Problem connecting to a VPN/Firewall gateway RV042G
Hello
I am new to Cisco, so far I have used the NetAsq materials.
First of all I'm getting is to connect a new RV042G by VPN to a NetAsq firewall.
Today, I can connect without any problems by using the TheGreenbow VPN client on my laptop.
But no chance to try the RV042G.
The corporate network:
-Fixed official IP
-Internal subnet is 192.168.11.0
Firewall is configured with:
-Set up with the aggressive Mode and identity of the type [email protected] / * /
-Pre-shared key is set with e-mail address and password
Remote network:
-Official dynamic IP (but I can't control the remote router)
-Address IP internal FIXED for RV042G is 192.168.13.2 (it means the RV042 is behind a NAT network)
-Subnet behind RV042G is 10.0.0.0
Don't forget; I can connect my laptop from the same network, and even behind the RV042G.
Yes, this means also I have internet access behind the RV042G.
Editing and I tried with Client-to-gateway and gateway to catwalk (I think the last option is correct).
For local security, I can't choose [email protected] / * / just, I need to select IP + [email protected] / * / (?)
For the remote, the same security
For the rest; I've reproduced my Greenbow VPN client settings.
No luck at all; and Yes, I'm VERY sure I set address email and Preshare key correct and identical.
Any ideas?
Hi Stigh,
Can you try this procedure and make sure to have the latest firmware on RV042G 4.2.2.08
Here the link to download the firmware:
On RV042G
-----------
-Change the lifecycle of Phase 1 SA of 28800 to 21600 (6 hours) (should be the same as Netask)
-Enable NAT - T (because the RV behind a NAT)
-Activate Dead Peer Detection
On Netask
----------
-On proposal 1 change the strength of the encryption algorithm and 256-bit hash algorithm
Best regards
Mehdi
Tags: Cisco Support
Similar Questions
-
Use this printer (wireless) for a few years without problem connected to a Linksys 802.11n wireless router. Connected to a desktop computer and two laptops.
Comcast asked recently that I update my modem cable to a new wireless, which also serves as a 802.11n access point wireless router. I installed the new point wireless very well and has been able to set up the printer on a wireless network. (IP, host name and Mac address doesn't appear on the thin printer).
I reinstalled the printer drivers on each computer and everything worked very well last weekend. This weekend, I went to turn the Scanner on the desktop (HP Pavilion, Windows 7, 64-bit) and it wouldn't work. Then I reinstalled the device drivers and then there was no connection to the printer (many reboots the PC and printer at various times during the tests). So I ran again the connection settings on the printer - and led wireless term. (I was able to get the scan to the connection to the computer once on one of the laptops, never the office, then lost. When I send to the printer, it goes into the queue, a very small number of bytes, cross (usually hear the printer starts) then there lost error "connection to a printer. Oddly enough, a couple of times after canceling the print job in the queue, the printed test page actually printed a few minutes later...
I tried to use HP Print & Scan Doctor - it was a complete waste of time. To date, it has always died (do not connect not not the unit) and never been able to diagnose something. I end up having to go to the Task Manager to kill him because he always hangs.
Any thoughts? I'm puzzled.
Appreciate any help/ideas that someone can think.
FYI - I have still no idea what the question is / was?
Connected to the gateway wireless from Comcast to the old Linksys router and I went back to my old wireless network. After you have reinstalled the printer drivers, re-connection of the printer to the old wireless network, re-start the printer and computers - I was (finally...) manages to get printing and scanning works again.
What a waste of a morning/afternoon.
-
Problem connecting to the PL/SQL gateway embedded
I have Oracle XE installed on a machine running Oracle Enterprise Linux 5.3 (64-bit). It took a little effort to set up, but I got here in the end. I updated Apex Apex 3.2.1 default 2.2 installed and configured to use the PL/SQL gateway shipped on port 8500. I used the 8500 port because I also Apache Tomcat running and uses port 8080.
My problem is that I can access the web interface of Apex using the URL http://localhost:8500 / apex, but not when I use the static IP address assigned to my workstation which is 10.0.0.6. When I try the URL http://10.0.0.6:8500 / apex, Firefox gives error "Firefox can't establish a connection with the server 10.0.0.6:8500.
I tried turning off the firewall system but get the same problem. I also have SELinux installed, but it is running in permissive mode.
I think it's a problem Oracle XE/Apex because I can access the Tomcat home page using localhost or IP 10.0.0.6 in the URL - so I think that this excludes security/firewall problems.
I would like to be able to access the Apex, implemented by other computers, so it is very important to get this issue is resolved.
Does anyone have ideas, what may be the problem?Please try it.
To set access HTTP remotely connects:
Start
DBMS_XDB.setListenerLocalAccess (l_access-online FALSE);
end; -
Problems connecting to help connect any and the Ipsec VPN Client
I have problems connecting with the VPN client connect no matter what. I can connect with the Ipsec VPN client in Windows 7 32 bit.
Here is my latest config running.
