Choosing iMac and MacPro
Looking for entry and helps in this decision-making process. Considering an iMac on a MacPro I for the convenience of space and portability currently and want to ask people here in the Mac publishing community for their 'opinion' and ' experience' with similar applications, work or use. I have retired and you want to reduce the amount of work that I do more to clean up my workspace of excessive and other cables.
Or the other system I edit with Photoshop CS5, FCPX, Lightroom and use (use) external thunderbolt matrix RAID 0 with two internal disks, mini disks external hard thunderbolt and a CD/DVD/BluRay external burner. I will edit not 3D. I will edit 1 4K video camera eventually, but not much. Most of my work will be no emergency BUT that said when I'm working I don't LIKE COLOR WHEEL LOOKS or mini jams. Finally, I get the SSD single bolt of lightning and hope that sometimes in 2016 thunderbolt RAID 0 with dual SSD.
Here are my specs current and proposed with the MacPro CURRENT being a "just above entry level" Late 2013 and proposed iMac which is an end of 2015 and at the top of the iMac.
CURRENT MacPro - iMac PROPOSED spec'd
MODEL: 6.1 end 2013-2015 (most recent) late
PROCESSOR: 3.7 GHz Quad Core Xeon E5 - 4.0 GHz i7 Skylake (burst at 4.3 GHZ
VIDEO: Over-pants D300 2 GB x 2 - Radeon R9 M395X 4 GB GDDR5 VRAM
MEMORY: 16 GB 1867 MHz DDR3 ECC - 32 GB 1867 MHz DDR3 ECC
SSD: 256-256 GB
FORMER ANNUAL VIDEO WORK: 50-100 @ 3 camera HD TV programs; ~ 15 weddings @ 3 camera HD; ~ 20 events; advertisements of 20-30 @ 1 HD camera; 20 to 30 other productions mainly @ 1 HD camera.
OLD WORK of ANNUAL PHOTO: ~ 10 commercials. ~ 8-10 marriages; ~ 3-5 events, ~ 3-5 birthdays/anniversies
PROPOSED CURRENT VIDEO:< 12="" tv="" programs="" @="" 1-3="" camera="" hd;="" 2-5="" weddings="" @="" 2="" or="" 3="" camera;="" 2-5="" events="" @="" 1-2="" cameras="" hd;="" ~="" 30="" commercials="" @="" 1="" camera="" hd;="" 10-12="" other="" @="" 1="">
Thanks to all those who respond and if the expected choice to make the iMac purchase, I will sell the MacPro and aged a year Thunderbolt display.
just an opinion, no experience in this League of the boxes, no users 'pro', just an amateur enthusiast here...:
I'm 4-6 rivers multicam editing on my MacMini (well Yes, tupperware box) on a weekly basis, no beach balls - how is it? FCPX using ' smart function to distribute the media on several media (and mine are just usb3, no CT). Bulit (transformation, CC, Center) effects are 'live', no need renderining effects no wheels, no waiting.
My latest toy is a cam 4 (Lumix fz1k) k - without no flaws, no lock either using proxies.
speaking of proxies, ok, when it comes to conversions on im - and export, I must admit hours might go look at a bar, more and more warp of snail...
Two links:
• my "stunt", 4x4k on a mini, set up at the same time improved by a post, usb3 SSD
• the speed test only elusive, BruceX, because FCPX is so highly integrated with Mac OS and hardware, any other criterion of reference is, imho!, simple waste of time. In terms of specs, my Mini is a Pocket Calculator-, but he runs circles around a consumer grade Windows machine, performing simple tasks, AP...
as said, me no technician, I am a user, what's going on "under the hood" is of no interest to me. Miss me the discussion of any 'speed'; faster conversions would be nice... nice2have, but it doesn't make sense for me to spend a sum of 5digit, just to wait 20 min instead of 25...
For the AP, the not-so-newMP seems to also not so well suited, what I have heard (but do not understand... CUDA? OpenGL? drivers?) its GPU doesn't support Adobe speed tips. Not first hand here, my budget does not rent the software.
My lil' son's latest project, a holiday film, with hundreds of photos and a gross of phone-vid mixture and actioncam-stuff, almost no matter what color corrected framework, the effects of home-brewn & titles, 35 min, fullHD > No when editing > 1 h beach balls for export, and even ancient iDVD (for Grandma & Grandpa) was done at least 30 min...
TL; Dr
a nMP? breathtaking! an iMac 2015 maxed out? same breathtakinger !
If you need it , if you need now - buy an iMac.
This "brutal by physicalattack" will solve your problems? I have the doubt.
Tags: Professional Applications
Similar Questions
-
Hello
I bought an air iMac, and now I would like to make a backup of my iPhone on this computer.
but the question is, if I do not have the backup that I did before, it is possible that I lost my dates?
because the computer I had entered is not an iMac.
Thank you
Francesca
Hello Francesca Montani,.
Thank you for using communities of Apple Support.
Congratulations on your new iMac! I understand from your message that you want to create a backfile to your iPhone 5 c, but are afraid of losing the data on it. I know how it is important for you to keep your data on your iPhone 5 c and to create a backup file for it.
When you plug your iPhone 5 c in your new iMac, iTunes should open. Your iPhone 5 c should also receive a message asking if you trust the computer. Go ahead and trust of the computer.
iTunes should display a page that says: Welcome to iTunes and you give 2 options. You want to choose the option to play up like new. Don't worry, it will not erase anything from your iPhone. The next page, you should see if the page summary of the iPhone. You should see a picture of an iPhone and a description.
In the middle of the right side, you should see a section called manually backup and restore. To create a backup file, select Back Up Now. This article has steps and a picture to help you create an iTunes up. I have also highlighted the steps below:
The backup of your iPhone, iPad and iPod touch
iTunes
- Open iTunes and connect your device to your computer.
