Weird name of parachuting.
Hello!
I use an iPhone 6 recently updated to iOS 9.2.1. I noticed something strange. When I want to share a file from my mac to my iPhone, instead saying os iPhone of Catalin like before he says a weird name. I checked the name of my device and it says Catalin iPhone. Only when I want to use airdrop it appears as follows
I enclose a screeshot this question. Hope that there is someone who can help me with this. Thank you very much.
Try restarting your device if you have already.
For the iPhone, do a hard reset by holding the Power and Home button for 7-8 seconds until it stops. Then turn on again.
Tags: iPhone
Similar Questions
-
Send the form web (for the newsletter) - how to stop having create a weird name?
Hello
We have an e-form that captures only the customers email address.
The problem is wierdly makes their email address first name too...
Our online form code is:
[code]
< do action = "/ FormProcessv2.aspx?" WebFormID = 54239 & amp; OID = {module_oid} & amp; OTYPE = {module_otype} & amp; EID = {module_eid} & amp; CID = {module_cid} & amp; OPTIN = true & amp; "PageID = / thanks-you-free-flowe rs ' enctype =" multipart/form-data"onsubmit ="return checkWholeForm8936 (this)"method ="post"name ="catwebformform8936">
< input type = "text" maxlength = placeholder "255" = "Enter your e-mail" class = "cat_textbox lfloat" id = "EmailAddress" name = "EmailAddress" style = "" width: 65%; "/ >"
< div style = "" display: none; "> < input type ="checkbox"name ="CampaignList_34192"checked ="checked"/ > subscribe to the: consumers only < / div >"
{module_ccsecurity}
< id button = "catwebformbutton" value = "Submit" class = "cat_button lfloat" style = "width: 25%;" margin-top: 0px; "> sign Up < / button >
"< script src="/CatalystScripts/ValidationFunctions.js "type =" text/javascript"> < / script >
< script type = "text/javascript" >
<! [CDATA]
var submitcount54012 = 0; function checkWholeForm54012 (theForm) {var why = ""; if (theForm.EmailAddress) why += checkEmail (theForm.EmailAddress.value);} If (why! = "") {alert (why);} return false ;} If (submitcount54012 == 0) {submitcount54012 ++; theForm.submit (); return false ;}; else {alert ("the form submission is in course."); return false ;}}}}
[]] >
< /script >
< / make >
[/ code]
For example, a person registers with email [email protected] then BC will strangely automatically their first name field testingform which is false. For example [email protected] his name as smittenkitten <- so when Polly Bloggs made an order his plot gets addressed to the 'smittenkitten"not Polly Bloggs that she captures in her confirmation page.
Has anyone found a fix or a solution?
It's ok - chatted to great Anshul in support and which product do it via a list of campaign would be best.
Works perfectly now yaye! Also tested with a prescription and he name of updates perfectly.
I leave you here in case that anyone has same issue.
-
How can I get automatic fill-in of the user name and password?
It is similar but different from my previous question. On a computer when I open Firefox it opens automatically log me in my homepage (a Yahoo mail account). When I open a new tab in my gmail login happens with my already filled username. All I have to do is click NEXT and it goes to the login with my password information page. I can't get firefox my my other computer to do this. My homepage comes up with my informed user name, but I have to manually go through the login process. When I open gmail in a new tab, I can't do anything except: 1. press ENTER and get an error message, and then click in the user name box, or 2. Re - click the gmail to re - open the tab. Once I did this the page comes with connection two names - the strange correct one and a few. (I've not been able to get rid of the weird name, either). I would like to be able to fix things, so Firefox will do the same thing on this computer as it does on the other.
Someone at - it suggestions?
A detail as a website to remember you (automatically log you) is stored in a cookie.
You can use these steps to make a Web site recognize and remember you:
- Create a cookie 'allow' except to keep these cookies, in particular in the case of secure websites and when the cookies expire when Firefox is closed.
- Tools > Options > privacy > "Use the custom settings for history" > Cookies: Exceptions
You can delete cookies for a Web site to make the site forget about you.
-
Hello
I have filenames with weird values inside (created by Application software).
