanent
IP route 10.200.110.0 255.255.254.0 10.41.14.99 7 permanent
IP route 74.200.107.0 255.255.255.0 10.41.14.99 5 permanent
IP route 74.200.110.0 255.255.254.0 10.41.14.99 4 permanent
IP route 208.67.188.32 255.255.255.224 10.41.14.99 2 Permanent
IP route 208.67.188.96 255.255.255.224 10.41.14.99 3 permanent
!
auto discovering IP sla
Logging trap errors
host 192.168.10.29 record
access-list 2 Note HTTP access class
Note access-list category 2 CCP_ACL = 1
Note access-list 2 Platinum LAN
access-list 2 permit 10.41.14.0 0.0.0.255
access-list 2 refuse any
Access-list 101 remark rules Master
Note access-list 101 category CCP_ACL = 1
Note access-list 101 FaxFinder WWW traffic
access-list 101 permit tcp any host 71.xx.160.123 eq www
Note access-list 101 traffic HTTPS FaxFinder
access-list 101 permit tcp any host 71.xx.160.123 eq 443
Note access-list 101 NTP Time Protocol
access-list 101 permit udp any host 71.xx.160.123 eq ntp
Access-list 101 remark IPSEC protocols
access-list 101 permit udp any host 71.xx.160.123 eq non500-isakmp
Access-list 101 remark IPSEC protocols
access-list 101 permit udp any host 71.xx.160.123 eq isakmp
Note access-list 101 traffic ESP
access-list 101 permit esp any host 71.xx.160.123
Note the access list 101 General License
access list 101 ip allow a whole
Note access-list 102 CCP_ACL category = 2
access-list 102 deny ip 10.41.14.0 0.0.0.255 192.168.76.0 0.0.0.255
Note access-list 102 IPSec rule
access-list 102 deny ip 10.41.14.0 0.0.0.255 10.0.2.0 0.0.0.255
Note access-list 102 IPSec rule
access-list 102 deny ip 10.41.14.0 0.0.0.255 192.168.10.0 0.0.0.31
Access-list 102 remark Platinum LAN NAT rule
access-list 102 permit ip 10.41.14.0 0.0.0.255 any
Note category from the list of access-104 = 4 CCP_ACL
Note access-list 104 IPSec rule
access-list 104. allow ip 10.41.14.0 0.0.0.255 192.168.10.0 0.0.0.31
Note access-list 108 CCP_ACL category = 4
access-list 108 allow ip 10.41.14.0 0.0.0.255 any
Note access-list 109 IPSec rule
Note access-list 109 CCP_ACL category = 4
access-list 109 allow ip 10.41.14.0 0.0.0.255 192.168.76.0 0.0.0.255
Note access-list 110 CCP_ACL category = 4
Note access-list 110 IPSec rule
access-list 110 permit ip 10.41.14.0 0.0.0.255 10.0.2.0 0.0.0.255
not run cdp
!
allowed SDM_RMAP_1 1 route map
corresponds to the IP 102
There is more then one way how you can achieve this goal.
(1) the best way is possible if the two VPN counterparts are IOS routers. Then you can migrate to virtual VPN - tunnel interfaces (VTI). With this, the external interface doesn't mix - and non-VPN-traffic VPN.
(2) if VTI is not possible, you can restrict the translation to only non - VPN traffic using a roadmap:
object-group network RFC1918
10.0.0.0 255.0.0.0
172.16.0.0 255.240.0.0
192.168.0.0 255.255.0.0
NAT-SERVER - 10.41.14.103 allowed 10 route map
corresponds to the TRAFFIC-NAT-SERVER IP - 10.41.14.103
TRAFFIC-NAT-SERVER extended IP access list - 10.41.14.103
deny ip host 10.41.14.103 object-group RFC1918
permit tcp host 10.41.14.103 eq 80 a
allow a host EQ 10.41.14.103 tcp 443
IP nat inside source static 10.41.14.103 71.xx... map route NAT-SERVER - 10.41.14.103
What makes that?
When your server communicates with a system with an address in the range RFC1918, then the road map does not correspond and the translation is not used. It is you, the VPN scenario. But if the server communicates with a non-RFC1918 address, then the translation is used and the server can be reached.
--
Don't stop once you have upgraded your network! Improve the world by lending money to low-income workers:
http://www.Kiva.org/invitedBy/karsteni -
I'm new to the ASA and try to understand something with ACL. It will take I understand about their creation and by adding entries and that all should have the same name, but I'm confused about the ACLs that do not have the same name that already exist on a device or may be named differently.
