DMVPN + isakmp profile + CA
I'm trying to use a "isakmp profile" with a DMVPN configuration so that we can have accounting RADIUS (which I think should be done with an isakmp profile). I can operate using pre-shared keys, but I can't make it work using certificates that I need.
Spoke it seems to be fine (it goes to IKE_P1_COMPLETE and I see no problem in debugging). It is only at the hub where the isakmp profile is set up where we have "% CRYPTO-6-IKMP_MODE_FAILURE: fast mode processing failed with the peer to 5.0.0.20.
Both devices are definitively authenticated and registered with the certification authority.
I have attached what, in my view, are the relevant config of the hub and speaks and debugging of the hub (edited to remove identifying information).
Any help appreciated,
Ray
Looks like your routers are unable to find a profile matching not ISAKMP to match peer. You could try to create a certificate mapping which refers to the OU of the cert to indicate to what IKE profile to use the router. You can do this by using one of the following ways:
1. create a certificate mapping by using the command "map of crypto pki certificate. In this command, specify a corresponding setting on (such as "name of the object OU = mgmt co"). Then, according to your profile of IKE, 'match certificate.'
2. According to your profile of IKE, simply change the command "match identity address 0.0.0.0" for "corresponds to the identity Mgmt Group."
Either way, I think that will solve your problem. In addition, it is not in your config file, but you can also change your 'ca trustpoint' config to specify that the keys are for the use of IKE only ("use ike") and which touches the pair to use ("rsakeypair").
HTH,
Aaron
Tags: Cisco Security
Similar Questions
-
DMVPN ISAKMP running in manual mode
Our main goal is to improve safety on our WAN DMVPN using current equipment of Cisco.
We use currently pré-partagées on our DMVPN IPsec keys are configured.
We would like to switch to locally generated RAS keys, but our (spokes) Cisco routers have maps of crypto accelerator that prevents the use of RSA keys. We cannot move to Certs at this stage.
We then tried to upgrade to IKEv2 IKEv1, but routers hub with the latest Cisco IOS code, do not support IKEv2.
We thought we could use ISAKMP manual but need cryptographic cards.
I can't locate any documentation that relates to manual DMVPN and IKSAMP.
Someone at - it a URL or a configuration that supports manual DMVPN and ISAKMP in a Cisco environment?
TKS
Frank
Frank,
What exactly do you mean by "manaul" isakmp? ISAKMP is key management protocol - IE dynamic.
If you mean the manual keys for IPsec as described here:
http://www.Cisco.com/en/us/Tech/tk583/TK372/technologies_configuration_example09186a0080093c26.shtml
They don't provide any security additional tho.
IKE v2 has been intriduced in 15.0 I believe, I did not (yet) a deployment with DMVPN and IKEv2 (don't know if that is even supported at the moment).
Please note that any router IOS can be a certification authority at the same time as a DMVPN hub or talk. If you want to deploy certificates.
If it is added security you're looking for, a quick way, you can add for example add proxy authentication to access resources via the tunnel.
Marcin
-
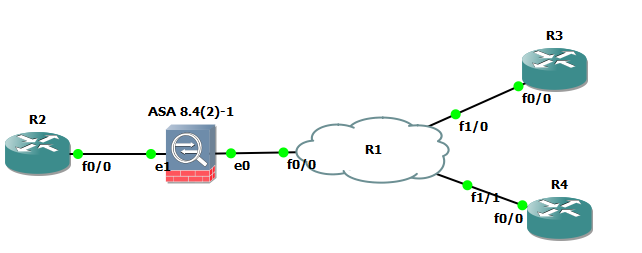
DMVPN router behind ASA - need help please.
Hello
After reading many other discussions on this topic, it appears with the correct IOS and NAT - T active router, you bring up DMVPN behind a NAT device.
I tried to perform this task, but I can not even phase 1 going to the DMVPN. The routing was checked and I can ping the routers DMVPN public IP. I'm sure that the configurations for routers are good, but asked if any additional NAT is required on the ASA.
Here is the topology:
Plate rotating DMVPN > ASA > Internet > ASA > DMVPN Branch
The SAA on the side of the hub is in our data center and in production with several site-to-site and traffic to DMZ. Devices DMVPN is a Cisco 2921 and 1921. When I run a "debug crypto isakmp" on both routers, I see ISAKMP messages are sent on the branch DMVPN router. Nothing in the hub and no hits on the ASA ACL. I tried both the public IP address and the private IP address of the ACL on the ASA.
I have attached the relevant training and can post more if necessary.
Thank you
Brandon
Hello
I finally had time to laboratory it.
I used this topology:
I have
ASA (config) # sh run nat
NAT (INSIDE, OUTSIDE) static source HUB-ROUTER-REAL-IP interface service udp-eq-4500 udp-eq-4500
NAT (INSIDE, OUTSIDE) static source HUB-ROUTER-REAL-IP interface service udp-eq-500 udp-eq-500
!
object network HUB
dynamic NAT interface (INSIDE, OUTSIDE)ASA (config) # sh run access-list
extended OUTSIDE permitted udp access list any HUB-ROUTER-REAL-IP eq isakmp object
list access extended OUTSIDE permitted udp any eq HUB-ROUTER-REAL-IP 4500R2 #sh run inter t0
interface Tunnel0
172.16.0.1 IP address 255.255.255.0
no ip redirection
no ip next-hop-self eigrp 1
no ip split horizon eigrp 1
dynamic multicast of IP PNDH map
PNDH id network IP-99
source of tunnel FastEthernet0/0
multipoint gre tunnel mode
tunnel key 100000
Tunnel ipsec DMVPN-IPSEC-PROFILE protection profileSo it should be the same configuration that you use.
The only thing is that I had to ' stop/no shut' tunnel interface and removing some config that I also need to clear the connection on the ASA using "clear conn."
R2 #sh dmvpn
Legend: Attrb--> S - static, D - dynamic, I - incomplete
Local N - using a NAT, L-, X - no Socket
# Ent--> entries number of the PNDH with same counterpart NBMA
State of the NHS: E--> RSVPs, R--> answer, W--> waiting
UpDn time--> upward or down time for a Tunnel
==========================================================================Interface: Tunnel0, IPv4 PNDH details
Type: hub, PNDH peers: 2,.# Ent Peer NBMA Peer Tunnel Addr add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
1 200.20.0.10 172.16.0.2 UNTIL 00:11:28
1 200.30.0.10 172.16.0.3 AT 00:11:22R2 #.
-
DMVPN spoke of issues after migration double ISR2 3925 hub to ASR-1001 X
Hello world
After our hub solution migration DMVPN double ISR2 3925 to ASR - 1001 X (running asr1001x - universalk9.03.12.03.S.154 - 2.S3 - std.SPA.bin) we started to have some problems with tunnels rays beat (which goes up and down) and sometimes never came.