Here is an example:
GIBtmpphoto0_11:27:16.145.pngWhen I try to delete it, I have the following error:
The specified file is not valid or too long. Specify a different file name.And it takes a lot of space in my hard drive.
How is it possible to remove it?
Thank you.
Best regards
MarcOriginal title: delete files with weird names
Hello
My corrupt files are found on a disk of material on my computer.
I have re-formatted the full disk to remove these files.Best regards
Marc -
An odd index in the execution plan name
Hi all
Today someone came to aks my help on setting a SQL. Follow-up is compositions of the entire plan. Although I resovled performance issue, I still don't understand why
the index with the name "BIN$ ld5VAtb88PngQAB/AQF8hg == $0 ' similar appear in the plan."
If I remember correctly, this kind of names mean the items in the Recycle Bin. But the index has been abandoned can be used in the execution plan?
Someone sees potential problems involved with this kind of index name, index name, just please?
Best regards
Leon--------------------------------------------------------------------------------------------------------------------------------------- | Id | Operation | Name | Rows | Bytes | Cost (%CPU)| Time | ---------------------------------------------------------------------------------------------------------------------------------------- | 0 | SELECT STATEMENT | | 1 | 231 | 5 (0)| 00:00:01 | |* 1 | FILTER | | | | | | | 2 | TABLE ACCESS FULL | TBL_SYS_USERS | 344 | 79464 | 5 (0)| 00:00:01 | | 3 | NESTED LOOPS | | 1 | 80 | 13 (0)| 00:00:01 | |* 4 | TABLE ACCESS FULL | TBL_SYS_DATA_ACCESS_RULES | 1 | 54 | 13 (0)| 00:00:01 | |* 5 | INDEX UNIQUE SCAN | BIN$ld5VAtb88PngQAB/AQF8hg==$0 | 1 | 26 | 0 (0)| 00:00:01 | | 6 | NESTED LOOPS | | 1 | 80 | 13 (0)| 00:00:01 | |* 7 | TABLE ACCESS FULL | TBL_SYS_DATA_ACCESS_RULES | 1 | 54 | 13 (0)| 00:00:01 | |* 8 | INDEX UNIQUE SCAN | BIN$ld5VAtb88PngQAB/AQF8hg==$0 | 1 | 26 | 0 (0)| 00:00:01 | | 9 | NESTED LOOPS | | 1 | 80 | 13 (0)| 00:00:01 | |* 10 | TABLE ACCESS FULL | TBL_SYS_DATA_ACCESS_RULES | 1 | 54 | 13 (0)| 00:00:01 | |* 11 | INDEX UNIQUE SCAN | BIN$ld5VAtb88PngQAB/AQF8hg==$0 | 1 | 26 | 0 (0)| 00:00:01 | |* 12 | TABLE ACCESS BY INDEX ROWID | TBL_SYS_EMPLOYEES | 1 | 26 | 1 (0)| 00:00:01 | |* 13 | INDEX UNIQUE SCAN | BIN$ld5VAtba8PngQAB/AQF8hg==$0 | 1 | | 0 (0)| 00:00:01 | |* 14 | TABLE ACCESS FULL | TBL_SYS_DATA_ACCESS_RULES | 1 | 54 | 13 (0)| 00:00:01 | |* 15 | TABLE ACCESS FULL | TBL_SYS_DATA_ACCESS_RULES | 1 | 54 | 13 (0)| 00:00:01 | |* 16 | TABLE ACCESS FULL | TBL_SYS_DATA_ACCESS_RULES | 1 | 54 | 13 (0)| 00:00:01 | |* 17 | TABLE ACCESS BY INDEX ROWID | TBL_SYS_EMPLOYEES | 1 | 26 | 1 (0)| 00:00:01 | |* 18 | INDEX UNIQUE SCAN | BIN$ld5VAtba8PngQAB/AQF8hg==$0 | 1 | | 0 (0)| 00:00:01 | | 19 | NESTED LOOPS | | 1 | 80 | 14 (0)| 00:00:01 | | 20 | TABLE ACCESS BY INDEX ROWID | TBL_SYS_EMPLOYEES | 1 | 26 | 1 (0)| 00:00:01 | |* 21 | INDEX UNIQUE SCAN | BIN$ld5VAtba8PngQAB/AQF8hg==$0 | 1 | | 0 (0)| 00:00:01 | |* 22 | TABLE ACCESS FULL | TBL_SYS_DATA_ACCESS_RULES | 1 | 54 | 13 (0)| 00:00:01 | | 23 | NESTED LOOPS | | 1 | 80 | 14 (0)| 00:00:01 |user12064076 wrote:
Hi allToday someone came to aks my help on setting a SQL. Follow-up is compositions of the entire plan. Although I resovled performance issue, I still don't understand why
the index with the name "BIN$ ld5VAtb88PngQAB/AQF8hg == $0 ' similar appear in the plan."If I remember correctly, this kind of names mean the items in the Recycle Bin. But the index has been abandoned can be used in the execution plan?
