Machine using certificate authentication
Hello
I am facing this error while the machine authenticates agaist AD for wireless users. My requirement is users with company laptop get vlan privileged and BYOD should get vlan normal. I use Cisco ISE 1.1.1 and rules of authentication configured in client diffrenciate based on the assets of corp and BYOD. Result of the authentication policy is sequence of identity that uses the certificate profile and AD. All laptops Corp. must be authenticated using certificates and then followed by past and user of the AD. When I set up XP users to validate the certificate of the server this error comes in Journal of ISE "failed authentication: 11514 suddenly received empty message TLS; treat it as a rejection by the customer' and if I turn off validate sewrver certificate then this error "failed authentication: 22049 binary comparison of the certificates has failed."
Any help?
Thanks in advance.
Hello
It is a limitation on native begging him, when you activate the smart card or certificate of authentication for the network connection, and then he tries to use it for the computer and user authentication. It does not use certificate for machine auth authentication and authentication of the password for the user authentication.
You can use the anyconnect Network Access Manager (which is free if you have a cisco wireless network) and not only it allows you to define what type of desired authentication (certificate of machine) and password for the user, but it has a new feature called the chaining of eap. Chaining of EAP is a powerful option because you can choose the order (machine first then user) when the client connects to the network. You have is no longer to point out about machine authentication timers and I was wondering what that is best suited when it comes to registration of users in and out of their machines in order to refresh the cache of authentication machine at ISE. However chaining eap uses eap-fast, which is a framework for authentication based on the CAP.
This is the last note of release on this feature (currently in beta):
Tarik Admani
* Please note the useful messages *.
Tags: Cisco Security
Similar Questions
-
Two factor authentication to cisco anyconnect using certificates
I plan to factor authentication two configuration, and intend to buy thawte Certificate, but need help to choose which certificate do I need to buy. Can I purchase a code signing ssl certificate and use it to two-factor authentication? If this is not the case, what should I buy and what is the procedure?
Concerning
NH
Hi, NH,
I see that you have authentication two factor for customers who connect to your network by using AAA + certificates head.
I also see that you are looking to get the signed certificate from Thawte.
> In two authentication factors in your scenario, the client when the connection must present the name of user and password and a client certificate to complete the authentication.
> You can get the client signed any Public certificate authority (CA) certificate.
> The certificate with the key usage extension attribute value, such as the authentication of the Client can only be used by the client during client certificate authentication.
> If extended key usage does not 'Authentication of customer' as one of its value then this certificate cannot be used for authentication of the client certificate.
> Now, once you get the client certificate and installed it on the post, and currently the head of network during authentication may fail once again validating the certificate of the network head as it is necessary that the head of network must have the certificate root certificate Client installed in his store of Certificate Authority (CA).
Kind regards
Nouredine Sethi
-
AnyConnect VPN client authentication using certificates
Guys, I'm trying to configure my ASA5505 to authenticate the AnyConnect VPN clients using certificates. I have 'Certificates' defined as my method of authentication in my AnyConnect connection profile (see screenshot), but I get 'Certificate Validation failure' whenever I try to connect. The certificate I want to use is a computer issued by my CA certificate company root (Windows Server 2008 running Active Directory Certificate Services). Screenshot of certificate is attached. I added the root certificate on the SAA, and I tried all kinds of combinations by using the corresponding certificate in the AnyConnect Client profile. Each attempt failed, and I'm having no luck finding documentation on how to proceed. Any help would be greatly appreciated!
Hello Shaun,
The problem you're describing, not be able to authenticate through certificate through Microsoft Internet Explorer, is the fact that the certificate is in the computer store. You do not want to confirm with Microsoft, but, I understand that only Microsoft Internet users explore the user store, this certificate is not available to attend the ASA via the Internet browser.
-Craig
-
Use certificate and form to the same application of ADF basic authentication
Hello
We have an application that needs to use time based authentication CLIENT-CERT and FORM.
I have configured a domain with Client certificate requested and applied, generated a client certificate, created an Asserter custom identity with a Login Module and successfully recorded in our application using the CLIENT-CERT. , our customer wants to use the FORMS authentication at the same time with the CLIENT-CERT authentication type.
