VISA: Is denied access to the resource or to the remote machine.
Hello.
I use a cRIO-9076 to communicate with a Keithley 2400 via port RS-232 on the cRIO. I have a vi test which is built using the Keithley 2400 drivers and it works perfectly fine with the vi is located under 'My Computer' in my project. If I'm moving that vi on the potion of distance OR cRIO9076 of the project and try to run the vi I get a
VISA: (Hex 0xBFFF00A8 to the resource or the remote machine access is denied...
I realized I need to add something to the list of remote access on the cRIO that I find a little confusing. I want to use the serial port on the cRIO by VISA to communicate to the Keithley, so I need to give permission to cRIO on the cRIO? I'm obviously confused.
I tried to add a simple * (wildcard) to the list of access as a temporary solution but I still get the same error.
I would like some advice.
Thank you
Roth
cRIO 9076
Lab View 2013
Keithley 2400
NI-VISA 5.4.0
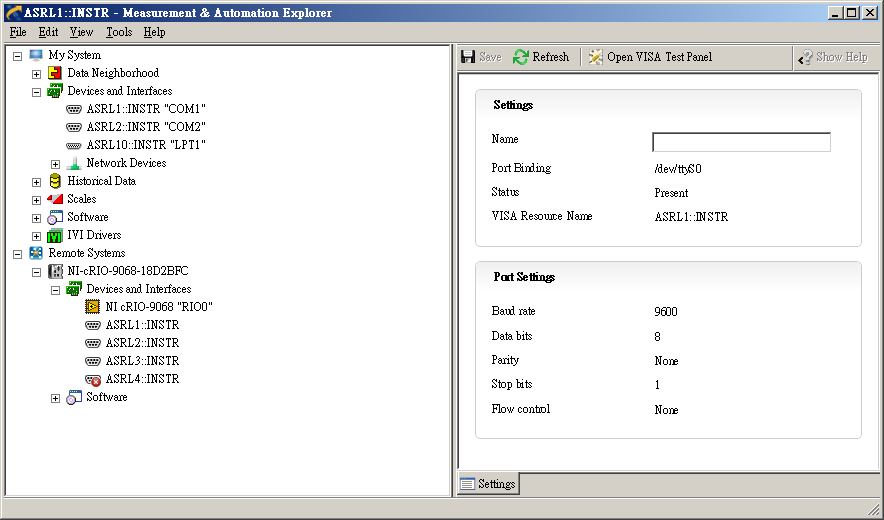
If you want to move the vi to the CRIO, you can change the name of the resource.
my example is based on the cRIO-9068. When running at MAX on my local host, it can show as below.
The resource for the cRIO-9068 should like 'ASRLx:INSTR '.
Good luck!
Tags: NI Hardware
Similar Questions
-
Need of a rule on the NAC to deny access to the XP machines
We run NAC 4.9.1 and I'm trying to think of a way to refuse any client Windows XP to get full network access. I created a new cheque which examines the registry key under:
HKLM\Software\Microsoft\Windows NT\CurrentVersion\ProductName
For any string that contains "Windows XP." I have it on Audit right now and I see in the newspapers that the XP mahcines hit this requirement.
Now, how can I deny that check?
Hello
The NAC itself has rules of compliance different OS that you want to allow on your network.
Simply create a compliance rule indicating that you only allow windows 7. It works much better than the condition of the registry.
I used to support this product back to Cisco, but unfortunately I don't have access to a NAC server so I don't know where exactly is this option.
If you need more help feel free to ask and I'll be happy to help you.
Kind regards
Erdelgad
-
"The operating system denied access to the specified file"
I'm playing simcity4 & it keeps saying "operating system denied access to the specified file.
Hello
- Exactly when you receive this error message?
- This occurs during the installation of the game or the game?
SimCity 4 is not compatible with Windows vista. You can check this link:
I suggest you to contact the support of the environmental assessment for better assistance.
-
I am very new to Cisco firewalls (got a little thrown in there) and I had a request to come down the pipe to deny access to the internet for a single internal IP address. My firewall is a PIX 515e. I'm guessing this has to do with the access list, but I don't know if I need to create a group and add only a single IP address to it or how really, even go about it. Any help would be appreciated.