Thank you for taking the time to read this.
passwd encrypted W/KqlBn3sSTvaD0T
no names
name 192.168.1.117 kylewooddesk kyle description
!
interface Vlan1
nameif inside
security-level 100
IP 192.168.1.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
IP address dhcp setroute
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
boot system Disk0: / asa822 - k8.bin
passive FTP mode
DNS lookup field inside
DNS domain-lookup outside
DNS server-group DefaultDNS
domain wood.local
permit same-security-traffic intra-interface
object-group service rdp tcp
access rdp Description
EQ port 3389 object
outside_access_in list extended access permit tcp any interface outside eq 3389
outside_access_in list extended access permit tcp any interface outside eq 8080
outside_access_in list extended access permit tcp any interface outside eq 3334
outside_access_in to access extended list ip 192.168.5.0 allow 255.255.255.240 192.168.1.0 255.255.255.0
woodgroup_splitTunnelAcl list standard access allowed host 192.168.1.117
inside_nat0_outbound to access ip 192.168.1.0 scope list allow 255.255.255.0 192.168.5.0 255.255.255.240
outside_access_in_1 list extended access permit tcp any host 192.168.1.117 eq 3389
woodgroup_splitTunnelAcl_1 list standard access allowed 192.168.1.0 255.255.255.0
inside_nat0_outbound_1 to access ip 192.168.1.0 scope list allow 255.255.255.0 192.168.5.0 255.255.255.240
inside_nat0_outbound_1 to access extended list ip 192.168.5.0 allow 255.255.255.240 all
inside_test list extended access permit icmp any host 192.168.1.117
no pager
Enable logging
timestamp of the record
asdm of logging of information
Debugging trace record
Within 1500 MTU
Outside 1500 MTU
mask pool local Kyle 192.168.5.1 - 192.168.5.10 IP 255.255.255.0
IP local pool vpnpool 192.168.1.220 - 192.168.1.230
ICMP unreachable rate-limit 1 burst-size 1
ASDM image disk0: / asdm - 631.bin
don't allow no asdm history
ARP timeout 14400
Global (inside) 1 interface
Global 1 interface (outside)
NAT (inside) 0-list of access inside_nat0_outbound_1
NAT (inside) 1 0.0.0.0 0.0.0.0
public static interface 3389 (indoor, outdoor) 192.168.1.117 tcp 3389 netmask 255.255.255.255 dns
public static tcp (indoor, outdoor) interface 8080 192.168.1.117 8080 netmask 255.255.255.255
public static tcp (indoor, outdoor) interface 3334 192.168.1.86 3334 netmask 255.255.255.255
static (inside, upside down) 75.65.238.40 192.168.1.117 netmask 255.255.255.255
Access-group outside_access_in in interface outside
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-registration DfltAccessPolicy
WebVPN
the files enable exploration
activate the entry in the file
enable http proxy
Enable URL-entry
SVC request no svc default
AAA authentication http LOCAL console
Enable http server
http 192.168.1.0 255.255.255.0 inside
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
Crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
Crypto ipsec transform-set ESP-DES-SHA esp - esp-sha-hmac
Crypto ipsec transform-set ESP-DES-MD5 esp - esp-md5-hmac
Crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
Crypto ipsec transform-set ESP-3DES-MD5-esp-3des esp-md5-hmac
Crypto ipsec transform-set ESP-AES-256-SHA 256 - aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-SHA aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-MD5-esp - aes esp-md5-hmac
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 pfs Group1 set
Crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 value transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA MD5-ESP-3DES ESP-DES-SHA ESP-DES-MD5
outside_map card crypto 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
outside_map interface card crypto outside
crypto isakmp identity address
crypto ISAKMP allow outside
crypto ISAKMP policy 10
preshared authentication
3des encryption
sha hash
Group 2
life 86400
Telnet 192.168.1.0 255.255.255.0 inside
Telnet timeout 5
SSH timeout 5
Console timeout 0
dhcpd dns 8.8.8.8 8.8.4.4
dhcpd lease 3000
!
dhcpd address 192.168.1.100 - 192.168.1.130 inside
dhcpd allow inside
!
a basic threat threat detection
host of statistical threat detection
Statistics-list of access threat detection
no statistical threat detection tcp-interception
WebVPN
allow outside
SVC disk0:/anyconnect-win-2.4.1012-k9.pkg 1 image
enable SVC
internal sslwood group policy
attributes of the strategy of group sslwood
VPN-tunnel-Protocol svc webvpn
WebVPN
list of URLS no
internal group woodgroup strategy
woodgroup group policy attributes
value of server DNS 8.8.8.8 8.8.4.4
Protocol-tunnel-VPN IPSec
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list woodgroup_splitTunnelAcl_1
mrkylewood encrypted Q4339wmn1ourxj9X privilege 15 password username
username mrkylewood attributes
VPN-group-policy sslwood
VPN - connections 3
VPN-tunnel-Protocol svc webvpn
value of group-lock sslwood
WebVPN
SVC request no webvpn default
tunnel-group woodgroup type remote access
tunnel-group woodgroup General attributes
address pool Kyle
Group Policy - by default-woodgroup
tunnel-group woodgroup ipsec-attributes
pre-shared key *.
type tunnel-group sslwood remote access
tunnel-group sslwood General-attributes
address pool Kyle
authentication-server-group (inside) LOCAL
authentication-server-group (outside LOCAL)
Group Policy - by default-sslwood
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the netbios
inspect the rsh
inspect the rtsp
inspect the skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect the tftp
inspect the sip
inspect xdmcp
Review the ip options
type of policy-card inspect dns MY_DNS_INSPECT_MAP
parameters
!
global service-policy global_policy
context of prompt hostname
call-home
Profile of CiscoTAC-1
no active account
http https://tools.cisco.com/its/service/oddce/services/DDCEService destination address
email address of destination [email protected] / * /
http https://tools.cisco.com/its/service/...es/DDCEService destination address
destination-mode http transport
Subscribe to alert-group diagnosis
Subscribe to alert-group environment
Subscribe to alert-group monthly periodic inventory
monthly periodicals to subscribe to alert-group configuration
daily periodic subscribe to alert-group telemetry
Cryptochecksum:6fa8db79bcf695080cbdc1159b409360
: end
asawood (config) #.
