L2l VPN via TCP
Hello
Is someone can you please tell me if it is possible to configure a tunnel between two firewalls PIX 515E L2L over TCP?
Praveen
Praveen,
Cannot be used for Tunnels IPSEC Lan to Lan on the Pix.
You can use a feature called "Ipsec over TCP", but it is for only for the VPN Clients.
If you don't mind, could you share the reason for this type of requirement. Thank you!
I hope it helps.
Kind regards
Arul
Tags: Cisco Security
Similar Questions
-
VPN Client TCP connection to router IOS
Hello
I try to get a VPN client to connect via TCP to a router. I currently have the router put in place (and work) in using a VPN - UDP. Unfortunately one of the sites I visit will not allow VPN traffic outside of their firewall. I have searched all over the site of Cisco and can't find any information on the IOS configuration to accept TCP - VPN connections. I would like to change the TCP port 80, so my VPN traffic looks like just standard internet browsing my client firewall. Any links/pointer would be greatly appreciated.
Thanks in advance!
-Joe
Take a look at this:
http://www.Cisco.com/en/us/docs/iOS/12_2t/12_2t8/feature/guide/ftunity.html#wp1310210
http://www.Cisco.com/en/us/docs/iOS/12_2t/12_2t8/feature/guide/ftunity.html#wp1305478
http://www.Cisco.com/en/us/docs/iOS/12_2t/12_2t8/feature/guide/ftunity.html#wp1315635
Please rate if useful.
Concerning
Farrukh
-
L2l VPN tunnel is reset during the generate a new IPSec key
I have a tunnel VPN L2L that resets completely, start with Phase 1, at the expiration of the timer of the IPSec Security Association. Although there are several SAs, it always resets all of the tunnel.
I see the following in the log errors when this happens:
03/06/2013 12:54:41 Local7.Notice ipRemoved June 3, 2013 12:54:41 LKM-NVP-L2L-01: % 713050-5-ASA: Group = ipRemoved, IP = ipRemoved, completed for the ipRemoved peer connection. Reason: Peer terminate Proxy remote n/a, Proxy Local n/a
03/06/2013 12:54:41 Local7.Notice ipRemoved June 3, 2013 12:54:41 LKM-NVP-L2L-01: % 713259-5-ASA: Group = ipRemoved, IP = ipRemoved, Session is be demolished. Reason: The user has requested
03/06/2013 12:54:41 Local7.Warning ipRemoved June 3, 2013 12:54:41 LKM-NVP-L2L-01: % ASA-4-113019: Group = ipRemoved username = ipRemoved, IP = ipRemoved, disconnected Session. Session type: IKE, duration: 4 h: 00 m: 06 s, xmt bytes: 260129, RRs bytes: 223018, reason: the user has requested
03/06/2013 12:55:33 Local7.Notice ipRemoved June 3, 2013 12:55:33 LKM-NVP-L2L-01: % 713041-5-ASA: IP = ipRemoved, IKE initiator: New Phase 1, Intf inside, IKE Peer ipRemoved local Proxy 204.139.127.24 address, address remote Proxy 156.30.21.200, Card Crypto (L2LVPN)
03/06/2013 12:55:33 Local7.Notice ipRemoved June 3, 2013 12:55:33 LKM-NVP-L2L-01: % 713119-5-ASA: Group = ipRemoved, IP = ipRemoved, PHASE 1 COMPLETED
Local7.Notice ipRemoved June 3, 2013 03/06/2013-12:55:33 12:55:33 LKM-NVP-L2L-01: % 713049-5-ASA: Group = ipRemoved, IP = ipRemoved, the security negotiation is complete for LAN - to - LAN Group (ipRemoved) initiator, Inbound SPI = 0x9213bdc9, outbound SPI = 0x1799a099
03/06/2013 12:55:33 Local7.Notice ipRemoved June 3, 2013 12:55:33 LKM-NVP-L2L-01: % 713120-5-ASA: Group = ipRemoved, IP = ipRemoved, PHASE 2 COMPLETED (msgid = b8a47603)
03/06/2013 13:02:11 Local7.Notice ipRemoved June 3, 2013 13:02:11 LKM-NVP-L2L-01: % 713041-5-ASA: Group = ipRemoved, IP = ipRemoved, IKE initiator: New Phase 2, Intf inside, IKE Peer ipRemoved local Proxy 204.139.127.71 address, address remote Proxy 156.30.21.200, Card Crypto (L2LVPN)
Local7.Notice ipRemoved June 3, 2013 03/06/2013-13:02:11 13:02:11 LKM-NVP-L2L-01: % 713049-5-ASA: Group = ipRemoved, IP = ipRemoved, the security negotiation is complete for LAN - to - LAN Group (ipRemoved) initiator, Inbound SPI = 0x93f9be6c, outbound SPI = 0x1799a16d
03/06/2013 13:02:11 Local7.Notice ipRemoved June 3, 2013 13:02:11 LKM-NVP-L2L-01: % 713120-5-ASA: Group = ipRemoved, IP = ipRemoved, PHASE 2 COMPLETED (msgid = 1f6c9acd)
Any thoughts on why she would do that?
