Tunnel of speaks of talking DMVPN routing via hub
I have a DMVPN network with several linked sites and everything works fine, with one exception. Two sites (which can connect spoke to speak perfectly well to all other spoke routers in the network) can not directly connect and route the traffic through the hub. Routing tables (EIGRP) you will see the routes are properly being announced, however see the PNDH ip indicates the following
Router 1 (spoke router initiateing the connection)
10.31.248.246/32 by 10.31.248.246, created Tunnel10 00:00:25, expire 00:09:34
Type: dynamic, flags: implicit router
The NBMA Address: * address of Router 2 *.
(non-socket)
2 router (router talk recipient)
10.31.248.244/32 via 10.31.248.244
Tunnel10 created at 00:01:53, expire 00:01:12
Type: dynamic, flags: temporary
The NBMA Address: * address of our server DMVPN router *.
Any help to fix this would be extremely appreciated because the two offices are in Asia and our server router is the United States which means a round-trip time which should be approximately 50 ms between those offices is actually taking more than 400 ms
Hello
What happens, is that ROUTER1 already resolved correctly ROUTER2 via PNDH, but for some reason any cannot establish IPsec to send a response of PNDH to Router 2.
Can you check if ISAKMP/IPsec between these two routers trying to establish when you ping from one side to the other? My guess is you'll see MM_NO_STATE ;-)
M.
Tags: Cisco Security
Similar Questions
-
PIX v7 speaks to talk about vpn access via the hub of pix
Hello
Does anyone know if the v7 PIX code supports the overs speaks of talking about VPN connectivity?
For example, 3 sites, Hub, to talk to and A of spoke spoke of b and B connect in the hub (PIX) with VPN.
With earlier versions of the software, the rays would not be able to communicate. Is this possible with the new version of the code?
Thank you
Hello
As long as the hub is running v7, you should be able to do. See
for an example.
HTH
Kind regards
Cathy
-
DMVPN and INTERNET VIA HUB RENTAL ISSUES
Hello everyone,
I really wish you can help me with the problem I have.
I explain. I test a double Hub - double DMVPN Layout for a client before we set it up in actual production.
The client has sites where routers are behind some ISP routers who do NAT.
How things are configured:
-All rays traffic must go through the location of the hub if no local internet traffic on the rays.
-Hub 1 and 2 hub sends a default route to rays through EIGRP. But only Hub 1 is used.
-Hub 1 is the main router to DMVPN. In case of connection / hardware failure of the Internet Hub 2 become active for DMVPN and Internet.
-Hub 1 and 2 hub are both connected to an ISP and Internet gateway for rays.
-Hub 1 and 2 hub are configured with IOS Firewall.
-On the shelves I used VRF for separate DMVPN routning Global routning table so I could receive a default route of 1 Hub and Hub 2 to carry the traffic of rays to the Internet via the location of the hubWhat works:
-All rays can have access to the local network to the location of the hub.
-All the rays can do talk of talk
-Working for DMVPN failover
-Rais NOT behind the router NAT ISP (i.e. the public IP address) directly related to their external interface can go Internet via hub location and all packages are inspected properly by the IOS and Nat firewall properly
What does not work:-Rays behind the NAT ISP router can not access Internet via Hub location. They can reach a local network to the location of the hub and talk of talks.
IOS Firewall Router hub shows packages from rays of theses (behind a NAT) with a source IP address that is the router og PSI of public IP address outside the interface. Not the private address LAN IP back spoke.
In addition, the packets are never natted. If I do some captge on an Internet Server, the private source IP is the IP LAN to the LAN behind the rays. This means that the hub, router nat never these packages.How to solve this problem?
/ * Style definitions * / table. MsoNormalTable {mso-style-name : « Tabel - Normal » ; mso-tstyle-rowband-taille : 0 ; mso-tstyle-colband-taille : 0 ; mso-style-noshow:yes ; mso-style-priorité : 99 ; mso-style-qformat:yes ; mso-style-parent : » « ;" mso-rembourrage-alt : 0 cm 5.4pt cm 0 5.4pt ; mso-para-margin : 0 cm ; mso-para-marge-bottom : .0001pt ; mso-pagination : widow-orphelin ; police-taille : 11.0pt ; famille de police : « Calibri », « sans-serif » ; mso-ascii-font-family : Calibri ; mso-ascii-theme-font : minor-latin ; mso-fareast-font-family : « Times New Roman » ; mso-fareast-theme-font : minor-fareast ; mso-hansi-font-family : Calibri ; mso-hansi-theme-font : minor-latin ; mso-bidi-font-family : « Times New Roman » ; mso-bidi-theme-font : minor-bidi ;}
Well I don't know that's why I need your help/advice :-)
I don't know that if I have to configure a VRF on the location of the hub gets also like things might mess upward.