The idea only I had was to use a servlet proxy deployed on another instance of WebLogic (10.3.6) that uses the CLIENT-CERT authentication that will forward requests to the main ADF application using classic FORM based authentication. The problem with this approach is that the proxy servlet is accessible using HTTPS and the communication between himself and the application of the ADF is made by using HTTP, so the client browser is redirected to HTTP on first access. For example, if I used Apache to proxy requests that would have been easily solved using RequestHeader set true WL-Proxy-SSL.
You have any other suggestions on how to achieve this?
Thank you in advance,
Ionut Cristian Paraschiv
Multichannel Solution Architect
Advahoo Business Solutions
I found a work around for this problem:
-l'application uses FORMS authentication in function
-l'application is deployed on a server managed with Client Cert has requested and applied (only clients with certificates will connect over HTTPS)
-the login page has only one input for the password text
-in the bean of login, in the doLogin() method page, we can get the certified client and get the username with a custom class of UserNameMapper
Object certChain = request.getAttribute ("javax.servlet.request.X509Certificate");
Certificate CERT [] = certChain (certificate []);
X509Certificate cert = (X509Certificate) CERT [0];
... to get the user name
Ionut Cristian Paraschiv
Multichannel Solution Architect
Advahoo Business Solutions
-
Windows 7 Edition using Home Premium. Had Adobe Reader and Flash work and then had problems to update. Uninstalled all Adobe products and now cannot re - install. I get the error "certificate authentication failed. Other proposed help sites enter gpedit.msc but it is not installed on my machine (not available with Win 7 Home Premium, I understand, $220 upgrade to Ultimate... :-(
Hello
Step 1: Run the fixit to solve the problems of the uninstalling and reinstalling:
Solve problems with programs that cannot be installed or uninstalled
http://support.Microsoft.com/mats/Program_Install_and_Uninstall
Step 2: I suggest to try a clean boot and install.
How to troubleshoot a problem by performing a clean boot in Windows Vista or in Windows 7
http://support.Microsoft.com/kb/929135
Note: After installing windows update, follow step 7 in the link provided to return the computer to a Normal startup mode
To further support contact Adobe support to improve assistance to this topic:
http://forums.Adobe.com/community/webplayers/flash_player
http://www.Adobe.com/support/Flash/
The video problems with Internet Explorer
http://support.Microsoft.com/kb/2532294
It will be useful.
-
ISE-based certificate authentication
Hello
I am developing an understanding of certificate based authentication using EAP - TLS on the ISE. My question is do we really certificate authentication profile (CAP) even if it is enough just to perform certificate-based authentication and we don't are not interested in setting up authorization rules based on which field of the certificate was specified as username in the CAP. I'm asking this because I think that probably in certificate based authentication, ISE has just need to check the validity of the certificate and if it was signed by a certification authority that it can check by looking in the certificate store. Please let me know if I have the wrong concept.
I am curious to know what the whole purpose of CAP? I read in a book that:
To validate the identity ISE must ensure that the credentials are valid. In the case of authentication based on certificates, it must determine if:
 The digital certificate was issued and signed by a certification authority (CA).
The digital certificate was issued and signed by a certification authority (CA). The certificate has expired (check the dates of the beginning and end).
The certificate has expired (check the dates of the beginning and end). The certificate has been revoked.
The certificate has been revoked. The customer has provided evidence of possession.
The customer has provided evidence of possession. This certificate has the correct use of the key, the critical extensions and extended values present key usage.
This certificate has the correct use of the key, the critical extensions and extended values present key usage.So in above listed points where is used specifically for CAP?
Thank you for taking the time to answer.
Kind regards
Quesnel
Hi, Quesnel, I'll try to answer your points as best I know :)
#1) I don't really know what the mechanics of ISE are when it comes to the CAP. It is however a snip-it of the Cisco Design Guide:
S certificate of authentication profiles (CAP) are used in the rules of authentication for authentication based on certificates. The CAP sets certain attributes in the certificate to find out & use as a source of additional identity. For example, if the username is in the CN = field of the certificate, you can create a COURSE that examines the CN = field. Then these data can be used and verified against other sources of identity, such as Active Directory
(#2), you should be able to set a COURSE and use it as a storage of identity without the need to put in a sequence. I've done several times and just re - confirm is it possible in my lab. Please check again :)
(#3) une sequence of identity store lets examine you more than one identity store. In addition, it defines defines the order in which the Sources of identity are questioned. Once a match is found, the process stops and the information returned to ISE.
Thank you for evaluating useful messages!
-
Certificate authentication mode?
