Newspapers of the ASA
I try to display the traffic logs. Can someone help me with the command?
Here are the steps to install syslog server.
First of all, you need to install syslog on a computer server software. You can
Download one of the popular kiwisyslog Server
http://www.kiwisyslog.com/software_downloads.htm . He is listed as Kiwi
Syslog Daemon and the latest version is 8.2.8. You can download the standard edition, which works as
a program.
Once the syslog server is installed, then you should connect to the ASA in
the terminal configuration mode and enter the following commands.
Logging host [in_if_name] ip_address
(example: host inside 1.2.3.4 record)
We assume syslog server is installed on the computer with 1.2.3.4 IP address in the
inside the network.)
timestamp of the record
exploitation forest siphon 4
opening of session
These commands allow the ASA begin sending messages syslog on the syslog server.
For more information about the logging commands, you can see at this URL:
http://www.Cisco.com/en/us/products/sw/secursw/ps2120/products_command_refer
ence_chapter09186a008010578b.html #1028090
----------------------------------------------------------------------------------
Levels of trap
. 0-emergency-system unusable messages
. 1-alerts-take immediate action
2 State - criticism-criticism
. 3 errors error message
. 4 warnings-Warning message
. 5 notifications-Normal but significant condition
message information. 6-Information
. 7-debug-Debug messages and orders of FTP and WWW URL log
Note the useful messages.
Kind regards
Sushil
Tags: Cisco Security
Similar Questions
-
Unable to connect to the ASA vpn Android client
secHello, I have problem with android client. So I've solved many problems and finally could get the PHASE 1 and PHASE 1 COMPLETED messages in newspapers :). In any case, I have a problem different, even if the client of the phase 1 and 2 completed failed to connect again. Here are the logs:
| 21456 | *** | 500 | Built of UDP connection entrants for outdoor 600577524: * / 21456 (* / 21456) identity: * / 500 (* / 500)
| 27262 | *** | 4500 | Built of UDP connection entrants for outdoor 600577567: * / 27262 (* / 27262) identity: * / 4500 (* / 4500)
Group = ANDROID_PROF, IP = *, automatic NAT detection status: remote endpoint IS behind a NAT device this end is behind a NAT device
Group = ANDROID_PROF, IP = *, floating NAT - T of * port 21456 to * port 27262
Group = ANDROID_PROF, IP = *, PHASE 1 COMPLETED
Group = ANDROID_PROF, IP = *, IPSec initiator of the substitution of regeneration of the key time of 0 to 4608000 Kbs
IPSEC: Remote access out HIS (SPI = 0x0429CEA7) between * and * (user = ANDROID_PROF) was created.
Group = ANDROID_PROF, IP = *, the security negotiation is complete for user (Responder), Inbound SPI = 0xc95803fc outbound SPI = 0x0429cea7
IPSEC: Incoming remote access between HIS (SPI = 0xC95803FC) * and * (user = ANDROID_PROF) was created.
Group = ANDROID_PROF, IP = *, PHASE 2 COMPLETED (msgid = 9aab13ed)
| 27262 | *** | 1701 | Built of UDP connection entrants for outdoor 600577657: * / 27262 (* / 27262) identity: * / 1701 (* / 1701)
L2TP tunnel created, tunnel_id 24, remote_peer_ip is *, 1/ppp_virtual_interface_id, client_dynamic_ip is 0.0.0.0, user name is *.
Tunnel L2TP deleted, tunnel_id = 24, remote_peer_ip = *.
IPSEC: Remote access out HIS (SPI = 0x0429CEA7) between * and * (user = ANDROID_PROF) has been removed.
IPSEC: Incoming remote access between HIS (SPI = 0xC95803FC) * and * (user = ANDROID_PROF) has been removed.
Group = ANDROID_PROF, IP = *, Session is to be demolished. Reason: The user has requested
Group = ANDROID_PROF, user name =, IP = *, disconnected Session. Session type: IPsecOverNatT, duration: 0 h: 00 m: 07 s, xmt bytes: 1021, RRs bytes: 955, reason: the user has requestedAs you can see session was demolished immediately, said Android failure. The Android settings:
Name: ANDROID_PROFType: L2TP/IPsec Psk
The IPsec identifier: ANDROID_PROF
Pre-shared key IPsec: cisco
The ASA config:
attributes global-tunnel-group ANDROID_PROF
address IPSEC_RA_POOL pool
Group-LDAP LOCAL authentication server
LDAP authorization-server-group
NOACCESS by default-group-policy
IPSec-attributes tunnel-group ANDROID_PROF
IKEv1 pre-shared-key *.
tunnel-group ANDROID_PROF ppp-attributes
CHAP Authentication
ms-chap-v2 authenticationANDROID_PROF_GP group policy attributes
value of DNS server *.
