Phase DMVPN I fail when migration of PSK to GIPR
I'm currently is the migration process of my network key preshared certificate DMVPN. Most of the rays have developed and works without any problem, but there are several that are not past the phase I. I have included the isakmp debug of the hub and one of the rays who fail. I see that the hub goes QM_IDLE after receiving the certificate of the talks, but it looks like not to speak it never receives the cert of the hub. I suspect a problem with the ISP, but it's not as simple as filtering 500 as seem to do all messages except the cert. If I bring him talking on PSK it works fine. Has anyone seen this problem before and what is the resolution?
DMVPN Hub
7 Oct 19:38:36.213: ISAKMP: 500 local port, remote port 500
7 Oct 19:38:36.213: ISAKMP: find a dup her to the tree during the isadb_insert his 7F1AA7CC5920 = call BVA
7 Oct 19:38:36.213: ISAKMP: (0): entry = IKE_MESG_FROM_PEER, IKE_MM_EXCH
7 Oct 19:38:36.213: ISAKMP: (0): former State = new State IKE_READY = IKE_R_MM1
7 October 19:38:36.214: ISAKMP: (0): treatment ITS payload. Message ID = 0
7 October 19:38:36.214: ISAKMP: (0): load useful vendor id of treatment
7 October 19:38:36.214: ISAKMP: (0): provider ID seems the unit/DPD but major incompatibility of 69
7 Oct 19:38:36.214: ISAKMP (0): provider ID is NAT - T RFC 3947
7 October 19:38:36.214: ISAKMP: (0): load useful vendor id of treatment
7 October 19:38:36.214: ISAKMP: (0): provider ID seems the unit/DPD but major incompatibility of 245
7 Oct 19:38:36.214: ISAKMP (0): provider ID is NAT - T v7
7 October 19:38:36.214: ISAKMP: (0): load useful vendor id of treatment
7 October 19:38:36.214: ISAKMP: (0): provider ID seems the unit/DPD but major incompatibility of 157
7 October 19:38:36.214: ISAKMP: (0): provider ID is NAT - T v3
7 October 19:38:36.214: ISAKMP: (0): load useful vendor id of treatment
7 October 19:38:36.214: ISAKMP: (0): provider ID seems the unit/DPD but major incompatibility of 123
7 October 19:38:36.214: ISAKMP: (0): provider ID is NAT - T v2
7 Oct 19:38:36.214: ISAKMP: (0): pair found pre-shared key matching 2.8.51.58
7 October 19:38:36.214: ISAKMP: (0): pre-shared key local found
7 October 19:38:36.214: ISAKMP: (0): IKE-> PKI get configured TrustPoints State (R) MM_NO_STATE (post 2.8.51.58)
7 October 19:38:36.214: ISAKMP: (0): ICP-> IKE Got set up TrustPoints State (R) MM_NO_STATE (post 2.8.51.58)
7 Oct 19:38:36.214: ISAKMP: (0): audit ISAKMP transform 1 against policy priority 5
7 Oct 19:38:36.214: ISAKMP: 3DES-CBC encryption
7 Oct 19:38:36.214: ISAKMP: MD5 hash
7 Oct 19:38:36.214: ISAKMP: default group 1
7 Oct 19:38:36.214: ISAKMP: auth RSA sig
7 Oct 19:38:36.214: ISAKMP: type of life in seconds
7 Oct 19:38:36.214: ISAKMP: life (IPV) 0 x 0 0 x 1 0 x 51 0x80
7 Oct 19:38:36.214: ISAKMP: (0): atts are acceptable. Next payload is 3
7 Oct 19:38:36.214: ISAKMP: (0): Acceptable atts: real life: 0
7 Oct 19:38:36.214: ISAKMP: (0): Acceptable atts:life: 0
7 Oct 19:38:36.214: ISAKMP: (0): fill atts in his vpi_length:4
7 Oct 19:38:36.214: ISAKMP: (0): fill atts in his life_in_seconds:86400
7 October 19:38:36.214: ISAKMP: (0): IKE-> PKI start PKI Session state (R) MM_NO_STATE (post 2.8.51.58)
7 October 19:38:36.214: ISAKMP: (0): ICP-> IKE started PKI Session state (R) MM_NO_STATE (post 2.8.51.58)
7 Oct 19:38:36.214: ISAKMP: (0): return real life: 86400
7 Oct 19:38:36.214: ISAKMP: (0): timer life Started: 86400.
7 October 19:38:36.214: ISAKMP: (0): load useful vendor id of treatment
7 October 19:38:36.214: ISAKMP: (0): provider ID seems the unit/DPD but major incompatibility of 69
7 Oct 19:38:36.214: ISAKMP (0): provider ID is NAT - T RFC 3947
7 October 19:38:36.214: ISAKMP: (0): load useful vendor id of treatment
7 October 19:38:36.214: ISAKMP: (0): provider ID seems the unit/DPD but major incompatibility of 245
7 Oct 19:38:36.214: ISAKMP (0): provider ID is NAT - T v7
7 October 19:38:36.214: ISAKMP: (0): load useful vendor id of treatment
7 October 19:38:36.214: ISAKMP: (0): provider ID seems the unit/DPD but major incompatibility of 157
7 October 19:38:36.214: ISAKMP: (0): provider ID is NAT - T v3
7 October 19:38:36.214: ISAKMP: (0): load useful vendor id of treatment
7 October 19:38:36.214: ISAKMP: (0): provider ID seems the unit/DPD but major incompatibility of 123
7 October 19:38:36.214: ISAKMP: (0): provider ID is NAT - T v2
7 Oct 19:38:36.214: ISAKMP: (0): entry = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
7 Oct 19:38:36.214: ISAKMP: (0): former State = new State IKE_R_MM1 = IKE_R_MM1
7 October 19:38:36.214: ISAKMP: (0): built of NAT - T of the seller-rfc3947 ID
7 October 19:38:36.214: ISAKMP: (0): lot of 2.8.51.58 sending my_port 500 peer_port 500 (R) MM_SA_SETUP
7 Oct 19:38:36.214: ISAKMP: (0): sending a packet IPv4 IKE.
7 Oct 19:38:36.214: ISAKMP: (0): entry = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
