Confusion of the AAA
In the AAA configuration guide, it says you must apply the method of access to lines and interfaces, but if I use the aaa authentication login apparently apply the authentication method for all methods of login anyway?
Is it because I'm using a default method list?, and I only need to apply the method defined lists of interfaces or lines? but as I don't have the default value is used.
When we use by default it is applied to all lines. If there is no list of methods defined on the default interface will not take effect.
Kind regards
~ JG
Tags: Cisco Security
Similar Questions
-
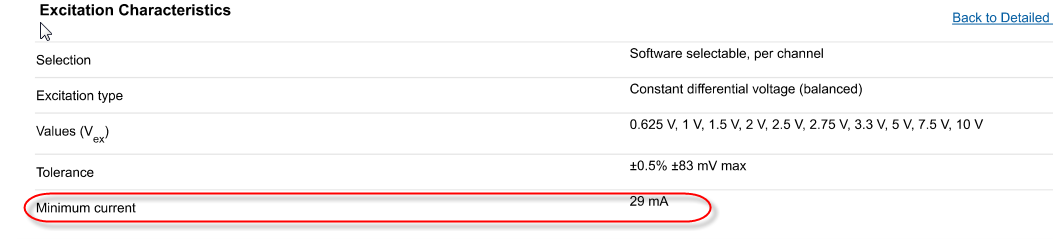
Confusion about the Source of excitement in the bridge SMU-4331 input module
Hello
I had some confusion through the input of the bridge SMU-4331 sheet module.
In the features section of excitement, its current Minimum as 29mA says. What it means. It can only current greater than 29mA delivery!
I think this should me Maximum current specification.
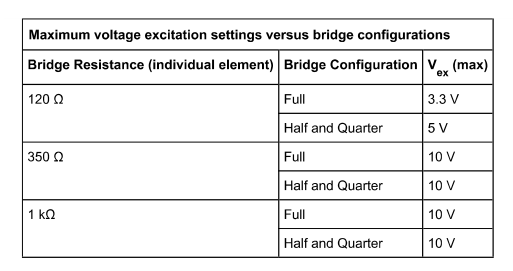
If you look at the table below
350 ohm resistance, the current should be 10V/350 ohm = 28.5mA
but for 1 K ohm, current will me 10V/1Kohm = 10mA, which isn't normal, if you specify current minimum as 29mA.
any thoughts?
Kind regards
Mirash
Hello Mirash,
I'm glad I could help!
As for your other question, the SMU-4330/4331 are inherently peripheral ratiometric. This means that they are designed to detect the level of excitement and range of the ADC to the appropriate scale. In this way, we can compensate for permanent changes in the voltage. One of our engineers wrote a big article really nice area on the subject I would recommend that you take a look at: Sensors of Measuring Bridge-Based with the ratiometric approach
See you soon,.
-
Confused about the notion of VLAN
I'm confused about the VLAN. I thought that the notion of VLAN was this computer on different VLANS were not suppose to be able to communicate with each other. I am setting up a 6248 and for me to get DHCP to work, I need to enable ip Routing. When I turn the routing ip, all computers on different VLANS are able to ping each other. Is - it the way it was suppose to work, or am I missing something?MGMT is on vlan 4093DHCP is on VLAN 100 trunk e34 10.10.1.1Host 1 is on VLAN 200 trunk e34 10.10.2.1Host 2 is on VLAN 300 trunk e34 10.10.3.1active IP routing
-
Extremely confused with the extremely complicated presentation of BlackBerry applications
Please help me, I'm very confused with the extremely complicated presentation of BlackBerry applications.
I made an app, the name is "App", I got signed and downloaded the App using the emulator Ripple, with the word 'HelloWorld' signature (password not true of course).
Now, I do another application, with the name of the App (B) I CAN'T use the same HelloWorld signature password because the emulator Ripple said "Oh, Snap!" Build request failed with the message: [ERROR] error: Code signing request failed because this version of the application or the package has been previously signed. If please increment the version (s) and try to connect again. »
Now, I don't understand and I am EXTREMELY confused with the presentation of the model of application for Blackberry.
