FW IOS record timestamp
Hi guys,.
I configure logging for firewall IOS and local zone time/clock, but logging use always UTC format not local time. Any recommendation? Thanks in advance.
Router #sh logging
-output omitted-
02:41:15.572 Nov 2: % s-6-IPACCESSLOGDP: list 103 denied icmp 67.70.aaa.bbb-> 142.176.xxx.yyy (0/8), 1 packet
Router # sh clock
22:41:33.644 Halifax Wednesday, November 1, 2006
Router #.
Log service timestamps datetime msec
logging buffered debugging 51200
clock timezone Halifax-4
summer time clock Halifax date April 6, 2003 02:00 October 12, 2003 12:00
Try this.
Log service timestamps show-timezone datetime
Then you should get UTC in your journal.
I hope this helps.
Steven
Tags: Cisco Security
Similar Questions
-
The GPS data with other analyzed data record
Hello!
I am a new user of DASYLab and not very good with coding, so please bear with me! I try to record (timestamp, latitude, longitude) already analysed GPS data with other data (accelerometer, etc.) in the same. DDF file. Right, GPS analysed is now sent through a series of three demultiplexers for each signal and only 1 of 16 channels, reducing the size of the output data. This data is then saved in a. The CAD file. Other data on average, recorded in one. DDF file, then saved another. The CAD file. We used to compare the data from the GPS and other devices by comparing timestamps.
I would like to save all data to a file, either. DDF of. CSA (.) DDF would be preferable).
When I try to add more channels in the. DDF save the module after the demultiplexer black box and GPS data to it, I get an error saying "the data to an entry in this module are the wrong type." I also receive this error when trying to send the data GPS to the. CSA Save module. I learned that this means that the size of the files is not the same of this thread. My question is, how can I make sure that the data have the same characteristics of time so I can save to the same file?
If you need more information I would be happy to provide it, I apologize if I have something important to go.
Thanks for reading,
etdiv
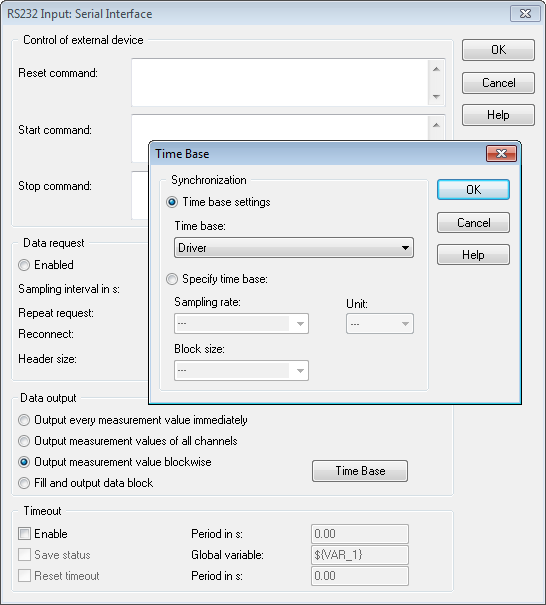
That's what I needed. Your time is the driver. In the RS232 input module, click the Options button.
Select the measurement of output value, and then click the button on the time Base and select sync/time Base driver.
That should allow you to write to the DDF file.
-
How to turn Pix timestamp of the log messages in the buffer
How can I activate the timestamp of the log 'stamped' PIX messages? I activated the "record timestamp" command that generates timestamps for 'syslogd' messages but my messages saved in the buffer do not have a timestamp on them.
I'm running ver 6.2 (2) 'warnings of logging in buffered memory ".
Rgds tony
Unfortunately you don't have. As you have seen, the "horodateurs log" command the timestamps on the syslog messages, but still put on the console messages.
There is a bug already open about it, CSCdu18237. No word on when it will be resolved, however.
-
Logging without timestamp display PIX
I need to see the timestamps on our current PIX 515e with enabled logging timestamp.
All this illustrates that it is the identification number and the warning message.
Any help would be appreciated thanks
Tony
Hello
Assuming you use the 6.3 software or less, then record timestamp adds a timestamp in syslog messages to a syslog server - as far as I know has no way to obtain local messages to display a timestamp.
HTH
Andrew.
-
Hello guys,.
I have an ASA 5505 firewall tries to create a VPN tunnel from site to site with a router of 2621 running Advanced IP services. The tunnel keeps do not and I don't know why. Below is the config.
!
hostname SeCuReWaLL
domain default.domain.invalid
activate 2KFQnbNIdI.2KYOU encrypted password
2KFQnbNIdI.2KYOU encrypted passwd
names of
name 192.168.2.0 outside
name 192.168.3.0 inside
!
interface Vlan1
Description of network links extended to outside of the
nameif outside
security-level 0
192.168.2.101 IP address 255.255.255.0
!
interface Vlan2
Description within a private network
nameif inside
security-level 100
address 192.168.3.1 IP 255.255.255.0
!
interface Ethernet0/0
!
interface Ethernet0/1
switchport access vlan 2
!
interface Ethernet0/2
Shutdown
!
interface Ethernet0/3
Shutdown
!
interface Ethernet0/4
Shutdown
!
interface Ethernet0/5
Shutdown
!
interface Ethernet0/6
Shutdown
!
interface Ethernet0/7
Shutdown
!