Thank you.
Jason
Hello
Both the log messages seems to suggest that the remote end is closed/compensation connection.
Is this a new connection that suffer from this problem or has it started on an existing connection?
The Cisco documentation associated with the Syslog messages does really not all useful information about these log messages.
I guess that your problem is that TCP by L2L VPN connections suffer from the complete renegotiations of the L2L VPN.
I wonder if the following configuration can help even if this situation persists
Sysopt preserve-vpn-flow of connection
Here is a link to the order of the ASA reference (8, 4-8, 6 software) with a better explanation of this configuration.
http://www.Cisco.com/en/us/docs/security/ASA/asa84/command/reference/S8.html#wp1538395
It is not enabled by default on the SAA.
Hope this helps
-Jouni
-
flatten to a string for sending via TCP/IP contains CRLF characters
Hello
I use a function 'flatten in string' to send data via TCP/IP.
To minimize delays, I use CRLF mode so that the receive function returns as soon as it receives a sequence CRLF (stop character).
I noticed that every now and then that part of the data is transmitted as the flattened string itself sometimes (but rarely) contains CRLF characters.
I was wondering if this is a correct behavior, or if I'm missing something. I expected to flatten to string in order to get channels pure ASCII without special characters.Now I must first parse the string replace the CRLF characters of some known series of characters and do the opposite to the front desk and hope that that particular sequence never occurs.
Any comment is appreciated,
Manu
mkdieric wrote:
I expected to flatten to string in order to get channels pure ASCII without special characters.
I don't know why you would think this. A CR or LF is no more extraordinary than any character. In addition, the string you out is not "ASCII" and has never been--check the documentation. The output is entirely dependent on the entry, and it is perfectly possible to get a (hex 13) CR followed by a LF (10 hex) if the entry would produce flattened data which means that.
A better method, in my opinion, is to precede that you send with the number of bytes to wait. Then beside reception read you a fixed number of bytes for the numerical value that indicates the number of bytes comes, and read you this amount. The examples provided with LabVIEW show you this method.
-
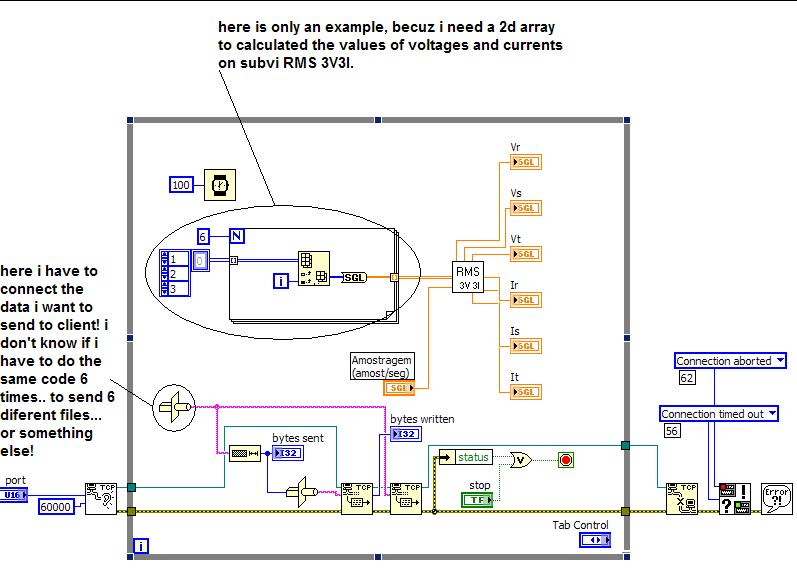
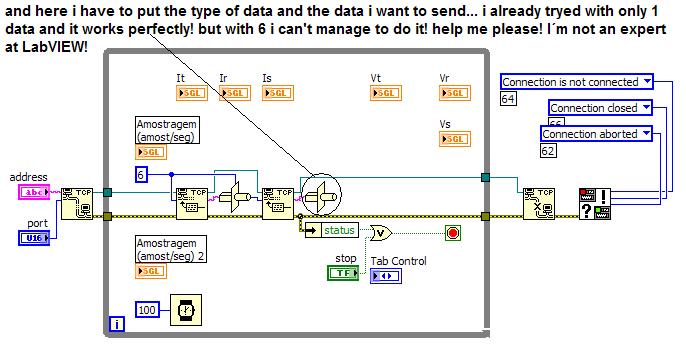
How to send data then other more via tcp
Well guys, I am having some problems with it
I have a program to labview that record and show for me in a chart, the voltages and currents
now, I want to do a software... that I can follow the datas of my company...