- If a message asks you to Trust This Computer or device password, follow the steps on the screen. If you have forgotten your password, get help.
- Select your iPad, iPhone or iPod when it appears in iTunes. If your device does not appear in iTunes, know what to do.
- If you want to save data of health and activity of your device iOS or Apple Watch, you must encrypt your backup: check the box called Encrypt [device] backup and create a memorable password.
Write down your password and store it somewhere safe, because there is no way to recover your backups iTunes without this password.
If you do not need to save your health data and activity, you can make a backup that is not encrypted. Just click Back Up Now.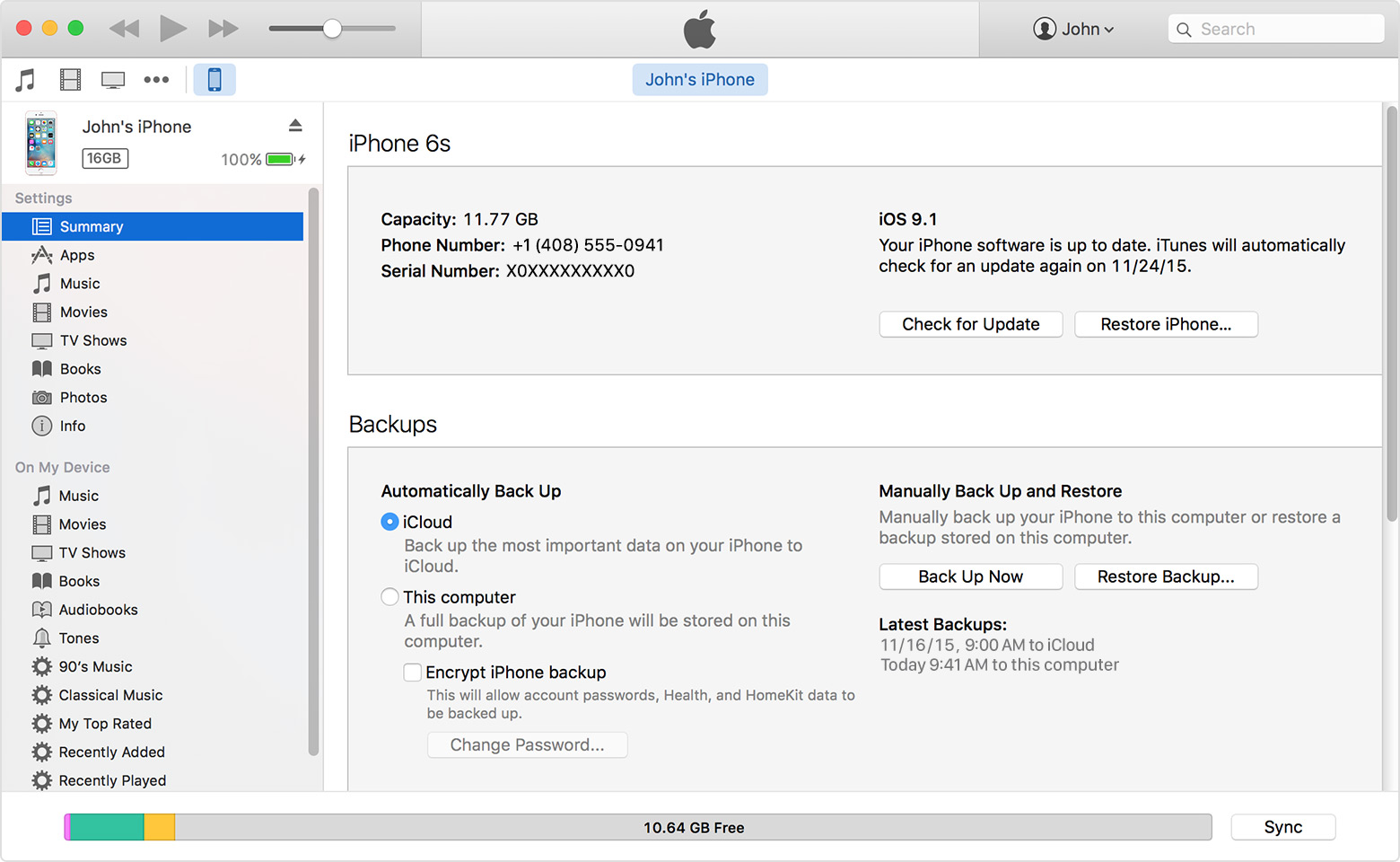
- After the end of the process, you can see if your backup completed successfully in the iTunes preferences > devices. You should see the name of your device with the date and time that iTunes created the backup. If you encrypted your backup, you should also see
 next to the name of your device.