The problem seems to be NAT - T the rays that are not behind a NAT, among which go over the Internet through a Hub and inspection of Cisco IOS and NAT are trying to find.
I tested today with the customer at the start them talking behind nat could ping different server on the Internet but not open an HTTP session. DNS was to find work. The IOS Firewall has been actually
inspection of packages with private real IP address. Then I thought it was a MTU issue, so I decided to do a ping on the Internet with the largest MTU size and suddenly the pings were no more.
I could see on the router Hub1 IOS Firewall was inspecting the public IP of the ISP NAT router again alongside with rays and not more than the actual IP address private. Really strange!
Attached files:
I attach the following files: a drawing of configuration called drawing-Lab - Setup.jpeg | All files for HUB1, BRANCH1 and BRANCH2 ISP-ROUTER configs, named respectively: HUB1.txt, BRANCH1.txt, BRANCH2.txt and ISP - ROUTER .txt
Hub1 newspapers when ping host 200.200.200.200 on the Internet of Branch2 (behind the NAT ISP router):
Branch2 #ping vrf DMVPN-VRF 200.200.200.200 source vlan 100
Type to abort escape sequence.
Send 5, echoes ICMP 100 bytes to 200.200.200.200, time-out is 2 seconds:
Packet sent with a source address of 192.168.110.1
.....
Success rate is 0% (0/5)* 06:04:51.017 Jul 15 UTC: % FW-6-SESS_AUDIT_TRAIL_START: start session icmp: initiator (110.10.10.2:8) - answering machine (200.200.200.200:0)
If the IOS Firewall does not inspect the true private source IP address that can be, in this case: 192.168.110.2. He sess on the public IP address.
HUB1 #sh ip nat translations
Inside global internal local outside global local outdoor Pro
ICMP 80.10.10.2:1 80.10.10.2:1 100.10.10.2:1 100.10.10.2:1
ICMP 80.10.10.2:2 80.10.10.2:2 110.10.10.2:2 110.10.10.2:2
UDP 80.10.10.2:4500 80.10.10.2:4500 110.10.10.2:4500 110.10.10.2:4500There is no entry for packets of teas present NAT
Captge on Tunnel 1 on Hub1 interface (incoming packets in):
7 7.355997 192.168.110.1 200.200.200.200 request ICMP (ping) echo
So that the firewall controllable IOS to the 110.10.10.2:8 public IP sniffing capture said that the package come from private real IP addressInhalation of vapours on the server (200.200.200.200) with wireshark:
114 14.123552 192.168.110.1 200.200.200.200 request ICMP (ping) echo
If the private IP address of source between local network of BRANCH2 is never natted by HUB1
If the server sees the address source IP private not natted although firewall IOS Hub1 inspect the public IP address 110.10.10.2:8
Hub1 newspapers when ping host 200.200.200.200 on the Internet of Branch1 (not behind the NAT ISP router):
Branch1 #ping vrf DMVPN-VRF 200.200.200.200 source vlan 100
Type to abort escape sequence.
Send 5, echoes ICMP 100 bytes to 200.200.200.200, time-out is 2 seconds:
Packet sent with a source 192.168.100.1 address
!!!!!* 06:05:18.217 Jul 15 UTC: % FW-6-SESS_AUDIT_TRAIL_START: start session icmp: initiator (192.168.100.1:8) - answering machine (200.200.200.200:0)
This is so the firewall sees the actual private IP which is 192.168.100.1
HUB1 #sh ip nat translations
Inside global internal local outside global local outdoor Pro
ICMP 80.10.10.2:1 80.10.10.2:1 100.10.10.2:1 100.10.10.2:1
ICMP 80.10.10.2:2 80.10.10.2:2 110.10.10.2:2 110.10.10.2:2
UDP 80.10.10.2:4500 80.10.10.2:4500 110.10.10.2:4500 110.10.10.2:4500
ICMP 80.10.10.2:22 192.168.100.1:22 200.200.200.200:22 200.200.200.200:22The real private source IP address is also find natted 1 Hub outside the public IP address
Captge on Tunnel 1 on Hub1 interface (incoming packets in):
8 7.379997 192.168.100.1 200.200.200.200 request ICMP (ping) echo
Real same as inspected by IOS Firewall so all private IP address is y find.
