NAT Firewall rules
Experts, please help understand the below statements of a firewall.
+++++++++++++++++++++++++++++++++++
SH running-config nat
NAT (inside) 0-list of access inside_nat0_outbound
NAT (inside) 1 0.0.0.0 0.0.0.0
SH running-config global
Global (dmz) 2 Test_PC - 10.11.2.3
Global 1 interface (outside)
allowed to Access-list inside_nat0_outbound line 34 extended ip Site2_Net 255.255.0.0 host WebServer_Test
_________________________________
I understand that nat (inside) is used for the sort of pat anything inside of the network to the public ip address on the external interface.
Correct me if wrong.
But I'm at loggerheads to understand with nat0 and the acl statement that refers to it.
Please suggest.
Thank you!
Q1: If the server was a way back to the ip address that is not translated then it won't hurt.
Q2: It applies to all traffic that hit the inside of the interface and matches the ACL.
PK
Tags: Cisco Security
Similar Questions
-
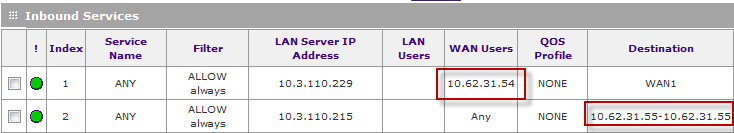
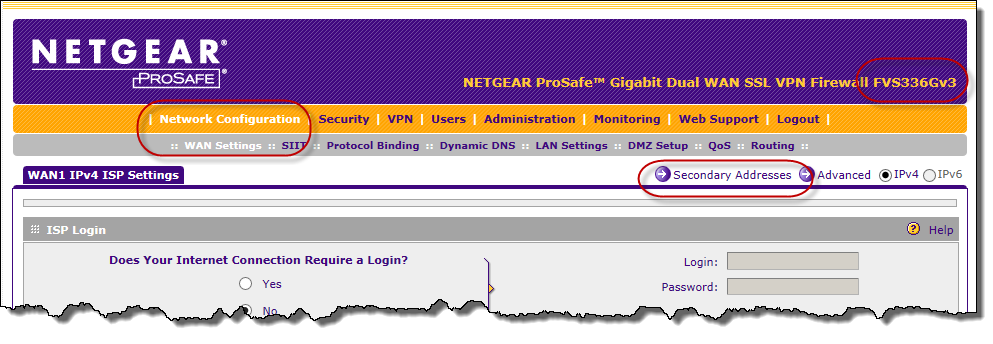
FVS336Gv3 multi-NAT inbound firewall rules does not
I have about 30 Netgear FVS338 and a few FVS336Gv2 routers in use. I use for firewall and provide multi-NAT between industrial machines and WAN. The configuration was changed on Gv3 models and I can't get an answer behind the firewall or router in the diagnostics page when you use the WAN address.
In the examples below the WAN is 10.62.
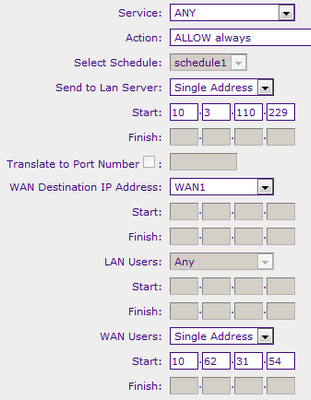
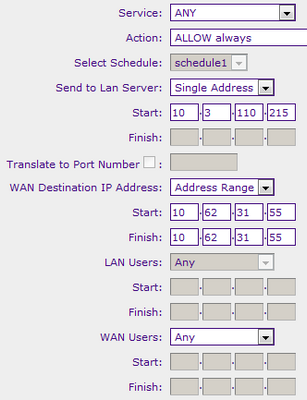
Figure 1. Two different devices with two different configuration options.