I want to try to build a more secure LAN. I want that every client (with or without wire) to connect the network used a certificate not a username/password pair.
But now, as I am a newbie, I don't know what to choose between GANYMEDE + and RADIUS. Because I have a Mac mini, RAY is perhaps more appropriate, but I don't know how to establish the certification authority.
Any help or suggestion will be appreciated!
More generally, we do this in the context of the implementation of a product as of Cisco Identity Services Engine (ISE). ISE uses 802. 1 x and has the ability to check clients for things such as a certificate during authentication / posture assessment / remediation process.
Also, it acts as a RADIUS server, and can dynamically remove permission (CoA) change to the authenticator (i.e. switch or wireless controller) to control things like the assignment of VLAN client and everything you can apply access lists.
Client side, a supplicant is used to interact with the authenticator. You can use native supplicants to OS X or Windows, etc, but we generally recommend use of the Cisco AnyConnect Secure Mobility client with its access network (NAM) Module, because it is much more complete for this purpose.
You could also make 802. 1 x with certificate authentication and use an authentication server different backend (like a regular Cisco ACS or Microsoft Network Policy Server), but you get only basic authentication more vs rich functionality what ISE gives (although ISE is much more ;)).
Take a look at this Youtube video for an example of setting up certificates of authentication on ACS:
-
Wireless, machine and user authentication
Hi all
I have a problem with my connection to employee wireless (802. 1 X EAP connection).
When users are on a wired connection and then come to the employee wireless on XP or 7 machine name is not automatically sent to ISE in the message of 802. 1 x. I have to restart the machine to thave the computer name sent in the 802. 1 x Message.
Is this normal? Is there any setting to have the name of the auromaticaly machine has sent on the wireless!
Thanks for the support
Hi Boris,.
You mean you use the authentication of the computer? and that is not used correctly when the device is already connected to the wired side? and it is only sending the username? not the name of the computer?
Well, the problem with the windows machine auth and ACS (and ISE is the same) that windows sends the auth trigger machine only when it starts. for example, if the user is already connected to the auth machine cannot be triggered.
Rather than restart the machine, I thing logging off and it will trigger demand for auth machine as well.Microsoft RADIUS (NPS or the older IAS) can detect the State of machine auth, while the user is running. This is because Windows and the radius of the same provider, they fit together better.
I know a customer who left the entire RADIUS ACS for NPS becaue of this issue.
I hope this answers your concern.
Kind regards
Amjad
Rating of useful answers is more useful to say "thank you".
-
Error: Tunnel research group using certificate cards failed for the peer certificate
I have the research group of the Tunnel using certificate cards failed for peer certificate error when signing the SAA on my SSL VPN. I have the certificate installed on the client, I have no mapping of certificate created.
I can map user certificate to a user name used to connect to the SSL VPN?
Y at - it good documentation describing the certificate mapping?
Off topic: I listen to a podcast of TAC security this week, and one of the members of the Group of experts preparing for an introduction to PKI to Networkers (I don't remember not the year). Videos of these presentations are available?
Once more, I appreciate all the help.
Triton
Hello
I guess the previous fill command comes in the webvpn under tunnel like this group attributes:
tunnel-group test general attributes
user name of certificate-CN
tunnel-group test webvpn-attributes
pre-fill-username-customer ssl
No aaa authentication
aaa authentication certificate
You can also specify which field of the certificate you want to that username is taken.Users will be able to change the username (which beats the objective right?), but then they will not be able to connect using any other username. So if they change they will not be able to connect.Also, you can use the username to hide which will not allow users to change the user name it will be greyed out.And Yes, it's essentially a double authentication coz we use the certs and aaa to authenticate a user. -
Cisco ASA IPSEC from the understanding of a site to tunnel auth using certificates
assuming that my company and another company (BBT) attempt to set up a tunnel to a site by using certificates. lets say we have asa 5520 s and have agreed to use says that our certification authority.
On my end, I do registration certificate using SCEP Protocol and suggests that the end BBT is set up exactly the same way.
First, I generate a pair of keys RSA - Im assuming that it is key to my ASA public private for the encryption and decryption-(pls correct me if wrong Im)
Then I set up a trustpoint to registration certificate (in this case, it will be Server CA Entrust). I will set up my full domain name and the parameters of CRL.