Someone sees potential problems involved with this kind of index name, index name, just please?Best regards
LeonThe simple answer is that the table has been abandoned and flashed then back to before the fall. When this happens, the table name is restored to its original name, but the index names are not restored. A quick to demonstrate test case.
First, create us a table and an index, and then collect statistics:
DROP TABLE T1 PURGE; CREATE TABLE T1 AS SELECT ROWNUM C1, RPAD('A',255,'A') C2 FROM DUAL CONNECT BY LEVEL<=10000; COMMIT; CREATE INDEX IND_T1_C1 ON T1(C1); EXEC DBMS_STATS.GATHER_TABLE_STATS(OWNNAME=>USER,TABNAME=>'T1',CASCADE=>TRUE)Then we will check that the index will be used with a sample SQL statement:
SELECT C1, SUBSTR(C2,1,2) FROM T1 WHERE C1<=5; C1 SU --- -- 1 AA 2 AA 3 AA 4 AA 5 AA SELECT * FROM TABLE(DBMS_XPLAN.DISPLAY_CURSOR(NULL,NULL,NULL)); PLAN_TABLE_OUTPUT ----------------------------------------------------------------------------------------- SQL_ID g0kkvxqg3v145, child number 0 ------------------------------------- SELECT C1, SUBSTR(C2,1,2) FROM T1 WHERE C1<=5 Plan hash value: 683303157 ----------------------------------------------------------------------------------------- | Id | Operation | Name | Rows | Bytes | Cost (%CPU)| Time | ----------------------------------------------------------------------------------------- | 0 | SELECT STATEMENT | | | | 3 (100)| | | 1 | TABLE ACCESS BY INDEX ROWID| T1 | 5 | 1300 | 3 (0)| 00:00:01 | |* 2 | INDEX RANGE SCAN | IND_T1_C1 | 5 | | 2 (0)| 00:00:01 | ----------------------------------------------------------------------------------------- Predicate Information (identified by operation id): --------------------------------------------------- 2 - access("C1"<=5)The index has been used.
Then, we will empty the trash, delete the index and see if it can still be used in an execution plan:
PURGE RECYCLEBIN; DROP INDEX IND_T1_C1; SELECT C1, SUBSTR(C2,1,2) FROM T1 WHERE C1<=5; C1 SU --- -- 1 AA 2 AA 3 AA 4 AA 5 AA SELECT * FROM TABLE(DBMS_XPLAN.DISPLAY_CURSOR(NULL,NULL,NULL)); PLAN_TABLE_OUTPUT -------------------------------------------------------------------------- SQL_ID g0kkvxqg3v145, child number 0 ------------------------------------- SELECT C1, SUBSTR(C2,1,2) FROM T1 WHERE C1<=5 Plan hash value: 3617692013 -------------------------------------------------------------------------- | Id | Operation | Name | Rows | Bytes | Cost (%CPU)| Time | -------------------------------------------------------------------------- | 0 | SELECT STATEMENT | | | | 137 (100)| | |* 1 | TABLE ACCESS FULL| T1 | 5 | 1300 | 137 (5)| 00:00:01 | -------------------------------------------------------------------------- Predicate Information (identified by operation id): --------------------------------------------------- 1 - filter("C1"<=5)Note that in the foregoing that falling was not used.