For example:
Access-List Corporate1 permit tcp any any eq www
Access-List permits Corporate1 tcp everything any https eq
Access list ip Inside_Out allow a whole
Access-group Coprorate1 in interface outside
Ignoring the content at the moment, I have 2 ACL: one with 2 inputs and one with a single entry. The Corporate1 of the ACL applies within the interface and is active. I get this part... My question is: is the Inside_Out of the grouped ACL in automatically with the ACL and activates them as well active or is it safe to say it is not active and can be removed without causing damage? Is the ACL only activates the ACL with the same name as the Access-Group Corporate1?
I have 2 different people telling me two different things. I'm lost on this one, any help would be greatly appreciated.
-Jon
Working with ACLs imply always two steps:
- You configure the ACL (with possibly multiple lines but the same name).
- You set the ACL to a function. Which might be filtering on an interface with the control-group-access, but is not limited to the one that the ACL is used in several places when the ASA must match the traffic.
(If you did both) 1 and 2), then the ACL is active and currently in use. If you have set up the ACL only but the ACL was never assigned to a function, then the ACL is not active and can be removed.
In your example:
If you find that the ACL 'Inside_Out' but you don't know if the ACL is used, then do one
sh run | inc Inside_Out
If the output shows only the ACL lines, it is unused and can be removed.
clear configure access-list Inside_Out
Or it is but not used must be used, and then apply the ACL for the desired purpose.
-
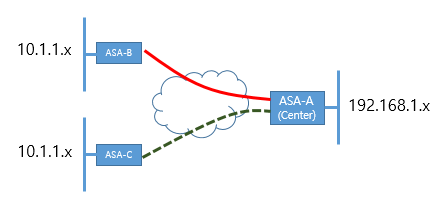
Currently, ASA - A (Center) and B has connected by VPN IPSec.
I would like a VPN establsh A ASA and ASA-C both.
But unfortunately, within the network range has same range B-ASA and ASA-C both. (10.1.1.x)
In this case, how can I connect IPSec VPN to ASA-B and C - ASA ASA - A at a time?
Thank you
Hello
You can go with policy subnet Nating ASA-C on another subnet on ASA - C (ex: 10.1.10.x) and use this as your ACL subnet subnet. It should work. Please search online for examples of configuration.
HTH
MS
-
Hi I have a Cisco Asa 5520 and I want to vpn site-to-site by using another interface with a carrier of lan to lan, the problem is when I try to pass traffic have the syslog error to follow:
No translation not found for udp src lan2lan:10.5.50.63/44437 dst colo: biggiesmalls groups / 897LAN to LAN service interface is called: lan2lan
one of the internal interfaces is called: colo
I think that is problem with Nat on the SAA but I need help with this.Config:!
interface GigabitEthernet0/0
nameif outside
security-level 0
eve of fw - ext 255.255.255.0 address IP XXaaaNNaa
OSPF cost 10
OSPF network point-to-point non-broadcast
!
interface GigabitEthernet0/1
No nameif
no level of security
no ip address
!
interface GigabitEthernet0/1.50
VLAN 50
nameif lb
security-level 20
IP 10.1.50.11 255.255.255.0
OSPF cost 10
!
interface GigabitEthernet0/1,501
VLAN 501
nameif colo
security-level 90
eve of fw - int 255.255.255.0 172.16.2.253 IP address
OSPF cost 10
!
!
interface GigabitEthernet1/1
Door-Lan2Lan description
nameif lan2lan
security-level 0
IP 10.100.50.1 255.255.255.248
!
access extensive list ip 10.1.0.0 lan2lan_cryptomap_51 allow 255.255.0.0 object-group elo
permit access list extended ip sfnet 255.255.255.0 lan2lan_cryptomap_51 object-group elo
pager lines 24
Enable logging
host colo biggiesmalls record
No message logging 313001
External MTU 1500
MTU 1500 lb
MTU 1500 Colo
lan2lan MTU 1500
ICMP unreachable rate-limit 1 burst-size 1
ARP timeout 14400
NAT-control
Global 1 interface (external)
interface of global (lb) 1
Global (colo) 1 interface
NAT (lb) 1 10.1.50.0 255.255.255.0
NAT (colo) - access list 0 colo_nat0_outbound
NAT (colo) 1 10.1.13.0 255.255.255.0
NAT (colo) 1 10.1.16.0 255.255.255.0
NAT (colo) 1 0.0.0.0 0.0.0.0
external_access_in access to the external interface group
Access-group lb_access_in in lb interface
Access-group colo_access_in in interface colo
Access-group management_access_in in management of the interface
Access-group interface lan2lan lan2lan
!