VPN - 4 concurrent connections
Protocol-tunnel-VPN l2tp ipsec
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list ANDROID_PROF_USERS
Cisco.local value by default-field
the address value IPSEC_RA_POOL poolsHello
Your problem is with Android L2TP/IPsec client that connects to the AAS has been caused by: CSCug60492 (Android phone disconnected from l2tpoveripsec and reconnect asa hung)
It is Android actually issue, not a bug of the SAA. This resolution is based on Android.
I hope this helps.
Thank you
Vishnu
-
How to open the port 161 on the ASA and Cisco switches for monitoring of BB
Dear all,
I want to install BB to monitor snmptraps suffering of failure.
The newspaper shows BB cannot connect to all ports of the switch 161, and I even can't telnet to 161 XXX_17f for example.
My switches are Cisco C3550, C2950, etc. of the ASA.
Mon 7 Nov 15:43:03 2011 bbnet cannot connect to the server XXX_17f on port 161
Mon 7 Nov 15:43:03 2011 bbnet cannot connect to the server XXX_9f on port 161
Mon 7 Nov 15:43:03 2011 bbnet can't connect to XXX server on port 161
Thank you
Anson
no need to adjust anything in bb-hosts. If you have added setings in bb-hosts, delete them. Also remove associated in bbvar/logs log files. (otherwise, you'll have purple when you delete the SNMP, trap tags bb-hosts)
A column of trap will be that no show until the device sends a trap to BB.
-
No access to the interface of the ASA by behind the other is
Hello
I am faced with the issue of not being able to access the interface of "dmz" behind the interface 'internet '.
Here is a brief description of the topology:

List entry on the internet access "," allows for 1xx.xxx.172.1 traffic.
No nat is configured between these interfaces.
The routing is OK because hosts on the DMZ network are accessible from the Internet.
The software version is 9.1 (3).
Security level of the interfaces is the same.
Security-same interface inter traffic is allowed.
Here's what packet trace says:
tracer # package - entry internet udp 7x.xxx.224.140 30467 1xx.xxx.172.1 det 500
Phase: 1
Type:-ROUTE SEARCH
Subtype: entry
Result: ALLOW
Config:
Additional information:
identity of the 255.255.255.255 1xx.xxx.172.1Phase: 2
Type:-ROUTE SEARCH
Subtype: entry
Result: ALLOW
Config:
Additional information:
identity of the 255.255.255.255 1xx.xxx.172.1Result:
input interface: internet
entry status: to the top
entry-line-status: to the top
the output interface: NP identity Ifc
the status of the output: to the top
output-line-status: to the top
Action: drop
Drop-reason: (headwall) No. road to hostPlease help me find the cause why asa is unable to find the path to its own interface.
Thank you in advance.
Hello
You will not be able to connect to an IP address of an interface ASA behind another ASA interface. It is a limit that has been there for Cisco firewalls as long as I can remember.
The only exception is when you have a VPN connection that is connected to an ASA interface, then you can connect through this VPN connection to another interface of the ASA. In this case the ASA will also require that you have the following command
access to the administration
Where is the name of the interface to which you are connected.
-Jouni
-
How to block ping the ASA 5506 outside interface?
I configured a Cisco ASA VPN configuration and Setup. Everything works fine. The SAA outside interface is to pings (on the internet) which is a threat to security. How to only block ping to the external interface without interrupting the functions of the ASA. I tried what follows, but does not seem to work.
outside the IP = 169.215.243.X
ASA 2.0000 Version 2
Access list BLOCK_PING refuse icmp any host 169.251.243.X echo-reply
Access-group BLOCK_PING in interface outside
You have set up the ACL is only for traffic that gets sent through the ASA, ASA traffic is controlled in different ways. For ICMP, you can refuse the rattling of the SAA and that allows all other ICMP with the following configuration:
icmp deny any echo outsideicmp permit any outside
It is also possible to ban all ICMP:icmp deny any outside
The 'truth' is probably somewhere between these two options. It's your choice. -
Licenses of the ASA, a license or two for a failover pair
I had two units ASA firewall configured as a failover pair. Now I need increases the SSL VPN license, do I need a licence for the ASA pair or two licenses, one for each unit. Can use a key of activation on both units?
