VPN on 2nd ISP
ASA5505 with 2 ISP. Want general Internet default ISP (outdoors). Want VPN site-to-site on 2nd ISP. Base license, so I use a 'no before. I think I'm close, but I just can't get my VPN test to negotiate - don't see any attempt even when I ping to generate interesting traffic on another. Switching to 'surf' of isps1 to ISP2 works very well. Attached config. Thanks in advance.
You also need the following route:
route VPN 10.10.1.0 255.255.255.0 yy.yy.yy.1 1
route VPN 10.13.1.0 255.255.255.0 yy.yy.yy.1 1
route VPN 10.14.1.0 255.255.255.0 yy.yy.yy.1 1
route VPN 10.15.1.0 255.255.255.0 yy.yy.yy.1 1
Tags: Cisco Security
Similar Questions
-
VPN out 2 ISP - no failover Bgp - Multihome -.
Hello Experts,
I have read and read a read... so I appreciate all help. I would like to configure VPN dating 2 ISP of as a new HWIC was installed on my 1841.
BGP is not an option, because the links don't communicate with each other.
I understand that this can be done with ip sla and objects, but I don't know
If I need some tweaking with the VPN traffic so that it can failover or it actually work in this config.
Want your comments because it's on a live environment and I can't test on a lab.
My requirements are:
1. I need only 1 host (172.16.4.20) to exit through the second (Antena_NEW_Gateway) interface FA0/1/0 over VPN
with gateway 192.168.51.1 and switching to the default gateway 'original' (the rest is using network) in which case it fails.
2-all my other VPN network traffic remains the same output through my original gateway (190.11.1.1)
The interfaces are as follows:
interface FastEthernet0/0
Outside description
IP dhcp customer_id FastEthernet0/0
3desmap card crypto
!
interface FastEthernet0/1
Inside description
IP 172.16.4.60 255.255.255.0
!
interface FastEthernet0/1/0
Description ANTENA_NEW_Gateway
IP 192.168.51.2 255.255.255.0
Acts1 card crypto
political intellectual property map route acts
Please let me know if I'm missing something. I created a different encryption card for the 2nd interface, I use the same traffic transform-set acl and interesting of before.
interface FastEthernet0/1/0
Description ANTENA_NEW_Gateway
IP 192.168.51.2 255.255.255.0
Acts1 card crypto
political intellectual property map route acts
IP route 0.0.0.0 0.0.0.0 190.11.1.1
host IP 172.16.4.20 road 192.168.51.1 follow 123
host IP 172.16.4.20 road 190.11.1.1 254
ALS IP 1
ICMP echo - 192.168.51.1
timeout of 1000
threshold 2
frequency 3
IP SLA annex 1 point of life to always start-time now
accessibility of rtr 1 track 123
access-list 101 permit icmp any echo host 192.168.51.1
route map acts allow 10
IP match route # 101
Router # set interface FastEthernet0/1/0 Null 0
Router # exit
Also, I am attaching my setup.
the road map should look like
Rout-map allowed acts1 10
corresponds to the ip address 1
IP 192.168.51.1 jump according to the value
Rout-map allowed acts1 20
IP 190.11.1.1 jump according to the value
access-list 1 permit host 172.16.4.20
then apply it to the source interface that is your interface FastEthernet0/1 case
interface FastEthernet0/1
IP policy route map acts1
remove the old map of the route of the external interface.
Good luck
If useful rates
-
VPN on several ISP load balancing
Hi all
Please explaing on VPN load balancing based on a scenario where two Internet service providers are here. How can I configure vpn balance in such a scenario?
Thank you
Shijo.
Hi Shijo
What type of VPN connections you want to balance the load? VPN remote access right? You can essentially set up a cluster within your VPN to load device balanced local traffic, passing through the same ISP... but for a scenario with 2 different ISPS, this may seem a bit difficult... Just because of the fact that your vpn device will have two different IPs on the outer side and have to finish on two different interfaces... tracking and grouping two interfaces are difficult..., your VPN clients will point to a single IP address on the part of ISPS, and virtual IPs have in this case is difficult...
Hope this helps... good luck...