Running 'show dmvpn' speak it is stuck in State PNDH to our hub. To solve the problem, we run 'stop' and then 'non-stop' on the tunnel interface to actually speak that DMVPN Monte. Also runs "clear encryption session
" on the shelf often solves the problem. So, it seems that the question has something to do with IPSEC. When the problem occurred, and then debug crypto ipsec, crypto, crypto isakmp and crypto engine socket the following can be seen on the hub:
Jun 25 10:01:41 SUMMERT: ISAKMP:(46580):Sending NOTIFY DPD/R_U_THERE protocol 1 spi 140130067548488, message ID = 629121681 Jun 25 10:01:41 SUMMERT: ISAKMP:(46580): seq. no 0x64B2238C Jun 25 10:01:41 SUMMERT: ISAKMP:(46580): sending packet to
my_port 500 peer_port 500 (I) QM_IDLE Jun 25 10:01:41 SUMMERT: ISAKMP:(46580):Sending an IKE IPv4 Packet. Jun 25 10:01:41 SUMMERT: ISAKMP:(46580):purging node 629121681 Jun 25 10:01:41 SUMMERT: ISAKMP:(46580):Input = IKE_MESG_FROM_TIMER, IKE_TIMER_IM_ALIVE Jun 25 10:01:41 SUMMERT: ISAKMP:(46580):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE Jun 25 10:01:41 SUMMERT: ISAKMP (46580): received packet from dport 500 sport 500 ISP1-DMVPN (I) QM_IDLE Jun 25 10:01:41 SUMMERT: ISAKMP: set new node 3442686097 to QM_IDLE Jun 25 10:01:41 SUMMERT: ISAKMP:(46580): processing HASH payload. message ID = 3442686097 Jun 25 10:01:41 SUMMERT: ISAKMP:(46580): processing NOTIFY DPD/R_U_THERE_ACK protocol 1 spi 0, message ID = 3442686097, sa = 0x7F72986867D0 Jun 25 10:01:41 SUMMERT: ISAKMP:(46580): DPD/R_U_THERE_ACK received from peer , sequence 0x64B2238C Jun 25 10:01:41 SUMMERT: ISAKMP:(46580):deleting node 3442686097 error FALSE reason "Informational (in) state 1" Jun 25 10:01:41 SUMMERT: ISAKMP:(46580):Input = IKE_MESG_FROM_PEER, IKE_INFO_NOTIFY Jun 25 10:01:41 SUMMERT: ISAKMP:(46580):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE Jun 25 10:01:42 SUMMERT: IPSEC: delete incomplete sa: 0x7F729923A438 Jun 25 10:01:42 SUMMERT: IPSEC(send_delete_notify_kmi): not sending KEY_ENGINE_DELETE_SAS Jun 25 10:01:42 SUMMERT: ISAKMP:(46580):purging node 1111296046 Jun 25 10:01:44 SUMMERT: ISAKMP (46580): received packet from dport 500 sport 500 ISP1-DMVPN (I) QM_IDLE Jun 25 10:01:44 SUMMERT: ISAKMP: set new node 928225319 to QM_IDLE Jun 25 10:01:44 SUMMERT: ISAKMP:(46580): processing HASH payload. message ID = 928225319 Jun 25 10:01:44 SUMMERT: ISAKMP:(46580): processing SA payload. message ID = 928225319 Jun 25 10:01:44 SUMMERT: ISAKMP:(46580):Checking IPSec proposal 1 Jun 25 10:01:44 SUMMERT: ISAKMP: transform 1, ESP_AES Jun 25 10:01:44 SUMMERT: ISAKMP: attributes in transform: Jun 25 10:01:44 SUMMERT: ISAKMP: encaps is 2 (Transport) Jun 25 10:01:44 SUMMERT: ISAKMP: SA life type in seconds Jun 25 10:01:44 SUMMERT: ISAKMP: SA life duration (basic) of 3600 Jun 25 10:01:44 SUMMERT: ISAKMP: SA life type in kilobytes Jun 25 10:01:44 SUMMERT: ISAKMP: SA life duration (VPI) of 0x0 0x46 0x50 0x0 Jun 25 10:01:44 SUMMERT: ISAKMP: authenticator is HMAC-SHA Jun 25 10:01:44 SUMMERT: ISAKMP: key length is 256 Jun 25 10:01:44 SUMMERT: ISAKMP:(46580):atts are acceptable. Jun 25 10:01:44 SUMMERT: CRYPTO_SS(TUNNEL SEC): Active open, socket info: local /255.255.255.255/0, remote /255.255.255.255/0, prot 47, ifc Tu3300 Jun 25 10:01:44 SUMMERT: IPSEC(recalculate_mtu): reset sadb_root 7F7292E64990 mtu to 1500 Jun 25 10:01:44 SUMMERT: CRYPTO_SS(TUNNEL SEC): Sending Socket Ready message Jun 25 10:01:44 SUMMERT: ISAKMP:(46580): processing NONCE payload. message ID = 928225319 Jun 25 10:01:44 SUMMERT: ISAKMP:(46580): processing ID payload. message ID = 928225319 Jun 25 10:01:44 SUMMERT: ISAKMP:(46580): processing ID payload. message ID = 928225319 Jun 25 10:01:44 SUMMERT: ISAKMP:(46580):QM Responder gets spi Jun 25 10:01:44 SUMMERT: ISAKMP:(46580):Node 928225319, Input = IKE_MESG_FROM_PEER, IKE_QM_EXCH Jun 25 10:01:44 SUMMERT: ISAKMP:(46580):Old State = IKE_QM_READY New State = IKE_QM_SPI_STARVE Jun 25 10:01:44 SUMMERT: ISAKMP:(46580):Node 928225319, Input = IKE_MESG_INTERNAL, IKE_GOT_SPI Jun 25 10:01:44 SUMMERT: ISAKMP:(46580):Old State = IKE_QM_SPI_STARVE New State = IKE_QM_IPSEC_INSTALL_AWAIT Jun 25 10:01:44 SUMMERT: IPSEC(crypto_ipsec_sa_find_ident_head): reconnecting with the same proxies and peer Jun 25 10:01:44 SUMMERT: IPSEC(crypto_ipsec_update_ident_tunnel_decap_oce): updating profile-shared Tunnel3300 ident 7F7298B2BF80 with lookup_oce 7F7296BF5440 Jun 25 10:01:44 SUMMERT: IPSEC(create_sa): sa created, (sa) sa_dest= , sa_proto= 50, sa_spi= 0x14F40C56(351538262), sa_trans= esp-aes 256 esp-sha-hmac , sa_conn_id= 27873 sa_lifetime(k/sec)= (4608000/3600), (identity) local= :0, remote= :0, local_proxy= /255.255.255.255/47/0, remote_proxy= /255.255.255.255/47/0 Jun 25 10:01:44 SUMMERT: IPSEC(create_sa): sa created, (sa) sa_dest= , sa_proto= 50, sa_spi= 0x3B4731D7(994521559), sa_trans= esp-aes 256 esp-sha-hmac , sa_conn_id= 27874 sa_lifetime(k/sec)= (4608000/3600), (identity) local= :0, remote= :0, local_proxy= /255.255.255.255/47/0, remote_proxy= /255.255.255.255/47/0 Jun 25 10:01:44 SUMMERT: ISAKMP:(46580):Received IPSec Install callback... proceeding with the negotiation Jun 25 10:01:44 SUMMERT: ISAKMP:(46580):Successfully installed IPSEC SA (SPI:0x14F40C56) on Tunnel3300 Jun 25 10:01:44 SUMMERT: ISAKMP:(46580): sending packet to my_port 500 peer_port 500 (I) QM_IDLE Jun 25 10:01:44 SUMMERT: ISAKMP:(46580):Sending an IKE IPv4 Packet. Jun 25 10:01:44 SUMMERT: ISAKMP:(46580):Node 928225319, Input = IKE_MESG_FROM_IPSEC, IPSEC_INSTALL_DONE Jun 25 10:01:44 SUMMERT: ISAKMP:(46580):Old State = IKE_QM_IPSEC_INSTALL_AWAIT New State = IKE_QM_R_QM2 Jun 25 10:01:44 SUMMERT: ISAKMP (46580): received packet from dport 500 sport 500 ISP1-DMVPN (I) QM_IDLE Jun 25 10:01:44 SUMMERT: ISAKMP: set new node 1979798297 to QM_IDLE Jun 25 10:01:44 SUMMERT: ISAKMP:(46580): processing HASH payload. message ID = 1979798297 Jun 25 10:01:44 SUMMERT: ISAKMP:(46580): processing NOTIFY PROPOSAL_NOT_CHOSEN protocol 3 spi 351538262, message ID = 1979798297, sa = 0x7F72986867D0 Jun 25 10:01:44 SUMMERT: ISAKMP:(46580): deleting spi 351538262 message ID = 928225319 Jun 25 10:01:44 SUMMERT: ISAKMP:(46580):deleting node 928225319 error TRUE reason "Delete Larval" Jun 25 10:01:44 SUMMERT: ISAKMP:(46580):peer does not do paranoid keepalives. Jun 25 10:01:44 SUMMERT: ISAKMP:(46580):Enqueued KEY_MGR_DELETE_SAS for IPSEC SA (SPI:0x3B4731D7) Jun 25 10:01:44 SUMMERT: ISAKMP:(46580):deleting node 1979798297 error FALSE reason "Informational (in) state 1" Jun 25 10:01:44 SUMMERT: ISAKMP:(46580):Input = IKE_MESG_FROM_PEER, IKE_INFO_NOTIFY Jun 25 10:01:44 SUMMERT: ISAKMP:(46580):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE Jun 25 10:01:44 SUMMERT: IPSEC: delete incomplete sa: 0x7F729923A340 Jun 25 10:01:44 SUMMERT: IPSEC(key_engine_delete_sas): delete SA with spi 0x3B4731D7 proto 50 for Jun 25 10:01:44 SUMMERT: IPSEC(update_current_outbound_sa): updated peer current outbound sa to SPI 0 Jun 25 10:01:44 SUMMERT: IPSEC(send_delete_notify_kmi): not sending KEY_ENGINE_DELETE_SAS Jun 25 10:01:44 SUMMERT: CRYPTO_SS(TUNNEL SEC): Sending request for CRYPTO SS CLOSE SOCKET #sh pl ha qf ac fe ipsec data drop ------------------------------------------------------------------------ Drop Type Name Packets ------------------------------------------------------------------------ 3 IN_US_V4_PKT_FOUND_IPSEC_NOT_ENABLED 127672 19 IN_OCT_ANTI_REPLAY_FAIL 13346 20 IN_UNEXP_OCT_EXCEPTION 4224 33 OUT_V4_PKT_HIT_IKE_START_SP 1930 62 IN_OCT_MAC_EXCEPTION 9 #sh plat hard qfp act stat drop | e _0_ ------------------------------------------------------------------------- Global Drop Stats Packets Octets ------------------------------------------------------------------------- Disabled 1 82 IpFragErr 170536 246635169 IpTtlExceeded 4072 343853 IpsecIkeIndicate 1930 269694 IpsecInput 145256 30071488 Ipv4Acl 2251965 215240194 Ipv4Martian 6248 692010 Ipv4NoAdj 43188 7627131 Ipv4NoRoute 278 27913 Ipv4Unclassified 6 378 MplsNoRoute 790 69130 MplsUnclassified 1 60 ReassTimeout 63 10156 ServiceWireHdrErr 2684 585112
In addition, after you run "logging dmvpn rate-limit 20' on the hub
%DMVPN-3-DMVPN_NHRP_ERROR: Tunnel292: NHRP Encap Error for Resolution Request , Reason: protocol generic error (7) on (Tunnel:
NBMA: ) On the talks both the following can be seen debugging as well:
*Jun 25 09:17:26.884: ISAKMP:(1032): sitting IDLE. Starting QM immediately (QM_IDLE ) *Jun 25 09:17:26.884: ISAKMP:(1032):beginning Quick Mode exchange, M-ID of 1599359281 *Jun 25 09:17:26.884: ISAKMP:(1032):QM Initiator gets spi *Jun 25 09:17:26.884: ISAKMP:(1032): sending packet to
