AAA Cisco 600 and 700
Cisco ACS GANYMEDE + AAA can be activated for telnet to Cisco 600 and 700 routers?
Unfortunately you can not configure radius AAA or Ganymede in routers series 600 or 700.
Tags: Cisco Security
Similar Questions
-
FIDO solutions AAA Cisco support
Hi all
I wanted to know if Cisco is planning on integrating the FIDO standard in its products from AAA, specifically ACS and ISE.
Best regards
Patrick
ISE and Acs rely heavily on the reliance on passwords to authenticate users, also in their upcoming release. It is not so easy to eliminate the use of passwords. Cisco will certainly join the alliance in the near future. This is in the roadmap
-
Cisco VCS and integration Lync2013
Hello!
Could you tell me please, when CISCO officially support Lync2013 - free new software for VCS - C and documentation on integration?
The main interest is the possibility of transferring video between CISCO/MCU and Lync endpoints on the H.264 Protocol, who hails from Lync2013.
Right now, I've got VCS - C and RTM Lync2013 X7.2. During the video call without AMGW appeal established as audio only.
When using with Lync2010, it worked on Protocol H.263 and CIF resolution.
Evgeniy salvation,
We are currently investigating the possibilities to achieve interoperability between Lync 2013, VCS and video devices on the side of the VCS standards-based, it is a work in progress and at this stage, it is to early to provide any factual information on when interop will be available.
In contrast to Lync 2010, Lync 2013 does not support H.263 for video and it so that will remove the OCS/Lync integration. I do however think that you should be able to make a two-way video between Lync 2013 and VCS-joined endpoints if you use an AMGW tried that yet?
Thank you
Andreas
-
Backdoor in Cisco routers and firewalls.
The more I read on the NSA scandal (and Yes, I apparently a scandal) less I trust corporations hardware and software. There is no reason for anyone to doubt that all Cisco equipment comes with a backdoor. Because these probable backdoors exist it's a matter of time before hackers discover and exploit them. It's happened to Microsoft a number of times and there is no reason that it could not happen to Cisco. It is no longer our trust Cisco equipment and have already started researching alternatives network.
It is more a crazy conspiracy theory, that is the reality.
In all liklihood, we use a series of firewall to further isolate our network against intrusions. To reduce costs, we can keep our existing in this topology Cisco equipment, but we will replace hardware Cisco when it breaks down or needs to be upgraded. I do the same thing with my home network.
In the last months, we already moved all of our e-mail to secure servers overseas and changed all our McAfee, AVG and Avast antivirus software. We are also researching Linux distributions to replace Microsoft.
If Cisco wants to protect their brand, they need to take a stand or see their market share continue to erode. There must be a CEO to a U.S. company that will take this position and be a hero rather that continue to be a lap dog.
Hello
use open-source based linux firewalls and routers.
and check the source cod
-
Cisco show and share to publish on the internet
Dear Experts
We have new deployment for Cisco SNS, and we publish SNS on the internet. I need help to do it and any recommendations, please.
Thank you
Richard
Hi Richard
Solve you your problem? I have to make sure of the following.
1. you can access external SNS internally.
2-natting is ok between IP Public & private.
3. for the DNS record, make sure that the name must be the same on the inside & outside. For example internlly vod.bnp.med.ca and create a record public vod.bnp.med.ca should be the same FQDN, otherwise your SNS will never work. For authentication, you must publish the DMM.
Note: your question this internal FQDN differs from the external FQDN of the SNS.
Thank you
Please note all relevant information
-
I am very new to Cisco ISE and Meraki. I try to get the Radius configuration for wireless authentication. When I do a test of the Meraki to ISE, it passes.