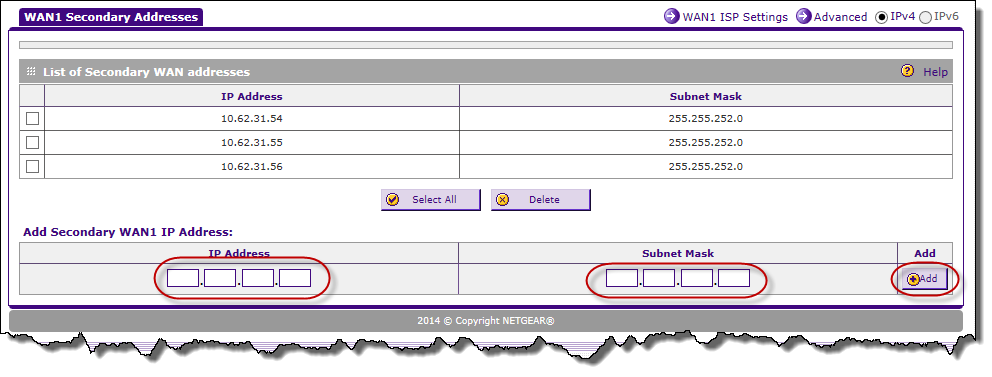
Figures 2 and 3. The first is bad - it would only connect from this address. Have I set up another correctly to the NAT WAN to LAN 10.3.110.215 address 10.62.31.55 address?
Q1: Is Figure 3 configured correctly?
Q2: Why is it forcing me to create a range of addresses? On the older routers, I had the opportunity to address.
Q3: Is anyone aware of any problem with this router?
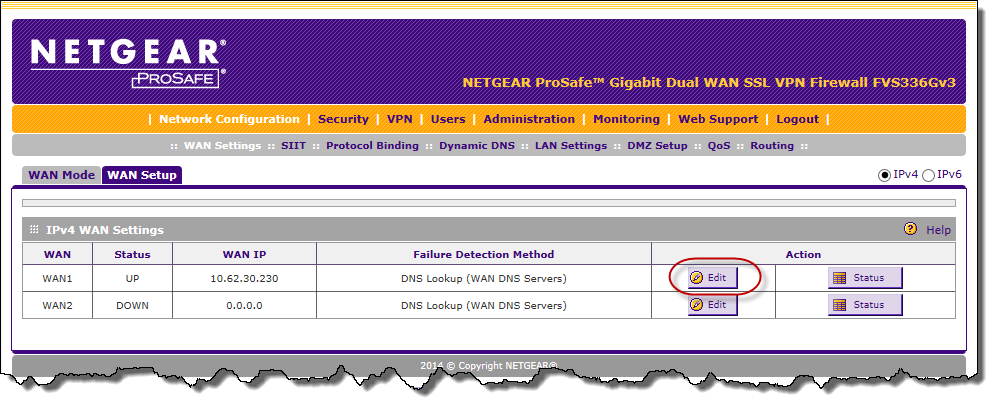
For anyone having the same problem, the FVS336Gv3 requires the manual addition of each new address WAN-side. He is buried in the menu structure:
Figure 1. Network configuration | WAN settings | WAN configuration. WAN1 - Edit.
Figure 2. Select the secondary addresses.
Figure 3. Add the required WAN addresses.
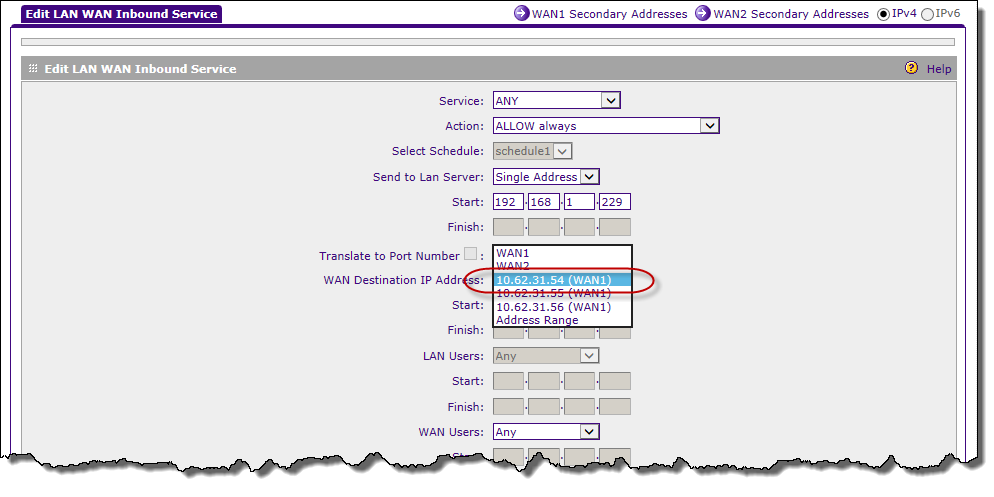
Now configure the inbound firewall rules:
Figure 4. Security | Firewall rules. Add or change. Note that the WAN secondary addresses are available in the drop-down list address WAN IP.
