(How) are queued not reentrant VIs?
I have one COM port used RS485 multidrop to 17 different items, different parts (simultaneous loops) of my LabVIEW program want to talk with the different pieces of the kit attached to the RS485 communications. But given that a physical on the PC port, I used a single VI (duration continuous) to fight against it, any part of my program that wants to use the port makes a request in a queue, then the port service VI transaction RS485 and puts the response in a taxfiler data (request queued had included an 'applicant' ID for the routine of service RS485 knows what notifier wants the answer).
And everything works great, but...
Since then, I started to use functional Global Variables and therefore much better understand the concept of reentrancy (or not). Now, I'm wondering why I've bothered with all the queues and the authors of notifications! If I just let the (called from anywhere and everywhere) VI running RS485 transactions marked as non-reentrant, surely it would have been nice in any case, any part of my program that wants to use the port when it is in use will have to just wait of (almost) the same way.
It occurs to me that perhaps gives my use of queues more greater predictability of the order in which applications are processed, but so far I can't find information on how many non-reentrant calls to a VI are served. that is not reentrant VI works for each 'call' in the same order calls came, or does it have its own idea on priority where two or more additional calls are made while he is busy?
Even this wonderful thread:
http://forums.NI.com/T5/LabVIEW/Community-Nugget-4-08-2007-action-engines/m-p/503801?query.ID=538785...
only show me how the subvi is allocated in the case nearly trivial where two simultaneous processes want to the same not reentrant VI.
LabVIEW uses the services of the OS to do programming.
Because I'm not a developer NOR I have no inside knowledge, so what follows is a display admitted of "hand waving" those who know more should feel free to contradict (go ahead I dare you  ).
).
When EI is already running and another thread want to run this code, a mutex is checked and if busy, the tuft of the code is placed in a State of "resource pending" (at least that's what the used to call before the days of Windows).
Then begins the hand waving extreme...
That the thread is then placed in the queue of resources so when the resource is relased, then next in the queue should lead poped off the power of the given stack the mutex and then placed in the "queue of calculation" and is scheduld as the operating system determines.
There are a lot of non-deterministic questions coming into the game.
If the thread 2 and 3 try to get EI while thred 1 uses it, then it comes down to which of these two asked for the resource first wil determine where they end up in the queue of resources.
Also acfter get the mutex, the Scheduler of the operating system could (or at least it used) son out of order process, if it determines a thread does not receive the attention it deserves.
So if the order of operations is important and you already if she had thought of using queues, then (brace yourself) you can revert to the version of the queue.
Don't know if I want to tell you want but I give it a go.
Ben
Tags: NI Software
Similar Questions
-
There is NO selection update software on my phone! How are Iphone 3 # IOS updated?
It may not be this difficult OR the answer is "It cannot be upgraded" - which is?
The model number you have listed is an iPhone 4, which can be upgraded to iOS 7.1.2. To have the option to update software on the phone, you need at least iOS 5, otherwise you will need to use iTunes on your computer sync to perform the upgrade.
-
How to view all the titles that are currently not in a playlist?
Hello world
my iTunes library has become huge in the past years. I created more than 400 playlists. Now, I'm looking for a way to show (and remove) all securities that are currently not in playlists (because obviously, I don't listen to their).
Someone at - it an idea how to do? I planned to create a smart playlist for that, but I can't think of the right criteria.
Thanks in advance.
Jonathan of Germany
This operation may take several, what I call, "maintenance" smart playlists An option in the smart playlists is "not in the playlist xx". It would be ridiculous to choose for all the playlists of 400. I suggest you make the smart playlists that contain groups of playlists that you created for similar purposes. Finally, you will have a more manageable number of master smart playlists that include all your playlists. Then, create a smart playlist that has songs not in playlist xx and choose all these masters playlists
-
Hi all
I am new to TestStand. Still in the learning process.
What are the parameters? How are Variables differenet? Why we can not use variables to pass data to one sequnece to another? What is the advantage to use parameters instead of Variables?
Thanks in advance,
LaVIEWan
I'm sorry... I discovered that... its not at all possible to pass data to another sequence using variables... it must be through settings... once again I apologize for the display of such a stupid question
-
How to make another firewall that windows firewall my default firewall? I have to start firewall CA every time I connect and the firewall Windows will are also not activated.
Hello
- What version of Windows are you using?
You can check this link:
http://Windows.Microsoft.com/en-us/Windows7/Firewall-frequently-asked-questions
-
How to stop the series 'VISA read' the sends packets instead of bytes available.