You also need to add the following:
WebVPN
tunnel-group-list activate
output
tunnel-group sslwood webvpn-attributes
activation of the Group sslwood alias
Let us know if it works.
-
Default gateway when connected to the VPN
Thanks for reading!
It is probably a dump so bear with me the question...
I set up a VPN connection with a Cisco ASA 5505 giving over the internet, with customers behind him (on the same subnet), when environmental connected ot the VPN I can reach the router inside giving me and the other pass behind the router (each switch is connected to the router), but nothing else.
My beets is that the router is to play with my connection, but nevermind that!, Setup is not complete when even... my question is more related to the bridge I'm missing when I'm outside, is connected to VPN on the ASA, pourrait this BUMBLE? I would not a Standard gateway in the command ipconfig settings in windows?
That's who it looks like now:
Anslutningsspecifika-DNS suffix. : VPNOFFICE
IP-adress...: 10.10.10.1
Natmask...: 255.255.255.0.
Standard-gateway...:
The internal network is:
172.16.12.0 255.255.255.0
Here is my config for the SAA, thank you very much!
! FlASH PA ROUTING FRAN VISSTE
! asa841 - k8.bin
!
DRAKENSBERG hostname
domain default.domain.invalid
activate the password XXXXXXX
names of
!
interface Vlan1
nameif inside
security-level 100
IP 172.16.12.4 255.255.255.0
!
interface Vlan10
nameif outside
security-level 0
IP 97.XX. XX.20 255.255.255.248
!
interface Ethernet0/0
switchport access vlan 10
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
passive FTP mode
clock timezone THATS 1
clock to summer time CEDT recurring last Sun Mar 02:00 last Sun Oct 03:00
DNS server-group DefaultDNS
domain default.domain.invalid
object-group Protocol TCPUDP
object-protocol udp
object-tcp protocol
172.16.12.0 IP Access-list extended sheep 255.255.255.0 allow 10.10.10.0 255.255.255.0
MSS_EXCEEDED_ACL list extended access permitted tcp a whole
Note to access VPN-SPLIT-TUNNEL VPN TUNNEL from SPLIT list
standard of TUNNEL VPN-SPLIT-access list permits 172.16.12.0 255.255.255.0
!
map-TCP MSS - map
allow to exceed-mss
!
pager lines 24
Enable logging
timestamp of the record
exploitation forest-size of the buffer to 8192
notifications of recording console
logging buffered stored notifications
notifications of logging asdm
Within 1500 MTU
Outside 1500 MTU
mask pool local 10.10.10.1 - 10.10.10.40 VPN IP 255.255.255.0
ICMP unreachable rate-limit 1 burst-size 1
ICMP allow any inside
ICMP allow all outside
ASDM image disk0: / asdm-625 - 53.bin
don't allow no asdm history
ARP timeout 14400
Global 1 interface (outside)
NAT (inside) 0 access-list sheep
NAT (inside) 1 172.16.12.0 255.255.255.0
Route outside 0.0.0.0 0.0.0.0 97.XX. XX.17 1
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout, uauth 0:05:00 absolute
dynamic-access-policy-registration DfltAccessPolicy
the ssh LOCAL console AAA authentication
Enable http server
http 172.16.12.0 255.255.255.0 inside
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
Crypto ipsec transform-set ESP-DES-SHA esp - esp-sha-hmac
Crypto ipsec transform-set ESP-DES-MD5 esp - esp-md5-hmac
Crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
Crypto ipsec transform-set ESP-3DES-MD5-esp-3des esp-md5-hmac
Crypto ipsec transform-set ESP-AES-256-SHA 256 - aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-SHA aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-MD5-esp - aes esp-md5-hmac
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 pfs Group1 set
Crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 value transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA MD5-ESP-3DES ESP-DES-SHA ESP-DES-MD5
outside_map card crypto 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
outside_map interface card crypto outside
crypto ISAKMP allow outside
crypto ISAKMP policy 10
preshared authentication
3des encryption
sha hash
Group 2
life 86400
crypto ISAKMP policy 65535
preshared authentication
3des encryption
sha hash
Group 2
life 86400
Telnet timeout 5
SSH 172.16.12.0 255.255.255.0 inside
SSH timeout 5
Console timeout 0
!
a basic threat threat detection
Statistics-list of access threat detection
internal VPNOFFICE group policy
VPNOFFICE group policy attributes
value of server DNS 215.122.145.18
Protocol-tunnel-VPN IPSec
Split-tunnel-policy tunnelspecified
Split-tunnel-network-list value TUNNEL VPN-SPLIT
value by default-field VPNOFFICE
Split-dns value 215.122.145.18
no method of MSIE-proxy-proxy
username password admin privilege 15 XXXXXX
username privilege XXXXX Daniel password 0
username Daniel attributes
VPN-group-policy VPNOFFICE
type tunnel-group VPNOFFICE remote access
attributes global-tunnel-group VPNOFFICE
VPN address pool
Group Policy - by default-VPNOFFICE
IPSec-attributes tunnel-group VPNOFFICE
pre-shared key XXXXXXXXXX
!
class-map MSS_EXCEEDED_MAP
corresponds to the MSS_EXCEEDED_ACL access list
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the netbios
inspect the rsh
inspect the rtsp
inspect the skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect the tftp
inspect the sip
inspect xdmcp
inspect the icmp error
inspect the pptp
inspect the amp-ipsec
inspect the icmp
class MSS_EXCEEDED_MAP
advanced connection options MSS-map
!