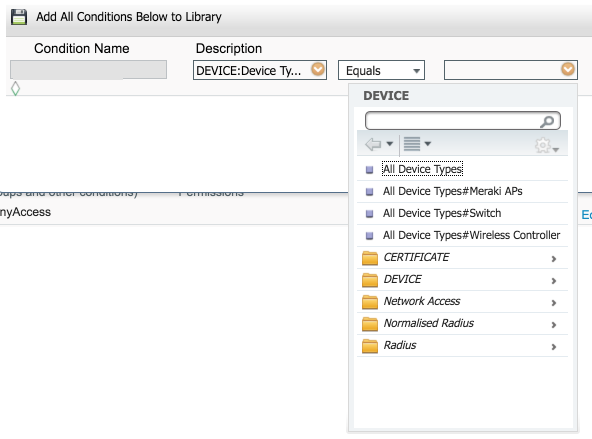
When I try to connect from my laptop, I look at the logs of the Radius and it passes; However, it does not connect me to good policy. I keep hitting the default policy. I have my Meraki police above the default policy in the strategy defined in article. I have attached what looks like my strategy game.
Devices does not really matter. Here is what I see when I create a device group (where you add the access point to this group), and then create the condition:
And here is where I create the condition of strategy game and you should be able to select the Meraki access points:
This will give you the condition similar to what I posted above. This is perhaps why you aren't hit that is not matching the condition for this game.
-
The traffic load between the power of Cisco ASA and FireSight Management Center fire
Hi all
I have a stupid question to ask.
Can I know what is the traffic load and the e/s flow between firepower Cisco ASA and FireSight Management Center?
Currently working on a project, client require such information to adapt to their network. Tried to find in the document from Cisco, but no luck.
Maybe you all have no idea to provide.
It varies depending on the number of events reported from the module to the CSP. No event = only health controls and policy changes are exchanged. 10,000 events per second = much more traffic.
Generally it is not a heavy load, however.
-
Configure to integrate Cisco ASA and JOINT
Hello
We have Cisco ASA and JOINT, need assistance on the integration of the same thing; Please email me so that I'll share the details of the architecture.
Thank you best regards &,.
REDA
Hi reda,.
If I correctly your diagram, you do not want to send any traffic from the external switch to the JOINT with a SPAN port and all traffic from your DMZ interfaces with another.
Is this correct?
If so, can you tell me why you want to inspect the traffic before it goes through the firewall? As I said in my original answer, we generally advise putting IP addresses after the firewall.
Not to mention that in your case, I guess that some traffic will be inspected twice so you will need to assign a different virtual sensors to each JOINT internal interfaces to ensure that the same instance does not see the traffic of several times.
Kind regards
Nicolas
-
What is the difference between Cisco NAC and ACS?
I am currently part of a new construction project and my Cisco account manager and sales engineer recommend Cisco NAC for our new MDF. I'm confused because I don't clearly know the difference between a Cisco ACS and the NAC. What is the difference?
Thank you
Chris
Chris,
The two are completely different, maybe the sales rep could present you with more information and application. Each offers a variety of services tailored to the specific needs. I think that we need to read more in depth on the proceeds of the NAC. NAC seems an excellent solution for authentication authorization but other regulatory compliance.
When you see ask your representative to sales for more information/demo.
ACS is more widely use as a central point to access control to network devices routers, an example is for acs accounting management and the authority to order on all devices on the network using acs as RADIUS server. Considering that the NAC is over a central point of safety inspection on earlier systems of access to your network by via LAN or outside, an example of these respected regulatory defined could be inspections could be virus definition checks before getting lan access thus preventing access to the LAN if the system does not have regulatory compliance defined in NAC access is denied. Another example could be the unknown local host connections etc... So, it seems that NAC is a much broader product that provides endpoint security internal, not only the authentication authorization as acs... ACS has been there for a long time, NAC is rather new product.
NAC
http://www.Cisco.com/en/us/NetSol/ns466/networking_solutions_package.html
ACS
http://www.Cisco.com/en/us/products/sw/secursw/ps5338/index.html
Rgds
Jorge
-
Turn on the mtu on cisco switch and cisco user server
Hi all
someone got bad luck turning on the mtu on their cisco switch? I guess I need to turn it on for all because the command is for all ports on cisco catalyst and my server switch is nearby to my user of switches and a broadband bandwidth 6 G or 6 ports, I need to turn it on for all user ports?