my_port 500 peer_port 500 (R) QM_IDLE *Jun 25 09:17:26.884: ISAKMP:(1032):Sending an IKE IPv4 Packet. *Jun 25 09:17:26.884: ISAKMP:(1032):Node 1599359281, Input = IKE_MESG_INTERNAL, IKE_INIT_QM *Jun 25 09:17:26.884: ISAKMP:(1032):Old State = IKE_QM_READY New State = IKE_QM_I_QM1 *Jun 25 09:17:26.940: ISAKMP (1032): received packet from dport 500 sport 500 Global (R) QM_IDLE *Jun 25 09:17:26.940: ISAKMP:(1032): processing HASH payload. message ID = 1599359281 *Jun 25 09:17:26.940: ISAKMP:(1032): processing SA payload. message ID = 1599359281 *Jun 25 09:17:26.940: ISAKMP:(1032):Checking IPSec proposal 1 *Jun 25 09:17:26.940: ISAKMP: transform 1, ESP_AES *Jun 25 09:17:26.940: ISAKMP: attributes in transform: *Jun 25 09:17:26.940: ISAKMP: encaps is 2 (Transport) *Jun 25 09:17:26.940: ISAKMP: SA life type in seconds *Jun 25 09:17:26.940: ISAKMP: SA life duration (basic) of 3600 *Jun 25 09:17:26.940: ISAKMP: SA life type in kilobytes *Jun 25 09:17:26.940: ISAKMP: SA life duration (VPI) of 0x0 0x46 0x50 0x0 *Jun 25 09:17:26.940: ISAKMP: authenticator is HMAC-SHA *Jun 25 09:17:26.940: ISAKMP: key length is 256 *Jun 25 09:17:26.940: ISAKMP:(1032):atts are acceptable. *Jun 25 09:17:26.940: IPSEC(ipsec_process_proposal): proxy identities not supported *Jun 25 09:17:26.940: ISAKMP:(1032): IPSec policy invalidated proposal with error 32 *Jun 25 09:17:26.940: ISAKMP:(1032): phase 2 SA policy not acceptable! (local remote ) *Jun 25 09:17:26.940: ISAKMP: set new node -1745931191 to QM_IDLE *Jun 25 09:17:26.940: ISAKMP:(1032):Sending NOTIFY PROPOSAL_NOT_CHOSEN protocol 3 spi 834718720, message ID = 2549036105 *Jun 25 09:17:26.940: ISAKMP:(1032): sending packet to my_port 500 peer_port 500 (R) QM_IDLE *Jun 25 09:17:26.940: ISAKMP:(1032):Sending an IKE IPv4 Packet. *Jun 25 09:17:26.940: ISAKMP:(1032):purging node -1745931191 *Jun 25 09:17:26.940: ISAKMP:(1032):deleting node 1599359281 error TRUE reason "QM rejected" *Jun 25 09:17:26.940: ISAKMP:(1032):Node 1599359281, Input = IKE_MESG_FROM_PEER, IKE_QM_EXCH *Jun 25 09:17:26.940: ISAKMP:(1032):Old State = IKE_QM_I_QM1 New State = IKE_QM_I_QM1 *Jun 25 09:17:34.068: ISAKMP (1032): received packet from dport 500 sport 500 Global (R) QM_IDLE *Jun 25 09:17:34.068: ISAKMP: set new node 1021264821 to QM_IDLE *Jun 25 09:17:34.072: ISAKMP:(1032): processing HASH payload. message ID = 1021264821 *Jun 25 09:17:34.072: ISAKMP:(1032): processing NOTIFY DPD/R_U_THERE protocol 1 spi 0, message ID = 1021264821, sa = 0x32741028 *Jun 25 09:17:34.072: ISAKMP:(1032):deleting node 1021264821 error FALSE reason "Informational (in) state 1" *Jun 25 09:17:34.072: ISAKMP:(1032):Input = IKE_MESG_FROM_PEER, IKE_INFO_NOTIFY *Jun 25 09:17:34.072: ISAKMP:(1032):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE *Jun 25 09:17:34.072: ISAKMP:(1032):DPD/R_U_THERE received from peer , sequence 0x64B2279D *Jun 25 09:17:34.072: ISAKMP: set new node 716440334 to QM_IDLE *Jun 25 09:17:34.072: ISAKMP:(1032):Sending NOTIFY DPD/R_U_THERE_ACK protocol 1 spi 834719464, message ID = 716440334 *Jun 25 09:17:34.072: ISAKMP:(1032): seq. no 0x64B2279D *Jun 25 09:17:34.072: ISAKMP:(1032): sending packet to my_port 500 peer_port 500 (R) QM_IDLE *Jun 25 09:17:34.072: ISAKMP:(1032):Sending an IKE IPv4 Packet. *Jun 25 09:17:34.072: ISAKMP:(1032):purging node 716440334 *Jun 25 09:17:34.072: ISAKMP:(1032):Input = IKE_MESG_FROM_PEER, IKE_MESG_KEEP_ALIVE *Jun 25 09:17:34.072: ISAKMP:(1032):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE *Jun 25 09:17:35.356: ISAKMP:(1032):purging node 206299144 Obviously something seems to be wrong Phase 2 not to come. But why is it going up after having erased the session encryption or close the tunnel interface and activate the interface of tunnel has spoken?
Very weird. Also, in looking at att the hub debugging messages it seems that Cryptography is associated with evil Tu3300 tunnel interface when it is Tu2010. Normal or Bug?
The configuration of the hub looks like this:
crypto keyring ISP1-DMVPN vrf ISP1-DMVPN pre-shared-key address 0.0.0.0 0.0.0.0 key
crypto isakmp policy 10 encr aes authentication pre-share crypto isakmp keepalive 10 3 periodic crypto isakmp nat keepalive 10 crypto isakmp profile ISP1-DMVPN keyring ISP1-DMVPN match identity address 0.0.0.0 ISP1-DMVPN keepalive 10 retry 3 crypto ipsec transform-set AES256-MD5 esp-aes 256 esp-md5-hmac mode tunnel crypto ipsec transform-set AES256-SHA-TRANSPORT esp-aes 256 esp-sha-hmac mode transport crypto ipsec profile ISP1-DMVPN set transform-set AES256-SHA AES256-SHA-TRANSPORT set isakmp-profile ISP1-DMVPN vrf definition ISP1-DMVPN description DMVPN-Outside-ISP1 rd 65527:10 ! address-family ipv4 exit-address-family ! ! interface TenGigabitEthernet0/0/0 no ip address ! interface TenGigabitEthernet0/0/0.71 description VPN;ISP1-DMVPN;Outside;VLAN71 encapsulation dot1Q 71 vrf forwarding ISP1-DMVPN ip address 255.255.255.128 no ip proxy-arp ip access-group acl_ISP1-DMVPN_IN in ! ip route vrf ISP1-DMVPN 0.0.0.0 0.0.0.0 name ISP1;Default ip access-list extended acl_ISP1-DMVPN_IN permit icmp any any permit esp any host permit gre any host permit udp any host eq isakmp permit udp any host eq non500-isakmp deny ip any any vrf definition 2010 description CUSTA - Customer A rd 65527:2010 route-target export 65527:2010 route-target import 65527:2010 ! address-family ipv4 exit-address-family ! ! interface Tunnel2010 description CUSTA;DMVPN;Failover-secondary vrf forwarding 2010 ip address 10.97.0.34 255.255.255.240 no ip redirects ip mtu 1380 ip nhrp map multicast dynamic ip nhrp network-id 2010 ip nhrp holdtime 120 ip nhrp server-only ip nhrp max-send 1000 every 10 ip tcp adjust-mss 1340 tunnel source TenGigabitEthernet0/0/0.71 tunnel mode gre multipoint tunnel key 2010 tunnel vrf ISP1-DMVPN tunnel protection ipsec profile ISP1-DMVPN shared router bgp 65527 ! address-family ipv4 vrf 2010 redistribute connected metric 10 redistribute static metric 15 neighbor 10.97.0.39 remote-as 65028 neighbor 10.97.0.39 description spokerouter;Tunnel1 neighbor 10.97.0.39 update-source Tunnel2010 neighbor 10.97.0.39 activate neighbor 10.97.0.39 soft-reconfiguration inbound neighbor 10.97.0.39 prefix-list EXPORT-IVPN-VRF2010 out neighbor 10.97.0.39 route-map AllVRF-LocalPref-80 in neighbor 10.97.0.39 maximum-prefix 5000 80 default-information originate exit-address-family Configuring spoke:
crypto keyring DMVPN01 pre-shared-key address 0.0.0.0 0.0.0.0 key
crypto isakmp policy 10 encr aes authentication pre-share crypto isakmp invalid-spi-recovery crypto isakmp profile DMVPN01 keyring DMVPN01 match identity address 0.0.0.0 keepalive 10 retry 3 crypto ipsec transform-set AES256-SHA esp-aes 256 esp-sha-hmac mode tunnel crypto ipsec transform-set AES256-SHA-TRANSPORT esp-aes 256 esp-sha-hmac mode transport crypto ipsec profile DMVPN01 set transform-set AES256-SHA-TRANSPORT set isakmp-profile DMVPN01 vrf definition inside rd 65028:1 route-target export 65028:1 route-target import 65028:1 ! address-family ipv4 exit-address-family ! interface Tunnel1 description DMVPN to HUB vrf forwarding inside ip address 10.97.0.39 255.255.255.240 no ip redirects ip mtu 1380 ip nhrp map 10.97.0.33 ip nhrp map multicast ip nhrp map 10.97.0.34 ip nhrp map multicast ip nhrp network-id 1 ip nhrp holdtime 120 ip nhrp nhs 10.97.0.33 ip nhrp nhs 10.97.0.34 ip nhrp registration no-unique ip nhrp registration timeout 60 ip tcp adjust-mss 1340 tunnel source GigabitEthernet0/0 tunnel mode gre multipoint tunnel key 2010 tunnel protection ipsec profile DMVPN01 shared router bgp 65028 ! address-family ipv4 vrf inside bgp router-id 172.28.5.137 network 10.97.20.128 mask 255.255.255.128 network 10.97.21.0 mask 255.255.255.0 network 10.97.22.0 mask 255.255.255.0 network 10.97.23.0 mask 255.255.255.0 network 172.28.5.137 mask 255.255.255.255 neighbor 10.97.0.33 remote-as 65527 neighbor 10.97.0.33 description HUB1;Tunnel2010 neighbor 10.97.0.33 update-source Tunnel1 neighbor 10.97.0.33 timers 10 30 neighbor 10.97.0.33 activate neighbor 10.97.0.33 send-community both neighbor 10.97.0.33 soft-reconfiguration inbound neighbor 10.97.0.33 prefix-list IROUTE-EXPORT out neighbor 10.97.0.33 maximum-prefix 5000 80 neighbor 10.97.0.34 remote-as 65527 neighbor 10.97.0.34 description HUB2;tunnel2010 neighbor 10.97.0.34 update-source Tunnel1 neighbor 10.97.0.34 timers 10 30 neighbor 10.97.0.34 activate neighbor 10.97.0.34 send-community both neighbor 10.97.0.34 soft-reconfiguration inbound neighbor 10.97.0.34 prefix-list IROUTE-EXPORT out neighbor 10.97.0.34 route-map AllVRF-LocalPref-80 in neighbor 10.97.0.34 maximum-prefix 5000 80 exit-address-family If more information is needed, please say so.