REDA
-
Unable to access the local network with VPN with some ISPS
Hello
We have a VPN Remote Access IPSEC with an ASA5505. Install VPN it correctly but can not access the inside or the ASA to my office.
But at home with another Internet service provider, it works! You can access inside.
We are trying with other ISP and it works with 2 and does not work with the other 2!
Office we also have an ASA5505, but we have another VPN other sites that work properly.
Any ideas?
Thank you and sorry for my English.
Add...
ISAKMP nat-traversal crypto
That should do the trick! Please rate if this can help.
-
I'm running a pix to pix VPN of NYC in Chiba in Japan without any problem. I need to add a 2nd VPN to pix even in New York to a pix no VPN in Frankfurt in Germany that does not work.
Ben, I have provided the following information to Germany:
IKE:
Encryption: AES 256 bit
Auth. ALGOR. : SHA1 160 bits
IKE Diffie-Hellman group: DH group 5 (MODP1536)
SA life duration: 3600
IPSec settings:
Encryption: AES 256 bit
Auth. ALGOR. : SHA1 160 bits
IKE Diffie-Hellman group: DH group 5 (MODP1536)
SA life duration: 3600
Transform-set esp - aes 256 esp-sha-hmac
shared before key *.
Below my setup with the additions for the VPN of the Germany is indented. I am not able to connect to the Germany and I seem to lose my connection Chiba sometimes.
:
6.3 (1) version PIX
interface ethernet0 100full
interface ethernet1 100full
Auto interface ethernet2
ethernet0 nameif outside security0
nameif ethernet1 inside the security100
nameif ethernet2 intf2 interieure4
hostname pix
domain pix
fixup protocol ftp 21
fixup protocol h323 h225 1720
fixup protocol h323 ras 1718-1719
fixup protocol http 80
fixup protocol they 389
fixup protocol rsh 514
fixup protocol rtsp 554
fixup protocol sip 5060
fixup protocol sip udp 5060
fixup protocol 2000 skinny
fixup protocol smtp 25
fixup protocol sqlnet 1521
names of
access-list 101 permit ip 10.10.10.0 255.255.255.0 10.10.40.0 255.255.255.0
access-list 101 permit ip 10.10.20.0 255.255.255.0 10.10.40.0.0 255.255.255.0
access-list 101 permit ip 10.10.30.0 255.255.255.0 10.10.40.0 255.255.255.0
-access-list 101 permit ip 10.10.10.0 255.255.255.0 10.10.50.0 255.255.255.0
pager lines 24
Outside 1500 MTU
Within 1500 MTU
intf2 MTU 1500
IP outdoor 200.200.200.130 255.255.255.240
IP address inside 10.10.10.254 255.255.255.0
No intf2 ip address
alarm action IP verification of information
alarm action attack IP audit
history of PDM activate
ARP timeout 14400
Global 1 interface (outside)
(Inside) NAT 0-list of access 101
NAT (inside) 1 0.0.0.0 0.0.0.0 0 0
allow icmp a conduit
Route outside 0.0.0.0 0.0.0.0 200.200.200.130 1
Route inside 10.10.20.0 255.255.255.0 10.10.10.1 1
Route inside 10.10.30.0 255.255.255.0 10.10.10.1 1
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0: CPP 02:00 0:10:00 01:00 h225
H323 timeout 0:05:00 mgcp 0: sip from 05:00 0:30:00 sip_media 0:02:00
Timeout, uauth 0:05:00 absolute
GANYMEDE + Protocol Ganymede + AAA-server
RADIUS Protocol RADIUS AAA server
AAA-server local LOCAL Protocol
No snmp server location
No snmp Server contact
SNMP-Server Community public
No trap to activate snmp Server
enable floodguard
Permitted connection ipsec sysopt
Crypto ipsec transform-set esp - esp-md5-hmac chiba
-crypto ipsec transform-set esp-aes-256, hmac-sha-esp Frankfurt
MYmap 1 ipsec-isakmp crypto map
correspondence address 1 card crypto mymap 101
card crypto mymap 1 set peer 60.40.60.30
card crypto mymap 1 set of transformation-chiba
-map mymap 5 ipsec-isakmp crypto
-correspondence address card crypto mymap 5 101
-map mymap crypto 5 peers set 62.80.90.80
-map mymap crypto 5 value transform-set Frankfurt
mymap outside crypto map interface
ISAKMP allows outside