Service resetoutside
card crypto match 51 lan2lan_map address lan2lan_cryptomap_51
lan2lan_map 51 crypto map set peer 10.100.50.2
card crypto lan2lan_map 51 game of transformation-ESP-3DES-SHA
crypto lan2lan_map 51 set reverse-road map
lan2lan_map interface lan2lan crypto card
quit smoking
ISAKMP crypto identity hostname
ISAKMP crypto enable lan2lan
crypto ISAKMP policy 10
preshared authentication
3des encryption
sha hash
Group 2
life 86400
Crypto isakmp nat-traversal 20
enable client-implementation to date
IPSec-attributes tunnel-group DefaultL2LGroup
pre-shared-key xxXnnAA
tunnel-group 10.100.50.2 type ipsec-l2l
tunnel-group 10.100.50.2 General-attributes
Group Policy - by default-site2site
No vpn-addr-assign aaa
No dhcp vpn-addr-assign
Telnet timeout 5
!The VPN is OK? ("' isakmp crypto to show his" should show a MM_Active tunnel to the peer address ")
Normally exempt us VPN site-to-site of NAT traffic. This could be your problem. If you can share your configuration, we can have a look.
p.s. you should affect the question of the security / VPN forum.
-
Cisco ASA.
For example, I have the subnet in the tunnel of splitting ACL 192.168.0.0/16. I need made an exception to remove 192.168.89.0/24 in the ACL CE-tunnel - what is the best way to do it?
Hi rioneljeudy ,
You can restrict the subnets in the ACL used for the tunnel of split for example change the 16 something more specific or apply a filter, VPN policy. See an example on the following link:
It may be useful
-Randy-
-
Currently, I am at a very basic level of agreement and have obtained internet access via binding of pep to the router and seem to have reached an active VPN connection. VPN connection is active, but the traffic counters are at 0. When I change the sequence of the ACL, it connects perfectly.
2800 router using
There is not enough information given here for us to understand the problem and propose solutions. If you change the sequence number of ACL and it connects perfectly then maybe the problem is solved?
HTH
Rick
-
Hello
I have configured ISE and WLC for use with CWA guestportal but there is a problem with the CoA - he won't apply airespace alc after auth to guestportal.
1. on page authC, I configured a MAB wireless to continue if not found user and use an internal users as an identity store.
2. on page authZ I configured a WEBAUTH as a default rule with the following:
Access type = ACCESS_ACCEPT
Cisco-av-pair = url-redirect-acl = ACL-WEBAUTH-REDIRECT
Cisco-av-pair = redirect url =https://ip:port/guestportal/gateway? sessionId = SessionIdValue & action = cwa
3. I've also configured this ACL to WLC to allow
permit any - any icmp and dns
allow all-to-the-ise-8443
ise-to-any license
This part works very well because I could redirect to guestportal and use my guest connection & pw to allow myself. The guest account has been previously generated by portal sponsor and it works too.
4. on page authC, I use a dot1x wireless to use internal users
5. in the authZ page I use a "if internal users: Guest can leave COMMENTS" rule
6 rule PROMPT resembles the following:
Access type = ACCESS_ACCEPT
Airespace-ACL-Name = GUEST_INTERNET_ONLY
7. this ACL is configured on the WLC allowing all unless private networks (ISE is also permitted)
After authentication Portal comments, I see a success message and I was able to ping internet but I don't have web access. It looks like CoA and Airespace acl are not working and I continue to use my access ACL-WEBAUTH-REDIRECT-list and I see a strange error messages in newspapers WLC:
* apfReceiveTask: 17:32:27.317 12 Nov: % ENTRY_DONOT_EXIST-3-ACL: acl.c:369 cannot find an ACL by name.
I swear my ACL name spelling is correct and ACL-WEBAUTH-REDIRECT and GUEST_INTERNET_ONLY are on the WLC with counters more!
I have not one point what problem could be...
Any ideas?
P.S. see attach for authentication log Live
You can try "debug client" in the CLI WLC and try to connect with the customer. It you see if the WLC applies your ACL.
Looks like this for my license - all ACLs
* apfReceiveTask: 25 Oct 11:17:05.867: c8:bc:c8:13:4e:35 172.16.10.13 WEBAUTH_REQD (8) change IPv4 ACL 'none' (ACL ID 255) ===> 'PERMIT-ALL' (ACL ID 1)-(calling apf_policy.c:1762)
It must be near the bottom.
