Newbie configuration VPN 5505 for client Win7
I have a client who has an installed 5505. They want VPN with their laptop Win7 but they don't want to shell out $1000 for customer VPN Cisco 10pcs.
I have correctly set up the VPN without customer and through a browser, they can get to their files, but they would map network drives is just as if they were in the office.
I tried to configure the IP Sec on 5505 and then using the built-in VPN Win7 network connection, but no go.
I do also everything through the ASDM, but I know that certain things cannot be done. I prefer to use the ASDM!
Anyone else get this set up? 99% of what I see here is how to connect the 5505 for VPN site to site.
Thank you!
Hello
To my knowledge all ASA5505 should have the ability to have 2 VPN SSL connections with the Base license. To my knowledge, this also includes using the AnyConnect SSL VPN Client (which replaces the old VPN IPsec Client software) and the VPN without customer via the Web browser.
The AnyConnect VPN Client should be available on the Flash of the ASA and is set when you configure the Client AnyConnect SSL VPN for the first time.
On the ASDM, you should be able to configure the client AnyConnect SSL VPN with the "Wizard" as any other type of VPN configuration.
The AnyConnect VPN Client is a better choice to use the old client IPsec, especially when it comes to new operating systems. The AnyConnect VPN Client can be installed in the ASA at the users computer when he or she first attempts to connect to the ASA via Web browser and connects with his credentials.
-Jouni
Tags: Cisco Security
Similar Questions
-
I am new to the use of Cisco devices and I need a little help with some configurations on an ASA5505 with 8.4.
I want to connect 2 ASA5505 with a site-to-site.
Site 1
is where I want to connect to. Site 1 we have access to 192.168.40.x and 192.168.42.x networks. This ip is: 192.168.40.254
Site 2
I want to connect to site 1 and see the 40.x and 42.x networks. I am able to connect to the network 40.x and can see devices on it, but I can't go to the 42.x network. This ip device is: 192.168.50.1
The sites are not in the same place, just in case someone asks about it.
Hello
Seems to me that you do not have good rules configured on Site1 and Site2 ASA on the VPN
You must add the following configurations
Site1
access extensive list ip 192.168.42.0 inside_nat0_outbound allow 255.255.255.0 192.168.50.0 255.255.255.0
access extensive list ip 192.168.42.0 outside_cryptomap allow 255.255.255.0 192.168.50.0
-It would add both traffic between networks for VPN configurations and unnated traffic through to the remote end
Site2
outside_cryptomap to access extended list ip 192.168.50.0 allow 255.255.255.0 192.168.42.0 255.255.255.0
This would add the traffic between networks for VPN configurations
Seems that you already have the NAT0 configurations in place for networks, but not above the line for the VPN itself.
Please rate if it helped
-
ASA5505: Configure the ASA for IPSec and SSL VPN?
Hello-
I currently have my 5505 for SSL AnyConnect VPN connections Setup. Is it possible to set up also the 5505 for IPSec VPN connections?
So, basically my ASA will be able to perform SSL and IPSec VPN tunnels, at the same time.
Thank you!
Kim,
Yes, you can configure your ASA to support the AnyConnect VPN IPSec connections and at the same time. In short, for the configuration of IPSec, you should configure at least a strategy ISAKMP, a set of IPSEC, encryption, tunnel group card processing and associated group policy.
Matt
-
Please give index on configuring vpn site to site on 881 to ASA 5505 cisco router
Earlier my boss asked me to prepare to implement the VPN site-to site on router Cisco 881 Integrated Services to ASA 5505 router, which is now running on the side of HQ. Someone please give me a hint. I am now learning the pdf file from Cisco that mention how to configure VPN site to site between 1812 Cisco IOS router and router of the ASA 5505 using ASDM V6.1 and SDM V2.5. Cannot find the book for the Cisco 881 device.
Someone please please suggest me something as soon as POSSIBLE.