One thing I know for sure, put the key on the Active unit, cannot synchronize the license to the standby unit.
Thank you very much in advance.
It depends on the version. The ASA 8.3 and later versions, you can share a single license through an HA pair.
-
The ASA to use a different Port SSH
Please let me know if you have heard of this
Thank you
Dave
Dave,
According to my knowledge the ASA does not support this. Anthony we have a device before the ASA natting redirect some ther port at 22 of the SAA.
I hope this helps.
Kind regards
SOM
PS: Please check the issue as resolved if it is answered. Note the useful messages. Thank you.
-
Hello
The ASA is not my strong point. I had to make some changes to my ASA clients when the provider has changed. The ASA has been NAT would be an NTU gave us the previous provider, the new provider of the SAA is NAT had a modem. The only thing that does not work right is the VPN.
When IPSec VPN connects we cannot ping, telnet/ssh or RDP to one of imagine. My guess is that the ACL are not quite right. Could someone take a look at the config and propose something?
WAN - ASA - LAN (192.168.20.x)
I deleted the names of user and password and changed the public IP address around security.
ASA # sh run
: Saved
:
ASA Version 8.2 (5)
!
host name asa
domain afpo.local
activate the encrypted password of JCdTyvBk.ia9GKSj
d/TIM/v60pVIbiEg encrypted passwd
names of
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
interface Vlan1
nameif inside
security-level 100
address 192.168.20.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
PPPoE client vpdn group idnet
IP address pppoe setroute
!
banner exec *****************************************************
exec banner * SCP backup enabled *.
exec banner * SYSLOG enabled *.
banner exec *****************************************************
passive FTP mode
clock timezone GMT/UTC 0
summer time clock GMT/BDT recurring last Sun Mar 01:00 last Sun Oct 02:00
DNS lookup field inside
DNS server-group DefaultDNS
Server name 192.168.20.201
domain afpo.local
permit same-security-traffic intra-interface
object-group network GFI-SERVERS
object-network 5.11.77.0 255.255.255.0
object-network 93.57.176.0 255.255.255.0
object-network 94.186.192.0 255.255.255.0
object-network 184.36.144.0 255.255.255.0
network-object 192.67.16.0 255.255.252.0
object-network 208.43.37.0 255.255.255.0
network-object 228.70.81.0 255.255.252.0
network-object 98.98.51.176 255.255.255.240
allowed extended INCOMING tcp access list any interface outside eq https inactive
allowed extended INCOMING tcp access list any interface outside eq 987
interface of access inactive list allowed extended object-group GFI SERVERS off eq smtp tcp INBOUND
interface to access extended permitted list INCOMING tcp object-group GFI SERVERS off eq ldaps
access-list SHEEP extended ip 192.168.20.0 allow 255.255.255.0 10.0.0.0 255.255.0.0
access-list SHEEP extended ip 192.168.20.0 allow 255.255.255.0 172.16.0.0 255.255.255.0
access-list SHEEP extended ip 192.168.20.0 allow 255.255.255.0 172.16.0.0 255.255.255.128
IP 10.71.79.0 allow Access - list extended RITM 255.255.255.0 10.0.0.0 255.255.0.0
CLIENT_VPN list of allowed ip extended access any 172.16.0.0 255.255.255.128
Standard access list SPLIT_TUNNEL allow 10.71.79.0 255.255.255.0
Standard access list TSadmin_splitTunnelAcl allow 10.71.79.0 255.255.255.0
pager lines 24
Enable logging
logging trap information
asdm of logging of information
host of logging inside the 10.71.79.2
Within 1500 MTU
Outside 1500 MTU
local pool CLIENT_VPN_POOL 172.16.0.1 - 172.16.0.126 255.255.255.128 IP mask
local pool SSL_VPN_POOL 172.16.0.129 - 172.16.0.254 255.255.255.128 IP mask
IP verify reverse path to the outside interface
IP audit attack alarm drop action
ICMP unreachable rate-limit 1 burst-size 1
ICMP allow 10.71.79.0 255.255.255.0 echo inside
ICMP allow any inside
ICMP allow any inaccessible outside
ICMP allow 86.84.144.144 255.255.255.240 echo outside
ICMP allow all outside
ASDM image disk0: / asdm - 645.bin
enable ASDM history
ARP timeout 14400
NAT-control
Global 1 interface (outside)
NAT (inside) 0 access-list SHEEP
NAT (inside) 1 192.168.20.0 255.255.255.0
public static tcp (indoor, outdoor) interface smtp 10.71.79.2 smtp netmask 255.255.255.255
public static tcp (indoor, outdoor) interface https 10.71.79.2 https netmask 255.255.255.255
public static tcp (indoor, outdoor) interface 987 10.71.79.2 987 netmask 255.255.255.255
public static tcp (indoor, outdoor) interface ldaps 10.71.79.2 ldaps netmask 255.255.255.255
Access-group ENTERING into the interface outside
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
Floating conn timeout 0:00:00
dynamic-access-policy-registration DfltAccessPolicy
RADIUS protocol AAA-server Serveur_RADIUS
AAA-server host 10.71.79.2 Serveur_RADIUS (inside)
key *.
