Backdoor in Cisco routers and firewalls.
The more I read on the NSA scandal (and Yes, I apparently a scandal) less I trust corporations hardware and software. There is no reason for anyone to doubt that all Cisco equipment comes with a backdoor. Because these probable backdoors exist it's a matter of time before hackers discover and exploit them. It's happened to Microsoft a number of times and there is no reason that it could not happen to Cisco. It is no longer our trust Cisco equipment and have already started researching alternatives network.
It is more a crazy conspiracy theory, that is the reality.
In all liklihood, we use a series of firewall to further isolate our network against intrusions. To reduce costs, we can keep our existing in this topology Cisco equipment, but we will replace hardware Cisco when it breaks down or needs to be upgraded. I do the same thing with my home network.
In the last months, we already moved all of our e-mail to secure servers overseas and changed all our McAfee, AVG and Avast antivirus software. We are also researching Linux distributions to replace Microsoft.
If Cisco wants to protect their brand, they need to take a stand or see their market share continue to erode. There must be a CEO to a U.S. company that will take this position and be a hero rather that continue to be a lap dog.
Hello
use open-source based linux firewalls and routers.
and check the source cod
Tags: Cisco Security
Similar Questions
-
PowerConnect switch and Cisco routers
I have 4 Cisco routers connected to our Dell Powerconnect 7024. This is a laboratory environment where I'm having every act of router (2 per site) as a WAN gateway for these 2 sites.
Site 1 Site 2
2 3 router
PC - Dumb_switch PowerConnect Dumb_switch client - PC Client
Router 1 router 4
There are a few other Vlans on the switch with connected devices. With the current configuration, these two sites can communicate with any other "site" connected to the switch on each route, with the exception of the other.
Directly connected to the router interfaces are in trunk mode, as it's the only way I could get the dell to connect with the Cisco. Ive read in other threads that the general mode is usually suggested on the powerconnect switch, but had no luck with this configuration.
Router 1---> item in gi1/0/15 (vlan 10)
Router 2---> item in gi1/0/14 (vlan 11)
Router 3---> item in gi1/0/22 (vlan 16)
Router 4---> article gi1/0/23 (vlan 14)
Example: a ping from Site 1 can reach int 22 of the switch without problem, but I can't ping jump according to R3. As all the other devices on this switch can talk to these sites, I'm not clear if the problem is my config switch dell or routers. Any input would be greatly appreciated. Thank you!
! Current configuration:
! Description of the system "PowerConnect 7024, 5.1.2.3, VxWorks 6.6"
! 5.1.2.3 system software version
! 'Normal' system operation mode
!
Configure
GVRP enable
VLAN 2-7, 9-14, 16
output
VLAN 2
name 'BOSTON '.
output
VLAN 3
name "MIAMI".
output
VLAN 4
name of 'THE
output
VLAN 5
name "SEATTLE".
output
VLAN 6
name "DALLAS".
output
VLAN 7
name "London".
output
VLAN 9
name "Frankfurt".
output
VLAN 10
name "Rome".
output
VLAN 11
name "Sczecin.
output
VLAN 12
name "Budapest".
output
VLAN 13
name "Moscow".
output
VLAN 14
name "Quebec".
output
-Other - or ITU (q)
VLAN 16
name "Winnipeg".
output
hostname "Devlin".
