IPSec in LAN
I have two router 1721 Pentecost VPN Modules into a single network connected 192.168.1.0/255.255.255.0 Pentecost FastEthernet0 everyone. Can I run IPSec 3DES of Pentecost in this LAN. I don't have a WAN port in this Roters.And I want to run routing between two VLAN Pentecost on a fastethernet dot1.q 2 end switch 29erxx na third LAN network 192.168.2.0/255.255.255.0
I don't see why you can't run IPSec on a LAN. I don't remember coming in the limitations of the interface. Apply the crypto map statement to interface ethernet at the two ends and things should work fine.
Tags: Cisco Security
Similar Questions
-
VPN IPsec: several LAN on one side - is it possible?
Hi people!
I have an IPsec Site to Site VPN branch (R2). There was a single LAN (LAN1) at HQ and another (LAN2) on the Executive.
The tunnel end points:
- R1 - Microsoft ISA Server
- R2 - Cisco 2921 SRI
LAN3 was created recently, behind R2 (see image below):

So, I need to access LAN3 of LAN1. How could I solve this problem? I see two options for now.
OPTION 1: Create a separate tunnel between R1 and R2

I see a problem here:
- How to set a key for this tunnel?
If I run something like this:
ISAKMP crypto key LAN1_to_LAN2_key address 1.1.1.1
then LAN1, LAN2 tunnel will be abandoned due to the modified key - Everything else looks good - political maps, road maps, etc.
Traffic stand between them
OPTION 2: Create a summary route in config VPN

