Access for interal AND external users through a single login server?
Hey,.
Apart from redundancy, it is possible to have a single connection server that allows internal users AND external access virtual resources?
For external access, I have associated my login server security server. It works perfectly if I activate the PCoIP Secure Gateway option on my server of connection and enter the public IP address of the Security server.
But with this configuration internal users are not able to connect (listing the works of resources, but the connection fails).
If I disable the PCoIP Secure Gateway option, internal users can access, but not external users via the Security server.
Any contribution is appreciated.
Thank you very much!
No, it's the only way you can do it for internal users and external to share the same login server - activation of the MTP setting is by CS. If you want to PSG on for external users (and it is practically a necessity unless you use a third-party VPN), but offshore for internal users, they will point to the servers of different connection and so you'll need two.
Tags: VMware
Similar Questions
-
WLC with ACS 5.1 (RADIUS) for management * AND * Network users
Hello
I have authentication RADIUS of installation for the users of the network AND management on my NM - WLC (5.2 ongoing execution) against ACS 5.1
My Question is:-
For users to log in to Admin, I need to come back "Service-Type = Administrative - User" in order to make it work.
Because the ACS sees all applications from the same device (WLC) for Admin and network users,
the way I am currently treats it is by creating a filter based on the user name
Thus, users that contain 'admin' in their ID, use a set of
Network access policy authorization, who has an authorization associated with the attributes RADIUS profile.
Normal users have a ' network access policy authorization different rule ", with a different profile.
While this DOES WORK fine, still me I was wondering if there is a better way to do it, rather than create a rule
based on the user name.
I could use GANYMEDE + for the management, but I don't think that ACS allows the same client AAA (WLC) to use both protocols.
Thank you
I think it's something very common for things to do
You may notice that ACS 5 comes preinstalled with a selection policy of service that differentiates them the Protocol-based queries and orders or service 'Access to the network by default' or "Default Device Admin" out of the box
If you want only to RAY can either disable or delete the rule for applications of GANYMEDE + or not choose GANYMEDE + in the definitions of the unit
-
Hello
I'm a new 5.1 installation deployment view and came to the point of wanting to grant external users access to their desktop using PCoIP. I have currently only a single connection to the server in place and don't get any display on external clients unless I have activate the option 'Use PCoIP Secure Gateway for connections PCoIP desktop' and specify the external IP address that I am NAT'ing in the login server. However, once I do that, it breaks the connectivity for all of my internal users. Deactivation of the PCoIP Secure Gateway option restores internal connectivity, but then I'm back to square one and only a black screen and disconnected my external when users I'm trying to connect to the desktop computer.
Roll on a new security server will solve this problem for me? Or do I need a second connection to my external users server instead? We have no DMZ area... Is there any question, place security server (if it's the real solution) on the same local network as my existing connection server segment?
Thanks for any help!
-Matt
Here is the video I made which will answer your questions on the servers VMware View and security for external access: http://www.virtualdojo.com/content/how-configure-security-server-security-servers-101
-
Installation MS AD and Exchange Connector on a single connector server.
Hello
I have to install MS AD and Exchange on a single connector server.
I configured and installed this con .NET Server as directed by the documentaion as it works well.
With regard to the installation of the 11.1.1. MS AD & Exchange Connector on this server, the oracle documentation says to both of them that:
Starting from the installation media, copy and extract the contents of the bundle/ActiveDirectory.Connector-1.1.0.6380.zip file in the CONNECTOR_SERVER_HOME directory.
http://docs.Oracle.com/CD/E22999_01/ doc.111 /e20347/deploy.htm#BGBHFEHF
Starting from the installation media, copy and extract the contents of the bundle/Exchange.Connector-2.0.0.1.zip file in the CONNECTOR_SERVER_HOME directory.
http://docs.Oracle.com/CD/E22999_01/ doc.111 /e27258/deploy.htm#BGBDFHDD
I have server connector installed on the machine as C:\Program Files\Identity Connectors\Connector Server\
So I think that above Server Connector DIR will be the CONNECTOR_SERVER_HOME
My query is:
(1) for the installation of a single connector (say AD), I have to just extract content of ActiveDirectory.Connector - 1.1.0.6380.zip and paste them on the C:\Program Files\Identity Connectors\Connector Server\?