so I do a server/client via tcp
and I've managed to pass data from one... but I need pass 6 data both
I tried to make a tab control...
But if I put the data received as a tab control
the values do not change x)
I put the server code and client...
so maybe if you guys see
you will understand!
Thank you guys!
-
The reading of data acquisition via tcp
Hello
I am building an application that controls an acquisition of data via tcp.
I have a JAVA program that communicate with labview, give a command and data acquisition starts. (So, I read the correct Java data at Labview)
My problem is if I try to read data acquired by data acquisition (continuous sample 1 k samples), I've read strange values.
I transform of double values in the string and send it via tcp.
How can I read it in Java? What type of socket should I use? What is a rate problem?
I also tried to transform small/big-endian byte order, but it does not work.I enclose a sketch of this part of the application.
Please help me, I try for 2 weeks!
Thank you all...I find the solution in the lavag forum.
I post here, if it can help someone.http://lavag.org/topic/16359-sending-LabVIEW-data-via-TCP/page__pid__99983#entry99983
-
Connect two targets in real time via TCP/IP
Hello everyone
I need to connect two targets of RT on TCP/IP protocols
I have two sbRIO Council related to a single host PC through an Ethernet router
and I have two IP address of these two targets, how do I RT - RT ping using the TCP/IP protocol...
Thank you
Syed irfan
irfan789 wrote:
As I am with RT if the IP address of the two targets has a role to play in this communication via TCP/IP
In order to open a TCP connection, you must provide the IP address of the remote computer. It does not matter what operating system, the remote computer is running. If that does not meet your question, so I don't understand what you're asking.
-
Hi all
I am trying to write a very simple application that will transfer data via TCP to another computer running a TCP server. (About 3K of data)
Although I followed the code example in the 4.6 Java Development Guide, page 101, on the use of the socket connections, (http://na.blackberry.com/eng/deliverables/3802/development.pdf) I've been running into questions that data transfer crashes after an undetermined number of bytes.
Someone at - it sample code to open a TCP connection and sending the data? This seems to be a very common thing to do, so I don't know what is my problem.
Thank you
DanielI'm not going to answer your first question, I think that we must resolve this problem before you watch something else (and I suspect they are all related).
I would almost guarantee that you run your socket send and receive on the thread of events. The thread of events, that's what treats your interaction Menu, trackball movement etc. If you perform a long running or blocking on this Thread, your device will freeze.
Look at the demo of Socket and move your network of transformation to a Thread separate, as does the sample.
To confirm that the treatment of your socket is executed on the event Thread, you can add this code, run it in the Simulator and watch it in the output window of the debugger and set a breakpoint on the line to System.out.
If {(Application.getApplication (), isEventThread ())}
System.out.println ("running in the thread of events and should not be");
}
-
Hi all
My apologies if this is a trivial question, but I spent considerable time trying to search and had no luck.
I encountered a problem trying to set up a temporary L2L VPN from a Subscriber with CISCO2911 sitting behind the router of the ISP of an ASA. ISP has informed that I can't ignore their device and complete the circuit Internet on the Cisco for a reason, so I'm stuck with it. The Setup is:
company 10.1.17.1 - y.y.y.y - router Internet - z.z.z.z - ISP - LAN - 10.x.x.2 - XXX1 - ASA - 10.1.17.2 - CISCO2911 - 10.1.15.1 LAN
where 10.x.x.x is a corporate LAN Beach private network, y.y.y.y is a public ip address assigned to the external interface of the ASA and the z.z.z.z is the public IP address of the ISP router.