location 1/0 2. PowerConnect 7024
clock timezone-5 minutes 0
battery
1 2 Member! PCT7024
output
out-of-band interface
Shutdown
output
no ip domain-lookup
"local" IP domain name
IP routing
IP route 0.0.0.0 0.0.0.0 172.16.37.3
IP route 172.16.37.160 255.255.255.240 172.16.37.162
IP route 172.16.37.112 255.255.255.240 172.16.37.162
IP route 172.16.37.112 255.255.255.240 172.16.37.147
IP route 172.16.37.144 255.255.255.240 172.16.37.147
IP route 172.16.37.240 255.255.255.240 172.16.37.244
IP route 172.16.37.224 255.255.255.240 172.16.37.244
IP route 172.16.37.224 255.255.255.240 172.16.37.217
-Other - or ITU (q)
IP route 172.16.37.208 255.255.255.240 172.16.37.217
ARP 172.16.37.162 0022.9057.7F51
interface vlan 1
IP 172.16.37.4 255.255.255.240
bandwidth 10000
IP ospf cost 10
output
interface vlan 2
IP 172.16.37.17 255.255.255.240
output
interface vlan 3
IP 172.16.37.33 255.255.255.240
output
interface vlan 4
IP 172.16.37.49 255.255.255.240
output
interface vlan 5
IP 172.16.37.65 255.255.255.240
output
interface vlan 6
IP 172.16.37.81 255.255.255.240
output
interface vlan 7
-Other - or ITU (q)
IP 172.16.37.97 255.255.255.240
output
interface vlan 9
IP 172.16.37.129 255.255.255.240
bandwidth 10000
output
interface vlan 10
IP 172.16.37.145 255.255.255.240
bandwidth 1000
IRDP IP
output
interface vlan 11
IP 172.16.37.161 255.255.255.240
bandwidth 1000
IRDP IP
output
interface vlan 12
IP 172.16.37.177 255.255.255.240
bandwidth 100000
output
interface vlan 13
IP 172.16.37.193 255.255.255.240
bandwidth 1000
output
interface vlan 14
IP 172.16.37.209 255.255.255.240
bandwidth 1000
output
interface vlan 16
IP 172.16.37.241 255.255.255.240
bandwidth 1000
IP ospf cost 100
output
No flowcontrol
!
interface item in gi1/0/3
spanning tree portfast
output
!
interface item in gi1/0/4
spanning tree portfast
output
!
interface item in gi1/0/5
spanning tree portfast
switchport access vlan 2
output
!
interface item in gi1/0/6
spanning tree portfast
switchport access vlan 3
output
!
interface item in gi1/0/7
spanning tree portfast
switchport access vlan 4
output
!
interface item in gi1/0/8
spanning tree portfast
switchport access vlan 5
output
!
interface item in gi1/0/9
switchport access vlan 6
output
!
interface item in gi1/0/10
switchport access vlan 7
output
!
interface item in gi1/0/11
spanning tree portfast
switchport mode trunk
output
!
interface item in gi1/0/12
spanning tree portfast
switchport mode trunk
output
!
interface item in gi1/0/13
switchport access vlan 9
output
!
interface item in gi1/0/14
Speed 100
full duplex
switchport mode trunk
switchport general allowed vlan add 10 tag
switchport access vlan 10
output
!
interface item in gi1/0/15
Speed 100
full duplex
switchport mode trunk
switchport general allowed vlan add 11 tag
switchport access vlan 11
output
!
interface item in gi1/0/16
switchport access vlan 12
output
!
interface item in gi1/0/17
switchport access vlan 12
output
!
interface item in gi1/0/18
switchport access vlan 13
output
!
interface item in gi1/0/19
switchport access vlan 13
output
!
interface item in gi1/0/22
Speed 100
full duplex
switchport mode trunk
switchport general allowed vlan add 16 tag
switchport access vlan 16
output
!
interface item in gi1/0/23
Speed 100
full duplex
switchport mode trunk
VLAN allowed switchport General add 14
switchport access vlan 14
output
!
interface item in gi1/0/24You could probably create a static route in Router 1 router 4 with a priority which is better than the other options, so we're going unless the link is down.
-
Will there be improvements made to the features of VPN configuration and firewalls in the ACC?
Future versions of CCA will have the ability to set up the VPN site-to site on UC520s, UC540s and SR520s without having to use the Multisite Manager or CLI? With non-SBCS Cisco VPN products have a Cisco's GUI to configure site-to-site VPNs. The UC520, UC540 and SR520 are the only Cisco products (with the exception of products that have reached end of life status) who do not have this capability in a sort of Cisco's GUI (apart from the Multisite Manager of CCA 2.1 and later versions).
Future versions of CCA will allow you to modify the firewall on UC520s, UC540s and SR520s rules without having to resort to the CLI?
Almost all Cisco products, except for UC520, UC540 and SR520 series products, have a Cisco's GUI to configure these features. The SA520 and SA540, these features can be configured in the web GUI. The Cisco ISR, these features can be configured through SDM or CCP. CCA has always had the ability to fix UC520 unit, but he had not the possibility to fine-tune the settings of firewall and security, unlike the web interface SA500, SDM or CCP.
Reasons why having the skills to the CCA is important:
- These characteristics are indicated on the data of UC520, UC540 and SR520 sheets
- The opportunity to refine and verify access control lists in the ACC can accomplish the following:
- Ability to comply with HIPAA, Sarbanes-Oxley, PCI, etc.