(2) what can I do, f I have to install the Exchange Connector as well? I noticed that bundle of Exchange and the AD have common files.
Kindly let me know the solution/steps, or something I can do bad
Edited by: 902488 Sep 26, 2012 12:04 AMI think you're talking about files such as ActiveDirectory.Connector.dll, ActiveDirectory.Connector.pdb, Interop.ActiveDs.dll, Shell.ScriptExecutorFactory.dll and THIRDPARTYREADME.txt.
They are ABSOLUTELY identical files for the two AD and Exchange clusters. There is therefore no problem. -
Policy nat for L2L and external access
Hello
I'm running into an interesting question with a 506th PIX 6.3 (4)
I created a VPN with our central location and implemented a policy nat on the 506th NAT their local 192.168.1.0/24 IPs to 10.200.25.0/24. This NATing works very well except for servers that also provide a static external IP address. I made a few captures of packets and traffic is crossing the VPN as expected and what actually at the remote end, but the answers are nat would be on the 'outside' ip of the host instead of the NAT. political I can ping other hosts on the remote network very well from the central location, not just those who have a static external IP address.
Example:
10.10.7.1 is my central site and try to ping a server with an IP address of 10.200.25.11 through the VPN. The traffic leaves the site central, is encrypted and delivered the firewall remotely. The firewall remotely translated 10.200.25.11-> 192.168.1.11 (the REAL Server IP) and delivers the package and the server responds, but answers are nat would be its public ip address of 75.X.X.X instead of 10.200.25.11.
Any thoughs on how I can work around this problem?
Here are the relevant config:
permit for line of policy-nat access-list 1 ip 192.168.1.0 255.255.255.0 10.1.1.0 255.255.255.0
allowed for access policy-nat-list line 2 ip 192.168.1.0 255.255.255.0 10.1.2.0 255.255.255.0
allowed for line of policy-nat to access list 3 ip 192.168.1.0 255.255.255.0 10.10.7.0 255.255.255.0
list of access vpn-sheep allowed ip 192.168.1.0 255.255.255.0 192.168.2.0 255.255.255.0
list of access vpn-sheep allowed ip 192.168.1.0 255.255.255.0 172.16.100.0 255.255.255.0
list of access vpn-sheep allowed ip 192.168.1.0 255.255.255.0 10.100.11.0 255.255.255.0
NAT (inside) 0-list of access vpn-sheep
NAT (inside) 1 0.0.0.0 0.0.0.0 0 0
Global 1 interface (outside)
public static 75.x.x.x (indoor, outdoor) 192.168.1.11 netmask 255.255.255.255 0 0
public static 10.200.25.0 (inside, outside) - list of access policy-nat 0 0
Try to rearrange your static rules:
Do the static strategy, the first to be read by the pix
public static 10.200.25.0 (inside, outside) - list of access policy-nat 0 0
public static 75.x.x.x (indoor, outdoor) 192.168.1.11 netmask 255.255.255.255 0 0
See how it goes
-
Hyperlinks - different settings for internal and external links?
Hello
I was wondering if it is possible to change the "Open link in a new window or tab" for individual links?
I'm linking to some sites of clients, and for all this, I want the links to open in a new window/tab so that my site remains active behind.
I then several links that are in the anchorages and pages within my site - for the latter, I want they will open in the same window, so the user can use the back buttons and not end up with a ton of windows/tabs open at the same time.
If external link - internal - and open in a new window, same window. Is this possible?
Thank you
Hi Ryan,
You can change the option "Open link in a new window or tab" for individual links.
You must select the links individually, and then make the changes.