7 Oct 19:38:36.214: ISAKMP: (0): former State = new State IKE_R_MM1 = IKE_R_MM2
7 Oct 19:38:36.240: ISAKMP (0): received 2.8.51.58 packet 500 Global 500 (R) sport dport MM_SA_SETUP
7 Oct 19:38:36.240: ISAKMP: (0): entry = IKE_MESG_FROM_PEER, IKE_MM_EXCH
7 Oct 19:38:36.240: ISAKMP: (0): former State = new State IKE_R_MM2 = IKE_R_MM3
7 October 19:38:36.240: ISAKMP: (0): processing KE payload. Message ID = 0
7 October 19:38:36.242: ISAKMP: (0): processing NONCE payload. Message ID = 0
7 October 19:38:36.242: ISAKMP: (38618): payload processing CERT_REQ. Message ID = 0
7 October 19:38:36.242: ISAKMP: (38618): peer wants a cert CT_X509_SIGNATURE
7 October 19:38:36.242: ISAKMP: (38618): peer wants cert issued by cn = Tetra Pak Root CA - G1
7 October 19:38:36.242: ISAKMP: (38618): load useful vendor id of treatment
7 October 19:38:36.242: ISAKMP: (38618): provider ID is DPD
7 October 19:38:36.242: ISAKMP: (38618): load useful vendor id of treatment
7 October 19:38:36.242: ISAKMP: (38618): addressing another box of IOS!
7 October 19:38:36.242: ISAKMP: (38618): load useful vendor id of treatment
7 October 19:38:36.242: ISAKMP: (38618): provider ID seems the unit/DPD but major incompatibility of 209
7 October 19:38:36.242: ISAKMP: (38618): provider ID is XAUTH
7 Oct 19:38:36.242: ISAKMP: receives the payload type 20
7 Oct 19:38:36.242: ISAKMP (38618): sound not hash no match - this node outside NAT
7 Oct 19:38:36.242: ISAKMP: receives the payload type 20
7 Oct 19:38:36.242: ISAKMP (38618): No. NAT found for oneself or peer
7 Oct 19:38:36.242: ISAKMP: (38618): entry = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
7 Oct 19:38:36.242: ISAKMP: (38618): former State = new State IKE_R_MM3 = IKE_R_MM3
7 October 19:38:36.243: ISAKMP: (38618): IKE-> PKI get configured TrustPoints State (R) MM_KEY_EXCH (post 2.8.51.58)
7 October 19:38:36.243: ISAKMP: (38618): ICP-> IKE Got set up TrustPoints State (R) MM_KEY_EXCH (post 2.8.51.58)
7 October 19:38:36.243: ISAKMP: (38618): IKE-> PKI obtain IssuerNames State (R) MM_KEY_EXCH (post 2.8.51.58)
7 October 19:38:36.243: ISAKMP: (38618): ICP-> IKE got IssuerNames State (R) MM_KEY_EXCH (post 2.8.51.58)
7 Oct 19:38:36.243: ISAKMP (38618): construction CERT_REQ for issuer cn = Tetra Pak issuing CA 01 - G1 n, dc = tp1, dc = ad1, dc is tetrapak, dc = com
7 October 19:38:36.243: ISAKMP: (38618): lot of 2.8.51.58 sending my_port 500 peer_port 500 (R) MM_KEY_EXCH
7 Oct 19:38:36.243: ISAKMP: (38618): sending a packet IPv4 IKE.
7 Oct 19:38:36.243: ISAKMP: (38618): entry = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
7 Oct 19:38:36.243: ISAKMP: (38618): former State = new State IKE_R_MM3 = IKE_R_MM4
7 Oct 19:38:36.484: ISAKMP (38618): received 2.8.51.58 packet 500 Global 500 (R) sport dport MM_KEY_EXCH
7 Oct 19:38:36.484: ISAKMP: (38618): entry = IKE_MESG_FROM_PEER, IKE_MM_EXCH
7 Oct 19:38:36.484: ISAKMP: (38618): former State = new State IKE_R_MM4 = IKE_R_MM5
7 October 19:38:36.484: ISAKMP: (38618): payload ID for treatment. Message ID = 0
7 Oct 19:38:36.484: ISAKMP (38618): payload ID
next payload: 6
type: 2
FULL domain name: s2s-lvrirt - 01.nvv .net .company .com
Protocol: 17
Port: 500
Length: 42
7 October 19:38:36.484: ISAKMP: (38618): processing CERT payload. Message ID = 0
7 October 19:38:36.484: ISAKMP: (38618): treatment of a cert CT_X509_SIGNATURE
7 October 19:38:36.484: ISAKMP: (38618): IKE-> certificate PKI add the peer of State (R) MM_KEY_EXCH (post 2.8.51.58)
7 October 19:38:36.485: ISAKMP: (38618): ICP-> certificate of the peer IKE Added State (R) MM_KEY_EXCH (post 2.8.51.58)
7 October 19:38:36.485: ISAKMP: (38618): IKE-> PKI get PeerCertificateChain State (R) MM_KEY_EXCH (post 2.8.51.58)
7 October 19:38:36.485: ISAKMP: (38618): ICP-> IKE got PeerCertificateChain State (R) MM_KEY_EXCH (post 2.8.51.58)
7 October 19:38:36.485: ISAKMP: (38618): pubkey from the counterpart is cached
7 October 19:38:36.485: ISAKMP: (38618): IKE-PKI > validate the chain of certificates of State (R) MM_KEY_EXCH (post 2.8.51.58)
7 October 19:38:36.485: ISAKMP: (38618): ICP-> IKE Validate string certificates of State (R) MM_KEY_EXCH (post 2.8.51.58)
7 October 19:38:36.485: ISAKMP: (38618): failed to get the certificate DN!
7 October 19:38:36.485: ISAKMP: (38618): payload processing GIS. Message ID = 0
7 Oct 19:38:36.486: ISAKMP: received payload type 17
7 October 19:38:36.486: ISAKMP: (38618): treatment protocol NOTIFIER INITIAL_CONTACT 1
SPI 0, message ID = 0, a = 0x7F1AA7CC5920
7 Oct 19:38:36.486: ISAKMP: (38618): SA authentication status:
authenticated
7 Oct 19:38:36.486: ISAKMP: (38618): SA has been authenticated with 2.8.51.58
7 Oct 19:38:36.486: ISAKMP: (38618): SA authentication status:
authenticated
7 October 19:38:36.486: ISAKMP: (38618): process of first contact.
lowering existing phase 1 and 2 with local 15.18.1.1 2.8.51.58 remote remote port 500
