How to check my site to site vpn using ASDM?
How can I check that my VPN site-to-site really works by using ASDM? I was expecting to see some sort of graphical OWL or a counter is ASDM, but I see nothing. The CLI by "sh crypto ipsec SA" I see the program and crypt increment so I think it works.
ASA5505 at each end
The ASA version: 8.0.5
ASDM Version: 6.3.5
Hi Tod,
on the cli, indeed the counters in "crypto ipsec to show his" will tell you if the data passes over the tunnel.
In ASDM, you can go to monitoring-> VPN-> statistical VPN-> Sessions and select "IPsec Site to Site" as the filter.
I do not think that we have graphics for data on the tunnels, but you can have a graph of the number of active tunnels (surveillance-> VPN-> graphics-> tunnels IPsec VPN connection)
HTH
Herbert
Tags: Cisco Security
Similar Questions
-
Site to Site VPN using an interface to Peer and LAN
Hello
I have an ASA 5580 to the site to site VPN with our partner. VPN connection is through my external interface and Local for the VPN network comes from the external interface too. Is it possible to do? Thank you.
The layout you describe is contrary to the concept of basic firewall of the approved facility and no approved interfaces (upper and lower security level).
If your LAN is on the external interface, which is to stop remote users simply access it directly?
-
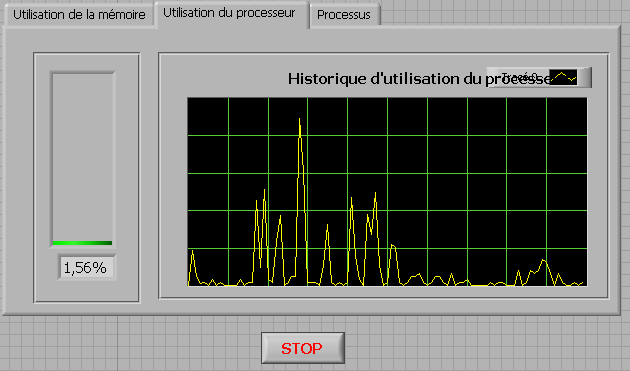
How to check the CPU usage and paging using LabVIEW
Hi guys,.
I build an application that is used to check the CPU usage and paging using LabVIEW. How can I do?
any help, suggestions or advice will be greatly appreciated...
Kind regards
Prashant
Hello
If you plan to build your app for Windows, you can use .NET classes. (System.PerformanceCounter), there is a simple example with LabVIEW:
C:\Program NIUninstaller Instruments\LabVIEW 2010\examples\comm\dotnet\SimpleTaskMonitor.llb
Also, you have several screws that you can use to verify information about the processor.
Kind regards
-
How to check if a key has been used
Hi all
Is there a way to determine whether a key has been used in a SQL statement?
Example of
I received a call from a developer said that their request was going very slowI checked what oracle was doing
He was using an index with 5 distinct values on a table with a number of lines of 9.2 million
Selectivity is very bad.
Then I discovered after talking to the Director it was a hint to use the (silly) hints
Once we had the suspicion that he did a scan of Table full and actually ran much faster.
However, when I was watching the SQL text in v$ sql and v$ sqlarea he had no way of knowing if we used a hint
IE, I saw: / * + RULE * / in the code.
Does anyone know how to check (from the DB), if an indication is used in a sql statement?
And if the indication is used, what is the indicator.
Thank you
G.
You can use the following to see the execution plan with the outline and see advice
Select * from table (dbms_xplan.display_cursor (null, null, 'schema'));
select /*+ rule */ sum(id) from t1 where flag = 0 Plan hash value: 2170464548 ------------------------------------------------ | Id | Operation | Name | ------------------------------------------------ | 0 | SELECT STATEMENT | | | 1 | SORT AGGREGATE | | | 2 | TABLE ACCESS BY INDEX ROWID| T1 | |* 3 | INDEX RANGE SCAN | T1_FLAG | ------------------------------------------------ Outline Data ------------- /*+ BEGIN_OUTLINE_DATA IGNORE_OPTIM_EMBEDDED_HINTS OPTIMIZER_FEATURES_ENABLE('10.2.0.1') RBO_OUTLINE OUTLINE_LEAF(@"SEL$1") INDEX(@"SEL$1" "T1"@"SEL$1" ("T1"."FLAG")) END_OUTLINE_DATA */ Predicate Information (identified by operation id): --------------------------------------------------- 3 - access("FLAG"=0) Note ----- - rule based optimizer used (consider using cbo)HTH
Kind regards
Jagdeep Seven
-
How to check if the directory is created using create or replace directory
Hello
I create a directory like below:
Create or replace directory TEST_DIR AS 'C:\ABCD '.
How to check if the directory is created or not? Is there any request for it?
Thanks in advance.