Thank you
CLI version:
ASDM and SDM Version:
-
How to configure VPN 3000 Concentrator for remote access
I have inherited a VPN concentrator and want to configure it to provide remote access to my internal laboratory network when I'm traveling. Private interface is configured as 192.168.1.240/24. Public interface is configured as one of my public IP addresses. I have a public IP pool on the back side of a cable modem Roadrunner. I created a pool of addresses for clients such as 192.168.1.200 by 192.168.1.205. I created all group configurations, group and user base.
In the IP Routing tab, I see a default route pointing to my IP address of public gateway - the IP address of my box of roadrunner cable modem gateway.
Since my VPN client, I am able to connect to the VPN concentrator. I get an address from the pool and check the details of the tunnel under the statistics section shows IP address correct pool for the customer and the correct public IP address of my VPN reorga
Jeff,
According to statistics, it seems that the client sends traffic to the hub, but his answer not get back.
We need check the hub settings itself.
I need check the hub settings and that it is a GUI based device so I can't even ask to see the technology and the only option available is to WebEx.
You're ok with webex, pls lemme session comfortable time id and e-mail to send the invitation, it takes no more time and we will carry it out
Thank you
Ankur
-
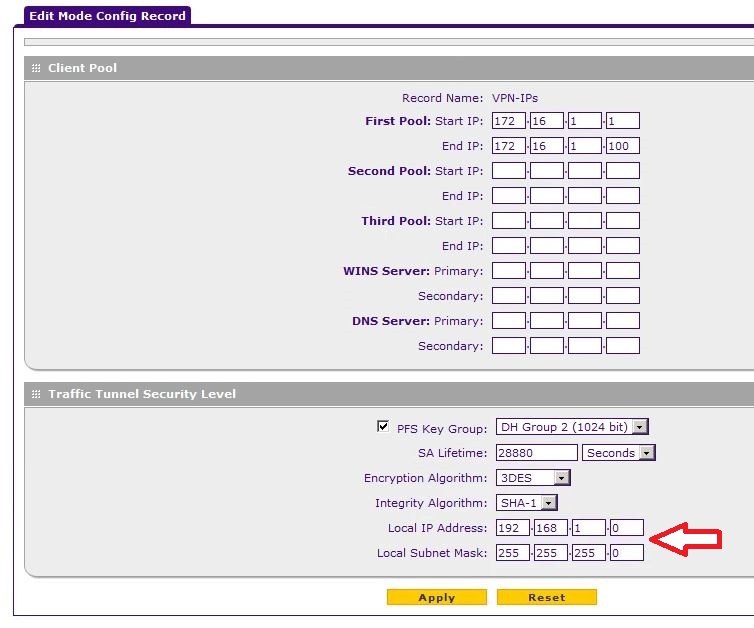
SRX5308 IPsec Config Mode - [IKE] ERROR: no configuration is found for...
I have a real simple setup for Client-to-gateway VPN installation. Base tunnels seem to work fine, but when I try to install
a policy of Mode Config I get an error in the connection and cannot ping resources on the local VPN network.
The local IP address at the end of check-in Mode Config is 192.168.1.0. The manual says to leave the field empty and it will default to the address of the gateway, which is 192.168.1.1. If I leave the field blank this wrong address gets automatically enrolled and if I try to manually enter the right one I get an error saying it's an invaild address?
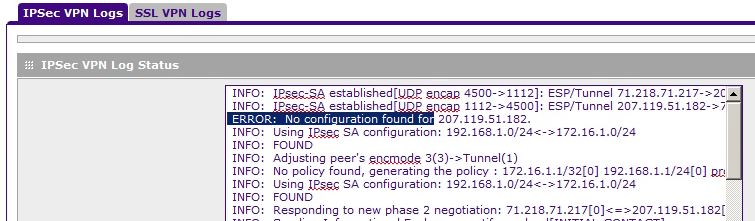
Then when I connect, I get the following error:
I think that is the question. How to work around this problem or do it properly? The manual is not any help and I googled my old brian dead.