Inhalation of vapours on the server (200.200.200.200) with wireshark:
/ * Style definitions * / table. MsoNormalTable {mso-style-name : « Tabel - Normal » ; mso-tstyle-rowband-taille : 0 ; mso-tstyle-colband-taille : 0 ; mso-style-noshow:yes ; mso-style-priorité : 99 ; mso-style-qformat:yes ; mso-style-parent : » « ;" mso-rembourrage-alt : 0 cm 5.4pt cm 0 5.4pt ; mso-para-margin : 0 cm ; mso-para-marge-bottom : .0001pt ; mso-pagination : widow-orphelin ; police-taille : 11.0pt ; famille de police : « Calibri », « sans-serif » ; mso-ascii-font-family : Calibri ; mso-ascii-theme-font : minor-latin ; mso-fareast-font-family : « Times New Roman » ; mso-fareast-theme-font : minor-fareast ; mso-hansi-font-family : Calibri ; mso-hansi-theme-font : minor-latin ; mso-bidi-font-family : « Times New Roman » ; mso-bidi-theme-font : minor-bidi ;}
67 10.441153 80.10.10.2 200.200.200.200 request ICMP (ping) echo
So, here's all right. The address is natted correctly.
__________________________________________________________________________________________
Best regards
Laurent
Hello
Just saw your message, I hope this isn't too late.
I don't know what your exact problem, but I think we can work through it to understand it.
One thing I noticed was that your NAT ACL is too general. You need to make it more
specific. In particular, you want to make sure that it does not match the coming of VPN traffic
in to / out of the router.
For example you should not really have one of these entries in your NAT translation table.
HUB1 #sh ip nat translations
Inside global internal local outside global local outdoor Pro
ICMP 80.10.10.2:1 80.10.10.2:1 100.10.10.2:1 100.10.10.2:1
ICMP 80.10.10.2:2 80.10.10.2:2 110.10.10.2:2 110.10.10.2:2
UDP 80.10.10.2:4500 80.10.10.2:4500 110.10.10.2:4500 110.10.10.2:4500Instead use:
Nat extended IP access list
deny ip any 192.168.0.0 0.0.255.255 connect
allow an ip
deny ip any any newspaperIf you can use:
Nat extended IP access list
deny ip 192.168.0.0 0.0.255.255 192.168.0.0 0.0.255.255 connect
IP 192.168.0.0 allow 0.0.255.255 everything
deny ip any any newspaperAlso, I would be very careful with the help of the "log" keyword in an ACL, NAT.
I saw problems.
What are the IOS versions do you use?
Try to make changes to the NAT so that you no longer see the entries of translation NAT
for packages of NAT - T (UDP 4500) in the table of translation NAT on the hub. It may be
This puts a flag on the package structure, that IOS Firewall and NAT is
pick up on and then do the wrong thing in this case.
If this does not work then let me know.
Maybe it's something for which you will need to open a TAC case so that we can
This debug directly on your installation.
Mike.
-
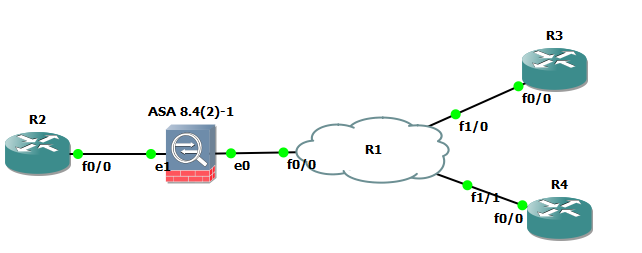
DMVPN router behind ASA - need help please.
Hello
After reading many other discussions on this topic, it appears with the correct IOS and NAT - T active router, you bring up DMVPN behind a NAT device.
I tried to perform this task, but I can not even phase 1 going to the DMVPN. The routing was checked and I can ping the routers DMVPN public IP. I'm sure that the configurations for routers are good, but asked if any additional NAT is required on the ASA.
Here is the topology:
Plate rotating DMVPN > ASA > Internet > ASA > DMVPN Branch
The SAA on the side of the hub is in our data center and in production with several site-to-site and traffic to DMZ. Devices DMVPN is a Cisco 2921 and 1921. When I run a "debug crypto isakmp" on both routers, I see ISAKMP messages are sent on the branch DMVPN router. Nothing in the hub and no hits on the ASA ACL. I tried both the public IP address and the private IP address of the ACL on the ASA.
I have attached the relevant training and can post more if necessary.
Thank you
Brandon
Hello
I finally had time to laboratory it.
I used this topology:
I have
ASA (config) # sh run nat
NAT (INSIDE, OUTSIDE) static source HUB-ROUTER-REAL-IP interface service udp-eq-4500 udp-eq-4500
NAT (INSIDE, OUTSIDE) static source HUB-ROUTER-REAL-IP interface service udp-eq-500 udp-eq-500
!
object network HUB
dynamic NAT interface (INSIDE, OUTSIDE)ASA (config) # sh run access-list
extended OUTSIDE permitted udp access list any HUB-ROUTER-REAL-IP eq isakmp object
list access extended OUTSIDE permitted udp any eq HUB-ROUTER-REAL-IP 4500R2 #sh run inter t0
interface Tunnel0
172.16.0.1 IP address 255.255.255.0
no ip redirection
no ip next-hop-self eigrp 1
no ip split horizon eigrp 1
dynamic multicast of IP PNDH map
PNDH id network IP-99
source of tunnel FastEthernet0/0
multipoint gre tunnel mode
tunnel key 100000
Tunnel ipsec DMVPN-IPSEC-PROFILE protection profileSo it should be the same configuration that you use.