boot system Disk0: / asa822 - k8.bin
passive FTP mode
DNS server-group DefaultDNS
domain default.domain.invalid
allow inside_access_in to access extended list ip inside outside 255.255.255.0 255.255.255.0
outside_access_in list extended access permit icmp any any echo response
site_router to access extended list ip inside 255.255.255.0 allow 192.168.5.0 255.255.255.0
pager lines 24
Outside 1500 MTU
Within 1500 MTU
ICMP unreachable rate-limit 1 burst-size 1
ASDM image disk0: / asdm - 625.bin
don't allow no asdm history
ARP timeout 14400
Global 1 interface (outside)
NAT (inside) 0-list of access site_router
NAT (inside) 1 inside 255.255.255.0
Access-group outside_access_in in interface outside
Route outside 0.0.0.0 0.0.0.0 192.168.2.1 1
Outdoor 192.168.5.0 255.255.255.0 192.168.2.107 1
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-registration DfltAccessPolicy
Enable http server
HTTP inside 255.255.255.0 inside
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Crypto ipsec transform-set esp-3des esp-sha-hmac secure_set
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
peer set card crypto ipsec_map 10 192.168.2.107
card crypto ipsec_map 10 transform-set secure_set
ipsec_map interface card crypto outside
crypto ISAKMP allow outside
crypto ISAKMP policy 10
preshared authentication
3des encryption
md5 hash
Group 5
lifetime 28800
Telnet timeout 5
SSH timeout 5
Console timeout 0
dhcpd dns 192.168.2.1
!
dhcpd address 192.168.3.10 - 192.168.3.40 inside
dhcpd allow inside
!a basic threat threat detection
Statistics-list of access threat detection
no statistical threat detection tcp-interception
WebVPN
username admin privilege 15 encrypted password f3UhLvUj1QsXsuK7
tunnel-group 192.168.2.107 type ipsec-l2l
IPSec-attributes tunnel-group 192.168.2.107
pre-shared key *.
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
maximum message length automatic of customer
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the netbios
inspect the rsh
inspect the rtsp
inspect the skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect the tftp
inspect the sip
inspect xdmcp
Review the ip options
!
global service-policy global_policy
context of prompt hostname
call-home
Profile of CiscoTAC-1
no active account
http https://tools.cisco.com/its/service/oddce/services/DDCEService destination address
email address of destination [email protected] / * /
destination-mode http transport
Subscribe to alert-group diagnosis
Subscribe to alert-group environment
Subscribe to alert-group monthly periodic inventory
monthly periodicals to subscribe to alert-group configuration
daily periodic subscribe to alert-group telemetry
Cryptochecksum:a6ffc4e9572dbee8e526c3013a96a510
: end!
InternetRouter hostname
!
boot-start-marker
boot-end-marker
!
!
No aaa new-model
no location network-clock-participate 1
No network-clock-participate wic 0
IP cef
!
!
!
!
no ip domain search
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
crypto ISAKMP policy 10
BA 3des
md5 hash
preshared authentication
Group 5
lifetime 28800
key cisco address 192.168.2.101 crypto ISAKMP xauth No.
!
!
Crypto ipsec transform-set esp-3des secure_set
!
ipsec_map 10 ipsec-isakmp crypto map
defined peer 192.168.2.101
Set transform-set secure_set
match the address router_site
!
!
!
!
interface Loopback0
192.168.5.1 IP address 255.255.255.0
!
interface FastEthernet0/0
IP 192.168.2.107 255.255.255.0
automatic duplex
automatic speed
ipsec_map card crypto
!
interface Serial0/0
no ip address
Shutdown
!
interface FastEthernet0/1
no ip address
Shutdown
automatic duplex
automatic speed
!
interface Serial0/1
no ip address
Shutdown
!
IP route 192.168.3.0 255.255.255.0 192.168.2.101
!
!
IP http server
no ip http secure server
!
router_site extended IP access list
ip licensing 192.168.5.0 0.0.0.255 192.168.3.0 0.0.0.255
!
!
!
!
control plan
!
!
!
Voice-port 1/0/0
!
Voice-port 1/0/1
!
Voice-port 1/1/0
!
Voice-port 1/1/1
!
!
!
!
!
!
!
!
Line con 0
exec-timeout 0 0
Synchronous recording
line to 0
line vty 0 4
opening of session
!
!
endInternetRouter #debug isakmp crypto
Crypto ISAKMP debug is on
InternetRouter #ping
Protocol [ip]:
Target IP address: 192.168.3.10
Number of repetitions [5]:
Size of datagram [100]:
Timeout in seconds [2]:
Extended commands [n]: y
Address source or interface: 192.168.5.1
Type of service [0]:
Set the DF bit in the IP header? [None]:
Validate the response data? [None]:
Data model [0xABCD]:
In bulk, Strict, Record, Timestamp, Verbose [no]:
Scan the range of sizes [n]:
Type to abort escape sequence.
Send 5, echoes ICMP 100 bytes to 192.168.3.10, time-out is 2 seconds:
Packet sent with the address source 192.168.5.1* 01:49:47.699 Mar 1: ISAKMP: ke received message (1/1)
* 01:49:47.699 Mar 1: ISAKMP: (0:0:N / A:0): THE application profile is (NULL)
* 01:49:47.699 Mar 1: ISAKMP: created a struct peer 192.168.2.101, peer port 500
* 01:49:47.699 Mar 1: ISAKMP: new created position = 0x8553C778 peer_handle = 0 x 80000013
* 01:49:47.699 Mar 1: ISAKMP: lock struct 0x8553C778, refcount IKE peer 1 for isakmp_initiator
* 01:49:47.699 Mar 1: ISAKMP: 500 local port, remote port 500
* 01:49:47.699 Mar 1: ISAKMP: set new node 0 to QM_IDLE
* 01:49:47.703 Mar 1: insert his with his 84074CC8 = success
* 01:49:47.703 Mar 1: ISAKMP: (0:0:N / A:0): cannot start aggressive mode, try the main mode.
