Check EZVPN ASA-to - ASA
I have a remote location with about 10 PCs and users behind it. I am currently using a standard IPSEC S2S connection but (don't ask, long story) the site soon will move to an ISP who can give him it is the own public IP address. You get a private on its external interface IP address and using a NAT behind the public IP address of the ISP endangered. This obviously means that I can't use a normal IPSEC tunnel. My thought was to EZVPN to connect the clients/subnet behind the ASA remote to subnets behind the ASA HQ. I just need someone for the sanity check my work. Here's the config EZVPN I plan on adding the remote control and HQ ASAs. I want that all traffic to RFC 1918 IPs to travel through the tunnel, while the internet traffic to the remote site continues to get out its own connection and not in the tunnel.
192.168.98.0 24 will be the subnet to the remote site. The HQ site has subnets in all 3 areas of RFC 1918.
--------------------------------------------
ASA HQ CONFIG:
inside_nat0_outbound list of allowed ip extended access all 192.168.98.0 255.255.255.0
NAT (inside) 0-list of access inside_nat0_outbound
EZVPNSPLIT list of allowed ip extended access any 192.168.0.0 255.255.255.0
EZVPNSPLIT list of allowed ip extended access any 10.0.0.0 255.0.0.0
EZVPNSPLIT list of allowed ip extended access any 172.16.0.0 255.240.255.0
crypto ISAKMP allow outside
crypto ISAKMP policy 10
preshared authentication
3des encryption
sha hash
Group 2
life 86400
internal RemoteTG group strategy
attributes of Group Policy RemoteTG
Protocol-tunnel-VPN IPSec
Split-tunnel-policy tunnelspecified
Split-tunnel-network-list EZVPNSPLIT
value by default-field
allow to NEM WebVPN username password remote CLI! privilege 0 username remote attributes VPN-group-policy RemoteTG type tunnel-group RemoteTG remote access attributes global-tunnel-group RemoteTG Group Policy - by default-RemoteTG IPSec-attributes tunnel-group RemoteTG pre-shared key CLI! ----------------------- ASA REMOTE CONFIG: vpnclient Server
vpnclient mode network-extension-mode vpnclient vpngroup password CLI RemoteTG! vpnclient username password remote CLI! vpnclient enable Overall, it seems. Two things: (1) on the SAA, normally a standard ACL is used for split Tunneling, but the scope can also work. Some subnet masks were wrong in your ACL: EZVPNSPLIT list standard access allowed 10.0.0.0 255.0.0.0 EZVPNSPLIT list standard access allowed 172.16.0.0 255.240.0.0 EZVPNSPLIT list standard access allowed 192.168.0.0 255.255.0.0 (2) if it isn't already in your config file (and depending on your version) you must enable NAT-Traversal: Crypto isakmp nat-traversal 20 -- Tags: Cisco Security Cisco ezvpn ASAs cannot ping each other inside interfaces I have a set ezvpn in place with a 5506 (position B) client-side and a 5520 (location A) server-side. I have successfully connected vpn, and traffic flows. My problem is that I can't SSH in the location b. investigate this more than I can not ping is within the interface of the ASA opposing, or the machines inside each ASA ASA. I found the following links that describes a scenario similar to mine, but nothing on one of them helped me. I joined sanitized versions of these two configs. Any help is appreciated. Hi Adam The site of B I'm not able to see "management of access to inside. Please try to set up the same. He could solve the problem. Also on the instruction of the ASA takes place nat can you please try to add keywords 'search non-proxy-arp route'. something like: Customer behind EzVPN remotely (ASA 5505) Hello I try to set up a simple EzVPN infrastructure: EzVPN Server (CISCO2811, hostname cme) < --=""> EzVPN remotely (ASA5505, hostname ezvpn - asa) < --=""> Client Attached you will find the two server EzVPN configuration and remote control. The tunnel is getting up and if I ping from the ASA to the router, I see the packets be encrypted: ezvpn - asa # ping 172.16.100.1 ... ezvpn - asa # crypto ipsec to show her Interface: outside Tag crypto map: _vpnc_cm, seq num: 10, local addr: 172.16.100.2 _vpnc_acl the host 172.16.100.2 ip access list permit 172.16.100.1 local ident (addr, mask, prot, port): (172.16.100.2/255.255.255.255/0/0) Remote ident (addr, mask, prot, port): (172.16.100.1/255.255.255.255/0/0) current_peer: 172.16.100.1, username: 172.16.100.1 dynamic allocated peer ip: 0.0.0.0 #pkts program: 5, #pkts encrypt: 5, #pkts digest: 5 decaps #pkts: 5, #pkts decrypt: 5, #pkts check: 5 compressed #pkts: 0, unzipped #pkts: 0 #pkts uncompressed: 5, comp #pkts failed: 0, #pkts Dang failed: 0 success #frag before: 0, failures before #frag: 0, #fragments created: 0 Sent #PMTUs: 0, #PMTUs rcvd: 0, reassembly: 20th century / of frgs #decapsulated: 0 #send errors: 0, #recv errors: 0 If I connect a customer with IP 192.168.1.2 interface eth0/1 and do a ping to the cme, I see not all packets are encrypted. I have no idea on the VPN, I just need a wireless lab environment. I need to configure on the SAA, so the Interior traffic is encrypted? Thanks in advance and best regards Dominic Hello Looks like you are missing split-tunnel list in 2811. Please see the link to the example configuration below. HTH MS Hello I didn't send a CX module before. We are about to deploy firewalls 2xASA5585-X with CX (for STROKE and WSE) modules. I'm sure I know the answer to this (I've deployed a lot of old OLD ASA with CSC modules in them, and I'm guessing that the CX module has the same). 