The only thing is that I had to ' stop/no shut' tunnel interface and removing some config that I also need to clear the connection on the ASA using "clear conn."
R2 #sh dmvpn
Legend: Attrb--> S - static, D - dynamic, I - incomplete
Local N - using a NAT, L-, X - no Socket
# Ent--> entries number of the PNDH with same counterpart NBMA
State of the NHS: E--> RSVPs, R--> answer, W--> waiting
UpDn time--> upward or down time for a Tunnel
==========================================================================Interface: Tunnel0, IPv4 PNDH details
Type: hub, PNDH peers: 2,.# Ent Peer NBMA Peer Tunnel Addr add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
1 200.20.0.10 172.16.0.2 UNTIL 00:11:28
1 200.30.0.10 172.16.0.3 AT 00:11:22R2 #.
-
Printer Officejet 6500 E709a wire to the router via USB
Can I connect my Officejet 6500 E709a via the USB connection to my router 9100EM Ultraline series 3 model so that it can be seen by both of my PC, which is connected directly to the router via LAN Ethernet ports? If so, what measures are necessary? At the present time, the printer is connected via USB to a PC and the other PC cannot use the printer, unless the first PC is on.
I gave up on the online software update from HP for the Officejet 6500 E709a and removed it. So, I just use my old CD to install the printer, this time to install it as a printer wired ethernet, which worked. Thanks for trying to help.
-
I have my printer connected to my router via a usb cable. I also have my (Vista) computer connected to the router by ethernet cable. How can I set the computer to print to my printer via the router?
Usually, you need to install the printing software / drivers on your PC, configured / installed specially for a printer "remote" (its an option in the installation of the printer software)
-
Migration phase 3 DMVPN with Central Hub
I'm looking at the migration of my network DMVPN phase 2 phase 3. The current system contains 3 regional poles each serving about 100 rays. The final goal is to be able to build tunnels speaks to talk between sites that are hosted to the hubs in different regions. I understand from reading the document "Migrating from Dynamic Multipoint VPN Phase 2 phase 3" regional poles of phase 3 can be related in a hierarchy through a central hub, but there are no details in the doc and I was not able to find a white paper that addresses this specifically. Someone at - it experience with this topology or have the material regarding the deployment and configuration of nodal point?
Kind regards
Mike
Mike,
DMVPN phase 3 is still a valid design choice, even if we are heading for FlexVPN/IKEv2 combo (eventually finished on ASRs)
That being said, the deployment is quite easy:
-Shortcuts PNDH (+ redirect PNDH, really unnecessary during stable operation) on the shelves
-Redirect PNDH on the hubs.
Generally on regional hubs you would have a tunnel interface to the rays and the other (like talking) tunnel to the global hubs, remember that they must belong to the same network PNDH (i.e. same id PNDH network).
Now according to your choice Routing Protocol (BGP dimensionnera better, obviously), it's just a matter of right summarized advertising and setting the delays and costs.
The top level I know, if you want to read, google "BRKSEC DMVPN" you will find some different item of Cisco Live/Networkes of the past - my resource of choice.
M.
-
(1) if I understand correctly - Phase 1 DMVPN is Star technology. Is it possible to use two hubs of the network?
(2) is it possible to use the router 1841 as Phase 1 DMVPN hub?
(3) imagine this network topology:
* PIX *-(static vpn tunnel)-> router 1841 (hub)-(dynamic vpn tunnel)-> rays.
I'm having problems with routing in VPN between PIX and rays through 1841?
In the attachment, see diagram.
Thnx in advance!
Hello
It should be possible. The tunnel between the PIX and Hub 2 is going to be a regular with PIX IPSEC tunnel configured with all networks to talk as destination the ACL crypto and vice versa on the hub. Hub 2 will have a static route for the private subnet route tis and PIX will be redestributed in the routing process so that it is announced to the rays. Please keep in mind that the protection tunnel profile you are configuring should have configured 'shared' keyword.
HTH,
Please rate if this can help.
Kind regards
Kamal
-
Speaking of talk (VIGOR to CISCO) routing
Hi all
I have a problem with my config, it's a 7 rays star configuration. The address of the network hub is the 192.168.6.0.
I wish that sites spoke to communicate to other rays through the hub. The site talks are the routers of the force and the hub is a cisco 1842, the routing table is present on the vigors. I assume it's an ACL problem, but I've spent the last 3 hours trying figure this one and got no where, can anyone help?
I also nat has ports 80, 443, that work very well from outside the local network, but do not work inside? Anyone got any suggestions?
