CSA Client unistall and disable.
Is it possible to set a password so that users cannot disable, change, or uninstall the client on the local desktop?
Thank you
Dan
Go to the policy page, find the 'Base - CSA Service and control of the client user interface' you will see the module 'Base - CSA UI control customer' rule and then you will see the "basic - service control of CSA."
The service order is more to the protection of the service from other applications are trying to kill/stop/change agent service CSA, not so much for the protection of the user.
Located in the module 'Base - CSA UI control customer' rule itself, you will see the "Agent UI control rule", examine it and you will see the following text:
Control interface user agent rule [2112]
Interaction of the UI control agent
Allow the user to reset the settings to default user interface agent
Allow a user interaction
Allow access to the configuration of the user agent and contact information
Allow the user to modify the security settings for agent
Allow user change agent of personal firewall settings
Remove the taskbar notifications
Of course if you check / uncheck these it will allow or not allow respectively.
Tags: Cisco Security
Similar Questions
-
CSA with the Client VPN and remote access
Hello world!
I have the folowing isue: I have to tune in to the CSA for a clinet it connects remote with VPN Client only. He should not be able to connect to any other network or lan or dial-up.
No idea what the policy should change or tune?
Thank you
You can create an access network rule that depends on a State of the system. The State of the system can be defined to have a game of skill, which belongs to the range of VPN and the network access rule would declare that the client computer cannot act as a server on UDP/TCP ports when the State of the system is ensured.
So, if the laptop is not connected to the VPN, it would not be able to act as a server for connections to all and will be locked out. You will need to create an exception for the IP address of the VPN server to your corporate offices and allow the CSA client opening these ports.
-
How to enable and disable, copy or rename the rules via the groovy script?
A client, we received this question:
How to enable and disable, copy or rename the rules via the groovy script?
Foglight 5.7.5
Hello
There is this example of support KB
support.Software.Dell.com/.../99059
and there is also documentation of Service layer of the administration on the RuleService console.
Best regards
Golan
-
I am running APF on a number of jobs in direct mode, but I wanted to give some users a privileged access (Tech) so I created a group of States with these users user and when users log into a machine with the CSA, they are able to see the interface user and turn csa to install applications. For other users of that rule of the user interface is not enabled so not visible on their desktop. It seems to work, but the user interface often disappears if I make it a rule to change or create a new rule. It's a good way or I'm hacking in a way that should not be used. Now technicians need to reboot the machine and relog in their accounts to see the icon of the CSA client. Seems to me that there should be a better way.
Sounds like a good way. Don't forget there is no other User Agent interface control rules that could be walking on the one you have created.
In addition, the User Agent interface will disappear if there is no User Agent applied to the host interface control rule.
Tom
-
WRVS4400N Client filtering and AP Isolation Options missing
I have a WRVS4400N with v1.1.13 firmware (latest firmware for versions 1.0 and 1.1 of the material).
I need to configure the wireless client filtering and isolation of the AP. The frequently asked questions for this router contains information on this subject. However, my firmware on the router does contain no options described in the FAQ. These settings are only available in the v2.0 hardware? I hope that these settings can be made available in the 1.0 1.1 hardware. I wouldn't have to buy a new router to do this.
The following is extracted from the FAQ WRVS4400N (Document ID: 109207)
http://www.Cisco.com/en/us/products/ps9923/products_qanda_item09186a0080a39097.shtml> Q. How can I configure the clients of filtering on the WRVS4400N wireless?
>
> A. Complete these steps in order to allow filtering wireless have:
> 1. open the WRVS4400N web configuration page.
> 2.Click the wireless tab.
> 3.Click the subtab to access the wireless network.
> 4.Select prevent access to and allow the access keys.
> 5.Fill in the wireless MAC address which is filtered so that you can control what wireless client can connect because of the road.>
> Q. What is the characteristic of Isolation AP, and how does it work?
>
> A. The Isolation AP feature isolates all the wireless clients and the wireless on your network devices to each other. The insulation is made at the level of the MAC address so > all wireless devices are able to communicate with the router, but not to each other. In order to use this feature, click on the button Activate and save the > parameters. The AP isolation is disabled by default.
FAQ seems to be for an older version of the firmware and the firmware later has the options you want under different headings.
Filtering wireless is managed by going under wireless > wireless control. Select 'Enable' and then decide whether or not to control the connections by allowing only certain MAC addresses or deny certain MAC address and allowing all other wireless. There is even a button that shows the current wireless connected clients to make it easier to determine the MAC addresses of valid customers when filling out your list.
The isolation of the AP is called Wireless insulation. Go under wireless > wireless security and select 'Enable' for isolation wireless. This will prevent communication between wireless clients.