Thanks for any comments, that you can add.
I assume you mean Jumbo frame support! You shouldn't have any problems with that. Please take a look at for example http://www.cisco.com/en/US/products/hw/switches/ps700/products_configuration_example09186a008010edab.shtml for more details and the configuration of the different switches. According to the model, the parameters are for dedicated ports only or the entire switch. In the case of the switch everything you will need to reload (reboot) switch, so be careful.
André
-
Cisco VPN and Cisco 2651 customer support
I 2651 and remote VPN client
Client can successfully establish VPN to 2651 but nothing through this tunnel. In the stats customers there are no decrypted packets. In 2651 I saw the incoming packets but no response. What evil? (This cisco also make VPN tunnel with each other)
2651 config:
version 12.3
customer password username
AAA new-model
AAA authentication login userauthen local
AAA - the id of the joint session
crypto ISAKMP policy 3
BA 3des
preshared authentication
Group 2
!
crypto ISAKMP policy 10
md5 hash
preshared authentication
ISAKMP crypto key xxxx address xx.xx.xx.xx
ISAKMP crypto nat keepalive 20
!
ISAKMP crypto client configuration group 3000client
xxxxxxxxxxxx key
DNS 192.168.77.1
win 192.168.77.1
area xxx.xx
pool ippool
ACL 111
!
!
Crypto ipsec transform-set esp - esp-md5-hmac M-Chel
!
Crypto-map dynamic dynmap 10
game of transformation-M-Chel
!
!
card crypto client TunnelMap of authentication list userauthen
card crypto isakmp authorization list groupauthor TunnelMap
client configuration address card crypto TunnelMap answer
map TunnelMap 1 ipsec-isakmp crypto
defined peer xx.xx.xx.xx
game of transformation-M-Chel
match address 110
map TunnelMap 10-isakmp ipsec crypto dynamic dynmap
!
!
!
interface FastEthernet0/0
Description link to DMZ
IP address xxx.xxx.xxx.252 255.255.255.224
no ip route cache
no ip mroute-cache
automatic duplex
automatic speed
No cdp enable
no cache route NCLC
NAT outside IP
card crypto TunnelMap
!
interface FastEthernet0/1
Description network internal
IP 192.168.77.17 255.255.255.0
no ip route cache
no ip mroute-cache
automatic duplex
automatic speed
No cdp enable
NAT outside IP
no cache route NCLC
!
local pool IP 192.168.10.1 ippool 192.168.10.50
IP nat inside source list 1 interface FastEthernet0/0 overload
IP route 0.0.0.0 0.0.0.0 xxx.xxx.xxx.xxx permanent
!
access-list 110 permit ip 192.168.77.0 0.0.0.255 host xx.xx.xx.xx
access-list 111 allow ip 192.168.77.0 0.0.0.255 192.168.10.0 0.0.0.255
Two things:
You have not defined a group of authorization specifying that authorization for VPN clients will be done locally. Add the following:
AAA authorization groupauthor LAN
And your NAT statement is probably wrong, even if you have not shown that the ACL 1 is equal to. follow these steps:
IP nat inside source list 100 int fa0/0 overload
access-list 100 deny ip 192.168.77.0 0.0.0.255 host xx.xx.xx.xx
access-list 100 deny ip 192.168.77.0 0.0.0.255 192.168.10.0 0.0.0.255
access-list 100 permit ip 192.168.77.0 0.0.0.255 any
no nat ip within the source list 1 int Fa0/0 overload
Note that if you get an error after this last order saying NAT entries are in use, leave the config mode, do:
clear the ip nat trans *.
return to mode config, and then retype the command. You must make sure that when you do a 'wr t', there is only a single command 'ip nat inside source... ". "in the config and it is the one that refers to ACL 100.
-
Problem with Cisco ACS and different areas
Hello
We are conducting currently a problem with Cisco ACS that we put in place, and I'll try to describe:
We have ACS related directory AD areas, where we have 2 domains and appropriate group mappings.
Then we have our Cisco switches with the following configuration,
AAA new-model
AAA-authentication failure message ^ CCCC
Failled to authenticate!