* 01:49:47.703 Mar 1: ISAKMP: (0:0:N / A:0): found peer pre-shared key matching 192.168.2.101
* 01:49:47.703 Mar 1: ISAKMP: (0:0:N / A:0): built the seller-07 ID NAT - t
* 01:49:47.703 Mar 1: ISAKMP: (0:0:N / A:0): built of NAT - T of the seller-03 ID
* 01:49:47.703 Mar 1: ISAKMP: (0:0:N / A:0): built the seller-02 ID NAT - t
* 01:49:47.703 Mar 1: ISAKMP: (0:0:N / A:0): entry = IKE_MESG_FROM_IPSEC, IKE_SA_REQ_MM
* 01:49:47.707 Mar 1: ISAKMP: (0:0:N / A:0): former State = new State IKE_READY = IKE_I_MM1* 01:49:47.707 Mar 1: ISAKMP: (0:0:N / A:0): early changes of Main Mode
* 01:49:47.707 Mar 1: ISAKMP: (0:0:N / A:0): send package to 192.168.2.101 my_port 500 peer_port 500 (I) MM_NO_STATE
* 01:49:47.711 Mar 1: ISAKMP (0:0): packet received 192.168.2.101 dport 500 sport Global 500 (I) MM_NO_STATE
* 01:49:47.711 Mar 1: ISAKMP: (0:0:N / A:0): entry = IKE_MESG_FROM_PEER, IKE_MM_EXCH
* 01:49:47.711 Mar 1: ISAKMP: (0:0:N / A:0): former State = new State IKE_I_MM1 = IKE_I_MM2* 01:49:47.715 Mar 1: ISAKMP: (0:0:N / A:0): treatment ITS payload. Message ID = 0
* 01:49:47.715 Mar 1: ISAKMP: (0:0:N / A:0): load useful vendor id of treatment
* 01:49:47.715 Mar 1: ISAKMP: (0:0:N / A:0): supplier code seems the unit/DPD but major incompatibilite.123
* 01:49:47.715 Mar 1: ISAKMP: (0:0:N / A:0): provider ID is NAT - T v2
* 01:49:47.719 Mar 1: ISAKMP: (0:0:N / A:0): load useful vendor id of treatment
* 01:49:47.719 Mar 1: ISAKMP: (0:0:N / A:0): supplier code seems the unit/DPD but major incompatibility of 194
* 01:49:47.719 Mar 1: ISAKMP: (0:0:N / A:0): found peer pre-shared key matching 192.168.2.101
* 01:49:47.719 Mar 1: ISAKMP: (0:0:N / A:0): pre-shared key local found
* 01:49:47.719 Mar 1: ISAKMP: analysis of the profiles for xauth...
* 01:49:47.719 Mar 1: ISAKMP: (0:0:N / A:0): audit ISAKMP transform 1 against the policy of priority 10
* 01:49:47.719 Mar 1: ISAKMP: 3DES-CBC encryption
* 01:49:47.719 Mar 1: ISAKMP: MD5 hash
* 01:49:47.719 Mar 1: ISAKMP: group by default 5
* 01:49:47.719 Mar 1: ISAKMP: pre-shared key auth
* 01:49:47.723 Mar 1: ISAKMP: type of life in seconds
* 01:49:47.723 Mar 1: ISAKMP: life (basic) of 28800
* 01:49:47.723 Mar 1: ISAKMP: (0:0:N / A:0): atts are acceptable. Next payload is 0
* 1 Mar 01:49:48.119: ISAKMP:(0:1:SW:1): load useful vendor id of treatment
* 1 Mar 01:49:48.119: ISAKMP:(0:1:SW:1): vendor ID seems the unit/DPD but major incompatibility of 123
* 1 Mar 01:49:48.123: ISAKMP:(0:1:SW:1): vendor ID is NAT - T v2
* 1 Mar 01:49:48.123: ISAKMP:(0:1:SW:1): load useful vendor id of treatment
* 1 Mar 01:49:48.123: ISAKMP:(0:1:SW:1): vendor ID seems the unit/DPD but major incompatibility of 194
* 01:49:48.123 Mar 1: ISAKMP: (0:1:SW:1): entry = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
* 01:49:48.123 Mar 1: ISAKMP: (0:1:SW:1): former State = new State IKE_I_MM2 = IKE_I_MM2* 1 Mar 01:49:48.127: ISAKMP:(0:1:SW:1): sending package to 192.168.2.101 my_port 500 peer_port 500 (I) MM_SA_SETUP
* 01:49:48.127 Mar 1: ISAKMP: (0:1:SW:1): entry = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
* 01:49:.48.131 Mar 1: ISAKMP: (0:1:SW:1): former State = new State IKE_I_MM2 = IKE_I_MM3* 01:49:48.383 Mar 1: ISAKMP (0:134217729): packet received 192.168.2.101 dport 500 sport Global 500 (I) MM_SA_SETUP
* 01:49:48.383 Mar 1: ISAKMP: (0:1:SW:1): entry = IKE_MESG_FROM_PEER, IKE_MM_EXCH
* 01:49:48.383 Mar 1: ISAKMP: (0:1:SW:1): former State = new State IKE_I_MM3 = IKE_I_MM4* 1 Mar 01:49:48.387: ISAKMP:(0:1:SW:1): processing KE payload. Message ID = 0
* 1 Mar 01:49:48.887: ISAKMP:(0:1:SW:1): processing NONCE payload. Message ID = 0
* 01:49:48.887 Mar 1: ISAKMP: (0:1:SW:1): found peer pre-shared key matching 192.168.2.101
* 01:49:48.891 Mar 1: ISAKMP: (0:1:SW:1): SKEYID generated State
* 1 Mar 01:49:48.891: ISAKMP:(0:1:SW:1): load useful vendor id of treatment
* 1 Mar 01:49:48.891: ISAKMP:(0:1:SW:1): vendor ID is the unit
* 1 Mar 01:49:48.891: ISAKMP:(0:1:SW:1): load useful vendor id of treatment
* 1 Mar 01:49:48.891: ISAKMP:(0:1:SW:1): vendor ID seems the unit/DPD but major incompatibility of 145
* 1 Mar 01:49:48.891: ISAKMP:(0:1:SW:1): vendor ID is XAUTH
* 1 Mar 01:49:48.895: ISAKMP:(0:1:SW:1): load useful vendor id of treatment
* 1 Mar 01:49:48.895: ISAKMP:(0:1:SW:1): speaking to another box of IOS!