-
PIX-to-client VPN and how to reach on other interfaces systems
Hi all
I've implemented a Pix-to-Client VPN and it seems works ok.
As you can see, customer gets the same inside the class address (192.168.100.x) so I can reach across systems.
My questions are:
If I give different subnet pool addresses, how can 1 I still reach inside systems?
2 if I have other systems on these interfaces such dmz1 (192.168.10.0) dmz2 (192.168.20.0) how to get to these systems of the
even the client vpn access?
Concerning
Alberto Brivio
IP local pool vpnpool1 192.168.100.70 - 192.168.100.80
access-list 102 permit ip 192.168.100.0 255.255.255.0 192.168.100.0 255.255.255.0
NAT (inside) - 0 102 access list
Permitted connection ipsec sysopt
Crypto ipsec transform-set esp - esp-md5-hmac trmset1
Crypto-map dynamic map2 10 set transform-set trmset1
map map1 10 ipsec-isakmp crypto dynamic map2
map1 outside crypto map interface
ISAKMP allows outside
ISAKMP identity address
part of pre authentication ISAKMP policy 10
encryption of ISAKMP policy 10
ISAKMP policy 10 md5 hash
10 2 ISAKMP policy group
ISAKMP life duration strategy 10 86400
vpngroup address vpnpool1 pool test
vpngroup split tunnel 102 test
vpngroup test 1800 idle time
test vpngroup password *.
It is generally preferable to use another range of IP addresses. The PIX will know that the VPN Client uses that vary and route it properly whitch is not the case when you are using the same IP range as the inside interface.
To access another interface use the SHEEP (your ACL 102) access list which disables NAT between the VPN and the neworks to which you want to connect.
Example of config:
access-list allowed SHEEP Internalnet ISubnetMask VPN-pool 255.255.255.0 ip
access-list allowed SHEEP DMZnet DMZSubnetMask VPN-pool 255.255.255.0 ip
NAT (inside) 0 SHEEP
AAA-server local LOCAL Protocol
AAA authentication secure-http-client
Permitted connection ipsec sysopt
Crypto ipsec transform-set esp-3des esp-md5-hmac TRANS
Crypto-map dynamic outside_dyn_map 20 game of transformation-TRANS
card crypto 65535 REMOTE ipsec-isakmp dynamic outside_dyn_map
REMOTE client authentication card crypto LOCAL
interface card crypto remotely outside
ISAKMP allows outside
ISAKMP identity address
ISAKMP nat-traversal 20
part of pre authentication ISAKMP policy 10
ISAKMP policy 10 3des encryption
ISAKMP policy 10 md5 hash
10 2 ISAKMP policy group
ISAKMP life duration strategy 10 86400
IP pool local VPNPool x.y.z.1 - x.y.z.254
vpngroup VPNGroup address pool VPNPool
vpngroup VPNGroup dns-server dns1 dns2
vpngroup VPNGroup default-domain localdomain
vpngroup idle 1800 VPNGroup-time
vpngroup VPNGroup password grouppassword
username, password vpnclient vpnclient-password
sincerely
Patrick
-
my browser cannot open google and facebook and other https sites that it does not open even the app store does not work, I tried to change my DNS google DNS and disable IPv6 but still no use, help PLZ!
You may have installed one or more variants of the malware "VSearch' ad-injection. Please back up all data, and then take the steps below to disable it.
Do not use any type of product, "anti-virus" or "anti-malware" on a Mac. It is never necessary for her, and relying on it for protection makes you more vulnerable to attacks, not less.
Malware is constantly evolving to work around defenses against it. This procedure works now, I know. It will not work in the future. Anyone finding this comment a couple of days or more after it was published should look for a more recent discussion, or start a new one.
Step 1
VSearch malware tries to hide by varying names of the files it installs. It regenerates itself also if you try to remove it when it is run. To remove it, you must first start in safe mode temporarily disable the malware.
Note: If FileVault is enabled in OS X 10.9 or an earlier version, or if a firmware password is defined, or if the boot volume is a software RAID, you can not do this. Ask for other instructions.
Step 2
When running in safe mode, load the web page and then triple - click on the line below to select. Copy the text to the Clipboard by pressing Control-C key combination:
/Library/LaunchDaemons
In the Finder, select
Go ▹ go to the folder...
from the menu bar and paste it into the box that opens by pressing command + V. You won't see what you pasted a newline being included. Press return.
A folder named "LaunchDaemons" can open. If this is the case, press the combination of keys command-2 to select the display of the list, if it is not already selected.
There should be a column in the update Finder window. Click this title two times to sort the content by date with the most recent at the top. Please don't skip this step. Files that belong to an instance of VSearch will have the same date of change for a few minutes, then they will be grouped together when you sort the folder this way, which makes them easy to identify.