- Improved troubleshooting
- Eliminates the need to use CLI to refine or verify the firewall settings
- VPN site to site can currently be configured via CLI or the CCA Multisite Manager
- Multisite Manager CCA can be used for virtual private networks between UC500 or SR520s placed in front of UC500 units units
- CCA Multisite Manager cannot be used for VPN between autonomous SR520 units, or between a unit UC500 and endpoint non-UC500 (with the exception of a placed in front of a UC500 unit SR520)
- All images IOS Supportepar UC520 units, UC540 and SR520 routers have firewalls and VPN capabilities described here
Hi John,.
The ACC is a configuration tool for platforms that are part of the SBCS solutions. Multisite manager is the approach we take to configure a VPN site. Enchancements in customization of the firewall and access lists is something we plan to put on the roadmap. We will continue to improve the CCA to meet these requirements. We will schedule to get these features added in the 2010 calendar.
Thank you
Saurabh
-
Cisco ACS GANYMEDE + AAA can be activated for telnet to Cisco 600 and 700 routers?
Unfortunately you can not configure radius AAA or Ganymede in routers series 600 or 700.
-
Time-out for ARP cache on Cisco routers
Hello
I was reading a book on Cisco routers, in which the author said: "the router resets the age ARP meter to zero whenever he sees valid traffic from the corresponding device.» This ensures that the addresses of active devices are never emptied in the cache, regardless of how long they have been known. »
I'm really surprised at this topic because I always thought the age counter ARP was an absolute of the meter and not compared to the last time a package was seen coming from the corresponding IP address. After reading this, I did a few tests that tend to confirm the age counter ARP is absolute and that he cares not if we have movement active in the corresponding period of INQUIRY or not.
: Question 1 can someone confirm this please?
I am unable to find clear statements in the Cisco documentation.
QUESTION 2: when the router sends a new ARP request?
For example, when the time-out of the ARP is 4 hours or 240 minutes (default value of Cisco), the router sends an ARP request reaching 239 minutes (1 minute before the expiration time). This value is a fixed (send us a 1 minute before aging ARP request) or is it a relative value (x % of the value of timeout)?
Thanks for your help.
Sam
I have some additional information that might help. I found an ad of a Cisco engineer, which gives some information about the behavior of ARP in Cisco IOS. He said clearly (and is an example) that if Cisco receives an ARP to a host request it will use this request to refresh the ARP entry and reset the timer so that the entrance without making its own application ARP. Maybe that's the behavior they were trying to talk in the IOS Cookbook.
It also speaks to a unicast ARP request 60 seconds before the expiration of the entry so that the entry can be updated. It does not specifically say, but I think that this interval is fixed.
Here is the link if you want to see the details:
http://puck.nether.NET/pipermail/Cisco-NSP/2005-February/017400.html
Regarding the error in the book, I worked as an examiner on a few pounds and can tell you that the authors and reviewers are working hard to do the right thing. But sometimes mistakes are not captured and appear in the publication. With the amount of detail covered in the book some mistakes are bound to crawl through.
HTH
Rick
-
Problem on the establishment of a GRE/IPsec tunnel between 2 cisco routers
Hello world
I am trying to establish a GRE IPsec tunnel between two cisco routers (2620XM and a 836).
I created a tunnel interfaces on both routers as follows.
2620XM
interface Tunnel0
IP 10.1.5.2 255.255.255.252
tunnel source x.x.x.x
tunnel destination y.y.y.y
end
836
interface Tunnel0
IP 10.1.5.1 255.255.255.252
tunnel source y.y.y.y
tunnel destination x.x.x.x
end
and configuration of isakmp/ipsec as follows,
2620XM
crypto ISAKMP policy 10
md5 hash
preshared authentication
ISAKMP crypto key {keys} address y.y.y.y no.-xauth
!
!
Crypto ipsec transform-set esp - esp-md5-hmac to_melissia
!
myvpn 9 ipsec-isakmp crypto map
defined peer y.y.y.y
Set transform-set to_melissia
match address 101
2620XM-router #sh ip access list 101
Expand the access IP 101 list
10 permit host x.x.x.x y.y.y.y host will
836
crypto ISAKMP policy 10
md5 hash
preshared authentication
ISAKMP crypto key {keys} address x.x.x.x No.-xauth
!
!
Crypto ipsec transform-set esp - esp-md5-hmac to_metamorfosi
!
myvpn 10 ipsec-isakmp crypto map
defined peer x.x.x.x
Set transform-set to_metamorfosi
match address 101
836-router #sh access list 101
Expand the access IP 101 list
10 licences will host host x.x.x.x y.y.y.y
Unfortunately I had no isakmp security associations at all and when I enter the debugging to this output.