PKSELECT * FROM ALL_DIRECTORIES WHERE DIRECTORY_NAME LIKE '% TEST_DIR %. "
Published by: user3522507 on 2010.06.16. 07:19
-
How to create several site VPN on Cisco 2801
Hello
We use 2801 to our VPN needs. We have already configured a VPN site-to site inside. My current scenario is to create several VPN IE at different sites and a remote client VPN server for our road warriors (they use a cisco VPN client to connect).
Let me know how can I achieve that scenario. Currently we have in VPN profiling in place. can I fill the script using VPN profiles, how it can be used. Kindly advice me at the earliest.
Please find attached the 2801 direct configuration file, which is quite works very well
Thanks in advance.
Djamel.
Djamel
As much as I know it does no harm to have political isakmp 9 and isakmp 10 with the same parameters in each of them. But it also is not good. Others that extra isakmp policy I don't see anything that seems problematic in the config you have posted.
HTH
Rick
-
How to check my site from https to the Web site with you? The warning triangle should disappear.
www.needlepointnow.com has a caution symbol triangle it's https address.
What are the steps to verify my site with firefox? Keep in mind I'm not SHE but a humble Designer. So step by step please.This must be resolved so that our readers feel secure renewing subscriptions.
Your site is currently using TLS 1.0, which is obsolete and unsafe. You must upgrade to TLS 1.2 or later
-
How to check if the address pool is used by the vpn client
Hello world
I need config anyconnect VPN on ASA existing who also owns the remote VPN client running.
Under the ASDM when I click the address pools
I see two address pools
Pooldefault that I can see is used by vpn distance courses.
PoolX - this subnet is not assigned to the user now.
Is there a way I can check if PoolX subnet is configured to assign the IP address to the remote VPN?
Concerning
MAhesh
Hello
On the CLI, you could check the output of
See establishing group policy enforcement
and
See the tunnel-group race
to see if the PoolX is used nowhere in the VPN configurations.
Of course, you can also just simply look for the configuration and see if there is anything else than the current configuration of the PoolX on the SAA.
See the race | PoolX Inc.
This should probably display only the command "ip local pool ' if the address pool has just been created but is not used anywhere.
-Jouni
-
Configure the ASa 5505 of remote site by using ASDM
I would like to be able to administer the ASA 5505 from another site, which is connected via a LAN of Ipsec site-to-site.
How to activate this feature?
Hello
You can remotely administer an ASA using the public IP address (via the Internet), or through the tunnel to the private IP address.
You can reach the private IP address by activating the command:
management-access inside
You can access the ASA by IP address private via CLI or GUI.
Federico.
-
How to check if "PO output for communication" uses XLM or OracleReports
I need to change the purchasing document "Exit IN. for communication", but I must first identify if it uses XML Publisher report or reports of the Oracle.
How can I check that using the client?
Any help is welcome.
RodrigoHello
OK, here's what I did to customize the presentation of PO:
1 create new templates in BI Publisher:
1.1 Please download the original models:
In my evolution, I used the original models of Oracle as a starting point. If you get their first:Logon with respo XML Publisher administrator and navigate to 'Models' > search model whose name "Standard purchase order Stylesheet" and click on it in the result of the research. Click the download link to download the file .xls on your local drive. You can repeat that for all other models that I mentioned earlier, depending on which layout you want to change.
I do not recommend to change the original files. In case of problems you can always return to the original version of Oracle.
1.2 now to create your own templates:
In XML Publisher administrator, you can create a new template. As model name, use a meaningful name with a prefix such as "XX" or something that you usually use for your own developments.The rest of the fields in the template definition must be equal to the standard models (so just copy & paste the values from there). And you can download the original .xsl file to the beginning.
2 let know to use your own XML Publisher templates:
connection with a PO administrator/super user responsibility:
2.1 (by purchase) > Setup > organizations > Options purchases > control tab > set "Output PO Format" = PDF
2.2 (by purchase) > Setup > purchases > Document Types > find the 'Purchase order - Standard' Document Type > define the presentation of the Document Type = "XX purchase order Stylesheet" (put the name of your custom here template!)Repeat step 2.2 for other Types of documents, such as agreements to cover and if necessary press coverage.
3. test:
Now try the PO output for communication. If everything has worked, you should see a purchase order as a PDF with the same layout as before. Now it's time to start customizing the layout.4 customize the page layout:
You must change the XSL templates. You need some knowledge of XSL - FO, but with some programming experience little, you will have the concept quite easily. In fact, the XSL - FO offers many possibilities to model your page layout.BUT: Change the XSL template to change your "LAYOUT" only, not the data of the report part. Of course you can text coded hard and calculations in your XSL, but dramatic changes of the portion of data are not really possible with this.
If you want to do, then search on Metalink, there is a document that explains how to customize the data for printing of PO. I don't have the Note in his hand right now...
BTW. XML Publisher is the former name of the product, Oracle has renamed it BI Publisher. In EBS, it is still often referred to as "XML Editor". You can see the two names as synonyms. You pay more attention to the version of BI Publisher, which is integrated into EBS is different from what you can have as a stand-alone versions.