Any help or advice would be greatly appreciated!
Thank you!
It is possible that you touch it--the failure of negotiations of phase 2:
https://Tools.Cisco.com/bugsearch/bug/CSCup72039/?reffering_site=dumpcr
[Too little detail to say with certainty:]
M.
-
DMVPN question "" change btwn CONF_XAUTH & MM_NO_STATE ".
Hi all
can you please help on below: thanks in advance.
HQ which is configured to accept remote vpn client using crypto map and also it is configured for dynamic vpn with branch.
Static public IP HQ is 82.114.179.120, tunnel 10 172.16.10.1 and local lan ip is 192.168.1.0
Branch has dynamic public ip, 10 ip 172.16.10.32 tunnel local lan is 192.168.32.0 It is also configured by using tunnel 0 with an another CA that works very well.
Directorate-General for the Lan (192.168.32.0) is required to access lan (192.168.1.0) HQ...
Debug files attached
HQ:
AAA authentication login local acs
AAA authorization network local acs
!
AAA - the id of the joint session
!
IP cef
!8.8.8.8 IP name-server
No ipv6 cef
!
Authenticated MultiLink bundle-name Panel
!redundancy
!VDSL 0/1/0 controller
!cryptographic keys ccp-dmvpn-keyring keychain
pre-shared key address 0.0.0.0 0.0.0.0 key [email protected] / * /
!
crypto ISAKMP policy 10
BA 3des
md5 hash
preshared authentication
Group 2
ISAKMP crypto 5 3600 keepalive
ISAKMP crypto nat keepalive 3600
ISAKMP xauth timeout 60 crypto!
ISAKMP crypto client configuration group NAMA
namanama key
pool mypool
ACL 101
Save-password
Profile of crypto isakmp dmvpn-ccp-isakmprofile
CCP-dmvpn-keyring keychain
function identity address 0.0.0.0
!
Crypto ipsec transform-set esp-3des esp-md5-hmac test
tunnel mode
Crypto ipsec transform-set ESP-AES-MD5-esp - aes esp-md5-hmac comp-lzs
transport mode
!
Profile of crypto ipsec CiscoCP_Profile1
game of transformation-ESP-AES-MD5
define the profile of isakmp dmvpn-ccp-isakmprofile
!card dynamic crypto map 10
Set transform-set test
market arriere-route
!
the i-card card crypto client authentication list acs
card crypto i-card isakmp authorization list acs
card crypto i-map client configuration address respond
card crypto i-card 10 isakmp ipsec dynamic map!
interface Tunnel10
bandwidth 1000
address 172.16.10.1 IP 255.255.255.0
no ip redirection
IP 1400 MTU
authentication of the PNDH IP DMVPN_NW
dynamic multicast of IP PNDH map
PNDH id network IP-100000
property intellectual PNDH holdtime 360
IP tcp adjust-mss 1360
delay of 1000
Shutdown
source of Dialer1 tunnel
multipoint gre tunnel mode
tunnel key 100000
Tunnel CiscoCP_Profile1 ipsec protection profile
!
the Embedded-Service-Engine0/0 interface
no ip address
Shutdown
!
interface GigabitEthernet0/0
IP 192.168.0.254 255.255.255.0
IP nat inside
IP virtual-reassembly in
automatic duplex
automatic speed
!
interface GigabitEthernet0/1
IP 192.168.1.1 255.255.255.0
IP nat inside
IP virtual-reassembly in
automatic duplex
automatic speed
!
ATM0/1/0 interface
DSL Interface Description
no ip address
No atm ilmi-keepalive
PVC 8/35
aal5snap encapsulation
PPPoE-client dial-pool-number 1!
interface Dialer0
no ip address
!
interface Dialer1
the negotiated IP address
IP mtu 1492
NAT outside IP
IP virtual-reassembly in
encapsulation ppp
Dialer pool 1
PPP authentication chap callin pap
PPP chap hostname nama20004
password PPP chap 0 220004
PPP pap sent-username nama20004 password 0 220004
i-crypto map
!
IP local pool mypool 192.168.30.1 192.168.30.100
IP forward-Protocol ND
!
IP http server
IP http secure server
!
overload of IP nat inside source list 171 interface Dialer1
IP route 0.0.0.0 0.0.0.0 Dialer1
IP route 192.168.32.0 255.255.255.0 172.16.10.32
!
access-list 101 permit ip 192.168.0.0 0.0.0.255 192.168.30.0 0.0.0.2
access-list 101 permit ip 192.168.1.0 0.0.0.255 192.168.30.0 0.0.0.2
access-list 101 permit ip 192.168.1.0 0.0.0.255 192.168.32.0 0.0.0.2
access-list 101 permit ip 192.168.1.0 0.0.0.255 192.168.35.0 0.0.0.2
access-list 171 deny ip 192.168.0.0 0.0.0.255 192.168.30.0 0.0.0.2
access-list 171 refuse ip 192.168.1.0 0.0.0.255 192.168.30.0 0.0.0.2
access-list 171 refuse ip 192.168.1.0 0.0.0.255 192.168.35.0 0.0.0.2
access-list 171 refuse ip 192.168.1.0 0.0.0.255 192.168.32.0 0.0.0.2
access ip-list 171 allow a whole
Dialer-list 2 ip protocol allow
!HQ #sh cry isa his
IPv4 Crypto ISAKMP Security Association
DST CBC conn-State id
82.114.179.120 78.137.84.92 CONF_XAUTH 1486 ACTIVE
82.114.179.120 78.137.84.92 MM_NO_STATE 1483 ACTIVE (deleted)
82.114.179.120 78.137.84.92 MM_NO_STATE 1482 ACTIVE (deleted)See the branch to execute:
!
!
crypto ISAKMP policy 1
BA 3des
preshared authentication
Group 2
!
crypto ISAKMP policy 11
BA 3des
md5 hash
preshared authentication
Group 2
ISAKMP crypto key [email protected] / * / address 82.114.179.105
ISAKMP crypto key [email protected] / * / address 82.114.179.120
ISAKMP crypto keepalive 10 periodicals
!
!
Crypto ipsec transform-set ESP-AES-MD5-esp - aes esp-md5-hmac comp-lzs
transport mode
Crypto ipsec transform-set esp - aes Taiz esp-md5-hmac comp-lzs
transport mode
!
Profile of crypto ipsec CiscoCP_Profile1
game of transformation-ESP-AES-MD5
!
Profile of crypto ipsec to Taiz-profile-
the value of the transform-set in Taiz
!
interface Tunnel0
bandwidth 1000
IP 172.16.0.32 255.255.255.0
IP 1400 MTU
authentication of the PNDH IP DMVPN_NW
map of PNDH 172.16.0.1 IP 82.114.179.105
PNDH id network IP-100000
property intellectual PNDH holdtime 360
property intellectual PNDH nhs 172.16.0.1
IP tcp adjust-mss 1360
delay of 1000
source of Dialer0 tunnel
tunnel destination 82.114.179.105
tunnel key 100000
Tunnel CiscoCP_Profile1 ipsec protection profile
!
interface Tunnel10
bandwidth 1000
IP 172.16.10.32 255.255.255.0
IP 1400 MTU
authentication of the PNDH IP DMVPN_NW
property intellectual PNDH 172.16.10.1 card 82.114.179.120
PNDH id network IP-100000
property intellectual PNDH holdtime 360
property intellectual PNDH nhs 172.16.10.1
IP tcp adjust-mss 1360
delay of 1000
source of Dialer0 tunnel
tunnel destination 82.114.179.120
key to tunnel 22334455
tunnel of ipsec to Taiz-profile protection
!
interface Ethernet0
no ip address
Shutdown
!