Then, I get a certificate of the AC CA. This package contains a fingerprint of the certificate which is loaded on my ASA. apparently - the fingerprint of the certificate is used by the 'end' entity to authenticate the received CA certificate. Why would the final entity to authenticate a CA certificate that has already been installed on this subject?
In other words, what really does this print? Surely this cant be the same footprint that GETS installed on the BBT ASA?Finally, I request and install a certificate of identity. It asks for a password? I believe that it is used in case I want to make changes to the certificate, such as the revocation of the certificate. (Once again, please correct me if wrong Im)
a few additional questions
during the phase of authentication isakmp how my asa verifies that the certificate that the ASA BBT sent was indeed signed by the certification authority approved. How exactly?
My ASA and ASA BBT must trust the same CA. In other words, it must be set up the same trustpoints?
or can I have to entrust CA server as a trustpoint and verisign?How the certificate authentication process works since the ASA receives valuable traffic through the exchange of encrypted data?
1 million thanks!
Hello west33637,
You can read this document to get a simple example of setting up a VPN S2S using certificates on an ASA
http://www.Cisco.com/en/us/products/ps6120/products_configuration_example09186a0080aa5be1.shtml
I would try to separate your questions and see if I can answer. I will speak without using the SCEP Protocol because it adds a layer of complexity that can be confusing.
(Q) Comment can I get a certificate?
1 generate a RSA key pair. A pair of RSA keys as you indicate has a public and private key. Public and private keys are large number created by multiplying the other prime number (very simple explanation). These keys are used for encryption simple control. The private key is kept private and never awarded. The public key is provided for everyone through the certificate received from the device.
Data encrypted by the public key can only be decrypted by the private key and vice versa.
more details here: http://en.wikipedia.org/wiki/RSA
2. we create a trustpoint (container to configure and set parameters in the certificate). In the trustpoint that we associate the RSA key pair, give a name (usually the FQDN of the server that will present this certificate), configure if certificates that are authenticated by the trustpoint must also be checked in the LCR... etc.
3. then we can create CSR using the crypto ca enroll command. Now, we take this REA and provide it to Entrust. If this is done via the SCEP protocol you would have already done the next step of the authentication of the trustpoint.
4. When you receive a certificate from a third party, such as Entrust, they should also provide the certificate chain that allows the authentication of the certificate that they have signed all the way upward at the root (self-signed certificate server, the certificate must already be approved by most of the systems of operation/web-browsers). We want to install the string in the ASA because the ASA does not trust any certificate by default, it has an empty certificate store.
5. on the SAA, we now install the string provided by Entrust. Usually your identification certificate will be signed by an intermediate CA, just like the certificate of supportforums.cisco.com. Trustpoint ASA system for a CA (root or intermediate) and an ID (identity) by trustpoint. So we will probably have at least a trustpoint more.
Crypto ca trustpoint Entrust_ROOT
Terminal registration
output
authenticate the crypto ca trustpoint Entrust_ROOT
Don't forget to use trustpoint names who will lead them to you and your organization. Create a trustpoint for each of the CA certificates except for the signer of the certificate direct to your ID. Authenticate the signer directly in the trustpoint even where you install your certificate ID.
the import of crypto ca trustpoint ID certificate.
You should now have a fully usable authenticated certificate. PKCS12 import require a certificate to decrypt the private key that is stored in a PKCS12. But if you generate your CSR on the same device that when you install the certificate, then it would not need to export PKCS12 and a password.
---
A small side is not on the signature, a signature of certificate (fingerprint), also known as the name of a digital signature is a hash of the certificate encrypted with the signer's private key. As we know, whatever it is encrypted with a key only can be decrypted by the public key... all those who approves the signer's public key. So when you receive the certificate, and you already trust the signer, then 1) to decrypt the signature and 2) check that your certificate hash table corresponds to the decrypted hash... If the decrypted hash does not match then you do not trust the certificate.
For example, you can watch the certificate for supportforums.cisco.com,
The topic is: CN = supportforums.cisco.com
The subject of sender (signatory) is CN = Akamai subordinate CA 3
Akamai subordinate CA 3 is an intermediate certification authority. It is not self-signed
CN = Akamai subordinate CA 3 issuer is CN = GTE CyberTrust Global Root
CN = GTE CyberTrust Global Root is a certificate root (Self signed).
We would like to install this entire chain in the ASA so that we can provide this certificate and chain to any device and safely as long as this device trusts CN = GTE CyberTrust Global Root, then it should be able to verify the signatures of the intermediary and, finally, our certificate of identity of us trust.