Dear Labvillians,
Highlights:
How can I stop series "VISA read" send me packages rather bytes?
Background:
I have a system which publishes series of 14 bytes on a semi-regular interval packets.
At busy times, the producer of these these queues of data packets, effectively producing Super-paquets multiple of 14 times larger than 8 packages (112 bytes) bytes.
My protocol handler is designed to process bytes, packets, or packets Super.
Now, my request has multiple devices and the order of message processing is essential to the proper functioning.
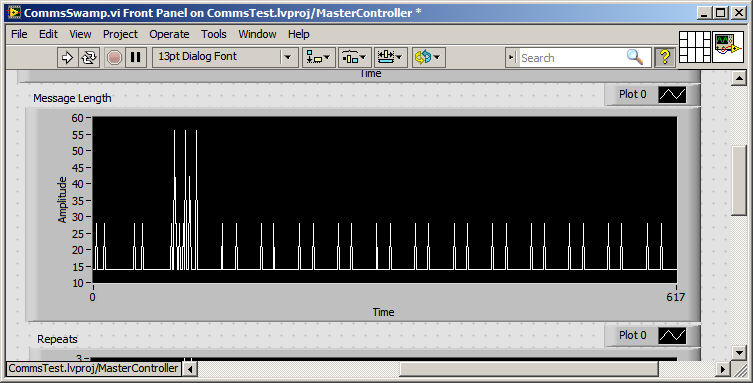
My observation is that read VISA waits until the end of a package / super package before moving the data to the application code. (See chart below)
My expectation is that VISA read should give me bytes available, get too smart for itself and not wait for a package.
.
I noticed this on PXI, PC shipped, PSC and, more recently, cRIO
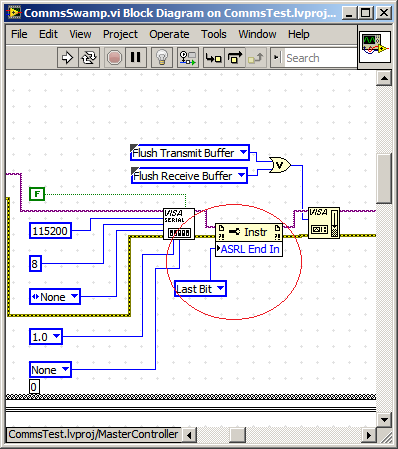
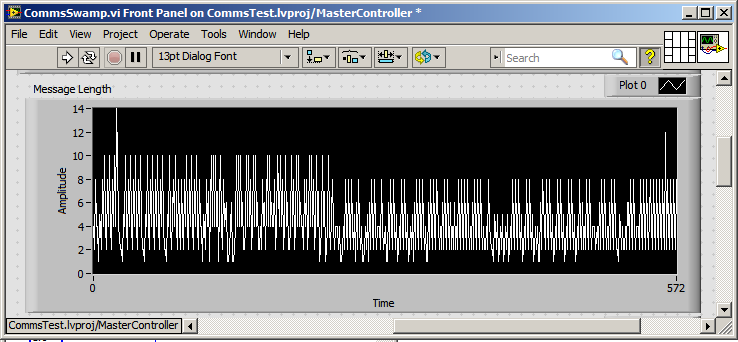
I've experimented with Scan interface the cRIO rate, which helps to reduce the backlog of packages but don't decide to package under read byte.
I understand that a solution is FPGA code write to handle and pass the bytes by R/T-FIFO, and there are some great examples on this site.
Unfortunately, it does not help with FPGA devices not.
I have also dabbled in the event based sequential reads, but he is evil on vxWorks devices.
Any help is appreciated
It is helpful to sometimes talk to yourself.
I hope that is useful for someone sprinkle in the future
-
I'm trying to transfer data between my PXI to my PC via ethernet system. My HDD PXI contains gigbytes of data in multiple files for 9 bus. I open a TCP port for each bus and transfer all the files of this bus through its own TCP port. TCP ports are opened at the beginning of the application and closed at the end of the end of the application. The enclosed screws can be called whenever the application is running.
TgtDownload.vi takes the unique information of each bus and calls simultaneously, in parallel to TgtReadFiles.vi. TgtReadFiles.vi is a reentrant VI. On the side of the host; HostDownload.vi takes the unique information of each bus and initites calls simultaneously, in parallel to HostFileWrite.vi, who is also a reentrant VI. The work of screws with the exception of 5 buses. TgtReadFiles never, ends, however, not HostFileWrite. This only happens for 5 buses. All other buses work perfectly.