1 will be the failure of the module CX trigger a failover event (fail-over active standby)? My guess is not? 2. If it is not and policy service is set to 'closed' this means that the client should perform a manual failover to the secondary/sleep to restore access, web - this correct? Pete Hi Pete,. 1 will be the failure of the module CX trigger a failover event (fail-over active standby)? My guess is not.? Yes he custom of tipping your ASA, depends on configuration either will be allowed or close the traffic In the area if ASA CX card fails, click permit traffic or close traffic. The narrow traffic option defines the ASA to block all traffic if the ASA CX module is not available. Permits for movement option sets the ASA to allow all traffic through, if not inspected, the ASA CX module is not available. 2 if it is not and the service policy is set to 'closed' this means that the client should perform a manual failover to the secondary/sleep to restore access, web - this correct? .When set to allow traffic CX failure, there is no need to manually failover your ASA firewall between HA Step 8 http://www.Cisco.com/c/en/us/TD/docs/security/ASA/Quick_Start/CX/cx_qsg.html#wp49530 Hi all I want to make a file any cleaning on my 5505 without affecting any of its services. could someone throw me a glance and to highlight what should be removed? Thanks in advance! ASA5505 # dir Directory of disk0: /. 152 - rwx 27260928 13:53:20 November 24, 2012 asa901 - k8.bin 153 - rwx 4181246 07:32:20 5 June 2010 securedesktop - asa - 3.2.1.103 - k9.pkg 154 - rwx 398305 sslclient-victory - 1.1.0.154.pkg June 5, 2010 07:32:38 155 - rwx 17449432 13:23:38 November 24, 2012 asdm - 701.bin 156 - rwx 14240396 15:53:48 asdm - 631.bin March 11, 2010 drwx 17 4096 07:36:28 crypto_archive June 5, 2010 10 drwx 4096 Journal 22:12:48 December 4, 2010 158 - rwx 1530 04:31:54 7_2_4_0_startup_cfg.sav May 17, 2013 18 drwx 4096 22:13:20 coredumpinfo December 4, 2010 159 - rwx 4096 03:00:06 14 April 2013 ._asa901 - k8.bin 160 - rwx 4096 03:00:10 14 April 2013 ._asdm - 701.bin drwx 161 4096 12:01:08 .fseventsd 14 April 2013 162 - rwx 4096 23:38:12 December 4, 2010. _. Trashes drwx 163 4096 23:38:12 December 4, 2010. Trashes drwx 164 4096 23:38:14 December 4, 2010. Spotlight-V100 165 - rwx 15943680 15:51:14 March 11, 2010 asa831 - k8.bin 166 - rwx 28119320 13:23:52 24 November 2012 asdm-demo - 701.msi 167 - rwx 4096 03:00:16 14 April 2013 ._asdm-demo - 701.msi 168 - rwx 1189 00:42:28 upgrade_startup_errors_201304140042.log 14 April 2013 169 - rwx 1189 09:36:58 upgrade_startup_errors_201304140936.log 14 April 2013 170 - rwx 1189 22:13:20 upgrade_startup_errors_201012042213.log December 4, 2010 171 - rwx 1189 04:11:30 upgrade_startup_errors_201305060411.log 6 may 2013 172 - rwx 1189 22:52:32 upgrade_startup_errors_201012042252.log December 4, 2010 173 - rwx 1189 06:41:10 upgrade_startup_errors_201305090641.log may 9, 2013 174 - rwx 1189 02:45:26 upgrade_startup_errors_201012050245.log December 5, 2010 175 - rwx 1189 06:34:08 May 10, 2013 upgrade_startup_errors_201305100634.log 176 - rwx 1189 15:19:34 upgrade_startup_errors_201012111519.log December 11, 2010 177 - rwx 1189 03:38:04 16 may 2013 upgrade_startup_errors_201305160338.log 178 - rwx 1189 17:04:14 upgrade_startup_errors_201012121704.log December 12, 2010 179 - rwx 1189 04:31:58 upgrade_startup_errors_201305170431.log may 17, 2013 180 - rwx 1189 21:44:30 upgrade_startup_errors_201101252144.log January 25, 2011 181 - rwx 100 05:50:40 upgrade_startup_errors_201306300550.log 30 June 2013 182 - rwx 200 06:20:12 upgrade_startup_errors_201306300620.log June 30, 2013 183 - rwx 14524416 05:50:46 July 27, 2013 asa802 - k8.bin 184 - rwx 2142 05:23:44 8_0_2_0_startup_cfg.sav 25 October 2013 185 - rwx 1138 03:33:20 upgrade_startup_errors_201308290333.log August 29, 2013 186 - rwx 1138 05:23:48 upgrade_startup_errors_201310250523.log October 25, 2013 total 127111168 bytes (2596864 bytes free) first check what ASA version you are running (see version). If you run the 9.1 version then you can remove 183 - rwx 14524416 05:50:46 July 27, 2013 asa802 - k8.bin 165 - rwx 15943680 15:51:14 March 11, 2010 asa831 - k8.bin check what ASDM version you are running (version show and show run asdm). If you are running version 7.1 so you can remove 56 - rwx 14240396 15:53:48 asdm - 631.bin March 11, 2010 You have two 7.1 pictures and a few demo also. Demos, you should be able to withdraw without a problem, but you must identify what VersionYesYou ASDM are running before you remove the extra 7.1 166 - rwx 28119320 13:23:52 24 November 2012 asdm-demo - 701.msi 167 - rwx 4096 03:00:16 14 April 2013 ._asdm-demo - 701.msi 160 - rwx 4096 03:00:10 14 April 2013 ._asdm - 701.bin 155 - rwx 17449432 13:23:38 November 24, 2012 asdm - 701.bin You should be able to remove any of the upgrade starts the error logs... unless you need it for future documentation. "ITS creation failed" problem for IPSec VPN An ASA 5100 is used to provide VPN access for my business. The configuration was made by a permeable man who has been missing for some time, and the configuration used to be OK until this morning. This morning, some users reported that their VPN would have fallen once got connected. I checked the ASA and ASDM, I see every time when user deletes, it IPSec tunnel is always action. Furthermore, I faked the problem and got the newspaper