ISAKMP key * address 60.40.60.30 netmask 255.255.255.255
ISAKMP - key * address 62.80.90.80 netmask 255.255.255.255
part of pre authentication ISAKMP policy 1
of ISAKMP policy 1 encryption
ISAKMP policy 1 md5 hash
1 1 ISAKMP policy group
ISAKMP policy 1 lifetime 1000
-share of pre authentication isakmp policy 5
-isakmp strategy 5 aes-256 encryption
-isakmp strategy 5 sha hash
-Group politics 5 isakmp 5
-isakmp duration strategy of life 5-3600
Having only one access list 101 for specify encrypted at both sites traffic is incorrect. Cryptographic cards are read from top to bottom, so "crypto mymap map 1" (the tunnel in Chiba) is always going to read everything first. This tunnel specifies the new traffic to Frankfurt, Chiba because that's what you said the PIX is actually subcutaneous traffic you want to go to Frankfurt. You must divide your crypto access lists at both sites with the following text:
MYmap 5 ipsec-isakmp crypto map
correspondence address card crypto mymap 5 102
card crypto mymap 5 peers set 62.80.90.80
card crypto mymap 5 game of transformation-Frankfurt
access-list 102 permit ip 10.10.10.0 255.255.255.0 10.10.50.0 255.255.255.0
However, you must also make sure now that the TWO ACL 101 and 102 are not THAT NAT would have, currently only ACL 101 is specified in your command "nat 0 access-list. Since you cannot specify several "nat 0 access-list" commands per interface, you must define a completely new ACLs that includes 101 and 102 and then set the "nat 0" on this subject, something like:
access-list ip 10.10.10.0 sheep allow 255.255.255.0 10.10.40.0 255.255.255.0
IP 10.10.20.0 allow Access-list sheep 255.255.255.0 10.10.40.0.0 255.255.255.0
IP 10.10.30.0 allow Access-list sheep 255.255.255.0 10.10.40.0 255.255.255.0
access-list ip 10.10.10.0 sheep allow 255.255.255.0 10.10.50.0 255.255.255.0
NAT (inside) 0 access-list sheep
Who should you get, or at least get the process of construction of tunnel passes, you will have to wait and see if all the options that you specified are actually correct (they seem very well).
-
IPsec VPN with 2 ISP on a single backup endpoint router
I have the following configuration setup:
Cisco 1811 (router Client)
FA0 - network internal 192.168.0.0/24
SA1 - connection of ISPS, we'll call it 1.1.1.1
FA2 - Vlan 800
VLAN 800 - secondary ISP connection, we'll call it 2.2.2.2
ASA 5580 running 8.2
Outside of the interface we will call 3.3.3.3
crypto map set 5 peer 1.1.1.1 2.2.2.2
crypto 5 game card address test_network
I have a tunnel-group defined for 1.1.1.1 and 2.2.2.2
Now for the question. I have the setup of 1811 with SLA monitoring. I use a default road map to ensure that the ICMP out Fa1 continuously and I have followed the default route with this. I have a route weighted 250 floating default pointing to the ISP of backup.
While the two networks are available, I can create the tunnel using the ISP to 3.3.3.3 (of 1.1.1.1). I can ping through the tunnel without end. I can then simulate a failure of the ISP and will give the blow the way secondary. I ping through the tunnel again, and on the ASA, I see that a new ISAKMP connection has been set up. Looking on the 1811, I see isakmp QM_IDLE connections (2).
While the main link does not work, I can still ping through the tunnel without end. The primary session isakmp on the 1811 falls never turned off, but on the ASA, in fact get deleted. The ASA has only a connection made to 2.2.2.2. Once the primary link retrieves and the default route is back to the first ISP connection, the tunnel never recovers. The ASA appears to think that the secondary ISP is still the active connection and routing does not work in the tunnel as the 1811 tries to send data to the ISP.