next to the name of your device.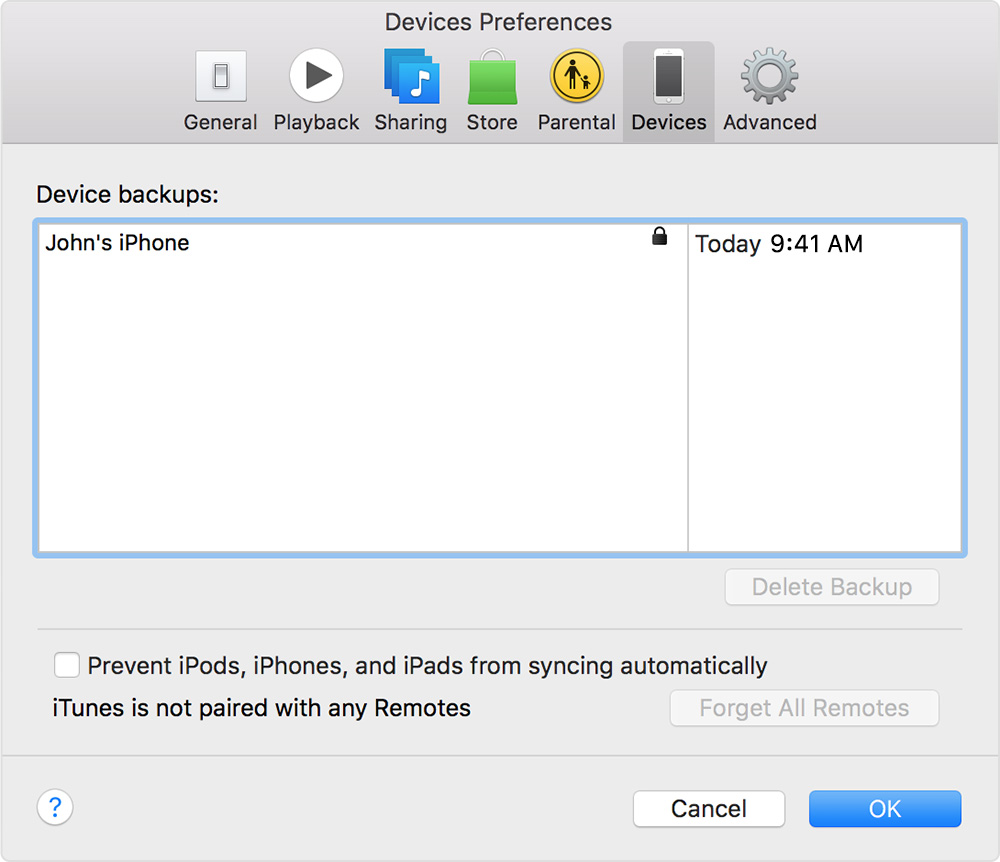
Best regards
-
Is a necessary additional security, such as McAfee software on the new iMac and iPad?
Is a necessary additional security, such as McAfee software on the new iMac and iPad?
Mac users often ask if they should install "anti-virus" (AV) or software "anti-malware". The answer is 'no', but it can give the false impression that there is no threat of what is loosely called 'virus '. There is a threat.
1. it is a comment on what you should - and should not-do to protect you from malicious software ("malware") that runs on the Internet and gets onto a computer as an unintended consequence of the user's actions.
It does not apply to the software, such as keyloggers, which can be installed deliberately by an intruder who has convenient access to the computer, or who has been able to take control of it remotely. This threat is in a different category, and there is no easy way to defend against it. AV software is not intended to and does not, to defend against these attacks.
The comment is long because the issue is complex. The essential points are in articles 5 and 11.
OS X implements now three levels of integrated protection specifically against malware, not to mention the protections of runtime such as quarantine the file, execute disable, sandbox, protecting the integrity of system, System Library randomization and randomized address space layout , which can also prevent other kinds of exploits.
2. all versions of Mac OS X 10.6.7 were able to detect the malware Mac known in downloaded files and block non-secure web plugins. This feature is transparent to the user. Apple calls internally it "XProtect."
The malware used by XProtect recognition database is automatically updated. However, you should not count on it, because the attackers are still at least a day before the defenders.
The following restrictions apply to XProtect:
☞ circumvented by some third-party network software, such as the BitTorrent clients and Java applets.
☞ It applies only to software downloaded on the network. Software installed from a CD or other media is not verified.
As new versions of Mac OS X are available, it is not clear whether Apple will continue indefinitely maintain the older versions such as 10.6 XProtect database. Versions of obsolete systems security may eventually be affected. Updates to security for the code of obsolete systems will be stop being released at any given time, and which can leave them open to other types of attack in addition to malware.
3. starting with the OS X 10.7.5, there was a second layer of built-in malware protection, designated "Gatekeeper" by Apple. By default, applications and installation packages downloaded from the network will be run only if they are digitally signed by a developer to a certificate issued by Apple. Certified software in this way has not been checked for safety by Apple, unless it comes to the App Store, but you can be reasonably sure that it has not been changed by someone other than the developer. His identity is known to Apple, so it could be held legally responsible if it distributes malicious software. Which may not mean much if the developer lives in a country with a weak legal system (see below).
Access controller does not depend on a database of known malware. He has, however, the same limitations as XProtect and in addition the following:
☞ It can easily be turned off or overridden by the user.
☞ A malware attacker could find a way around it, or could take control of a certificate of signing of code under false pretenses or could simply ignore the consequences of the distribution of malware Tryggvason.
☞ Developer App store could find a way around the Apple control, or the control may fail due to human error.
Apple took too long to revoke some known attackers codesigning certificates, thus diluting the value of the keeper and the program developer ID. These variances do not involve the App Store products, however.
For the reasons given, App Store, and, to a lesser extent - other applications recognized by signed Gatekeeper, are safer than others, but they cannot be considered to be absolutely sure. "Sand" applications could make to access to private data, such as your contacts, or for access to the network. Think that before granting access. Security sandbox is based on user input. Never click through any application for leave without thinking.
4. by starting with OS X 10.8.3, a third layer of protection has been added: a "Malware Removal Tool" (MRT). MRT runs automatically in the background. He checks and removes, malware that corresponds to a database of recognition held by Apple. To ensure that MRT will be executed when the database is updated, the App Store tab in system preferences and check the box marked
Install the system data files and security updates
If it is not already done.
As XProtect, MRT is effective against known threats, but not against strangers. It alerts you if it detects malware, but otherwise, it has no user interface.
5. the built-in Mac OS x security features reduce the risk of malware attack, but they are not and will never be complete protection. Malware is a problem of human behavior, not a behavior machine, and none only of technological solution will solve. Software protect you from trust only will make you more vulnerable.
The best defense is always going to be your own intelligence. Except perhaps feats of Java, all the known malware, circulating on the Internet wearing reached a completely setting installation to update to OS X 10.6 or later takes the form of so-called "Trojans", which may have no effect if the victim is deceived in their execution. The threat thus amounts to a battle of wits between you and cybercriminals. If you are better informed, they think you are, you win. In effect, it means that you always stay in the shelter of practical computing. How do you know when you leave the safe harbor? Here are a few signs warning of danger.