Password
There seems to be a problem with this router about the session timeout. I got them several times on the navigation menu and log on again and renavigate. Idle time-out is set to 90 minutes. I never saw this problem on routers earlier.
Also, note that the password field now has a limited character set. for example, it does not accept ' $'.
-
Hello world
Everyone can share codes sample detailed to set firewall rules and NAT for c# rules? I looked in the examples provided with the API, but I need more samples.
Here is the example of function to configure the firewall to VCloud API 5.1 for c# rule.
///
To create an object of type of firewall rule. This object is used to configure the firewall.
///
Name of the rule
Source IP address range
Firewall Type protocols
Type of firewall policy
Source port
Destiniation Ip address range.
Destination
Toggle rule
Turn logging on or off.
Firewall rule public static FirewallRuleType CreateFirewallRule (string name, string sourceIpRange, FirewallRuleTypeProtocols protocols, FirewallPolicyType action, sourcePort int, string destinationIpRange, int destinationPort, bool isEnabled, bool enableLogging)
{
Create an object of type firewall rule.
FirewallRuleType firewallRuleType = new FirewallRuleType();
Configure the setting was active user interface check box.
firewallRuleType.IsEnabled = isEnabled;
firewallRuleType.IsEnabledSpecified = true;
Set the description of the rule from the user interface name text box.
firewallRuleType.Description = name;
Normally, this is a port number.
firewallRuleType.SourcePortRange = sourcePort.ToString ();
firewallRuleType.SourcePortSpecified = true;
Configure the Protocol
Protocol of var = new FirewallRuleTypeProtocols();
Value of the Protocol Set object
Protocol. Items = new Object() {true};
Define the name of element
Protocol. ItemsElementName = new ItemsChoiceType [] {ItemsChoiceType.Tcp};
Protocol Set
firewallRuleType.Protocols = Protocol;
Set the destination IP address range
firewallRuleType.Item = destinationIpRange;
Normally this is the port number.
firewallRuleType.DestinationPortRange = destinationPort.ToString ();
Set Source Ip range
firewallRuleType.Item1 = sourceIpRange;
Configure logging check box UI activate recording.
firewallRuleType.EnableLogging = enableLogging;
firewallRuleType.EnableLoggingSpecified = true;
Configuration by default allow/deny action.
firewallRuleType.Policy = action. Value();
Return firewallRuleType;
}
-
RV320 firewall rules, VLAN and IP Aliasing
I bought and RV320 to replace our router SA520W. I have 2 servers SBS located on the VLANS separated.
The 320 RV is set with 1 WAN IP XX. XX. XX.43
SBS1 a IP internal of the XX. XX.16.2 on VLAN 1 port 1 on the router
SBS2 a IP internal of the XX. XX.2.2 on the VLAN 5 port on Router 2
On the old SA520W, I was able to configure alias IP XX. XX. XX.47 and XX. XX. XX.46 with firewall rules if 47 designated SBS1 and 46 stressed SBS2 to their respective ports.
How to make on the RV320 so I can have 2 isp server IP addresses to go through WAN1 to their VLAN respective?
SBaalman1,
The feature you're looking for is called NAT of individuals on most routers Cisco SMB. You can find under Setup.