We'll re-create the index and gather statistics (when the index is created on Oracle Database 10.1 and higher, the index of statistics will be automatically collected, so it's actually an unnecessary step):
CREATE INDEX IND_T1_C1 ON T1(C1); EXEC DBMS_STATS.GATHER_TABLE_STATS(OWNNAME=>USER,TABNAME=>'T1',CASCADE=>TRUE)We could verify that the index will be used again, but we can skip this step.
Now we remove the table and pick up the trash. Then we run the simple query of the T1 table again and retrieve the execution plan:
DROP TABLE T1; FLASHBACK TABLE T1 TO BEFORE DROP; SELECT C1, SUBSTR(C2,1,2) FROM T1 WHERE C1<=5; C1 SU --- -- 1 AA 2 AA 3 AA 4 AA 5 AA SELECT * FROM TABLE(DBMS_XPLAN.DISPLAY_CURSOR(NULL,NULL,NULL)); PLAN_TABLE_OUTPUT -------------------------------------------------------------------------------------------------------------- SQL_ID g0kkvxqg3v145, child number 0 ------------------------------------- SELECT C1, SUBSTR(C2,1,2) FROM T1 WHERE C1<=5 Plan hash value: 3441582395 -------------------------------------------------------------------------------------------------------------- | Id | Operation | Name | Rows | Bytes | Cost (%CPU)| Time | -------------------------------------------------------------------------------------------------------------- | 0 | SELECT STATEMENT | | | | 3 (100)| | | 1 | TABLE ACCESS BY INDEX ROWID| T1 | 5 | 1300 | 3 (0)| 00:00:01 | |* 2 | INDEX RANGE SCAN | BIN$PESygWW5R0WhbOaDugxqwQ==$0 | 5 | | 2 (0)| 00:00:01 | -------------------------------------------------------------------------------------------------------------- Predicate Information (identified by operation id): --------------------------------------------------- 2 - access("C1"<=5)In the above, you will notice that the index has been used, but now has a funny name.
We will resolve the weird name and re - run the query:
ALTER INDEX "BIN$PESygWW5R0WhbOaDugxqwQ==$0" RENAME TO IND_T1_C1; SELECT C1, SUBSTR(C2,1,2) FROM T1 WHERE C1<=5; C1 SU --- -- 1 AA 2 AA 3 AA 4 AA 5 AA SELECT * FROM TABLE(DBMS_XPLAN.DISPLAY_CURSOR(NULL,NULL,NULL)); PLAN_TABLE_OUTPUT ----------------------------------------------------------------------------------------- SQL_ID g0kkvxqg3v145, child number 0 ------------------------------------- SELECT C1, SUBSTR(C2,1,2) FROM T1 WHERE C1<=5 Plan hash value: 683303157 ----------------------------------------------------------------------------------------- | Id | Operation | Name | Rows | Bytes | Cost (%CPU)| Time | ----------------------------------------------------------------------------------------- | 0 | SELECT STATEMENT | | | | 3 (100)| | | 1 | TABLE ACCESS BY INDEX ROWID| T1 | 5 | 1300 | 3 (0)| 00:00:01 | |* 2 | INDEX RANGE SCAN | IND_T1_C1 | 5 | | 2 (0)| 00:00:01 | ----------------------------------------------------------------------------------------- Predicate Information (identified by operation id): --------------------------------------------------- 2 - access("C1"<=5)The index is now back to normal.
Charles Hooper
http://hoopercharles.WordPress.com/
IT Manager/Oracle DBA
K & M-making Machine, Inc. -
Why firefox can not open with the default profile. It should be renamed?
trying to install "malwarebytes" for extra protection, the Norton toolbar on firefox has been reduced in size by losing my option "Vault". This prompted reinstalling on securities Notion which then prevented the opening of firefox. Internet Explore works well but I use firefox for years so why change. Firefox won't open (even after being uninstalled and downloaded and reinstalled. The message 'your firefox profile cannot be loaded, etc.' following the instructions of your forum, I locate a profile with the word 'profile' embedded file. The word "profile" in the flow path is preceded by a weird name (such as a foreign name). Path =
'C:\Users\Owner\AppData\Roaming\Mozilla\Firefox\Profiles\bzjajhor.default-1419035389504 '. This file needs to be renamed and can they?Please help me to go back to firefox. Thank you
Do not rename a profile folder.