CRYPTO: IPSEC (crypto_map_check_encrypt_core): CRYPTO: removed package as currently being created cryptomap.
Any ideas why I get this result? Any help will be a great help
Thank you!!!
I think it's possible. It seems to me that you are assuming that the address of the interface where goes the card encryption is peering address. While this is the default action, it is possible to configure it differently.
As you have discovered the card encryption must be on the physical output interface. If you want the peering address to have a different value of the physical interface address outgoing, then you can add this command to your crypto card:
card crypto-address
so if you put loopback0 as the id_interface then he would use loopback0 as peering address even if the card encryption may be affected on serial0/0 or another physical interface.
HTH
Rick
-
What is the difference between Cisco NAC and ACS?
I am currently part of a new construction project and my Cisco account manager and sales engineer recommend Cisco NAC for our new MDF. I'm confused because I don't clearly know the difference between a Cisco ACS and the NAC. What is the difference?
Thank you
Chris
Chris,
The two are completely different, maybe the sales rep could present you with more information and application. Each offers a variety of services tailored to the specific needs. I think that we need to read more in depth on the proceeds of the NAC. NAC seems an excellent solution for authentication authorization but other regulatory compliance.
When you see ask your representative to sales for more information/demo.
ACS is more widely use as a central point to access control to network devices routers, an example is for acs accounting management and the authority to order on all devices on the network using acs as RADIUS server. Considering that the NAC is over a central point of safety inspection on earlier systems of access to your network by via LAN or outside, an example of these respected regulatory defined could be inspections could be virus definition checks before getting lan access thus preventing access to the LAN if the system does not have regulatory compliance defined in NAC access is denied. Another example could be the unknown local host connections etc... So, it seems that NAC is a much broader product that provides endpoint security internal, not only the authentication authorization as acs... ACS has been there for a long time, NAC is rather new product.
NAC
http://www.Cisco.com/en/us/NetSol/ns466/networking_solutions_package.html
ACS
http://www.Cisco.com/en/us/products/sw/secursw/ps5338/index.html
Rgds
Jorge
-
ALS IP Cisco 2901 and POLITICS with dual gateways LAN-based ROUTING
Hello
I am configuring a failover solution combined with the ACB using two bridges already configured. See the attached diagram.
I currently have two ASA 5505 and a 2901.
According to the example: http://www.firewall.cx/cisco-technical-knowledgebase/cisco-routers/861-c... I've set up the following in the 2901:
Interface Port - channel1.1
encapsulation dot1Q 1 native
IP 192.168.200.100 255.255.255.0
intellectual property policy map RM-Comcast-traffic routeIP route 0.0.0.0 0.0.0.0 192.168.200.200 track 1
IP route 0.0.0.0 0.0.0.0 192.168.200.150 track 2
Route IP 10.10.10.1 255.255.255.252 192.168.200.150IP extended ACL-Comcast-traffic access list
object-group permit COMCAST_Routed 192.168.200.0 0.0.0.255 anyRM-Comcast-traffic route map permit 1
corresponds to the IP ACL-Comcast-traffic
set ip next-hop check availability 10.10.10.2 1 excerpt 2object-group service COMCAST_Routed
Eq ftp TCP
TCP eq www
TCP eq ftp - dataALS IP 1
ICMP echo - 192.168.200.200
threshold 2
timeout of 1000
frequency 30
IP SLA annex 1 point of life to always start-time nowALS IP 2
10.10.10.2 ICMP echo
threshold 2
timeout of 1000
frequency 30
IP SLA annex 2 to always start-time life nowtrack 1 accessibility of als 1 ip
Track 2 accessibility of ALS 2 ipI did some tests and the part of failover seems to work but the configuration of the ACB does not work as expected. Only thing missing track 1 each time delivering properly and trak 2 is declining.
Any help clarifying the feasibility and practicality of this configuration is greatly appreciated.
Dan
Adding a value of AD won't fix ACB (sorry if I gave that impression).
On the client that you are testing with can you look it's the example routing table ' netstat - nr ' example and see what it shows in terms of gateways.
It can be that you want to debug your routing policy to see what is happening on the router.