Andrew
What you posted, it is difficult to find how different access lists are applied (how they are used). But it seems that you need another list of access. What you might look like this:
inside_access_out access-list deny ip host everything
inside_access_out ip access list allow a whole
inside_access_out access to the interface inside group
HTH
Rick
-
Need to deny access to the file for the User Manager
Hello
I need be able to deny access to the file manager, as I don't want my client, deleting files. However, for some reason, I have to allow him access to what he should be able to download files via InContext Editor (he needs to link the pages to documents that are not on the server so he needs to download and do it, I have to grant access to the file manager). How can I get around this? I don't want to reupload the site whenever it deletes a file...
Unfortunately we can not do - file manager access to removal as well as download and at this stage that cannot be changed.
-
Why the system operating to deny access to the file specified to run wipe Drive 5
Why deny operating system access to the specified file for execution unit 5 Wipe to wipe my hard drive, I need permission.
Hi JoyceScott,
· What is the operating system installed on the computer?
If you receive no error message indicating that access is denied, take the permissions on the drive and check if it helps.
a. right click on the external hard drive, and then select Properties.
b. click on the Security tab, select the user name and click on modify.
c. now, click Add and type the user name that you want to grant permissions to sub enter the names of the objects to select, and then click on check names. Click OK.
d. now, select the user name you typed in group or user names and check full control under the terms of the authorization for.
e. click on apply and OK. Check whether the problem exists.
For more information, visit: What are the permissions?
-
Remote clients are denied access to the portal...
We're having sporadic problems with remote clients are denied access to our portal, they do not even have a login prompt. We use a SRA 4600 with SonicOS SSL - VPN 8.0.0.3 - 23sv but have see on 8.0.0.1 as well.
Journal entry:
Threat of prevented WAF: Injection SQL 1 attack
More detailsEntry matching: _ga = ga1.2.676072112.1440205737; _dc_gtm_ua-21325736-1 = 1
Threat: SQL Injection attack 1
Threat ID: 9005
Description: SQL Injection is a technique of attack used to exploit websites that construct SQL statements from user-supplied input
URI: remote.ncmic.com:443/
Agent: Mozilla/5.0 (Windows NT 10.0;) WOW64; Trident/7.0; RV:11.0) as the GeckoThe field 'entry matched' is not indicative of the entry that is triggering the signature. There would be something else, we need to study. Can you please make a ticket and we provide access to the portal so we can try to reproduce it?
-
How to deny access to the user control panel?
A PC running under that Windows 7 is used by several users, I connect PC as an administrator and try to change the policy to prohibit access for the user in the control panel.
But I can't find a way to block certain users access to the control panel.
I don't know other users information to connect.
Is it possible to block some users access to the control panel at the same time of admin account?
Advice me please.
A PC running under that Windows 7 is used by several users, I connect PC as an administrator and try to change the policy to prohibit access for the user in the control panel.
But I can't find a way to block certain users access to the control panel.
I don't know other users information to connect.
Is it possible to block some users access to the control panel at the same time of admin account?
Advice me please.
You can use Group Policy prohibit access to the control panel...
http://answers.Microsoft.com/en-us/Windows/Forum/Windows_7-Security/Windows-7-options-for-standard-user-account/07c1084b-B65F-4b33-8579-1749ca661dedits for all users this grouppolicy is enabled
-
What are the limitations of access to the remote system?
I've got a PXI-1042 remote controller 8108 and 5112, 6723 & 8420 PXI. I can see all the devices remotely from my laptop to the MAX 4.4 (under NIVisaServer). My problem is that I don't know if I can use all of these cards remotely?
I am programming in C++ of MS using VISA & DAQmx libraries and have been able to use the serial ports of the 8420 distance without any problem. But the programming remotely 6723 poses a greater challenge. On previous projects (not involving remote systems) I simply defined virtual world channels in NOR-MAX and DAQmx... used library calls to control. But I'm not able to access the Global virtual channels on the remote system and I can't create anything on my laptop that connect la carte 6723.
Also, I can't run OR-SCOPE Soft Front Panel on my laptop because it is impossible to find the 5112 digitizer.
Is it possible to have full access and the capacity for remote 5112 & 6723 card?
Ken
You are able to view the various devices on the network to the MAX, but unfortunately you can not create glodbal virtual channels or use the functionality of these cards. The best way to use these cards on the network is to use the remote façade (in LabVIEW only), Remote Desktop, etc. I have included some useful links to get more information.
