Discover 5.1 upgrade issue SSL certificates
So I heard that the SSL stuff in 5.1 is different from previous versions and by reading the upgrade guide, I think I'll be ok as I am now however, it is always nice to get confirmation currently we lack 5.0 on all pieces of our environment in mind, we have a Secure Gateway in our DMZ for external access and the main connection inside our LAN Server. Both servers use a CA signed SSL cert (generic) and both decide the same DNS name (on the outside using the public DNS records inside using internal DNS records). For example, if on an iPad, the connection to the server is configured as view.mydomain.com with the same DNS name resolved to our external public IP address that points to the gateway secure in the demilitarized zone. Inside, I have a DNS entry that points "display" then inside of the connection to the server. Everything works well and we don't get the guests of SSL certificate. My question is that, if I understand although it for upgrading view must import existing certificates because they are without my intervention, see below:
I think your ok to continue, but I would go ahead and have the facility ready guide in case you have problems. Just saw a blog post by Jason Boche onto the upgrade of his laboratory experience.
Tags: VMware
Similar Questions
-
When to access Intranet sites who have the SSL certificates issued by our internal PKI, FF for Windows gives an error message - an error occurred when connecting to myshaw. Security Library: improperly formatted DER encoded message. (Error code: sec_error_bad_der)
Chrome and IE work fine. This is a PKI again using the signature SHA-2 algorithm.
I was able to identify the problem. Our public key infrastructure has been using some signature algorithms that FF did not support.
-
Firefox for Mac does not recognize a valid SSL certificate
Firefox for Mac does not recognize the SSL certificate that is valid for this site, I got: https://www.georgeglazer.com. It gives a warning "not reliable." However, the Firefox for Windows does not give a warning. This happens even if I clear the cache and it happens in the Mavericks and OS of Yosemite. The certificate is up-to-date and with Comodo. Firefox for Mac is now the only browser producing these errors (v. 39, put updated) - Internet Explorer, Safari and Chrome are not. Our hosting provider has said it's probably a browser issue, perhaps having to do with intermediate certificates in Firefox being obsolete. I really hope you'll solve the problem, as it's annoying for us when we're going to do right by our customers and pay for the SSL certificate. I have attached a picture of the warning and the other from what you see on a PC: a pop-up that says it is a verified SSL certificate and gives details about the issuer, the period of validity, etc.
COMODO should you sent a link to download the file 'bundle' containing the intermediate certificates. Who needs to go in the same directory as the certificate of your site. If you are using a control panel, your host can probably help with this process. And if you bought through them, shame on them for not taking care of this for you already!
-
How to accept a new ssl certificate in Thunderbird?
7.15.15
I can't get or send emails on my cell phone two days ago.
- Neither the "Configuration Options for certificates" worked to bring in the certificate that I use that allows you to send and receive e-mail. Under the "Digital Signature" or "Encryption" when I press "Select" to select a certificate, I get the pop-up message "Certificate Manager cannot locate a valid certificate... ». When I press 'View certificates' certificate that I use is listed under 'Servers' and the 'authorities' and is up to date.
-In addition, under Tools - Options - Advanced - certificates for: "when a server requests my personal certificate", I selected "Ask Me every time" and left "query OSCP responder servers to confirm...". ', the box is checked.I think that this problem is bound to accept a new ssl certificate has been recently renewed. I've never had this problem before. How to start accepting a new certificate?
Thank you.
No you can not communicate with the server using a common product of Mozilla. In a short while you will not be able to co interact with it with any product. The operator/administrator of the server needs to fix their server to issue certificates 1024-bit or better. Or stop using TLS.
The best explanation of this change and it's because I've seen is here https://weakdh.org/
(right at the bottom of the page is what you need to do stuff)In essence, that the server does not have a security flaw serious patched and Mozilla products have been modified to not interact with servers that have not corrected the vulnerability. Vulnerability leaves you open to man in the middle attack on piracy.
-
Thunderbird does not recognize a self-signed SSL certificate
Dear support,
I have a very strange problem that I don't understand.
I run a server ISP offering IMAP and TLS/SSL HTTPS encryption. Both services use the same SSL certificate issued by RapidSSL/GeoTrust Server edward.ennabe.de
When I open an https connection to the server, Firefox correctly solves the certificate chain and use the certification authority root Equifax (which is correct).