I should first request, for an another RDK and COMINCO files create a new signature for App B password?
Or should I just increment the bundle version? the problem is when I tried it on Blackberry server seems to give narrations of error message that the APP ID is already used.
Okay, I'm officially stuck and I don't know what to do. Can any developer of blackberry here or the official employee blackberry tells me what I need to do?
Thank you.
I do not use ripple either but can see what the problem is (nothing to do with the ripple)
Open your file config.xml for the new project (probably copied 'App A'?)
In the widget section, change the id to something different, for example com.example.AppB
Save - reload the ripple and make sure you have the new ID in the Config-> Widget
All sorted
-
the AAA authentication enable default group Ganymede + activate
I implement CSACS 4.0. First of all on the client, I will apply aaa authenticatio / authorization under vty. The issure if I use the followin command
the AAA authentication enable default group Ganymede + activate
What happens if I connect via the console? I need to enter a name of user and password?
Here is my configuration
AAA new-model
Group authvty of connection authentication AAA GANYMEDE + local
the AAA authentication enable default group Ganymede + activate
authvty orders 15 AAA authorization GANYMEDE + local
RADIUS-server host IP
Radius-server key
Ganymede IP source interface VLAN 3
AAA accounting send stop-record an authentication failure
AAA accounting delay start
AAA accounting exec authvty start-stop group Ganymede +.
orders accounting AAA 15 authvty power group Ganymede +.
AAA accounting connection authvty start-stop group Ganymede +.
line vty 0 15
connection of authentication authvty
authorization orders 15 authvty
authvty connection accounting
accounting orders 15 authvty
accunting exec authvty
Any suggestion will be appreciated!
It should work because it is a guest message.banner whenever you try to connect (console/vty). I set it up on my router.
If you have banner motd, it will appear as well (see below). So, I have to remove it to get only the aaa banner & prompt is displayed:
************************************************************
Username: cisco, password: cisco (priv 15f - local) *.
************************************************************
Any unauthorized use is prohibited.
Enter your name here: User1
Now enter your password:
Router #.
The configuration more or less looks like this:
AAA new-model
AAA authentication banner ^ is forbidden to use CUnauthorized. ^ C
AAA authentication password prompt "enter your password now:
AAA-guest authentication username "enter your name here:
Group AAA authentication login default RADIUS
local authentication AAA CONSOLE connection
HTH
AK
-
Need help with the configuration of the AAA
I try to configure AAA on my network devices. I use GANYMEDE + with an ACS (3.2) server. I have groups of users of installation against two in the ACS, 1 voice server and allow privileges and the other without. I am able to get the AAA configuration to work when telnet in devices. However, when you connect in the port of the console, the user with privileges to activate Group do not go directly in the activation of the mode as do the users of telnetted. How to solve this problem?
Hello
You should not use the following command: -.
authorization AAA console
This command will not be displayed on the help.
Kind regards
Vivek
-
The AAA authentication configuration
We have ACS server 3.1 to AAA for authentication for all routers and switches. I want each person to connect the router using its own id, password password and activate. If the ACS server is unavailable, I want to have different id, password and enable password for console and telnet access. What is the right way to do this? I also want to follow all orders entered on the router.
That's what I have:
AAA new-model
AAA authentication login default group Ganymede + local
enable AAA authentication login no_tacacs
the AAA authentication enable default group Ganymede + line
AAA authorization exec default group Ganymede + local
AAA authorization commands 15 default group Ganymede + local
AAA accounting exec default start-stop Ganymede group.
orders accounting AAA 15 by default start-stop Ganymede group.
!
username admin password 7 xxxxxxxxxxxxxxxx
!
!