-
Change the default file for downloads and some user folders locations
A big thank you to all who have helped me, more recently DAXnnn and try * 3. I come once more in need with questions. For the cleaning of my boot partition before cloning to a smaller SSD, I'm getting cause folders USER My Documents, my music, my pictures, and my videos to be moved to a different physical disk drive. I also want to do the same with the downloads. After trying to use MKLINK (without success) and the location of the tab in the properties for folders (in vain), try * 3 put me on editing the registry. While I did not yet any change, I followed his instructions to look under HKEY > CurrentUser > software > Microsoft > Windows > CurrentVersion > Explorer > Shell user folders and confirm watch registry.
What I found is that the actions I took before running into problems using the options of localities had caused registry entries updated to show the new names of path of My Documents (under personal in the registry path) and my music. This leaves downloads, my pictures, and my videos to be changed before the data transfer of the boot partition to reduce before cloning. I discovered the writings of my pictures and my videos contain a variable %UserProfile% then the names of folders. My assumption (often a wrong thing to do, I know) is that I can change these entries replacing %UserProfile% with the name of path, including the drive etc letter describing where I want to move the old data and write new data and changes. IS THAT CORRECT?
Regarding downloads, what I discovered is the second entry in HKEY > CurrentUser > software > Microsoft > Windows > CurrentVersion > Explorer > User Shell Folders, below (default) is a name {374DE290-123F-4565-9164-...}, displayed once indicating the value of % USERPROFILE%\Downloads. Using my penchant for the skip logic, I assume that I can edit this article replace the value data with the path name where I want future writing downloads. IS THAT CORRECT?
If I can confirm or correct information, I am very close to stripping the size of my partition boot prefixed operation clone to place what's left on my SSD.
Thanks to all for participating in such a large forum community!
HR
Yes you are right. If you want that your download location for be moved, just change:
Old: %userprofile%\downloads
New: E:\OtherDrive\Some Windows\
This will make all your downloads stored in the folder 'folder of some '. Just be sure to include a folder name and make sure that this folder actually exists. Make sure not to say a disc like E:\ or all your documents could get dumped at the top of this reader, rather than in a folder.
-
File system for FRA and external backups
Oracle 11g R2.
The FRA drive is formatted using Linux x 83 put on Diskgroup + FRA system.
Backups are stored outside on an ext3 file system.
Suppose now the database gets completely crashed and I need to recover by continuing external backups. I will copy the external backups to the + FRA disk and then perform the recovery from there.
My question is, given that external backups are on ext3 file system, while the FRA is the Oracle ASM filesystem, there will be a problem for the use of the file systems of the two difference?
Thank you
Scott
scottjhn wrote:
To summarize the issue:
In my system, the database will be on ASM disk group + DATA (disk1 disk2).
I will use another disk, disk3 (ext3 file system) for FRA, to organize data files backups and multiplexed logs (archive logs, online newspapers and control files).
Earlier you said "I'll use the + FRA (ASM disk group) for the fast recovery area that holds that archiving multiplexed logs, recovery online logs, and control files.» Nothing else. »
Now, I need one more place to hold the copy of the multiplexed logs.
Wouldn't not on the same + (ABOVE)? Alternatively, use a disk full-fledged, disk4 (ext3 file system)?
Thank you
Scott
First of all, the reason for multiplexing online redo logs and control files is not the same as that of multiplexing archivelogs. Do it online and the control file are actually a part of the database. The database will not work without them. This is why it is so important to have multiplex. Archivelogs, on the other hand, are part of your backup strategy. The database itself really doesn't care if you have any archivelogs at all. The archivelogs multiplexing is much less common. I have never multiplexed mine, but I do not have a task that runs every hour to copy any newly created on a server off-site.
If your database is on ASM, at least a control file and a member of each group of redo log must be in ASM. Technically, is not having to be, but it's really foolish not to do so. Where to put the second copy? Probably several schools of thought on this. If your FRA is on ext3, so it seems a simple decision... a FRA copy, a copy in its default location in ASM.
-
Access to several cubes Essbase ASO through a single cube
Hello
I have 10 cubes ASO and each cube contains data of one day (one day contains lines of facts about 30 million). Is there a feature in Essbase that combines all these cubes ((like a virtual cube)? Or can we do this task using the BI server. If we are unable to combine these cube then what is the best method I could use to query all 10 cubes at a time?