Display of an Application or a front panel remote using LabVIEW
http://zone.NI.com/reference/en-XX/help/371361B-01/lvhowto/viewfrntpnlrmtlyusnglv/
Do the NI 5102, NI 5112, and NI 5911 Oscilloscope cards support remote device access (RDA)?
http://digital.NI.com/public.nsf/allkb/8AC1067C0944FACD8625697A005B92C8
What is device Remote Access (RDA) and where is the server?
http://digital.NI.com/public.nsf/allkb/5CC9792C6CD4A34C862565BC0072D5DF
-
Hello
I'm trying to solve a problem with the VPN, and I hope that someone could give me a helping hand.
We have 3 offices, each with an ASA 5505 like the router/firewall, connected to a cable modem
(NC Office) <----IPSEC----->(office of PA) <----IPSEC----->(TC Office)
Internally, we have a full mesh VPN, so all offices can talk to each other directly.
I have people at home, by using remote access VPN into the Office of PA, and I need them to be able to connect to two other offices there.
I was able to run for the Office of CT, but I can't seem to work for the Office of the NC. (I want to say is, users can remote access VPN in the PA Office and access resources in the offices of the PA and CT, but they can't get the Office of NC).
Someone could take a look at these 2 configs and let me know if I'm missing something? I am newer to this, so some of these configs do not have better naming conventions, but I'm getting there
PA OFFICE
Output of the command: "show run".
: Saved
:
ASA Version 8.2 (5)
!
hostname WayneASAnames of
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
interface Vlan1
nameif inside
security-level 100
IP 192.168.1.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
IP 70.91.18.205 255.255.255.252
!
passive FTP mode
clock timezone IS - 5
clock to summer time EDT recurring
DNS lookup field inside
DNS domain-lookup outside
DNS server-group DefaultDNS
75.75.75.75 server name
75.75.76.76 server name
domain 3gtms.com
permit same-security-traffic intra-interface
object-group Protocol TCPUDP
object-protocol udp
object-tcp protocol
inside_access_in of access allowed any ip an extended list
IPSec_Access to access ip 192.168.1.0 scope list allow 255.255.255.0 192.168.2.0 255.255.255.0
IPSec_Access to access extended list ip 192.168.10.0 allow 255.255.255.224 192.168.2.0 255.255.255.0
IPSec_Access to access extended list ip 192.168.10.0 allow 255.255.255.224 192.168.5.0 255.255.255.0
inside_nat0 to access ip 192.168.1.0 scope list allow 255.255.255.0 192.168.10.0 255.255.255.224
inside_nat0 to access ip 192.168.1.0 scope list allow 255.255.255.0 192.168.2.0 255.255.255.0
inside_nat0 to access ip 192.168.1.0 scope list allow 255.255.255.0 192.168.5.0 255.255.255.0
TunnelSplit1 list standard access allowed 192.168.10.0 255.255.255.224
TunnelSplit1 list standard access allowed 192.168.1.0 255.255.255.0
outside_1_cryptomap to access ip 192.168.1.0 scope list allow 255.255.255.0 192.168.2.0 255.255.255.0
outside_2_cryptomap to access ip 192.168.1.0 scope list allow 255.255.255.0 192.168.5.0 255.255.255.0
outside_cryptomap to access ip 192.168.1.0 scope list allow 255.255.255.0 192.168.5.0 255.255.255.0
RemoteTunnel_splitTunnelAcl list standard access allowed 192.168.1.0 255.255.255.0
RemoteTunnel_splitTunnelAcl_1 list standard access allowed 192.168.1.0 255.255.255.0
RemoteTunnel_splitTunnelAcl_1 list standard access allowed 192.168.2.0 255.255.255.0
RemoteTunnel_splitTunnelAcl_1 list standard access allowed 192.168.5.0 255.255.255.0
out_access_in list extended access udp allowed any SIP host 70.91.18.205 EQ
out_access_in list extended access permit tcp any host 70.91.18.205 eq 5000
out_access_in list extended access permits any udp host 70.91.18.205 range 9000-9049
out_access_in list extended access permit tcp any host 70.91.18.205 EQ SIP
out_access_in list extended access allowed object-group TCPUDP any host 70.91.18.205 eq 5090
out_access_in list extended access permit udp any host 70.91.18.205 eq 5000
Note to outside-nat0 access-list NAT0 for VPNPool to Remote Sites
outside-nat0 extended ip 192.168.10.0 access list allow 255.255.255.224 192.168.2.0 255.255.255.0
outside-nat0 extended ip 192.168.10.0 access list allow 255.255.255.224 192.168.5.0 255.255.255.0