I have forwarded ports 500, 4500 and ESP on the ISP router for 10.1.17.2. The 2911 config attached below, what I can't understand is what peer IP address to configure on the SAA, because if I use z.z.z.z it will be a cause of incompatibility of identity 2911 identifies himself as 10.1.17.2...
! ^ ^ ^ ISAKMP (Phase 1) ^ ^ ^!
crypto ISAKMP policy 5
BA 3des
md5 hash
preshared authentication
Group 2
lifetime 28800
isakmp encryption key * address no.-xauth y.y.y.y! ^ ^ ^ IPSEC (Phase 2) ^ ^ ^!
crymap extended IP access list
IP 10.1.15.0 allow 0.0.0.255 10.0.0.0 0.255.255.255
Crypto ipsec transform-set ESP-3DES-SHA 3rd-esp esp-sha-hmac
card crypto 1 TUNNEL VPN ipsec-isakmp
defined peer y.y.y.y
game of transformation-ESP-3DES-SHA
match the address crymapGi0/2 interface
card crypto VPN TUNNELHello
debug output, it seems he's going on IPSEC States at the tunnel of final bud QM_IDLE's.
What I noticed in your configuration of ASA box, it's that you're usig PFS but not on 2911 router.
So I suggest:
no card crypto OUTSIDE_map 4 don't set pfs <-- this="" will="" disable="" pfs="" on="" asa="">
Then try tunnel initiate.
Kind regards
Jan
-
ASA with several L2L VPN Dynamics
I have an ASA 5510 such as VPN, used for about 30 L2L - VPN concentrator.
I need also some VPN L2L with dynamic peer remote.
While the configuration for a single dyn - VPN is quite simple (as described in several examples), how can I configure the ASA in the case of many dyn - VPN?
Basically, all the VPN - dyn must use the same PSK (the DefaultL2LGroup).
But using the "aggressive" on the remote peer mode, I could use a different PSK for every dyn - VPN:
tunnel-group ipsec-attributes ABCD
pre-shared-key *.
This configuration is correct?
Best regards
Claudio
Hello
Maybe the solutions provided in the following document may also be an option to configure multiple dynamic VPN L2L connections on the SAA
http://www.Cisco.com/en/us/products/ps6120/products_tech_note09186a0080bc7d13.shtml
Hope this helps
-Jouni
-
Hello
I think that vpn via nat is 'enabled' in the 6.3.1 software for the pix? I have problems to run. Can someone give me directions, including everything I need to know about the router?
I guess that everything that I have to do is create a static nat from 1 to 1 of the legal IP outside the pix outside IP router? Then configure the vpn as usual to accept vpn as usual (I use the 4.0.1 cisco client).
I'd appreciate any help.
Thanks for your time
Andy
I think that you need to configure the NAT-Traversal, the command to do this is isakmp nat-traversal]
NAT - T can be enabled or disabled:
By default? OFF for site to site tunnels
By default? We'RE for hardware and software VPN clients
-
Hello Experts from Cisco,
I run in trouble with one of my l2l ipec vpn between an asa 5510 and 5520 cisco running version 8.2.2.
Our existing l2l VPN are connected fine and work very well. Currently SITE a (10.10.0.0/16) connects to the SITE B (10.20.0.0/16). SITE A connects to SITE C (10.100.8.0/21). These are OK.
What is a failure is when I try to connect SITE B to SITE C. The tunnel coming up and phase 1 and 2 complete successfully. However, even if in the course of execution: ' entry packet - trace within the icmp 10.20.8.2 8 0 detailed 10.100.8.1 ' I get the following:
Phase: 10
Type: VPN
Subtype: encrypt
Result: DECLINE
Config:
Additional information:
Direct flow from returns search rule:
ID = 0xad1c4500, priority = 70, domain = encrypt, deny = false
hits = 609, user_data = 0 x 0, cs_id = 0xad1c2e10, reverse, flags = 0 x 0 = 0 protocol
SRC ip = 10.20.0.0, mask is 255.255.0.0, port = 0
DST ip = 10.100.8.0, mask is 255.255.248.0, port = 0, dscp = 0 x 0
I noticed that when the tunnel came, the road to 10.100.8.0/21 was added in the routing table and cyrpto what ACL has not been applied on the SAA remote. I added the route manually but cannot get the cryto ACL to apply.