Thank you in advance.
Concerning
ChandraIt sounds like you could have 10 cubes ASO partitioned seamlessly to a cube of target (OSB?) users could connect you to receive the combined data. It makes life easier if they are all the same size. The target would have every day and each source cube could be partitioned by day.
-
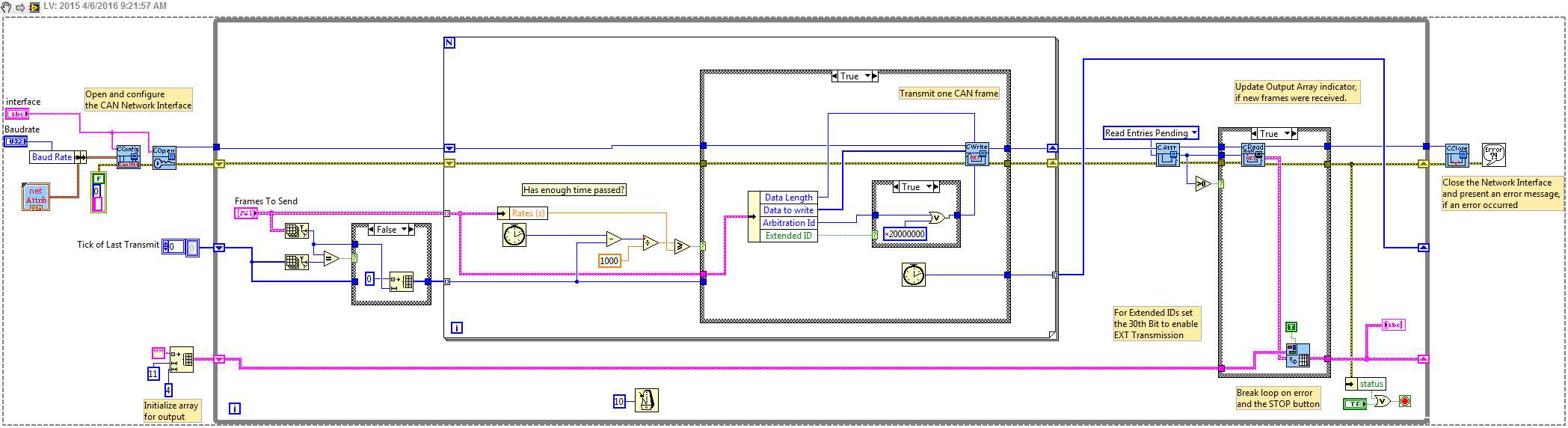
Is it possible to send several messages with IDS of different arbitration periodically (messages can have different periods) by simple CAN interface?
I use CAN frame API 2.7.5.
Not any material support retransmit material timed, so I usually stick with software programmed if calendar is not super critical. An improved version that works with an array of broadcast signals is attached. Each rate is assessed at the same time, and then this frame is sent, if enough time has passed.
-
Separate authentication for external and internal users?
Hello
Asked me to come with a CEP for a client who wants a new system APEX is accessible to internal and external users. The client security team want to have two separate copies of the request for the APEX and both copies of the auditor of the APEX on separate databases on two separate servers from Weblogic to support different security requirements for both internal and external users. I don't think that is necessary as APEX should be able to impose conditions depending on what type of user is connected, by questioning the cookie passed in which could contain a flag to say whether the user is internally and externally. In addition, CAE can be used to further restrict external access.
The middleware for the customer solution is managed by a third party, who have made the following recommendations:
The domestic channel requires SSO to configure on WebLogic while the outside lane. Internal users must be validated on Active Directory, with RSA Authentication Manager used for external users. We cannot set up a listener APEX instance to use and not to use SINGLE sign-on at the same time. Two applications are necessary.
Now, I understand from my understanding limited the listener of the APEX, it is possible to implement different rules depending on the type of user to access. However, might just as well not be managed from Magnatune APEX? We could write a custom authentication procedure that verifies again road and the SSO user authentication cookie or otherwise, as required.