Line con 0
connection of authentication no_tacacs
line to 0
line vty 0 4
password 7 xxxxxxxxxxxxxxxxxxxxxxxx
!
Yes, it's Joy on the right. Thank you, Renault
-
The AAA for PIX515E 6.3 rules (5)
Hello. If I wanted to configure the PIX for the authentication of an ACS server (for the purpose of management of PIX), what else would need apart from what follows:
AAA-server Admin-FW Protocol Ganymede +.
AAA-Server Admin-FW max-failed-attempts 3
AAA-Server Admin-FW deadtime 10
!
AAA-Server Admin-FW (inside) host 192.168.2.9 access timeout 10
!
console series FW-Admin-AAA authentication
Console telnet authentication AAA Admin-FW
authentication AAA ssh console Admin-FW
As far as I KNOW, I did not specify which IP addresses can someone telnet from to connect on the PIX. I tried the following, but I do not know I did not provide the correct instructions:
the AAA authentication include telnet inside 192.168.0.0 255.255.0.0 Admin-FW
... and I have a username / password to invite him on the PIX but it keeps asking for a user name and password. I know my account GANYMEDE is good because I can connect on the routers with the same details as what I use to authenticate on the PIX.
I also ran a debugging on the PIX when I was trying to authenticate. The output is attached.
Thank you
Timothy
Hi Tim,.
There is no need to order,
the AAA authentication include telnet inside 192.168.0.0 255.255.0.0 Admin-FW
Try it now and see if you get hits on ACS. Incase it is not working, pls get again him debugs.
Thank you
Jagdeep
-
Excluding the lines of Terminal Server in the AAA authentication
Hi all
Hope you can help, I'm trying to find a solution to exclude only the following line port by using the AAA authentication (ACS GANYMEDE +) on a map of Terminal Server on a Cisco 2600 router. Does anyone know how to do this, or point me in the right direction to solve?
I've included the output below:
AAA authentication login default group Ganymede + local
AAA authorization exec default group Ganymede + local
AAA accounting exec default start-stop Ganymede group.
AAA accounting network default start-stop Ganymede group.
AAA accounting default connection group power Ganymede
AAA accounting system default start-stop Ganymede group.
AAA - the id of the joint sessionline 41
session-timeout 20
decoder location - XXXXXX XXXXXX BT
No banner motd
No exec-banner
absolute-timeout 240
Modem InOut
No exec
transport of entry all
StopBits 1
Speed 38400Is it a question of disabling the command line or using a defined group?
Thanks a lot for your help.
Jim.
Hi Jim
You may need to create another group for authentication to the and send your AAA configuration
line to 0
connection of authentication aux_auth
AAA authentication login aux_auth line
You can also configure a username local/pw and map it on the group to here...
Console and telnet would still use the configured default group, or you can specify specific groups:
Line con 0
console login authentication
line 4 vty0
vty authentication login
and specify the aaa authentication settings individually...
I hope this helps... all the best
REDA
-
Hi, need to provide an ACS reports that will include all orders captured on barrier-lights/switches/routers.
Installation successfully acs for these network devices, basic AAA is work, can connect has failed/past authentications, different levels of authentication has been correctly configured, but I see only the orders that were denied in reports, (have tested different user levels). How can I configure the AAA sign orders enterend e.g. network device admins?
Hi Ganesh, thanks for reply.
Unfortunately i am still unable to see executed commands in tacacs+ accounting report. I have all report fields enabled, configuration is the same as you suggested but still no luck. I setup shell command authorization set and can see if readonly users (which has rights to run only commands in readonly authorization set) trying to execute commands they are not authorize to run but cannot see all commands executed on the switch.
This is really important to have a record who and when initiated what commands on network devices.
07/16/2010,09:18:30,AAAServer,GRoup,SWITCHES,CAT3560-T,UserName,192.168.182.1,start,15,,,,,,2,(Default),,,shell,,,,,,,,,,,,,,UTC,,,,,,,,,,,,,,,,,,,,,,,,No,Login,1,6,192.168.182.20,tty1
Any other suggestions?