RADIUS-common-pw *.
not compatible mschapv2
the ssh LOCAL console AAA authentication
Enable http server
Server of http session-timeout 60
http 0.0.0.0 0.0.0.0 inside
http 87.84.164.144 255.255.255.240 outside
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
resetinbound of service inside interface
resetinbound of the outside service interface
Service resetoutside
Crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
Crypto ipsec transform-set ESP-DES-SHA esp - esp-sha-hmac
Crypto ipsec transform-set ESP-DES-MD5 esp - esp-md5-hmac
Crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
Crypto ipsec transform-set ESP-3DES-MD5-esp-3des esp-md5-hmac
Crypto ipsec transform-set ESP-AES-256-SHA 256 - aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-SHA aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-MD5-esp - aes esp-md5-hmac
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
address DYN_CLIENT_VPN 10 of the crypto dynamic-map CLIENT_VPN
Crypto dynamic-map DYN_CLIENT_VPN 10 the value transform-set ESP-AES-256-SHA ESP-3DES-MD5
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 pfs Group1 set
Crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 value transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA MD5-ESP-3DES ESP-DES-SHA ESP-DES-MD5
crypto IPSEC_VPN 10 card matches the address RITM
card crypto IPSEC_VPN 10 set peer 88.98.52.177
card crypto IPSEC_VPN 10 the value transform-set ESP-AES-256-SHA ESP-3DES-MD5
card crypto IPSEC_VPN 100-isakmp dynamic ipsec DYN_CLIENT_VPN
card crypto IPSEC_VPN 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
IPSEC_VPN interface card crypto outside
crypto ISAKMP allow outside
crypto ISAKMP policy 10
preshared authentication
aes-256 encryption
sha hash
Group 5
life 86400
crypto ISAKMP policy 20
preshared authentication
aes-192 encryption
sha hash
Group 5
life 86400
crypto ISAKMP policy 30
preshared authentication
aes encryption
sha hash
Group 5
life 86400
crypto ISAKMP policy 40
preshared authentication
3des encryption
sha hash
Group 2
life 86400
Telnet timeout 5
SSH enable ibou
SSH 0.0.0.0 0.0.0.0 inside
SSH 88.98.52.176 255.255.255.240 outside
SSH 175.171.144.58 255.255.255.255 outside
SSH 89.187.81.30 255.255.255.255 outside
SSH timeout 60
SSH version 2
Console timeout 30
management-access inside
VPDN group idnet request dialout pppoe
VPDN group idnet localname
VPDN group idnet ppp authentication chap
VPDN usernamepassword *. a basic threat threat detection
scanning-threat shun except ip 10.0.0.0 address threat detection 255.255.0.0
scanning-threat time shun 360 threat detection
threat detection statistics
a statistical threat detection tcp-interception rate-interval 30 burst-400-rate average rate 200
NTP server 130.88.202.49 prefer external source
TFTP server outside 86.84.174.157 /Aberdeen_Fishing_Producers_ (ASA5505) .config
WebVPN
port 4443
allow outside
DTLS port 4443
SVC disk0:/anyconnect-win-2.4.0202-k9.pkg 1 image
SVC disk0:/anyconnect-macosx-i386-2.4.0202-k9.pkg 2 image
Picture disk0:/anyconnect-macosx-powerpc-2.4.0202-k9.pkg 3 SVC
SVC profiles ANYCONNECT_PROFILE disk0: / AnyConnectProfile.xml
enable SVC
attributes of Group Policy DfltGrpPolicy
value of server WINS 10.71.79.2
value of server DNS 10.71.79.2
VPN - 10 concurrent connections
Protocol-tunnel-VPN IPSec svc
enable IP-comp
enable PFS
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list SPLIT_TUNNEL
afpo.local value by default-field
WebVPN
time to generate a new key of SVC 60
SVC generate a new method ssl key
profiles of SVC value ANYCONNECT_PROFILE
SVC request no svc default
internal TSadmin group strategy
Group Policy attributes TSadmin
value of server WINS 10.71.79.2
value of server DNS 10.71.79.2