So my question is this: can it really be necessary to implement two versions of an APEX application, with two distinct on different servers APEX headphones, to meet the security requirements of separate here? Ultimately at the end of the day if that's what the customer wants, we have to build it, but I'm looking to reassure them via a CEP that won't be necessary. I think that the seller of hardware/middleware recommend that the client just because they do not know available in APEX itself custom authentication options.
Please forgive any simplifications or the lack of details in the above - I'm more a developer APEX as a person of the infrastructure and a bit of a 'newbie' where the listener APEX is concerned. All advice gratefully appreciated!
Graham.Hi Graham,
It's a matter of people paranoid how and to what extent they trust their own infrastructure. Things could be easier than to split the environments, but I don't know if I just depends on the cookie because cookie can be easily rigged. But I think that the following architecture would be safe:
1 internal users connect APEX listener somehow security team requires, come to APEX and maybe be identified using the internal IP address (range). To simulate the INVESTIGATION period should be difficult for external users.
2. external users connect APEX listener through a defined gateway, preferably a proxy. All future requests through this gateway would be considered external users.
You may add additional logic to the proxy, for example use something like 'mod_headers' in Apache HTTPD to add a page header to requests, so that you may identify as external users.
You could, of course, also put it the other Tower and allow internal users to use some proxy to enforce certain rules of IP based address, or perhaps a few additional references as authentication for access to the proxy (which again could be transparent user in AD-configuration, at least if you stick with IE).You can easily implement the separation in your custom authentication process. But this architecture also allows some other compromise: even if someone does not trust your application logic to handle two types of application successfully, you can also use the proxy to enforce the specific call for an application id. Certainly you don't need to duplicate the infrastructure...
Most of the companies already have a proxy for external users, for example to activate SSL and to hide other internal resources, for load balancing,... so I think you just need to put some configuration of the existing infrastructure and end up needing no component additional. Even if there is no proxy and yet, it would be an element of very light weight, easy to handle.So far, all this has nothing to do with the earpiece of the APEX. It's 'just' a web front-end for the instance of the APEX in the database. I wouldn't put a logic of network security in this service, but the split things upward front. The APEX listener can be patched to add some logic, but which was not supported.
I think that this would work and should be sufficient for most of the safety requirements.
If my picture was not painted understandable, let me know.-Udo
-
SSH and Telnet access for catalyst 4503 list
I was wondering the structure of command to apply an access list to ssh and telnet on a catalyst 4503. I keep a list of access for indoors and outdoors. Can afford two different IPs from the outside? Thank you
You will need create an access list indicating the networks/hosts that you want to allow.
-Example
access-list 10 permit 10.10.1.10
access-list 10 permit 10.10.2.10
access-list 10 permit 127.1.0.0 0.0.255.255
access-list 10 permit 192.168.1.0 0.0.0.255
So you want to put this list of access on the VTY interfaces.
-Example
line vty 0 4
access-class 10
entry ssh transport * if you only want to SSH *.
line vty 5 15
access-class 10
entry ssh transport * Ditto *.
Now you can do all this with * line vty 0 15 * but, it gives you a better idea of what is happening. It is a simplistic configuration. Remember that it is advisable not to allow ssh. If you want to allow at the same time, let him * transport input ssh * out of the configuration.
I hope that gives you an idea of the structure. If this is not the case, let me know.
-
How to access e-business applications by external users via internet
Dear all
We have e-business application 12.1.3, currently accessible by internal users only
We intend to access the site by external users also via internet
Please suggest me.
material requirement
requirement of network
safety requirement
procedure of implementation & Doc Oracle.
Thank you
MUBA
Review pl MOS Doc 380490.1
-
User profile folders that are created on the login server?
All went to watch the C:\Users folder on my server to connect internal and noticed there are profiles it for all of my users. We will connect with zero clients for a floating office pool and redirect all profiles using the Persona management, so I'm surprised to see them here. No idea why the user profile folders created on the VCS?