-Marty
-
searching for NAT/Firewall/static routing tips
Hello
I am very new to vCloud network and security. I've read the documentation, but it can be confusing for me. I am attaching a schema to help provide a context for what I'm trying to achieve. Keep in mind that the IP address has been changed for security reasons. Address ranges are not accurate but for the context.
We have an org routed with a single VM VAPP, directly connected to the VCC-Net. It is a Linux server. We have a vShield edge device. There is no rule of firewall, NAT, static routes configured. Essentially of deployment costs. The owner of the server wants to be able to connect to a Linux repo for updates/etc.
For testing purposes, I have disabled the vShield firewall to allow all traffic through. from the Linux server, I was able to ping both addresses assigned to the border of vShield (192.168.1.1 and 10.10.16.17) but I couldn't ping 10.10.2.140. This leads me to believe the vShield Edge does not know how to route packets between 192.168.1.0/24 and 10.10.0.0/16.
I have read and what I'm gathering is that I have to configure NAT and firewall rules to achieve. I googled everything I can, and now I'm just confused. Can someone please give me some advice?
VShield Edge routing feature is similar to traditional router. By default, it can discover only directly attached networks and deliver packages, in this case 192.168.1.0/24 and 10.10.16.0/16 are direct networks. So if you need reach any other private network, we need to define a static route (it is not supported / configurable in vshield edges of dynamic routing since then). For Linux VM 192.168.1.10/24 join the public network, set a NAT NAT vShield edge rules and enable the appropriate firewall rules.
-
quick way to add multiple subnets of Server 2008 firewall rules?
I set up a firewall in windows server 2008. I need to add several subnets to a rule for inbound traffic, but it is making me add subnets one at a time. Is it possible to add several subnets simultaneously? I tried separating them by commas and add them via the GUI, but he wouldn't take it (he said that specify an address valid). Also if you have already entered a long list of subnets in a firewall rule is it possible to copy it to another firewall rule?
Hi Goatberg,
Your question of Windows Server 2008 is more complex than what is typically covered in the Microsoft Answers forums. It is better suited for the IT Pro TechNet public. Please post your question in the Technet Forum. You can follow the link to your question:
http://social.technet.Microsoft.com/forums/en-us/category/WindowsServer
-
"Error of SJphone: ' NAT/firewall: blocked".
"SJphone has stopped working a few months ago on 3 computers of x. error display: ' NAT/firewall: blocked".
Using Wireshark ISP said: "This shows that traffic is having issues is internal to your network." Please try to disable the firewall. "They have all been disabled.
Tried X-Lite and receive: registration error: 503 - no route to the host.
Could MS security updates caused the problem?
Any suggestion is appreciated.
Ultimately VoIPtalk could not solve the problem except by suggesting the X-Lite. That works fine!
-
RVL200 - SSL VPN and firewall rules
Forgive my ignorance, but I have been immersed in the configuration of this device RVL200 to allow Remoting SSL VPN to a customer site, sight unseen. I have the basics of the VPN set up in config, but now move the firewall rules. We want to block all internal devices to access the Internet, but I don't want to cripple the remote clients that will be borrowed by blocking their return via the SSL VPN traffic. This leads to my questions:
(1) a rule of DENIAL of coverage for all traffic OUTBOUND will prevent the primary function of the VPN (to allow the administration away from machines on the local network)?
(2) if the answer to #1 is 'Yes', what ports/services do I need to open the side LAN?
(3) building # 2, configuring authorized outbound rules apply only for VPN clients, rather than all the hosts on LAN?
(4) as the default INCOMING traffic rule is to REFUSE EVERYTHING, do I have to create a rule to allow the VPN tunnel, or guess that in the configuration of the router?
Here are some other details:
- The LAN behind the RVL200 is also isolated LAN in a manufacturing environment
- All hosts on this network have a static IP address on a single subnet.
- The RVL200 has been configured with a static, public IP on the WAN/INTERNET side.
- DHCP has been disabled on the RVL200
- Authentication to the device will use a local database.