Software from a reliable source
☞ Software with a brand, such as Adobe Flash Player, does not come directly from the Web site. Don't be fooled an alert of any website for updating Flash, or your browser, or other software. A real alert that Flash is outdated and blocked is shown on this support page. In this case, follow the instructions on the support page. Furthermore, assume that the alert is false and that someone is trying to rip you off to install malicious software. If you see these alerts on more than one Web site, ask for instructions.
☞ Software any is distributed via BitTorrent or Usenet, or on a Web site that distributes pirated music and movies.
☞ Rogue sites Web such as CNET Download MacUpdate, Soft32, Softonic and SourceForge distribute free applications that have been packaged in a superfluous "install".
☞ The software is advertised through spam or intrusive web ads. Any announcement, on any site, which includes a direct link to a download should be ignored.
Software that is clearly illegal or doing something illegal
Commercial software ☞ high-end such as Photoshop is "cracked" or "free."
☞ An application helps you violates copyright law, for example to circumvent the copy protection on a commercial software, or streamed media recording to be reused without permission. All the 'YouTube downloaders' are in this category, but not all are necessarily malicious.
Conditional or unsolicited offer from strangers
☞ A phone calling or a web page you indicates that you have a "virus" and offers to remove. (Some reputable sites warned visitors who have been infected with the malware "DNSChanger" legitimately. The exception to this rule applies.)
☞ A web site offers a free content like music or video, but for use, you must install a "codec", 'plug-in', 'player' 'Downloader', 'extractor', or 'certificate' which comes from the same site, or a stranger.
☞ You win a prize in a competition that you are never entered.
☞ someone on a forum like this is eager to help you, but only if you download an application of your choice.
☞ a 'FREE WI - FI!' network presents itself in a public place like an airport, but is not provided by management.
☞ Online everything that you expect to pay is 'free '.
Unexpected events
☞ a file is downloaded automatically when you visit a web page, without any further action on your part. delete any file without opening it.
☞ You open what you think, it is a document and you receive an alert that it is "an application downloaded from the Internet." Click Cancel and delete the file. Even if you don't get the alert, you must always remove any download that is not what you expected it to be.
☞ An application does something you don't expect, such as permission to access your contacts, your location or the Internet without obvious reason.
☞ Software is attached to the email you na not ask, even if it is (or seems to come) by a person of trust.
I do not leave the safe harbour that once will necessarily lead to disasters, but make a habit of it will weaken your defenses against malicious software attacks. None of the above scenarios must, at the very least, make you uncomfortable.
6. Java on the Web (not to be confused with JavaScript, to which it is not related, despite the similarity of names) is a weak point in the security of any system. Java is, among other things, a platform to run complex applications in a web page. That was always a bad idea, and Java developers have proved unable to apply it without also creating a portal for malware to enter. Past Java exploits are the closest thing there has ever been a type virus Windows affecting OS X. simply load a page with Java malicious content could be harmful.
Fortunately, client-side Java on the Web is outdated and largely disappeared. Only a few outdated sites still use it. Try to accelerate the process of extinction by avoiding these sites, if you have a choice. Forget to play games or other uses not Java essentials.
Java is not included in OS X 10.7 and later versions. Discrete Java installers are distributed by Apple and Oracle (the developer of Java). Do not use one unless you need it. Most of the people don't. If Java is installed, turn it off- not the JavaScript in your browser.
Whatever the version, experience has shown that Java on the Web is not reliable. If you must use a Java applet for a job on a specific site, Enable Java only for the site in Safari. Never activate Java for a public Web site that carries the third-party advertising. Use only on websites that are well known, protected by login and secure without ads. In Safari 6 or later, you will see a padlock icon in the address bar when you visit a secure site.
7. another perennial weak point is Adobe Flash Player. Like Java, Flash is declining well deserved, but content Flash is still much more widespread than the contents of Java on the Web. If you choose to install the Flash plugin, you can reduce your exposure to Flash by checking the box marked
Stop the plug-ins to save energy
in the Advanced tab of the preferences of Safari window, if not already done. Consider also installing an extension Safari as "ClickToFlash" or "ClickToPlugin." They will prevent the Flash content automatically load and are initially not Flash video is substituted for Flash on YouTube and perhaps a few other sites. I tested the extensions and found them safe, but you should always do your own research before you decide whether to trust any third party software.
8. remain within the sphere of security, and you will be as safe from malware you can be practically. The rest of this comment is what you must do to protect you.
Never install any AV or products 'Internet security' for Mac if you have a choice, because they are all worse than useless. If you are required by a (wrong) institutional policy to install some kind of AV, choose one of the free apps in the Mac App Store, nothing else.
Why you should not use products AV?
☞ To recognize malware, software depends on a database of known threats, which is always at least one day to day. This technique is a proven failure, as a major supplier of AV software has admitted. Most of the attacks are "zero-day" - that is, previously unknown. Recognition-based AV does not defend against such attacks, and the enterprise IT industry comes to realize that the traditional AV software is worthless.
☞ design is based generally on the nonexistent threat that malware can be injected at any time, anywhere in the file system. Malware is downloaded from the network; He is not of the blue leaves. To meet this threat does not exist, a commercial AV software changes or low level functions of the operating system, which is a waste of resources and a frequent cause of instability, bugs, poor performance, and duplicates.
☞ changing the operating system, the software can also create weaknessesthat could be exploited by malicious attackers.
☞ especially, a false sense of security is dangerous. This fact relates to all AV software it will never be any changes elsewhere.
9. a free AV product from the Mac App Store is safe as long as you don't let it delete or move files. Ignore all the warnings that it can give you on "heuristic" or "phishing." These warnings, if they are not simply false positives, see the text of e-mail messages or updates cached web pages, not malware.