global service-policy global_policy
privilege level 3 mode exec cmd command perfmon
privilege level 3 mode exec cmd ping command
mode privileged exec command cmd level 3
logging of the privilege level 3 mode exec cmd commands
privilege level 3 exec command failover mode cmd
privilege level 3 mode exec command packet cmd - draw
privilege show import at the level 5 exec mode command
privilege level 5 see fashion exec running-config command
order of privilege show level 3 exec mode reload
privilege level 3 exec mode control fashion show
privilege see the level 3 exec firewall command mode
privilege see the level 3 exec mode command ASP.
processor mode privileged exec command to see the level 3
privilege command shell see the level 3 exec mode
privilege show level 3 exec command clock mode
privilege exec mode level 3 dns-hosts command show
privilege see the level 3 exec command access-list mode
logging of orders privilege see the level 3 exec mode
privilege, level 3 see the exec command mode vlan
privilege show level 3 exec command ip mode
privilege, level 3 see fashion exec command ipv6
privilege, level 3 see the exec command failover mode
privilege, level 3 see fashion exec command asdm
exec mode privilege see the level 3 command arp
command routing privilege see the level 3 exec mode
privilege, level 3 see fashion exec command ospf
privilege, level 3 see the exec command in aaa-server mode
AAA mode privileged exec command to see the level 3
privilege, level 3 see fashion exec command eigrp
privilege see the level 3 exec mode command crypto
privilege, level 3 see fashion exec command vpn-sessiondb
privilege level 3 exec mode command ssh show
privilege, level 3 see fashion exec command dhcpd
privilege, level 3 see the vpnclient command exec mode
privilege, level 3 see fashion exec command vpn
privilege level see the 3 blocks from exec mode command
privilege, level 3 see fashion exec command wccp
privilege, level 3 see the exec command in webvpn mode
privilege control module see the level 3 exec mode
privilege, level 3 see fashion exec command uauth
privilege see the level 3 exec command compression mode
level 3 for the show privilege mode configure the command interface
level 3 for the show privilege mode set clock command
level 3 for the show privilege mode configure the access-list command
level 3 for the show privilege mode set up the registration of the order
level 3 for the show privilege mode configure ip command
level 3 for the show privilege mode configure command failover
level 5 mode see the privilege set up command asdm
level 3 for the show privilege mode configure arp command
level 3 for the show privilege mode configure the command routing
level 3 for the show privilege mode configure aaa-order server
level mode 3 privilege see the command configure aaa
level 3 for the show privilege mode configure command crypto
level 3 for the show privilege mode configure ssh command
level 3 for the show privilege mode configure command dhcpd
level 5 mode see the privilege set privilege to command
privilege level clear 3 mode exec command dns host
logging of the privilege clear level 3 exec mode commands
clear level 3 arp command mode privileged exec
AAA-server of privilege clear level 3 exec mode command
privilege clear level 3 exec mode command crypto
level 3 for the privilege cmd mode configure command failover
clear level 3 privilege mode set the logging of command
privilege mode clear level 3 Configure arp command
clear level 3 privilege mode configure command crypto
clear level 3 privilege mode configure aaa-order server
context of prompt hostname
Cryptochecksum:aaa1f198bf3fbf223719e7920273dc2e
: end
Right if disbaled all traffic will pass tunnel and snack active local internet gateway is used specific traffic wil go to the tunnel.
-
Unable to gateway ping after the connection to the VPN
I've implemented a ASA 5505 with virtually any configuration. I changed the interface of the 192.168.168.250 inside and set up DSL PPPoE for the external interface.
The ASA works perfectly for all my Internet needs so I set up a VPN using Ipsec VPN Wizard. This also works perfectly, except that I noticed a thing. Once I connect to the VPN, I'm not able to ping from the inside address of the ASA at the 192.168.168.250. When I ping or manage the ASA using this IP address, while I work on the site it works fine. Why is this and is there a way that I can change?
Thank you!
-Pete
peterdallas wrote:
I've set up an ASA 5505 with hardly any configuration. I changed the Inside interface to 192.168.168.250 and configured PPPoE DSL for the outside interface.
The ASA is working perfectly for all of my Internet needs so I set up a VPN using the Ipsec VPN wizard. That also works perfectly, except I noticed one thing. Once I connect to the VPN, I'm not able to ping the inside address of the ASA at 192.168.168.250. When I ping or manage the ASA using that IP address while I'm working on site it works fine. Why is that and is there a way I can change it?
Thanks!
-Pete
Pete
Add this to your config file-
ASA (config) # management - access inside
all the details-
http://www.Cisco.com/en/us/docs/security/ASA/asa80/command/reference/m.html#wp1987122
Jon
-
Unable to connect to the Internet after connecting to a VPN server.
As soon as I connect to the VPN, I can't access the Web or e-mail.
An article published by Microsoft Support to http://support.microsoft.com/kb/317025 seems to refer to the same problem. However, it is for Win 2000 and NT platforms, not XP. The problem seems to be due to the VPN connection (being configured) to use the default gateway on the remote network.
Issues related to the:
- The problem indeed because the VPN connection is configured to use the default gateway on the remote network?
- If so, a) how can I know if it's like my VPN connection is configured and b) how I set up so I can use VPN to the network remotely and still being able to use internet locally?
Thank you.