Thanks for any idea that you can give me!
CC
Thanks for the reply okadis and thanks for the link to this site, it is very useful!
I was able to find a solution. Turns out that the works of very good firewall configuration. All I had to do was use the remote configuration of the CLIENT as the LAN address 192.168.1.0, and then everything worked.
Now, for me, it's 2 "bugs" in the SRX5308 of Mode Config record:
1 192.168.1.0 is not the address of the Local network subnet, it is 192.168.1.1; The manual says if left blank by default subnet LAN, which it isn't, it's default 192.168.1.0
2. it won't let you enter ANY ip address here. It must be left blank.
Maybe I'm missing something here, but it works perfectly after using what is there in the end customer.
Should have been simple. Well...
CC
-
WRT1900AC cannot configure VPN
I CURRENTLY HAVE 2 WIRELESS ROUTERS AN ASUS RT-N56U WHICH WAS EASY to set UP WITH ExpressVPN. COMING TO EXPAND MY NETWORK & IMPROVE USING A LINKSIS WRT1900AC. UNABLE TO SET TO THE TOP OF THE SAME. BOTH ROUTERS ARE HARD CABLES TO THE ISP ROUTER & WILL BE POSITIONED AT DIFFERENT AREAS OF THE HOUSE FOR COVER. I HAVE THE ExpressVPN PAST & DETAILS USER password, LIST OF GLOBAL SERVER ADDRESSES & THEIR ADDRESSES IP CONCERNED.
CAN SOMEONE HELP ME IN THE BASIC CONFIGURATION. I AM NOT AN IT WIZZ BUT YOU CAN FOLLOW THE INSTRUCTIONS ESPECIALLY WITH SCREENSHOTS SUPPORTED. HELP IS GREATLY APPRECIATED.
OK gents,
Answers very well. It gives me a lot to think so thank you very much.
Temporarily, I currently have 2 routers connected switch wired to asus to linksys with the linksys being connected on the local network of the asus through the cable network. The asus is configured as L2TP that allows the details of user, password & VPN server. Use them in this way gives me the IP addresses associated with the address of the server used. This IP address is provided if connected to a router. Probably not the fastest or the best way but will suffice until I have work on your tech talk. I have an ASUS RT - 68U (which has the VPN Client) available to replace the Asus RT - 56U to come. I can use the 56U on the edge of the property similar to the linksys. Trial & error prototyping will I hope make me it in the absence of knowledge or understanding.
Can someone advise on potential pitfalls with the current configuration or plans for the future?
Thanks again.
-
LT2P configuration vpn cisco asa with the internet machine windows/mac issue
Dear all,
I have properly configured configuration vpn L2TP on asa 5510 with 8.0 (4) version of IOS.
My internet does not work when I connect using the vpn. Even if I give power of attorney or dns or I remove the proxy
It does not work. only the resources behind the firewall, I can access. I use the extended access list
I tried also with the standard access list.
Please please suggest what error might be.
Thank you
JV
Split for L2TP over IPSec tunnel tunnel is not configured on the head end (ASA), it must be configured on the client itself, in accordance with the following Microsoft article:
-
Router WAN double with SSL VPN inaccessible for customers
I have a configured in a Dual WAN setup Cisco 888. There is an ADSL link connected to the VLAN 100 and a SDSL link associated with the Dialer0. The customer wishes to use the ADSL link to the normal navigation and external SSL VPN users to complete on the SDSL connection. I tried to configure the link failover for the ADSL SDSL.
What works:
-Access to the Internet for clients the
What does not work:
-The ADSL SDSL connection failover.
-Access SSL VPN for customers. Surf to the external IP address will cause only a page by default HTTP. Specification webvpn.html results in a 404 not found error.