An AV application is not necessary and may not be invoked for protection against malware for OS X. It is useful, or even not at all, only to detect malware Windows and even for this use it is not really effective, because the new Windows malware makes its appearance much faster than OS X malware.
Windows malware cannot hurt you directly (unless, of course, you use Windows). Just do not pass to someone else. A malicious link in the e-mail is usually easy to recognize by the name alone. A concrete example:
London Terror Moovie.avi [124 spaces] Checked By Norton Antivirus.exe
You don't need software to tell you it's a horse Trojan for Windows. Software may be able to tell what trojan is, but who cares? In practice, there is no reason to use a recognition software, unless an organizational strategy requires. Malware Windows is so widespread that you must assume that it is in each attachment until proof to the contrary. Nevertheless, a free AV product on the App Store can serve a purpose if it fulfills a misinformed network administrator that says you must have some sort of application AV. An App Store product will not change the operating system; in fact, it does nothing, unless you run it.
If you are just curious to know if a file is considered malware by the AV engines, you can download it from the "VirusTotal" site, where it will be tested against most of them without charge. A negative result is evidence of what whether, for the reasons given above. I do not recommend doing this with a file that may contain private information.
10. There seems to be a common belief that the firewall Application acts as a barrier to infection, or prevents operation of malware. He does not. It blocks incoming connections to some network services you are using, such as file sharing. It is disabled by default, and you should leave it like that if you're behind a router on a private home or office network. Activate only when you are on an untrusted network, for example a public Wi - Fi hotspot, where you do not want to provide services. Disable services that you don't use in the sharing preferences window. All are disabled by default.
11. as a Mac user, you don't have to live in fear that your computer may be infected whenever you install the software, read emails, or visit a web page. But nor can you assume that you will always be free from exploitation, no matter what you do. Internet browsing, it's like walking the streets of a big city. It can be as safe or as dangerous that you choose to do so. The greatest harm done by software AV is precisely its selling point: it makes people feel safe. They can then feel sufficiently safe to take risks, which the software does not protect them. Nothing can reduce the need for safe computing practices.
-
Print via Wi - Fi on Photosmart Premium C309 connection problem on an iMac and MacBook Pro
Hi all
I just bought and installed a Photosmart Premium C309.
I am running the latest Mac OS 10.6.5 on two computers: an IMac and a MacBook Pro.
The printer software installation went well and I was able to print via USB cable.
Then I connected the printer to my wireless network (Modem-Router: Fritz!) Box Fon WLAN), again without problems.
I printed out a page of the control panel the printer network Test and got "no problems found. Congratulations on the successful your printer wireless installation.
But when I tried to print via the wireless network, I continued to get "printer offline".
I have disabled the firewall on the computer but no joy.
Now, I'm unable to print via the USB port that the printer is "offline".
Help!
Thank you
Problem solved! It has to do with Hello.
When you set up the printer with the HP installation wizard must install the Hello printer drivers when you are prompted to choose the drivers. Simple.
Thank you.
-
View the file encrypted on my iMac and iPhone
I have a file that contains sensitive data in what to be encrypted and password protected.
I need to read this file on my iMac and iPhone and also share this file with others who need it.
Is this possible?
Thank you
-Mike
A PDF file can be encrypted and password protected. A Mac can view this file by using either a snippet or Acrobat Reader and devices such as iPhones can also view these protected PDF files.
-
my iMac and paramedics have a bug
iMac (end 2013) 2.7 GHz Intel Core i5; 8 GB 1600 MHz DDR3; El Capitan 10.11.5
I had big problems with iTunes for years; developed but many more issues with Apple and other applications, data "disappear." quiting apps; need to reboot, etc., so took the Mac in a service center that has deleted all the data; reinstalled OSx and restored the backup data. This solves none of the problems and they said it was therefore "a bug" that was on the iMac and the back-up, so the only recourse would be to remove all the data permanently and start from scratch. Is there a possible way around this? (I'm not savvy). wise ideas would be much appreciated, thanks.
Download and run EtreCheck, created by one of his own assistants here in CSA. It is a diagnostic tool that is very useful for us to find problems. It will also give us additional specifications on your Mac. After his execution after the logfile here. It will never contain any personal information.
-
Hi, I'm updating my iMac and after that it restart again and write this panic report. Pleas if somebody know what can I do please help me
Anonymous UUID: F566129E-3EB9-4E28-4DF3-63D440FEBBB2
Kills Jul 26 14:32:01 2016
Panic report *.
panic (the appellant 2 cpu 0xffffff800dbb3bf2): "pointers element of invalid queue for 0xffffff8024cb0a40: 0 0"@/Library/Caches/com.apple.xbs/Sources/xnu/xnu-3248.60.10/osfmk/kern/queue.h prev: 241.