Please IT networks Contact Group for more information.
^ C
AAA authentication login default group Ganymede + local
AAA authorization exec default group Ganymede + local
AAA authorization network default group Ganymede + local
AAA accounting exec default start-stop Ganymede group.
orders accounting AAA 15 by default start-stop Ganymede group.
!
AAA - the id of the joint session
But the problem is that with the users in a domain, we can authenticate, but not the other. Basically, the question is that when we check on the past of authentication, two authentications are passage and the display of 'Authentic OK', but on the side of the switch, there is a power failure.
There may be something wrong with the ACS?
Thank you
Jorge
Try increasing the timeout on IOS device using radius-server timeout 10.
Do we not have journaling enabled on the ACS server remotely?
-Philou
-
I have configured the aaa authentication in the pix firewall to see the ACS RADIUS Server for verification of the user. If the ACS server becomes unavailable, then I could not connet the pix firewall.
In the router, I have the configuration option
AAA authentication login default group Ganymede + local
that tells the router first looking for a radius server and if is not available connect through the local database.
Is there an option in the Cisco pix firewall to connect using local information if ACS is not available?
Thanks in advance
Hello
PIX back up method to entered the unit in the event of server failure aaa works on 6.3.4 code and above. In the codes plus late 6.3.4 If the RADIUS server fails it is impossible to get in unless password recovery. "However if we have not configured for console aaa authentication than user name: pix and password: cisco" works by default.
Kind regards
Mahmoud Singh
-
VPN poor Performance - Cisco RV220W and routers WRVS4400N
Hello
To one of our customer IPSec VPN is established between Cisco RV 220W and routers of Cisco WRVS4400N.
Router VPN /ISP details are as below
Location was Location B Details of the Internet
----------------------
DOWNLOAD: 6 to 10 Mbps
Upload: 1 to 2 MbpsDetails of router
----------------------
Cisco RV220W
Firmware: 1.0.3.5
IKE policy
Encryption: 3DES
Authentication: MD5
Group: Group 2
Life key: 28800 secVPN strategy
Encryption: 3DES
Authentication: SHA - 1
Group: 1024 bits (Group 2)
Life key: 3 600 s
Perfect Forward Secrecy: enabledDetails of the Internet
-------------------------
DOWNLOAD: 1.35 Mbps
Upload: 1.24 MbpsDetails of router
----------------------
Cisco WRVS4400N
Firmware version: V2.0.1.3
Phase 1
Encryption: 3DES
Authentication: MD5
Group: 1024 bits (Group 2)
Life key: 28800 secPhase 2
Encryption: 3DES
Authentication: SHA - 1
Group: 1024 bits (Group 2)
Life key: 3 600 s
Perfect Forward Secrecy: enabledFrom the day that VPN has been implemented, the performance was poor. Frequent disconnections sessions live to the VPN nodes and very low transfer rate was alarming to users.
The servers in A location and users to the site B gets authenticated at the server DC level in A location
Applications of Terminal Server remote as Quickbooks, QQ Evolution, attendance RX serve also the location has by users to the location B
The login is your time and all applications are extremely slow.
I tried to copy files between share data between two locations and the results are as follows
Location A to location B-> 130 Kbps 140 Kbps
Location location B A-> 150 Kbps to 160 Kbps
What can be the problem for these poor performance VPN?
-Change the encryption for the least secure OF THE /MD5 would have a significant impact because it can reduce the overload on the routers?
-Even if both routers are routers SMB, it has really good VPN flow according to the data sheets. I couldn't find VPN flow mentioned in the WRVS4400N data sheet. One of the sons of CSC, I also noticed the VPN of WRVS4400N flow seemed really low as only about 1.6Mbps. (https://supportforums.cisco.com/thread/2107881) Whereas RV220W router has VPN 90Mbps flow, according to the datasheet.
So, what can be the cause of the problem and what can be fixes possible?
Help, please!