Best regards
David. -
How to check if the assignment is in use?
Hello
before you export a document as a pdf, I run a few controls on the links (if out of date or missing etc...). But I realized that you can have inaccessible assignment which is a little harder to find. Can someone help me with this one... y at - there a way to check if the transfer is 'in service' next to check if the assignment file lock file exists?
The thing is that in some kind of workflow that you can export the document to PDF without knowing that someone is always holding a piece of text in InCopy. Navigation through links is not helpful with this situation.
TNX!
Kind regards
Marko
Hello
isn't just the lockState of storyproperty?
var currStories = app.activeDocument.stories.everyItem().getElements(); l= currStories.length; while(l--){ cS = currStories[l] ; lS = cS.lockState; if(lS == LockStateValues.LOCKED_STORY){ cS.textContainers[0].select() alert('Locked Story') } }the other way around: assignments--> assignedStories--> storyReference-> check if history-> check lockState
-
How to check if a SQL profile is used or not?
Hello
We have a few plans and profiles SQL in the database. There has been some changes to the code and it is now difficult to follow if a SQL profile or outline is still used? Is it possible to find out who?
Thanks in advanceLook for the entry corresponding to the SQL statement you are reviewing in V$ SQL. Look at the OUTLINE_CATEGORY and SQL_PROFILE columns. NULL indicates that no plan/profile has been used.
-
site to site vpn - internal network even on both sides of the tunnel
Hi all
I have the following questions about the Site Site VPN using ASA 5510 and 5505
Scenerio is
1. we have five branches & headquarters
2. we want to establish a vpn between branches & Head Office (VPN from Site to Site)
3. all branches & head office using the same internal network (192.168.150.0 255.255.255.0)
My question is
How can I configure VPN site-to-site between branches & head office with the same internal network (192.168.150.0/24)
Please help me with the configuration steps & explanation
I have experience on setting up vpn site to site between branches with differnet internal network (for example: 192.168.1.0/24 and 192.168.2.0/24)
Waiting for your valuable response
Hello
Here are a few links on policy nat
http://www.Cisco.com/en/us/products/ps6120/products_configuration_example09186a008046f31a.shtml#T10
http://www.Cisco.com/en/us/products/ps6120/products_configuration_example09186a00807d2874.shtml
Concerning
-
Hi all
I was wondering if I have a Cisco ASA firewall and there several site to site VPN using pre-shared keys. If I want to add an another VPN Firewall. Do I have to add all the crypto ISAKMP stuff yet or what. Or I can just all ready config VPN in the firewall. I mean besides the new card Crypto, ACLs and the NAT 0 statement that other statements do I need to enter this new site to the other tunnel in the buld order? I don't want to end up ordering more than is necessary.
No, you don't need to add new isakmp crypto policies if you already have a configured strategies match. You can also reuse the crypto ipsec transform-set political if it is the same on the other site of the LAN-to-LAN tunnel (as long as it matches at both ends).
You're right, the only statements, you need to add would be the ACL for NAT entry 0 and new sequence card crypto (with crypto ACL, all processing and input of game peer).
Hope that helps.
-
PIX Site to Site VPN to aid to specific port
Good day to all!
I know that to have establish a site to site VPN using 2 PIX firewall, it should be noted the interesting traffic on both sides. Usually, we make the following statement:
accessList AllowedTraffic ip 192.168.2.1 allow 192.168.3.1
But I thought what happens if specify us specific ports on the
The ACL that is used for interesting VPN as HTTPS traffic? Like the one below:
Acccess-list AllowedTraffic tcp 192.168.2.1 192.168.3.1 eq 443
Comments would be nice...
Thank you...
Chris
Here are my configs when I tested it. I hope this helps! If Yes, please rate.
Thank you
Maybe you are looking for
-
Facebook, play pogo, I get this message "cannot find the plot of pogo, xd does not.
This happens when I try to play games pogo on Facebook, "couldn't find the frame of pogo, xd does not.
-
my phone will not ring when making calls, texts or emails-phone-shop finds nothing wrong and say its faulty?
-
ELITEBOOK 2540p: WINDOWS XP WE ELITEBOOK 2540p?
Hello Claudio my name is and I am looking for someone who could help me how do to install Windows Xp on my Elitebook 2540p because that whenever I try to make my pc starts to load my DVD but after a few minutes, it appears a blue screen that said ins
-
Sculpt Desktop Comfort dongle and sculpt comfort keyboard
I bought Sculpt Comfort Desktop. It comes with a keyboard and a mouse, but the keyboard was not working and I got a replacement keyboard. Keyboard replacement provided with a dongle. I'm not able to use the current dongle to work with my new keyboard
-
My e240 V1 is now paralyzed...
It's a sad day. After 4 great years, the best consumer electronic device I have ever owned has finally succumed to a failure of shabby headphone jack (I suspect a loose/damaged solder joint). After that an upgrade to rockbox and an sdhc card it was