* 1 Mar 01:49:48.895: ISAKMP:(0:1:SW:1): load useful vendor id of treatment
* 01:49:48.895 Mar 1: ISAKMP: (0:1:SW:1): supplier code seems the unit/DPD but hash mismatch
* 01:49:48.895 Mar 1: ISAKMP: receives the payload type 20
* 01:49:48.895 Mar 1: ISAKMP: receives the payload type 20
* 01:49:48.895 Mar 1: ISAKMP: (0:1:SW:1): entry = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
* 01:49:48.899 Mar 1: ISAKMP: (0:1:SW:1): former State = new State IKE_I_MM4 = IKE_I_MM4* 01:49:48.899 Mar 1: ISAKMP: (0:1:SW:1): send initial contact
* 01:49:48.899 Mar 1: ISAKMP: (0:1:SW:1): ITS been pr.e using id ID_IPV4_ADDR type shared-key authentication
* 01:49:48.899 Mar 1: ISAKMP (0:134217729): payload ID
next payload: 8
type: 1
address: 192.168.2.107
Protocol: 17
Port: 500
Length: 12
* 01:49:48.903 Mar 1: ISAKMP: (0:1:SW:1): the total payload length: 12
* 1 Mar 01:49:48.903: ISAKMP:(0:1:SW:1): sending package to 192.168.2.101 my_port 500 peer_port 500 (I) MM_KEY_EXCH
* 01:49:48.907 Mar 1: ISAKMP: (0:1:SW:1): entry = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
* 01:49:48.907 Mar 1: ISAKMP: (0:1:SW:1): former State = new State IKE_I_MM4 = IKE_I_MM5* 01:49:48.907 Mar 1: ISAKMP (0:134217729): packet received 192.168.2.101 dport 500 sport Global 500 (I) MM_KEY_EXCH
* 1 Mar 01:49:48.911: ISAKMP:(0:1:SW:1): payload ID for treatment. Message ID = 0
* 01:49:48.911 Mar 1: ISAKMP (0:134217729): payload ID
next payload: 8
type: 1
address: 192.168.2.101
Protocol: 17
Port: 0
Length: 12
* 1 Mar 01:49:48.911: ISAKMP:(0:1:SW:1): peer games * no * profiles
* 1 Mar 01:49:48.911: ISAKMP:(0:1:SW:1): HASH payload processing. Message ID = 0
* 01:49:48.915 Mar 1: ISAKMP: received payload type 17
* 1 Mar 01:49:48.915: ISAKMP:(0:1:SW:1): load useful vendor id of treatment
* 1 Mar 01:49:48.915: ISAKMP:(0:1:SW:1): vendor ID is DPD
* 01:49:48.915 Mar 1: ISAKMP: (0:1:SW:1): SA authentication status:
authenticated
* 01:49:48.915 Mar 1: ISAKMP: (0:1:SW:1): SA has been authenticated with 192.168.2.101
* 01:49:48.915 Mar 1: ISAKMP: attempts to insert a 192.168.2.107/192.168.2.101/500/ peer and inserted 8553 778 successfully.
* 01:49:48.919 Mar 1: ISAKMP: (0:1:SW:1): entry = IKE_MESG_FROM_PEER, IKE_MM_EXCH
* 01:49:48.919 Mar 1: ISAKMP: (0:1:SW:1.): O State of LD = new State IKE_I_MM5 = IKE_I_MM6* 01:49:48.919 Mar 1: ISAKMP: (0:1:SW:1): entry = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
* 01:49:48.919 Mar 1: ISAKMP: (0:1:SW:1): former State = new State IKE_I_MM6 = IKE_I_MM6* 01:49:48.923 Mar 1: ISAKMP: (0:1:SW:1): entry = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
* 01:49:48.923 Mar 1: ISAKMP: (0:1:SW:1): former State = new State IKE_I_MM6 = IKE_P1_COMPLETE* 01:49:48.927 Mar 1: ISAKMP: (0:1:SW:1): start Quick Mode Exchange, M - ID of 590019425
* 1 Mar 01:49:48.931: ISAKMP:(0:1:SW:1): sending package to 192.168.2.101 my_port 500 peer_port 500 (I) QM_IDLE
* 01:49:48.931 Mar 1: ISAKMP: (0:1:SW:1): entrance, node-590019425 = IKE_MESG_INTERNAL, IKE_INIT_QM
* 01:49:48.931 Mar 1: ISAKMP: (0:1:SW:1): former State = new State IKE_QM_READY = IKE_QM_I_QM1
* 01:49:48.931 Mar 1: ISAKMP: (0:1:SW:1): entry = IKE_MESG_INTERNAL, IKE_PHASE1_COMPLETE
* 01:49:48.935 Mar 1: ISAKMP: (0:1:SW:1): former State = new State IKE_P1_COMPLETE = IKE_P1_COMPLETE* 01:49:48.939 Mar 1: ISAKMP (0:134217729): packet received 192.168.2.101 dport 500 sport Global 500 (I) QM_IDLE
* 01:49:48.939 Mar 1: ISAKMP: node set 330122531 to QM_IDLE
* 1 Mar 01:49:48.943: ISAKMP:(0:1:SW:1): HASH payload processing. Message ID = 330122531
* 1 Mar 01:49:48.943: ISAKMP:(0:1:SW:1): treatment protocol NOTIFIER INVALID_ID_INFO 1
0, message ID SPI = 330122531, a = 84074CC8
* 01:49:48.943 Mar 1: ISAKMP: (0:1:SW:1): the peer is not paranoid KeepAlive.* 01:49:48.943 Mar 1: ISAKMP: (0:1:SW:1): remove the reason for HIS "fatal Recevied of information' State (I) QM_IDLE (ext. 192.168.2.101)
* 01:49:48.943 Mar 1: ISAKMP: (0:1:SW:1): remove error node 330122531 FALSE reason 'informational (en) st.