The selected TCP port are: 6000, 6100, 6200, 6300, 6400, 6500, 6600, 6700 and 6800. TCP segment size is 38400 bytes. I changed the TCP port for bus 5 from 6500 to 6550, without success. The TCP Read function seems to think that the port is closed (error 66). However, this does not happen until the application is closed.
I read the KB http://zone.ni.com/devzone/cda/pub/p/id/1020. What a better way to create my parallel loops? Is there a better way to transfer in parallel on TCP data? Suggestions on how to debug a reentrant VI.
Are you sure your table of file sizes are correct and correspond to two VI download?
You have a timeout of-1 on TCP/IP functions in the hostwrite and the targetread of VI. If one of these values do not match, then TCP/IP read could wait for always to one byte more is never sent. That would explain why you would only have a problem with a bus and not the others. Incompatibility in sizes between the table host 2D and 2D target table would not be in row 5.
-
How are added to my network WPA2-PSK authentication settings? I need to log on to my place of work.
How are added to my network WPA2-PSK authentication settings? I need to log on to my place of work.
original title: WPA2-PSKtblack1970,
Thank you for visiting the Microsoft Answers community forum.This should be something that your wireless adapter on your computer supports, or does not work. It is not a feature of Vista, but the network hardware. When your wireless adapter on your computer sees the router which has the active Protocol, it must ask the key and once offers you the key, it needs to connect. If you do not see this option for your network card, then you should contact the manufacturer.
http://windowshelp.Microsoft.com/Windows/en-us/help/b385cc8a-AF25-489e-a82e-decf6df26b681033.mspx#ECC
What are the different wireless network security methods?If you plan to have a wireless network, you must configure the only people that can access your choice. Here are a few options for the security of wireless networks.
Wi - Fi Protected Access (WPA)
WPA encrypts information and it checks to make sure that the network security key has not been modified. WPA also authenticates users to ensure that only authorized individuals can access the network.There are two types of WPA authentication: WPA and WPA2. WPA is designed to work with all wireless network cards, but it might not work with the older routers or access points. WPA2 is more secure than WPA, but it will not work with some older network cards. WPA is designed to be used with an authentication server 802.1 X, which distributes different keys to each user. This is referred to as WPA-Enterprise or WPA2-Enterprise. It can also be used in pre-shared key (PSK), where each user has the same passphrase. This is referred to as WPA-Personal or WPA2-Personal.
Wired Equivalent Privacy (WEP)
WEP is an older network security who is still able to support older devices, but it is not recommended. When you enable WEP, you configure a network security key. This key encrypts the information that one computer sends to another computer on your network. However, WEP security is relatively easy to crack.We do not recommend the use of WEP. WPA or WPA2 are more secure. If you try WPA or WPA2 and they do not work, we recommend that you upgrade your network card to those who work with WPA or WPA2.
Authentication of 802. 1 X
802. 1 X authentication can help improve the security of 802.11 wireless networks and wired Ethernet networks. 802. 1 X uses an authentication server to validate users and to provide network access. On wireless 802. 1 X can work with key Wired Equivalent Privacy (WEP) or Wi - Fi Protected Access (WPA). This type of authentication is typically used when connecting to a network of workplaces.
Let us know if you need additional assistance.
Thank youGloria
Microsoft Answers Support Engineer
Visit our Microsoft answers feedback Forum and let us know what you think. -
Why are they not all the photos on my phone on icloud?
Why are they not all the photos on my phone visible on icloud?
You have settings > iCloud > iCloud library turned on in the phone? Since how long you turn on this setting? Have you been connected to wi - fi? How many photos is on iCloud and how much is missing?
-
How to use notes during the writing of my book with pages?
How are used to write a book with pages of notes?
You need the Apple EndNote plug-in for Pages v2.0and the EndNote 7.3.4 application (or later version) installed for compatibility El Capitan. With the plug-in installed and EndNote works, then you start Pages v5.6.1 and the Insert menu: reference EndNote is available for use. Launch Pages v5.6.1 prior to 7.3.4 EndNote and endnote reference entry in the Insert menu is not active.
-
Hello
I want to add on the screen controls to custom FCP generators and effects. How are controls in movement on the screen?
Thank you
Ivan
Basically, you need to use those already provided in motion (unless you can program the FxPlug plugins).