ATM0 interface
no ip address
No atm ilmi-keepalive
!
point-to-point interface ATM0.1
PVC 8/35
PPPoE-client dial-pool-number 1
!
!
interface FastEthernet0
# CONNECT TO LAN description #.
no ip address
!
interface FastEthernet1
# CONNECT TO LAN description #.
no ip address
!
interface FastEthernet2
# CONNECT TO LAN description #.
no ip address
!
interface FastEthernet3
# CONNECT TO LAN description #.
no ip address
!
interface Vlan1
# LAN INTERFACE description #.
customer IP dhcp host name no
IP 192.168.32.254 255.255.255.0
IP nat inside
IP virtual-reassembly in
IP tcp adjust-mss 1412
!
interface Dialer0
the negotiated IP address
IP mtu 1452
NAT outside IP
IP virtual-reassembly in
encapsulation ppp
Dialer pool 1
Dialer-Group 1
PPP authentication chap callin pap
PPP chap hostname mohammadaa
password PPP chap 0-123456
PPP pap sent-name of user mohammadaa password 123456 0
!
IP forward-Protocol ND
IP http server
10 class IP http access
local IP http authentication
no ip http secure server
!
the IP nat inside source 1 interface Dialer0 overload list
IP route 0.0.0.0 0.0.0.0 Dialer0
Route IP 192.168.0.0 255.255.255.0 172.16.0.1
IP route 192.168.1.0 255.255.255.0 172.16.10.1
!
auto discovering IP sla
Dialer-list 1 ip protocol allow
!
access-list 1 permit 192.168.32.0 0.0.0.255
access-list 10 permit 192.168.1.0 0.0.0.255
access-list 10 permit 192.168.0.0 0.0.0.255
!Branch #sh cry isa his
IPv4 Crypto ISAKMP Security Association
DST CBC conn-State id
82.114.179.120 78.137.84.92 MM_NO_STATE ACTIVE 2061 (deleted)
82.114.179.120 78.137.84.92 MM_NO_STATE 2060 ACTIVE (deleted)Mohammed,
No probs, ensure safety.
The config you home has only one profile of IKE again. i.e. your DMVPN and ezvpn fall into the same basket.
What you need is a clean separation.
In the example you have
crypto isakmp profile VPNclient match identity group hw-client-groupname client authentication list userauthen isakmp authorization list hw-client-groupname client configuration address respond
which is then linked to:crypto dynamic-map dynmap 10 set isakmp-profile VPNclient reverse-route set transform-set strong
and separately a Profile of IKE DMVPN:
crypto isakmp profile DMVPN keyring dmvpnspokes match identity address 0.0.0.0
linked to your profile DMVPN IPsec:
crypto ipsec profile cisco set security-association lifetime seconds 120 set transform-set strong set isakmp-profile DMVPN
You apply the same logic here and clean to the top of your current config (i.e. move the features that you have applied to the level of the crypto map to your new profile of IKE).
M.
-
Hello
I have a DMVPN between 1 hub & router 1 Backup Server Setup.
Here is the config of tunnel of Hub:
Tunnel1 interface
IP 10.101.0.1 255.255.255.0
no ip redirection
IP mtu 1416
property intellectual PNDH authentication abcd
dynamic multicast of IP PNDH map
PNDH id network IP-123
No eigrp split horizon ip 100
source of tunnel FastEthernet0/1
multipoint gre tunnel mode
tunnel key 1234567
Protection ipsec DMVPN tunnel profile
!
Router eigrp 100
Network 10.100.0.0 0.0.0.255
network 192.168.9.0
No Auto-resume
!
Spoke about Config:
Tunnel1 interface
IP 10.101.0.250 255.255.255.0
no ip redirection
IP mtu 1416
property intellectual PNDH authentication abcd
property intellectual PNDH card 10.101.0.1 publicIPhere
map of PNDH IP multicast publicIPhere
PNDH id network IP-123
property intellectual PNDH nhs 10.101.0.1
intellectual property PNDH hides not authoritative
source of tunnel FastEthernet0/0
multipoint gre tunnel mode
tunnel key 1234567
Protection ipsec DMVPN tunnel profile
!
Router eigrp 100
Network 10.101.0.0 0.0.0.255
network 192.168.2.0
No Auto-resume
My problem is that I can't get the EIGRP working between the HUB and the SPOKE routers. My isakmp and ipsec work fine. I am able to ping the two GREtunnel IP through the IPSEC tunnel.
If I use static routing communication works very well, is it possible to get the eigrp to travel through the tunnel, so I can avoid static routing?
TIA,
Fred
Hello
the hub has the eigrp wrong config... Here is the correct config-
Router eigrp 100
Network 10.101.0.0 0.0.0.255
network 192.168.9.0
No Auto-resume
you had
Router eigrp 100
Network 10.100.0.0 0.0.0.255
network 192.168.9.0
No Auto-resume
-
Hello.
Could you please tell me, how to create the second IPSec VPN on my router if crypto card is already set to the interface, and there is no other. This interface is also the NHRP\DMVPN interface. Router is a hub.
Hey, Nikolay.
For new dmvpn cloud you don't don't have set up a crmap to the interface. You can create a new tunnel interface and link a different transfer for her.
If you want to add an IPsec-l2l connection or a new EasyVPN you can look at this example:
Crypto ipsec transform-set esp-3des esp-md5-hmac trset1
transport mode
outputCrypto ipsec transform-set trset2 aes - esp esp-sha-hmac
map CRNAME 1 ipsec-isakmp crypto
Description - VPN - 1
defined peer IP_1
Set transform-set trset1
match address ACL_1
outputmap CRNAME 2 ipsec-isakmp crypto
Description - VPN - 2
defined peer IP_1
Set transform-set trset2
match address ACL_2
outputinterface FastEthernet0/0
Description - outdoors-
card crypto CRNAME
outputFor an EasyVPN (or any other dynamic encryption card), you can use this example:
crypto dynamic-map DYNMAP 1
transform-set Set feat
market arriere-route
outputcard crypto crmap 3 - isakmp dynamic ipsec DYNMAP
And example for DmVPN clouds to the 1 Router 2:
Crypto ipsec transform-set esp-3des esp-sha-hmac trset_1
tunnel mode
output
Crypto ipsec transform-set esp-3des esp-md5-hmac trset_2
transport mode
outputCrypto ipsec Dmvpn-Profile1 profile
Set transform-set trset_1
output
Crypto ipsec profile Profil2 dmvpn
Set transform-set trset_2
outputTunnel1 interface
[network] IP address
dynamic multicast of IP PNDH map
PNDH network IP-1 id
source of tunnel FastEthernet0/0
multipoint gre tunnel mode
key 1 tunnel
Tunnel protection ipsec Dmvpn-Profile1 profile
outputinterface tunnels2
[network] IP address
dynamic multicast of IP PNDH map
PNDH network IP-2 id
source of tunnel FastEthernet0/0
multipoint gre tunnel mode
tunnel key 2
Profile of tunnel dmvpn Profil2 ipsec protection
outputBest regards.
-
Double-Cloud DMVPN spoke Router Configuration
I have a decided to adopt an architecture dual-cloud DMVPN (1 head of network in the main office, 1 head of bed instead of DR) with the option later to go to double / hub in each of my network places.
I tried to configure each of the clouds to have its own key.
Cloud Hub 1 1:
ISAKMP crypto key KEY123 address 0.0.0.0 0.0.0.0 no.-xauth
1 2 hub cloud:
ISAKMP crypto key KEY456 address 0.0.0.0 0.0.0.0 no.-xauth
Of course, the rays I want to connect to the two clouds not would allow me to use the same simple crypto isakmp key command twice.
Several of my sites will have 2 internet connections. Given that I source a tunnel each of these Internet connections, I came up with the following solution:
talk 1:
door-key crypto X-RING
address Gig0/1 (internet connection interface 1)
preshared key address 0.0.0.0 0.0.0.0 touches 0 KEY123
door-key crypto Y-RING
address Gig0/2 (internet connection interface 2)
preshared key address 0.0.0.0 0.0.0.0 touch 0 KEY456
Crypto isakmp DMVPN_ISAKMP_X profile
X-RING keychain
function identity address 0.0.0.0
address Gig0/1
Crypto isakmp DMVPN_ISAKMP_Y profile
Y-RING keychain
function identity address 0.0.0.0
address Gig0/2
OK... to the question... the first site I tried to connect the two clouds DMVPN has only 1 internet connection!
Without changing both my DMVPN clouds to the same key (almost all of the examples have this) - how can I make sure that tunnels speaks - has spoken-star work?
Is there anything else I can match? or create on each configs speaks and hub?
I tried:
-
identity group match, but couldn't figure out how to set a group name on each of the rays - or the hub also. Also, no.-xauth wouldn't prevent it being considered? -matching fqdn does not seem to work either.
-vrf is not an option - not applicable
-telesignalisations behind the ip address do not appear to be an option and seems to complicate the issue too.Thank you very much in advance!
There is something special with ICP when seen DMVPN. PKI or preshared keys is just how isakmp authenticates the session, and there is no difference between DMVPN or Site to Site.
Basically, you'd have to do these things:
-create a CA. The basic can be created on some of your routers.