Thank you
Mark
192.168.6.0 HUB
192.168.18.0 TALK
192.168.23.0 TALK
192.168.28.0 SPEAKS
192.168.48.0 TALK
192.168.78.0 TALK
192.168.88.0 TALK
192.168.108.0 TALK
10.0.0.0 SPEAKS
Current configuration: 4558 bytes
!
version 12.4
horodateurs service debug datetime msec
Log service timestamps datetime msec
no password encryption service
!
BURTON hostname
!
boot-start-marker
boot-end-marker
!
enable secret 5 xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
activate the password xxxxxxxxxxxxxx
!
No aaa new-model
IP cef
!
!
property intellectual auth-proxy max-nodata-& 3
property intellectual admission max-nodata-& 3
!
!
name of the server IP 62.XX.x.2
name of the server IP 195.xxx.xxx.10
!
!
Crypto pki trustpoint TP-self-signed-692553461
enrollment selfsigned
name of the object cn = IOS - Self - signed - certificate - 692553461
revocation checking no
rsakeypair TP-self-signed-692553461
!
!
TP-self-signed-692553461 crypto pki certificate chain
certificate self-signed 01
308201A 5 A0030201 02020101 3082023C 300 D 0609 2A 864886 F70D0101 04050030
2 060355 04031325 494F532D 53656 C 66 2 AND 536967 6E65642D 43657274 30312E30
69666963 36393235 35333436 31301E17 313031 31323530 39353934 0D 6174652D
315A170D 2E302C06 1325494F 03550403 32303031 30313030 30303030 5A 303031
532D 5365 6C662D53 69676E65 4365 72746966 69636174 652 3639 32353533 642D
06092A 86 4886F70D 01010105 34363130 819F300D 0003818D 00308xxx 02818100
BA51CDF7 D418D270 7DCE516E 1ADE6DF5 82FE4507 CD1EBE0A 4B6E4B15 9A3C20ED
B1D19FC9 63D0B925 0A4611FF CE8D935C 264FC3FE DF8BFAC2 76EC38ED 68115F43
20A68D85 C04A564E 8BDE86FE 127F79B4 8E123D9C 8430940C BCD5CDA4 ADAAE387
FA1E14A6 ECF92197 0CF54E89 B33915E7 A4E01EC7 CE45DDF6 AA60D168 38C92E67
02030100 01A 36630 03551 D 13 64300F06 0101FF04 05300301 01FF3011 0603551D
11040A 30 08820642 5552544F 4E301F06 23 04183016 03551D 8014645E 3FDE4E90
A8773580 81EE4217 F4821238 993A301D 0603551D 0E041604 14645E3F DE4E90A8
77358081 EE4217F4 3A300D06 01040500 03818100 86F70D01 82123899 092A 8648
914EE910 C1EFCDB3 2C3B277B 45E4149F B8A78E94 94D6558F 7A1D5B45 D057DC02
1FCF0C28 5B29728B 9480E807 D7E7DF9E 751DD005 E108D94B 6B3FC03B 8EB1603B
9AF1E4CA 49067084 5B906C74 4D07217A 13FD0113 B721068A 3EC6C990 54101B4B
FC9860E4 3xxxB064 586EC91D EF7C5A8F 8BBF33C6 29BCF148 A7E2B987 F2A028F8
quit smoking
!
!
!
!
crypto ISAKMP policy 1
md5 hash
preshared authentication
Group 2
life 3600
!
crypto ISAKMP policy 5
BA 3des
md5 hash
preshared authentication
Group 2
ISAKMP crypto key xxxxxxxxxx address 77.xxx.xxx.176
ISAKMP crypto key xxxxxxxxxx address 85.xxx.xxx.85
ISAKMP crypto key xxxxxxxxxx address 85.xxx.xxx.9
ISAKMP crypto key xxxxxxxxxx address 85.xxx.xxx.81
ISAKMP crypto key xxxxxxxxxx address 85.xxx.xxx.228
ISAKMP crypto key xxxxxxxxxx address 85.xxx.xxx.153
ISAKMP crypto key xxxxxxxxxx address 85.xxx.xxx.10
ISAKMP crypto key xxxxxxxxxx address 85.xxx.xxx.61
!
!