It seems that there is a problem with the profiles.ini.See:
This is usually caused by a problem with the file profiles.ini and the profile marked as the default value = 1 in this file is no longer present on the hard drive.
- Windows: %AppData%\Mozilla\Firefox\
C:\Users\ < user > < profile > \AppData\Roaming\Mozilla\Firefox\Profiles\. - Linux: ~/.mozilla/firefox/
- Mac: ~/Library/Application Support/Firefox /.
You can use one of them to make Firefox/reuse to create a new default profile:
- Remove the profiles.ini file to force Firefox to create a new default profile
- Use the Profile Manager to create a new profile
Use "Choose a folder" when you create a new profile to select the location of a lost profile and recover this profile
- Windows: %AppData%\Mozilla\Firefox\
-
What is "Andrea ST FIlters Service"?
I bought a new HP laptop with VIsta and there is a service that runs on it that has no description and a weird name.
Is it a a legimitate service and what do I do?
Why would I want it?
Thank you
Chip
Hello CHIPDAWES,
Andrea ST FIlters Service is related with SigmaTel Audio, mostly used with Microphones for noise cancellation, so it's a legitimate
Hope this helps

-
Files (hiding...) I should delete?
Hello
I thought attribute on the system Finder and discovered, that there are many many many files, which I don't do, or have weird names, like:
System/library /...
I understand not all folders in the library, and I have to remove them? I have just 6 GB on my Mac Book Air left. Can you explain to me?
Good day
Tlumination
Absolutely never delete anything if you don't know what it is for. OS X is based on a version of BSD Unix. This type of folder structure is typical for Unix system. The system folder is just what it says; Items for the operating system work. Nothing else belongs to it. The root folder of the library also contains many elements of the system, but can also contain application files and articles for apps install so that they are available for all user accounts (example, Photoshop works for all users).
If all the space that you left is 6 GB, you need to get rid of some large items. Video files in particular take a lot of space. Off copy them on an external drive and then delete them from your MacBook Air.
-
Settings of the proxy in Profile Manager
Hello
I have a Mac client where already the proxy settings have been entered (including authentication).
Now for this client, I create a custom in OSX Profile Manager setting and push it to that client (push is successful). I also see the profile applied in settings > profile.
But for some reason that the proxy settings are not applied. In the settings > network > and so on the 'old' proxy is always present.
My proxy (with a weird name like blablabla.bla.com) is not, therefore, apply, I would not be able to browse the internet.
How the * does this work?
Is there some good manuals about except "enter proxy here and push it. "Now, little magic and maybe it will work" Apple as 'server administrator manual "?
I want to change the proxy server on all network connections (Ethernet 1/2, Thunderbolt bridge, WiFi,...) on all clients of my Mac without touching the authentication.
How can I do?
Thanks for your help!
It does not answer your question, but in general I would say that the best way to get the proxy settings is as follows.
- Implement a DHCP 252 option code to set the address of a web server that "serves" a proxy.pac aka. WPAD.dat file
- Optionally, define a DNS record for your internal network, this might be a record, but more generally would be a CNAME and would be for wpad.yourdomain.com
- Create a proxy.pac aka. WPAD.dat file
- Do the proxy.pac aka. WPAD.dat file is available via a web server internal and given 2. above ideally via the address http://wpad.yourdomain.com/wpad.dat
Note: the proxy.pac file contains not only the address of your proxy server, but also rules on websites can bypass the proxy server and sites that can go through the proxy server but bypass authentication.
The foregoing is a network standard called WPAD - discovery automatic Web Proxy which was originally designed by Microsoft and incorporated originally in Internet Explorer. The advantage of this approach is that if you take your laptop out of Office that does not reconfigure not to use your LAN proxy server.
It is found that I got Apple to add support not only to set DHCP option codes in their own DHCP server and thus be able to set the option 252 necessary for this purpose, but also separately I got Apple to add support for OS X to act as a client for WPAD to 'learn' which proxy server to use. Apple calls this "Automatic Proxy Discovery" in their proxies in the network settings tab.