pager lines 24
asdm of logging of information
Within 1500 MTU
Outside 1500 MTU
IP mask 255.255.255.224 local pool VPNPool 192.168.10.1 - 192.168.10.30
no failover
ICMP unreachable rate-limit 1 burst-size 1
don't allow no asdm history
ARP timeout 14400
Global 1 interface (outside)
NAT (inside) 0-list of access inside_nat0
NAT (inside) 1 0.0.0.0 0.0.0.0
NAT (outside) 0-list of access outside-nat0
inside_access_in access to the interface inside group
Access-group out_access_in in interface outside
Route outside 0.0.0.0 0.0.0.0 70.91.18.206 1
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
Floating conn timeout 0:00:00
dynamic-access-policy-registration DfltAccessPolicy
the ssh LOCAL console AAA authentication
Enable http server
http 0.0.0.0 0.0.0.0 inside
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
Crypto ipsec transform-set ESP-DES-SHA esp - esp-sha-hmac
Crypto ipsec transform-set ESP-DES-MD5 esp - esp-md5-hmac
Crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
Crypto ipsec transform-set ESP-3DES-MD5-esp-3des esp-md5-hmac
Crypto ipsec transform-set ESP-AES-256-SHA 256 - aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-SHA aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-MD5-esp - aes esp-md5-hmac
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
Crypto ipsec transform-set esp-3des esp-md5-hmac VPNTransformSet
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 pfs Group1 set
Crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 value transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA MD5-ESP-3DES ESP-DES-SHA ESP-DES-MD5
card crypto IPSec_map 1 corresponds to the address IPSec_Access
card crypto IPSec_map 1 set peer 50.199.234.229
card crypto IPSec_map 1 the transform-set VPNTransformSet value
card crypto IPSec_map 2 corresponds to the address outside_2_cryptomap
card crypto IPSec_map 2 set pfs Group1
card crypto IPSec_map 2 set peer 98.101.139.210
card crypto IPSec_map 2 the transform-set VPNTransformSet value
card crypto IPSec_map 65535-isakmp dynamic ipsec SYSTEM_DEFAULT_CRYPTO_MAP
IPSec_map interface card crypto outside
card crypto outside_map 1 match address outside_1_cryptomap
peer set card crypto outside_map 1 50.199.234.229
crypto ISAKMP allow outside
crypto ISAKMP policy 1
preshared authentication
3des encryption
sha hash
Group 2
life 43200
Telnet 192.168.1.0 255.255.255.0 inside
Telnet timeout 5
SSH 0.0.0.0 0.0.0.0 inside
SSH timeout 60
Console timeout 0
management-access inside
dhcpd outside auto_config
!
dhcpd address 192.168.1.100 - 192.168.1.199 inside
dhcpd dns 75.75.75.75 75.75.76.76 interface inside
dhcpd allow inside
!a basic threat threat detection
Statistics-list of access threat detection
no statistical threat detection tcp-interception
WebVPN
internal RemoteTunnel group strategy
attributes of Group Policy RemoteTunnel
value of server DNS 75.75.75.75 75.75.76.76
Protocol-tunnel-VPN IPSec
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list RemoteTunnel_splitTunnelAcl_1
dfavier vUA99P1dT3fvnDZy encrypted password username
username dfavier attributes
type of remote access service
rduske vu0Zdx0n3oZWFSaX encrypted password username
username rduske attributes
type of remote access service
eric 0vcSd5J/TLsFy7nU password user name encrypted privilege 15
lestofts URsSXKLozQMSeCBk username encrypted password
username lestofts attributes
type of remote access service
jpwiggins 3WyoRxmI6LZjGHZE encrypted password username
username jpwiggins attributes
type of remote access service
tomleonard cQXk0RJCBtxyzZ4K encrypted password username
username tomleonard attributes
type of remote access service
algobel 4AjIefFXCbu7.T9v encrypted password username
username algobel attributes
type of remote access service
type tunnel-group RemoteTunnel remote access
attributes global-tunnel-group RemoteTunnel
address pool VPNPool
Group Policy - by default-RemoteTunnel
IPSec-attributes tunnel-group RemoteTunnel
pre-shared key *.
tunnel-group 50.199.234.229 type ipsec-l2l
IPSec-attributes tunnel-group 50.199.234.229
pre-shared key *.
tunnel-group 98.101.139.210 type ipsec-l2l
IPSec-attributes tunnel-group 98.101.139.210
pre-shared key *.