You'll find commands to the screen in several filters. The most common is Poke (in the set of filters of distortion.) However, * any * filter CSOS have to publish in its parameter list can be used and there are several different types. ('Exotic' favourites are blur > blur Gradient, tile > Kaleidotile and aesthetic > extrusion.)
Create a new top-level group - rename CSO (or CSO if you have more than one). In the Group Inspector (you * must *) set a fixed resolution 2D. (Otherwise will be very unexpected effects.)
The group selected, add filters > distortion > Poke.
In the Inspector of Poke, find and check CSOS to publish.
Note: the group still has a length of 0 images. You can in properties > calendar > and set the time to the length of your project (or more) or more simply, just add a shape: rectangle, circle, what is practical and then put it in the wide (or turn off the group so it does not appear). The group will have its length defined for the duration of the project (if your preferences > project > create a new layer at the beginning of the project is on or your playhead is 0.) Onscreen controls appear only in FCPX to the number of frames including the object/group parent in the timeline panel. Simply adding a filter does not add an object and filters have no length if there is nothing to act accordingly.
Add behaviors to link to the X and the parameters Y of your object under control. (You need add separate links to individual settings, because there is a mismatch of types of settings.)
In Wells of the behaviour Source object, add the group to the OSC. For the Source parameter in the compatible settings drop-down list, select Filters.Poke.Center.X and Y respectively. Your object will move to the upper right corner of the canvas. At the bottom of each link behavior Inspector, there is an Offset value. Define each of these to-0.5 (which resets the object in the middle of the canvas.)
Your object will now be controllable in FCPX with the control on the screen.
You know how application relates to several destinations resolution and how it applies to what you were doing just a little.
Motion (very skillfully I must add) treated all resolutions screens as having the coordinates of 0 and 1 (inclusive). No matter what draft resolution you have, SD, HD, 4 K, etc... Controls of the OSC are considered as having the same dimensions. Real pixel values are calculated from the screen resolutions for horizontal and vertical to the destination video (project) dimensions. [Fixed resolution dimensions help you determine the proportions in FCPX, but according to me, are automatically set to adapt to the target FCPX project when it is applied.] Maybe it's not always true, and if you make adjustments, then you essentially override this behavior in your specific model project. See below.]
In the middle of the canvas to an object, as a form, etc., is (0,0), but for a CSO is 0.5, 0.5. When you create a relationship between an object and the parameters on-screen control center, you're "setting" the Center in a different coordinate system. Compensation for these values to the negative terminal of the Center value resets the position to the original 'normal '.
Whatever he says, you can actually fool onscreen controls by setting a custom 'resolution' of the group you places in the dimensions of fixed resolution (say: 300x500pixels). So if you want to create something like a "HUD" to appear in FCPX and have the only control flow within its limits and control another object on the screen, which can be done (using the behaviors of clamp to restrict the Center.X and the Center.Y to between 0 and 1 and the OSC will remain within the limits of the resolution group fixed dimensions you set). If you don't 'get' this still, forget about it then for now, it is not so important and has nothing to do with what you were asking. [In the case of a "HUD" type configuration, you can create another group with other CSO to control the placement of objects on the screen HUD Group, and everything in this group would be sent as CSOS, including the CSOS of the object of HUD designed... get some practice with CSO, then venture into complicated. You are only limited by what you can put together with what you have available in motion if you do not program such things at the level of the application/plugin. [Here is an example of this type of control project - it's very simple and used to define the background color: https://www.youtube.com/watch?v=jpIxuuZuko8 - it has been designed to be taken apart and studied.]
If you build a model with CSO and the OSC does not appear in FCPX: return in movement and check that his group has length (Timing) and make sure that you have checked the box publish CSOS (and that the effect is selected in the Inspector of FCPX - click the title bar of effect).
On the resolution fixed. Motion, by default, the account of dynamic groups - they grow and to shrink to just be the bounding box of all that they contain. By setting the fixed resolution, you force Motion to limit the group size to what you have defined. When control of the center of CSOS goes beyond the limits of a dynamic group, it acts as a multiplier of positional - and your purpose (most of the time immediately) disappears very quickly off the screen. If your initial group of the OSC has no physical object in it, it's dynamic ratings are 0 x 0 and * any * movement of the control on the screen increases by whole numbers for each pixel, it moves. If you move the OSC 1/2 pixel in any direction, the object's Center is already aligned with the edge of the canvas.