Protocol-tunnel-VPN IPSec
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list TSadmin_splitTunnelAcl
afpo.local value by default-field
username password backup encrypted qwzcxbPwKZ7WiiEC privilege 15
backup attributes username
type of remote access service
admin Cg9KcOsN6Wl24jnz encrypted privilege 15 password username
attributes of user admin name
type of remote access service
tsadmin encrypted v./oXn.idbhaKhwk privilege 15 password username
R60CY/username password 7AzpFEsR ritm. O encrypted privilege 15
ritm username attributes
type of remote access service
attributes global-tunnel-group DefaultWEBVPNGroup
address SSL_VPN_POOL pool
authentication-server-group LOCAL Serveur_RADIUS
type tunnel-group RemoteVPN remote access
attributes global-tunnel-group RemoteVPN
address CLIENT_VPN_POOL pool
authentication-server-group LOCAL Serveur_RADIUS
IPSec-attributes tunnel-group RemoteVPN
pre-shared key *.
tunnel-group 87.91.52.177 type ipsec-l2l
IPSec-attributes tunnel-group 89.78.52.177
pre-shared key *.
tunnel-group TSadmin type remote access
tunnel-group TSadmin General attributes
address CLIENT_VPN_POOL pool
strategy-group-by default TSadmin
tunnel-group TSadmin ipsec-attributes
pre-shared key *.
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
maximum message length automatic of customer
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the rsh
inspect the rtsp
inspect sqlnet
inspect the skinny
inspect sunrpc
inspect xdmcp
inspect the sip
inspect the netbios
inspect the tftp
Review the ip options
inspect the icmp
!
global service-policy global_policy
context of prompt hostname
no remote anonymous reporting call
Cryptochecksum:9ddde99467420daf7c1b8d414dd04cf3
: end
ASA #.Doug,
The nat will knit from inside to out if the LAN is 192.168.20.0 nat should be like this:
access-list SHEEP extended ip 192.168.20.0 allow 255.255.255.0 172.16.0.129 255.255.255.128
Just to get this clear you use remote VPN, you must add the 192.168.20.0 to split ACL road tunnel:
SPLIT_TUNNEL list standard access allowed 192.168.20.0 255.255.255.0
-JP-
-
Hello
I have a question about the steps for using on IPS on ASA - all using a NAT addresses or configuration of access list for interesting traffic, that I have to use really. Specifically, NAT and the list of access or access and NAT?
Keep the ACL extended near the source and the REAL IP address. NAT occurs within the ASA, then you're dealing with external systems.
If you have 6 or 14 addresses external, public IP by your ISP, you can NAT... otherwise, you're stuck with PAT.
For entrants to the outside: use the real, REAL public IP addresses have been assigned by your service provider in order to allow certain incoming traffic. It could be access list 100 or a list named more extensive access, such as 'inbound-outside '.
For entrants inside the interface: use internal IP address private plan [192.168.x.x, 172.16.x.x - 172.31.255, 10.0.0.0] with appropriate subnet mask to allow traffic from the inside to the outside for your users. Most of the people open the "permit ip any any" here, but I prefer to limit the internal address, specific private only. It could be access list 102 or a named example lsit access 'inbound_inside '.
Traffic, which is not "allowed" will be implicitly denied.
-
How to change the ASA and ASDM on ASA5505 questioned once
Can anyone suggest the way to upgrade the software on the Cisco ASA5505 simultaneously both ASA and ASDM without trouble, like I just did?
Here is what happened. I copied the files asa821 - k8.bin and asdm - 621.bin for flash memory, then renamed the old versions like Oasa724 - k8.bin and Oasdm - 524.bin and then issued the command reload from the GUI of Windows.