---
Looking for another post to do a quick discussion about how the certificate is used in ISAKMP and IPSec.
Kind regards
Craig -
If my Time Capsule is connected by ethernet to my Mac, Time Machine uses this connection or the wireless connection?
It depends on the order of connection of your Mac. If your Mac has been defined first connect using Ethernet if an Ethernet connection is present, then the Mac will save over Ethernet, even if the WiFi is enabled on the Mac.
However, if your Mac has WiFi to connect first and WiFi is on... then the Mac connects using WiFi, even if an Ethernet connection exists.
To see the binding command or service so that your Mac is using...
Open the preferences system (gear on the dock icon)
Open network
Click on the gear at the bottom of the list of connection icon
Click the Set Service command
If you want to make sure that your Mac will always connect to Ethernet first, even if WiFi is turned on... then you want to make sure that Ethernet appears at the top of the service order. If this isn't the case, drag it to the top. Click OK, and then click apply at the bottom right of the window.
Another simple method to ensure that the backups will be produce by Ethernet is simply disable WiFi on Mac and let up to that you unplug the Ethernet cable, date at which you would be back on WiFi
-
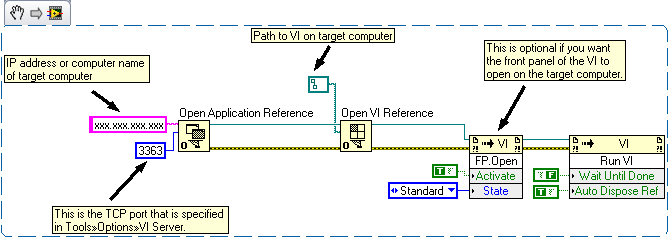
Cannot run VI on the Remote Machine using VI Server
Hello!
I'm trying to run a VI on a remote machine using VI server, but not luck. I used the 'remote execution VI' off the coast of LV inter II. I have check and follow up of the VI server configuration. I also tried to turn firewall on the PC but still nothing. Can't think of anything whatsoever that judgment of the VI to run on the remote PC. Any help will be appreciated. Thank you!
Hi KowdTek,
You do something like that?
Thanks for choosing National instruments.
Aaron Peña
National Instruments
Technical sales engineer
-
Problems with ImageAssist on the machines using SSDS m2 (NOT is)
Hello guys,.
first of all, I must admit, I am facing ImageAssist the first time, so maybe I m ask stupid or boring. I tried the search within this Forum, but didn t get results...
Okay, so here´s I want to do... our new generation of material (E7270, E5570, OptiPlex7040 far, precision 7710) must be distributed to our subsidiaries around the world. Sometimes they must implement a customer, so I want to create a Sysprep Image BASE + APPS, which I can send to these guys here.
Here´s so what I've done (problem follows when restoring my Image)
for example allows to take the E5570, 8 GB of RAM, 256 SED m.2SSD. I installed Win7x64 Enterprise with a Microsoft ISO in a virtual machine using VMWare Workstation 11. My VM config: 4 GB of RAM, 60 GB HD, network in bridged Mode, turn off sound and VM printer and here my first question:
Inside VM:BIOS or EFI Mode and drive hard ACHI or SATA Raid or SCSI mode? OK, I m prepared and tried all the...
so after installing win7 and .net 4.5.2 (VMWare Tools also, for the use of slides &) and 2 Reg settings with regard to our environment (MaxTokenSize = 65535 and EnableLUA = 0) I created my BASE Image/Snapshot.
After you add a few packages of software, I created my BASE + APPS (always with VMWare Tools).
Next step, uninstall VMWare Tools... restart, after this judgment. now boot into DELL's PE and I created our MaintenanceImage to a network drive. So far all is working well, so I used the installation without assistance-creator tool and define our values (name & Company, selectable language, workgroup, computer name must be completed by the regional IT guy, and I checked to copy the profile to the default user profile... that s he)
Validation tool crossed without moaning, capturing also...
I sliced two of the Image (about 10 GB) to some 2 GB and copied on our USB key for testing purposes...
Stick plugged USBPort E5570, restored, added DELL drivers CAB files and after restoration, the E5570 started Win7x64 for the first time... everything worked fine, etcpp... devices to about 90 percent of the first boot, I get the message: "Windows cannot configure one or more system components. TI install Windows, reboot, and re-install Windows.