7 Oct 19:38:36.486: ISAKMP: (38617): received first contact, delete SA
7 Oct 19:38:36.486: ISAKMP: (38617): peer does not paranoid KeepAlive.
7 Oct 19:38:36.486: ISAKMP: (38617): deletion of 'Initial of receive Contact' State HIS reason (R) QM_IDLE (post 2.8.51.58)
7 Oct 19:38:36.486: ISAKMP: (38618): entry = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
7 Oct 19:38:36.486: ISAKMP: (38618): former State = new State IKE_R_MM5 = IKE_R_MM5
7 Oct 19:38:36.487: ISAKMP: node set 2177251913 to QM_IDLE
7 October 19:38:36.487: ISAKMP: (38617): lot of 2.8.51.58 sending my_port 500 peer_port 500 (R) QM_IDLE
7 Oct 19:38:36.487: ISAKMP: (38617): sending a packet IPv4 IKE.
7 Oct 19:38:36.487: ISAKMP: (38617): purge the node 2177251913
7 Oct 19:38:36.487: ISAKMP: (38617): entry = IKE_MESG_INTERNAL, IKE_PHASE1_DEL
7 Oct 19:38:36.487: ISAKMP: (38617): former State = new State IKE_P1_COMPLETE = IKE_DEST_SA
7 October 19:38:36.487: ISAKMP: (38618): IKE-> PKI get self CertificateChain State (R) MM_KEY_EXCH (post 2.8.51.58)
7 October 19:38:36.487: ISAKMP: (38618): ICP-> IKE Got self CertificateChain State (R) MM_KEY_EXCH (post 2.8.51.58)
7 October 19:38:36.487: ISAKMP: (38618): IKE-> PKI obtain SubjectName State (R) MM_KEY_EXCH (post 2.8.51.58)
7 October 19:38:36.487: ISAKMP: (38618): ICP-> IKE got SubjectName State (R) MM_KEY_EXCH (post 2.8.51.58)
7 Oct 19:38:36.487: ISAKMP: (38618): My ID configured as IPv4 address, but Addr not in Cert!
7 Oct 19:38:36.487: ISAKMP: (38618): using domain FULL as my ID name
7 Oct 19:38:36.487: ISAKMP: (38618): ITS been RSA authentication of signature using id ID_FQDN type
7 Oct 19:38:36.487: ISAKMP (38618): payload ID
next payload: 6
type: 2
FULL domain name: dmvpn-selurt - 01.nvv .net .company .com
Protocol: 17
Port: 500
Length: 44
7 Oct 19:38:36.487: ISAKMP: (38618): the total payload length: 44
7 October 19:38:36.487: ISAKMP: (38618): IKE-> PKI is CertificateChain to be sent through peer review of State (R) MM_KEY_EXCH (post 2.8.51.58)
7 October 19:38:36.488: ISAKMP: (38618): ICP-> IKE got CertificateChain to be sent through peer review of State (R) MM_KEY_EXCH (post 2.8.51.58)
7 Oct 19:38:36.489: ISAKMP (38618): construction of CERT payload for hostname = selurt-dmvpn - 01.nvv .net .company .com, serialNumber = 4279180096
7 Oct 19:38:36.489: ISAKMP (38618): construction CERT payload for cn = Tetra Pak issuing CA 01 - G1 n, dc = tp1, dc = ad1, dc is tetrapak, dc = com
7 October 19:38:36.489: ISAKMP: (38618): using the key of the TP_NAD_CA trustpoint to sign pair
7 October 19:38:36.494: ISAKMP: (38618): lot of 2.8.51.58 sending my_port 500 peer_port 500 (R) MM_KEY_EXCH
7 Oct 19:38:36.494: ISAKMP: (38618): sending a packet IPv4 IKE.
7 Oct 19:38:36.494: ISAKMP: (38618): entry = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
7 Oct 19:38:36.494: ISAKMP: (38618): former State = new State IKE_R_MM5 = IKE_P1_COMPLETE
7 Oct 19:38:36.494: ISAKMP: (38617): deletion of 'Initial of receive Contact' State HIS reason (R) QM_IDLE (post 2.8.51.58)
7 Oct 19:38:36.494: ISAKMP: (38617): entry = IKE_MESG_FROM_PEER, IKE_MM_EXCH
7 Oct 19:38:36.494: ISAKMP: (38617): former State = new State IKE_DEST_SA = IKE_DEST_SA
7 Oct 19:38:36.494: ISAKMP: (38618): IKE_DPD is enabled, the initialization of timers
7 October 19:38:36.494: ISAKMP: (38618): IKE-> end of the PKI public PKI Session state (R) QM_IDLE (post 2.8.51.58)
7 October 19:38:36.494: ISAKMP: (38618): ICP-> IKE session completed ICP State (R) QM_IDLE (post 2.8.51.58)
7 Oct 19:38:36.494: ISAKMP: (38618): entry = IKE_MESG_INTERNAL, IKE_PHASE1_COMPLETE
selurt-dmvpn-01 #.
7 Oct 19:38:36.494: ISAKMP: (38618): former State = new State IKE_P1_COMPLETE = IKE_P1_COMPLETE
selurt-dmvpn-01 #.
7 Oct 19:38:46.492: ISAKMP (38618): received 2.8.51.58 packet 500 Global 500 (R) sport dport QM_IDLE
7 October 19:38:46.492: ISAKMP: (38618): package of phase 1 is a duplicate of a previous package.
7 October 19:38:46.492: ISAKMP: (38618): retransmission due to phase 1 of retransmission
7 October 19:38:46.992: ISAKMP: (38618): transmit phase 1 QM_IDLE...
7 Oct 19:38:46.992: ISAKMP (38618): increment the count of errors on his, try 1 5: retransmit the phase 1
7 October 19:38:46.992: ISAKMP: (38618): transmit phase 1 QM_IDLE
7 October 19:38:46.992: ISAKMP: (38618): lot of 2.8.51.58 sending my_port 500 peer_port 500 (R) QM_IDLE
selurt-dmvpn-01 #.
7 Oct 19:38:46.992: ISAKMP: (38618): sending a packet IPv4 IKE.
selurt-dmvpn-01 #.