of errors such as: 1 11:14:45.898 12/06/07 Sev = WARNING/3 IKE/0xE3000065 could not find an IKE SA for 10.2.1.8. Abandoned KEY_REQ. 2 11:14:45.898 12/06/07 Sev = WARNING/2 IKE/0xE3000099 could not open the P2 generate a new key: error detected(Initiate:176) 3 11:14:45.898 12/06/07 Sev = WARNING/2 IKE/0xE3000099 cannot open the QM (IKE_MAIN:458) On the side of the AS I did "debug crypto isakmp" and 'debug crypto ipsec' and I got the following errors: iscoasa # ERROR IPSEC: expiration of the timer of the asynchronous operation, SPI: 0x114CA5B6, user: roeladmin, peer: 202.x.x.70, time: 2 seconds, ctm_ipsec_create_sa:856 IPSEC ERROR: Material outside ITS create command failed, SPI: 0x114CA5B6, error code: 0 x 17 IPSEC ERROR: Asynchronous Operation timeout expired, SPI: 0x61BE2022, user: roeladmin, peer: 202.x.x.70, time: 2 seconds, ctm_ipsec_create_sa:856 IPSEC ERROR: Cannot add a user auth, SPI input: 0x61BE2022, user: roeladmin, peer: 202.172.62.70 IPSEC ERROR: Cannot create an inbound SA SPI: 0x61BE2022 document IPSEC ERROR: Unable to complete the command of IKE UPDATE 12 June at 14:25:13 [IKEv1]: Group = LANWORKS, Username = roeladmin, IP = 202.172.62.70, error QM WSF (P2 struct & 0 x 4699058, mess id 0xf37ec6f4). 12 June at 14:25:13 [IKEv1]: Group = LANWORKS, Username = roeladmin, IP = 202.172.62.70, peer table correlator Removing failed, no match! IPSEC ERROR: Material Inbound ITS create command failed, SPI: 0x61BE2022, error code: 0 x 17 It shows that ITS creation has failed. But I can't find the problem with the configuration. Can someone help me on this? Thank you Outgoing material ITS create command failed, SPI: 0x114CA5B6, error code: 0 x 17 It is a hardware problem, reset the firewall and it will work, I saw 4 times in different ASAs Please hate the post if help. I set up a new connection profile for remote access using IKEv2 instead of ssl. I used the following link for instructions: https://supportforums.Cisco.com/document/74111/ASA-AnyConnect-IKEv2-CONF... It's pretty simple, but it does not work for me. When I try to connect to the profile connection I get the following error: "Connection refused, mechanism of connection not allowed, contact your administrator." I have not configured any DAP records he is just using the default which allows all connections. I'm not really finding much too much information on this error, anyone know what I can do to fix this? Thank you! I just checked our ASA. Your config is very similar to mine. I don't have this line: Several groups of ACS/announcements in NDG Hello I've been racking my brain on this for a few days, and it's just not coming to me. I'll try and also be suscinct as possible. I am in the process of transition of my users of IPSEC to SSL VPN client/web. During this process, I want to limit users to what they need to get to only. ASA firewall configured for SSL VPN and IPSEC VPN (8.2.1) Cisco ACS for Windows (4.2) Active Directory Windows domain We have several departments who will each of the different levels of access. We currently have a group of users who belong to an ad group that is mapped to an ACS group. Everthing is going fine for the IPSEC VPN and SSL VPN as it is. The problem that I am running is adding a new group (s) adding to the mix and get the right checks up to join this group. Example: If you are in the OWA ad group, you should only have access to OWA when you access SSL VPN. Example: If you are in the ad Marketing Group, you should have access to the actions and resources that are predefined. There could be up to 10 groups. I have added a new group to the ACS server and it mapped to the corresponding group. But I guess I don't understand how to get the ASA--> ACS to verify membership in this group. I tried the DAP of ASA with controls against the Radius attributes - but it fails. I feel just like I'm missing something in the ACS server, I need to do first. Thanks in advance for the help. Hi Chris, By checking groups, ASA, GBA package access attribute class only reads accept, depending on the value of class the asa will map like you on a policy of group as your configuration. ACS will read the first memberOf value retrieved from the profile AD and map the user to the group, accordingly, so if you have multiple groups on one user it will always match one on the list (don't ask me what is the order that AD sends the group for GBA) The first statement, I think you will need that many strategies of groups like the functions you need and based on the value of the class they will be mapped to this group policy and then these features will be enabled. I believe that with the radius authentication plain and RADIUS atts or DAP (dap gives you more customization options), so you can skip ACS and use ASA - ldap - AD) and use memberOf attributes. Let me know if this has any sense at all. Management access to an ASA5505 via connection NEM Hello I work with a configuration ASA5505 NEM. Everything works well except the access to content the device across the tunnel. From the ASA local network I can access the device via HTTPS, Telnet and SSH, but it does not work in France via the tunnel. I am running version 7.2 (4). No idea what I am doing wrong? Thank you There is no attachment in your post... You can check out asa have access to the administration: See the race | Management Inc. If no output from the top Configure asa with stated below, then try to access to asa by