Hello
If your version of ACS is 4.1 GANYMEDE + accounting command no longer works. No accounting is visible in the journal of Administration GANYMEDE + (bug CSCsg97429).
Click on this link if you use ACS Solution Engine: http://www.cisco.com/pcgi-bin/tablebuild.pl/acs-soleng-3des?psrtdcat20e2 and download:
applAcs_4.1.1.23_ACS - 4.1 - CSTacacs -CSCsg97429.zip
Hope to help!
Ganesh.H
Don't forget to note the useful message
-
The AAA authentication and VRF-Lite
Hello!
I encountered a strange problem, when you use authentication Radius AAA and VRF-Lite.
The setting is as follows. A/31 linknet is configured between PE and THIS (7206/g1 and C1812), where the EP sub-si is part of a MPLS VPN and VRF-Lite CE uses to maintain separate local services (where more than one VPN is used..).
Access to the this, via telnet, console etc, will be authenticated by our RADIUS servers, based on the following configuration:
--> Config start<>
AAA new-model
!
!
Group AA radius RADIUS-auth server
Server x.x.4.23 auth-port 1645 acct-port 1646
Server x.x.7.139 auth-port 1645 acct-port 1646
!
AAA authentication login default group auth radius local
enable AAA, enable authentication by default group RADIUS-auth
...
touch of 1646-Server RADIUS host x.x.4.23 auth-port 1645 acct-port
touch of 1646-Server RADIUS host x.x.7.139 auth-port 1645 acct-port
...
source-interface
IP vrf 10 RADIUS ---> Config ends<>
The VRF-Lite instance is configured like this:
---> Config start<>
VRF IP-10
RD 65001:10
---> Config ends<>
Now - if I remove the configuration VRF-Lite and use global routing on the CE (which is OK for a simple vpn installation), AAA/RADIUS authentication works very well. "" When I activate transfer ip vrf "10" on the interface of the outside and inside, AAA/RADIUS service is unable to reach the two defined servers.
I compared the routing table when using VRF-Lite and global routing, and they are identical. All roads are correctly imported via BGP, and the service as a whole operates without problem, in other words, the AAA/RADIUS part is the only service does not.
It may be necessary to include a vrf-transfer command in the config of Group server as follows:
AAA radius RADIUS-auth server group
Server-private x.x.x.x auth-port 1645 acct-port
1646 key ww
IP vrf forwarding 10
See the document below for more details:
http://www.Cisco.com/en/us/partner/docs/iOS/12_4/secure/configuration/guide/hvrfaaa.html
-
Test command of the AAA for EAP - TLS authentication for wireless users
Hi all
Can anyone suggest me the test command to verify the eap - tls authentication for the Cisco WAP's wireless.
If it's an authetication jump we can use the command to test the connection below
Radius of group aaa Testwap-01 #test [email protected] / * / o4 & yJ) NoL$ new-code %0
Trying to authenticate with the server radius group
User successfully authenticatedBut eap - tls is not delivered with the password. He insists that for the user name.
We strive for remote location then test remotely before production.
If someone help pls in that if we have a command to test or debug command to test this authentication.
EAP - TLS requires a client certificate. How can you have a simple command that analysis without loading any certificate on the router/switch? It does not exist. This is why eap - tls is not considered an easy to deploy eap method: because it can go wrong on several levels.
The aaa command test performs a PAP authentication, therefore, it tests the connectivity of the base RADIUS and name of user and password.
If it works, the only thing that can break for eap - tls are certificates, as well as the radius server will be able to tell if something worng.
-
Accounting and authorization of the AAA
Hello everyone.
I give myself a proposed implementation of AAA on routers and switches in our environment. Can someone please help me understand the difference between.
command option 1) aaa authorization exec and the authorization of the aaa.
aaa accounting exec command option 2) and the aaa accounting.