Geoff
I had this same problem with my login server. I had about 30 users on one of them and less than 10 on the other. I couldn't find any reason to make it, so I ended up opening a case of low priority with VMware Support. They have found the answer:
---
Found the answer for you: it seems that users who require a change of password and change it as they connect to their desktop to view create a user profile on the login server
http://social.technet.Microsoft.com/forums/WindowsServer/en-us/eb56b301-FEAA-4753-a70a-cd950bafa303/Windows-2008-invokechangepassword-lots-of-profiles-in-cusers
---Thinking about it some more, this organizations probably affects the only running the customer view as a replacement for Explorer shell (do us), effectively replace normal windows authentication. So basically, when a password is about to expire, the only interface that they need to change it is through the Client view. Apparently this changes the mechanism eventually create an empty profile on windows server itself?
Article, it would be interesting to test changing the newspaper locally allow an option to see if it prevents the creation of profile, or if it breaks the password!
-
CUPS, Jabber IM for iPhone, Mobile and external access
Hello world
How do you provide external secure access for email Instant Jabber for iPhone client and the Cisco Mobile customer on an iPhone?
There are so-called security SSL for Jabber Instant Messaging, but is unable to find all the information on how. The Cisco Mobile client appears to the needs of the AnyConnect VPN client and encourage users to connect via VPN, first...
After a bit of bumping into a wall your head wondering why there was no documentation for external access to Cisco Jabber for iPhone, I realized that Cisco Jabber IM for iPhone is an entirely different product and Jabber for iPhone seems to be the new name of Cisco Mobile customers. Yet, the only documentation I can find for the Jabber Instant Messaging is that I can "security by using the Secure Sockets Layer (SSL) encryption" but no information on implimenting it with CUPS.
On top of that, the Jabber IM for iPhone can not make calls but rather calls Cisco Mobile, which raises the question of providing external access to this too, and the only solution I've ever found is to use the AnyConnect VPN client on the device also. Suddenly, it seems to offer a solution of Cisco Unified Communications on an iPhone, I need three different and is applications is no longer quite as unified.
Thank you
Mark
Conclusions you drew on the product names are correct. They are transitioning to Jabber like a brand name, but it did not in the iOS VoIP client yet. The most recent Cisco Jabber for Android is the first to include Secure Connect (remote access protected or ensure access transparent, aka). The BU seems characteristic knocking out on a single platform and then replicating them on others before moving on to the next batch of features. I don't have a specific timetable to share but expect customers to iOS updated in the coming months with Secure Connect.
With regard to the separate clients: I can see both sides of this room. The more I use them more, I agree with the decision to keep them separated and cross-launch when necessary. If you think it is consistent with the way the user interacts already with their phone: voice and texting are two separate applications. I suspect that the developers also get some benefits by keeping things more targeted (e.g. less than test whenever they change something). The only downside to this approach is that each app consumes its own tunnel AnyConnect on the SAA.
Maybe you are looking for
-
The OE Mail recover after the damage caused by the virus.
My PC has just blown to bits by a virus.I hope to be able to save the data files, including those that define the accounts rules, for example, and contain emails.How can I restore my EYE as much as possible in its original configuration and emails us
-
HP Pavilion P6000 series (MN: p6710cs-m)
Hi guys I have some problems with this desktop computer. This PC is 1.5 years. I bought an external graphics (GV-R725O5-2gi), but the new GC will not work. I ran the card on an old PC of 5 year with maybe end of 1 PCIe slot that it runs. I have suspe
-
Can I control the activity of the two loops independently while in the same vi?
I would like to run two generators of random numbers (RNG) in the same vi. The first GNA go all the time that the vi is running. But I would like to be able to control the second RNG (turn on and off at will). I consider start and stop buttons wired
-
After I installed XP SP3, get code error 0 x 80040509
I have a valid copy of Windows XP with Service Pack 2 installed on my computer. When I install sp3 and reboot the computer, I get the error 0 x 80040509 code. I can't open a session with this error code. I had to reformat my computer and reinstall
-
A device w / ethernet connection is REALLY necessary to change the wifi password?
I'm not all that intuitive technology. About 6 years ago my son helped us set up our wireless and router. We opted to NOT have a password that we were the only House in the area at the time and never understood the risks of unlocked despited being ta