-create the Trustpoint on each DMVPN hub and spokes.
-change the type of authentication in isakmp profile of pre-shared key to rsa - SIG.
You can certainly more trustpoint then one, one for each cloud, but I highly doubt that it is necessary for the public key infrastructure.
Maybe this doc will be of little help, even if it has too much info:
http://www.Cisco.com/en/us/docs/solutions/enterprise/security/DCertPKI.html
If you need, I can bring up some full example site to site with PKI auth.
-
Tunnel DMVPN is establishing is not - a wrong address PNDH
I am trying to establish a DMVPN tunnel a new router that move us in a remote location. We already have a hub and several other remote sites that work properly. I can ping everywhere on another remote site, but I do not see the correct address appears when I do a 'show dmvpn.' Also the SA does not appear when I do a "show isakmp crypto his.".
UARouter #show dmvpn
Legend: Attrb--> S - static, D - dynamic, I - incomplete
Local N - using a NAT, L-, X - no Socket
# Ent--> entries number of the PNDH with same counterpart NBMA
State of the NHS: E--> RSVPs, R--> answer, W--> waiting
UpDn time--> upward or down time for a Tunnel
==========================================================================
Interface: Tunnel0, IPv4 PNDH details
Type: talk, PNDH peers: 1,.
# Ent Peer NBMA Peer Tunnel Addr add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
1 63.162.52.254 172.19.1.1 UP 1d10h S
Then I do a ping on a remote machine.
UARouter #ping 192.168.2.40 loopback source 5
Type to abort escape sequence.
Send 5, echoes ICMP 100 bytes to 192.168.2.40, wait time is 2 seconds:
Packet sent with a source address of 192.168.12.254
!!!!!
Success rate is 100 per cent (5/5), round-trip min/avg/max = 352/353/356 ms
UARouter #show dmvpn
Legend: Attrb--> S - static, D - dynamic, I - incomplete
Local N - using a NAT, L-, X - no Socket
# Ent--> entries number of the PNDH with same counterpart NBMA
State of the NHS: E--> RSVPs, R--> answer, W--> waiting
UpDn time--> upward or down time for a Tunnel
==========================================================================
Interface: Tunnel0, IPv4 PNDH details
Type: talk, PNDH peers: 1,.
# Ent Peer NBMA Peer Tunnel Addr add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
2 63.162.52.254 172.19.1.1 UP 1d10h S
172.19.1.2 UP TO 00:00:32
It does not seem to resolve on the real peer NBMA Address 203.98.212.254, but rather fixed to the hub.
UARouter #show ip nh
UARouter #show ip PNDH bis
Target Via NBMA Mode claimed Intfc
172.19.1.1/32 172.19.1.1 63.162.52.254 Tu0 static< >
172.19.1.2/32 172.19.1.2 63.162.52.254 dynamic Tu0< >
UARouter #show cry isa his
IPv4 Crypto ISAKMP Security Association
DST CBC conn-State id
63.162.52.254 109.237.82.114 QM_IDLE 1003 ACTIVE
Here is the result of a different router that works.
TaiwanRTR #show dmvpn
Legend: Attrb--> S - static, D - dynamic, I - incomplete
Local N - using a NAT, L-, X - no Socket
# Ent--> entries number of the PNDH with same counterpart NBMA
State of the NHS: E--> RSVPs, R--> answer
UpDn time--> upward or down time for a Tunnel
==========================================================================
Interface: Tunnel0, IPv4 PNDH details
Type: talk, PNDH peers: 8.
# Ent Peer NBMA Peer Tunnel Addr add State UpDn Tm Attrb
----- --------------- --------------- ----- -------- -----
1 63.162.52.254 172.19.1.1 UP 1w4d S
1 203.98.212.254 D 1w4d 172.19.1.2
TaiwanRTR #show ip PNDH bis
Target Via NBMA Mode claimed Intfc
172.19.1.1/32 172.19.1.1 63.162.52.254 Tu0 static< >
172.19.1.2/32 172.19.1.2 203.98.212.254 dynamic Tu0< >
Here's the DMVPN configs. They are identical except for the ip address and the fact that I can not use the command no ip mroute-cache because it is not recommended on the new router because we use a newer IOS. I also use the interface directly instead of looping. The closure on the TawainRTR is a public IP address.
Router AU
interface Tunnel0
bandwidth 1000
IP 172.19.1.12 255.255.255.0
no ip redirection
IP 1400 MTU
the PNDH IP authentication
property intellectual PNDH card 172.19.1.1 63.162.52.254
map of PNDH IP multicast 63.162.52.254
PNDH 1000000 IP network ID.
property intellectual PNDH holdtime 600
property intellectual PNDH nhs 172.19.1.1
IP tcp adjust-mss 1360
delay of 1000
QoS before filing
source of tunnel GigabitEthernet0/0
multipoint gre tunnel mode
tunnel key 100000
Shared protection ipsec DMVPN tunnel profile
TaiwanRTR
interface Tunnel0
bandwidth 1000
IP 172.19.1.6 255.255.255.0
no ip redirection
IP 1400 MTU
the PNDH IP authentication
property intellectual PNDH card 172.19.1.1 63.162.52.254
map of PNDH IP multicast 63.162.52.254
PNDH 1000000 IP network ID.
property intellectual PNDH holdtime 600
property intellectual PNDH nhs 172.19.1.1
IP tcp adjust-mss 1360
no ip mroute-cache
delay of 1000
source of Loopback2 tunnel
multipoint gre tunnel mode
tunnel key 100000
Shared protection ipsec DMVPN tunnel profile
end
On both devices, we use the same crypto map parameters. We use certificates instead of pre-shared keys.
crypto ISAKMP policy 1
BA 3des
ISAKMP crypto keepalive 10
!
!
Crypto ipsec transform-set esp-3des esp-sha-hmac RIGHT
transport mode
!
Profile of crypto ipsec DMVPN
Set transform-set RIGHT
Does anyone have ideas, what could happen?
Here is the my DMVPN router ACL...
10 licences of everything esp (22214502 matches)
20 permit udp any any eq isakmp (375 matches)
30 permit udp any any eq non500-isakmp
40 permits all icmp (40005 matches)
Works 100% for me.
I will note, my line 20 has been ' permit udp any isakmp eq all isakmp eq ' but I found when my routers were behind the devices from the source don't would not 500 and things didn't work so I had to open it.
-
problem applying IPSEC to DMVPN
Hi, I have a few problems with DMVPN
I have configured the PNDH between a HUB and aSPOKE:
HUB
tU0 tu1
| |
INTERNET SERVICE PROVIDER
|
tU0, tu1
TALK
the HUB has two physical interfaces and two logical interfaces.
The RADIUS has a physical interface and two logical interfaces.
in PNDH configured correctly, the tunnels are detected in the HUB and the SPOKES.
When I add the IPSEC profile for the controls I lose tunnel1.
SPOKE1 #sh ip PNDH
10.1.1.4/32 via 10.1.1.4, Tunnel0 created 02:22:01, never expire
Type: static, flags: used by authority
The NBMA Address: 190.1.1.1
10.2.2.4/32 via 10.2.2.4 Tunnel1 created 02:18:21, never expire
Type: static, flags: used by authority
The NBMA Address: 190.1.2.1
SPOKE1 #debug ip PNDH
Tunnel0
* 03:50:09.399 Mar 1: PNDH: try to send packages via DEST 10.1.1.4
* 03:50:09.399 Mar 1: PNDH: Encapsulation succeeded. Tunnel IP addr 190.1.1.1
* 03:50:09.399 Mar 1: PNDH: send the registration request via Tunnel0 vrf 0, the packet size: 82
* 03:50:09.403 Mar 1: CBC: 10.1.1.1, dst: 10.1.1.4
* 03:50:09.403 Mar 1: PNDH: 82 bytes in Tunnel0
* 03:50:09.519 Mar 1: PNDH: receive the response for registration via Tunnel0 vrf 0, the packet size: 102
* 03:50:09.519 Mar 1: PNDH: netid_in = 0, to_us = 1
tunnel 1
* 03:50:30.575 Mar 1: PNDH: try to send packages via DEST 10.2.2.4
* 03:50:30.575 Mar 1: PNDH: Encapsulation succeeded. Tunnel IP addr 190.1.2.1
* 03:50:30.575 Mar 1: PNDH: send the registration request via Tunnel1 vrf 0, the packet size: 82
* 03:50:30.579 Mar 1: CBC: 10.2.2.1, dst: 10.2.2.4
* 03:50:30.579 Mar 1: PNDH: 82 bytes to Tunnel1
* 03:50:30.579 Mar 1: PNDH: reset retransmission due to the wait timer for 10.2.2.4
no response from the HUB.
HUB #sh ip PNDH
10.1.1.1/32 through 10.1.1.1, 00:05:05 created Tunnel0, expire 00:08:29
Type: dynamic, flags: single authority registered
The NBMA Address: 191.1.1.11
just tunnel0 is here!
I also have it on the HUB:
* 03:58:54.519 Mar 1: % CRYPTO-6-IKMP_MODE_FAILURE: fast processing mode failed with the peer to 191.1.1.11 (physical address of the SPOKE1)
configs:
HUBS:
!
crypto ISAKMP policy 10
BA aes
md5 hash
preshared authentication
Group 2
techservices key crypto isakmp address 0.0.0.0 0.0.0.0
!
!
Crypto ipsec transform-set AES_MD5 aes - esp esp-md5-hmac
!