Hope someone could snap this suspicion to my face :D
I also tried a BIOS/MBR Installation with the 7710 of precision using a standard 2.5 "SSD... I didn t get an error or a problem with this one... restroing & syspreping went well
Waiting for lots of helpful tips to fix this :)))
Best wishes & greetings from Germany
CHRIS
Hello Tyler,
Problem solved, everything works like a charm...
Thx for your help...
Got the wrong information of the German support. I tried some things over the weekend, and now it works.
Kind regards...
-
Client certificate authentication and proxy HTTPS WSA
Hello
on a clients site, we have a virtual Proxy WSA with WCCP running behind a firewall of ASA. Only we are facing a problem: the customer has a site that authenticates the client through the certificate. It does not work. If I dasable the transparent proxy for this host, everything works fine.
I solved it now bypassing the proxy server for the spicific site. Is there another solution to allow clients to authenticate using certificates to a Web site?
Hello
Does it means that websites (some sites) request for client certificate to authenticate during the SSL negotiation?
If this is true, can you check your option since default CLI interface HTTPS when HTTPS servers request certificate of the client during the handshake, WSA will respond with unavailable certificate and the handshake will normally be breaks.
To check this:
1. log in to the CLI
2. control of type advancedproxyconfig
3. type HTTPS
4. keep pressing enter to accept the value by default until you reach "measures to be taken when the HTTPS servers request certificate of the client during the handshake:" and change it to "get through the operation.5. keep pressing enter until the initial scope guest
6. type commit to save the change. -
http using aaa authentication when Ganymede server is down
I installed AAA using Ganymede and everything works well except for authentication http through a browser or a network Assistant when the RADIUS server is down. For console and telnet connections, the default authentication line when Ganymede is out of service.
AAA new-model
AAA authentication login default group Ganymede + line
AAA authorization exec default group Ganymede + authenticated if
AAA accounting update newinfo
AAA accounting exec default start-stop Ganymede group.
only AAA 0 default stop accounting controls group Ganymede +.
only AAA 1 default stop accounting controls group Ganymede +.
accounting AAA commands default 15 stop only Ganymede group.
!
aaa IP http authentication
!
radius-server host 10.161.161.20
111111 radius-server key
It must be something with the fact that on http or ANC, it connects to the router at level 15, but I have played with all sorts of orders of different authorization and cannot operate.
Paul
What you want to do for authentication if the RADIUS server is down? For telnet and console access you can use the line as a backup method because it is possible to configure a password for the line on the console and vty ports. Which type of backup method you want for HTTP? The one that seems most logical to me would be to a local authentication in order to cover the situation where the server is down.
To use local authentication, you must do the following:
-create a definition of the local user (maybe more if you need extended security).
-specify a special method for authentication of the aaa.
-specify that http, using the special method.
The configuration might look like this:
password user tech1 tech1
AAA authentication login http_auth group Ganymede + local
IP http authentication aaa - authentication of the connection http_auth
Or you can decide to use the secret to activate (or password that is configured in office). The config might look like this:
AAA authentication login http_auth group Ganymede + activate
IP http authentication aaa - authentication of the connection http_auth
If you want a different backup method, let us know what it is and we'll see how it could be implemented.
HTH
Rick
Maybe you are looking for
-
code 80080005 Windows Update encountered an unknown error
I get this error when trying to run Windows Update.code 80080005 Windows Update encountered an unknown error. Rerun is ineffective. Vista 64-bit Service Pack 1 operating system
-
How can I take two simultaneous images of one of the NI PCIe-1430 Board? Is this possible?
I have two cameras (JAI - HP - M4 + CL) and I would like to take images captured at the same time two of them by a Council NI PCIe-1430, using an external trigger. Is this possible? Is there another type of solution for my problem? What I need is jus
-
For about two weeks screen installation 18 Windows updates at the stop.
For about two weeks when I shut down Windows 7, I get the message that Windows installs updates 18; do not to stop the computer. The screen shows that each update is installed and the computer then goes to the closure program. Installation time is
-
After istalling vista not showing no hardware networking
After installin vista windows is unable to connect to the net network and sharing Center showing no hardware detected a networking.
-
I was workiing online, and I started to have problems with ie10, freezes, stop down, and then the entire HDD crashed, any program, file system went. System Restore used to regain control of my computer, but now all my media files, music, photos, ever