Backtrace (2 CPU), Frame: Return address
0xffffff918935b440: 0xffffff800dadab52
0xffffff918935b4c0: 0xffffff800dbb3bf2
0xffffff918935b640: 0xffffff800db508dc
0xffffff918935b710: 0xffffff800dae430a
0xffffff918935b750: 0xffffff800dfa228e
0xffffff918935b790: 0xffffff800e004324
0xffffff918935b7d0: 0xffffff800dfee5da
0xffffff918935b7f0: 0xffffff800dd383e8
0xffffff918935b830: 0xffffff800dd37fa8
0xffffff918935b890: 0xffffff800dd26ea7
0xffffff918935b8f0: 0xffffff800dd1a79f
0xffffff918935b9a0: 0xffffff800dd06358
0xffffff918935bbe0: 0xffffff800dd06e70
0xffffff918935bf60: 0xffffff800e028380
0xffffff918935bfb0: 0xffffff800dbeca58
The process corresponding to the current thread BSD name: AdobeUpdateDaemo
Mac OS version:
15G 31
Kernel version:
15.6.0 Darwin kernel version: Thu Jun 23 18:25:34 PDT 2016; root:XNU-3248.60.10~1/RELEASE_X86_64
Kernel UUID: B5AA8E3E-65B6-3D0E-867B-8DCCF81E536C
Slide kernel: 0x000000000d800000
Text of core base: 0xffffff800da00000
Text __HIB base: 0xffffff800d900000
Name of system model: iMac12, 2 (Mac-942B59F58194171B)
Availability of the system in nanoseconds: 94483899823
last load kext to 53361190473: com.apple.driver.AppleBluetoothHIDKeyboard 181 (addr 0xffffff7f8fadd000, size 16384)
kexts responsible:
com.apple.driver.AudioAUUC 1.70
com.apple.driver.AppleHWSensor 1.9.5d0
com.apple.driver.AppleTyMCEDriver 1.0.2d2
com.apple.driver.AGPM 110.22.0
com Apple.filesystems.autofs 3.0
com.apple.driver.AppleBluetoothMultitouch 90.3
com.apple.driver.AppleOSXWatchdog 1
com.apple.driver.AppleMikeyHIDDriver 124
com.apple.driver.AppleMikeyDriver 274.12
3.12.8 com.apple.driver.ApplePolicyControl
com.apple.driver.AppleHDAHardwareConfigDriver 274.12
com.apple.driver.AppleHDA 274.12
com.apple.driver.AppleUpstreamUserClient 3.6.1
com.apple.kext.AMDFramebuffer 1.4.2
com Apple.Driver.pmtelemetry 1
com.apple.iokit.IOUserEthernet 1.0.1
com.apple.AMDRadeonX3000 1.4.2
com.apple.driver.AppleIntelHD3000Graphics 10.0.0
3.12.8 com.apple.driver.AppleMuxControl
com.apple.iokit.IOBluetoothSerialManager 4.4.6f1
com.apple.driver.AppleThunderboltIP 3.0.8
com.apple.driver.AppleBacklight 170.8.9
com.apple.iokit.BroadcomBluetoothHostControllerUSBTransport 4.4.6f1
com.apple.driver.AppleSMCPDRC 1.0.0
com.apple.driver.AppleLPC 3.1
com.apple.kext.AMD6000Controller 1.4.2
com.apple.driver.AppleIntelSNBGraphicsFB 10.0.0
com.apple.driver.AppleSMCLMU 208
com.apple.Dont_Steal_Mac_OS_X 7.0.0
com.apple.driver.ACPI_SMC_PlatformPlugin 1.0.0
com.apple.driver.AppleFIVRDriver 4.1.0
com.apple.driver.AppleMCCSControl 1.2.13
com.apple.driver.AppleHV 1
com.apple.driver.AppleIntelSlowAdaptiveClocking 4.0.0
com.apple.iokit.IOBluetoothUSBDFU 4.4.6f1
com.apple.iokit.SCSITaskUserClient 3.7.7
com.apple.driver.AppleIRController 327,6
com.apple.driver.AppleUSBStorageCoexistentDriver 3.7.1
com.apple.driver.AppleUSBCardReader 3.7.1
com.apple.driver.AppleFileSystemDriver 3.0.1
com.apple.AppleFSCompression.AppleFSCompressionTypeDataless 1.0.0d1
com.apple.AppleFSCompression.AppleFSCompressionTypeZlib 1.0.0
com.apple.BootCache 38
2.8.5 com.apple.iokit.IOAHCIBlockStorage
com.apple.iokit.AppleBCM5701Ethernet 10.2.0
com.apple.driver.AppleAHCIPort 3.1.8
com.apple.driver.AppleFWOHCI 5.5.4
com.apple.driver.AirPort.Atheros40 700.74.5
com.apple.driver.usb.AppleUSBUHCIPCI 1.0.1
com.apple.driver.usb.AppleUSBEHCIPCI 1.0.1
com.apple.driver.AppleRTC 2.0
com.apple.driver.AppleACPIButtons 4.0
com.apple.driver.AppleHPET 1.8
com.apple.driver.AppleSMBIOS 2.1
com.apple.driver.AppleACPIEC 4.0
com.apple.driver.AppleAPIC 1.7
com.apple.driver.AppleIntelCPUPowerManagementClient 218.0.0
com Apple.NKE.applicationfirewall 163
com Apple.Security.Quarantine 3
com.apple.security.TMSafetyNet 8
com.apple.driver.AppleIntelCPUPowerManagement 218.0.0
com.apple.driver.AppleBluetoothHIDKeyboard 181
com.apple.driver.AppleHIDKeyboard 181
com Apple.kext.Triggers 1.0
com.apple.driver.IOBluetoothHIDDriver 4.4.6f1
com.apple.driver.AppleMultitouchDriver 304.12
com.apple.driver.AppleHIDTransport 5
com.apple.driver.DspFuncLib 274.12
com.apple.kext.OSvKernDSPLib 525
com.apple.iokit.IOSurface 108.2.3
com.apple.iokit.IOAcceleratorFamily2 205.11
3.12.8 com.apple.driver.AppleGraphicsControl
com.apple.iokit.IOSerialFamily 11
com.apple.iokit.IOFireWireIP 2.2.6