Big mistake, I lost connectivity ASDM entirely and has been obliged to buy a USB to serial port adapter and plug the cable from port of CLI command so she can return to the unit. I found that he was running the kernel asa821 - k8.bin, as expected, but apparently the ASDM was still under the version 5.24.
Should I have created a new folder and moved the older versions of this file, then issued the command reload system and hope for the best?
I feel that I've defiled things upwards, I guess I have to use tftp to reload the boot image to get the ASA5505 back up again (using the ROMMON commands)
In fact, the only way that I was able to recover the GUI of Windows used start to asa724 image - k8.bin older command.
What is the right way to upgrade to new versions asa 8.2 (1) and asdm 6.2 (1)?
Really, I don't want to risk losing my ability to speak with this box and I spent an anxious afternoon yesterday, when I got to the pop-up message box "can not display the asdm manager."
======
After working with the CLI port, I noticed the following error:
Set of images of Manager devices, but unable to find disk0: / asdm - 524.bin
Out of config line 75, "asdm image disk0: / asdm-5...» »So apparently some configuration file must point to the correct asdm and just blindly change the files in the folder will NOT work.
========
After working more with the port of the CLI and the GUI of Windows port, I found that the 'asdm image' command did NOT work in the CLI software, but was apparently working in the GUI software, so I ran this command to tell the system to use the recent 6.21 on start.
After that and issuing the command reload of the CLI, I was able to set up successfully with the latest software of asa and asdm.
I would like to have access to CLI is valuable in this case.
I DON'T know why the command 'asdm image' appears inaccessible on the CLI port.
Any ideas?
As far as I'm concerned this problem has been resolved (using educated error)
The boot of the ASA when he tries to use the command 'system startup' file in the config. If it is not very well this file (it was not there because you renamed it), it starts the first image he will find...
However for ASDM ASA uses just the image you have. You were pointing to asdm5.2 and renamed, there was no valied ASDM image to use.
In other words you must have just changed the 'asdm image"and"system start"commands in the config and point to new files, save the configuration and restart and then it would have worked fine.
I hope it helps.
PK
-
What is the current status of the feature of Kerberos delegation constrained on the platform of the ASA?
Hi Oscar,.
It is not yet available in the current software. Now, we can give no official information on this forum about software that has not yet been published, but if you really want to know, I suggest that you contact your local sales office Cisco to confirm with your account team that news will be in the next version of Software ASA 8.4.
HTH
Herbert
-
Is it possible to change the source of e-mail alerts interface created by the ASA?
Hello
We have configured our ASA to send alerts by e-mail of events such as the connection, it works very well between our ASA and the mail server that is contacted through the 'inside' interface, however we tried to configure it to an another ASA on a remote site that is connected via a VPN from site to site , the problem is when the ASA remote attempts to send an email to our email server, it uses the source IP address of the external interface, we need to use the source IP address of the inside of the interface so that it is sent over the VPN. Is there a way to configure that?
Now when the ASA attempts by e-mail to our mail server, it uses the source interface IP from outside because he see this interface, as the output of the interface accordingly of the email does not get sent over the VPN.
Thank you
If the remote mail server is available on the VPN site-to site, I don't think that you can configure the ASA for him come traffic one interface other than the one with a route to the remote server. And it will only encrypt in VPN tunnel packets that arrive on the interface where the card encryption is applied (i.e. inside of an interface).
You could mail proxy or set up a redirection on your local mail server rule.
-
Hello
I didn't send a CX module before. We are about to deploy firewalls 2xASA5585-X with CX (for STROKE and WSE) modules.
I'm sure I know the answer to this (I've deployed a lot of old OLD ASA with CSC modules in them, and I'm guessing that the CX module has the same).
1 will be the failure of the module CX trigger a failover event (fail-over active standby)? My guess is not?
2. If it is not and policy service is set to 'closed' this means that the client should perform a manual failover to the secondary/sleep to restore access, web - this correct?
Pete
Hi Pete,.
1 will be the failure of the module CX trigger a failover event (fail-over active standby)? My guess is not.?
Yes he custom of tipping your ASA, depends on configuration either will be allowed or close the traffic
In the area if ASA CX card fails, click permit traffic or close traffic. The narrow traffic option defines the ASA to block all traffic if the ASA CX module is not available. Permits for movement option sets the ASA to allow all traffic through, if not inspected, the ASA CX module is not available.