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
maximum message length automatic of customer
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the rsh
inspect the rtsp
inspect esmtp
inspect sqlnet
inspect the skinny
inspect sunrpc
inspect xdmcp
inspect the sip
inspect the netbios
inspect the tftp
Review the ip options
inspect the icmp
inspect the pptp
!
global service-policy global_policy
context of prompt hostname
no remote anonymous reporting call
Cryptochecksum:6d1ffe8d570d467e1ea6fd60e9457ba1
: endCT OFFICE
Output of the command: "show run".
: Saved
:
ASA Version 8.2 (5)
!
hostname RaleighASA
activate the encrypted password of Ml95GJgphVRqpdJ7
2KFQnbNIdI.2KYOU encrypted passwd
names of
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
interface Vlan1
nameif inside
security-level 100
192.168.5.1 IP address 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
IP 98.101.139.210 255.0.0.0
!
passive FTP mode
clock timezone IS - 5
clock to summer time EDT recurring
DNS lookup field inside
DNS server-group DefaultDNS
Server name 24.25.5.60
Server name 24.25.5.61
permit same-security-traffic intra-interface
object-group Protocol TCPUDP
object-protocol udp
object-tcp protocol
Wayne_Access to access extended list ip 192.168.5.0 allow 255.255.255.0 192.168.1.0 255.255.255.0
Wayne_Access to access extended list ip 192.168.5.0 allow 255.255.255.0 192.168.10.0 255.255.255.0
Shelton_Access to access extended list ip 192.168.5.0 allow 255.255.255.0 192.168.2.0 255.255.255.0
out_access_in list extended access permit tcp any host 98.101.139.210 eq www
out_access_in list extended access permit tcp any host 98.101.139.210 eq ftp
out_access_in list extended access permit udp any host 98.101.139.210 eq tftp
out_access_in list extended access udp allowed any SIP host 98.101.139.210 EQ
out_access_in list extended access permit tcp any host 98.101.139.210 eq 5090
out_access_in list extended access permit tcp any host 98.101.139.210 eq 2001
out_access_in list extended access permit tcp any host 98.101.139.210 eq 5080
out_access_in list extended access permit tcp any host 98.101.139.210 eq ssh
out_access_in list extended access permit tcp any host 98.101.139.210 eq 81
out_access_in list extended access permit tcp any host 98.101.139.210 eq 56774
out_access_in list extended access permit tcp any host 98.101.139.210 eq 5000
out_access_in list extended access permit tcp any host 98.101.139.210 eq 902
out_access_in list extended access permit tcp any host 98.101.139.210 eq netbios-ssn
out_access_in list extended access permit tcp any host 98.101.139.210 eq 445
out_access_in list extended access permit tcp any host 98.101.139.210 eq https
out_access_in list extended access allowed object-group TCPUDP any host 98.101.139.210 eq 3389
out_access_in list extended access allowed object-group TCPUDP range guest 98.101.139.210 5480 5487
out_access_in list extended access permits any udp host 98.101.139.210 range 9000-9050
inside_nat0 to access extended list ip 192.168.5.0 allow 255.255.255.0 192.168.1.0 255.255.255.0
inside_nat0 to access extended list ip 192.168.5.0 allow 255.255.255.0 192.168.2.0 255.255.255.0
inside_nat0 to access extended list ip 192.168.5.0 allow 255.255.255.0 192.168.10.0 255.255.255.0
pager lines 24
asdm of logging of information
Within 1500 MTU
Outside 1500 MTU
ICMP unreachable rate-limit 1 burst-size 1
don't allow no asdm history
ARP timeout 14400
Global 1 interface (outside)
NAT (inside) 0-list of access inside_nat0
NAT (inside) 1 0.0.0.0 0.0.0.0Access-group out_access_in in interface outside
Route outside 0.0.0.0 0.0.0.0 98.101.139.209 1
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
Floating conn timeout 0:00:00
dynamic-access-policy-registration DfltAccessPolicy
the ssh LOCAL console AAA authentication
Enable http server
http 0.0.0.0 0.0.0.0 inside
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Crypto ipsec transform-set esp-3des esp-md5-hmac WayneTransform
Crypto ipsec transform-set esp-3des esp-md5-hmac SheltonTransform
Crypto ipsec transform-set ESP-AES-128-SHA aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-128-MD5-esp - aes esp-md5-hmac
Crypto ipsec transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