However, when I try to connect to a mailbox via Thunderbird, all I get in the hierarchy of certificates is my server edward.ennabe.de. I don't think that it's "working as intended", or is it?Is something wrong with my Thunderbird or My Dovecot configuration? What is really strange that firefox recognizes it correctly.
Thanks in advance
Kind regards
ZeroEnna
In Thunderbird, click the 'Détails' tab in the display of the certificate.
See all certificates of CA listed in the field "Certificate hierarchy" also installed in your Thunderbird certificate store?
When checking this look for the tab 'authorities '.
If there are no certificates listed in the missing chain in the Thunderbird certificate store (for some reason any), you can try to export it in Firefox and import them into Thunderbird. -
When you visit a Web site that has some kind of issue of Certificate SSL, as missing certificate untrusted or invalid etc, the browser is supposed to display a warning message, which should warn us of the potential dangers of visiting the website. I realized that my browsers have not shown such warning for very long. Can someone give me an idea of why this is happening?
Thank you
SatyaHi satyabratasharma, there are two different pieces of information at this location:
(1) this Web site does not provide identity information.
It's normal. Firefox is convinced only a certificate EVSSL (green lock) in order to provide reliable identity information.
(2) your connection to this Web site is not encrypted.
Yes, because it is an HTTP URL, Firefox does not attempt to establish a secure connection. There is no warning, unless it's an HTTPS URL and there is a problem with the certificate.
-
When I visit a Web site that requires SSL I displays the message "this connection is untrusted". Any Web site that I visit, it's always exactly the same message and the same SSL certificate that she is no longer valid for www.thawte.com
support.Mozilla.org uses an invalid security certificate.
The certificate is not approved, because no sender string has been provided.
The certificate is valid for www.thawte.com
The certificate expired on 11/11/2011 23:59. The time now is 11:46 28/01/2012.When I click "Add the Exception" on a Web site and view the certificate, it is exactly the same certificate with the exact same serial number.
I had a similar problem with Internet Explorer showing a 404 error when I visited SSL protected pages but to do a restore of the system a month ago to correct this. All other bowsers are / were very good.
I installed Firefox 3.x month last to test something that is when the problem started. I have since uninstalled Firefox 3.x and reinstalled the latest version. I deleted all the preferences/settings, disabled modules and reinstalled many times. I did a Windows system restore to before that the problem started with no luck.
The time / Date on my computer are correct. I have no firewall other than the windows one. I had no antivirus (netbook) until I installed a (Avast) yesterday to see if a virus was causing issues (found nothing). This problem arises on any internet connection (tested to work and home).
or try to use the module Skip Cert error (to jump to the SSL/TLS certificate error page)
Thank you
Please check 'Resolved' the answer really solve the problem, to help others with a similar problem.
-
So I come back on an interesting question that can cause significant problems, unless I can find a reasonable solution.
Until yesterday a number of software programs that run in a number of remote sites were running all fortunately accessing a database. This database is accessible via the HTTPS POST and screw HTTPCLIENT, and for the past two years, everything worked fine while having the true flag to check server, the database is part of a site that is all signed and certified.
However, as of yesterday, they all decide to stop, investigate the server itself it seems that the SSL certificate has switched from the previous period. While browsing the forums of LAVA, I managed to find the reference to the problem with which a LabVIEW ca - bundle.crt file making the obsolete object so not check the validity of the new certificate.
Now, while there is here a workaround which the server verify the Pavilion from true to FALSE switching, I can do all programs work again, there's the issue of having to update and rebuild several years worth of programs. So I was expecting something that I could do outside of LabVIEW to try to solve the problem, I had considered to replace ca - bundle.crt, but I'm not sure of the validity of this idea.
So, any ideas are likely to be accepted if they mean that I don't have to go to several versions of LabVIEW.
TLDR:
I can do something with it to solve the problem?
Welll the good news is that I found a solution. The problem is that I don't know to what extent this solution will get me, it should mean at least I can reach the single database I'm targeting.
Subsequently to the rear since the database certificate (COMODO) provider I found they provide CA bundle which when used to replace the LabVIEW supplied ca - bundle.crt allows the system HTTP access the database without problem.
For remote computers, it's probably fine as it is guaranteed to have the only secure site SSL they will try to access the database that I know the data are compatible with. For my development system however it may still remain a problem that I don't know when I'll have to try to access another site certified and whether or not the new authority will work. Although in all fairness for the moment I don't know if the LabVIEW provided one or the other will work.