Useful info:
C SITE
the object-group NoNatDMZ-objgrp network
object-network 10.10.0.0 255.255.0.0
object-network 10.10.12.0 255.255.255.0
network-object 10.20.0.0 255.255.0.0
access extensive list ip 10.100.8.0 outside_30_cryptomap allow 255.255.248.0 10.20.0.0 255.255.0.0
IP 10.100.8.0 allow Access - list extended sheep 255.255.248.0 sheep-objgrp object-group
card crypto outside_map 30 match address outside_30_cryptomap
card crypto outside_map 30 peers set x.x.x.x
crypto outside_map 30 card value transform-set ESP-AES256-SHA
crypto outside_map 30 card value reverse-road
outside_map interface card crypto outside
SITE B
object-group network sheep-objgrp
object-network 10.10.0.0 255.255.0.0
object-network 10.21.0.0 255.255.0.0
object-network 10.10.12.0 255.255.255.0
network-object 10.100.8.0 255.255.248.0
IP 10.20.0.0 allow Access - list extended sheep 255.255.0.0 sheep-objgrp object-group
allow outside_50_cryptomap to access extended list ip 10.20.0.0 255.255.0.0 10.100.8.0 255.255.248.0
card crypto outside_map 50 match address outside_50_cryptomap
game card crypto outside_map 50 peers XX. XX. XX. XX
outside_map crypto 50 card value transform-set ESP-AES256-SHA
outside_map crypto 50 card value reverse-road
outside_map interface card crypto outside
I've been struggling with this these days. Any help is very appreciated!
Thank you!!
Follow these steps:
no card outside_map 10-isakmp ipsec crypto dynamic outside_dyn_map
map outside_map 65535-isakmp ipsec crypto dynamic outside_dyn_map
clear crypto ipsec its SITE_B_Public peer
Try again and attach the same outputs.
Let me know.
Thank you.
-
Hi all!
I have a question about L2L VPN and NAT.
Can I set up the VPN tunnel between two ASAs or routers using the NAT translation from within the private IP addresses to a single public IP address outside the interface and then implement interesting crypto with the source of the public IP address and the destination of the remote private network on the other end (also ASA). For example, I want to translate a private network to the public ip address at one end and use the VPN tunnel with a public IP address as the source. Policy-NAT is not an option, because we really do not want to provide any IP address to the remote end, and IP addresses of the remote end can overlap with our end.
Thank you!
Hello
You can definitely set up an IPSec tunnel between two devices in the translation of your subnet in a single public IP address. You just create the translation and as you mentioned define interesting traffic using the public IP address.
This is exactly what we call political NAT, I don't understand why you say that NAT policy is not an option. Perhapps you misunderstood concept NAT policy or I misunderstood your question.
For example, assuming that the LAN private at your side is 172.16.1.0/24, the remote subnet is 192.168.150.0/24, and that the public IP address that you want to use is 200.200.200.200 your NAT config should look like this:
access-list 199 permit ip 172.16.1.0 255.255.252.0 192.168.150.0 255.255.255.0
Global (outside) 6 200.200.200.200
NAT (inside) 6 access-L199
Which would be NAT traffic to the public IP address only when the traffic matches the ACL.
Your ACL crypto should then be something like
cryptomap list of allowed access host ip 200.200.200.200 192.168.150.0 255.255.255.0
That would hide your address real and all they see is the public IP address you give them. Note that since the NAT takes place on your side your side will be able to raise the tunnel.
I hope this helps.
Raga
-
How to move the ASA of IPSEC VPN via UDP to TCP
I have a client who has a remote desktop with 2 PCs than VPN in to their location of HQ. Previously, two computers where in different places now that they are in the same place. Both PC's are able to successfully establish a VPN connection to the CA by using the Version of the Client VPN Cisco 5.0.07.0290, but only 1 system actually passes the traffic and is able to access the resources at Headquarters.
I asked another engineer, and they said ' you must configure IPSEC over TCP or use Anyconnect to have multiple clients behind the same PAT' public ed remote ip address... ". ». I would go with IPSEC for TCP connection, so I won't have to uninstall the old client and go through the process of installing the AnyConnect client. Here is the configuration of the ASA 5505 thanks in advance for any help.