7 Oct 19:38:56.481: ISAKMP (38618): received 2.8.51.58 packet 500 Global 500 (R) sport dport QM_IDLE
7 October 19:38:56.481: ISAKMP: (38618): package of phase 1 is a duplicate of a previous package.
7 October 19:38:56.481: ISAKMP: (38618): retransmission due to phase 1 of retransmission
7 October 19:38:56.981: ISAKMP: (38618): transmit phase 1 QM_IDLE...
7 Oct 19:38:56.981: ISAKMP (38618): increment the count of errors on his, try 2 of 5: retransmit the phase 1
7 October 19:38:56.981: ISAKMP: (38618): transmit phase 1 QM_IDLE
7 October 19:38:56.981: ISAKMP: (38618): lot of 2.8.51.58 sending my_port 500 peer_port 500 (R) QM_IDLE
selurt-dmvpn-01 #.
7 Oct 19:38:56.981: ISAKMP: (38618): sending a packet IPv4 IKE.
selurt-dmvpn-01 #.
7 Oct 19:39:06.481: ISAKMP (38618): received 2.8.51.58 packet 500 Global 500 (R) sport dport QM_IDLE
7 October 19:39:06.481: ISAKMP: (38618): package of phase 1 is a duplicate of a previous package.
7 October 19:39:06.481: ISAKMP: (38618): retransmission due to phase 1 of retransmission
7 October 19:39:06.981: ISAKMP: (38618): transmit phase 1 QM_IDLE...
7 Oct 19:39:06.981: ISAKMP (38618): increment the count of errors on his, try 3 of 5: retransmit the phase 1
7 October 19:39:06.981: ISAKMP: (38618): transmit phase 1 QM_IDLE
7 October 19:39:06.981: ISAKMP: (38618): lot of 2.8.51.58 sending my_port 500 peer_port 500 (R) QM_IDLE
selurt-dmvpn-01 #.
7 Oct 19:39:06.981: ISAKMP: (38618): sending a packet IPv4 IKE.
selurt-dmvpn-01 #.
7 Oct 19:39:09.880: ISAKMP: (38616): serving SA., his is 7F1AA7721158, delme is 7F1AA7721158
selurt-dmvpn-01 #.
7 Oct 19:39:16.481: ISAKMP (38618): received 2.8.51.58 packet 500 Global 500 (R) sport dport QM_IDLE
7 October 19:39:16.481: ISAKMP: (38618): package of phase 1 is a duplicate of a previous package.
7 October 19:39:16.481: ISAKMP: (38618): retransmission due to phase 1 of retransmission
7 October 19:39:16.980: ISAKMP: (38618): transmit phase 1 QM_IDLE...
7 Oct 19:39:16.980: ISAKMP (38618): increment the count of errors on his, try 4 out 5: retransmit the phase 1
7 October 19:39:16.980: ISAKMP: (38618): transmit phase 1 QM_IDLE
7 October 19:39:16.980: ISAKMP: (38618): lot of 2.8.51.58 sending my_port 500 peer_port 500 (R) QM_IDLE
selurt-dmvpn-01 #.
7 Oct 19:39:16.980: ISAKMP: (38618): sending a packet IPv4 IKE.
selurt-dmvpn-01 #.
7 Oct 19:39:26.481: ISAKMP (38618): received 2.8.51.58 packet 500 Global 500 (R) sport dport QM_IDLE
7 October 19:39:26.482: ISAKMP: (38618): package of phase 1 is a duplicate of a previous package.
7 October 19:39:26.482: ISAKMP: (38618): retransmission due to phase 1 of retransmission
7 October 19:39:26.981: ISAKMP: (38618): transmit phase 1 QM_IDLE...
7 Oct 19:39:26.981: ISAKMP (38618): increment the count of errors on his, try 5 of 5: retransmit the phase 1
7 October 19:39:26.981: ISAKMP: (38618): transmit phase 1 QM_IDLE
7 October 19:39:26.981: ISAKMP: (38618): lot of 2.8.51.58 sending my_port 500 peer_port 500 (R) QM_IDLE
selurt-dmvpn-01 #.
7 Oct 19:39:26.981: ISAKMP: (38618): sending a packet IPv4 IKE.
selurt-dmvpn-01 #.