And then after all debug disable.
Another question, you can test internet but no web access, as well as the URL? Is DNS works after applying the last ACL?
On this line in the log:
* apfReceiveTask: 17:32:27.317 12 Nov: % ENTRY_DONOT_EXIST-3-ACL: acl.c:369 cannot find an ACL by name.
I get that with CWA to work so I don't know which is linked. (for my setup)
Concerning
MikaelSent by Cisco Support technique iPad App
Post edited by: Mikael Gustafsson
-
Hi all
I have some problems with the implementation of a VPN using IPSEC to establish a connection from Site to Site.
What I'm trying to Setup is the following, his IP address of a site can reach the beaches on site B and visa versa.
Site A Site B
192.168.10.0 172.16.0.0
192.168.20.0 IPSEC tunnel - 172.17.0.0 -.
192.168.30.0 172.18.0.0
I tested with one subnet to another subnet that works. However, when I try to group the objects it fails.
As an example I can set up a VPN of 192.168.20.0 to 172.18.0.0 that I can pass the traffic through but its unable to reach other subnets.
Excerpts from the config.
crypto ISAKMP allow outside
ACL
list of allowed outside_1_cryptomap ip access dmz LAN object dmz-network-remote
Tunnel group
tunnel-group
type ipsec-l2l IPSec-attributes tunnel-group
pre-shared key
ISAKMP retry threshold 10 keepalive 2
Phase 1
part of pre authentication isakmp crypto policy 10
crypto ISAKMP policy 10 3des encryption
crypto ISAKMP policy hash 10 sah
10 crypto isakmp policy group 2
crypto ISAKMP policy life 10 86400
Phase 2
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
card crypto outside_map 1 match address outside_1_cryptomap
card crypto outside_map 1 set pfs Group1
map 1 set outside_map crypto peer
card crypto outside_map 1 set of transformation-ESP-3DES-SHA
outside_map interface card crypto outside
NAT
NAT (inside, outside) 1 static source local-network-dmz dmz LAN destination static remote-network-dmz dmz-network distance
Any advice would be greatly appreciated.
Thank you.
Andrew,
Accroding to your config, each network is behind a different interface of the SAA, so you will need to change the NAT rule for each of them, for example:
NAT (DMZ_Zone, outside) 1 static source ad-network-local ad-network-local destination static obj obj-remote control-remote control
NAT (DB_Zone, outside) 1 static source local-network-db db-network-local destination static obj obj-remote control-remote control
NAT (AD_Zone, outside) 1 static source local-network-dmz dmz LAN destination static obj obj-remote-distance
Please review and give it a try.
I hope hear from you soon.
-
Site to Site ASA translation problem
Hello
I would like to ask how to solve this problem:
Site A is ASA5520 (v7.2) with:
Interface backwards
External interfaceOn site B is ASA5520 (v8.2) with:
Interface backwards
External interface
DMZ interfaceThere's a L2L IPSec tunnel between network ASAs - tunnel is and the correct work of the networks within the ASA networks inside the ASA B.
-----------------
I can do a ping to the server (172.25.106.221) on UI inside the ASA A for server (192.168.1.5) within the Interface of the ASA b.But I can't do a ping to the server (172.25.106.221) on the UI inside the ASA A server (192.168.0.31) on the Interface of the DMZ of ASA B with a pattern of ASA B: log % ASA-3-305005: no outside group translation not found for icmp src: 172.25.106.221 DMZ:192.168.0.31 (type 8, code 0) dst
No doubt is there a problem with the static translation on ASA B, so im looking how to solve this problem.
I posted configuration files (I omitted a few unnecessary configuration line to resolve this problem, I think).
Thank you much for the help.
Hey there,
Checked the config and I noticed he was missing a sheep of the DMZ, there is one for the inside very well.
: so you can add the following to the ASA B
NAT (DMZ) 0-list of access ACL_NONAT
Let me know how it goes, if it helped you can give then replied
See you soon,.
MB
-
1800 to ASA VPN problem, fail to Phase 2
Hello
I have a series of 1800 running IOS 12.4 (6) T11 and an ASA 5505 8.2 I try to connect using a lan lan tunnel 2 running.
1800:
WAN a.b.c.141
LAN 192.168.0.0/24
ASA5505:
WAN x.y.z.125
LAN 10-180.3.0/24
The 1800s also has pptp, 172.16.99.0/24 network clients.