CLIENTASA # sh run
: Saved
:
ASA Version 7.2 (4)
!
hostname CLIENTASA
domain client.local
activate 72LucMgVuxp5I3Ox encrypted password
2KFQnbNIdI.2KYOU encrypted passwd
names of
!
interface Vlan1
nameif inside
security-level 100
IP 192.168.1.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
IP x.x.x.x where x.x.x.x
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
passive FTP mode
DNS server-group DefaultDNS
domain client.local
standard SPLIT-TUNNEL access list permit 192.168.1.0 255.255.255.0
outside_in list extended access permit tcp any any eq smtp
outside_in list extended access permit tcp any any eq www
outside_in list extended access permitted tcp everything any https eq
access-list extended sheep allowed ip 192.168.1.0 255.255.255.0 10.99.99.0 255.255.255.0
pager lines 24
Enable logging
recording of debug console
debug logging in buffered memory
asdm of logging of information
Within 1500 MTU
Outside 1500 MTU
pool local IP VPN-10.99.99.100 - 10.99.99.200
ICMP unreachable rate-limit 1 burst-size 1
ASDM image disk0: / asdm - 523.bin
don't allow no asdm history
ARP timeout 14400
Global 1 interface (outside)
NAT (inside) 0 access-list sheep
NAT (inside) 1 192.168.1.0 255.255.255.0
NAT (inside) 1 0.0.0.0 0.0.0.0
public static tcp (indoor, outdoor) interface www 192.168.1.2 netmask 255.255.255.255 www
public static tcp (indoor, outdoor) interface https 192.168.1.2 netmask 255.255.255.255 https
public static tcp (indoor, outdoor) interface smtp 192.168.1.2 netmask 255.255.255.255 smtp
Access-group outside_in in external interface
Route outside 0.0.0.0 0.0.0.0 x.x.x.x 1
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
AAA authentication enable LOCAL console
the ssh LOCAL console AAA authentication
Enable http server
http 192.168.1.0 255.255.255.0 inside
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Crypto ipsec transform-set esp-3des esp - esp-md5-hmac
Crypto dynamic-map VPNDYN 1 set transform-set esp-3des
vpn ipsec dynamic VPNDYN 65535-isakmp crypto map
vpn outside crypto map interface
crypto ISAKMP allow outside
crypto ISAKMP policy 100
preshared authentication
the Encryption
md5 hash
Group 2
life 86400
crypto ISAKMP policy 65535
preshared authentication
the Encryption
sha hash
Group 2
life 86400
Telnet 0.0.0.0 0.0.0.0 inside
Telnet timeout 5
SSH 0.0.0.0 0.0.0.0 inside
SSH 0.0.0.0 0.0.0.0 outdoors
SSH timeout 5
Console timeout 0
dhcpd dns 192.168.1.2
dhcpd outside auto_config
!
des-sha1 encryption SSL rc4 - md5
VPN-POLICY group policy interns
attributes of VPN-POLICY-group policy
value of server DNS 192.16.1.2
Split-tunnel-policy tunnelspecified
Split-tunnel-network-list value of SPLIT TUNNEL
admin PWpqnmc2BqJP9Qrb encrypted privilege 15 password username
password encrypted vpn2 ZBNuNQsIyyMGbOB2 user name
username vpn3 encrypted password 15c4LrPNccaj1Ufr
vpn1 fsQgwXwSLokX6hEU encrypted password username
tunnel-group CLIENTVPN type ipsec-ra
attributes global-tunnel-group CLIENTVPN
address VPN-POOL pool
Group Policy - by default-VPN-POLICY
IPSec-attributes tunnel-group CLIENTVPN
pre-shared-key *.
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the rsh
inspect the rtsp
inspect esmtp
inspect sqlnet
inspect the skinny
inspect sunrpc
inspect xdmcp
inspect the sip
inspect the netbios
inspect the tftp
!
global service-policy global_policy
context of prompt hostname
Cryptochecksum:41bd95c164a63bb26b01c109ab1bd68a
: end
CLIENTASA #.
Hello
You can try adding
Crypto isakmp nat-traversal 30
And test connections
I think that you need to add to use the TCP protocol
Crypto isakmp ipsec-over-tcp 10000
You will also need to change the Transparent tunnel setting on the profile of Client VPN software to use TCP instead of option of NAT/PAT.