Crypto ipsec transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
Crypto ipsec transform-set ESP-AES-256-SHA 256 - aes - esp esp-sha-hmac
Crypto ipsec transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
Crypto ipsec transform-set ESP-3DES-MD5-esp-3des esp-md5-hmac
Crypto ipsec transform-set ESP-DES-SHA esp - esp-sha-hmac
Crypto ipsec transform-set ESP-DES-MD5 esp - esp-md5-hmac
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
card crypto IPSec_map 1 corresponds to the address Wayne_Access
card crypto IPSec_map 1 set pfs Group1
card crypto IPSec_map 1 set peer 70.91.18.205
card crypto IPSec_map 1 the transform-set WayneTransform value
card crypto IPSec_map 2 corresponds to the address Shelton_Access
card crypto IPSec_map 2 set pfs Group1
card crypto IPSec_map 2 set peer 50.199.234.229
card crypto IPSec_map 2 the transform-set SheltonTransform value
IPSec_map interface card crypto outside
crypto ISAKMP allow outside
crypto ISAKMP policy 1
preshared authentication
3des encryption
sha hash
Group 2
life 43200
Telnet timeout 5
SSH 0.0.0.0 0.0.0.0 inside
SSH timeout 5
Console timeout 0
management-access inside
dhcpd outside auto_config
!
dhcpd address 192.168.5.100 - 192.168.5.199 inside
dhcpd dns 24.25.5.60 24.25.5.61 interface inside
dhcpd allow inside
!a basic threat threat detection
Statistics-list of access threat detection
no statistical threat detection tcp-interception
WebVPN
eric 0vcSd5J/TLsFy7nU password user name encrypted privilege 15
tunnel-group 50.199.234.229 type ipsec-l2l
IPSec-attributes tunnel-group 50.199.234.229
pre-shared key *.
tunnel-group 70.91.18.205 type ipsec-l2l
IPSec-attributes tunnel-group 70.91.18.205
pre-shared key *.
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
maximum message length automatic of customer
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the rsh
inspect the rtsp
inspect esmtp
inspect sqlnet
inspect the skinny
inspect sunrpc
inspect xdmcp
inspect the sip
inspect the netbios
inspect the tftp
Review the ip options
inspect the icmp
!
global service-policy global_policy
context of prompt hostname
no remote anonymous reporting call
Cryptochecksum:3d770ba9647ffdc22b3637e1e5b9a955
: endHello
I might have found the problem.
To be honest, I'm a little tired and concentration is difficult, especially when access between multiple device configurations. So second pair of eyes is perhaps in order.
At the moment it seems to me that this configuration is the problem on the SITE of PA
IPSec_Access to access extended list ip 192.168.10.0 allow 255.255.255.224 192.168.5.0 255.255.255.0
This is an ACL that defines networks the and remote for a connection VPN L2L.
Now, when we look at what connection VPN L2L this belong we see the following
card crypto IPSec_map 1 corresponds to the address IPSec_Access
card crypto IPSec_map 1 set peer 50.199.234.229
card crypto IPSec_map 1 the transform-set VPNTransformSet value
Now, we see that the peer IP address is 50.199.234.229. Is what site this? The IP address of the CT Site that works correctly?
Now what that said the ACL line I mentioned more early basically is that when the 192.168.10.0 network 255.255.255.224 wants to connect to the network 192.168.5.0/24 should be sent to the CT Site. And of course, this should not be the case as we want traffic to go on the NC Site
Also worth noting is that on the SITE of the above connection is configured with the '1' priority so it gets first compared a connection. If the VPN L2L configurations were in different order then the VPN Client connection can actually work. But it's just something that I wanted to point out. The actual resolution of the problem, of course, is to detach the configuration which is the cause of the real problem in which ASA attempts to route traffic to a completely wrong place.
So can you remove this line ACL of the ASA of PA
No IPSec_Access access list extended ip 192.168.10.0 allow 255.255.255.224 192.168.5.0 255.255.255.0
Then, test the VPN Client connection NC SITE again.
Hope that this will finally be the solution
-Jouni
-
Filtering of VPN and local access to the remote site
Hello
I set up vpn, filtering on all my VPN l2l. I have limited access to remote resources at the local level to the specified ports. It works perfectly.