7 Oct 19:39:36.493: ISAKMP: (38617): serving SA., his is 7F1AA79AD9E0, delme is 7F1AA79AD9E0
DMVPN speaks
7 October 19:38:36.181: ISAKMP: (0): profile of THE request is (NULL)
7 Oct 19:38:36.181: ISAKMP: created a struct peer 15.18.1.1, peer port 500
7 Oct 19:38:36.181: ISAKMP: new position created post = 0x2B1F480C peer_handle = 0x80001DF4
7 Oct 19:38:36.181: ISAKMP: lock struct 0x2B1F480C, refcount 1 to peer isakmp_initiator
7 Oct 19:38:36.181: ISAKMP: 500 local port, remote port 500
7 Oct 19:38:36.181: ISAKMP: set new node 0 to QM_IDLE
7 Oct 19:38:36.181: ISAKMP: find a dup her to the tree during the isadb_insert his 2B16C9FC = call BVA
7 Oct 19:38:36.181: ISAKMP: (0): cannot start aggressive mode, try the main mode.
7 Oct 19:38:36.181: ISAKMP: (0): pair found pre-shared key matching 15.18.1.1
7 October 19:38:36.181: ISAKMP: (0): IKE-> PKI get configured TrustPoints State (I) MM_NO_STATE (ext. 15.18.1.1)
7 October 19:38:36.181: ISAKMP: (0): ICP-> IKE Got set up TrustPoints State (I) MM_NO_STATE (ext. 15.18.1.1)
7 October 19:38:36.181: ISAKMP: (0): built of NAT - T of the seller-rfc3947 ID
7 October 19:38:36.181: ISAKMP: (0): built the seller-07 ID NAT - t
7 October 19:38:36.181: ISAKMP: (0): built of NAT - T of the seller-03 ID
7 October 19:38:36.181: ISAKMP: (0): built the seller-02 ID NAT - t
7 Oct 19:38:36.181: ISAKMP: (0): entry = IKE_MESG_FROM_IPSEC, IKE_SA_REQ_MM
7 Oct 19:38:36.181: ISAKMP: (0): former State = new State IKE_READY = IKE_I_MM1
7 October 19:38:36.181: ISAKMP: (0): Beginner Main Mode Exchange
7 October 19:38:36.181: ISAKMP: (0): 15.18.1.1 package sending 500 peer_port 500 (I) my_port MM_NO_STATE
7 Oct 19:38:36.181: ISAKMP: (0): sending a packet IPv4 IKE.
7 Oct 19:38:36.205: ISAKMP (0): packet received 15.18.1.1 dport 500 sport Global 500 (I) MM_NO_STATE
7 Oct 19:38:36.205: ISAKMP: (0): entry = IKE_MESG_FROM_PEER, IKE_MM_EXCH
7 Oct 19:38:36.205: ISAKMP: (0): former State = new State IKE_I_MM1 = IKE_I_MM2
7 October 19:38:36.205: ISAKMP: (0): treatment ITS payload. Message ID = 0
7 October 19:38:36.205: ISAKMP: (0): load useful vendor id of treatment
7 October 19:38:36.205: ISAKMP: (0): provider ID seems the unit/DPD but major incompatibility of 69
7 Oct 19:38:36.205: ISAKMP (0): provider ID is NAT - T RFC 3947
7 Oct 19:38:36.205: ISAKMP: (0): pair found pre-shared key matching 15.18.1.1
7 October 19:38:36.205: ISAKMP: (0): pre-shared key local found
7 Oct 19:38:36.205: ISAKMP: analysis of the profiles for xauth...
7 October 19:38:36.205: ISAKMP: (0): IKE-> PKI get configured TrustPoints State (I) MM_NO_STATE (ext. 15.18.1.1)
7 October 19:38:36.205: ISAKMP: (0): ICP-> IKE Got set up TrustPoints State (I) MM_NO_STATE (ext. 15.18.1.1)
7 Oct 19:38:36.205: ISAKMP: (0): audit ISAKMP transform 1 against policy priority 5
7 Oct 19:38:36.205: ISAKMP: 3DES-CBC encryption
7 Oct 19:38:36.205: ISAKMP: MD5 hash
7 Oct 19:38:36.205: ISAKMP: default group 1
7 Oct 19:38:36.205: ISAKMP: auth RSA sig
7 Oct 19:38:36.205: ISAKMP: type of life in seconds
7 Oct 19:38:36.205: ISAKMP: life (IPV) 0 x 0 0 x 1 0 x 51 0x80
7 Oct 19:38:36.205: ISAKMP: (0): atts are acceptable. Next payload is 0
7 Oct 19:38:36.205: ISAKMP: (0): Acceptable atts: real life: 0
7 Oct 19:38:36.205: ISAKMP: (0): Acceptable atts:life: 0
7 Oct 19:38:36.205: ISAKMP: (0): fill atts in his vpi_length:4
7 Oct 19:38:36.205: ISAKMP: (0): fill atts in his life_in_seconds:86400
7 October 19:38:36.205: ISAKMP: (0): IKE-> PKI start PKI Session state (I) MM_NO_STATE (ext. 15.18.1.1)
7 October 19:38:36.205: ISAKMP: (0): ICP-> IKE started PKI Session state (I) MM_NO_STATE (ext. 15.18.1.1)
7 Oct 19:38:36.205: ISAKMP: (0): return real life: 86400
7 Oct 19:38:36.205: ISAKMP: (0): timer life Started: 86400.
7 October 19:38:36.205: ISAKMP: (0): load useful vendor id of treatment
7 October 19:38:36.205: ISAKMP: (0): provider ID seems the unit/DPD but major incompatibility of 69
7 Oct 19:38:36.205: ISAKMP (0): provider ID is NAT - T RFC 3947
7 Oct 19:38:36.205: ISAKMP: (0): entry = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
7 Oct 19:38:36.205: ISAKMP: (0): former State = new State IKE_I_MM2 = IKE_I_MM2
7 October 19:38:36.209: ISAKMP: (0): IKE-> PKI get configured TrustPoints State (I) MM_SA_SETUP (ext. 15.18.1.1)
7 October 19:38:36.209: ISAKMP: (0): ICP-> IKE Got set up TrustPoints State (I) MM_SA_SETUP (ext. 15.18.1.1)
7 October 19:38:36.209: ISAKMP: (0): IKE-> PKI obtain IssuerNames State (I) MM_SA_SETUP (ext. 15.18.1.1)
7 October 19:38:36.209: ISAKMP: (0): ICP-> IKE got IssuerNames State (I) MM_SA_SETUP (ext. 15.18.1.1)
7 Oct 19:38:36.209: ISAKMP (0): construction CERT_REQ for issuer cn = Tetra Pak Root CA - G1
7 October 19:38:36.209: ISAKMP: (0): 15.18.1.1 package sending 500 peer_port 500 (I) my_port MM_SA_SETUP
7 Oct 19:38:36.209: ISAKMP: (0): sending a packet IPv4 IKE.
7 Oct 19:38:36.209: ISAKMP: (0): entry = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
7 Oct 19:38:36.209: ISAKMP: (0): former State = new State IKE_I_MM2 = IKE_I_MM3
7 Oct 19:38:36.233: ISAKMP (0): packet received 15.18.1.1 dport 500 sport Global 500 (I) MM_SA_SETUP
7 Oct 19:38:36.233: ISAKMP: (0): entry = IKE_MESG_FROM_PEER, IKE_MM_EXCH
7 Oct 19:38:36.233: ISAKMP: (0): former State = new State IKE_I_MM3 = IKE_I_MM4
7 October 19:38:36.233: ISAKMP: (0): processing KE payload. Message ID = 0
7 October 19:38:36.245: ISAKMP: (0): processing NONCE payload. Message ID = 0
7 October 19:38:36.245: ISAKMP: (8329): payload processing CERT_REQ. Message ID = 0
7 October 19:38:36.245: ISAKMP: (8329): peer wants a cert CT_X509_SIGNATURE
7 October 19:38:36.245: ISAKMP: (8329): peer wants cert issued by cn = Tetra Pak issuing CA 01 - G1 n, dc = tp1, dc = ad1, dc is tetrapak, dc = com