Jon
-
Configuration of multiple L2L on cisco routers problems
Hi all, I have two cisco routers (Cisco 2911 and 871) I'm trying to establish a VPN L2L with. Each has a VPN configured to our cooperate Office located to the top and work. I'm now trying to establish VPN site to site in these two remote sites. I have my cryptographic cards and NoNats valuable traffic however set up, I don't even see a coming phase upwards.
I attached each config. Most of my experience of site to another is of pix and ASA, so I'm curious to know if there is something else I need to do on my external interface to allow several VPN?
Can you see where I am going wrong?
Thank you
Dan
Hi Dan,.
You can only have one card encryption on an interface (as well as on Pix / Asa). However, this encryption card can have multiple entries.
The Scottsdale router, so now instead of:
card crypto Chandler-address FastEthernet4
Chandler 2-isakmp ipsec crypto map
...
!
map Scottsdale address FastEthernet4 crypto
Scottsdale 1 isakmp ipsec crypto map
...
You must configure:
map Scottsdale address FastEthernet4 crypto
Scottsdale 1 isakmp ipsec crypto map
...
Scottsdale 2-isakmp ipsec crypto map
...
And of course, there must be a similar change on the other router.
HTH
Herbert
-
Disable SSH on Cisco routers/switches CBC encryption
Hello
Our customer ordered PenTest, and as a feedback, they got recommendation "disable SSH Mode CBC Ciphers, and don't allow that CTR ciphers ' and 'Disable weak SSH MD5 and algorithms MAC 96 bits' on their switches Cisco 4506-E with CIsco IOS 15.0
I went through Cisco documentation that I could find, also tried to find commands on the switch itself, but I found no way to manipulate these SSH options. (SSH v2 only is already set up)
Is it possible to do this on Cisco IOS? If this is not the case, what are my options?
You can use an external server for authentication. But that will not change anything in the encryption.
RAY will be fine for authentication, if you are also looking strong authorization, you should look into GANYMEDE +.
Back to you initial problem:
Some long time there was a similar problem with a client and it resolved in the following way:
- All routers and switches had a class of only two Linux servers access to access devices through SSH.
- The SSH server was accessed by admins and used as a jumping point to access the routers/switches
- Linux servers had a put to update the ssh-server config to allow only the strong crypto to Admins and also check the administrative work.
With this, there was strong crypto by the admin-workstations to linux server and pretty weak crypto of the Linux for routers switches (which was at the time-3900XL-2950). But as the linux-boxes have been placed in the management network, all on the risk has been reduced.
-
I recently reinstalled my copy of Vista 64 bit I hope to solve this problem that has been with me for a while. Before I wiped and reloaded, Security Center Windows would alert me every day that my firewall protection and malware have been disabled.
I use Kaspersky Internet Security, which is fully updated and works as it should. I am able to activate Windows Firewall and bypass the firewall Kaspersky and that error to go away, however, I can't remove the error of malicious software. I got all these errors directly after a restart after the installation of service pack 1.
Under Windows Security Center it says, "Kaspersky Internet Security reports that it is turned off," under the heading for malware protection. When I click on the button to activate under Windows Security, it goes through the steps who say do you trust this program, Yes, Yes, ok. After choosing all the options of trust Kaspersky and activate this protection, he thinks about it a little, but always returned and said it's off. It also has a green light saying that Windows Defender is actively protecting your computer.
I think that my Internet Security Suite is successfully active in these areas and work I checked the menu, check that they work. In my opinion, after installation of service pack 1 that something I have messed up in the statement that those programs are active or really uninstalled them.
Even if I can get the only message that the Kaspersky firewall is disabled to disappear by enabling the Windows Firewall, which is not yet as I want. I want the suite of internet security that I paid to be active and functional on the side of the Windows security features.
I would appreciate any help with this problem by addressing why he continues to warn me that my protection malware and firewalls are disabled. Thank you.
Also install Windows Vista SP2 this problem could be solved, otherwise try to uninstall and reinstall Kaspersky and also, try to get the latest version of Kaspersky.
If still the same issue please contact Kaspersky support.
-
Cisco VCS and integration Lync2013
Hello!
Could you tell me please, when CISCO officially support Lync2013 - free new software for VCS - C and documentation on integration?
The main interest is the possibility of transferring video between CISCO/MCU and Lync endpoints on the H.264 Protocol, who hails from Lync2013.
Right now, I've got VCS - C and RTM Lync2013 X7.2. During the video call without AMGW appeal established as audio only.
When using with Lync2010, it worked on Protocol H.263 and CIF resolution.