Realize that the VPN is intended to establish a secure connection to a remote network via a public internet. Allowing a client computer at the same time secure access that a secure network and a public network may pose a risk to data leaks out of the network security in the public internet. If "split tunneling" VPN server controls is allowed on a client computer. If allowed by the side of the VPN server, the client computer accesses the VPN and the internet by unchecking the 'use Gateway on the remote network' box. For more information:
"Split Tunneling for concurrent access to the Internet and an Intranet"
<>http://TechNet.Microsoft.com/en-us/library/bb878117.aspx >HTH,
JW -
AFTER VPN CONNECTED TO OFFICE VPN, PING TO A CERTAIN DESTINATION UNREACHABLE HOST BACK
Hello!
I have setup a connection to the vpn pptp from my home to my office.
I've successfully connected to my office vpn.
I can remote desktop to several server in my office, but there is that I can not remote to a pc desktop.
When I try to ping it will return the destination unreachable host
ping 192.168.9.50
Impossible to reach the destination response 192.168.0.1 host
it becomes instead of 192.168.9.50 192.168.0.1
Can someone help with this problem?
I really do work in this pc and I don't no how to connect there?
I'm pretty remote desktop is allowed in this pc.
Thank you
GUKGUK
The 192.168.0.1 address seems to be a gateway address. VPN gateway may have no route to that particular system, either by design or due to oversight. You should be facing this problem with your personal COMPUTER. Brian Tillman [MVP-Outlook]
--------------------------------
https://MVP.support.Microsoft.com/profile/Brian.Tillman
If a response may help, please vote it as useful. If a response to the problem, please mark it as an answer. -
AnyConnect vpn and a tunnel vpn Firewall even outside of the interface.
I have a (no connection) remote access vpn and ipsec tunnel connection to return to our supplier is on the same firewall outside interface.
The problem is when users remote vpn in they are not able to ping or join the provider above the tunnel network.
now, I understand that this is a Bobby pin hair or u turn due to traffic but I'm still not able to understand how the remote vpn users can reach the network of the provider on the tunnel that ends on the same interface where remote access vpn is also configured.
The firewall is asa 5510 worm 9.1
Any suggestions please.
Hello
You are on the right track. Turning U will be required to allow vpn clients access to resources in the L2L VPN tunnel.
The essence is that the split tunneling to access list must include subnets of the remote VPN to peer once the user connects they have directions pertaining to remote resources on anyconnect VPN
Please go through this post and it will guide you how to set up the u turn on the SAA.
https://supportforums.Cisco.com/document/52701/u-turninghairpinning-ASAKind regards
Dinesh MoudgilPS Please rate helpful messages.
-
Windows 7 not connecting to the VPN - gives error 930
I'm one of my boxes, upgrade to Windows 7 (x 64) and everything seems to work - until I try to connect to my VPN - it gives me an Error 930. On the same home network are a (x 64) Vista and XP (x 86) - both can make the VPN connection without problem to the same location. When this box is Vista, it has good work as well.
There is nothing fancy here - simple Windows work stations at a location behind a Linksys WRT54GS connection to a Windows Server 2003 server behind an ISA firewall.
I deleted the connection and recreated, and it worked. What is interesting is that the first connector name was identical to the location I tried to connect to (internal & external). When I change the name of the connector, everything worked.
To test, I deleted this connection and created another one as the first - named the same as the network tried to connect to and it wrong on. When I renamed the connection, everything worked perfectly. It seems that Windows 7 is lost when you name the connector, the same as the destination network FULL domain name.
-
Problem with remote access VPN
Hello
I installed a remote access VPN on my firewall ASA5505 via the ASDM Assistant.
I can successfully connect with the Cisco VPN client. My firewall also shows me the VPN session and shows the Rx packets. However, Tx packets remain 0, so no traffic is getting out. My ASA5505 is configured as a router on a stick with 25 different VLAN. I want to restrict traffic to one VLAN specific using a card encryption.
When I run a command to ping t on my connected Windows box, the firewall log shows me the following message:
"Unable to find political IKE initiator: outside Intf, Src: 10.7.11.18, Dst: ' 172.16.1.1
"This message indicates that the fast path IPSec processing a packet that triggered of IKE, but IKE policy research has failed. This error could be associated calendar. The ACL triggering IKE could have been deleted before IKE has processed the request for initiation. "This problem will likely correct itself."
Unfortunately, the problem is correct.