I might have to come back to this thread at a later date and to make the point about how everything worked.
-
Install a new SSL certificate for Server 2008 R2
Hello
We have a Windows 2008 R2 server running of the machine. As a company that manages payments, we need to be registered PCI DSS and the scan picked up a point of failure is that we do not have an SSL certificate installed. I bought a via GoDaddy and followed the instructions on their site to install it, but the PCI DSS Analysis is always a failure for the following reason: -.
"The following certificate was at the top of the certificate chain sent by the remote host, but is signed by an unknown certification authority."
The certificate at the top of the string is the default "integrated". How to promote the certificate GoDaddy installed at the top of the chain?
Thank you
This issue is beyond the scope of this site and must be placed on Technet or MSDN
-
How to install the ssl certificate in windows server 2008?
Hello
Can someone give me the steps to install the SSL certificate on my application hosted on windows server 2008 R2?
Hello
Although technet.microsoft.com should be the best forum for the problems of server below is a guide on how to install an SSL certificate.
It will be useful.
To install your newly acquired in IIS 7 SSL certificate, first copy the file somewhere on the server and then follow these instructions:
- Click on the start menu, go to administrativetools and click on Manager of Services Internet (IIS).
- Click the server name in the links on the left column. Double-click server certificates.
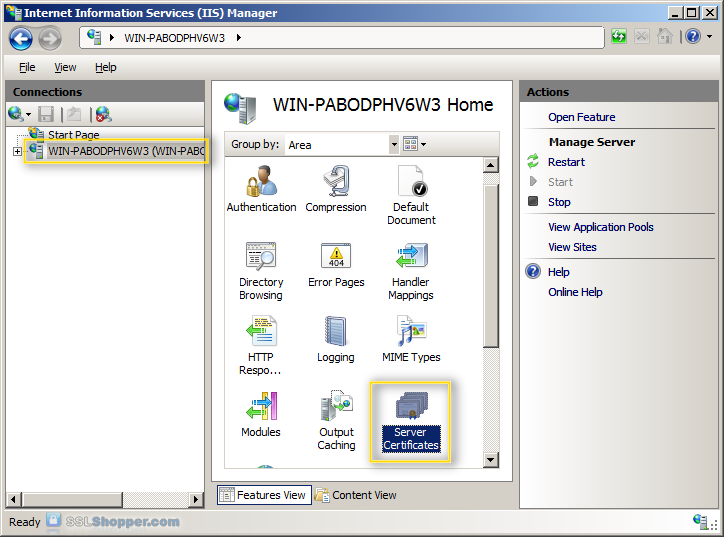
- In the Actions column to the right, click Complète Certificate Request...
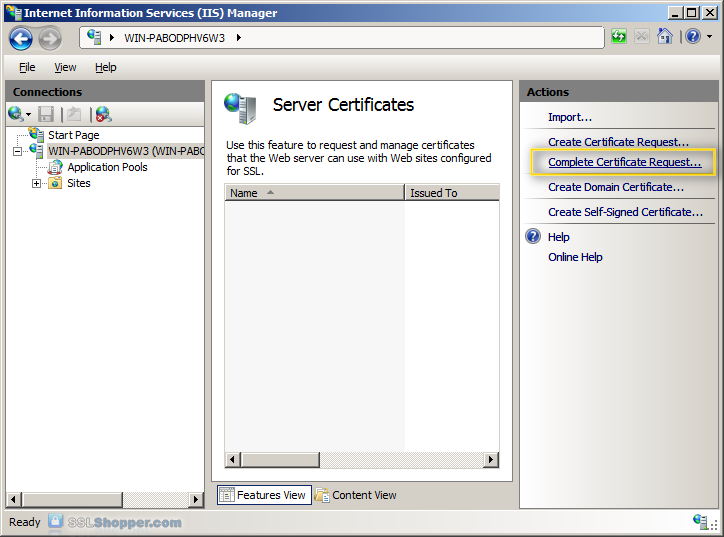
- Click on the button with the three points, and then select the server certificate that you received from the certificate authority. If the certificate does not have a .cer file extension, select this option to display all types. Enter a friendly name that you can keep track of certificate on this server. Click OK.