com.apple.driver.AppleBacklightExpert 1.1.0
com.apple.iokit.IONDRVSupport 2.4.1
com.apple.iokit.IOBluetoothHostControllerUSBTransport 4.4.6f1
com.apple.iokit.IOBluetoothFamily 4.4.6f1
com.apple.driver.AppleHDAController 274.12
com.apple.iokit.IOHDAFamily 274.12
com.apple.iokit.IOAudioFamily 204.4
com.apple.vecLib.kext 1.2.0
com.apple.driver.AppleThunderboltEDMSink 4.1.1
com.apple.kext.AMDSupport 1.4.2
3.12.8 com.apple.AppleGraphicsDeviceControl
com.apple.driver.AppleSMBusPCI 1.0.14d1
com.apple.driver.IOPlatformPluginLegacy 1.0.0
com.apple.driver.IOPlatformPluginFamily 6.0.0d7
com.apple.driver.AppleSMBusController 1.0.14d1
com.apple.iokit.IOGraphicsFamily 2.4.1
com.apple.driver.AppleSMC 3.1.9
com.apple.driver.CoreCaptureResponder 1
com.apple.iokit.IOSlowAdaptiveClockingFamily 1.0.0
com.apple.iokit.IOSCSIMultimediaCommandsDevice 3.7.7
com.apple.iokit.IOBDStorageFamily 1.8
com.apple.iokit.IODVDStorageFamily 1.8
com.apple.iokit.IOCDStorageFamily 1.8
com.apple.iokit.IOAHCISerialATAPI 2.6.2
com.apple.iokit.IOUSBHIDDriver 900.4.1
com.apple.iokit.IOUSBMassStorageClass 4.0.2
com.apple.iokit.IOSCSIBlockCommandsDevice 3.7.7
com.apple.iokit.IOUSBMassStorageDriver 1.0.0
com.apple.iokit.IOSCSIArchitectureModelFamily 3.7.7
com Apple.Driver.USB.cdc 5.0.0
com.Apple.Driver.USB.Networking 5.0.0
com.apple.driver.usb.AppleUSBHostCompositeDevice 1.0.1
com.apple.driver.usb.AppleUSBHub 1.0.1
com.apple.driver.AppleThunderboltDPInAdapter 4.1.3
com.apple.driver.AppleThunderboltDPOutAdapter 4.1.3
com.apple.driver.AppleThunderboltDPAdapterFamily 4.1.3
com.apple.driver.AppleThunderboltPCIDownAdapter 2.0.2
com.apple.driver.AppleXsanScheme 3
com.apple.driver.AppleThunderboltNHI 4.0.4
com.apple.iokit.IOThunderboltFamily 6.0.2
com.apple.iokit.IOEthernetAVBController 1.0.3b3
com.apple.driver.mDNSOffloadUserClient 1.0.1b8
com.apple.driver.AppleUSBMergeNub 900.4.1
com.apple.iokit.IOAHCIFamily 2.8.1
4.6.1 com.apple.iokit.IOFireWireFamily
com.apple.iokit.IO80211Family 1110.26
com.apple.iokit.IONetworkingFamily 3.2
com Apple.Driver.corecapture 1.0.4
com.apple.driver.usb.AppleUSBUHCI 1.0.1
com.apple.iokit.IOUSBFamily 900.4.1
com.apple.driver.usb.AppleUSBEHCI 1.0.1
com.apple.iokit.IOUSBHostFamily 1.0.1
com.apple.driver.AppleUSBHostMergeProperties 1.0.1
com.apple.driver.AppleEFINVRAM 2.0
com.apple.driver.AppleEFIRuntime 2.0
com.apple.iokit.IOHIDFamily 2.0.0
com.apple.iokit.IOSMBusFamily 1.1
com Apple.Security.sandbox 300.0
com.apple.kext.AppleMatch 1.0.0d1
com.apple.driver.AppleKeyStore 2
com.apple.driver.AppleMobileFileIntegrity 1.0.5
com.apple.driver.AppleCredentialManager 1.0
com.apple.driver.DiskImages 417,4
com.apple.iokit.IOStorageFamily 2.1
com.apple.iokit.IOReportFamily 31
com.apple.driver.AppleFDEKeyStore 28.30
com.apple.driver.AppleACPIPlatform 4.0
com.apple.iokit.IOPCIFamily 2.9
com.apple.iokit.IOACPIFamily 1.4
com.apple.kec.Libm 1
com Apple.KEC.pthread 1
com Apple.KEC.corecrypto 1.0
Model: iMac12, 2, IM121.0047.B23 of BootROM, 4 processors, Intel Core i5 2.7 GHz, 12 GB, MSC 1.72f1
Graphics card: AMD Radeon HD 6770 M, AMD Radeon HD 6770 M, PCIe, 512 MB
Memory module: BANK 0/DIMM0, 2 GB, DDR3, 1333 MHz, 0x80AD, 0x484D54333235533642465238432D48392020
Memory module: BANK 1/DIMM0, 2 GB, DDR3, 1333 MHz, 0x80AD, 0x484D54333235533642465238432D48392020
Memory module: 0/DIMM1 BANK, 4 GB DDR3, 1333 MHz, 0 x 0198, 0x393930353432382D3035312E4130304C4620
Memory module: 1/DIMM1 BANK, 4 GB DDR3, 1333 MHz, 0 x 0198, 0x393930353432382D3035312E4130304C4620
Airport: spairport_wireless_card_type_airport_extreme (0x168C, 0x9A), Atheros 9380: 4.0.74.0 - P2P
Bluetooth: Version 4.4.6f1 17910, 3 services, 27 aircraft, 1 incoming serial ports
Network service: Wi - Fi, AirPort, en1
Serial ATA Device: WDC WD1001FALS-403AA0, 1 TB
Serial ATA Device: OPTIARC DVD RW AD - 5680H
USB device: USB 2.0 Bus
USB device: FaceTime HD camera (built-in)
USB device: Hub
USB device: Hub BRCM2046
USB Device: USB Bluetooth host controller
USB device: USB 2.0 Bus
USB device: Hub
USB Device: IR receiver
USB Device: Card reader
Bus crush: iMac, Apple Inc., 22.1
First remove all the third-party RAM installed on the computer and re - built-in. Then, restart and test, whether the KIMBERLEY process continues to have a barrette of faulty RAM MEMORY.