tunnel. management-access inside PLS note any useful message Rgds Jorge Hello I'm deploying an SSL VPN in ASA 8.0, I have access to the public interface and authentication configured radius. I have the debug RADIUS in asa and I see authentication is OK, I also checked Ray asa and works for the authentication test button, but It does work for approval. I've already set up a local user to the radius server. Thanks for your help. Best regards Fran You may be hitting a license limit if a few sessions have not stopped correctly and that you have only the default value of 2 licenses SSL... Do 'show worm' to see how much you have licenses webvpn. Also try "vpn-sessiondb disconnection of all" to delete all existing connections. -heather Difference between IPSec over TCP and UDP IPsecover Hello world I'm testing the VPN to the user's PC. When I test the PC of the user using IPsecoverTCP it uses protocol 10000. When I check on ASA - ASDM under connection details ike1 - UDP Destination Port 500 IPsecOverTCP TCP Dst Port 10000 using Ipsecover UDP IKEv1 - Destination UDP 500 Port IPsecOverUDP - Port of Destination UDP Tunnel 10000 Therefore when using TCP or UDP uses the same port 500 and 10000. Is need to know what is the major difference between these two connections just TCP or UDP? Concerning MAhesh IPSec over TCP is used in scenarios where: 1 UDP port 500 is blocked, resulting in incomplete IKE negotiations 2 ESP is not allowed to cross and encrypted traffic thus do not cross. 3. network administrator prefers to use a connection oriented protocol. 4. IPSec over TCP may be necessary when the intermediate NAT or PAT device is stateful firewall. As there are IPSec over UDP with IPSec over TCP, there is no room for negotiation. IPSec on the TCP packets are encapsulated from the beginning of the cycle of implementation of the tunnel. This feature is available only for remote access VPN not for tunnel L2L. Also does not work with proxy firewall. While IPSec via UDP, similar to NAT - T, is used to encapsulate ESP packets using a UDP wrapper. Useful in scenarios where the VPN clients don't support NAT - T and are behind a firewall that does not allow the ESP packets to pass through. IN IPSec over UDP, the IKE negotiations has always use port UDP 500. Hi guys,. In Cisco ASA 5505 ASDM, is there a way to see the remaining LIFE expectancy for DNS entries. With the CLI, you can use the dns #show command and shows the remaining LIFE. How I see with ASDM? (Background: I use FQDN based ACL and therefore I would not like to see TTL in ASDM) Thank you and best regards, Rahul HI -. I checked my ASA and that information does not appear to be exposed in ASDM. I am running version 7.4 ASDM (2). PSC ASA 8.4 (6) "cannot retrieve or check the CRL. Hello I have configured our ASA to retrieve a list of Revocation provided through our Linux certification authority. The LCR is exported via Tinyca as a crl file and served by Apache. The file is accessible by the SAA and to date, I see an http 200 (OK). Despite this, I get an "impossible to extract or to check the Revocation list. The ASA is configured as follows: crypto ca trustpoint LINUX-CA-TP Which allows to debug and try a "request for LRC crypto ca LINUX-CA-TP: ASA (config)# crypto ca crl request LINUX-CA-TP CRYPTO_PKI: CRL is being polled from CDP http:// Unable to retrieve or verify CRL CRYPTO_PKI: transaction HTTPGetCRL completed I'm a little puzzled. The error is not really tell where the ASA is exactly a failure! Thank you Hello. I know this is a late response, but I found the solution. My CA was created through openssl commands and LCR was coppied to the www server. I installed the CA ASA certificate and I tried to check the Revocation list. But he has failed. It's the debug output: EzVPN between Cisco ASA 5505 (with NEM mode) and Ciscoo 881 Roure Hi friends, I configured the Cisco ASA 5505 and Cisco router with DMVPN 881. 3 offices works very well but one office remains failure. I did the same configuration for all facilities but this router does not work. Any ideas? Please find below the exit of 881 router Cisco: YF2_Tbilisi_router #. * 09:31:46.793 4 August: ISAKMP: (0): removal of reason ITS status of 'Death by retransmission P1' (I) AG_INIT_EXCH (peer 1.1.1.1) * 4 August 09:31:47.805: del_node 2.2.2.2 src dst 1.1.1.1:500 fvrf 0 x 0, ivrf 0 x 0 * 4 August 09:31:47.805: ISAKMP: (0): profile of THE request is (NULL) * 4 August 09:31:47.809: ISAKMP: (0): Beginner aggressive Mode Exchange
* 09:32:47.809 4 August: ISAKMP: (0): removal of reason ITS status of 'Death by retransmission P1' (I) AG_INIT_EXCH (peer 1.1.1.1) * 4 August 09:32:48.909: del_node src 2.2.2.2:500 dst 1.1.1.1:500 fvrf 0 x 0, ivrf 0 x 0 * 4 August 09:32:48.909: ISAKMP: (0): profile of THE request is (NULL)