Is there a way to do the following:
-When the ISP main breaks down on the 1811, the established tunnel is cancelled
-When the main ISPS back upward on the 1811, the SAA can re-establish the connection by using the primary link (or the backup on the 1811 tunnel is disconnected)?
Is it still possible to do on a single router (2 links ISP) or it can be done using 2 routers?
I would like to know if I need to explain a little better or if the configuration details are needed.
Thank you!
Jeff
Jeffrey,
In having followed IP SLA on the 1811, as soon as the track is down, the second tunnel should be established. (this also means that, by enabling KeepAlive on both ends, they should note that the main tunnel is not active and bring both ends).
The KeepAlive will constantly monitor the health of the other peer, so this should help you to these two questions.
Federico.
-
Creating remote VPN redundancy with 2 ISPS on ASA 8.3 running
Hello
I need help in implementing connection remote VPN with two ISPs (redundancy), so that the remote VPN client will be only one connection, but two ISPS will be linked to another.
I can do it on previous IOS, but things have changed in ASA 8.3, please help.
Hello
If you follow the post, you will find that the "tunnel-group" is a global command that is not set to a specific interface.
Basically, must be added the card encryption even for two interfaces, as follows:
backup_map interface card crypto outside
backup of crypto backup_map interface card
crypto ISAKMP allow outside
ISAKMP crypto enable backup
The only difference is related to the statements of NAT, reason why I included the pre - NAT post in my previous note.
Thank you.
-
SSH stops in double ISP configuration
ASA 7.2 (4)
I (unfortunately!) properly configured a site with double TIS, several site to site VPN (which do not failover), going forwards, etc... The only question that remains is SSH. Before adding a 2nd ISP, ssh on the inside and outside has worked well as expected. When the two interfaces of PSI are active and traffic moves on the primary, SSH is 'scales' on all 3 interfaces. Watch monitoring tool that goes up and down and is confirmed when I actually try to connect to it. Puzzled. Attached sanitized config, but for me, the party concerned is...
SSH 0.0.0.0 0.0.0.0 inside
SSH 67.xxx.xxx.0 255.255.255.0 outside
SSH 67.xxx.xxx.0 255.255.255.0 cable
SSH timeout 15
I could maybe understand if the interface not in use has expired due to lack of a return path, but all 3 interfaces are defective. As soon as one of the 2 wan interfaces is disconnected, ssh is well on the other 2.
Thank you
Ed
Yes, the way back could be a problem. I appreciate that you try to SSH on the internet and not on the VPN tunnel.
Can you check if it contains the same way when you try to access ASDM?
Can console yourself in the SAA and to collect and capture of ASA internet facing interfaces while you try to SSH.
-
How to create vpn with vista home premium on basis of vpn xp settings?
I can connect to the vpn with xp machine, but when I try to imitate xp setting with machine to vista Home premium I can't connect to the same vpn. What do you suggest me?
How to create a vpn connection in Vista: http://techrepublic.com.com/2346-1035_11-61437-1.html?tag=content;leftCol. NOTE: I don't know what you mean "based" vpn xp settings, but you will have to do the best you can with the options and settings available in Vista (that I n "' t know how they compare to XP, but I hope that you will be able to do so because).
Here is another article on the procedure: http://www.publicvpn.com/support/Vista.php.
Here is an article on how configure a VPN with an ISP in Vista: http://www.web-articles.info/e/a/title/How-to-create-a-VPN-connection-over-your-ISP-connection/.
Here is an article with a number of different other items all on vpn in Vista (I don't know exactly what type of configuration you "AVIC - as a host, as a customer, on what type of connection,--but this article covers many different aspects and I hope that at least a couple will be a help for you: http://compnetworking.about.com/od/vpnsetup/VPN_Setup_How_to_Set_Up_a_VPN.htm.)
I hope this helps.
Good luck!
Lorien - MCSA/MCSE/network + / has + - if this post solves your problem, please click the 'Mark as answer' or 'Useful' button at the top of this message. Marking a post as answer, or relatively useful, you help others find the answer more quickly.
-
Redundancy with double tis on cisco ASA VPN Site to Site
Dear supporters,
Could you help me to provide a configuration for the network as an attachment diagram.