If you have any questions, do not hesitate to ask. This topic may be a little hard to grasp until you actually out by yourself and see it in action.
-
How do I not what SATA driver do I need for the Satellite L300 - 03C
How do I not what SATA driver do I need for the Satellite L300 - 03C so I can make nlite
Hello
Your laptop seems to be a Satellite L300 - 03C PSLB8C-03C01X.
As already indicated on your first visit to thread the Toshiba Canada page and choose this model of laptop on the driver page.
http://209.167.114.38/support/download/ln_bymodel.aspThen download the Intel Matrix Storage Manager (SATA) - image of floppy drive. It of for Vista, but the files in this package should work with Win XP too.
Include these files using nLite to create the new disk Win XP that contains SATA drivers.Finally use this disk to start.
-
C# teststep: how to pass the correct Visa instrument reference?
Hello
in c#, I have created a DLL for an instrument with functions as initialize, SetVoltage, close.
In the Initialize function, I create the object of this session with:
RM = new ResourceManager();
Instrument = new FormattedIO488();Now, I put the Initialize function in TestStand as a 2014SP1. NET-Module-NumericLimitTest.
When you open the properties of my new step in the Type Editor there is a button "default Module" where I can choose the function of c#-DLL.
"All parameters are displayed (such as VISA / addresses) and also an additional parameter 'Return value' reference object ' OUT that was added by TestStand.
-> I store this value in a StationGlobal.
The question now is:
If I have more than one device of the same type (means two or more calls Initialize) how can I pass references saved to the next function (SetVoltage) that is performed on the correct instrument?
Thanks for help
Resolved:
Select "Use object existing" UN - Net Invocation and past the reference saved in there.
-
Several incoming clones with the FGV not reentrant timer
Hello
I want to create a launcher of timer. So I created simple timer based on a functional global variable and tried to launch several clones of her home "timer Launcher. The thing is that the timer is not reentrant (each FGV I saw was not reentrant) and I do not know how to create such a pitcher.Attached image illustrates the idea. So I throw clone1 (which is some reentrant VI), in this clone I have not reentrant timer but it is not reentrant in the perspective of clone 1 only. Clone 2, I have an another timer that is not reentrant from the point of view of clone 2 incoming but from the point of view of clone 1 and so on. It is quite complicated to describe, but I hope that the photo show my problem somehow.
Help, please
You can do this if you make your timer pre-allocate clones-reentrant and then call by reference (a reference in every clone of the Launcher timer so that each Launcher uses a clone of separate timer).
-
How are you 933XL cartridges in the HP 6600?
Which came with the printer are 933 3 std color cartridges and a 932XL black.
There are messages on the right and left of the printhead which seem to be not moveable, so I can not understand how to make it larger to fit all 4 cartrdiges as large high capacity XL.
I am breath through STD color cartridges and you want to use the C/M/Y 933XL
Thank you in advance.
While the black 932xl cartridges are physically larger that the 932 standard they replace, the cartrdiges of 933xl of color are the same size as the standard 933 cartrdiges. 933xl cartrdiges have more ink - color xl cartridges are rated up to 825 pages compared to 330 for standard cartridges. They deliver 250% page 142% of the cost.
Maybe you are looking for
-
What version of firefox I have my roboform works correctly
I use Firefox for several websites, but I NEED my roboform. It seems that there is a version of firefox that works well with Roboform and it is the version I need. where can I download it please? 2, roboform is much more important to me than the brow
-
Time capsule and extreme; Cannot create the roaming network
Problem: when you try to create a network roaming with time capsule and extreme, the wifi hangs and the network is up and down. Here are my deets: TC and extreme as well have the latest firmware of the 7.7.7 are the latest generation of products, pur
-
Re: Satellite A200-1AX does not start after the BIOS update
Hi all! I wanted to install XP on a Satellite A200-1AX.So I tried to update the Bios to the version that supports supported XP. When I tried to install it, crashed Vista and now the laptop won't even turn on. When I keep the power button pressed, the
-
The sony handycam dcr-hc30 can endure more than the 512 MB original memory? Thank you.
The sony handycam dcr-hc30 can endure more than the 512 MB original memory? Thank you.
-
Means PtbyPt in a loop with parallelism
Hello Can someone explain to me why this does not work as expected? (values 10.5 and 0.5) I got 5.5 and 5.5. I checked the MeanPtbyPt.vi, everything is cloned, the vi himself is set to pre-allocate clones. I also tried to "Inline", does not help. I t