For more information about WPAD, see this article - https://en.wikipedia.org/wiki/Web_Proxy_Autodiscovery_Protocol
For more information about the current configuration of the leading CAP see - https://en.wikipedia.org/wiki/Proxy_auto-config the proxy.pac and wpad.dat files are really exactly the same thing.
Note: The authentication settings are not provided via WPAD. It is possible to not use any authentication at all, or if you do what will happen is that the first time that the user gets asked a dialog box is presented asking the name of user and password and it is then saved in the keychain of connection of users - if your using Safari or other Apple applications. If your using Firefox it stores itself. It is a setting by user to another user, even on the same Mac would ask for their own authentication credentials.
-
Re: Overheating and lag issues on the Satellite C660/C660D
Hello community of Toshiba
I am a new user of Toshiba, I have a new Toshiba laptop as a model of its Satellite C660 / C660D, I use my new laptop for 6 months and I have some kind of a lot of time on my laptop. Sometimes I keep it open for more than 10 hours.
My problem is like 3-4 months at the bottom right of the screen there is a caution came out as "there's something wrong with your hard drive, you should give it to any service of Toshiba for warranty".
But it happened because I played on users, I mean users option for windows, not something material, changing just the current user name caused this and he now has weird name when I reversed the name change; He turned to something like TOSH ~ 1, etc.After several times, I mean like 1 month ago, my computer got very slow. Video games with their high resolution, but now the phone LAGS even I put it in low resolution, I played... I did not change any material or touched. But it is frustrating to see that I can't do the things I used to do more.
Another thing is, I'm afraid of the heat from the laptop. Is it normal to have 49-50 degrees? Because when I play games, it is around this level. I live in a hot city.
Some people asked me to use HD Tune to check that if I have a bad sector on the hard drive, I did. Does not work either.
I deleted some of my files to get the free space on my HARD drive also, likely 150 concerts altogether. I even wiped the empty space in my HDD via CCleaner. I often do the basis of registry-fix with it as well. Movies and games flash hangs out as well. And sometimes when I watch videos, the sound cuts, so I have to pause, and then click play it again to fix it but it happens in various video players, not youtube. Very probably all watching anime.And what do I do? I don't want to go for the service, I'm sure they'll make me wait several weeks of 100%. I use usually my laptop with its adapter. Oh and, over the life of my laptop, 2 - 3 times he got stopped himself while it wasn't on the map whenever I check, he was really but really hot.
So, what should I do? I don't want to open the computer to look inside, I do not understand, and he would risk my 2 year warranty.
I am looking forward for your answers, I'll be very happy. Thank you.
Post edited by: Blizzart (model added to the topic)
It is not easy to say what the problem is here. In General, you should think about upgrading the RAM to the maximum level. With more RAM laptop should have more power and different operations should be made much more quickly.
To make my laptop better and faster I ve upgraded RAM to the maximum level and also changed SSD HARD drive. So big difference there and phone now works like a rocket. Think about upgrading RAM.
> Another thing is, I'm afraid of the heat from the laptop. Is it normal to have 49-50 degrees?
From my point of view, this temperature is normal and certainly not too high. When you use your laptop, place it on the office and ensure that the cooling fan and cooling rack are free and not blocked.Don t open your laptop. Anyway, you can't do anything except to void your warranty. RAM upgrade can be done by the owner of the laptop and it will not void your warranty.
-
Why USB-6501 does not install on Win7?
We are in a process of migration of the old XP machine test system to the new system of Win7. All but got properly installed USB-6501. After you install LabView / DAQmx and connection USB-6501 windows could not find the drivers for this device (poster the exclamation sign on the icon of the device in devices and printers). MAX 4.7.4 detects either of the device. I looked for similar scenarios on the Forum OR and abroad and tried the solutions proposed. Nothing worked for me. I know the issue isn't with the USB-6501 material because it is functional on the old system. 4.7.4 MAXLE Win7 system detects a very well (GPIB-USB-HS) different USB device, but not for USB-6501.