Finally, what third party RAM brand has been installed? In these forums, because the iMacs are sensitive and benefit from the high quality of RAM, the Crucial two (buy it direct) and the two OWC (www.macsales.com) RAM are recommended because of their high quality and reasonable price. You can also have another hardware problem, in your case I would try to boot from the Partition Recovery (command + R to start) and open disk utility to see if the boot disk is found. You can also use Apple Hardware Test or Apple Diagnostics according to the age of the computer to run a test to see if two applications can detect any material error.
-
Implementation of new iMac in late 2006 iMac and external hard drive
I have a late 2006 iMac 2.16 GHz intel core 2 duo with 2.5 GB which I Lion 10.7.5. I don't think I can improve operating systems, or more if they are not compatible. I have an external hard drive that stores my photos, music etc I just ran out of space on iMac. I decided to upgrade to the new iMac. I thought that I would be able to plug in my external hard drive which has also my Time Machine backup and all the news would move to the new iMac. However, the external hard drive is Firewire 800. I connect it to the old iMac with adapter on the Firewire 400 port. The new iMac has USB3.
1. How can I connect external drive to the new iMac? You can get a Firewire 800 cable USB3 (online research I don't think)
2 read online it seems to say that you need to update your software on your old iMac to match the new iMac otherwise the time Machine can not read information correctly. It is not possible on the old iMac, what should I do?
I'm looking at my beautiful new iMac and the have not yet enabled.
The cable would probably be Thunderbolt to FireWire, check the available adapters
to see what should be the part. You would not upgraded an outdated old
Mac for a last OS X when he cannot go. Use the Migration Wizard or
migrate after installation. Some of these older applications or documents created
can be updated easily; Some may require conversion. Depending on your files.
The manual method is sometimes preferred. A new computer may balk
a lot of stuff which is reduced to an antique.
• OS X: manually migrating the data from another Mac - Apple Support
You may reflected on this article:
• Move your content to a new Mac - Apple Support
https://support.Apple.com/en-us/HT204350
If you have a time Machine, there are several articles on how to use it,
How to upgrade and so on. -A classic example of the info source is here:
• Apple OS X and Time Machine tips:
http://www.pondini.org/OSX/home.html
• If you cannot back up or restore your Mac with Time Machine - Apple Support
Good luck!
-
I was given this iMac and the Launchpad does not appear in the finder.
I was given this iMac and the Launchpad is missing from the folder in the Finder.
How can I get it back?
FWIW, you didn't say what iMac or which version of OSX, but reinstalling OS x is the only way I know.
-
Mail question: I want to remove my archived email (10, 000 ~) because I want to clean my iMac and make it more effective. Does anyone know if the removal of archive e-mail will leave my Inbox and saved intact E-mail or anything that doesn't fade too?
Who is your e-mail provider?
-
Before you synchronize my iMac and MacBook Pro, in my Bookmarks Menu dΘroulant, all my favorites were colored icons - now they have disappeared - how to bring them back?
It seemed to work on my FF 9.0.1 and Lion Mac. When I tried to set this parameter on FF 8.0.1 was ALREADY set to "FALSE". Must be something else?
-
I have 2 imacs and a laptop computer and you want to back up all three wireless via time capsule on my existing wifi network. If we can also use the time capsule as my wifi and replace my uverse wifi, that would be great. possible?
If you want to make sure that you will be able to get the Apple support in case of problems or questions with your backups, you must use the wireless Time Capsule to back up your Mac.
As long as the time Capsule provides a wireless signal, you can decide who to your 'main' network, then use it wireless Uverse for "guest", or children. If you do not need the Uverse router/modem wireless at all, it is possible to turn off wireless on the device and make it work only as a support modem/router...with Uverse wired.
At this point, you can start thinking about how you want to configure things and get back in touch if you need some advice on how to do it. We need to know what operating system that uses the Mac that you normally use to administer the time Capsule, provide good instructions, if you need it.
-
Don t work under El Capitan and I don't get an update/upgrade? I've used until yesterday an old MacBook pro and Lion, everything was perfect with an opening. Now, with the new element (iMac) and El Capitan, I have problems.
It is not possible to update the version of Aperture is 3.4.5
What can I do?
You can only update if you have a version of the AppStore of Aperture - if your version of Aperture appears in the history of your purchases on the App Store. Update and then reinstalling. See this tip of the user for more details:
-
I had an old iMac and had 2 external drives attached to it. I got a new iMac and now can not plug old external drives were firewire 400 how can I hook up t he old external hard drives?
You need a FireWire 400 adapter FireWire 800 and one FireWire 800 adapter Thunderbolt.
(141473)
-
I just bought a new IMAC and can't find my Cannon M8150 on printers
Can someone tell me what is it please
With your printer connected to your iMac and power, restart your iMac. Read this article from Apple on the management of your printer.
Maybe you are looking for
-
Text editor ' Save as... '. "broken - replaces the original file as well
' Save as... '. "removed some sort items of menu standards a long time ago, but I used this http://osxdaily.com/2012/08/27/enable-save-as-os-x-mountain-lion/ to restore a just as long. This addition of shortcut recently stopped working properly. Crea
-
Deletion notes on iPhone auto 5
On my wife 5 iPhone app notes removes the notes after 30 days; How can I disable this feature? Thank you
-
Satellite Pro 6070 - after reformatting the functions work
HelloI have an old pro SP 6070 satellite which was formatted after the virus attack. but reformatting reintall the functions such as speed, infrared and wireless antennas are function (Fn).Do you think that someone would have the original cd to reins
-
The meaning of the icons on the screen of welcome of LabVIEW
Hello ~ I think that the first icon on the left side meant the PC have been installed "in time real toolkit", and the second is 'Vision eradicating toolkit '. It's the third icon? Is - this Mathscript toolkit? Is there a source code for "Welcome.vi"
-
Images will not appear on Facebook in Google Chrome...
I have an icon with a red square, a blue triangle and a green circle instead of see a lot of images. How can I get rid of this problem and see my pictures again?