- If successful, you will see your newly installed in the list certificate. If you receive an error indicating that the request or the private key is not found, make sure that you use the correct certificate and you install it on the same server that you generated the CSR on. If you are sure these two things, you just create a new certificate and reissue or replace the certificate. If you have problems with this, contact your certification authority.
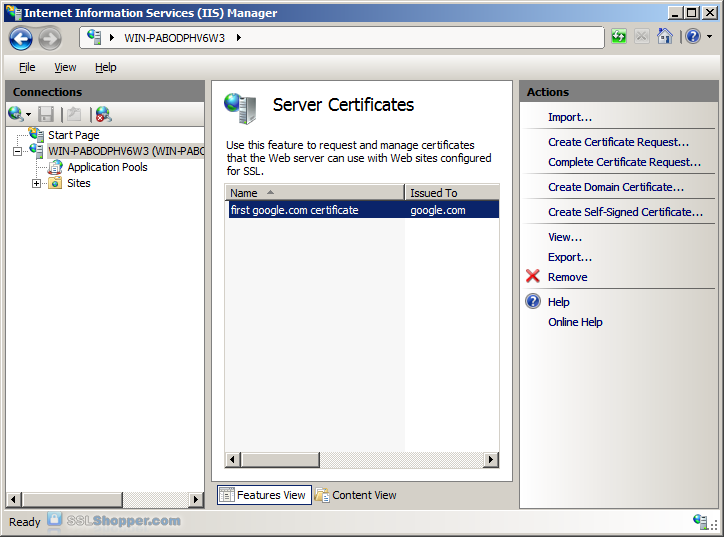
Bind the certificate to a Web site
- In the column of links on the left, expand the sites folder, and click the Web site that you want to bind the certificate to click links... in the right column.

- Click the Add... button.

- Change the Type to https , and then select the SSL certificate that you just installed. Click OK.
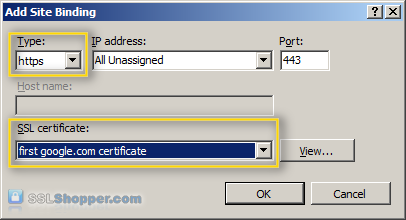
- You will now see the listed link for port 443. Click close.
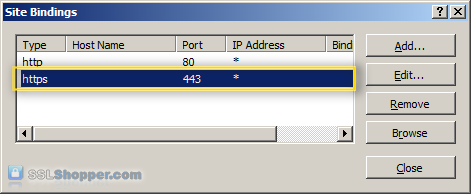
Install all the intermediate certificates
Most of the SSL providers issue certificates of server out of an intermediate certificate so you will need to install the intermediate certificate on the server as well or your visitors will receive a certificate error not approved. You can install each intermediate certificate (sometimes there are more than one) by following these instructions:
- Download the intermediate certificate in a folder on the server.
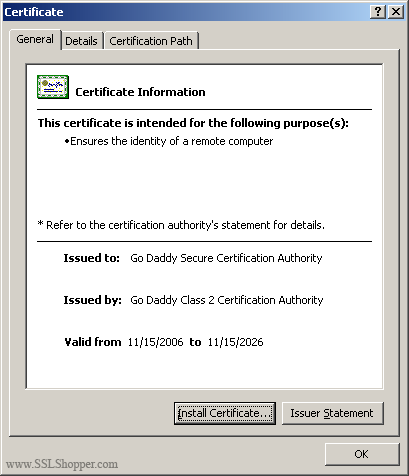
- Double-click the certificate to open the certificate information.
- At the bottom of the general tab, click the install Certificate button to start the Certificate Import Wizard. Click Next.
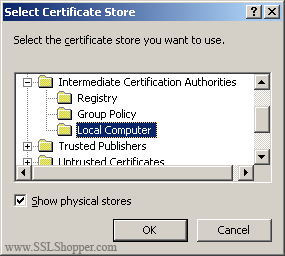
- Select place all certificates in the following store , and then click Browse.

- Select the Show physical stores checkbox, then expand the Intermediate certificate authorities folder, select the below folder on the Local computer . Click OK. Click Next, and then click Finish to complete the installation of the intermediate certificate.
You may need to restart IIS so that it starts the new certificate to give. You can verify that the certificate is installed correctly by visiting the site in your web browser using https rather than http.