I hope someone can help us identify the problem that we have struggled with for some time. Here are the differences between shipments of software on two systems:
Old system:
OS - XP SP3
LabView - 7.0
DAQmx - 8.0
VISA - 4.4.1
MAX - 4.5 (detects the GPIB-USB-HS and USB-6501.) Status on 6501 LIGHT flashes continuously)
New system:
OS - Win 7 Enterprise
LabView - 7.0
DAQmx - 9.2.2
VISA - 5.0.3
MAX - 4.7.4 (detects only GPIB-USB-HS. Status on 6501 LIGHT flashes 3 times and then road)
Germano,
The device has been appear in Manager devices, but with the yellow exclamation mark for no drivers found/expenses. Update drivers on the property page does not help.
So yesterday I spent most of the day removing all facilities OR according to the instructions, I found in this forum. Then I reinstalled the software OR in the order following, restarting after each installed:
(1) LabView 7.0
(2) DAQ 8.0.1
(3) NEITHER-488. 2 (v2.30)
(4) connected USB-6501 first. The installation of the device has gone well and is now detected to the MAX!

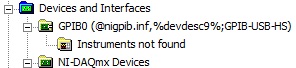
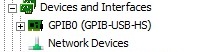
(5) connected GPIB-USB-HS. Scanned for changes on the hardware, peripheral GPIB presents itself to the MAX, but with a weird name announcement its INF file on his behalf. See the screenshots below:
GPIB device incorrectly installed:
GPIB device properly installed:
The strange thing is that this GPIB device was fully functional on my previous installation (see attachment max_report_3-23 - 11.pdf), now reinstall after its unusable (see attached max_report_3-24 - 11.pdf). Looking for GPIB instruments to help Max returns no result, but if I reconnect GPIB-USB-HS to the old system of PC all instruments are detected (for instrument scan error message see attached MAX after reinstall.jpg).
That my new problem is not related to USB-6501, maybe I should open a new forum thread.
-
Various problems about how to fix the corruption?
I quickly and desperately need help.
So, I listen to music on Windows Media Player. All my music is located on drive F, while the program itself is on a different drive. Suddenly, the song I listen to starts glitching. I close the program and try to restart. When it doesn't, I think it's just because the process did not finish completely. I try to open the Task Manager, but it will not. Then, when I try to open the F drive, it says it's corrupt. I restart my computer to perform the CHKDSK command. Many files will eventually be deleted. I think that too much dust got into my lap, but I did my best to fix this before restarting. In any case, fortunately, I got almost all of my files backed up, but when I try to copy them in F, it is said that he only TI-Cycle Redundancy Check. Naturally, this freaked me out. Meanwhile, I'm trying to open the Task Manager, but fail. To do this, this thing where he's looking for the file and asks me if I want to watch myself. I do this and go to the Drive E. But all the files in System32 have weird names, such as symbols and lines and other things. And when you hover over them, it has the same weird thing for the listed file type. I need to check that too? But it would be annoying that all the files on E has been deleted, since the filesystem there. Anyone know how to solve these problems? Help, please!
Hey SyberiaWinx,.
Reading your question, I have found a thread which I think will be very useful for you.Look at this thread and try the procedure described in the above thread and try these steps. If you have any questions, return to this topic and explain what were your results. Be sure to include all the details that you can when you describe your results.Thanks for posting of Microsoft Answers! Good luck with the troubleshooting. -
Try these two key entries when the central screen of the mail is present...
"Alt + t", then "c" that should work for Windows Live Mail 2009 (if it is the version you have).
Mr. bus bar:
Thank you for your patience. I've isolated the problem. The fact is that my account has been hijacked selectively. Most of the emails that I saved was not made by the attack, so if I answer them I don't get the * address email is removed from the privacy *. Unfortunately, many of the largest are requested and I do, in fact, get this weird name in the address bar. Incidentally, this address is for box in music/Ipod _ which I never use. My theory is that my daughter, who is, download such things, may be transferred to me. How I don't know, but the fact is that the pirate has made it impossible for me to answer my important contacts, which are about forty percent of my saved emails. I already created a new account also. I don't need advice on setting up a new account or change my password. I need advice to get rid of the intruder. The link suggested by one of the techs that I change my password and all other suggestions could not get rid of* address email is removed from the privacy *. When I use the link simply compromised account shows me something I've already tried. My question is this: "How do I get rid of this hijacker of air? I was going to download a program called Mailwash, but I'm not even sure it will work. If I'm at an impasse it please let me know. I have to do my business in a new account.