-Jouni
-
ASA L2L VPN UP with incoming traffic
Hello
I need help with this one, I have two identical VPN tunnel with two different customers who need access to one of our internal server, one of them (customer) works well, but the other (CustomerB) I can only see traffic from the remote peer (ok, RX but no TX). I put a sniffer on ports where the ASA and the server are connected and saw that traffic is to reach the server and traffic to reach the ASA of the server then nothing...
See the result of sh crypto ipsec his below and part of the config for both clients
------------------
address:
local peer 100.100.100.178
local network 10.10.10.0 / 24
local server they need access to the 10.10.10.10
Customer counterpart remote 200.200.200.200
Customer remote network 172.16.200.0 / 20
CustomerB peer remote 160.160.143.4
CustomerB remote network 10.15.160.0 / 21
---------------------------
Output of the command: "SH crypto ipsec its peer 160.160.143.4 det".
address of the peers: 160.160.143.4
Tag crypto map: outside_map, seq num: 3, local addr: 100.100.100.178outside_cryptomap list of allowed access host ip 10.10.10.10 10.15.160.0 255.255.248.0
local ident (addr, mask, prot, port): (10.10.10.10/255.255.255.255/0/0)
Remote ident (addr, mask, prot, port): (10.15.160.0/255.255.248.0/0/0)
current_peer: 160.160.143.4#pkts program: encrypt 0, #pkts: 0, #pkts digest: 0
#pkts decaps: 827, #pkts decrypt: 827, #pkts check: 827
compressed #pkts: 0, unzipped #pkts: 0
#pkts uncompressed: 0, comp #pkts failed: 0, #pkts Dang failed: 0
success #frag before: 0, failures before #frag: 0, #fragments created: 0
Sent #PMTUs: 0, #PMTUs rcvd: 0, reassembly: 20th century / of frgs #decapsulated: 0
#pkts not his (send): 0, invalid #pkts his (RRs): 0
#pkts program failed (send): 0, #pkts decaps failed (RRs): 0
#pkts invalid prot (RRs): 0, #pkts check failed: 0
invalid identity #pkts (RRs): 0, #pkts invalid len (RRs): 0
#pkts incorrect key (RRs): 0,
#pkts invalid ip version (RRs): 0,
replay reversal (send) #pkts: 0, #pkts replay reversal (RRs): 0
#pkts replay failed (RRs): 0
#pkts min frag mtu failed (send): bad frag offset 0, #pkts (RRs): 0
#pkts internal err (send): 0, #pkts internal err (RRs): 0local crypto endpt. : 100.100.100.178, remote Start crypto. : 160.160.143.4
Path mtu 1500, fresh ipsec generals 58, media, mtu 1500
current outbound SPI: C2AC8AAESAS of the esp on arrival:
SPI: 0xD88DC8A9 (3633170601)
transform: esp-3des esp-md5-hmac no compression
running parameters = {L2L, Tunnel}
slot: 0, id_conn: 5517312, crypto-card: outside_map
calendar of his: service life remaining (KB/s) key: (4373959/20144)
Size IV: 8 bytes
support for replay detection: Y
Anti-replay bitmap:
0xFFFFFFFF to 0xFFFFFFFF
outgoing esp sas:
SPI: 0xC2AC8AAE (3266087598)
transform: esp-3des esp-md5-hmac no compression
running parameters = {L2L, Tunnel}
slot: 0, id_conn: 5517312, crypto-card: outside_map
calendar of his: service life remaining (KB/s) key: (4374000/20144)
Size IV: 8 bytes
support for replay detection: Y
Anti-replay bitmap:
0x00000000 0x00000001-The configuration framework
ASA Version 8.2 (1)
!
172.16.200.0 customer name
name 10.15.160.0 CustomerB
!
interface Ethernet0/0
nameif outside
security-level 0
IP 100.100.100.178 255.255.255.240
!
interface Ethernet0/1
nameif inside
security-level 100
10.10.10.0 IP address 255.255.255.0
!