- There is no such thing as no DNS server on the local network
- The device upstream of the RVL200 is a modem using PPPoE DSL, and the device has been configured for this setting.
- Several database of local users accounts were created to facilitate the SSL VPN access.
I worked with other aspects of it for a long time, but limited experience with VPN and the associated firewall rules and zero with this family of aircraft. Any help will be greatly appreciated.
aponikikay, there is no port forwarding necessary to the function of the RVL200 SSL - VPN.
Topic 1. That is not proven. It shouldn't do. The router should automatically make sure that the SSL - VPN router service is functional and accessible.
Re 2. No transfer necessary. In addition, never before TCP/UDP port 47 or 50 for VPN functions. The TCP 1723 port is used for PPTP. UDP 500 is used for ISAKMP. You usually also to transmit TCP/UDP 4500 port for IPSec encapsulation.
Let's not port 47. ERM is an IP protocol that is used for virtual private networks. It is a TCP or UDP protocol. GRE has 47 IP protocol number. It has nothing to do with TCP or UDP port 47. TCP and UDP are completely different protocols of free WILL.
It goes the same for 50: ESP is the payload for IPSec tunnels. ESP is the Protocol IP 50. It has nothing to do with TCP or UDP port 50.
'Transfer' of the GRE is configured with PPTP passthrough option.
'Transfer' of the ESP is configured with IPSec passthrough option.
-
How to import a TXT file in my list of firewall rules?
Good then I exported a list of firewall rules in a txt file. I then copied on some firewall rules. Then I saved the file txt and I wonder how I can re - import the txt file. Please note that I don't know of import policy...
UH I thank you for responding, but apparently you misunderstood what I meant... When I go into windows firewall, there is an option to export the list of rules I want to know is how to re - import this list of rules in because there is no other choice... If so how do I do?
Since I couldn't find a solution that I found something different that also works. I found a .bat file that you can put in the folder in which you want to block the program and it crashes all the exe files in this folder and all subfolders. You can even choose a fix before custom firewall rule... If any other person having this problem follow the instructions, I provide below:
Instructions (found online modified by me)Create a .bat file, named "addfwrs.bat" without the quotes using italic text, then follow the additional instructions:
off @echo
REM FILE OF ORDERS CREATED BY CHARLES DE HAVILLAND 20/02/2012
CLS
If '%1 'is' ' GOTO: norulename
RULENAME SET = %1
ECHO creating/starting of firewall rules for all files with the rulename of 'RULENAME '? % *.exe
ECHO.
ECHO.pause
Echo.
FOR /r %% in ("*.exe") Do (@echo %%d KB
("NETSH advfirewall firewall add rule name =" "% RULENAME-% ~ nxG" dir = program = "% G" action = 'block' enable = 'yes')
FOR /r %% in ("*.exe") Do (@echo %%d KB
("NETSH advfirewall firewall add rule name =" "% RULENAME-% ~ nxG" dir = program = "% G" action = 'block' enable = 'yes')
Echo.
ECHO done.
Echo.
GOTO: finish
: norulename
Echo error! -You have not specified a type Rulename - Addfwrs 'Rulename '.
Echo.
: Finishing
ECHO batch finished...Additional instructions:
Firewall Windows 7 works fine, but it's not easy to set up with several (very long) programs.
I watched for centuries, trying to find a way to block several files .exe to Windows 7 only once; It seems that the only method was to create my own batch (windows script) file.
I've added below for anyone to use / modify for their own purposes.
Run the commands below (addfwrs.bat) file, will create inbound AND outbound firewall rules that block all .exe files in your chosen folder and subfolders to access internet.
Very useful.
To use:(1) place addfwrs.bat in the folder in which you want to block .exe programs (it crashes all the programs exe in no matter what subfolders if you can place it in a folder without any exe it blocks)
exe in several subfolders both programs)(2) now run CMD as administrator.
(3) copy the new directory (eg. c:\Programs Files (x 86) \YourProg\) where you put the addfwrs.bat file
(4) paste it into the directory with "cd" CMD and a space before the directory (example: cd c:\Programs Files (x 86) \YourProg\) and press ENTER.