* 4 August 09:32:48.913: ISAKMP: (0): Beginner aggressive Mode Exchange There is no DMVPN on the SAA. All that you have configured, is not compatible with the ASA or something another DMVPN then. At least debugging shows that there are some EzVPN involved. The debug version, it seems that there is no communication on UDP/500 possible between devices. Maybe something is blocking who? ASA EzVPN with several remote subnets Hello world I'll have the challenge of EasyVPN installation based on ASA 5520, and ASA 5505 (with the ASA5505 as the vpnclient) with several networks behind the ASA 5505. Access by the network directly connected on the 5505 to the central site works very well. But the second network segment (which is behind a router on the directly connected network) cannot connect to the central site. I guess I need to specify that some sort of acl's to be able to do that. BTW we do not use tunneling split, because all traffic moves through the tunnel (no local internet access). The layout looks like this (--LAN--)-5520---5505-(--LAN1--)-ROUTER-(--LAN2--)-(WAN)- LAN1 and LAN connection works great through the EZVPN Tunnel. LAN2 connection to the LAN does not work through the Tunnel of EZVPN. Here is the configuration used so far (outside the normal SHEEP, groups of objects and stuff ISAKMP crypto): Client: vpnclient Server 10.x.x.x extension-mode network mode vpnclient EzVPN vpngroup vpnclient password *. vpnclient username user1 password *. vpnclient enable Crypto ipsec df - bit clear-df outdoors Server: internal EzVPN group strategy Group Policy attributes EzVPN allow to NEM allow password-storage tunnel-group EzVPN type ipsec-ra General characteristics of tunnel-group EzVPN Group Policy - by default-EzVPN IPSec-attributes tunnel-group EzVPN pre-shared key *. user user1 password *. I hope you can help Best regards Jarle Unfortunately, it is not supported on the platform of the SAA. With EasyVPN on the SAA, only the connected networks can be advertised. To accomplish what you want to do, you need to configure a static IPSec tunnel and announce local networks via ACL interesting traffic. You can also use an IOS device that does not have the capabilities of "multiple subnet" with EasyVPN. YouTube is slowing down my computer! Any suggestions? Hello dear friends, I have a good MacBook Pro 2013 retina with i7 and SSD. I have noticed occasionally when I Watch youtube videos and try to make comments, while I type it needs some time to let the letters appear. Is like takes me a lot of energy a After fighting the photos 'upgrade' included with El Capitan, I managed to return to iPhoto 9.0.9 before has been damaged. Subsequently located iPhoto 9.6.1 and plan to use it. Now more cautious than ever with the software Apple "upgrades", I would I need to change in my hard drives computer I need to change in my computer drives hard disk drives hard C E My laptop does not start at the top. It indicates that the following file is missing or damaged WINDOWS\SYSTEM32\CONFIG\SYSTEM. Download this file from the Microsoft Web site. I put the XP CD in and it starts downloading files but it asks what window HP Pavilion won't mode 'sleep' I have a HP Pavlillion, which is about 3 years old. Recently the comeputer going on "standby mode" (or when I put it in mode "sleep"), but continuous computer to go in and out of fashion 'sleep'. It is as if the computer goes in "standby mode" then a
Don't stop once you have upgraded your network! Improve the world by lending money to low-income workers:
http://www.Kiva.org/invitedBy/karsteniSimilar Questions
http://www.experts-exchange.com/questions/28388142/cannot-ping-ASA-5505-inside-interface-across-VPN.html
https://www.fir3net.com/firewalls/Cisco/Cisco-ASA-proxy-ARP-gotcha.html
https://supportforums.Cisco.com/discussion/11755586/Cisco-ASA-VPN-established-cant-ping
nat (inside,outside) source static (Location A)_Networks (Location A)_Networks destination static (location B)-remote_network (location B)-remote_network no-proxy-arp route-lookup
as I have noted problems with inside access to interface via the VPN when those keywords are not applied. If I remember correctly 8.6.x ASA version had a bug regarding the same.
Cordially Véronique 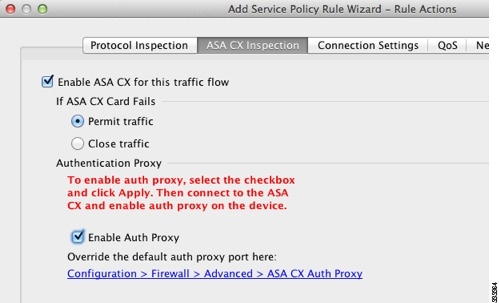
 check the ASA CX check this box traffic flow.
check the ASA CX check this box traffic flow.
anyconnect profiles ikev2-anyconnect_client_profile disk0:/ikev2-anyconnect_client_profile.xml
I also have a newer version of deployed AnyConnect:
anyconnect image disk0:/anyconnect-win-4.1.06020-k9.pkg 1 regex "Windows NT"
I found the customers *. Profile XML can be a little touchy. Here is an example of XML profile that I use:
revocation-check crl none
enrollment terminal
crl configure
policy static
url 1 http://
no protocol ldap
no protocol scep
vpn015pi(config)#
CRYPTO_PKI: HTTP response header:
HTTP/1.1 200 OK
Date: Wed, 18 Dec 2013 12:49:01 GMT
Server: Apache/2.2.22 (Ubuntu)
Last-Modified: Wed, 18 Dec 2013 09:50:20 GMT
ETag: ...
Accept-Ranges: bytes
Content-Length: 1170
Connection: close
Content-Type: application/x-pkcs7-crl
CRYPTO_PKI: CRL is being polled from CDP http://x.x.x.x/ca/root-ca/root-ca.crl.crypto_pki_req(0x00007fff2b9e3900, 24, ...)CRYPTO_PKI: Crypto CA req queue size = 1.Crypto CA thread wakes up!CRYPTO_PKI: http connection openedCRYPTO_PKI: content dump count 81----------CRYPTO_PKI: For function crypto_http_sendGET /ca/root-ca/root-ca.crl HTTP/1.0Host: x.x.x.x
CRYPTO_PKI: For function crypto_http_sendCRYPTO_PKI: content dump-------------------
CRYPTO_PKI: HTTP response header: HTTP/1.1 200 OKDate: Wed, 13 Jan 2016 08:10:01 GMTServer: Apache/2.4.7 (Ubuntu)Last-Modified: Tue, 12 Jan 2016 10:12:50 GMTETag: "31c-529204bc05097"Accept-Ranges: bytesContent-Length: 796Connection: closeContent-Type: application/x-pkcs7-crl
CRYPTO_PKI: CRL data2d 2d 2d 2d 2d 42 45 47 49 4e 20 58 35 30 39 20 | -----BEGIN X509 ...
CRYPTO_PKI: transaction HTTPGetCRL completedCrypto CA thread sleeps!CRYPTO_PKI: Failed to retrieve CRL for trustpoint: ASDM_TrustPoint3. Retrying with next CRL DP...