Crypto ipsec transform-set esp-3des esp-sha-hmac 3DES-SHA
Crypto ipsec transform-set AES - SHA aes - esp esp-sha-hmac
Crypto ipsec transform-set compression-SHA-3DES esp-3des esp-hmac-sha-comp-lzs
Crypto ipsec transform-set AES-SHA-compression, hmac-sha-esp esp - aes comp-lzs
Crypto ipsec transform-set esp cm-transformset-1-esp-sha-hmac
Crypto ipsec transform-set esp - esp-sha-hmac this_should_work
!
card card-VPN-1 10 ipsec-isakmp crypto
the value of 77.xxx.xxx.176 peer
Set transform-set this_should_work
match the stores addresses
!
card crypto ipsec VPN - card - 1 isakmp 11
the value of 85.xxx.xxx.85 peer
Set transform-set this_should_work
match address dalby
!
card card-VPN-1 12 ipsec-isakmp crypto
the value of 85.xxx.xxx.9 peer
Set transform-set this_should_work
match address braintree
!
card card-VPN-1 13 ipsec-isakmp crypto
the value of 85.xxx.xxx.81 peer
Set transform-set this_should_work
match address corby
!
card card-VPN-1 14 ipsec-isakmp crypto
the value of 85.xxx.xxx.228 peer
Set transform-set this_should_work
match against glasgow
!
card card-VPN-1 15 ipsec-isakmp crypto
the value of 85.xxx.xxx.153 peer
Set transform-set this_should_work
match address hadleigh
!
card card-VPN-1 16 ipsec-isakmp crypto
the value of 85.xxx.xxx.10 peer
Set transform-set this_should_work
northwich match address
!
card card-VPN-1 17 ipsec-isakmp crypto
the value of 85.xxx.xxx.61 peer
Set transform-set this_should_work
match address wycombe
!
!
!
interface FastEthernet0/0
Description $ETH - LAN$
IP 192.168.6.40 255.255.255.0
IP nat inside
IP virtual-reassembly
automatic duplex
automatic speed
!
interface FastEthernet0/1
no ip address
Shutdown
automatic duplex
automatic speed
!
ATM0/0/0 interface
no ip address
no ip mroute-cache
No atm ilmi-keepalive
Bundle-enable
DSL-automatic operation mode
PVC 0/38
aal5mux encapsulation ppp Dialer
Dialer pool-member 1
!
!
ATM0/1/0 interface
no ip address
no ip mroute-cache
No atm ilmi-keepalive
Bundle-enable
DSL-automatic operation mode
PVC 0/38
aal5mux encapsulation ppp Dialer
Dialer pool-member 1
!
!
interface Dialer0
the negotiated IP address
NAT outside IP
IP virtual-reassembly
encapsulation ppp
Dialer pool 1
Dialer-Group 1
PPP reliable link
Authentication callin PPP chap Protocol
PPP chap hostname xxxxxxxxxxxxxxxxxxxxxxxxxxxxx
PPP chap password 0 xxxxxxxx
PPP ipcp dns request
reorganizes the PPP link
multilink PPP Panel
PPP multilink sliding 16 mru
period of PPP multilink fragment 10
Panel multilink PPP interleave
multiclass multilink PPP
card crypto card-VPN-1
!
IP forward-Protocol ND
IP route 0.0.0.0 0.0.0.0 Dialer0
!
IP http server
IP http secure server
overload of IP nat inside source list 100 interface Dialer0
!
corby extended IP access list
ip licensing 192.168.6.0 0.0.0.255 192.168.18.0 0.0.0.255
northwich extended IP access list
ip licensing 192.168.6.0 0.0.0.255 192.168.23.0 0.0.0.255
wycombe extended IP access list
ip licensing 192.168.6.0 0.0.0.255 192.168.28.0 0.0.0.255
hadleigh extended IP access list
ip licensing 192.168.6.0 0.0.0.255 192.168.48.0 0.0.0.255
extended IP access list stores
ip licensing 192.168.6.0 0.0.0.255 192.168.78.0 0.0.0.255
dalby extended IP access list
ip licensing 192.168.6.0 0.0.0.255 192.168.88.0 0.0.0.255
glasgow extended IP access list
ip licensing 192.168.6.0 0.0.0.255 192.168.108.0 0.0.0.255
braintree extended IP access list
ip licensing 192.168.6.0 0.0.0.255 10.0.0.0 0.0.0.255
IP Internet traffic inbound-ACL extended access list
permit any isakmp udp host 77.xxx.xxx.176 eq
allow a host 77.xxx.xxx.176 esp
permit any isakmp udp host 85.xxx.xxx.85 eq
allow a host 85.xxx.xxx.85 esp
permit any isakmp udp host 85.xxx.xxx.9 eq
allow a host 85.xxx.xxx.9 esp
permit any isakmp udp host 85.xxx.xxx.81 eq
allow a host 85.xxx.xxx.81 esp
permit any isakmp udp host 85.xxx.xxx.228 eq
allow a host 85.xxx.xxx.228 esp
permit any isakmp udp host 85.xxx.xxx.153 eq
allow a host 85.xxx.xxx.153 esp
permit any isakmp udp host 85.xxx.xxx.10 eq
allow a host 85.xxx.xxx.10 esp
permit any isakmp udp host 85.xxx.xxx.61 eq
allow a host 85.xxx.xxx.61 esp
!