7 Oct 19:38:36.249: choose trustpoint TP_NAD_CA as transmitter
7 October 19:38:36.249: ISAKMP: (8329): load useful vendor id of treatment
7 October 19:38:36.249: ISAKMP: (8329): provider ID is the unit
7 October 19:38:36.249: ISAKMP: (8329): load useful vendor id of treatment
7 October 19:38:36.249: ISAKMP: (8329): provider ID is DPD
7 October 19:38:36.249: ISAKMP: (8329): load useful vendor id of treatment
7 October 19:38:36.249: ISAKMP: (8329): addressing another box of IOS!
7 Oct 19:38:36.249: ISAKMP: receives the payload type 20
7 Oct 19:38:36.249: ISAKMP (8329): sound not hash no match - this node outside NAT
7 Oct 19:38:36.249: ISAKMP: receives the payload type 20
7 Oct 19:38:36.249: ISAKMP (8329): No. NAT found for oneself or peer
7 Oct 19:38:36.249: ISAKMP: (8329): entry = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
7 Oct 19:38:36.249: ISAKMP: (8329): former State = new State IKE_I_MM4 = IKE_I_MM4
7 Oct 19:38:36.249: ISAKMP: (8329): send initial contact
7 October 19:38:36.249: ISAKMP: (8329): IKE-> PKI get self CertificateChain of State (I) MM_KEY_EXCH (ext. 15.18.1.1)
7 October 19:38:36.249: ISAKMP: (8329): ICP-> IKE Got self CertificateChain of State (I) MM_KEY_EXCH (ext. 15.18.1.1)
7 October 19:38:36.249: ISAKMP: (8329): IKE-> PKI obtain SubjectName State (I) MM_KEY_EXCH (ext. 15.18.1.1)
7 October 19:38:36.249: ISAKMP: (8329): ICP-> IKE got SubjectName State (I) MM_KEY_EXCH (ext. 15.18.1.1)
7 Oct 19:38:36.249: ISAKMP: (8329): My ID configured as IPv4 address, but Addr not in Cert!
7 Oct 19:38:36.249: ISAKMP: (8329): using domain FULL as my ID name
7 Oct 19:38:36.249: ISAKMP: (8329): ITS been RSA authentication of signature using id ID_FQDN type
7 Oct 19:38:36.249: ISAKMP (8329): payload ID
next payload: 6
type: 2
FULL domain name: s2s-lvrirt - 01.nvv .net .company .com
Protocol: 17
Port: 500
Length: 42
7 Oct 19:38:36.249: ISAKMP: (8329): the total payload length: 42
7 October 19:38:36.249: ISAKMP: (8329): IKE-> PKI is CertificateChain to send to the State peer (I) MM_KEY_EXCH (ext. 15.18.1.1)
7 October 19:38:36.253: ISAKMP: (8329): ICP-> IKE got CertificateChain to send to the State peer (I) MM_KEY_EXCH (ext. 15.18.1.1)
7 Oct 19:38:36.253: ISAKMP (8329): construction of CERT payload for hostname = s2s-lvrirt - 01.nvv .net .company .com, serialNumber = FCZ163860KW