Problem:
When I try to establish a connection to a host on a local network to another, I can see who works for phase 1. In phase 2, some interesting debugging messages are observed:
002611: * 19:15:24.142 Apr 11 UTC: map_db_find_best found no corresponding card
002612: * 19:15:24.142 Apr 11 UTC: IPSEC (crypto_ipsec_process_proposal): proxy unsupported identities
002613: * 19:15:24.142 Apr 11 UTC: ISAKMP: (2031): IPSec policy invalidated proposal with error 32
002614: * 19:15:24.142 Apr 11 UTC: ISAKMP: (2031): politics of ITS phase 2 is not acceptable! (local a.b.c.141 remote x.y.z.125)
002615: * 19:15:24.142 Apr 11 UTC: ISAKMP: node set-1883245570 to QM_IDLE
002616: * 19:15:24.142 Apr 11 UTC: ISAKMP: (2031): Protocol to send NOTIFIER PROPOSAL_NOT_CHOSEN 3
SPI 2215023312, message ID =-1883245570
002617: * 19:15:24.142 Apr 11 UTC: ISAKMP: (2031): sending x.y.z.125 my_port 500 peer_port 500 (R) QM_IDLE package
002618: * 19:15:24.142 Apr 11 UTC: ISAKMP: (2031): purge the node-1883245570
002619: * 19:15:24.142 Apr 11 UTC: ISAKMP: (2031): node-9204283 error suppression REAL reason "QM rejected."
002620: * 19:15:24.142 Apr 11 UTC: ISAKMP: (2031): entrance, node-9204283 = IKE_MESG_FROM_PEER, IKE_QM_EXCHWhen negotiating, 'show isakmp crypto' show first 'ACTIVE', but after a minute or two pass to ' ACTIVE (DELETED) ".
From what I see, the cisco 1800 seem to put an end to the tunnel because it meets some of the options phase 2.
# 1800
IPv4 Crypto ISAKMP Security Association
status of DST CBC State conn-id slot
a.b.c.141 x.y.z.125 QM_IDLE 2029 0 ACTIVE# on 5505
2 IKE peers: a.b.c.141
Type: L2L role: initiator
Generate a new key: no State: MM_ACTIVE# After a minute or so on the 1800 (no difference on output 5505 s)
IPv4 Crypto ISAKMP Security Association
status of DST CBC State conn-id slot
a.b.c.141 x.y.z.125 QM_IDLE 2030 0 ACTIVE
a.b.c.141 x.y.z.125 MM_NO_STATE 2029 0 ACTIVE (deleted)I think it might be because of NATing on each side. I'm a little unsure on the NAT of the 1800 config, if he tries to nat the 192.168.0.0/24 as it passes above the tunnel?
Hello
I don't see an exemption from nat configured on the router.
Please, try the following:
overloading the IP nat inside source route NATMAP interface map.
I hope this helps.
Kind regards
Anisha
P.S.: Please mark this thread as answered if you feel that your query is resolved. Note the useful messages.
-
ACL problems after upgrade to 11.2.0.2 11.2.0.1, please help
After that we went from 11.2.0.1 to 11.2.0.2, we started having this problem:
ORA-24247: network access denied by the ACL access (ACL) ORA-06512: at "SYS." DBMS_LDAP_API_FFI', line 25 ORA-06512: at "SYS." DBMS_LDAP", line 57 ORA-06512: at"BANINST1. ZPGKOUSR', line 1606
1606 line is:
l_session: = dbms_ldap.init (host name = > l_host,)
PortNum = > v_ADConfig.zgpwdrecfg_port);
We have an ACL with * and NULL lower and upper ports and connected user a plug in and solve this ACL privileges.
What do we lack?
Thank you
Alex.Hi Alex
Please check these references:
notes 1317940.1 DBMS_LDAP fails to authenticate after the DB to 11.2.0.2
notes 1361247.1 ORA-24247 after application 11.2.0.2 group patchsee that if 10170706 Patch can help, it is a problem when not all authorisations valid acl has been verified
a correspondent in some scenarios,Greetings,
Damage ten Monkshood
-
VPN Concentrator at the migration of ASA - auth problem.
Hi all
I'm migrating to remote access VPN (IPSec) VPN 3020 to ASA. Local authentication works very well. If I add the IAS radius for authentication servers, then I get the following error message
Secure VPN connection terminated by a peer.
433 reason: (reason unspecified peer)
The capture of shows "access-reject" in back IAS server packages. IAS server is configured in the same way as the VPN 3020.