Because the CRL file has been downloaded, I check my LCR with the command openssl on my linux server:
openssl crl -inform PEM -text -in crl/root-ca/root-ca.crl Certificate Revocation List (CRL): Version 2 (0x1) Signature Algorithm: sha256WithRSAEncryption Issuer: Last Update: Jan 12 10:09:33 2016 GMT Next Update: Jan 11 10:09:33 2017 GMT CRL extensions: X509v3 Authority Key Identifier: keyid:E9:5E:25:61:EB:5D:9D:7E:2E:1A:3A:DA:71:B3:7B:C2:55:8D:59:66
Authority Information Access: CA Issuers - URI:http://x.x.x.x/ca/root-ca/root-ca.cer
X509v3 CRL Number: 1No Revoked Certificates. Signature Algorithm: sha256WithRSAEncryption...
-----BEGIN X509 CRL-----...-----END X509 CRL-----
I founded CRL file is in PEM format. And because another available in LRC format is DER format I have converted to DER format and copied to the www server.
openssl crl -inform PEM -outform DER -in crl/root-ca/root-ca.crl -out crl/root-ca/root-ca-der.crl
After that I tried to download file CRL my ASA again and he succeeded.
CRYPTO_PKI: CRL is being polled from CDP http://x.x.x.x/ca/root-ca/root-ca.crl.crypto_pki_req(0x00007fff2b9e3900, 24, ...)CRYPTO_PKI: Crypto CA req queue size = 1.Crypto CA thread wakes up!CRYPTO_PKI: http connection openedCRYPTO_PKI: content dump count 81----------CRYPTO_PKI: For function crypto_http_sendGET /ca/root-ca/root-ca.crl HTTP/1.0Host: x.x.x.x
CRYPTO_PKI: For function crypto_http_sendCRYPTO_PKI: content dump-------------------
CRYPTO_PKI: HTTP response header: HTTP/1.1 200 OKDate: Wed, 13 Jan 2016 08:28:08 GMTServer: Apache/2.4.7 (Ubuntu)Last-Modified: Wed, 13 Jan 2016 08:25:54 GMTETag: "227-52932eb2c1926"Accept-Ranges: bytesContent-Length: 551Connection: closeContent-Type: application/x-pkcs7-crl
CRYPTO_PKI: CRL data30 ...
CRYPTO_PKI: Found suitable tpCRYPTO_PKI: Found suitable tpCRYPTO_PKI: Failed to create name objects to compare DNs. status = 1795CRYPTO_PKI(select cert) subject = ...CRYPTO_PKI: Found a subject match - inserting the following cert record into certListCRYPTO_PKI: Storage context locked by thread Crypto CA
CRYPTO_PKI: inserting CRLCRYPTO_PKI: set CRL update timer with delay: 31455520CRYPTO_PKI: the current device time: 08:30:53 UTC Jan 13 2016
CRYPTO_PKI: the last CRL update time: 10:09:33 UTC Jan 12 2016CRYPTO_PKI: the next CRL update time: 10:09:33 UTC Jan 11 2017CRYPTO_PKI: CRL cache delay being set to: 3600000CRYPTO_PKI: Storage context released by thread Crypto CA
CRYPTO_PKI: transaction HTTPGetCRL completedCrypto CA thread sleeps!
* 4 August 09:31:26.793: ISAKMP: (0): transmit phase 1 AG_INIT_EXCH...
* 09:31:26.793 4 August: ISAKMP (0): increment the count of errors on his, try 4 out 5: retransmit the phase 1
* 4 August 09:31:26.793: ISAKMP: (0): transmit phase 1 AG_INIT_EXCH
* 4 August 09:31:26.793: ISAKMP: (0): 1.1.1.1 package sending 500 peer_port 500 (I) my_port AG_INIT_EXCH
* 09:31:26.793 4 August: ISAKMP: (0): sending a packet IPv4 IKE.
* 4 August 09:31:36.793: ISAKMP: (0): transmit phase 1 AG_INIT_EXCH...
* 09:31:36.793 4 August: ISAKMP (0): increment the count of errors on his, try 5 of 5: retransmit the phase 1
* 4 August 09:31:36.793: ISAKMP: (0): transmit phase 1 AG_INIT_EXCH
* 4 August 09:31:36.793: ISAKMP: (0): 1.1.1.1 package sending 500 peer_port 500 (I) my_port AG_INIT_EXCH
* 09:31:36.793 4 August: ISAKMP: (0): sending a packet IPv4 IKE.
* 09:31:44.929 4 August: ISAKMP: (0): serving SA., its is 88961 B 34, delme is 88961 B 34
* 4 August 09:31:46.793: ISAKMP: (0): transmit phase 1 AG_INIT_EXCH...
* 09:31:46.793 4 August: ISAKMP: (0): the peer is not paranoid KeepAlive.
* 09:31:46.793 4 August: % CRYPTO-6-EZVPN_CONNECTION_DOWN: user (customer) = group = Youth_Facility_2 Server_public_addr = 1.1.1.1
* 4 August 09:31:46.793: ISAKMP:isadb_key_addr_delete: no key for address 1.1.1.1 (root NULL)
* 09:31:46.793 4 August: ISAKMP: (0): removal of reason ITS status of 'Death by retransmission P1' (I) AG_INIT_EXCH (peer 1.1.1.1)
* 09:31:46.793 4 August: ISAKMP: Unlocking counterpart struct 0x8AA90C50 for isadb_mark_sa_deleted(), count 0
* 09:31:46.793 4 August: ISAKMP: delete peer node by peer_reap for 1.1.1.1: 8AA90C50
* 09:31:46.793 4 August: ISAKMP: (0): entry = IKE_MESG_INTERNAL, IKE_PHASE1_DEL
* 09:31:46.793 4 August: ISAKMP: (0): former State = new State IKE_I_AM1 = IKE_DEST_SA
* 09:31:47.805 4 August: ISAKMP: (0): the peer is not paranoid KeepAlive.