Profile of crypto ipsec DMVPN
game of transformation-AES_MD5
!
!
interface Tunnel0
bandwidth 10000
10.1.1.4 IP address 255.255.255.0
no ip redirection
IP 1400 MTU
no ip next-hop-self eigrp 123
property intellectual PNDH authentication dmvpn1
dynamic multicast of IP PNDH map
PNDH id network IP-123
no ip split horizon eigrp 123
source of tunnel FastEthernet0/0
multipoint gre tunnel mode
tunnel key 123
Protection ipsec DMVPN tunnel profile
!
Tunnel1 interface
bandwidth 10000
10.2.2.4 IP address 255.255.255.0
no ip redirection
IP 1400 MTU
no ip next-hop-self eigrp 124
property intellectual PNDH authentication dmvpn2
dynamic multicast of IP PNDH map
PNDH id network IP-124
no ip split horizon eigrp 124
source of tunnel FastEthernet1/0
multipoint gre tunnel mode
tunnel key 124
Protection ipsec DMVPN tunnel profile
!
!
Router eigrp 123
Network 10.1.1.0 0.0.0.255
network 172.16.4.0 0.0.0.255
No Auto-resume
!
Router eigrp 124
Network 10.2.2.0 0.0.0.255
network 172.16.4.0 0.0.0.255
No Auto-resume
!
SPOKE1:
!
crypto ISAKMP policy 10
BA aes
md5 hash
preshared authentication
Group 2
techservices key crypto isakmp address 0.0.0.0 0.0.0.0
!
!
Crypto ipsec transform-set AES_MD5 aes - esp esp-md5-hmac
!
Profile of crypto ipsec DMVPN
game of transformation-AES_MD5
!
!
interface Tunnel0
bandwidth 10000
10.1.1.1 IP address 255.255.255.0
IP 1400 MTU
property intellectual PNDH authentication dmvpn1
map of PNDH IP multicast 190.1.1.1
map of PNDH 10.1.1.4 IP 190.1.1.1
PNDH id network IP-123
property intellectual PNDH holdtime 600
property intellectual PNDH nhs 10.1.1.4
property intellectual PNDH registration timeout 300
source of tunnel FastEthernet0/0
multipoint gre tunnel mode
tunnel key 123
Protection ipsec DMVPN tunnel profile
!
Tunnel1 interface
bandwidth 10000
10.2.2.1 IP address 255.255.255.0
IP 1400 MTU
property intellectual PNDH authentication dmvpn2
map of PNDH IP multicast 190.1.2.1
property intellectual PNDH 10.2.2.4 card 190.1.2.1
PNDH id network IP-124
property intellectual PNDH holdtime 600
property intellectual PNDH nhs 10.2.2.4
property intellectual PNDH registration timeout 300
source of tunnel FastEthernet0/0
multipoint gre tunnel mode
tunnel key 124
Protection ipsec DMVPN tunnel profile
!
!
Router eigrp 123
Network 10.1.1.0 0.0.0.255
network 172.16.1.0 0.0.0.255
No Auto-resume
!
Router eigrp 124
Network 10.2.2.0 0.0.0.255
network 172.16.1.0 0.0.0.255
No Auto-resume
!
concerning
Good to hear. Looks like it could be a timing problem. Recent releases logic for restart the timer recording during certain delays caused by the sequence of configuration has been added. Since you're using an old code that could be the reason why it worked after the reconfiguration of tunnel interface.
F.F. make sure that assign you this thread has responded so he can help others.
-
Changes of State DMVPN intermittent dmvpn
We run a double DMVPN hub and spoke configuration using the router ASR for hubs and 2811 routers for the spoke routers. Have passed us recently 3000 remote sites and discovered a problem in which we struggle with. On some routers spoke (we don't know for sure how much), we see that the show in some cases dmvpn responds with IKE or PNDH with one of the peers hub (see below)
Ro1-13349 #sho dmvpn
Legend: Attrb--> S - static, D - dynamic, I - incomplete
Local N - using a NAT, L-, X - no Socket
# Ent--> entries number of the PNDH with same counterpart NBMA
State of the NHS: E--> RSVPs, R--> answer
UpDn time--> upward or down time for a Tunnel
==========================================================================Interface: Tunnel1, IPv4 PNDH details
IPv4 recording timer: 30 secondsIPv4 NHS: 10.1.0.1 RE
Type: talk, Total NBMA peers (v4/v6): 1# Ent Peer NBMA Peer Tunnel Addr add State UpDn Tm Attrb target network
----- --------------- --------------- ----- -------- ----- -----------------
1 A.B.C.D 10.1.0.1 UP 6d14h S 10.1.0.1/32Interface: Tunnels2, IPv4 PNDH details
IPv4 recording timer: 30 secondsIPv4 NHS: 10.2.0.1 E
Type: talk, Total NBMA peers (v4/v6): 1# Ent Peer NBMA Peer Tunnel Addr add State UpDn Tm Attrb target network
----- --------------- --------------- ----- -------- ----- -----------------
1 A.B.C.D 10.2.0.1 IKE 3w6d S 10.2.0.1/32The State gets between IKE and PNDH and upward. We captured the data from our 3000 connections 3 times + and we saw about 15 to 20 on each capture data with 1 location that was on every list.
Is there an extra logging that can help determine the cause? We have recently added dmvpn logging on 32 branches and the typical message we see is as follows
Apr 4 10:34:29.619 CDT: % DMVPN-5-NHRP_NHS: tunnels2 10.2.0.1 is DOWN
Apr 4 10:35:53.048 CDT: % DMVPN-3-NHRP_ERROR: registration failed for on tunnels2 10.2.0.1In some cases, we get the following
Apr 4 14:28:40.558 CDT: % DMVPN-7-CRYPTO_SS: tunnels2 - A.B.C.D socket is BROKEN
Compensation crypto sessions or a tap continuously on the tunnel has rarely solves the problem. If the problem returns. We use a mixture of pre-shared key and CA cryptographic authentication. We use Version 12.4 (24) T1 as IOS based on other issues.
Please provide any idea that you may have on this type of problem. I'll add more as discover us more information and has no relevant data to add.
ERP,
I'm afraid that my expertiese lies in troubleshooting, rather than surveillance.
SNMP is an option? (I don't think there's much tagetted for DMVPN)
I thought something similar to this:
(although not sure how well ASR suppoorts this)
Regarding conditional debugging and debugging at all.
There is a debugging, you can generally activate "debug crypto isa err" which displays only the parts of the IKE negotiation error without risk.
For conditional debugging. We can narrown down particular peer VRF interfaces or even particular debugging connections - this however would require that we already know if / what specific rays are affected more than others.
PINGER#debug nhrp condition ?
interface based on the interface
peer based on the peer
vrf based on the vrfand
PINGER#debug crypto condi ?
connid IKE/IPsec connection-id filter
fvrf Front-door VRF filter
isakmp Isakmp profile filter
ivrf Inside VRF filter
local IKE local address filter
peer IKE peer filter
reset Delete all debug filters and turn off conditional debug
spi SPI (Security Policy Index) filter
unmatched Output debugs even if no context available
username Xauth or Pki-aaa username filterI trust mainly "debug crypto condition homologous ipv4.
Marcin
-
Someone at - it an example of use of several networks DMVPN and VRF (no MPLS) interfaces
I have a requirment to use a common link to transmit three talking about networks isolated to the Hub as encrypted data. It could be VTI doesn't bother me, but I can't use MPLS.
Thank you
Hello
"back in the day", I made this config:
of http://isamology.blogspot.com/2010/01/IPSec-and-vrfs-so-who-faire-vrf.html
But normally, I guess you've seen this:
http://www.Cisco.com/en/us/prod/collateral/iosswrel/ps6537/ps6586/ps6660/prod_white_paper0900aecd8034be03_ps6658_Products_White_Paper.htmlSame principles apply to the VRF lite little matter DMVPN/VTI/GREoIPsec configuration.
tunnel vrf VRF door =
IP vrf forwarding = inside the VRF
Now, if you add the cheat of Nico (for isakmp profiles) sheet especially if necessary, you should be all set.
https://supportforums.Cisco.com/docs/doc-13524
Marcin
-
DMVPN with VRF (redistribution a road by default via VRF)
Hi all
I was testing a DMVPN configuration so that users with POLES surfing the Internet on the Internet portal of the HUB. The SPOKE1PN is able to ping all internal IP addresses and route determination agrees. When he reached out to the Internet (HUB_INTGW) gateway, pings are okay, but traceroute requests time out. I was wondering if anyone has an idea. Here's my topology.
Basically, if SPOKE1PN pings to the Internet, it goes to SPOKE1, HUB1 via tu0, HUB1_INTGW and it gets overloaded NAT.

QUESTION (OK, TRACEROUTE DROPS AFTER OVERLOADED NAT PINGS)
SPOKE1PN #ping 202.0.0.2 rep 88
Type to abort escape sequence.
88, echoes ICMP 100 bytes to 202.0.0.2 sending, time-out is 2 seconds:
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!
Success rate is 100 per cent (88/88), round-trip min/avg/max = 144/211/328 ms
SPOKE1PN #traceroute 202.0.0.2
Type to abort escape sequence.