Here is my configuration:
version 15.0
no service button
horodateurs service debug datetime msec
Log service timestamps datetime msec
no password encryption service
!
host name x
!
boot-start-marker
boot-end-marker
!
logging buffered 51200 warnings
enable secret 5 x
!
AAA new-model
!
!
AAA authentication login local sslvpn
!
!
!
!
!
AAA - the id of the joint session
iomem 10 memory size
!
Crypto pki trustpoint TP-self-signed-3964912732
enrollment selfsigned
name of the object cn = IOS - Self - signed - certificate - 3964912732
revocation checking no
rsakeypair TP-self-signed-3964912732
!
!
TP-self-signed-3964912732 crypto pki certificate chain
self-signed certificate 03
x
quit smoking
IP source-route
!
!
IP dhcp excluded-address 192.168.10.254
DHCP excluded-address IP 192.168.10.10 192.168.10.20
!
DHCP IP CCP-pool
import all
network 192.168.10.0 255.255.255.0
default router 192.168.10.254
DNS-server 213.75.63.36 213.75.63.70
Rental 2 0
!
!
IP cef
no ip domain search
property intellectual name x
No ipv6 cef
!
!
udi pid CISCO888-K9 sn x license
!
!
username secret privilege 15 ciscoadmin 5 x
username password vpnuser 0 x
!
!
LAN controller 0
atm mode
Annex symmetrical shdsl DSL-mode B
!
interface Loopback1
Gateway SSL dhcp pool address description
IP 192.168.250.1 255.255.255.0
!
interface Loopback2
Description address IP VPN SSL
IP 10.10.10.1 255.255.255.0
route PBR_SSL card intellectual property policy
!
interface BRI0
no ip address
encapsulation hdlc
Shutdown
Multidrop ISDN endpoint
!
ATM0 interface
no ip address
load-interval 30
No atm ilmi-keepalive
PVC KPN 2/32
aal5mux encapsulation ppp Dialer
Dialer pool-member 1
!
!
interface FastEthernet0
switchport access vlan 100
!
interface FastEthernet1
!
interface FastEthernet2
!
interface FastEthernet3
!
interface Vlan1
LAN description
IP address 192.168.10.254 255.255.255.0
IP nat inside
IP virtual-reassembly
IP tcp adjust-mss 1300
!
interface Vlan100
Description KPN ADSL 20/1
DHCP IP address
NAT outside IP
IP virtual-reassembly
!
interface Dialer0
Description KPN SDSL 2/2
the negotiated IP address
IP access-group INTERNET_ACL in
NAT outside IP
IP virtual-reassembly
encapsulation ppp
Dialer pool 1
Dialer-Group 1
PPP pap sent-username password 0 x x
No cdp enable
!
IP local pool sslvpnpool 192.168.250.2 192.168.250.100
IP forward-Protocol ND
IP http server
local IP http authentication
IP http secure server
IP http timeout policy slowed down 60 life 86400 request 10000
!
pool nat SSLVPN SDSL 10.10.10.1 IP 10.10.10.1 netmask 255.255.255.0
IP nat inside source static tcp 10.10.10.1 443 interface Dialer0 443
IP nat inside source static tcp 10.10.10.1 80 Dialer0 80 interface
IP nat inside source overload map route NAT_ADSL Vlan100 interface
IP nat inside source overload map route NAT_SDSL pool SSLVPN SDSL
IP route 0.0.0.0 0.0.0.0 x.x.x.x
IP route 0.0.0.0 0.0.0.0 Dialer0 10
!
INTERNET_ACL extended IP access list
Note: used with CBAC
allow all all unreachable icmp
allow icmp all a package-too-big
allow icmp all once exceed
allow any host 92.64.32.169 eq 443 tcp www
deny ip any any newspaper
Extended access LAN IP-list
permit ip 192.168.10.0 0.0.0.255 any
refuse an entire ip
!
Dialer-list 1 ip protocol allow
not run cdp
!