ANUP sisi
Beginner to router Cisco VPN, please help
RVS4000 was designed to work in a small office. It supports 5 VPN tunnels with a maxium of 2 Mbps flow measured in a laboratory environment. It has a processor that has a motor integrated IPS, who would deliver 20 Mbps LAN - WAN throughput when IPS is enabled.
RV220W has been designed to operate in a slightly larger office with 25 IPsec VPN tunnels. It has a processor that has a built-in cryptographic engine able to deliver throughput 90 Mbps of IPsec. RV220W also supports 5 SSL VPN tunnels that can be used by employees and business partners for remote access.
-
IPSec vpn cisco asa and acs 5.1
We have configured authentication ipsec vpn cisco asa acs 5.1:
Here is the config in cisco vpn 5580:
standard access list acltest allow 10.10.30.0 255.255.255.0
RADIUS protocol AAA-server Gserver
AAA-server host 10.1.8.10 Gserver (inside)
Cisco key
AAA-server host 10.1.8.11 Gserver (inside)
Cisco key
internal group gpTest strategy
gpTest group policy attributes
Protocol-tunnel-VPN IPSec
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list acltest
type tunnel-group test remote access
tunnel-group test general attributes
address localpool pool
Group Policy - by default-gpTest
authentication-server-group LOCAL Gserver
authorization-server-group Gserver
accounting-server-group Gserver
IPSec-attributes of tunnel-group test
pre-shared-key cisco123
GBA, we config user group: VPN users. all VPN users in this group. ACS can visit his political profile: If the user in the 'VPN users' group, access ACS.
When we connect from a VPN Client to the server, all users connect to success. When you see the parser in ACS journal, each user success connect also get
error:
22040 wrong password or invalid shared secret
(pls see picture to attach it)
the system still works, but I don't know why, we get the error log.
Thanks for any help you can provide!
Duyen
Hello Duyen,
I think I've narrowed the issue. When remote access VPN using RADIUS authentication we must keep in mind that authentication and authorization are included on the same package.
Depending on your configuration, the ACS is defined as a server RADIUS (Gserver Protocol radius aaa server) and becomes the VPN Tunnel authenticated and 'authorized' on this server group:
authentication-server-group LOCAL Gserver
authorization-server-group Gserver
As noted above, the RADIUS of request/response includes authentication and authorization on the same package. This seems to be a problem of incorrect configuration that we should not set up the 'permission' in the Tunnel of the group.
Please remove the authorization under the Tunnel of Group:
No authorization-server-group Gserver
Please test the connection again and check the logs of the ACS. At this point there are only sucessful newspaper reported on the side of the ACS.
Is 'Permission-server-group' LDAP permission when authenticating to a LDAP server so to retrieve the attributes of permission on the server. RAY doesn't have the command as explained above.
I hope this helps.
Kind regards.
Maybe you are looking for
-
After update, can't login, just gear turns
After that I updated to 10.11.6, I cannot connect to my iMac. The login screen accepts my password, but the gear/turn icon just wirhout everything that happens. Then I rebooted into recovery mode and reinstalled bit El Capitan, the problem persists.
-
HP M9340f and Power Supply Upgrade graphics card
HP dear community, I read some of the forums on the upgrade of the 9500gs it's an old graphics used for the HP M9340f. It's been 4 years now and the computer still works very well. I need advice for the upgrade on the graphics card. My specs are: htt
-
Update to Windows 8.1 causing problems with S7-392
Since the upgrade to Windows 8.1, I have experienced frustrating problems with my S7-392. At this point the two main issues are: 1. when running on battery, it stops intermittently. Happens if I am using or not. I've fiddled with the power such as
-
Copy DVDs to drive hard and other DVD
I am a "senior" (67) with little experience with the new features. I have an old home movie a friend moved to a VCR tape to a DVD. My children want to best and I have no idea where to start. They make it sound simple and felt that I could do. Aparent
-
Wireless 800 keyboard some keys don't type symbol
I just installed 800 wireless keyboard. Some keyboard keys not typing the symbol displayed on the key. For example when I try to type the question mark when you press shift and the button with a question mark for this _. I have a problem with a numbe