The "sh cry isa his" and "sh cry ips its ' commands show the following output:
2 IKE peers: 62.140.137.99
Type: user role: answering machine
Generate a new key: no State: AM_ACTIVE
Interface: outside
Tag crypto map: SYSTEM_DEFAULT_CRYPTO_MAP, seq num: 65535, local addr: 85.17.xxx.xxx (outside interface IP)
local ident (addr, mask, prot, port): (0.0.0.0/0.0.0.0/0/0)
Remote ident (addr, mask, prot, port): (172.16.1.1/255.255.255.255/0/0)
current_peer: 62.140.137.99, username: eclipsevpn
dynamic allocated peer ip: 172.16.1.1
#pkts program: encrypt 0, #pkts: 0, #pkts digest: 0
#pkts decaps: 4351, #pkts decrypt: 4351, #pkts check: 4351
compressed #pkts: 0, unzipped #pkts: 0
#pkts uncompressed: 0, comp #pkts failed: 0, #pkts Dang failed: 0
success #frag before: 0, failures before #frag: 0, #fragments created: 0
Sent #PMTUs: 0, #PMTUs rcvd: 0, reassembly: 20th century / of frgs #decapsulated: 0
#send errors: 0, #recv errors: 0
local crypto endpt. : 85.17.xxx.xxx/4500, remote Start crypto. : 62.140.137.99/3698
Path mtu 1500, fresh ipsec generals 82, media, mtu 1500
current outbound SPI: B3D60F71
current inbound SPI: B89BA14A
SAS of the esp on arrival:
SPI: 0xB89BA14A (3097207114)
transform: aes - esp esp-sha-hmac no compression
running parameters = {RA, Tunnel, NAT-T program,}
slot: 0, id_conn: 196608, crypto-card: SYSTEM_DEFAULT_CRYPTO_MAP
calendar of his: service life remaining key (s): 25126
Size IV: 16 bytes
support for replay detection: Y
Anti-replay bitmap:
0xFFE1FFF8 0xFFFFFFFF
outgoing esp sas:
SPI: 0xB3D60F71 (3017150321)
transform: aes - esp esp-sha-hmac no compression
running parameters = {RA, Tunnel, NAT-T program,}
slot: 0, id_conn: 196608, crypto-card: SYSTEM_DEFAULT_CRYPTO_MAP
calendar of his: service life remaining key (s): 25126
Size IV: 16 bytes
support for replay detection: Y
Anti-replay bitmap:
0x00000000 0x00000001
I really have no idea what's going on. I installed a remote access VPN countless times, but this time it shows me the error as described above.
Hi Martijn,
just a few quick thoughts:
-is your ok NAT exemption, i.e. ensure that the return traffic is not NAT' ed.
-Make sure that there is no overlap crypto ACL
-When connected, make a package tracer to see what is happening with the return packages.
for example
packet-tracer in the interface within the icmp 10.7.11.18 0 0 172.16.1.1 detail
(where is the name of the interface on which 10.7.11.18 resides)
This will show you all the steps the rail package in-house (routing, nat, encryption etc.) so it should give you an idea of what is happening, for example when it comes to the bad interface, nat evil rule, wrong entry card crypto etc.
HTH
Herbert
-
Help, please! Cannot access the web after connected to the VPN
Hello
I'm a newbie on Cisco products. I configured a Cisco ASA 5505 with VPN firewall. However, I can't access the web after I connected to the remote IPSec VPN. I also cannot connect to the bands using the intellectual property. But I can connect to the internal servers in the office with no problems.
Here is my setup, can someone help please? Thank you very much
ASA Version 8.2 (5)
!
host name asa
xxxxxxxxx.com domain name
enable the encrypted password xxxxxxxxxxx
xxxxxxxxxxx encrypted passwd
names of
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
interface Vlan1
nameif inside
security-level 100
IP 192.168.1.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
IP address dhcp setroute
!
passive FTP mode
area of zone clock - 8 schedule
clock summer-time recurring PDT 1 Sun Apr 02:00 last Sun Oct 02:00
DNS lookup field inside
DNS server-group DefaultDNS
Server name 107.204.233.222
name-server 192.168.1.3
xxxxxxxxx.com domain name
inside_nat0_outbound list of allowed ip extended access all 192.168.1.96 255.255.255.240
pager lines 24
Enable logging
asdm of logging of information
Within 1500 MTU
Outside 1500 MTU
IP local pool sc-192.168.1.100 - 192.168.1.110 mask 255.255.255.0
ICMP unreachable rate-limit 1 burst-size 1
don't allow no asdm history
ARP timeout 14400
Global 1 interface (outside)
NAT (inside) 0-list of access inside_nat0_outbound
NAT (inside) 1 192.168.1.0 255.255.255.0
NAT (inside) 1 0.0.0.0 0.0.0.0
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
Floating conn timeout 0:00:00
dynamic-access-policy-registration DfltAccessPolicy
the ssh LOCAL console AAA authentication
Enable http server
http 192.168.1.0 255.255.255.0 inside
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
Crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
Crypto ipsec transform-set ESP-DES-SHA esp - esp-sha-hmac
Crypto ipsec transform-set ESP-DES-MD5 esp - esp-md5-hmac
Crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
Crypto ipsec transform-set ESP-3DES-MD5-esp-3des esp-md5-hmac
Crypto ipsec transform-set ESP-AES-256-SHA 256 - aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-SHA aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-MD5-esp - aes esp-md5-hmac
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 pfs Group1 set
Crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 value transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA MD5-ESP-3DES ESP-DES-SHA ESP-DES-MD5
outside_map card crypto 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
outside_map interface card crypto outside
Crypto ca trustpoint _SmartCallHome_ServerCA
Configure CRL
crypto ISAKMP allow outside
crypto ISAKMP policy 10
preshared authentication
3des encryption
sha hash
Group 2
life 86400
Telnet timeout 5
SSH 192.168.1.0 255.255.255.0 inside
SSH timeout 5
Console timeout 0
interface ID client DHCP-client to the outside
dhcpd outside auto_config
!
dhcpd address 192.168.1.5 - 192.168.1.36 inside
dhcpd dns 107.204.233.222 inside the 192.168.1.3 interface
dhcpd allow inside
!
a basic threat threat detection
Statistics-list of access threat detection
no statistical threat detection tcp-interception
WebVPN
internal strategy group xxxxxxxx-sc
attributes of xxxxxxxx-sc group policy
value of 107.204.233.222 DNS server 192.168.1.3
Protocol-tunnel-VPN IPSec
XXXXXXXXXX.com value by default-field
xxxxx xxxxxxxxxxx encrypted password username
Strategy Group-VPN-xxxxxxxx-sc
remote access to tunnel-group xxxxxxxx-sc type
attributes global-tunnel-group xxxxxxxx-sc
address sc-pool pool
Group Policy - by default-xxxxxxxx-sc
tunnel-group xxxxxxxx-sc ipsec-attributes
pre-shared key *.