Thank you very much.Sent by Cisco Support technique Android app
Hello
command option 1) aaa authorization exec and the authorization of the aaa.
One allows if the user has the privilege level right to enter unrestricted IOS (0,1,15) levels, you can customize it.The other allows different commands, a user can type and send to the device
aaa accounting exec command option 2) and the aaa accounting.
One represents once again when a user changes from a specific user-level (level preferred 15 or user-level Exec 1)
Secondly it sends a message of each shipment of order based costing to box
Check out my blog at http:laguiadelnetworking.com for more information.
See you soon,.
Julio Segura Carvajal
-
Remove the aaa in pix server configuration
I have pix 515 with version 6.x cisco and me configured RADIUS vpn connection client authenitcation. The radius server is windows 2003 and I have the following commands
RADIUS protocol AAA-server test
AAA-server test (inside) host x.x.x.x1 password timeout 10.
The vpn works great, now I want to change the radius server and I want to delete the order and add new, but I get errors of
When I give
clear the aaa-server test, Iget an error message
You must remove all corresponding entries before AAA
removing the last server in the test group
When I give
No server aaa test (inside) host x.x.x.x1 password timeout 10. I get
You must remove all corresponding entries before AAA
removing the last server in the test group
When I give
no RADIUS protocol aaa-server test I get
AAA servers configured! Cannot delete server_tag.
I'm in a loop. Can some one adivce me how to remove the aaa tag test the firewall server
Thanks in advance
you are probably still referencing it in the vpn setting somewhere.
for example
card crypto mymap TEST client authentication
You must remove this first
-
The AAA authentication not working method and 'by default' list
Guys,
I hope someone can help me here to the problem of the AAA. I copied the configuration and debugging below. The router keeps using username/password local name even if the ACS servers are accessible and functional. To debug, it seems he keeps using the method list 'default' ignoring GANYMEDE config. Any help will be appreciated
Config
**********************************
AAA new-model
!
username admin privilege 15 secret 5 xxxxxxxxxx.
!
AAA authentication login default group Ganymede + local
the AAA authentication enable default group Ganymede + activate
authorization AAA console
AAA authorization exec default group Ganymede + local
AAA authorization commands 15 default group Ganymede + local
AAA authorization default reverse-access group Ganymede + local
orders accounting AAA 0 arrhythmic default group Ganymede +.
orders accounting AAA 15 by default start-stop Ganymede group.
Default connection accounting AAA power Ganymede group.
!
AAA - the id of the joint session
!
RADIUS-server host x.x.x.x
RADIUS-server host x.x.x.x
RADIUS-server host x.x.x.x
RADIUS-server host x.x.x.x
RADIUS-server application made
RADIUS-server key 7 0006140E54xxxxxxxxxx
!
Ganymede IP interface-source Vlan200
***************************
Debugs
002344: 5 Dec 01:36:03.087 ICT: AAA/BIND (00000022): link i / f
002345: Dec 5 01:36:03.087 ICT: AAA/AUTHENTIC/LOGIN (00000022): choose method list "by default".
002346: Dec 5 01:36:11.080 ICT: AAA/AUTHENTIC/LOGIN (00000022): choose method list "by default".
core01 #.
002347: Dec 5 01:36:59.404 ICT: AAA: analyze name = tty0 BID type =-1 ATS = - 1
002348: Dec 5 01:36:59.404 ICT: AAA: name = tty0 flags = 0 x 11 type = 4 shelf = 0 = 0 = 0 = 0 = 0 channel port adapter slot
002349: Dec 5 01:36:59.404 ICT: AAA/MEMORY: create_user (0 x 6526934) user = "admin" ruser = "core01" ds0 = 0 port = "tty0" rem_addr = "async" authen_type = service ASCII = NONE priv = 15 initial_task_id = '0', vrf = (id = 0)
002350: Dec 5 01:36:59.404 ICT: tty0 AAA/AUTHOR/CMD (2162495688): Port = "tty0" list = "service = CMD
002351: Dec 5 01:36:59.404 ICT: AAA/AUTHOR/CMD: tty0 (2162495688) user = "admin".