!
!
!
NAT_SDSL allowed 10 route map
match the LAN ip address
match interface Dialer0
!
NAT_ADSL allowed 10 route map
match the LAN ip address
match interface Vlan100
!
PBR_SSL allowed 10 route map
set interface Dialer0
!
!
control plan
!
!
Line con 0
no activation of the modem
line to 0
line vty 0 4
privilege level 15
transport input telnet ssh
!
max-task-time 5000 Planner
!
WebVPN MyGateway gateway
hostname d0c
IP address 10.10.10.1 port 443
redirect http port 80
SSL trustpoint TP-self-signed-3964912732
development
!
WebVPN install svc flash:/webvpn/anyconnect-dart-win-2.5.0217-k9.pkg sequence 1
!
WebVPN install svc flash:/webvpn/anyconnect-macosx-i386-2.5.0217-k9.pkg sequence 2
!
WebVPN install svc flash:/webvpn/anyconnect-macosx-powerpc-2.5.0217-k9.pkg sequence 3
!
WebVPN context SecureMeContext
title "SSL VPN Service"
secondary-color #C0C0C0
title-color #808080
SSL authentication check all
!
login message "VPN".
!
Group Policy MyDefaultPolicy
functions compatible svc
SVC-pool of addresses "sslvpnpool."
SVC Dungeon-client-installed
Group Policy - by default-MyDefaultPolicy
AAA authentication list sslvpn
Gateway MyGateway
development
!
end
Any suggestions on where to look?
Hello
It works for me. When the client tries to resolve the fqdn for the domain specified in "svc split dns.." he will contact the DNS server assigned through the Tunnel. For all other questions, he contacts the DNS outside the Tunnel.
You can run a capture of packets on the physical interface on the Client to see the query DNS leaving?
Also in some routers, DNS is designated as the router itself (who is usually address 192.168.X.X), if you want to make sure that assigned DNS server doesn't not part of the Split Tunnel.
Naman
-
Issue of Cisco ASA 5505 Anyconnect Client NAT'ing
Hello
We have a split_tunnel RA Vpn configuration in a branch that works very well in all areas except the destinged of traffic for a specific website using https. This provider does not allow HTTPS connections to bring some outside IP addresses.
Essentially, this should work like this:
RAVPN_client (10.4.4.0/27)--> https request to the (208.x.x.x) vendor_ip---> ASA55XX--> NAT_to_outside_ip--> to the vendor_ip (208.x.x.x) https request
I need to understand how you would approach from ONLY this https traffic specific to the RA VPN without having to change the installer otherwise.
Internal hosts (aka behind the ASA physically) have not any question at this site, as would his nat ip address outside that we expect.
Here is what we use for the NAT Exemption it list 10.2.2.x, 192.168.100.x, and 172.23.2.x are other remote sites we have. The 10.4.4.0/27 RA VPN users don't have no problems connecting to them, regardless of the Protocol:
Note to inside_nat0_outbound access-list of things that should not be Nat would
access extensive list ip 10.12.1.0 inside_nat0_outbound allow 255.255.255.0 10.2.2.0 255.255.255.0
access extensive list ip 10.12.1.0 inside_nat0_outbound allow 255.255.255.0 192.168.100.0 255.255.255.0
access extensive list ip 10.12.1.0 inside_nat0_outbound allow 255.255.255.0 172.23.2.0 255.255.255.0
access extensive list ip 10.12.1.0 inside_nat0_outbound allow 255.255.255.0 10.4.4.0 255.255.255.224
access extensive list ip 10.4.4.0 inside_nat0_outbound allow 255.255.255.224 192.168.100.0 255.255.255.0
access extensive list ip 10.4.4.0 inside_nat0_outbound allow 255.255.255.224 10.2.2.0 255.255.255.0
access extensive list ip 10.4.4.0 inside_nat0_outbound allow 255.255.255.224 172.23.2.0 255.255.255.192
Here is the list of interesting traffic that we push to the customers through the tunnel of the VPN connection.