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
maximum message length automatic of customer
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the rsh
inspect the rtsp
inspect esmtp
inspect sqlnet
inspect the skinny
inspect sunrpc
inspect xdmcp
inspect the sip
inspect the netbios
inspect the tftp
Review the ip options
!
global service-policy global_policy
context of prompt hostname
call-home service
anonymous reporting remote call
call-home
contact-email-addr [email protected] / * /
Profile of CiscoTAC-1
http https://tools.cisco.com/its/service/oddce/services/DDCEService destination address
email address of destination [email protected] / * /
destination-mode http transport
Subscribe to alert-group diagnosis
Subscribe to alert-group environment
Subscribe to alert-group monthly periodic inventory
monthly periodicals to subscribe to alert-group configuration
daily periodic subscribe to alert-group telemetry
Cryptochecksum:5c1c99b09fb26fcc36a8bf7206af8e02
: end
Hello
Try adding the following commands
permit same-security-traffic intra-interface
NAT (outside) 1 192.168.1.96 255.255.255.240
Is there are always problems with VPN then I would maybe change VPN pool to anything other than something that comes into conflict with the LAN.
In this case, these configurations should do the trick
In order from top to bottom, they would do the following things
- First remove the pool VPN and VPN configurations
- Then remove the VPN pool
- Remake of the VPN Pool with different network
- Reattach the VPN pool for VPN configurations
- Configure NAT0 to the new cluster of VPN
- Remove the old line of the ACL of the configuration of NAT0
attributes global-tunnel-group xxxxxxxx-sc
no address-sc-swimming pool
no ip local pool sc 192.168.1.100 - 192.168.1.110 mask 255.255.255.0
IP local pool sc-192.168.2.10 - 192.168.2.254 mask 255.255.255.0
attributes global-tunnel-group xxxxxxxx-sc
address sc-pool pool
inside_nat0_outbound to access ip 192.168.1.0 scope list allow 255.255.255.0 192.168.2.0 255.255.255.0
no access list inside_nat0_outbound extended permits all ip 192.168.1.96 255.255.255.240
Of course you also have the NAT configuration for VPN pools new Internet traffic
NAT (outside) 1 192.168.2.0 255.255.255.0
Please rate if the information has been useful if this resolved the issue as mark responded.
-Jouni
-
problem with windows 2003 vpn servers. and xp pro clients vpn using bridge nic
I have installed 2 guests windows 2003 on 2 laptops. both are configured with 1 CC of backend and frontend 1 nat/vpn server that has 2 interfaces, a bridge and one configured for host only.
I configure nat on both servers windows 2003 rras and vpn services and have them connected to my local network. they are able to access internet, ping between them and other computers on the network, as well as the host systems on which they run.
the problem is that I am not able to connect to the vpn servers remotely from inside a guest virtual machine. I wanted to try a vpn site-to site between the guests 2 windows 2003, but the operation failed.
I then tested customer to type of a guest virtual computer pro xp vpn server. It is also a failure.
but I discovered that if I initiate a VPN from any one of the host computer system laptop or another computer on the physical network I am able to connect to the vpn servers I have set up.
I wish I could have these laptops to operate normally and
time to time be able to turn on virtual machines with vpn
servers and test as dfs things and replication active directory as if
they were running 2 separate real-world offices. the two laptops have invited Setup for 192.168.0.0 networks with subnet mask 255.255.255.192. each host that it supposed to be running a 1 subnet for the popular virtual machine with the servers vpn/nat connect together the 2 sites.
laptop computers are running xp pro and vista ultimate as the host systems. I'm only using the windows firewall but also tested with them disabled vpn connections. also launches the service ipsec on laptops to secure internal lan traffic, I have also tested with two guests with disabled ipsec.
is there something I'm missing here with the installation of the vmware bridge network?
Oh I forgot to mention, I test using pptp and ms-chap v2
I managed to do work by unchecking the tcp/ip settings and the microsoft file sharing on the bridged NIC resaeau.
now it works very well but who explain to me why it cannot work when you are using the same network as the host card. they all have two different ip addresses and mac addresses. but something seems to be in conflict
-
Drives and airport Extreme Base Station to disconnect after connection to the VPN
At home when I'm on WIFI, everything works fine. At the moment where I connect to the VPN to do office work, the base station will disconnect and accessible either.
Any help?
The problem you are experiencing is perhaps due to the type of VPN tunnel that you use to connect to your workplace. There are basically two types: 1) full or partial) 2. Note: The different VPN clients can use other words, but these are usually options when you set up a tunnel.
When you use a complete tunnel, all traffic between your computer and the VPN of your working server, through the tunnel. No traffic is allowed on your local network, and therefore, all local resources are not available. With a partial tunnel, your computer data traffic, may as well go through the tunnel and also to your local network. One reason to use a partial tunnel, for example, is that you have a local printer, you need to perform printing. You can be connected to this type of tunnel for access to the documents and then, be able to print on this printer... otherwise, with a tunnel of full, you would print to a printer at your place of work.