Links
- Move or copy an SSL certificate on a Windows Server to another Windows Server
- How to disable SSL 2.0 in IIS 7
- How to configure the SSL in IIS 7.0
- Video tutorials to install an SSL certificate in IIS 7 to NetoMeter
Kind regards
Joel
-
Internal and external customers see certificate of Cisco router, NOT Exchange SSL certificate
Cisco 876 Integrated Services router (ISR)
Exchange Server 2010 SP1Customer: 2013 Outlook, OWA, ActiveSync WP7/WP8 (?)
Put us in place a new Cisco ISR. Almost everything works fine, with a few exceptions. Exchange e-mail stopped altogether for several days until I realized that I needed to redirect the ports, SMTP, HTTP, and HTTPS, by external to the Exchange Server. Now, mail flow is fine, but...
Every time I start Outlook, I get a certificate error. When I look at the certificate in the error popup, it points actually to certificate self-signed Cisco router. When we try to use the Windows phones, they get a "certificate error" and direct the user to the network administrator. Even with OWA: a certificate error, even if it can be "accepted" / overridden.
Each customer can still work, with the exception of Windows phones. In Outlook and OWA, mail is always be sent and received, but must be accepted manually that the certificate is wrong before the customer takes care, and then it takes a little longer to load.
Any ideas?
I did "" port forwarding on the pots of 25, 80 and 443. Again, I did it yesterday and now mail seems to flow, whereas before, even if we could enter the client with Certificate error, message not be received. (There was also a problem with mail however not passed, but that was due to our mail relay provider and was set yesterday as well...)
Everything worked fine with the previous router (obviously). It was a high-end, the level of consumption Fritz! Box commonly used in Germany. I also had to allow ports through this box is not unlike using the nat ip inside static commands on the 876, but I don't know what he could have let his own or why SRI is the Exchange Server application SSL certificate hijacking.
Thanks in advance for any help.
jeremyNLSO
CCNA Routing & Switching, CCNA security
MCITP, MCTS
Berlin, GermanyIf we have actually figured this out today. The internal DHCP Server distributing the a DNS Server public as well as the internal DNS. The internal DNS was time and the customer became the external IP address of the public DNS and it received an unexpected cert of the router. Once we removed the public DNS servers from the DHCP server and used only DNS servers in-house, that the issue went away. Logical after we realized what was going on.
-
Windows 2000 SSL certificate export
Hi all
I am trying to export the certificate SSL in Windows 2000 server that is running Cisco ACS 3.3. This SSL certificate is issued by a third-party CA. This certificate is issued by CA bound our server host name. Thus, this certificate can be reused on another server with a different host name.
I followed under the installation program to export the certificate since 2000 planter
[1] start > run > Type "mmc" and press ENTER.
[2], click on Console > Add/Remove Snap-in...
[3], click Add > certificate > add > computer account > next > Local computer > finish > close > Ok
[4] expand Certificates > expand Trusted Root Certificate Authority and select certificates
[5] select the certificate CA ACS, right click > all tasks > export > next > select ' encoded in Base 64 X.509 (.) REB)' > next > Browse
Choose the storage location and give it a name.
Press next > finish
We should get a message "export was successful."
After the export of the certificate in the CERTIFICATION AUTHORITY folder ROOT of TRUST based on the name of the seller. I could see that the certifcates are self-signed certificate. This certificate is not valid certificate approved in the sound emitted by the CA.
My Question is: If this certifcate issued by 3 third party trust will be located in a different folder outside the ROOT of TRUST certificate folder. If the folder in which this certifcate trust will be so now.
I'm checking the certificates of
published by:
issued to:
SE signed certifcate times issued to and issued by is even
SETTING SNAP SHOT of certifcate MMC window.
Hello
ACSCertStore is a record of the certificate created in the MMC - folder of the server certificate.
I hope this helps.
Kind regards
Anisha.
P.S.: Please mark this message as answered if you feel that your query is resolved. Note the useful messages.
-
SSL certificate Expirtation concentrator
I'm getting an alert after my 3000 Concentrator: SSL certificate will expire in 26 daysIssuer. It seems that this (public/private) and a certificate of identity is issued by one of our servers 2003 (not 3rd party). I'm tempted to press the buttons of survivor on each of these certificates; However, being new to this arena, I'm leary which may (or may not) happen. My research told me that this can cause the rejected certificate. Can someone give me an overview of what these certificates and what do I find myself comfortable to breathe again status? Thank you.