VPN_splitunnel to access extended list ip 192.168.100.0 allow 255.255.255.0 any
VPN_splitunnel of access list scope 10.2.2.0 ip allow 255.255.255.0 any
Access extensive list ip 10.12.1.0 VPN_splitunnel allow 255.255.255.0 any
Access extensive list ip 172.23.2.0 VPN_splitunnel allow 255.255.255.192 all
Access extensive list ip 10.4.4.0 VPN_splitunnel allow 255.255.255.224 all
VPN_splitunnel list extended access permit ip host 208.x.x.x any newspaper<- this="" is="" the="" vendors="" external="" ip="" address="" (obfuscated="" for="" security="" but="" you="" get="" the="">
Here's the rest of the nat configuration:
NAT-control
Overall 101 (external) interface
NAT (inside) 0-list of access inside_nat0_outbound
NAT (inside) 101 0.0.0.0 0.0.0.0
Configuring VPN RA:
IP mask 255.255.255.224 local pool VPNPool 10.4.4.5 - 10.4.4.30
WebVPN
allow outside
AnyConnect essentials
SVC disk0:/anyconnect-dart-win-2.5.0217-k9.pkg 1 image
SVC disk0:/anyconnect-macosx-i386-2.5.2001-k9.pkg.zip 2 image
enable SVC
tunnel-group-list activate
internal RAVPN group policy
RAVPN group policy attributes
value no unauthorized access to banner
value of banner that all connections and controls are saved
banner of value this system is the property of MYCOMPANY
banner value disconnect IMMEDIATELY if you are not an authorized user.
value of server WINS 10.12.1.11 10.2.2.11
value of 10.12.1.11 DNS server 10.2.2.11
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list VPN_splitunnel
type tunnel-group RAVPN remote access
attributes global-tunnel-group RAVPN
address pool VPNPool
authentication-server-group NHCGRPAD
Group Policy - by default-RAVPN
tunnel-group RAVPN webvpn-attributes
enable RAVPN group-alias
Can someone ' a Please direct me as to what I'm doing wrong? I was assuming that since I don't have Ip 208.x.x.x address in the list of inside_nat0_outbound that it would be NAT had, but appears not to be the case (out of packet - trace below)
Packet-trace entry outside tcp 10.4.4.6 34567 208.x.x.x detailed https
*****************************************************************************
Phase: 1
Type:-ROUTE SEARCH
Subtype: entry
Result: ALLOW
Config:
Additional information:
in 0.0.0.0 0.0.0.0 outdoors
Phase: 2
Type: ACCESS-LIST
Subtype: Journal
Result: ALLOW
Config:
Access-group outside_access_in in interface outside
outside_access_in list extended access permitted ip VPN_ips 255.255.255.224 host 208.x.x.x Journal
Additional information:
Direct flow from returns search rule:
ID = 0xd7bd3b20, priority = 12, area = allowed, deny = false
Hits = 2, user_data is 0xd613bf80, cs_id = 0 x 0, flags = 0 x 0 = 0 protocol
SRC ip = VPN_ips, mask is 255.255.255.224, port = 0
IP = 208.x.x.x DST, mask = 255.255.255.255, port = 0, dscp = 0 x 0
Phase: 3
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional information:
Direct flow from returns search rule:
ID = 0xd7df8fa0, priority = 0, sector = inspect-ip-options, deny = true
hits = 2256686, user_data = 0 x 0, cs_id = 0 x 0, reverse, flags = 0 x 0 = 0 protocol
SRC ip = 0.0.0.0 mask 0.0.0.0, port = 0 =
DST ip = 0.0.0.0 mask = 0.0.0.0, port = 0, dscp = 0 x 0
Phase: 4
Type: VPN
Subtype: ipsec-tunnel-flow
Result: ALLOW
Config:
Additional information:
Direct flow from returns search rule:
ID = 0xd87c8fc8, priority = 12, area = ipsec-tunnel-flow, deny = true
hits = 550, user_data = 0 x 0, cs_id = 0 x 0, flags = 0 x 0 = 0 protocol