Thank you,-Wordsmith
-
What is this folder - C:\Windows\winsxs?
What is this C:\Windows\winsxs folder?
It is more than 4 GB... !!!I donno if I should delete or do it... because my disk space is weak now... a free 30 GB for Win7 and got only 2 GB disk...and the folder above contained as backup and some weird names... etc.Examples:x86_microsoft-windows - naturallanguage6_31bf3856ad364e35_6.1.7600.16385_none_9db12a5d8c0f6a9ex86_microsoft-windows-s chrecognizerenu.ale_31bf3856ad364e35_6.1.7600.16385_en - us_ce081cc30a31a65bx86_microsoft-windows-s chrecognizereng.ale_31bf3856ad364e35_6.1.7600.16385_en - gb_8785abd0727554a4and a folder named backup with content.x86_microsoft-windows-font-truetype - mingliub_31bf3856ad364e35_6.1.7600.16385_none_c8f7fdc19988b363_mingliub.ttc_b8743970x86_microsoft-windows-f e - microsoftjhenghei_31bf3856ad364e35_6.1.7600.16385_none_65170ea6416887a4_msjh.ttf_ea675e5cand so on...Is it a temporary folder or something that downloads updates and records here, or it creates a backup?If you remove winsxs your operating system (Windows 7) will no longer work. This article is also applicable to Windows 7:
What is the WINSXS Win2008 and Vista directory and why is it so important?
Here are some suggestions for the release of disk space:
http://www.WinVistaClub.com/T73.html
Or maybe you should buy a bigger hard drive. MS - MVP - Elephant Boy computers - don't panic!
-
Speakers Logitech Z313 stopped working after upgrading to Windows 7
I delayed upgrading to Windows 7 until after I graduated from College just for this reason. I just installed Windows 7 and my Logitech Z313 speakers that worked perfectly well in Windows XP are not recognized as material.
There is no yellow! device drivers, I have the "High Def Audio" largest later device driver installed. Troubleshooting Windows does not detect a problem with anything. My speakers are working properly. When I disconnect or shut down the PC, I can hear the feedback and the pop Logitech has no drivers for these speakers because they must be detected automatically by the system when they are connected. I tried unplugging / plugging in different ways.
Can anyone help?
Thank you.
Hello
I quite had the same problem and found the solution: you must uninstall your device, then go to control-online Device Manager Panel => are looking for the "!" symbol on your list, then right click on 'properties' and 'details', you will see a list with weird names (ex: HDAUDIO\FUNC_01 & VEN_10EC & DEV_0662 & SUBSYS_18497662)
Copy it and go to
, paste it into the search bar, and then select your 'Windows' (for me it was 10 Win 64-bit), download the driver and install it. Fact! :-) Problem solved ^^ not by Microsoft or Logitech, unable to understand this problem, caused by the update of Windows 10... (-_-(
Maybe you are looking for
-
How to sue a link is safe until I click on it
My friend sent me a link via email that she thought I would find interesting. How can I make sure that it is safe, before I open it?
-
Finally, I installed sp2 and everything now works very well only I have a problem:When the s1 is well unplugged the power cord and I start it, I get after you have filled my passw a blue screen. then the pc restarts, same problem, restarts and so on.
-
I try to save the result of running the xcopy by command line, but without success. Any suggestion? Please rename the xcopy.vi attached to xcopy.exe
-
Kodak esp3250 drivers do not install on Windows XP Professional 64-bit
Hello I just want to ask if it is possible to download drivers for my Kodak ESP 3250 printer. I heard that it is not compatible with Windows XP Professional 64-bit machines, but I think that it is not true. Thank you Zuga01
-
I use MSN Mail Premium on Microsoft Windows XP and these past months we started to have problems when you go to msn mail.It has become very slow and freezes. We get a message saying that he does not. Or we can be in mail and from the box tojunk mai