(5) now run the batch file by typing: addfwrs.bat "rulename" example: addfwrs "BLOCK_PROGRAM_NAME_HERE".
(Make sure there is no space in the rulename of the firewall rule, so use underscores as spaces.)N.B: It is important that you add a rulename firewall, so that you can identify the rules when adding to the firewall at a later date.
(6) follow the information on the screen, he will advise you what rules he is creating.
(7) check the Windows Firewall for new rules listed and you can then delete the addfwrs.bat file where you put it (it is necessary even if you can keep it somewhere for later).
Quite. Hope you find it useful, I certainly have!
Enjoy!N.B: The new rules contained in the bosom of your firewall (In/Out rules), change as and when you need.
-
[Solved] Research of firewall rule allowing Windows Update
The problem has been resolved here: https://social.technet.microsoft.com/Forums/en-US/62b9fd5c-10b2-4266-bc15-fcf3e79d20d4/solved-windows-firewall-rule-that-allows-windows-update?forum=w7itpronetworking
Everything down here is obsolete. (But you can read the true story about the virus of Bagel).
Someone at - it an outbound Windows Firewall rule allowing Windows Update?
Details.
Yesterday, I tried to run Windows Update. The rule of outbound firewall to allow Windows Update to get through, I added was:
Name: Allow Windows Update
Group:
Profile: Public
Activated: Yes
Action: allow
Program: %SystemRoot%\System32\wuapp.exe
Local address: no
Remote address: all
Protocol: all
The local railway: no
Remote port: any
Computers permit: allI got 10 updates to install and all 10 failed. The only way that they have all been able to fail is: '% SystemRoot%\System32\wuapp.exe' is the wrong program, OR "wuapp.exe" passes control to another program, I don't know.
Can anyone help me with this? I'll be forever grateful if you can.
Note that I had to fall back to the default settings (see 'Background', below) in order to succeed and who has not made me happy.
Background.
Despite what you think it means, "outbound connections (green check mark) that do not match a rule are allowed" (which is the default) means only, unless you went to the extreme penalty to create the blocking rules, the firewall is wide open for outbound - connections, essentially, you have no firewall for outbound connections. " That means, 1, if you have a Trojan horse on your computer that is looking to download his main-payload of viruses in your computer (see "A history of real virus", below), or 2, if you have a virus keylogger in your computer who wants to 'phone home' him make his Masters criminal of your online banking user name & password There is absolutely nothing to stop.
That's why I put my firewall: "(entry not red) outbound connections that do not match a rule are blocked".
A story real virus.
A couple of years ago, I visited a well known web site that had been hijacked - was - it cnet? I think so. The site seemed basically OK, but something made me shy away. I've left without clicking anything whatsoever. But the visitor of this site (with active javascript) transferred a Trojan horse in my computer (i.e. "Trojan", below).
Once it was in my computer, the Trojan horse, then went through my firewall, out - was my firewall zonealarm at this time? I think so - and downloaded Bagel, a key logger to rootkit.
I had no warning of the firewall as the Trojan horse used a well-known port that was wide open, and I had no antivirus warning because Bagel does not change any existing program. It uses the unallocated file space, patched itself in the initialization string, charged before the mode protected of windows at the next startup and reprogrammed the hardware memory to hide its presence in memory. It took me 2 months to discover Bagel and another 4 months to get rid of him. It was hell. My keyboard and mouse acted constantly upward. I didn't a bank online at this time. If I had, I'm sure that my account would have been cleaned up because that's what Bagel. It's a keylogger monitoring keyboard and browser waits to catch a connection to the Bank.
Details of Trojan.