7 October 19:38:36.253: ISKAMP: more send buffer from 1024 to 3072
7 October 19:38:36.253: ISAKMP: (8329): using the key of the TP_NAD_CA trustpoint to sign pair
7 October 19:38:36.449: ISAKMP: (8329): 15.18.1.1 package sending 500 peer_port 500 (I) my_port MM_KEY_EXCH
7 Oct 19:38:36.449: ISAKMP: (8329): sending a packet IPv4 IKE.
7 Oct 19:38:36.449: ISAKMP: (8329): entry = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
7 Oct 19:38:36.449: ISAKMP: (8329): former State = new State IKE_I_MM4 = IKE_I_MM5
7 Oct 19:38:36.481: ISAKMP (8328): packet received 15.18.1.1 dport 500 sport Global 500 (I) MM_NO_STATE
7 October 19:38:46.449: ISAKMP: (8329): transmit phase 1 MM_KEY_EXCH...
7 Oct 19:38:46.449: ISAKMP (8329): increment the count of errors on his, try 1 5: retransmit the phase 1
7 October 19:38:46.449: ISAKMP: (8329): transmit phase 1 MM_KEY_EXCH
7 October 19:38:46.449: ISAKMP: (8329): 15.18.1.1 package sending 500 peer_port 500 (I) my_port MM_KEY_EXCH
7 Oct 19:38:46.449: ISAKMP: (8329): sending a packet IPv4 IKE.
7 Oct 19:38:54.709: ISAKMP: (8327): purge the node 1841056658
7 Oct 19:38:54.709: ISAKMP: (8327): purge the node-57107868
7 October 19:38:56.449: ISAKMP: (8329): transmit phase 1 MM_KEY_EXCH...
7 Oct 19:38:56.449: ISAKMP (8329): increment the count of errors on his, try 2 of 5: retransmit the phase 1
7 October 19:38:56.449: ISAKMP: (8329): transmit phase 1 MM_KEY_EXCH
7 October 19:38:56.449: ISAKMP: (8329): 15.18.1.1 package sending 500 peer_port 500 (I) my_port MM_KEY_EXCH
7 Oct 19:38:56.449: ISAKMP: (8329): sending a packet IPv4 IKE.
7 Oct 19:39:04.709: ISAKMP: (8327): serving SA., his is 3169E824, delme is 3169E824
7 Oct 19:39:06.181: ISAKMP: set new node 0 to QM_IDLE
7 Oct 19:39:06.181: ISAKMP: (8329): SA is still budding. Attached new request ipsec. (2.8.51.58 local, remote 15.18.1.1)
7 Oct 19:39:06.181: ISAKMP: error during the processing of HIS application: failed to initialize SA
7 Oct 19:39:06.181: ISAKMP: error while processing message KMI 0, error 2.
7 October 19:39:06.449: ISAKMP: (8329): transmit phase 1 MM_KEY_EXCH...
7 Oct 19:39:06.449: ISAKMP (8329): increment the count of errors on his, try 3 of 5: retransmit the phase 1
7 October 19:39:06.449: ISAKMP: (8329): transmit phase 1 MM_KEY_EXCH
7 October 19:39:06.449: ISAKMP: (8329): 15.18.1.1 package sending 500 peer_port 500 (I) my_port MM_KEY_EXCH
7 Oct 19:39:06.449: ISAKMP: (8329): sending a packet IPv4 IKE.
7 Oct 19:39:10.261: ISAKMP: (8328): purge the node-1445247076
7 October 19:39:16.449: ISAKMP: (8329): transmit phase 1 MM_KEY_EXCH...
7 Oct 19:39:16.449: ISAKMP (8329): increment the count of errors on his, try 4 out 5: retransmit the phase 1
7 October 19:39:16.449: ISAKMP: (8329): transmit phase 1 MM_KEY_EXCH
7 October 19:39:16.449: ISAKMP: (8329): 15.18.1.1 package sending 500 peer_port 500 (I) my_port MM_KEY_EXCH
7 Oct 19:39:16.449: ISAKMP: (8329): sending a packet IPv4 IKE.
7 Oct 19:39:20.261: ISAKMP: (8328): serving SA., his is 2AD85BD0, delme is 2AD85BD0
7 October 19:39:26.449: ISAKMP: (8329): transmit phase 1 MM_KEY_EXCH...
7 Oct 19:39:26.449: ISAKMP (8329): increment the count of errors on his, try 5 of 5: retransmit the phase 1
7 October 19:39:26.449: ISAKMP: (8329): transmit phase 1 MM_KEY_EXCH
7 October 19:39:26.449: ISAKMP: (8329): 15.18.1.1 package sending 500 peer_port 500 (I) my_port MM_KEY_EXCH
7 Oct 19:39:26.449: ISAKMP: (8329): sending a packet IPv4 IKE.
7 October 19:39:36.449: ISAKMP: (8329): transmit phase 1 MM_KEY_EXCH...
7 Oct 19:39:36.449: ISAKMP: (8329): peer does not paranoid KeepAlive.
7 Oct 19:39:36.449: ISAKMP: (8329): removal of reason ITS status of 'Death by retransmission P1' (I) MM_KEY_EXCH (ext. 15.18.1.1)
7 Oct 19:39:36.449: ISAKMP: (8329): removal of reason ITS status of 'Death by retransmission P1' (I) MM_KEY_EXCH (ext. 15.18.1.1)
Mike,
Concentrator sends his cert but never spoke glow, it is usually a problem with the fragmentation of handling in transit networks.
Sniff the two end you can control and check if you are not missing any fragment on end spoke.
Could be as simple as a MTU problem on your end, or could be something in the path try reassambly.
Several ways to go, check your end if the fragments are missing in transit - begin studying with ISP (s).
M.
Tags: Cisco Security
Similar Questions
-
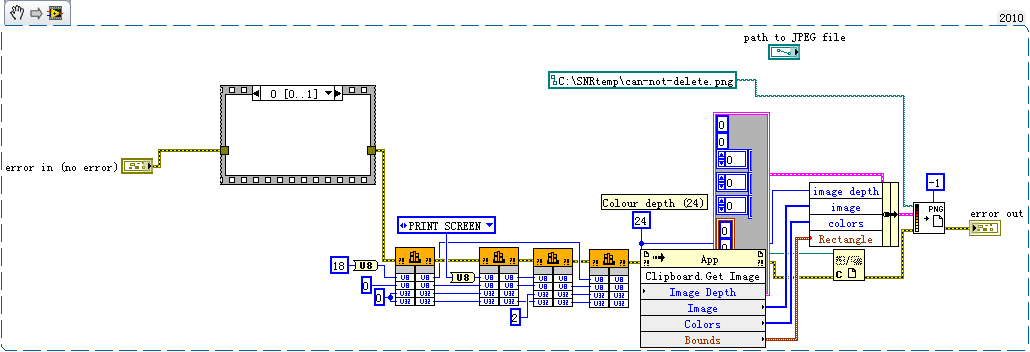
Writing PNG file failed when build exe, but operate normally on the development platform
See photo below, it is used to call WinAPI for screenshot and then save it in PNG file. This Vi operate normally on the flatform of development, but it failed when building the application .exe file. The pop-up dialog error 'chain of illegal path, OS', but it is clear that the path is correct. Note: run the same PC with Win XP.
Update:
I found the reason, but not a solution. In fact, the Clipboard.Get Image does not work when building application exe. But it's the private node invoke, impossible to get support of NOR.
It seems to be to the node to invoke public on the version of LabVIEW 2012, which can help you check on LV2012 version? Thank you very much.
-
Error message: "the server has failed", when you try to download "sp1aexpress_usa".
Original title: "Server failed" when it tries to connect to / download "http://xpSP1.microsoft.com/isapi/pstream3.dll/xp/SP1.USA.1106a".
I downloaded the file "sp1aexpress_usa", but when it works, I am getting error "Server failed" when it tries to connect to / download "http://xpSP1.microsoft.com/isapi/pstream3.dll/xp/SP1.USA.1106a".
Hi JasonVigh,
You can check the link for redownload SP1a and check if you can install it:
http://www.Microsoft.com/en-US/Download/details.aspx?ID=19751
For more information, see the links:
How to get Windows XP Service Pack 3 (SP3)
http://Windows.Microsoft.com/en-us/Windows/downloads/service-packs
You can also check the links of thread for more information:
-
Dear Sir.
Sending files has failed when sending from a mobile phone to the computer via bluetooth. But vice versa is possible.
OS: Win XP Prof
Bluetooth device: Widcomm connected to the desktop computer
Thank you & best regards
Magali U
Hey Ma U,.
Follow the steps in the article.
How to troubleshoot Bluetooth detection and connectivity issues in Windows XP Service Pack 2
-
Error - installation failed when trying to open AVG Antivirus and internet options will not open.
Original title: I need help to fix my 'internet options' in the control panel.
THiiS is a recent problem and I don't know what may have caused it. I tried to install a new virus program to see if the problem was a virus or spyware. I have read that sometimes AVG will cause problems. But in order to install the new antivirus, I have to remove AVG... cannot do! It says "installation failed" when I try to open the long counter. There is therefore no uninstall program. I need to open my internet options in the control panel to start the process of fixing things. but it does not open. I can't download all the programs from my browser. In the lower right hand corner of my IE on the left 'internet' is a white box with a red X.
UPDATE... I used my external CD/dvd drive and was able to copy the installation for firefox to a computer and put it on the shot, I have problems with. Hooray! success... Now, I have firefox and a navigation bar and was able to successfully download a program from the internet. Now, try to uninstall AVG... (how the hell uninstall something that says 'installation failed')
Hi patriciashifflett,
What version of Internet Explorer you have on your computer?
Due to Internet Explorer, you can follow this link & check if the problem persists.
Internet Explorer does not start or stops responding
To remove AVG Anti-virus, you can download and run AVG remover which eliminate all parts of your installation of AVG on your computer, including the registry, system files, user files, etc.
http://www.Avg.com/us-en/download-tools
You can also download & install Microsoft Security Essentials on your machine.
Hope the helps of information.
Please post back and we do know. -
Error message: MatsGetSapCatalogue failed when I try to log on to Fixit Center.
Original title: MatsGetSapCatalogue failed
Why do I receive the message > MatsGetSapCatalogue failed< when="" i="" try="" to="" log="" on="" to="" fixit="" center?="">
Hi Malgaff,
Since you get this message when you try to log on to Fixit Center, you can post your query on Microsoft Fix center for assistance.