* 09:31:47.805 4 August: ISAKMP: created a struct peer 1.1.1.1, peer port 500
* 09:31:47.805 4 August: ISAKMP: new created position = 0x8AA90C50 peer_handle = 0 x 80004819
* 09:31:47.805 4 August: ISAKMP: lock struct 0x8AA90C50, refcount 1 to peer isakmp_initiator
* 09:31:47.805 4 August: ISAKMP: (0): client configuration parameters 87531228 adjustment
* 09:31:47.805 4 August: ISAKMP: 500 local port, remote port 500
* 09:31:47.805 4 August: ISAKMP: find a dup her to the tree during his B 88961, 34 = isadb_insert call BVA
* 4 August 09:31:47.805: ISAKMP: (0): set up client mode.
* 4 August 09:31:47.805: ISAKMP: (0): built of NAT - T of the seller-rfc3947 ID
* 4 August 09:31:47.805: ISAKMP: (0): built the seller-07 ID NAT - t
* 4 August 09:31:47.805: ISAKMP: (0): built of NAT - T of the seller-03 ID
* 4 August 09:31:47.805: ISAKMP: (0): built the seller-02 ID NAT - t
* 4 August 09:31:47.805: ISKAMP: more send buffer from 1024 to 3072
* 09:31:47.805 4 August: ISAKMP: (0): ITS been pre-shared key and XAUTH authentication using id ID_KEY_ID type
* 09:31:47.805 4 August: ISAKMP (0): payload ID
next payload: 13
type: 11
Group ID: Youth_Facility_2
Protocol: 17
Port: 0
Length: 24
* 09:31:47.805 4 August: ISAKMP: (0): the total payload length: 24
* 09:31:47.809 4 August: ISAKMP: (0): entry = IKE_MESG_FROM_IPSEC, IKE_SA_REQ_AM
* 09:31:47.809 4 August: ISAKMP: (0): former State = new State IKE_READY = IKE_I_AM1
* 4 August 09:31:47.809: ISAKMP: (0): 1.1.1.1 package sending 500 peer_port 500 (I) my_port AG_INIT_EXCH
* 09:31:47.809 4 August: ISAKMP: (0): sending a packet IPv4 IKE.
* 4 August 09:31:57.809: ISAKMP: (0): transmit phase 1 AG_INIT_EXCH...
* 09:31:57.809 4 August: ISAKMP (0): increment the count of errors on his, try 1 5: retransmit the phase 1
* 4 August 09:31:57.809: ISAKMP: (0): transmit phase 1 AG_INIT_EXCH
* 4 August 09:31:57.809: ISAKMP: (0): 1.1.1.1 package sending 500 peer_port 500 (I) my_port AG_INIT_EXCH
* 09:31:57.809 4 August: ISAKMP: (0): sending a packet IPv4 IKE.
* 4 August 09:32:07.809: ISAKMP: (0): transmit phase 1 AG_INIT_EXCH...
* 09:32:07.809 4 August: ISAKMP (0): increment the count of errors on his, try 2 of 5: retransmit the phase 1
* 4 August 09:32:07.809: ISAKMP: (0): transmit phase 1 AG_INIT_EXCH
* 4 August 09:32:07.809: ISAKMP: (0): 1.1.1.1 package sending 500 peer_port 500 (I) my_port AG_INIT_EXCH
* 09:32:07.809 4 August: ISAKMP: (0): sending a packet IPv4 IKE.
* 4 August 09:32:17.809: ISAKMP: (0): transmit phase 1 AG_INIT_EXCH...
* 09:32:17.809 4 August: ISAKMP (0): increment the count of errors on his, try 3 of 5: retransmit the phase 1
* 4 August 09:32:17.809: ISAKMP: (0): transmit phase 1 AG_INIT_EXCH
* 4 August 09:32:17.809: ISAKMP: (0): 1.1.1.1 package sending 500 peer_port 500 (I) my_port AG_INIT_EXCH
* 09:32:17.809 4 August: ISAKMP: (0): sending a packet IPv4 IKE.
* 4 August 09:32:27.809: ISAKMP: (0): transmit phase 1 AG_INIT_EXCH...
* 09:32:27.809 4 August: ISAKMP (0): increment the count of errors on his, try 4 out 5: retransmit the phase 1
* 4 August 09:32:27.809: ISAKMP: (0): transmit phase 1 AG_INIT_EXCH
* 4 August 09:32:27.809: ISAKMP: (0): 1.1.1.1 package sending 500 peer_port 500 (I) my_port AG_INIT_EXCH
* 09:32:27.809 4 August: ISAKMP: (0): sending a packet IPv4 IKE.
* 4 August 09:32:37.809: ISAKMP: (0): transmit phase 1 AG_INIT_EXCH...
* 09:32:37.809 4 August: ISAKMP (0): increment the count of errors on his, try 5 of 5: retransmit the phase 1
* 4 August 09:32:37.809: ISAKMP: (0): transmit phase 1 AG_INIT_EXCH
* 4 August 09:32:37.809: ISAKMP: (0): 1.1.1.1 package sending 500 peer_port 500 (I) my_port AG_INIT_EXCH
* 09:32:37.809 4 August: ISAKMP: (0): sending a packet IPv4 IKE.
* 09:32:46.793 4 August: ISAKMP: (0): serving SA., his is 872E1504, delme is 872E1504
* 4 August 09:32:47.809: ISAKMP: (0): transmit phase 1 AG_INIT_EXCH...
* 09:32:47.809 4 August: ISAKMP: (0): the peer is not paranoid KeepAlive.