002352: Dec 5 01:36:59.404 ICT: tty0 AAA/AUTHOR/CMD (2162495688): send service AV = shell
002353: Dec 5 01:36:59.404 ICT: tty0 AAA/AUTHOR/CMD (2162495688): send cmd = AV set up
002354: Dec 5 01:36:59.404 ICT: tty0 AAA/AUTHOR/CMD (2162495688): send AV terminal = cmd - arg
002355: Dec 5 01:36:59.404 ICT: tty0 AAA/AUTHOR/CMD (2162495688): send cmd - arg = AV
002356: Dec 5 01:36:59.404 ICT: tty0 AAA/AUTHOR/CMD (2162495688): found the 'default' list
002357: Dec 5 01:36:59.404 ICT: tty0 AAA/AUTHOR/CMD (2162495688): method = Ganymede + (Ganymede +)
002358: Dec 5 01:36:59.404 ICT: AAA/AUTHOR/TAC +: (2162495688): user = admin
002359: Dec 5 01:36:59.404 ICT: AAA/AUTHOR/TAC +: (2162495688): send service AV = shell
002360: Dec 5 01:36:59.404 ICT: AAA/AUTHOR/TAC +: (2162495688): send cmd = AV set up
002361: Dec 5 01:36:59.404 ICT: AAA/AUTHOR/TAC +: (2162495688): send AV terminal = cmd - arg
002362: Dec 5 01:36:59.404 ICT: AAA/AUTHOR/TAC +: (2162495688): send cmd - arg = AV
Enter configuration commands, one per line. End with CNTL/Z.
core01 (config) #.
002363: Dec 5 01:37:04.261 ICT: AAA/AUTHOR (2162495688): permission post = ERROR
002364: Dec 5 01:37:04.261 ICT: tty0 AAA/AUTHOR/CMD (2162495688): method = LOCAL
002365: Dec 5 01:37:04.261 ICT: AAA/AUTHOR (2162495688): position of authorization = PASS_ADD
002366: Dec 5 01:37:04.261 ICT: AAA/MEMORY: free_user (0 x 6526934) user = "admin" ruser = "core01" port = "tty0" rem_addr = "async" authen_type = ASCII service = NONE priv = 15
core01 (config) #.
Ganymede + accessible servers use source vlan 200. Also in the Ganymede server + can you check if the IP address for this device is configured correctly and also please check the pwd on the server and the game of this device.
As rick suggested sh Ganymede would be good as well. That would show the failures and the successes
HTH
Kishore
Maybe you are looking for
-
Whenever I plug my charger into my iPhone more 6 seconds I get a pop that says this accessory may not be recognized and will not take a charge. It is the charger supplied with the phone. But my iPad charger is more than 2 years works great on my phon
-
Be involved in a number of different companies, I have 4 email accounts main which seamonkey maintained separately, but having migrated to thunderbird seems to receive all e-mails that themselves are coalition and keep picking up archive incorrect wh
-
Original title: 953691 Installation of webcam LifeCam HD-5000. I'm on Windows XP and you get to halfway through the installation and error message came through. Three times so far. Error message reads The installation cannot continue because an unexp
-
Try to download Bing Bar 7.0. Received the error code 61BO and will not download. What should I do
Windows Update has tried to install the update of Bing Bar 7.0 since 16/01/2012. Have tried many times update me. Display shows error code 61BO. and will not be installed. I installed Miscroft difficulty and tried again, but still get same error m
-
Precision M4700 and IDT Audio Driver (Windows 8 x 64)
Hello I have a problem with my new Dell Precision M4700 with Windows 8 x 64. I can not install audio driver IDT high definition. During the installation, I get the error message 'the hardware found is not supported by this package IDT', or if I try t