-
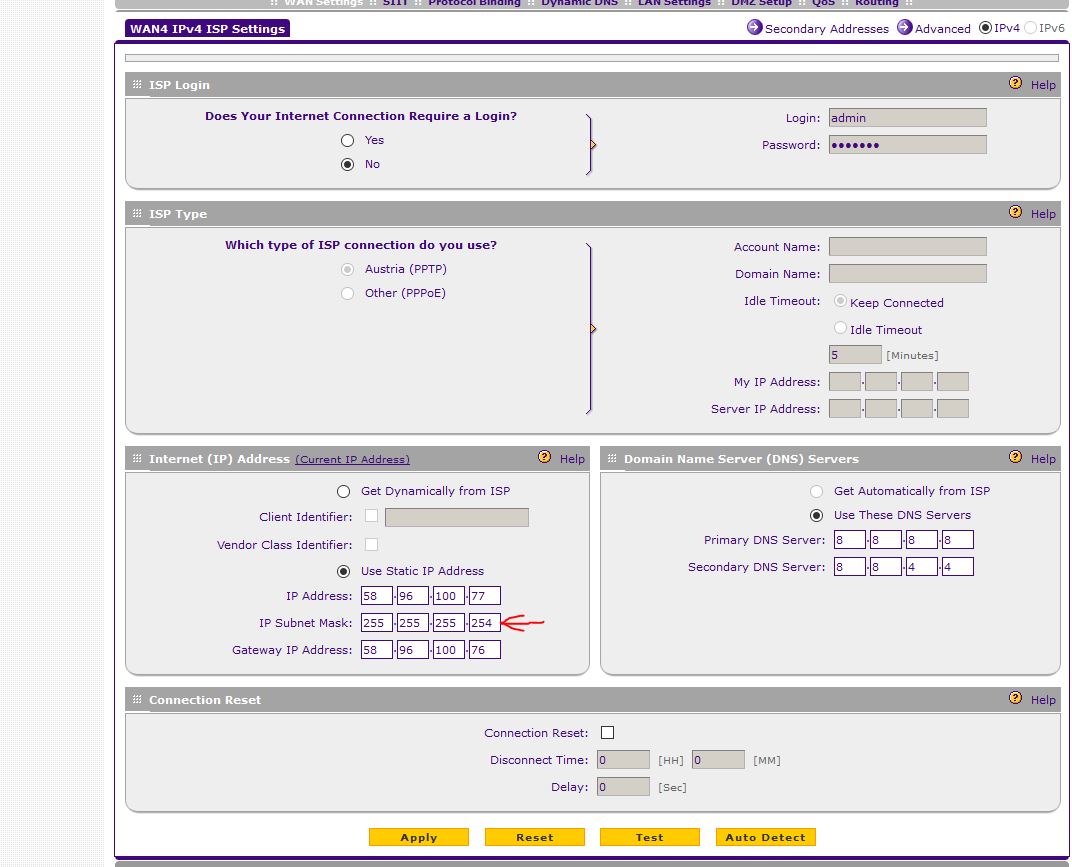
I can't add/subnet mask 31 255.255.255.254 ISP WAN > static IP setting in VPN Firewall SRX5308
Hello
I can't add/subnet mask 31 255.255.255.254 ISP WAN > static IP setting in VPN Firewall SRX5308. When I try to apply it, I get the popup error message like "invalid IP subnet mask. Please enter 0/128/192/224/240/248/252 for octet 4 ". I try to add provider NTU fiber optic internet service in one of the 4 WAN settings. The vendor gave me a 31 block IP and the subnet as 255.255.255.254 mask. It is a limitation in this firewall? I have to ask the provider to give me a 30 block the IP instead? With 30 block IP subnet mask will be 255.255.255.252 who is authorized by this firewall setting. I tried this on another (SnapGear SG560) firewall and it works without any problem. See the screenshots below. Can someone please?
concerning
Ridwan
/ 31 would be used in specific scenarios where you * really * need to keep the address space and on links only point to point. To be honest I've never met anyone, or any ISP that uses it. It works on point to point, because, well, there no need to broadcast address because there are only two devices on the link (one on each side of the cable)... IP address ranges would be;. 0-. 1,.2-. 3, etc.
Most (if not all) Netgear devices will prevent you from setting 31, but you will probably be able to use without problem in all 30 cases, according to the setup of the ISP I do not think that it would cause you problems really. But if you can, I would certainly ask a 30 instead.
Maybe you are looking for
-
Excite Pro - can not download fles on 32GB SD card
Hello I bought a 32 GB sd for the shelf card, but when I try to download something directly on the sd card I get an error like "no such file or directory". In file manager, I can copy and paste files from or to the sd card normally. For what I read,
-
'Fun' with snapshots do not delete
Hey everone I am clearly again and I tried to post not unless I really need help. Here's my situation. I spend 4 Bay NAS Bay 6 316 (really like it so far... if I could only utorrent works... but that's another post). I ran out of space during the tra
-
What is the brand name of the HP ENVY - 17 t 1 TB 5400 RPM HDD hybrid?
Hello I need help to identify the commercial name or the manufacturer of the • 1 TB 5400 RPM, a hard drive hybrid for the HP ENVY - 17 t with the manufacturer: G0U59AV. Looking forward for your reply. Thank you very much.
-
Helps the bad Image DLL C: Windows
Help can some please tell Me what I have to challenge these error messages whenever I connect to my pc I get them 1 Logi_MwX, Exe - bad Image The application or DLL C:\WINDOWS\system32\tuvtttTN.dll is not a valid WINDOWS image Check against your flop
-
How can I set the format of Windows Media Center at 16:10 in other than the full screen?
How can I set the format of Windows Media Center in Vista at 16:10 in other than the full screen? I use a screen as secondary display 1680x1050px.