I am suitable with your help.
Thank you
Best regards
Hi Sothengse,
You can visit the below link and configure ASA @ head and Canes accordingly to your condition.
You must change the configuration of the similar example with ends... Double TIS @ ends in your scenario...
http://networkology.NET/2013/03/08/site-to-site-VPN-with-dual-ISP-for-BA...
I hope this helps.
Concerning
Knockaert
-
Hello world
I was testing the few things at my lab at home.
PC - running ssl vpn - sw - router - ISP - ASA (anyconnect ssl)
AnyConnect ssl works very well and I am also able to access the internet.
I use full tunnel
I have ACLs on the external interface of the ASA
1 True any any intellectual property Deny 0 By default [] I know that the ACL is used to traffic passing by ASA.
I need to understand the flow of traffic for internet via ssl vpn access. ?
Concerning
MAhesh
As you correctly say, the ACL interface is not important for that because the VPN traffic is not inspected by the ACL. Of the at least not by default.
You can control the traffic with a different ACL that is applied to the group policy with the command "vpn-filter". And of course you need a NAT rule that translates your traffic when running to the internet. This rule should work on the pair of interface (outside, outside).
-
ASA 5510 VPN multiple tunnels through different interfaces
Is it possible to create VPN tunnels on more than one interface to an ASA (specifically 5510 with 8.4), or I'm doing the impossible?
We have 2 public interfaces on our ASA connected to 2 different suppliers.
We must work L2L tunnels of the SAA for remote offices through the interface that is our ISP 'primary' and also used as our default gateway for internet traffic.
We are trying to install a remote office use our secondary connection for its tunnel (office of high traffic we would prefer separate away from the rest of our internet and VPN traffic).
I can create the tunnel with the ACL appropriate for traffic tunnel, card crypto, etc., put in place a static route to force ASA to use the secondary interface for traffic destined for the public of the remote gateway IP address, and when I finished, traffic initiated by the remote site will cause the tunnel to negotiate and find - I can see the tunnel in Show crypto ikev1 his as L2L answering machine MM_ACTIVE , Show ipsec his with the right destination and correct traffic local or remote identities for interesting, but the ASA local never tries to send traffic through the tunnel. If I use tracers of package, it never shows a VPN that is involved in the trafficking of the headquarters in the remote desktop, as if the SAA is not seeing this as for the corresponding VPN tunnel traffic.
If I take the exact same access and crypo card statements list and change them to use the primary ISP connection (and, of course, change the remote desktop IP connects to), then the connection works as expected.
What Miss me?
Here is a sample of the VPN configuration: (PUBLIC_B is our second ISP link, 192.168.0.0/23 is MainOffice 192.168.3.0/24 is FieldOffice)
permit access list range 192.168.0.0 PUBLIC_B_map 255.255.254.0 192.168.3.0 255.255.255.0
NAT (Inside, PUBLIC_B) static source MainOffice MainOffice static FieldOffice FieldOffice
card crypto PUBLIC_B_map 10 corresponds to the address PUBLIC_B_map
card crypto PUBLIC_B_map 10 set counterpart x.x.x.x
card crypto PUBLIC_B_map 10 set transform-set ESP-3DES-SHA ikev1
PUBLIC_B_map PUBLIC_B crypto map interface
tunnel-group x.x.x.x type ipsec-l2l
tunnel-group ipsec-attributes x.x.x.x
IKEv1 pre-shared-key *.
Route PUBLIC_B x.x.x.32 255.255.255.224 y.y.y.y 1
If I take this same exact configuration and change it to use PUBLIC (our primary connection) instead of PUBLIC_B, remove the instruction PUBLIC_B route and change the desktop to point to the ip address of the PUBLIC, then everything works, so my access list and crypto map statements must be correct.
What I don't understand is why the ASA Head Office does not seem to recognize interesting for the tunnel traffic when the tunnel is for the second ISP connection, but works when it is intended for the main ISP. There is no problem of connectivity with the ISP Internet B - as mentioned previously, the tunnel will come and negotiate properly when traffic is started from the desktop, but the traffic of main office is never sent to the bottom of the tunnel - it's as if the ASA does not think that traffic of 192.168.0.x to 192.168.3.x should pass through the VPN.