Evgeniy salvation,
We are currently investigating the possibilities to achieve interoperability between Lync 2013, VCS and video devices on the side of the VCS standards-based, it is a work in progress and at this stage, it is to early to provide any factual information on when interop will be available.
In contrast to Lync 2010, Lync 2013 does not support H.263 for video and it so that will remove the OCS/Lync integration. I do however think that you should be able to make a two-way video between Lync 2013 and VCS-joined endpoints if you use an AMGW tried that yet?
Thank you
Andreas
-
Cisco show and share to publish on the internet
Dear Experts
We have new deployment for Cisco SNS, and we publish SNS on the internet. I need help to do it and any recommendations, please.
Thank you
Richard
Hi Richard
Solve you your problem? I have to make sure of the following.
1. you can access external SNS internally.
2-natting is ok between IP Public & private.
3. for the DNS record, make sure that the name must be the same on the inside & outside. For example internlly vod.bnp.med.ca and create a record public vod.bnp.med.ca should be the same FQDN, otherwise your SNS will never work. For authentication, you must publish the DMM.
Note: your question this internal FQDN differs from the external FQDN of the SNS.
Thank you
Please note all relevant information
-
I am very new to Cisco ISE and Meraki. I try to get the Radius configuration for wireless authentication. When I do a test of the Meraki to ISE, it passes.
When I try to connect from my laptop, I look at the logs of the Radius and it passes; However, it does not connect me to good policy. I keep hitting the default policy. I have my Meraki police above the default policy in the strategy defined in article. I have attached what looks like my strategy game.
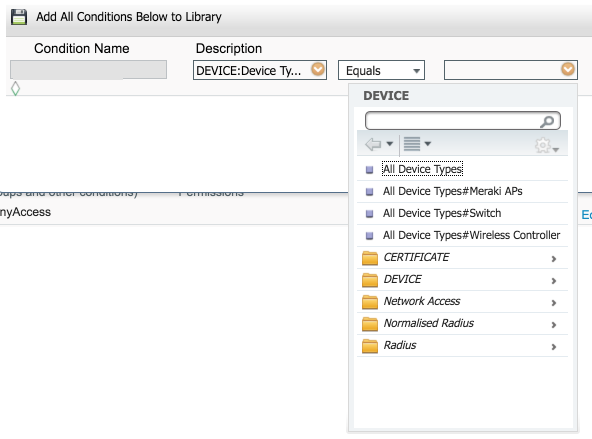
Devices does not really matter. Here is what I see when I create a device group (where you add the access point to this group), and then create the condition:
And here is where I create the condition of strategy game and you should be able to select the Meraki access points:
This will give you the condition similar to what I posted above. This is perhaps why you aren't hit that is not matching the condition for this game.
-
The traffic load between the power of Cisco ASA and FireSight Management Center fire
Hi all
I have a stupid question to ask.
Can I know what is the traffic load and the e/s flow between firepower Cisco ASA and FireSight Management Center?
Currently working on a project, client require such information to adapt to their network. Tried to find in the document from Cisco, but no luck.
Maybe you all have no idea to provide.
It varies depending on the number of events reported from the module to the CSP. No event = only health controls and policy changes are exchanged. 10,000 events per second = much more traffic.
Generally it is not a heavy load, however.
Maybe you are looking for
-
Hello, I have a mid 2010 21.5 (MC508LL/A) imac that has a bad graphics card. I've had this confirmed by an authorized Apple repair shop. I got an estimate of $643,00 for the repair, which I can't do right now. I heard that you can connect a second mo
-
Firefox works with Norton Identity Safe/Password Manager?
I tried the update of Firefox 5.0 to 6.0 before and seems to be losing my Norton Identity Safe/Password Manager installation. A this has been fixed, or I did something wrong before? See you soon. Micktaxi1
-
cookies.SQLite - shm & cookies.sqlite - wal?
While Firefox 6 is running, there are two additional cookies files in the profile of: cookies.sqlite - shm and cookies.sqlite - wal. They disappear when Firefox closes. What are doing?
-
Can I get notifications of text (tone) on my phone, as well as on the watch when I wear my watch?
Can I get notifications of text (tone) on my phone, as well as on the watch when I wear my watch?
-
Using a Cisco VPN on iPad and incorporating RSA tokens
Hello community of Cisco, I have what seems like a simple question. I have almost no experience network so hopefully someone here can answer that. I have this project iPad for my internship in which they want to create a remote access to their netw