Success rate is 0% (0/5)
InternetRouter #ate 1 "
* 01:49:48.943 Mar 1: ISAKMP: (0:1:SW:1): entry = IKE_MESG_FROM_PEER, IKE_INFO_NOTIFY
* 01:49:48.947 Mar 1: ISAKMP: (0:1:SW:1): former State = new State IKE_P1_COMPLETE = IKE_P1_COMPLETE* 01:49:48.947 Mar 1: ISAKMP (0:134217729): packet received 192.168.2.101 dport 500 sport Global 500 (I) QM_IDLE
* 01:49:48.951 Mar 1: ISAKMP: node set-412204705 to QM_IDLE
* 1 Mar 01:49:48.951: ISAKMP:(0:1:SW:1): sending package to 192.168.2.101 my_port 500 peer_port 500 (I) QM_IDLE
* 01:49:48.951 Mar 1: ISAKMP: (0:1:SW:1): purge the node-412204705
* 01:49:48.955 Mar 1: ISAKMP: (0:1:SW:1): entry = IKE_MESG_INTERNAL, IKE_PHASE1_DEL
* 01:49:48.955 Mar 1: ISAKMP: (0:1:SW:1): former State = new State IKE_P1_COMPLETE = IKE_DEST_SA* 01:49:48.955 Mar 1: ISAKMP: (0:1:SW:1): removal of HIS State "No reason" why (I) QM_IDLE (ext. 192.168.2.101)
* 01:49:48.955 Mar 1: ISAKMP: Unlocking IKE struct 0x8553C778 for isadb_mark_sa_deleted(), count 0
* 01:49:48.959 Mar 1: ISAKMP: delete peer node by peer_reap for 192.168.2.101: 8553 778
* 01:49:48.959 Mar 1: ISAKMP: (0:1:SW:1): error in node-590019425 FALSE reason for deletion "deleted IKE."
* 01:49:48.959 Mar 1: ISAKMP: (0:1:SW:1): node error 330122531 FALSE reason for deletion "removed IKE."
* 01:49:48.959 Mar 1: ISAKMP: (0:1:SW:1): entry = IKE_MESG_FROM_PEER, IKE_MM_EXCH
* 01:49:48.959 Mar 1: ISAKMP: (0:1:SW:1): former State = new State IKE_DEST_SA = IKE_DEST_SAHello
I gave a quick scan here for the configuration on both devices, found two or three commands are missing from the configuration of the ASA
ASA
---card crypto ipsec_map 10 correspondence address site_router
outside_access_in list extended access udp allowed any any eq 500
outside_access_in list extended access udp allowed any any eq 4500
outside_access_in list extended access allow esp a wholeI'm assuming pre shared key defined on ASA cisco is the same on router
On router
---------Try running the following commands: -.
No crypto ipsec transform-set esp-3des secure_set
Crypto ipsec transform-set esp-3des esp-sha-hmac secure_setAt the time of the opening of the tunnel, please gather at the debug crypto isa 127 output and debug crypto ipsec 127 of ASA
You can also check the configuration below document link
http://www.Cisco.com/en/us/products/ps6120/products_configuration_example09186a00805e8c80.shtml
Ignore the map route on router configuration contained in the above document *.
HTH...
Kind regards
Mohit -
IPSEC connection to the foreign system disorder
Hello!
I make an IPSEC for a V7 astaro on a clients site
the origin is a UC540 with the IOS 15
I see the 'green' on the astaro... Tunnel so its ok, but not the packets go through:
UC540 #show crypto ipsec his
Interface: FastEthernet0/0
Tag crypto map: CISCO, local addr x.x.x.202
protégé of the vrf: (none)
local ident (addr, mask, prot, port): (192.168.10.0/255.255.255.0/0/0)
Remote ident (addr, mask, prot, port): (192.168.49.0/255.255.255.0/0/0)
current_peer x.x.x.8 port 500
LICENCE, flags is {origin_is_acl},
#pkts program: 39, #pkts encrypt: 39, #pkts digest: 39
#pkts decaps: 40, #pkts decrypt: 40, #pkts check: 40
compressed #pkts: 0, unzipped #pkts: 0
#pkts uncompressed: 0, #pkts compr. has failed: 0
#pkts not unpacked: 0, #pkts decompress failed: 0
Errors #send 0, #recv 0 errors
endpt local crypto. : x.x.x.x, remote Start crypto. : x.x.x.x
Path mtu 1500, mtu 1500 ip, ip mtu IDB FastEthernet0/0
current outbound SPI: 0xABA3137B (2879591291)
PFS (Y/N): Y, Diffie-Hellman group: group2
SAS of the esp on arrival:
SPI: 0x349B38CE (882587854)
transform: esp-3des esp-sha-hmac.
running parameters = {Tunnel}
Conn ID: 18, flow_id: VPN:18 on board, sibling_flags 80000046, crypto card: CISCO
calendar of his: service life remaining (k/s) key: (4586494/835)
Size IV: 8 bytes
support for replay detection: Y
Status: ACTIVE
the arrival ah sas:
SAS of the CFP on arrival:
outgoing esp sas:
SPI: 0xABA3137B (2879591291)
transform: esp-3des esp-sha-hmac.
running parameters = {Tunnel}
Conn ID: 19, flow_id: VPN:19 on board, sibling_flags 80000046, crypto card: CISCO
calendar of his: service life remaining (k/s) key: (4586494/835)
Size IV: 8 bytes
support for replay detection: Y
Status: ACTIVE
outgoing ah sas:
outgoing CFP sas:
UC540 #.