Any ideas?
Hello
I think your problem is that there is no route for the actual remote network behind the VPN L2L through ISP B connection
You could try adding add the following configuration
card crypto PUBLIC_B_map 10 the value reverse-road
This should automatically add a static route for all remote networks that are configured in the ACL Crypto, through the interface/link-ISP B.
If this does not work, you can try to manually add a static route to the ISP B link/interface for all remote networks VPN L2L in question, and then try again.
The route to the remote VPN peer through the ISP B does not to my knowledge.
I would like to know if it works for you.
It may be useful
-Jouni
-
Hi all!
My client bought a SRP526W some time there, but now it has changed is the ISDN to POTS telephone line.
Is it possible to connect the router provided by the ISP to the SRP526W to continue using all the features of SRP526W (wireless, etc.)
Many thanks and marry Christmas in advance.
José Ventura.
Do you use the RPS to put an end to the dsl connection or use the WAN ethernet?
Because your provider has installed a new router, I guess it ends your DSL connection, if this is the case, then you can simply use the ethernet WAN on the RPS, the PSI unit ethernet LAN connection
Here is a free interpretation. If you wish to continue using VPN services, the ISP firewall must be on a different subnet LAN as ESP. In addition, it must support VPN passthrough and you should also port forwarding VPN respective ports... IPSec using 500 and 4500. CRS supports NAT - T for the site to site VPN so this should be OK.
.
-Tom
Please mark replied messages useful -
I have the following configuration:
Private network <->SW <->CISCO VPN <->MODEM to ISP
I have party VPN configured and working properly. I have a computer in the private network to the static address 192.168.1.100 and an application runs on this subject on the tcp port 8100 for customers.
Now, I need to connect over the Internet to the application on 192.168.1.100 on port 8100.
How to configure the CISCO router before inbound tcp port 8100 to machine 192.168.1.100?
ISP modem will discount all traffic to CISCO device.
Thank you
Hello
Well, I said public_ip just in case you want to use a different IP address to the external interface of the router.
The extensible keyword allows the user to configure several translations static ambiguous, where an ambiguous translation is translations with the same local or global address.
Example from a position of the SCC
IP nat inside source static x.x.x.x y.y.y.y extensible
IP nat inside source static x.x.x.x z.z.z.z extensible.
When a packet comes from outside for insde with destination
It will be sent to x.x.x.x y.y.y.y or z.z.z.z address,
Kind regards
Note all useful posts
Julio
-
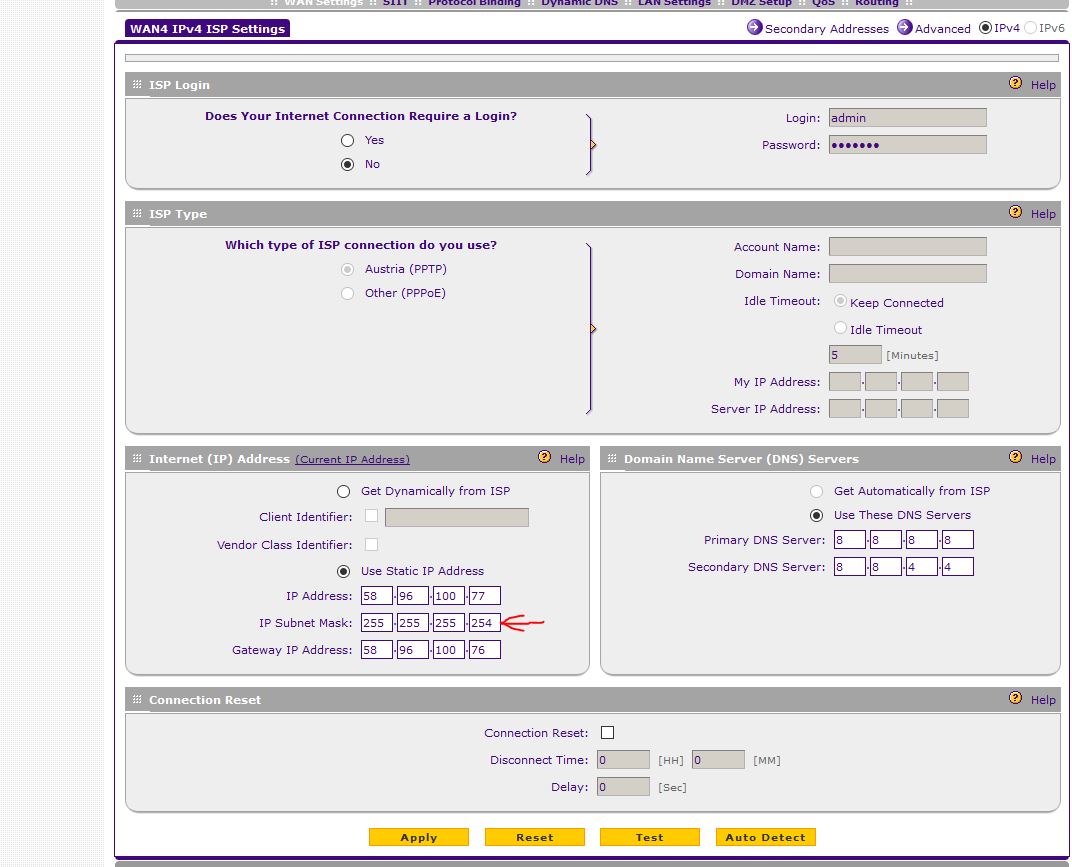
I can't add/subnet mask 31 255.255.255.254 ISP WAN > static IP setting in VPN Firewall SRX5308