2 if it is not and the service policy is set to 'closed' this means that the client should perform a manual failover to the secondary/sleep to restore access, web - this correct? .When set to allow traffic CX failure, there is no need to manually failover your ASA firewall between HA
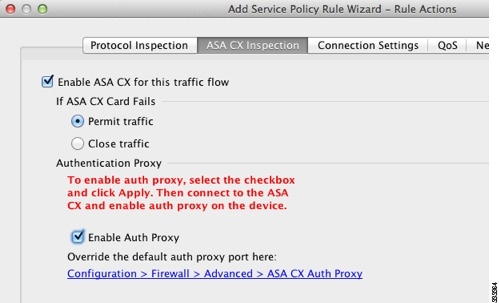
Step 8
 check the ASA CX check this box traffic flow.
check the ASA CX check this box traffic flow.http://www.Cisco.com/c/en/us/TD/docs/security/ASA/Quick_Start/CX/cx_qsg.html#wp49530
-
Content of the ASA CX filtering, looking for suggestions
I wanted to get some feedback on how the rest of you the security people do web content filtering.
The CX did a great job with HTTP but when it comes to HTTPS there leaves a lot to desire. When the CX first went live, it was configured to decrypt all the HTTPS traffic and deny transactions to servers "to the aid of a certificate not approved" and "If the secure session handshaking fails" lit.
Immediately, I started to implement the policy of 'do not read' and it worked very well for most of the sites affected by issues of HTTPS decryption. Other sites required certificate HTTPS imported to the CX for it to work.
However, due to the constant "error: 140920E3:SSL routines: SSL3_GET_SERVER_HELLO:parse tlsext" I experimented with different work a rounds until I found these articles.
http://www.exploresecurity.com/the-small-print-for-OpenSSL-legacy_renego...
https://www.digicert.com/news/2011-06-03-SSL-renego.htm
ATC suggestion was to create a deny statement (with the help of a group of objects that defines the ENTIRE domain name) at the top of the ACL that send traffic to the ASA to the CX. It was the only way to keep the CX deny "using a certificate not approved" and "If the secure session handshaking fails" decryption settings turned on.
Now I feel I'm back to square one, as the number of exceptions have grown exponentially. This led me to believe that I need to return to the path of the content filtering is implemented. My goal is to apply a simple and scalable solution. As I see it, I can continue to add to the list of exemptions "ASA to CX", is not a scalable solution, because it requires all FQDN to be defined (e.g. bank.com, server1.bank.com, server2.bank.com, etc.). The alternative is to relax the decryption CX configurations which I think is the equivalent to remove the airbags in a car for weight reduction to make it faster.
Any input would be appreciated!
I came to the conclusion that SSL decryption is no longer possible, where a robust PKI was deployed in a company. Even in this case we would ideally use a dedicated appliance SSL decryption, so we can give the CX (or ASA with firepower service module) good old http for inspection.
The right software modules do not have the processing power to line decryption rate for everything, but the more modest rate of return.
In addition, the CX is now removed for modules of firepower, so you won't see any significant new addressing this gap on the CX.
-
What is the reference of the item required to activate the failover of the asa?
you first need to safety over the license to enable failover if you run of ASA 5510, otherwise if you're running 5520's and higher then follow the steps in the example located here:
http://www.Cisco.com/en/us/customer/products/ps6120/prod_configuration_examples_list.html
Maybe you are looking for
-
The last update says that it does not support the current version of the plugin Symantec vulnerability, so I'm afraid to update because I would lose the security feature of Symantec. Why is the last significant update? When you support the current ve
-
Activation XP, updates, IE8 and Security Essentials after April 2014
Through my church, I recycle computers that have been brought in. They all have XP and most hard drives are removed. I have a generic restore XP Professional SP3 disk and am able to activate XP with key code on the side of the computer through a we
-
Where to get a copy of Windows XP SP1a full
I need to find a copy of Windows XP service pack 1A before I can using Windows Update (I hope) or Service Pack 2 to get up to SP3 so that I can re-updating to Windows 8, which was broken by a few .msi I installed. ;-} Lament www.Microsoft.com/en-US/D
-
Lost all Complements on my Start menu
My husband was card playing and all of a sudden he had an alert of the screen that says he needed to restart the computer. He did, and we lost all our desktop icons and all the items on the left side of the pop up screen when you click Start. any i
-
I find the minidump files and tried opening them and could not. Files and downloaded programs of debugging appear in the program. When I try to open them I get "you must be an administrator to open" insofar as I know that I am the administrator becau