The route to 202.0.0.2
1 192.168.1.1 88 MS 64 ms 16 ms
2 172.14.1.1 164 MS 92 MS 128 ms
3 10.1.0.254 152 MS 124 MS ms 116
4 * * *
5 * * *
6 * * *
7 * * *
8 * * *
9 * * *
10 * * *
11 * * *
12 * * *
13 * * *
14 * * *
15 * * *
16 * * *
17 * * *
18 * * *
19 * * *
20 * * *
21 * * *
22 * * *
23 * * *
24 * * *
25 * * *
26 * * *
27 * * *
28 * * *
29 * * *
30 * * *
SPOKE1
version 12.4
horodateurs service debug datetime msec
Log service timestamps datetime msec
no password encryption service
!
hostname SPOKE1
!
boot-start-marker
boot-end-marker
!
!
No aaa new-model
memory iomem size 5
IP cef
!
IP vrf DMVPN
RD 1:1
!
crypto ISAKMP policy 1
BA aes 256
md5 hash
preshared authentication
Group 5
address key crypto isakmp 0.0.0.0 @ngelam1chell3r1c 0.0.0.0
ISAKMP crypto keepalive 60 periodicals
!
Crypto ipsec transform-set SET1 IPSEC ah-md5-hmac esp - aes
!
Profile of crypto ipsec DMVPN
game of transformation-IPSEC-SET1
!
interface Tunnel0
IP vrf forwarding DMVPN
IP 172.14.1.2 255.255.255.0
no ip redirection
IP mtu 1416
property intellectual PNDH authentication cisco123
property intellectual PNDH card 172.14.1.1 200.0.0.2
map of PNDH IP multicast 200.0.0.2
property intellectual PNDH card 172.14.1.254 200.0.1.2
map of PNDH IP multicast 200.0.1.2
PNDH id network IP-99
property intellectual PNDH nhs 172.14.1.1
property intellectual PNDH nhs 172.14.1.254
source of tunnel FastEthernet0/1
multipoint gre tunnel mode
tunnel key 999
Protection ipsec DMVPN tunnel profile
!
interface FastEthernet0/0
IP vrf forwarding DMVPN
IP 192.168.1.1 255.255.255.0
automatic duplex
automatic speed
!
interface FastEthernet0/1
IP 201.0.0.2 255.255.255.240
Speed 100
full-duplex
!
Router eigrp 1
Auto-resume
!
address ipv4 vrf DMVPN family
redistribute connected
network 172.14.1.0 0.0.0.255
network 192.168.1.0
No Auto-resume
autonomous system of-1
output-address-family
!
IP forward-Protocol ND
IP route 0.0.0.0 0.0.0.0 201.0.0.1
!
no ip address of the http server
no ip http secure server
!
control plan
!
Line con 0
line to 0
line vty 0 4
!
end
HUB1
version 12.4
horodateurs service debug datetime msec
Log service timestamps datetime msec
no password encryption service
!
hostname HUB1
!
boot-start-marker
boot-end-marker
!
No aaa new-model
memory iomem size 5
IP cef
!
IP vrf DMVPN
RD 1:1
!
crypto ISAKMP policy 1
BA aes 256
md5 hash
preshared authentication
Group 5
address key crypto isakmp 0.0.0.0 @ngelam1chell3r1c 0.0.0.0
ISAKMP crypto keepalive 60
!
Crypto ipsec transform-set SET1 IPSEC ah-md5-hmac esp - aes
No encryption ipsec nat-transparency udp-program
!
Profile of crypto ipsec DMVPN
game of transformation-IPSEC-SET1
!
interface Tunnel0
IP vrf forwarding DMVPN
IP 172.14.1.1 255.255.255.0
no ip redirection
IP mtu 1416
property intellectual PNDH authentication cisco123
dynamic multicast of IP PNDH map
PNDH id network IP-99
source of tunnel FastEthernet0/1
multipoint gre tunnel mode
tunnel key 999
Protection ipsec DMVPN tunnel profile
!
interface FastEthernet0/0
IP vrf forwarding DMVPN
IP 10.1.0.1 255.255.255.0
automatic duplex
automatic speed
!
interface FastEthernet0/1
IP 200.0.0.2 255.255.255.240
Speed 100
full-duplex
!
Router eigrp 1
Auto-resume
!
address ipv4 vrf DMVPN family
redistribute connected
redistribute static
Network 10.1.0.0 0.0.0.255
network 172.14.1.0 0.0.0.255
No Auto-resume
autonomous system of-1
output-address-family
!
IP forward-Protocol ND
IP route 0.0.0.0 0.0.0.0 200.0.0.1
IP route vrf DMVPN 0.0.0.0 0.0.0.0 10.1.0.254
!
no ip address of the http server
no ip http secure server
!
control plan
!
Line con 0
line to 0
line vty 0 4
!
end
HUB1_INTGW
version 12.4
horodateurs service debug datetime msec
Log service timestamps datetime msec
no password encryption service
!
hostname HUB1_INTGW
!
boot-start-marker
boot-end-marker
!
No aaa new-model
memory iomem size 5
IP cef
!
no ip domain search
!
Authenticated MultiLink bundle-name Panel
!
Archives
The config log
hidekeys
!
interface FastEthernet0/0
IP 10.1.0.254 255.255.255.0
IP nat inside
IP virtual-reassembly
automatic duplex
automatic speed
!
interface FastEthernet0/1
IP 200.0.1.2 255.255.255.240
NAT outside IP
IP virtual-reassembly
Speed 100
full-duplex
!
IP forward-Protocol ND
IP route 0.0.0.0 0.0.0.0 200.0.1.1
IP route 192.168.1.0 255.255.255.0 10.1.0.1
!
no ip address of the http server
no ip http secure server
overload of IP nat inside source list ACL_NATOVERLOAD interface FastEthernet0/1
!
IP access-list standard ACL_NATOVERLOAD
permit 10.1.0.0 0.0.0.255
permit 192.168.1.0 0.0.0.255
permit 172.14.1.0 0.0.0.255
!
control plan
!
Line con 0
exec-timeout 0 0
Synchronous recording
line to 0
line vty 0 4
!
end
Desmon,
If the works of ping I can bet you that it's a problem of how ICMP unreachable it will be via NAT (PAT in fact) in response to UDP with expired TTL.
Can you do a static NAT on HUB1_INTGW to the IP test and you should see a difference... BTW the debug ip packet is your friend, try it :-) on INTGW and INT_RTR
Marcin
-
Is it possible to put behind a NAT DMVPN hub? (Speaks has a public IP address)
I he tried for a few days and couldn't make it work. The schema and configuration is in the attachment.
Crypto isakmp profile: QM slowed down on both sides.
Profile of crypto ipsec: NO ipsec profile established on both sides.
Show ip PNDH (side hub): nothing is saved at all. Empty.
Any ideas?
Thank you!
Difan
As long as the HUB has a static nat translation it should work, try to set your transformation mode of Transport rather than tunnel on two spokes and hub, close your tunnel on the hub and the spokes and then turn it back on, does make a difference?
-
DMVPN spoke with HSRP sells HUB
I have a basic DMVPN with an IPSEC config protect profile.
On the shelves, I use the VIP HSRP for (192.168.1.1) configuration and traffic stops treatment
map of PNDH 10.29.32.1 IP 192.168.1.1
If I use the real IP address of the HUB 192.168.1.2 interface, it works fine.
I changed the mode of multipoint gre tunnel and changed to point to the real or VIP and seems not in line with the VIP HSRP.
Is this a supported configuration, or am I missing something?
The end result is routers DMVPN HUB running HSRP and we talked, pointing to the VIP address.
I feel that, since then, IPSec, the communication breaks when you use the VIP
Thank you
Juan
Spoke about config below
interface Tunnel100
Description
bandwidth 6000
IP 10.29.47.254 255.255.240.0
no ip redirection
IP 1400 MTU
property intellectual PNDH authentication nhrpdomain
map of PNDH IP 192.168.1.2 multicast
map of PNDH 10.29.32.1 IP 192.168.1.2
PNDH id network IP-100
property intellectual PNDH holdtime 360
property intellectual PNDH nhs 10.29.32.1
IP tcp adjust-mss 1360
load-interval 30
QoS before filing
source of tunnel GigabitEthernet0/2
multipoint gre tunnel mode
tunnel key 1000
Protection ipsec DMVPN tunnel profile
end
Hello
The hub does not generate the packages using the VIP.
If the RADIUS is trying to connect to 192.168.1.1 while the hub will respond with 192.168.1.2.
For redundancy, you can create two tunnels on the RADIUS. 1 for every router and use eigrp to decide the best option.
You can still use hsrp to the internal network on the hubs (the network doesn't not facing rays) so the right router will be the gateway for internal routers.
Maybe you are looking for
-
Why the police does not change in itself?
I use a Mac, and continue to change my fonts. Today, they are italicized in the browser and my gmail.
-
Volume seems quiet on P10 - 573
When you use the headset on my P10-573, the volume seems not very strong even when the volume control is set to max. The same thing seems to be the case regardless of the media player I use. Is anyone aware of all hotfixes? Thank you. Dave
-
I moved it down to view more emails and now I can't bring him back. I restarted Mail and also my computer come and go between the classic layout and the other, but no track use. I get the arrow in half, but it does not work. I wonder if this is a bug
-
Photosmart C7280 and Mountain Lion
My printer is connected wireless to iMac running on Mountain Lion. No particular reason, the computer can not find printer. Tried to delete the printer and reconnect with the IP address, but still no joy. All of the suggestions. I tested the printer
-
shut computer down, restarted my time and the date has changed
shut computer down, restarted my time and the date has changed. My date always gose for December 31, 4001. Goin whats?