The Trojan horse was a javascript function which ran automatically when the page is loaded. He created a table (similar to a mathematical object matrix) made up of identical over 1 million members of the group. Each Member of the Group was a short string of numbers. As it looped to add table-members, the Trojan horse later (in fractions of a second) overflowed the heap memory management hardware had allocated to my browser. That overflow has partially replaced the next higher segment in memory - which is called a "violation of the limits", and Yes, it is possible, if you position the base register just below the upper part of your segment and then use a large lag. There was a flaw in Windows that could not detect this type of violation of the limits and Bagel is designed to exploit this vulnerability. But the story does not stop there. To take control, the short string of numbers in a table-member of the "wrong"side of this segment limit had to be performed. Now, it of the roll of the dice that viruses are facing, but if the program that was partly crushed is always loaded in memory and running and if it executes the code at the bottom of its segment, then - Voila! -the virus takes control of the timeslice allocated to the program that was partly crushed. In other words, the program that was partly crushed no longer control, the virus is in control. So, what did the do Trojan horse? Completely in the background and without any idea for me, he went to a web site in Ukraine and downloaded the main payload of Bagel. How do I know all this? I looked at the javascript trojan and I disassembled - disassembly is as kind of decoding - the payload of Bagel (the rootkit) that I saved after I found some 6 months later. I still have the payload of Bagel sequestered in a zip in quarantine - in fact, I have a menagerie of dozens of viruses that I use to test antivirus programs.
Hi Mark,
Please keep us updated on the issue.
I ask that you continue to try the suggestions in this article because the information in the article is good for Windows 7 as well.
Please let us know the result.
-
SRP527W setting DHCP address and source firewall rules
In my quest to find a decent ADSL router for VoIP, I found the SRP527W and so far it has been the best performer of a range of boxes from netgear, thomson, and zyxel. However, I have two questions:
(1) how to troubleshoot DHCP leases on the LAN address
(2) how to specify source ip in the firewall rule
Note:
I currently have 1 computer on the LAN, VLAN1 interface
* 192.168.15.100
and
2 IP phones on the LAN, VLAN100 interface
* 192.168.100.100
* 192.168.100.101
Address three assigned by the DHCP server lease times with approximately 20 days.
I would like to repair the three devices DHCP leases, for example if some port forwarding rules can be made with confidence that the rules will not point to another device in the future.
from PVC0-> 192.168.15.100, Port 3389 for remote desktop
of PVC0-> 192.168.100.100 ex.port 5881 to int.port 80 for voip phone web-gui
from PVC0-> 192.168.100.101 ex.port 5882 to int.port 80 for voip phone web-gui
Ideally, I would like the rules to act like that, limiting myself only to access these ports (from my remote site)
PVC0 interface where the source is ip 12.34.56.78-> 192.168.15.100, Port 3389 for remote desktop
PVC0 interface where the source is ip 12.34.56.78-> 192.168.100.100 ex.port 5881 to int.port 80 for voip phone web-gui
PVC0 interface where the source is ip 12.34.56.78-> 192.168.100.101 ex.port 5882 to int.port 80 for voip phone web-gui
I hope that makes sense, I appreicate any help you can give.
Kind regards
Paul
Hi Paul,.
Thank you for using the Cisco support community.
With regard to two questions:
1. Yes - it is possible to configure static DHCP assignments. Use the DHCP Server rule configuration page and click the 'Show DHCP booking' button to assign.
2. Unfortunately, it is not possible to configure rules to address source for the SRP520 list. (This is possible on the SRP540 for further reading).
Kind regards
Andy
-
How to restore Windows Firewall rules to the default settings
* Original title: Win7 firewall rules have disappeared AND the HKLM\System\CurrentControlSet\services\SharedAccess\Defaults also went
How do you get these restored once a virus (or what did it) delete them? He has not only deleted the incoming power and outgoing traffic rules, he removed the DEFAULT values is that all the default settings of the Control Panel-Windows Firewall-restoration netsh uses to perform a restore from a known set of the default initial settings. If none of these options work, and I don't have another machine to get something to copy. This may not be so rare lately, like virus get more aggravating at the time. All viruses that wants to do a thorough job of * you off clearly would remove the default values as well as the current rules precisely to do evil to restore. There must be a way to get a standard set of default values for initial return, either: - a low-level - canonical list of repair operation - fixit utility - Microsoft has to right Win7?
Hello
I suggest you to upgrade in Place on Windows 7 and check.