SRC ip = 0.0.0.0 mask 0.0.0.0, port = 0 =
DST ip = 0.0.0.0 mask = 0.0.0.0, port = 0, dscp = 0 x 0
Phase: 5
Type: HOST-LIMIT
Subtype:
Result: ALLOW
Config:
Additional information:
Direct flow from returns search rule:
ID = 0xd7dfbd28, priority = 0, domain = host-limit, deny = false
hits = 1194, user_data = 0 x 0, cs_id = 0 x 0, flags = 0 x 0 = 0 protocol
SRC ip = 0.0.0.0 mask 0.0.0.0, port = 0 =
DST ip = 0.0.0.0 mask = 0.0.0.0, port = 0, dscp = 0 x 0
Phase: 6
Type: IP-OPTIONS
Subtype:
Result: ALLOW
Config:
Additional information:
Reverse flow from returns search rule:
ID = 0xd7df8fa0, priority = 0, sector = inspect-ip-options, deny = true
hits = 2256688, user_data = 0 x 0, cs_id = 0 x 0, reverse, flags = 0 x 0 = 0 protocol
SRC ip = 0.0.0.0 mask 0.0.0.0, port = 0 =
DST ip = 0.0.0.0 mask = 0.0.0.0, port = 0, dscp = 0 x 0
Phase: 7
Type: CREATING STREAMS
Subtype:
Result: ALLOW
Config:
Additional information:
New workflow created with the 2380213 id, package sent to the next module
Information module for forward flow...
snp_fp_tracer_drop
snp_fp_inspect_ip_options
snp_fp_tcp_normalizer
snp_fp_translate
snp_fp_adjacency
snp_fp_fragment
snp_ifc_stat
Information for reverse flow...
snp_fp_tracer_drop
snp_fp_inspect_ip_options
snp_fp_translate
snp_fp_tcp_normalizer
snp_fp_adjacency
snp_fp_fragment
snp_ifc_stat
Result:
input interface: outdoors
entry status: to the top
entry-line-status: to the top
output interface: outside
the status of the output: to the top
output-line-status: to the top
Action: allow
*****************************************************************************
Thank you
Jason
You are on the right track with you divided the tunnel configuration. You need to add is the pool of Client VPN to be coordinated to your external ip address, IE: same as your local users of the ASA when he tries to access the intellectual property of the provider (208.x.x.x), allowing more traffic in and out of the same interface for traffic of U-turn.
Here's what you need to set up:
permit same-security-traffic intra-interface
nat-to-vendor ip 10.4.4.0 access list permit 255.255.255.224 host 208.x.x.x
NAT (outside) 101-list of nat-to-vendor access
The foregoing will allow VPN pool to be coordinated to your ASA outside the ip address of the interface when accessing the seller (208.x.x.x).
1 small correction to your ACL split tunnel:
-The following line is incorrect and should be deleted in the tunnel of split ACL:
Access extensive list ip 10.4.4.0 VPN_splitunnel allow 255.255.255.224 all
(As 10.4.4.0/27 is your pool of Client VPN, you do not add these subnet to your list of split tunnel. List of Split tunnel are only the network that you are difficult to access and sent through your VPN tunnel).
Hope that helps.
-
Can what iCloud password I use to configure my e-mail client? I get an authentication error.
While trying to set up my email client (non-Apple) to receive and send an email to my iCloud account, I get an authentication error when using my AppleID password.
I tried to reset my AppleID password, but the password is always a failure when you try to configure my e-mail client. I even called Apple Support today where they told me that the iCloud email password should be in sync with the AppleID password since the iCloud email is simply an alias for it. After 25 minutes, they told me that I must use just the Apple Mail client instead.