UC540 #ping 192.168.49.1
Type to abort escape sequence.
Send 5, echoes ICMP 100 bytes to 192.168.49.1, wait time is 2 seconds:
.....
Success rate is 0% (0/5)
UC540 #ping
Protocol [ip]:
Target IP address: 192.168.49.1
Number of repetitions [5]:
Size of datagram [100]:
Timeout in seconds [2]:
Extended commands [n]: y
Address source or interface: 192.168.10.1
Type of service [0]:
Set the DF bit in the IP header? [None]:
Validate the response data? [None]:
Data model [0xABCD]:
In bulk, Strict, Record, Timestamp, Verbose [no]:
Scan the range of sizes [n]:
Type to abort escape sequence.
Send 5, echoes ICMP 100 bytes to 192.168.49.1, wait time is 2 seconds:
Packet sent with the address 192.168.10.1 source
.....
Success rate is 0% (0/5)
UC540 #.
Any idea?If you have ACLs assigned to the interface, you'd be able to simply remove the ACL of the interface. If you use ZBFW, you can also take the Member of the area out of all interfaces (pls make sure that take you all the interfaces, otherwise, your traffic will not go through the router between certain interfaces, more if you ZBFW, remove the Member area to console the router as you may be locked on the router if you remove some of the Member area first while Telnet or SSH in) the router).
-
scope of traceroute to check the bulk port
Hello
Our client says somewhere in the internet clould of our network's color port. Most of the time, if the client's complaint, I will use the technique of telnet that indicates that the firewall does not block:
Telnet www.webserver.com 80/source-interface fa0/0
However, northeast of my client showed that output of its router:
router #trace
Protocol [ip]:
Target IP address: 192.168.100.1
Source address:
Digital display [n]:
Timeout in seconds [3]:
Probe County [3]:
Minimum time to live [1]:
Maximum time to live [30]:
Port number [33434]: 137
In bulk, Strict, Record, Timestamp, Verbose [no]:
Type to abort escape sequence.
The route to 192.168.100.1
1 202.183.1.161! A * ! A
What makes me confuse is the default port number 33434 but it changed to 137. Does it mean it will check the particular port along the jump?
Any documentation to understand the output this above?
Thank you.
Maher
Here is a link that will help you...
http://www.Cisco.com/univercd/CC/TD/doc/product/software/ios123/123tcr/123tfr/cfrgt_12.htm#wp1058298
When you use with Telnet port numbers, the port is a TCP port.
When you use numbers to port with Traceroute, the port is a UDP port.
And yes the! A way that blocks an access list.
Hope this helps,
~ ron
-
[Webworks-long Press Conference]
Hi all
How to get the event long press on an element of the list item?
Thank you.
Dennis Ritchie.
The DOM touchevent records such information
Your question is a little vague, so I can't really that trap touch events provides this information to the event record timeStamp so...
ontouchstart - retrieve the timeStamp
ontouchEnd - retrieve the timeStamp
Subtract the two and you have the milli-seconds the user pressed for
The same thing a little exists for mouse events
The other touch events are also important - particularly ontouchmove that the user can move out of the clickable area - e.g. accidentally click on leave, move outside it to stop what is happening if you need satisfy as well as
It is easy to work out the details in the ripple using the debugger by setting breakpoints on your event handlers
It is setting up a simple little test app, so you can also see exactly what events
-
How to configure the vpn using two segments in a tunnel?
Hi guys,.
Please help me how to set up two segment in a vpn tunnel. Our client has two segments which is 10.15 and 192.168. We have already established VPN connectivity. We can ping the 10.15 segment, but we can not ping 192.168. Attached is the sample configuration.
crypto ISAKMP policy 1
BA 3des
preshared authentication
Group 2
ISAKMP crypto key xxxxxx address 11.11.11.11
!
86400 seconds, duration of life crypto ipsec security association
!
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
!
map SDM_CMAP_1 1 ipsec-isakmp crypto
Tunnel description
defined peer 11.11.11.11
Set security-association second life 28800
game of transformation-ESP-3DES-SHA
match address 102
access-list 101 deny ip 192.168.202.0 0.0.0.255 host 10.15.0.177
access-list 101 deny ip 192.168.202.0 0.0.0.255 host 192.168.30.174
access-list 101 permit ip 192.168.202.0 0.0.0.255 any
access-list 102 permit ip 192.168.202.0 0.0.0.255 host 10.15.0.178
access-list 102 permit ip 192.168.202.0 0.0.0.255 host 192.168.30.174
Here is the extended ping.