How to perform an upgrade on the spot on Windows Vista, Windows 7, Windows Server 2008 & Windows Server 2008 R2
http://support.Microsoft.com/kb/2255099Important note: I would like to explain that the upgrade in place is a tool to repair the system. Thanks to the special upgrade process, we will be able to repair the system. The upgrade in place will not affect the settings like photos, movies, documents, etc. that are saved on the computer. However, it is recommended that you first back up your important information and files of other partitions or other disks.
For more information, see the link.
Reset the default settings in the Windows Firewall with advanced security
Please post back with the results and we will be happy to help you further.
-
In my windows7 when I migrated to the task force to the area, crashed by the firewall. And also it does not show in the services. In the firewall rules of incoming and outgoing traffic is missing.
Hello arjunpottekkad,
It is disheartening to know that have problems you with the firewall. As I understand it the incoming and outgoing traffic rules are missing from the firewall.
The question you posted would be better suited in the TechNet Forums . I would recommend posting your query in the TechNet Forums. You can follow the link to your question:
Answer to us if you are having problems with the Windows Firewall or any other problem of Windows, and I'd be happy to help you again and try to correct the problem as soon as possible.
Good day!
Hope this information helps.
-
How to create the firewall rule for Windows 7 for javaw.exe?
How to create the firewall rule for Windows 7 for javaw.exe? The application path differs from the new versions and user profiles. Is there generic symbols allowed for example asterisk?
Hello
I recommend you to send the request to another Department for assistance:
Security in Windows 7
http://social.technet.Microsoft.com/forums/en/w7itprosecurity/threads
I hope this helps.
-
Firewall rules for NSX through 2 vCentres
I have 2 vCentres, 1 in each physical site, in bound mode and NSX (single component DFW) running on two of them. In each site, the ESX hosts in the pools where I installed NSX are behind a firewall, so I found this doc to get the required ports:
6.2 NSX VMware vSphere Documentation Center
I now have the ports to open for guests of ESX NSX managers/vCentre on each site server, i.e. rules allow of NSX Manager/vCentre/ESX hosts communicate within the site 1 only.
I have similar firewall for site 2 rules.
My question is, do I need the firewall rules to allow the Manager to communicate with the vCentre NSX site 1 and ESX hosts in site 2 and vice versa?
Thanks for any help.
Take a look at the annex in the latest version of the hardening guide - put him to date with some tricks to cross-VC. You need primary and managers of NSX secondary to communicate for universal synchronization, two managers communicate with the Cluster of universal controller (site 1) and hosts on site 1 and 2 to be able to communicate with the UCC but I don't think you have to your site 2 vCenter/Hosts to communicate with the site 1 NSX Manager if I read it correctly.
NSX - v 6.2.x - Security Hardening Guide (Published version 1.6)
Maybe you are looking for
-
Why is my 4K display works only with Mac OS on a mac pro?
I have a Mac Pro (Darth Vader trash) 2013 edition. I installed today to MacOS of OS 11.11 El Capitan. My monitor AOC 4K (U2879VF) no longer works. Using a miniDisplay port to display port is to connect to the MacPro. It worked very well with El Ca
-
I have a keystone of opening that I can not open to rebuild a library which no longer exists. I have 8 arches and has been able to rebuild 6 of them in .aplibrary. But two of them does not open and the dialog box tells me that I must update the lib
-
Officejet 6310 all-in-One: can't send faxes from the computer screen
We use an Officejet 6310 all-in-one printer. Computer of my wife, a laptop Toshiba Satellite Windows 7 Professional, has suddenly come to the point that it will no longer send faxes from the computer screen. We get an error message that something mus
-
Windows 7 will not change main display when the screen is off
Hello I am running Windows 7 Professional 64 bit on a computer laptop Dell Precision M6800, Nvidia Quadro K3100M graphics card. I have a 3-monitor Setup: a monitor being the laptop LCD and the other two being Dell U2414h. My laptop is on the far ri
-
How to get the PIN for the bb device number
Hi all, I want to get the ID of device bb, how to get it thanks to all