-
Profiles of DRM fails when creating EPMA Interface
Hello
DRM getting authentication failed when creating profiles of EPMA.
I tried several times but his failure to get. do I need to do something in DRM. Please some guide.
Hello
Please follow him below the steps and, hopefully, this should solve your problem
1. connect to the DRM application server.
2. launch the DRM configuration console
3. click on the Application to change
4. on the register EPM tab, click the button cancel the registration.
5. in the identification information section change of user name and password for the correct credentials (as a general rule, the user is epm_admin)
6. click on the button Save
7. Enter the credentials of the user CSS (as a general rule, the user is epm_admin)
8. click on Save Configuration
9 restart DRM Services
10. try to create an import profile in EPMA
Thank you
~ KKT ~.
-
Windows build fails when add 'cordova-plugin-camera' + 'cordova-plugin-contacts'
all the details here
Windows build fails when add 'cordova-plugin-camera' + 'cordova-plugin-contacts'
Resolved in the thread on the GS.
-
I get a message "uninstalled failed" when you try to uninstall all applications of CC 2014 and the cleaning tool is of no help. Any ideas?
Hello
If please close the process below for task/monitor activity Manager and try again.
Hope that helps!
Kind regards
Sheena
-
Hello
I have a strange problem, and could ' thin t the answer yet on any forum.
AIR version: 17.0.0.99
The command-line ADT package for iOS fails when I add the two '-Yes hideAneLibSymbols ' and '-useLegacyAOT no ' and if it also contains the native extensions of .ane, which have been updated to support iOS arm64. "If I take the -" hideAneLibSymbols Yes "part of the command line, it works fine, but I need to use it as well, since I use several native extensions, and otherwise I get the error of duplicate symbol. So, it seems to me that hideAneLibSymbols is also there, then the useLegacyAOT is not taken into consideration.
That's how I tried to package it:
ADT-package - target ipa-test - hideAneLibSymbols no useLegacyAOT yes - no - keystore... / Certificates/ASD. P12 - stores pkcs12 - storepass asdasd-putting into service-profile... /Certificates/ASD.mobileprovision asd.ipa asd - app.xml asd.swf assets icons extdir - anes
How could I solve this problem? I used to .ipa files using Flash Pro CC 2014 compiled, but now I can't, since I can add there Yes hideAneLibSymbols .
Thank you
Lehel
Please try with the latest beta "Adobe AIR Beta 17 |" -development of applications Adobe Labs'and let us know if you still see problems.
-
Why keep the program fails when I click Update
Why keep the program fails when I click on update, in particular different editing software
Please read https://forums.adobe.com/thread/1499014
-try some steps such as changing browsers and disable your firewall
-also clear the cache of your browser if you start with a fresh browser
http://myleniumerrors.com/installation-and-licensing-problems/creative-cloud-error-codes-w ip.
http://helpx.Adobe.com/creative-cloud/KB/failed-install-creative-cloud-desktop.html
or
A chat session where an agent can remotely look inside your computer can help
Cloud creative support chat (all creative cloud customer service problems)
-
I created an alert in vCenter which applies to a virtual computer with the trigger setting to be "migrated VM". Basically, I want to follow when migrating virtual machines, either caused by a user or DRS. The alert I created doesn't seem to work. Someone else was able to create an alert that would send a mail when a migrated virtual machine? Thank you.
I applied the update 1 for my vCenter. My version is 4.1 build 345043.
-
Hi all...
Try to Thinapping MS Office 2007, but failed when an error «could not copy ##attributes...» "is thrown. I'm trying to save the project to a folder under vista (called "shared folder") to a virtual machine by using windows XP SP2. I made a mistake? Your help is really appreciated for the entire community, thank you.
Hi MrBean344,
If I was wrong, you will get the error for GetAttributes... while building the project. Am I wrong?
If so, then I think it was due to the long way to have more than 256 characters. Can you please try to save your project in the short path such as C:\ and rebuild the package?
I think that after doing this, error is not displayed and application is virtualized.
Thank you best regards &,.
Margaux Khopkar
-
Illustrator CS6 says 'installation failed' when installing.
Illustrator CS6 says 'installation failed' when installing. No explanation is given. I have not all previous versions of the installed AI or any trial. Help? I really need to use this product today!
We do not know. You must provide the information system and possibly Setup logs:
The problems with the installation logs
Mylenium
-
View failed when importing data mover
HII,
IAM HRMS and CS9.0 review-1 installation. When the loading of the peoplesoft using import database in the data mover. I had 1 error in the view. It's as follows:
Create view SAD_SL_PHONE_VW
-SQL error. Position of the error: 239 return: 905 - ORA-00905: lack of keyword
CREATE VIEW PS_SAD_SL_PHONE_VW (EMPLID, PHONE_TYPE, COUNTRY_CODE, PHONE, EXTENSION, PREF_PHONE_FLAG) AS SELECT A.EMPLID, B.PHONE_TYPE, B.COUNTRY_CODE, B.PHONE, B.EXTENSION, B.PREF_PHONE_FLAG OF (PS_PERSON A LEFT OUTER JOIN PS_PHONE_VW B WHERE A.EMPLID = B.EMPLID)
Error: Unable to process create for SAD_SL_PHONE_VW statement
Views rest: 2212
So, how can I continue with it... pls help me.Probably bug in forum, wire double
View failed when importing data moverNicolas.
Maybe you are looking for
-
Help please! Starting a new job and I was wondering if the Lenovo Thinkcentre M32 is capable of having two monitors. Or how to know. And if yes what cords do I use? Thank you
-
I'm a complete noobie and trying to record thermocouple data using Signal Express 2012. I can get the data to save and export to a text file, but it's a recording to 1.1 seconds. I would like to change to once per second, but do not see this option
-
Qual an estou atuando internet
Qual estou using an internet e porque cai muinto o ten erado no meu pc.
-
Buongiorno, abbiamo 5 Server PowerEdge R410 con co scaduta, uno di questi ha reported knew uno dei 4 brain SAS 600 GB installation. Original da Modello: Segate Cheetah ns.2 ST6600002SS Config Code: 1342 Firmware ER62 Abbiamo UN drive labor-intensive
-
Skype cannot find my sound card
Skype cannot find my Sound card - when I run the test of the Echo - it I heard say 'Hello' then it dies. I have a brand new Thinkpad (T420), Windows 7, internal camera and microphone, Windows loaded all drivers. I tried to find the communication help