? [None]:Router #pingProtocol [ip]:Target IP address: 10.15.0.177Number of repetitions [5]:Size of datagram [100]:Timeout in seconds [2]:Extended commands [n]: ySource address or the interface: 192.168.202.3Type of service [0]:Set the DF bit in the IP header? [None]:Validate the response data? [None]:Data model [0xABCD]:In bulk, Strict, Record, Timestamp, Verbose [no]:Scan the range of sizes [n]:Type to abort escape sequence.Send 5, echoes ICMP 100 bytes to 10.15.0.177, wait time is 2 seconds:Packet sent with a source address of 192.168.202.3.!!!!Success rate is 80% (4/5), round-trip min/avg/max = 172/172/172 msRouter #pingProtocol [ip]:Target IP address: 192.168.30.174Number of repetitions [5]:Size of datagram [100]:Timeout in seconds [2]:Extended commands [n]: ySource address or the interface: 192.168.202.3Type of service [0]:Set the DF bit in the IP header? [None]:Validate the response dataData model [0xABCD]:In bulk, Strict, Record, Timestamp, Verbose [no]:Scan the range of sizes [n]:Type to abort escape sequence.Send 5, echoes ICMP 100 bytes to 192.168.30.174, wait time is 2 seconds:Packet sent with a source address of 192.168.202.3.....Success rate is 0% (0/5)And here is the result of its crypto isakmp.Crypto ISAKMP router #show itsstatus of DST CBC State conn-id slot11.11.11.11 22.22.22.22 QM_IDLE 1 0 ACTIVEAnd here is the encryption session.Router #show crypto sessioSession encryption router #showCurrent state of the session cryptoInterface: FastEthernet0/0The session state: UP-ACTIVEPeer: 11.11.11.11 port 500FLOW IPSEC: allowed host 192.168.202.0/255.255.255.0 ip 192.168.30.174Active sAs: 2, origin: card cryptoFLOW IPSEC: allowed host 192.168.202.0/255.255.255.0 ip 10.15.0.177Active sAs: 2, origin: card cryptoAnd here are the details of the encryption session.Router #show crypto session detailCurrent state of the session cryptoCode: C - IKE Configuration mode, D - Dead Peer DetectionK - KeepAlive, N - NAT-traversal, X - IKE extended authenticationInterface: FastEthernet0/0The session state: UP-ACTIVEPeer: 11.11.11.11 port fvrf 500: (none) ivrf: (none)Phase1_id: 11.11.11.11DESC: (none)IKE SA: local 22.22.22.22/500 remote 11.11.11.11/500 ActiveCapabilities: (None) connid:1 life time: 23:44:02FLOW IPSEC: allowed host 192.168.202.0/255.255.255.0 ip 192.168.30.174Active sAs: 2, origin: card cryptoOn arrival: dec #pkts'ed drop 0 0 life (KB/s) 4568454/27867Outbound: #pkts enc'ed 4 drop 1 life (KB/s) 4568453/27867FLOW IPSEC: allowed host 192.168.202.0/255.255.255.0 ip 10.15.0.177Active sAs: 2, origin: card cryptoOn arrival: #pkts dec' 8 drop 0 ed life (KB/s) 4591368/27842Outbound: #pkts enc'ed 8 drop 2 life (KB/s) 4591368/27842Hello
Your side has 192.168.202.0/24 and you are trying to PING 10.15 successfully but not 192.168.30.174
Check that the ASA has a route to 192.168.30.174 pointing to the external interface.
Also check that the customer has defined the 192.168.30.174 as part of the VPN traffic correctly.
Federico.
-
Here's the Oracle Documentation of physical storage Structures
The control file contains the following types of records:
- Circular re-use recordsThese files contain non-critical information are eligible to be replaced if necessary. When all the available record places are full, the database expands the control file to make room for a new record or replace the oldest record. Examples of records on the RMAN backups and archived redo logs files.
Question:
How do I know the reuse circular timeline view v$ controlfile_record_section?
TSharma wrote:
You can generate a dump controlfile with highest level of dumping. More it dump level records re-use more circular, you will see at the end of the dump file.
For example:
ALTER session set events ' trace immediate name controlf level 3 ";
ALTER session set events ' trace immediate name controlf level 4 ";
.
.
.
ALTER session set events ' trace immediate name controlf level 15 ";
Interesting about the levels up to 15 point.
Level 10 actually gives you a raw dump of the file - so there's a funny jump 9-11, I had not noticed.
The OP removes the dumps that is not available in the v$ controlfile_record_section, well - since no matter what item that has not used all the records will not give any idea of whether or not it would recycle any additional information:
Excerpt from the opinion:
TYPE RECORD_SIZE RECORDS_TOTAL RECORDS_USED FIRST_INDEX LAST_INDEX LAST_RECID ---------------------------- ----------- ------------- ------------ ----------- ---------- ---------- ... LOG HISTORY 56 10888 10888 2545 2544 157246 OFFLINE RANGE 200 1021 0 0 0 0 ARCHIVED LOG 584 21480 21480 3203 3202 67642 BACKUP SET 40 32672 32672 15883 15882 717917 BACKUP PIECE 736 32128 32128 2155 2154 727763 BACKUP DATAFILE 200 29288 29288 22862 22861 836798 BACKUP REDOLOG 76 21488 21488 146 145 146154 DATAFILE COPY 736 63936 63936 52286 52285 468871 BACKUP CORRUPTION 44 1113 0 0 0 0 COPY CORRUPTION 40 1021 0 0 0 0 DELETED OBJECT 20 418048 418048 116058 116057 2210380 PROXY COPY 928 1006 0 0 0 0 BACKUP SPFILE 124 1812 1812 1438 1437 23634
It's a strong enough to bet that the sections where FIRST_INDEX is greater than LAST_INDEX sections where an array of limited size is reused. But what can infer you about the OFFLINE RANGE?
Compare with discharge, circular scales that have been used to show things like:
*************************************************************************** LOG FILE HISTORY RECORDS *************************************************************************** (size = 56, compat size = 56, section max = 292, section in-use = 292, last-recid= 311, old-recno = 20, last-recno = 19) (extent = 1, blkno = 95, numrecs = 292) Earliest record: RECID #20 Recno 20 Record timestamp 01/23/12 09:22:58 Thread=1 Seq#=20 Link-Recid=19 kccic-Recid=1 Low scn: 0x0000.0009914b 01/23/12 09:22:45 Next scn: 0x0000.00099d0d Latest record: RECID #311 Recno 19 Record timestamp 06/24/13 08:00:24 Thread=1 Seq#=311 Link-Recid=310 kccic-Recid=1 Low scn: 0x0b86.404a1635 06/14/13 16:06:45 Next scn: 0x0b86.404a8554
(Different control file, incidentally).