Hello
I can't add/subnet mask 31 255.255.255.254 ISP WAN > static IP setting in VPN Firewall SRX5308. When I try to apply it, I get the popup error message like "invalid IP subnet mask. Please enter 0/128/192/224/240/248/252 for octet 4 ". I try to add provider NTU fiber optic internet service in one of the 4 WAN settings. The vendor gave me a 31 block IP and the subnet as 255.255.255.254 mask. It is a limitation in this firewall? I have to ask the provider to give me a 30 block the IP instead? With 30 block IP subnet mask will be 255.255.255.252 who is authorized by this firewall setting. I tried this on another (SnapGear SG560) firewall and it works without any problem. See the screenshots below. Can someone please?
concerning
Ridwan
/ 31 would be used in specific scenarios where you * really * need to keep the address space and on links only point to point. To be honest I've never met anyone, or any ISP that uses it. It works on point to point, because, well, there no need to broadcast address because there are only two devices on the link (one on each side of the cable)... IP address ranges would be;. 0-. 1,.2-. 3, etc.
Most (if not all) Netgear devices will prevent you from setting 31, but you will probably be able to use without problem in all 30 cases, according to the setup of the ISP I do not think that it would cause you problems really. But if you can, I would certainly ask a 30 instead.
Maybe you are looking for
-
Why iTunes says my iPhone 6 s must be updated to iOS 9.2.1
iTunes says my iPhone 6 s must be updated to iOS 9.2.1 despite the fact that it is already on iOS 9.2.1. Updating the phone software shows that it is up-to-date, yet iTunes seems to think that's not. What should do?
-
HP TouchSmart 300-1120 do not start and with noisy fan
Hello Children were using the PC and recording of large amount of data (about 30 GB) on desktop? Suspecting this could be trigerred overheating that caused the major failure. The dust was found on the heatsink, but nothing was completely clogged. Whe
-
laptop password admin or power on password
did not use computers for a long time. When I finally turned it on this game a black screen with a blue box asking admin password or password running after unsuccessful attempts, he gave me a disabled system code #55146425
-
I saved data in public documents on Windows XP computers. C:\Documents and Settings\All Users\Documents\National Instruments\Data I just picked up a new machine, and it has Win7 on it. The path to the public folder has changed. Is it possible to pr
-
HP Slate 7 - problems with wireless connections
I wonder if anyone can help me? I had a BT Hub 4 installed last week and my Tablet connected for a few hours and now does not connect to the internet properly. I already talked to the line of HP technology and changed the terminal settings as they r