access-list 100 deny ip 192.168.6.0 0.0.0.255 192.168.78.0 0.0.0.255
access-list 100 deny ip 192.168.6.0 0.0.0.255 192.168.88.0 0.0.0.255
access-list 100 deny ip 192.168.6.0 0.0.0.255 10.0.0.0 0.0.0.255
access-list 100 deny ip 192.168.6.0 0.0.0.255 192.168.18.0 0.0.0.255
access-list 100 deny ip 192.168.6.0 0.0.0.255 192.168.48.0 0.0.0.255
access-list 100 deny ip 192.168.6.0 0.0.0.255 192.168.23.0 0.0.0.255
access-list 100 deny ip 192.168.6.0 0.0.0.255 192.168.28.0 0.0.0.255
access-list 100 deny ip 192.168.6.0 0.0.0.255 192.168.108.0 0.0.0.255
access-list 100 permit ip 192.168.6.0 0.0.0.255 any
Dialer-list 1 ip protocol allow
public RO SNMP-server community
!
!
control plan
!
!
Line con 0
line to 0
line vty 0 4
password: xxxxxxxxxxxxxxx
opening of session
!
Scheduler allocate 20000 1000
end
Also check this important Information on Vigor holding ipsec his.
https://supportforums.Cisco.com/thread/257320?decorator=print&displayFullThread=true
Manish
-
L L VPN routing via alternative tunnel... mesh?
Hi all
We have a L - L IPSEC tunnel between our head office and a hosting company, everything works fine, solid as a rock. But we now have a requirement for one of our branches to also run a tunnel to the host, but for cost and control reasons, it was decided that the office will be forwarded via the head office...
We also have an IPSEC tunnel running between the head and branch if all we need to the whole running is to get the branch to move towards the hosting via the headquarters company and have been performed.
It would be like a mesh full, but with one of the deleted links (branch of accommodation), or a hybrid any? BTW both Headquarters and branch run Cisco ASA5550 and 5515 respectively and we have full control over these devices, the hosting company, I'm not sure but maybe an ASA...
Links to documentation or advice would be greatly appreciated...
Hello
Well I don't know how you have configured NAT configuration for traffic between the branch and accommodation.
It appears from the foregoing that you add is the real network of agencies for headquarters accommodation L2L VPN? If this is true, then need you a NAT configuration in the seat which is between "outside" and "outside". In other words a NAT0 configuration for the "outside" interface. (My suggesting original was to PAT dynamic for the branch if you want to avoid changes of configuration on the hosting Site)
It would probably be something first of all, I would like to check.
If it is fine, then I would check the VPN counters
That both of the L2L VPN connections
Show crypto ipsec peer his
This should show you if the L2L VPN has negotiated for networks of branch and hosting on both connections from VPN L2L. It could also tell you if the packets are flowing in both directions.
If the problem is outside your network then headquarters you would see probably décapsulés/decrypted only packets for VPN L2L headquarters - L2L BOVPN and only encapsulated/encrypted packets for the headquarters - hosting Site
-Jouni
-
Connection spoke to talking DMVPN
Hello world
You will need to confirm on DMVPN say if R1 is the hub and R2 and R3 are spoke.
Need to talk to R3, R2 if it will use PNDH and go via R1 to R3?
Is it possible that R2 R3 can talk directly using PNDH?
Concerning
MAhesh
You mix a few features here:
PNDH is used in a DMVPN to save the rays on the hub and give them the opportunity to ask the hub speaks real addresses. With that, PNDH is always between the spokes and the hub. Just see this under the control of the traffic. There is no need to takl speaks to a spoken here.
When the ray is aware of the public IP address different sticks he wanted him to talk, then the IPSec connection is buid directly between the spokes.
Sent by Cisco Support technique iPad App
-
Why key tunnel must be same in DMVPN
Hello world
need to understand why key tunnel must be the same between all routers in the DMVPN?
Thank you
MAhesh
Key to tunnel, is how a demultiplexing several GRE tunnels.
Quoting RFC:
The Key field contains a four octet number which was inserted by the encapsulator. The actual method by which this Key is obtained is beyond the scope of the document. The Key field is intended to be used for identifying an individual traffic flow within a tunnel. For example, packets may need to be routed based on context information not present in the encapsulated data. The Key field provides this context and defines a logical traffic flow between encapsulator and decapsulator. Packets belonging to a traffic flow are encapsulated using the same Key value and the decapsulating tunnel endpoint identifies packets belonging to a traffic flow based on the Key Field value.
-
Ontario Regulation distributes dynamic routes via VPN S2S
Hi halijenn / experts
(1) please let me know if IPP works on a Site in tunnel
(2) I have a behind remote ASA 10.10.1.0 and 10.10.2.0 network that must be distributed to another branch ASA with S2S ASA remote via OSPF
3) there is an L3 Switch behind the ASA of the branch and Switch L3 there is a router that has a default route pointing router WAN
Router WAN
|
|
Users-> router-> L3 Switch-> ASA-> Internet-> remote ASA branch (10.10.1.0, 2.0)Note: 10.10.1.0 2.0 AND are already configured in the ACL Crypto at the ends.