Step 3
In the LaunchDaemons folder, there may be one or more files with the name of this form:
com Apple.something.plist
When something is a random string, without the letters, different in each case.
Note that the name consists of four words separated by dots. Typical examples are:
com Apple.builins.plist
com Apple.cereng.plist
com Apple.nysgar.plist
There may be one or more items with a name of the form:
com.something.plist
Yet once something is a random string, without meaning - not necessarily the same as that which appears in one of the other file names.
These names consist of three words separated by dots. Typical examples are:
com.semifasciaUpd.plist
com.ubuiling.plist
Sometimes there are items (usually not more than one) with the name of this form:
com.something .net - preferences.plist
This name consists of four words (the third hyphen) separated by periods. Typical example:
com.jangly .net - preferences.plist
Drag all items in the basket. You may be prompted for administrator login password.
Restart the computer and empty the trash.
Examples of legitimate files located in the same folder:
com.apple.FinalCutServer.fcsvr_ldsd.plist
com Apple.Installer.osmessagetracing.plist
com Apple.Qmaster.qmasterd.plist
com Apple.aelwriter.plist
com Apple.SERVERD.plist
com Tether.plist
The first three are clearly not VSearch files because the names do not match the above models. The last three are not easy to distinguish by the name alone, but the modification date will be earlier than the date at which VSearch has been installed, perhaps several years. None of these files will be present in most installations of Mac OS X.
Do not delete the folder 'LaunchDaemons' or anything else inside, unless you know you have another type of unwanted software and more VSearch. The file is a normal part of Mac OS X. The "demon" refers to a program that starts automatically. This is not inherently bad, but the mechanism is sometimes exploited by hackers for malicious software.
If you are not sure whether a file is part of the malware, order the contents of the folder by date modified I wrote in step 2, no name. Malicious files will be grouped together. There could be more than one such group, if you attacked more than once. A file dated far in the past is not part of the malware. A folder in date dated Middle an obviously malicious cluster is almost certainly too malicious.
If the files come back after you remove the, they are replaced by others with similar names, then either you didn't start in safe mode or you do not have all the. Return to step 1 and try again.
Step 4
Reset the home page in each of your browsers, if it has been modified. In Safari, first load the desired home page, then select
▹ Safari preferences... ▹ General
and click on
Set on the current Page
If you use Firefox or Chrome web browser, remove the extensions or add-ons that you don't know that you need. When in doubt, remove all of them.
The malware is now permanently inactivated, as long as you reinstall it never. A few small files will be left behind, but they have no effect, and trying to find all them is more trouble that it's worth.
Step 5
The malware lets the web proxy discovery in the network settings. If you know that the setting was already enabled for a reason, skip this step. Otherwise, you should undo the change.
Open the network pane in system preferences. If there is a padlock icon in the lower left corner of the window, click it and authenticate to unlock the settings. Click the Advanced button, and then select Proxies in the sheet that drops down. Uncheck that Auto Discovery Proxy if it is checked. Click OK, and then apply.
Step 6
This step is optional. Open the users and groups in the system preferences and click on the lock icon to unlock the settings. In the list of users, there may be some with random names that have been added by the malware. You can remove these users. If you are not sure whether a user is legitimate, do not delete it.
-
Why antivirus always incompatible and disabled
3 anti-virus kaspersky, norton and symantec not compatible and disabled by Mozila Firefox 23
If the antivirus is disabled when it is connected to the internet my computer is vulnerable to attacks
M.Firefox allow antivrus?If it's on Firefox extensions, so this does not affect the operation of the main components of the security software, but only extensions (Firefox/tools > Modules > Extensions) that they add to Firefox needs an update.
-
Firefox updated to the latest version and disabled or deleted all the Add-ons. Always get Crash Reporter.
Firefox DO opens in Mode without failure.
A ran MalwareBytes and AVG and SuperAntiSpyware. No viruses.
Firefox is restored to its default state.
Check the missing files in windows using the File Checker Windows system at the command prompt. There are not.
I'm running Windows 7 Ultimate on a Dell XPS 400.
The rest of my system works very well except for Firefox.
GET CRASH REPORTER!
Frustrated now.I was told in a response to my post on this topic in Mozillazine [http://forums.mozillazine.org/viewtopic.php?f=38 & t = 2685611]
that Crash report that an update of Windows had caused the crash. I went to the list of all my Windows updates and remove all updates of the date on which this occurred (3/29) and rebooted and my Firefox browser works again! I couldn't believe it! Thank you for your kindness and your help in this matter.
Kind regards. -
I forgot my security question answer Apple ID and my recovery email address has since been deleted and disabled. How to get answers to security questions and or change my email recovery?