I finally found the solution tonight when looking through the manage your site Apple ID. You must create a password App specific to your e-mail client:
- go to https://appleid.apple.com/account/home
- Sign in with your ID AppleID and password
- Once the page is loaded, click on the link 'Edit' in the Security section
- You should now see a section for App specific passwords
- Click the "generate Password... »
- Enter a name (I used my name to email client - Unibox)
- Click on create
Apple will generate a password you will use when you set up your email client. Use this new password instead of your AppleID password.
-
I am interested in establishing a VPN for my computer. I looked at some of the information to help Ms. I'm missing something in the way of understanding how do or end the connection.
You can configure VPN regardless of static or dynamic IP, both are possible. You can refer to:
-
How to configure the DDC for testing?
Hi all
I would like to implement Cisco Secure Desktop in our WebVPN configuration, but I need a way to set up and test without making our existing of WebVPN users.
It seems to me that if I create a Windows with a criterion that * only * my machine test matches, all other users will fail. If I activate the features "when the location corresponding fails", current users won't see a difference.
Is this correct? Furthermore, with this configuration, VPN tent making out the CSD software when users connect?
All advice is appreciated.
Thank you
-Steve
Yes, existing users will not see a difference "when the corresponding location fails. This option "what corresponding location fails" helps Windows customers use VPN to surf the web as a minimum connection option, if the client computer does not match any of the criteria of the configured locations.
-
SRP526W to transmit or provide VPN access to clients
Hello
We have a SRP526W here, which replaced a cheap, simple router. Now, we would like to set up VPN access for outside clients again. So far, this was done by sending PPTP (TCP 1723 and GRE) for the Routing and Windows 2000 RAS server within the network.
According to this post SRP521W, and therefore I guess so the SRP526W, are not able to pass the GRE: https://supportforums.cisco.com/thread/2093204
Is it possible to provide external client VPN access with this router? Perhaps with L2TP (but then you should transmit ESP) or IPSec (ESP and AH as far as I know)?
If there is no solution, we need to replace this device again once with a cheap, simple, router that is able to convey the Grateful - as you can imagine, we would like to save this shame Cisco.
Kind regards
Dominik
Hello Dominik,
The SRP520 only supports IPSec site-to-site at this time.
Advancements are made, please check in the new year.
Andy
-
How to configure a Windows NTP Client?
I work with Windows 7. And I need to configure the Windows NTP Client for online business.
I work with Windows 7. And I need to configure Windows NTP Client for online business.
NTP Network Time Protocol =?
Maybe you are looking for
-
Is it possible to have the number of words together to always display?
I use the statistics feature a lot of Pages and I think in a previous version, it was still visible. Now whenever I go to or create a different document that I have to manually switch to the view / display Word Count - go further down in the document
-
Hello I apppreciate want to do the thresholding of an image without using the functions of the IMAQ. How do we? Can someone explain the procedures step by step for it or post an example? Thank you
-
"Error code 0x800106ba" when you try to run Windows Defender
Original title: the defender of my ordenator portably windows have an error 0x800106ba and stop the program. What should I do? The defender of my ordenator portably windows have an error 0x800106ba and stop the program. What should I do?
-
How can I fix the error message Winsock cmd "this operation requires an elevation"?
I'm having serious trouble with my machine does not get on the internet. I have already established that it is not the modem or the access provider. I did a restore sys in the last 72 hours (a day) and nothing has been fixed. I will note that Sunday
-
Vista Ultimate 64 runs fast on 4 GB of memory but slow as a turtle with 8 GB
Hi all! I recently bought 4 x 2 GB Kingston KVR 800 MHZ DDR2 with a Western Digital Caviar Green 1 TB 64 MB Sata - 3 G to increase my gaming experience on my Windows vista 64 bit. My problem and the question is why windows takes so long to load (in