Yet once this only shows us anything on the beaches of circular reuse if they have not bee used.
Concerning
Jonathan Lewis
-
History of database file and line changes
Hi all
I've dug around a wile, but found no solution to this problem.
I have a DB (10g) on which I have a series of tables which I would like to follow the changes.
Is an example of Table structure
The process should be as followsID (Sequence driven record Id) Column_1 Column_2 .. Column_N IS_CURRENT (0/1 value which is 1 only for the current record) RESOURCE_ID (ID of the resource which I the record) TIMESTAMP (SYSDATE when the record was created)
(1) new creation of elements:
-By using an insert statement
-a new ID is taken from the sequence
-records is inserted with IS_CURRENT = 1
(2) update articleUPDATE MyTable SET IS_CURRENT = 0 WHERE ID = XXXXX
To avoid unnecessary history records the creation, I would like to check whether the properties of the "IS_CURRENT = 1' record has changed.INSERT INTO MyTable (ID, ................., IS_CURRENT, ......) VALUES (XXXXX, .............., 1, .......)
I can do for this SELECT COUNT usign with in which all the columns for recording, but I wondered if something more intelligent is there.
I checked if it was possible to use the comparison of ROWTYPE variables, but it is not possible.
Is it possible, after you have instantiated a ROWTYPE variable (the on input) to do something like
SELECT COUNT (*) FROM MaTable WHERE something = rowtype_variable?
Thanks for the support
Concerning
Andrea
Published by: user10374756 on 11-ott-2012 7.52user10374756 wrote:
I have a DB (10g) on which I have a series of tables which I would like to follow the changes.
The process should be as follows(1) new creation of elements:
-By using an insert statement
-a new ID is taken from the sequenceGood.
-records is inserted with IS_CURRENT = 1
Dangerous idea. Remember that multiple users may do so at the same time (or almost). And they will not notice the other session data, as long as it is not engaged.
(2) update article
Setting a DAY MyTable SET IS_CURRENT = 0 WHERE ID = XXXXX
This update will introduce a bottleneck in your application (point of serialization). Each session will have to wait the other session finished its update. And if it is implemented incorrectly, then you will still end up with two entries is_current = 1.
-
I seeks comments on the appropriateness of the Flash CS4 for a task. It is a clinical context
with a standalone PC running Vista and Flash CS4 (ActionScript 3).
I need to present a simple animation then place several small pictures on the screen and have the object to select one by clicking on it. Depending on the response, a new series of images (some random some derived from the selected item) appear and this is repeated until the task is completed. This part of the task is standard fare and is well suited to the Flash and AS 3.
However, I must also produce a log of activity. Specifically, I need a file needs to be created which shows which images have been placed on the screen and when (time since the application started), and whose object clicked on and when the images. In other words, I need to a record timestamped of which has been placed on the screen and what was clicked on. It takes a time of 0.1 s accuracy.
So my question is whether or not this can be done with ActionScript 3. Also, if possible, someone has a pointer to a relevant script this writing of file handles and timers or a good source of instruction on how to do the same thing?
Thank you
PauloYes, it can be done.
Quote:
However, I must also produce a log of activity. Specifically, I need a file to be createdIf you do in the AIR you can create the file. In the case of a web application - Flash does not create files. In this case, you can use the capabilities of class SharedObject to keep the record.
-
Hello friends, I am not able to record the songs in music in ios 9.3, please give me the solution.
Hello friend
I'm not able to record the songs in music in IOS 9.3, please give me the solution.
Click on album artwork, not the name of the song as you used to. the album art will fade to black revealing the old side thing.
-
Cannot record music on ipad after update to IOS 9.3.
Cannot record music on ipad after update to IOS 9.3. In the view 'now playing' I could tap on the title that opens a window where I could score 1-5 stars. Now by tapping on the title just changes the display of the album. What can I do? I would be very unfortunate if I could rate is no longer my music while listening to it on the IPad. The 1-5 star rating still works in Itunes, but it is a great help for me. Thanks for help.
Try this below the steps it will work!
You must press the title to bring up the option enter a star...
Once it is visible, touching it will bring back the title most of the time and allow entry only part of the time.
"need to press the title of music playback and the rating stars will appear."
-
How trigger (start) record in garageband (ios) of external midi controller?
It is possible to start and stop recording in the iOS version of Garageband using external midi controller MIDI controls? If so, what are the commands?
Maybe you are looking for
-
How can I find my battery cycles? I have a MacBook Pro under windows in Bootcamp.
I have a MacBook Pro running Windows 7 in Bootcamp. My battery indicator says I should replace my battery. How I 1) know how many cycles my current battery on it and 2) know what battery I should seek to replace? I found the system hardware, but it o
-
When I turn on my iPad mini 2 I'll click on the shock of the Royal. Then, when loading to 81 percent he turns back to the home screen. Please help me.
-
When I open Firefox only black appears
When I open firefox only black screen and menu or anything wear.I uninstall firefox and re install. But still the same problem.Help, please
-
I can't recover any storage and I do not know or cannot find what is using it.
-
For Satellite Pro U200 port replicator
Can anyone confirm which (if any) of the port replicator are compatible with the Satellite Pro U200? If I understand correctly, one of the USB models should be used, but all those I looked at only list the U300 as being compatible. Maybe it's just be