* 09:32:47.809 4 August: % CRYPTO-6-EZVPN_CONNECTION_DOWN: user (customer) = group = Youth_Facility_2 Server_public_addr = 1.1.1.1
* 4 August 09:32:47.809: ISAKMP:isadb_key_addr_delete: no key for address 1.1.1.1 (root NULL)
* 09:32:47.809 4 August: ISAKMP: (0): removal of reason ITS status of 'Death by retransmission P1' (I) AG_INIT_EXCH (peer 1.1.1.1)
* 09:32:47.809 4 August: ISAKMP: Unlocking counterpart struct 0x8AA90C50 for isadb_mark_sa_deleted(), count 0
* 09:32:47.809 4 August: ISAKMP: delete peer node by peer_reap for 1.1.1.1: 8AA90C50
* 09:32:47.809 4 August: ISAKMP: (0): entry = IKE_MESG_INTERNAL, IKE_PHASE1_DEL
* 09:32:47.809 4 August: ISAKMP: (0): former State = new State IKE_I_AM1 = IKE_DEST_SA
* 09:32:48.909 4 August: ISAKMP: (0): the peer is not paranoid KeepAlive.
* 09:32:48.909 4 August: ISAKMP: created a struct peer 1.1.1.1, peer port 500
* 09:32:48.909 4 August: ISAKMP: new created position = 0x8AA90C50 peer_handle = 0 x 80004818
* 09:32:48.909 4 August: ISAKMP: lock struct 0x8AA90C50, refcount 1 to peer isakmp_initiator
* 09:32:48.909 4 August: ISAKMP: (0): client setting Configuration parameters 88C05A48
* 09:32:48.909 4 August: ISAKMP: 500 local port, remote port 500
* 09:32:48.909 4 August: ISAKMP: find a dup her to the tree during the isadb_insert his 87B57D38 = call BVA
* 4 August 09:32:48.909: ISAKMP: (0): set up client mode.
* 4 August 09:32:48.909: ISAKMP: (0): built of NAT - T of the seller-rfc3947 ID
* 4 August 09:32:48.909: ISAKMP: (0): built the seller-07 ID NAT - t
* 4 August 09:32:48.909: ISAKMP: (0): built of NAT - T of the seller-03 ID
* 4 August 09:32:48.909: ISAKMP: (0): built the seller-02 ID NAT - t
* 4 August 09:32:48.909: ISKAMP: more send buffer from 1024 to 3072
* 09:32:48.913 4 August: ISAKMP: (0): ITS been pre-shared key and XAUTH authentication using id ID_KEY_ID type
* 09:32:48.913 4 August: ISAKMP (0): payload ID
next payload: 13
type: 11
Group ID: Youth_Facility_2
Protocol: 17
Port: 0
Length: 24
* 09:32:48.913 4 August: ISAKMP: (0): the total payload length: 24
* 09:32:48.913 4 August: ISAKMP: (0): entry = IKE_MESG_FROM_IPSEC, IKE_SA_REQ_AM
* 09:32:48.913 4 August: ISAKMP: (0): former State = new State IKE_READY = IKE_I_AM1
* 4 August 09:32:48.913: ISAKMP: (0): 1.1.1.1 package sending 500 peer_port 500 (I) my_port AG_INIT_EXCH
* 09:32:48.913 4 August: ISAKMP: (0): sending a packet IPv4 IKE.
* 4 August 09:32:58.913: ISAKMP: (0): transmit phase 1 AG_INIT_EXCH...
* 09:32:58.913 4 August: ISAKMP (0): increment the count of errors on his, try 1 5: retransmit the phase 1
* 4 August 09:32:58.913: ISAKMP: (0): transmit phase 1 AG_INIT_EXCH
* 4 August 09:32:58.913: ISAKMP: (0): 1.1.1.1 package sending 500 peer_port 500 (I) my_port AG_INIT_EXCH
* 09:32:58.913 4 August: ISAKMP: (0): sending a packet IPv4 IKE.
* 4 August 09:33:08.913: ISAKMP: (0): transmit phase 1 AG_INIT_EXCH...
* 09:33:08.913 4 August: ISAKMP (0): increment the count of errors on his, try 2 of 5: retransmit the phase 1
* 4 August 09:33:08.913: ISAKMP: (0): transmit phase 1 AG_INIT_EXCH
* 4 August 09:33:08.913: ISAKMP: (0): 1.1.1.1 package sending 500 peer_port 500 (I) my_port AG_INIT_EXCH
* 09:33:08.913 4 August: ISAKMP: (0): sending a packet IPv4 IKE.
* 4 August 09:33:18.913: ISAKMP: (0): transmit phase 1 AG_INIT_EXCH...
* 09:33:18.913 4 August: ISAKMP (0): increment the count of errors on his, try 3 of 5: retransmit the phase 1
* 4 August 09:33:18.913: ISAKMP: (0): transmit phase 1 AG_INIT_EXCH
* 4 August 09:33:18.913: ISAKMP: (0): 1.1.1.1 package sending 500 peer_port 500 (I) my_port AG_INIT_EXCH
* 09:33:18.913 4 August: ISAKMP: (0): sending a packet IPv4 IKE.
* 4 August 09:33:28.913: ISAKMP: (0): transmit phase 1 AG_INIT_EXCH...
* 09:33:28.913 4 August: ISAKMP (0): increment the count of errors on his, try 4 out 5: retransmit the phase 1
* 4 August 09:33:28.913: ISAKMP: (0): transmit phase 1 AG_INIT_EXCH
* 4 August 09:33:28.913: ISAKMP: (0): 1.1.1.1 package sending 500 peer_port 500 (I) my_port AG_INIT_EXCH
* 09:33:28.913 4 August: ISAKMP: (0): sending a packet IPv4 IKE.Maybe you are looking for