But I want to have as full access from local to remote networks (but still retain the remote access to the local level). VPN filter now works as I have two-way with a simple ACL. So is it possible to open all the traffic from the local to remote and all by limiting the remote to the local traffic?
ASA 5520 8.4 (3)
Thanks in advance
Tomasz Mowinski
Hello
Well let's say you have a filtering ACL rule when you allow http local network traffic to the remote host
LAN: 10.10.10.0/24
remote host: 192.168.10.10/32
The filter ACL rule is the following:
FILTER-ACL access-list permit tcp host 192.168.10.10 eq 80 10.10.10.0 255.255.255.0
I think that this ACL rule would mean also that until the remote host has been using source port TCP/80, it may access any port on any host tcp in your local network as long as it uses the source TCP/80 port.
I guess you could add a few ranges of ports or even service groups of objects to the ACL rules so that not all well-known ports would be accessible on the LAN. But I guess that could complicate the configurations.
We are usually management customer and completely different in ASA L2L VPN that allows us to all traffic on another filtering device and do not work in this kind of problems. But of course there are some of the situations/networks where this is not only possible and it is not a feasible option for some because of the costs of having an ASA extra.
Please indicate if you have found any useful information
-Jouni
-
Restrict access to the remote computer of single machine or the single IP address.
Hello
I have a server on which I want to prevent users from remote session. All I want is to give access to a user or machine or IP and that this machine/user/IP can access the server remotely.I tried the below mentioned step and it does not work for me, maybe I'm missing something.Control Panel > administrative tools > Windows Firewall with advanced security > inbound rules > Remote Desktop (TCP-In) and I tried every tab scope, users, computers, I am still able to access the server of any filling machine.Please suggest is possible I can prevent the other users, I can't create a new user account, I have to share the password what I can do is limited to the single machine/user/Ip address.Please suggest.Concerning
Yoann kassoum COULIBALYHi, VC.
I advise you to post this question in the Windows 7 IT PRO Forum /Networking. This community will be able to find solutions to your problems.
B Eddie
-
Hello
With the help of 11.2.0.3
SQL that accesses, one table of remote database link remote db - fonctionnee during over a link db months readonly
The remote database table has been abandoned and then recreatde.
Is there some other step needed to allow access to the table in the remote database?
Thank you
You have lost your privs when the table was dropped.
-
Remote access to the virtual machine from another computer?
is it possible to access my virtual machine, I have on my desk from the local network on a Bill pro forma raspberry for example or this kind of a thing is not possible?
VMware Workstation (or player) is needed on the source machine, i.e. one on which the virtual machine is running. Access to a properly configured VM trough the network is essentially the same as the access to a physical system.
André
-
No internet access on the Virtual Machine
Hey,.
I have a problem, I don't have internet access on my virtual machine. I tried to install Ubuntu as an operating system invited to this topic, but I don't have an internet connection...
[img] http://files.SA-MP.IM/uploads/c8cc2-1-E5.PNG [line]
[img] http://files.SA-MP.IM/uploads/c8cc2-2-11.PNG [line]
Is someone knows how to solve this problem to a solution?
Thanks in advance!
Jordy.
Go to the network settings on the Ubuntu VM and configure IP address, subnet, default gateway, and DNS mask. Then you should have access to the internet.
Maybe you are looking for
-
21 of Firefox crashes repeatedly
Each time you start Firefox now it hangs or crashes. Final crash report: Crash ID: bp-d13170bd-afd1-4f43-9d4b-126fb2130622 Using Internet explore that Firefox has become unusable.
-
Equium L20-264: unknown device PCI after Bios Update
Hi allI just updated the bios on my Equium L20-264 (PSL2ZE) to V1.80.After restarting windows XP has detected a new PCI device but no driver for it.Everything seems to work and all of the devices, I expected were there.The name of the device is devic
-
Watch USB key and not the Sansa player
When I plugged in my sansa e260 v1 to the computer for the first time, I think what he recognized as a sansa e260. Well, I wanted to get rid of the files of stock on the player that I did the format process (Virgin sansa.fmt file). Well I did, and
-
Another HP 3050 has cannot print wireless posts
2 hours of reading another post and I still don't have a solution. My new HP 3050 has is connected to my wireless network and pulling an IP from 192.168.0.144, but Wireless USB is not printer/scan/being recognized. -J' uninstalled software (from th
-
Midled-name of blackBerry Smartphones
I deleted my appworld and now I can't download it, it keep saying missing Midled-name.