Go to https://getsupport.apple.com . Click on "see all of the products and services ', then 'More', then 'Apple ID', then 'other Apple ID subjects' then 'security issues forgotten Apple ID". If you have problems with this test of this form: https://www.apple.com/emea/support/itunes/contact.html
-
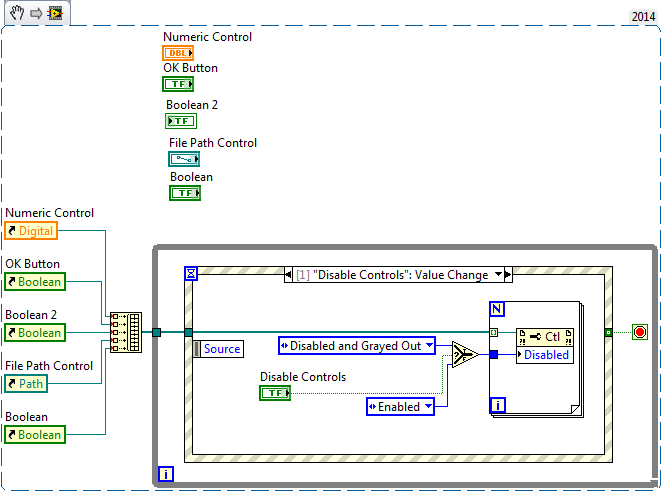
How to enable and disable the part of the "control panel".
I want to know if part of the control panel can be turned on and off by an external action, to use the mouse or a Boolean variable. Someone has an idea that help color? Thank you
Ricardo
You can disable cookies by using the node property and ownership "Disabled". You can create a tab control and disable the entire tab control that will disable all inside of it.
To do this programmatically, set up your code with a structure of the event and create an event when the user changes the value of a button or click the mouse.
See the example I did:
-
HP EliteBook 840 G2: How to enable and disable NFC on HP EliteBook 840 G2
Hello
1. Please help me how to activate and deactivate the NFC on HP EliteBook 840 G2?
2. what I have have Bluetooth activated on 930 Lumia and be paired with HP EliteBook 840 G2 if
I want to send the image of Nokia Lumia 930 file (Windows Phone 8.1) for HP EliteBook 840 G2 with
Windows 7 Enterprise 64-bit?
3. is it possible to transfer images between Windows 7 64 bit on HP EliteBook 840 G2 and 8.1 of Windows Phone?
Thanks a lot for any advice.
R,
Marek
Press the power button and press the ESC key to call the start menu.
Now, press the F10 key to access the BIOS.
Click on the tab advanced, as shown in the image below.
Under the heading device settings, click integrated device options.
NFC is activated when there is a check mark in the field of NFC and disabled when the tick is removed and the change is saved.
-
I visited a new client today and discovered that they are running a version of Microsoft Windows XP, I had never heard of, Black complete edition of Windows XP. What is black ultimate and what are its characteristics? Is this a legitimate copy of Windows?
Everything I read is not a legitimate copy. It's a pirated copy. I don't know about the features.
Jim
-
How to access the BIOS and disable hype-threading on xp
How to access the BIOS and disable hype-threading on xp
THXDuring the initial boot, you should see a brief message posted to press a specific key (usually the delete key) to access the BIOS. If there is an option to disable Hyper-Threading, you will need to find it. You can also see if there is a guide for your motherboard and the BIOS options.
Any reason, you need to disable?
J W Stuart: http://www.pagestart.com
-
Original title: sound problem
I've disabled all sounds and disabled my sound card. There is always a warning tone. Why?
Hello
When does this beep?
It probably comes from the speaker of your motherboard.
Listen to the PC (put close your ear) while producing the sound and then compare it with putting your ear near a speaker.
Tricky
Maybe you are looking for
-
You can play Pokémon go on iPad Pro?
Can you play Pokemon go on iPad Pro?
-
Satellite P300 - upgrade to larger hard drives and 7200 RPM?
I have a Satellite P300, model PSPCCA-01W073 (sold in Australia). Machine has two 320 GB of HARD drive. Yes, it's all up to 640 GB. I upgraded to Windows 7 OS and I have dual boot in to Linux Ubuntu. My job is editing/processing of multimedia files b
-
How to remove mac adware cleaner pop-up window
I have a pop up window whenever I am in google chrome, which says: "recommended download, install mac adware cleaner" now to protect our device mac malware, adware and other security threats. What is a real pop up or an adware? How can I get rid of h
-
I saved a game I played and now impossible to cancel the function. I don't want a game to be saved at all. I have tried leaving the saved game, but it never ask me for anything and the window closes without any possibility of 'give up' the game. Free
-
How can I make my items from smaller office? They are all real great.
All my desktop icons are real big. The resolution of the screen is ok, but all my shortcuts are enormous. I can't understand how to make them a normal size.