The hub is trying to tell you the SSL certificate installed on the hub will expire in 26 days unless a new SSL certificate is recreated.
To create a new SSL certificate, go to:
The administration | The certificate management | SSL certificates
In the interface that shows the SSL certificate with an expiry Date of mm/dd/yyyy, click
on the generate under the field of action. Accept the default setting and the client on the generate button.
Try this link for more information:
-
Cisco ASA 5505 and comodo SSL certificate
Hey all,.
I'm having a problem with setting up the piece of Certificate SSL of Cisco AnyConnect VPN. I bought the certificate and installed it via the ASDM under Configuration > VPN remote access > Certificate Management > identity certificates. I also placed the piece of 2 CA under the CA certificates. I have http redirect to https and under my browser, it is green.
Once the AnyConnect client installs and automatically connect I get no error or anything. The minute I disconnect and try to reconnect again, I get the "VPN Server untrusted certificates! ' which is not true because the connection information to be https://vpn.mydomain.com and the SSL certificate is configured as vpn.mydomain.com.
On that note, it lists the IP address instead of the vpn.mydomain.com as the unreliable piece of this. Now of course I don't have the IP as part of the SSL-cert, just the web address. On the side of the web, I have a record A Setup to go from vpn.mydomain.com to the IP address of the Cisco ASA.
What I'm missing here? I can post config if anyone needs.
(My Version of the Software ASA is 9.0 (2) and ASDM Version 7.1 (2))
Yes that's correct. technically, it will take you to EKU as keys to authenticate server who was a little forced in version 3.1. But eventually, he was taken away. If you get no error using the browser and ot only comes with the anyconnect client. Most likely, you do not have to configured values. I can confirm that if you can share the fqdn with me also, you can try the upgrade and check it out.
Thank you
Bad Boy
-
VUM 6.0, replacement of SSL certificates
Hello
VCSA device (6.0) external PSC
VCenter VCSA device (6.0)
VUM 6.0 (1 x R2 Windows 2012 running SQL 2014 and 1 x R2 Windows 2012 with VUM installed)
Open root SSL and subordinate CA
I replaced the certificates for the PSC with no problems, the VC and the hosts are all good :-)
To replace the VUM SSL certificates, I followed KB 1023011 and replaced the self CERT signed with certificates signed by a subordinate CA OpenSSL. When I open the VI client and activate the VUM plugin I get a certificate error. If I open the PFX and import it into my personal cert store the complete chain, subordinate and root is here, and all are approved. If I navigate over https to another server where I replaced the SSL certificate with the one that was signed by the same CA browser isn't moaning.
Issues related to the:
1. the error indicates that my PC does not trust the cert or vCenter does not support the cert?
2. If it is likely that the vCenter is not to trust the cert how to install the CA certificate root in the keystore on the vCenter? The PSC has already he is and trust her, otherwise she would not distribute certs kindly signed to esxi hosts.
3. the cert that was issued for MUV has the VUM server's dns name in the part of the cert SAN but not in the issued to. Who is likely to be a problem?
4. the CSR that has been generated for MUV did not come from the VUM server, instead, it was made from the workstation where he has installed OpenSSL. Who is likely to be a problem?
As a side note KB 1023011 has no mention of being the right process for 5.5, 6.0 let alone!
Thank you very much
Girardot
Hello
I managed to solve this problem by adding intermediate CA on the end of the rui.crt.
See you soon,.
Girardot
Maybe you are looking for
-
Hello, I want to start by saying that I had a repair done by HP in March that went beautifully, they have been so helpful, the repair was perfect and the whole process was effortless! I am hopeful but scared about it. I also got the hinge on my desir
-
Hi, can someone help me make a formula which detects and highlights the value of the cell that contains the items of data that I entered in another cell? Thank you
-
Has anyone bought and used a case for the remote siri yet and if yes using a limit the use of the touchpad somehow.
-
Downgrade of PC desktop HP Pavilion p6-2419
Where can I find the equivalent drivers for this PC to windows 7 64 bit?
-
I'm resetting of creation of a network of small business @ a client Office. They had a network configuration before but she was lost. I reset the network and made sure that we were on the same workgroup. All works well for a month. Then yesterday