Users are able to reach the 10.10.2.X network to the remote end.
Now for the 10.10.2.0 static routes are already there in the router and the switch finally pointing the ASA branch however as the network grows, it is impossible in the router behind the switch to add static whenever routes (such as the default route to router WAN points). This is why in order to learn routes dynamically, I will add an ospf process to the ASA to branch with the following configuration. Please let me know if iam correct when I add IPP and other OSPF commands to the ASA of the branch. (hope I have nothing to do on ASA remote associated with IPP or OSPF?)
I take just an example of a remote host 1 10.10.1.4. Inside ASA interface leading to users is 172.16.1.0/24
access-list redistribute allowed standard host 10.10.1.4 255.255.255.255
router ospf 1
network 172.16.1.0 255.255.255.0 area 0
Journal-adj-changes
redistribute static subnets redistribute route mapIn addition, I will also be allowing the order for IPP in the encryption of the VPN S2S said card.
Please help me understand if I'm wrong
Pls set the OSPF firstly on the SAA process before removing the static routes. Once you have confirmed that the OSPF is configured correctly and the roads are in the OSPF database, then you can delete the static routes. Static routes will always take precedence over OSPF because it has higher metric. Please keep the default route configured on the SAA.
Hope that confirms it.
-
Satellite Pro L300 - 12 H did not get the IP address of the DHCP router via cable
My Vista Premium SP1 laptop is connected via a wireless connection to a modem/router ADSL Buffalo WBMR-G54 model that works very well. However, I tried the other day to connect the NIC via a RJ45 cable to the router and it won't work! I get the message "limited connectivity" and an IP of 169.254.xxx.xxx that suggests he does not get an IP address from the router.
I was on various websites and tried all sorts of things as uncheck ipv6 on the properties of LAN card, put off the power of the DHCP Broadcast flag in the registry (according to the number of micrsoft) etc but nothing works.
Anyone have any suggestions to make it work?
NB: I took the laptop in work and plugged into the Windows 2003 Server network and got a DHCP IP immediately!You asked for help by your Internet provider?
-
Communication from router to router via an ISP router
Nice day
I have a Setup at home, with that I would like to help.
I have two routers in my house. One in the living room and the bedroom. The routers are connected to the router of my ISP.
I would like to communicate between my two routers for the purpose of sharing SMB between my NAS and the NUC Intel running kodi. I am not able to routers link the two and am stuck with the ISP router. If I filled two routers I can share, but I prefer to do (if possible) not in bridge mode. Is it possible to get both routers to talk with each other? I'm a little lost here

I put the 1900ACS in the lounge to have:
IP: 192.168.1.1
LAN DHCP: 192.168.1.2 to 192.168.1.50
And the EA6400 in the bedroom:
IP: 192.168.1.51
LAN DHCP: 192.168.1.52 to 192.168.1.100
Drawing enclosed with the installation program:
http://i.imgur.com/WoJ8nW7.PNG
Hi, @ckZA. Because the router is a NAT firewall, the installation type you want is not possible. The router will block incoming pings outside its own network.
You rather connect the EA6400 to the WRT1900ACS and the EA6400 value clipping that both computers are connected to the same DHCP. They should be able to discover each other with this configuration.
I hope this helps.
Maybe you are looking for
-
Google and all its related services are not displayed as a place safe and photographs are blocked.
I was forced to add manual exception for even use Google search AND Google Mail, but the photos are still blocked in the Google search. The first 12 pictures will show, but the rest simply reflect a square broken in the upper left corner where the pr
-
Battery not detected on Satellite A300-1BZ
I JUST REPLACED THE BATTERY IN MY SATELLITE A300-1BZ WITH A GENUINE NEWNOW I GET AN ERROR MESSAGE SAYING (NO BATTERY DETECTED)I WOULD BE GREATFULL FOR ANY ADVICE. SANDDANCER.
-
What can I do if my files etc./affichage/edition bar is not displayed?
Help! the bar at the top, the file edit view tools etc is not appear, because I installed firefox. What can I do? Thank you.
-
9.2 IOS (problem of tactile 3D on keyboard)
My favorite 3D tactile feature is the ability of force - press on the keyboard and use a slider as a mouse to maneuver through text. A that someone has noticed a slight change in performance since the 9.2 update? It's a characteristic that has worked
-
Windows 7 Ultimate 64 bit "not authentic".
Have been using windows 7 for more than a year without problem. Recently received no real advice. MGADiag report:Diagnostic report (1.9.0027.0):-----------------------------------------Validation of Windows data--> Validation code: 50Code of Valida