I run the code to 8.0 (0) on the SAA. Any idea of what is the cause?
Hello
You specify the shared secret between asa and IAS?
You specified in RADIUS server that ASA is allowed to send requests? In other words has specified that the SAA is a valid SIN?
This link may be useful: http://www.cisco.com/en/US/products/hw/vpndevc/ps2030/products_configuration_example09186a00806de37e.shtml
I hope this helps.
Best regards.
Massimiliano.
-
Hello everyone, for some reason any with this workshop of tracer of package I get the last piece of ACL incorrect.
This is the lab I've done so far (94%)
http://www.sendspace.com/file/gsnk07
They ask the following
Configure the standard named ACL on the vty lines R1 and R3, allowing the hosts directly connected to their Fast Ethernet subnets for Telnet access. Deny explicitly all other connection attempts. Name these ACLs VTY-Local standard.
They also ask that for the extended ACL
Name of the block of the ACL.
Ban traffic from the LAN R1 to reach the R3 LAN.
Ban traffic from the R3 LAN to LAN of R1.
Allow any other traffic.
Here's what I have on the Router 1 for the standard ACL
IP access-list standard VTY-Local
deny 10.1.0.0 0.0.0.3
deny 10.3.0.0 0.0.0.3
deny 10.3.1.0 0.0.0.255
10.1.1.1 permit 0.0.0.255
I couldn't understand why my ACL is incorrect.
Host 1 IP (connected to R1 ip host) - 10.1.1.1
Connecting series between R1 and R2 ip subnet is
10.1.0.0 30
East of R2 to R3
10.3.0.0 / 30
Host 2 to R2
10.3.1.0 24
2 host address is 10.3.1.1/24
Can someone help me?
deny 10.1.0.0 0.0.0.3 - corresponds to the IP 10.1.0.x
deny 10.3.0.0 0.0.0.3 - corresponds to the IP 10.3.0.x
deny 10.3.1.0 0.0.0.255 - corresponds to the IP 10.3.1.x
10.1.1.1 permit 0.0.0.255 - match IP 10.1.1.0
ACL must be correct: -.
deny 10.1.0.0 0.0.0.3
deny 10.3.0.0 0.0.0.3
deny 10.3.1.0 0.0.0.255
10.1.1.1 permit 0.0.0.0
or
10.1.1.1 permit 0.0.0.0
all refuse
HTH >
-
I have a question, I am doing an ACL extended to deny HTTP, Telnet, and FTP internet traffic to PC1 in an exercise that I do.
I did the ACL following and applied to the loopback interface on R2 (where the ISP is the 'cloud') PC1 is connected to R1 that is obviously connected to R2.
IP-access-list scope ACL_TCP
TCP 209.165.200.160 refuse 0.0.0.31 10.0.0.0 0.0.0.127 put in place
allow tcp any a Workbench
Is there a better way to do it? This ACL scope works for my purpose?
Tell R2 address is 192.168.1.2, and you only want to allow this address. You create the acl on R1 and R3, and they would look like:
R1: 192.168.1.1
R3: 192.168.1.3
access-list 23 allow host 192.168.1.2
You can apply this to your line on R1 and R3:
line vty 0 4
access-class 23 in
HTH,
John
Maybe you are looking for
-
The F5 can be upgraded to F55 The F55 can be implemented with a new plate shoulder ENG new controls offers forward for immediate changes at the World Bank and I think that audio. Difficult to see on the livestream.
-
Number of the results in the report variable
Hello everyone, I need help in TestStand reports. I use TestStand 2014 and 2014 of Labview, both 32 bits. The situation is like this: I am running a test with test steps 3. The first stage of the test is a step of "additional results" which records t
-
Xbox 360 questions (Modern Warefare 2) online
Hello, I request assistance with my Xbox 360 and Windows 7 online game, I would ask on Xbox.com, but they may not appear too willing to help. Anyway, I recently had the home edition of Windows Vista, and my online game has worked very well. I then
-
Instant Messaging online a second then the entire page is lost, im connected but I'm not getting any connection activity, very very frusrating and b4 are tell me 2 get broadband... its not avaiable in my area, I'm beside the ocean, guess it's the las
-
I don't know if this can be done without a lot of manual configuration. I have a router (a SRI 2921 15.4 (3) M3) which is connected to the other ISR routers running (running 2921 s 15.4 (3) M3 and 4451-Xs running using DMVPNs 15.4 (3) S3). DMVPN tun