outside_1_cryptomap list extended access allowed host ip 10.10.10.10 customer 255.255.240.0
inside_nat0_outbound_1 list extended access allowed host ip 10.10.10.10 customer 255.255.240.0
inside_nat0_outbound_1 list extended access allowed host ip 10.10.10.10 CustomerB 255.255.248.0
outside_cryptomap list extended access allowed host ip 10.10.10.10 CustomerB 255.255.248.0
NAT-control
Overall 101 (external) interface
NAT (inside) 0-list of access inside_nat0_outbound_1
NAT (inside) 101 0.0.0.0 0.0.0.0
Route outside 0.0.0.0 0.0.0.0 100.100.100.177
Route inside 10.10.10.0 255.255.255.0 10.10.10.254 1
Crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
Crypto ipsec transform-set ESP-DES-SHA esp - esp-sha-hmac
Crypto ipsec transform-set ESP-DES-MD5 esp - esp-md5-hmac
Crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
Crypto ipsec transform-set ESP-AES-256-SHA 256 - aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-SHA aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-MD5-esp - aes esp-md5-hmac
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
Crypto ipsec transform-set ESP-3DES-MD5-esp-3des esp-md5-hmac
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 pfs Group1 set
Crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 value transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA MD5-ESP-3DES ESP-DES-SHA ESP-DES-MD5
card crypto outside_map 1 match address outside_1_cryptomap
card crypto outside_map 1 set pfs
peer set card crypto outside_map 1 200.200.200.200
card crypto outside_map 1 set of transformation-ESP-3DES-SHA
card crypto outside_map 3 match address outside_cryptomap
peer set card crypto outside_map 3 160.160.143.4
card crypto outside_map 3 game of transformation-ESP-3DES-MD5
outside_map card crypto 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
outside_map interface card crypto outside
crypto ISAKMP allow outside
crypto ISAKMP policy 10
preshared authentication
3des encryption
md5 hash
Group 2
life 86400
crypto ISAKMP policy 20
preshared authentication
3des encryption
sha hash
Group 2
life 86400
crypto ISAKMP ipsec-over-tcp port 10000
attributes of Group Policy DfltGrpPolicy
Protocol-tunnel-VPN IPSec svc
internal customer group strategy
Customer group policy attributes
Protocol-tunnel-VPN IPSec svc
internal CustomerB group strategy
attributes of Group Policy CustomerB
Protocol-tunnel-VPN IPSec
tunnel-group 160.160.143.4 type ipsec-l2l
tunnel-group 160.160.143.4 General-attributes
Group Policy - by default-CustomerB
IPSec-attributes tunnel-group 160.160.143.4
pre-shared key xxx
tunnel-group 200.200.200.200 type ipsec-l2l
tunnel-group 200.200.200.200 General attributes
Customer by default-group-policy
IPSec-attributes tunnel-group 200.200.200.200
pre-shared key yyy
Thank you
A.
Hello
It seems that the ASA is not Encrypting traffic to the second peer (However there is no problem of routing).
I saw this 7.x code behaviors not on code 8.x
However you can do a test?
You can change the order of cryptographic cards?
card crypto outside_map 1 match address outside_cryptomap
peer set card crypto outside_map 1 160.160.143.4
map outside_map 1 set of transformation-ESP-3DES-MD5 crypto
card crypto outside_map 3 match address outside_1_cryptomap
card crypto outside_map 3 set pfs
peer set card crypto outside_map 3 200.200.200.200
card crypto outside_map 3 game of transformation-ESP-3DES-SHA
I just want to see if by setting the peer nonworking time to be the first, it works...
I know it should work the way you have it, I just want to see if this is the same behavior I've seen.
Thank you.
Federico.
Maybe you are looking for
-
Re: Satellite L650 - 15G - controller PCI required network driver
Hello Sometimes I reinstall windows 7 as my hard drive internal has been corrupted. If I want to install the drivers manually. I use the Satellite L650-15 G and Windows 7 64 bit operating system. While checking the Device Manager, I see an error disp
-
I have 1.4.1. My phone has not saved since March 5, even if it is set to back up every day. When I try to save manually the phone just chugs away with the message "preparation". I tried to disable the backup, but once again it just chugs away and is
-
BlackBerry smartphone WiFi HotSpot connection
Dear BlackBerry community I had my BBTorch 9800 OS6 over a year now, which is a fantastic phone that complements any work that I do, that I use my phone as a modem. I find that sometimes I can have text, but it puts pressure on connection cards, when
-
APEX 5 treatment of automatic line (DML) update fails
Hi allI need help because it seems I'm missing something to get this working:-J' have a page with a form that contains editable elements and some hidden items.-J' have a button on the same page, open a modal dialog box.-the modal dialog box contains
-
How can I make my evolutionary Flash movie?
Hello worldI'll put a small portfolio that uses the 3D so I need to put it into Flash. However, I want to be a little sensitive to the device and want to know how I can make the overall size of the evolutionary framework. How can I do this? It must b