Questions:
- R1 does not seem to support this kind of configuration (source, article "political quick mode negotiation fails with an error 'No configured policy'")
How could I solve this problem?
Running-config (security framework) is attached
On the side of Cisco, it's easy to solve. I can't explain how to fix the side R1 Microsoft but suspect that it is not difficult.
You don't want a second tunnel to solve this problem. You want to modify the access list that identifies the traffic is encrypted. If it were me, I would add this line to your existing access list
permit ip 192.168.3.0 0.0.0.255 192.168.101.0 0.0.0.255
or alternatively, you can replace this line
permit ip 192.168.2.0 0.0.0.255 192.168.101.0 0.0.0.255
with this line
permit ip 192.168.2.0 0.0.1.255 192.168.101.0 0.0.0.255
HTH
Rick
-
VPN IPSec in LAN-2LAN tunnel configuration
Hi all!!
I'll put up a tunnel between a cisco 1841 router and a VPN 3000 Concentrator LAN LAN 2 ipsec.
Here is running for the router configuration and basically what I want to know is to ensure that I put everything in place to do this work. So can you please take a look and see if you find something a little odd and if so let me know!
*****************************************
NOTE:
1 internal addressing behind the VPN concentrator: 172.4.4.0/24
2 internal addressing behind the router CISCO 1841 172.16.20.0/24
*****************************************
version 12.4
horodateurs service debug datetime msec
Log service timestamps datetime msec
encryption password service
!
hostname UACA-VPN
!
boot-start-marker
boot-end-marker
!
!
No aaa new-model
!
resources policy
!
no ip source route
IP cef
no ip bootp Server
no ip domain search
!
!
! IKE policies
crypto ISAKMP policy 1
BA 3des
preshared authentication
Group 2
disable ISAKMP aggressive mode crypto
!
!
! IPSec policies
Crypto ipsec transform-set ENLACE UACA BNCR esp-3des esp-sha-hmac
!
ENLACE-UACA-BNCR 10 ipsec-isakmp crypto map
defined by peer 200.91.79.6
defined by peer 200.122.146.38
game of transformation-ENLACE-UACA-BNCR
address of xxxxxxxxxxxx key cryptographic ipsec 200.91.79.6
! Traffic to encrypt according to ACL 101
match address 101
interface FastEthernet0/0
WAN Interface Description VPN tunnel
IP 201.196.33.30 255.255.255.248
NAT outside IP
IP virtual-reassembly
automatic duplex
automatic speed
card crypto ENLACE UACA BNCR
!
interface FastEthernet0/1
LAN Interface Description
IP 172.16.20.22 255.255.255.0
IP nat inside
IP virtual-reassembly
automatic duplex
automatic speed
!
no ip address of the http server
no ip http secure server
! Pool VPN
!
nat pool IP VPN-pool 201.196.33.30 201.196.33.30 netmask 255.255.255.248
IP nat inside source overload map route No. - NAT VPN-pool pool
IP route 0.0.0.0 0.0.0.0 201.196.33.25
! Traffic is encrypted
!
access-list 101 permit ip 172.16.20.0 0.0.0.255 172.4.4.0 0.0.0.255
access-list 101 permit tcp 172.16.20.0 0.0.0.255 172.4.4.0 0.0.0.255 eq 1000
access-list 101 permit udp 172.16.20.0 0.0.0.255 172.4.4.0 0.0.0.255 eq 1000
! Traffic from the NAT process
!
access-list 102 deny ip 172.16.20.0 0.0.0.255 172.4.4.0 0.0.0.255
!
route No. - NAT allowed 10 map
corresponds to the IP 102
!
!
!
!
control plan
!
Line con 0
Synchronous recording
line to 0
line vty 0 4
opening of session
!
Scheduler allocate 20000 1000
****************END**********************
Thank you very much in advance for your help
Glenn
Thanks for the configuration.
So you're natting and then to encrypt traffic natted. Which is totally fine. The reason, your ping does not work after the application of cryptography is due to the ACL entries below:
access-list 101 permit icmp any any echo
access-list 101 permit icmp any any echo response
The acl entries above are part of the traffic interesting Crypto. So once you apply the card encryption the router is supposed to encrypt all ICMP Echo and Echo-Reply, including traffic that is presented with the ip address of your 201.x.x.x. If you remove these two entries of the ACL 101 and apply only the below entries, then the ICMP should work with the applied crypto map.
access-list 101 permit ip 172.4.4.0 0.0.0.255 172.17.0.64 0.0.0.7
access-list 101 permit tcp host 172.4.4.5 host 172.17.0.65 eq 1000
access-list 101 permit udp host 172.4.4.5 host 172.17.0.65 eq 1000
After making the changes, make sure that crypto acl is images mirror on VPN3000 and router, or otherwise you will have problems in the implementation of the tunnel.
I would like to know how the test goes without the ACL 101 ICMP entries.
Kind regards
Arul
-
Hi guys,.
Tried to set up an ipsec VPN LAN - LAN between my WRV200 and WRVS4400N my companion. Filled all the relevant config... simple... but still nothing. They don't seem to connect. We are both on ADSL and using IP address by DNS. Routers are in the log file and try to establish the connection. Tried all the setting, both routers are configured the same. STILL NO JOY! Can anyone help, before having to migrate to a netgear or something nasty!
Sorry forgot to mention, using an AM200 modem in Bridge mode. It my router DHCP address direct WAN instead of NAT. The two systems are fixed the same where routers have outside the WAN address. The modem is transparent. I guess that NAT traversal in not required in that State.
-
LAN to Lan VPN on ASA - than a single public address...
Hello, I need to find a way to work around this problem.
We have an ASA 5510 8.3, we need to use to terminate a VPN IPSEC in LAN to LAN running.
Problem is that we have only a single public address available for having set up the link between the ASA and the Internet router on private addresses.
Is it possible to NAT the public facing the inside or to the outside interface of the ASA and terminate the VPN on this interface?
If this isn't the case, I have other options?
Thanks in advance!
Rob
No, you can't NAT, the IP address of the ASA on the SAA itself, which is not supported.
You can also terminate the VPN tunnel through the interface on the ASA.
How and where you currently do NAT for internet access? You cannot configure NAT on the same device where you are currently configuring your NAT?
-
Recovery site - redundant VPN peers
Hello all, thank you in advance for your expertise.
We put in place a recovery site disaster that will host the redundant copies of our servers and critical data in Kansas City. When disaster strikes, our headquarters site would be totally gone.
We currently have 7 locations that communicate to our HQ via VPN tunnels (whether on a circuit of the Internet or on a circuit of Cox Communications Ethernet WAN). Branch sites each can an ISR of Cisco 2821 router. At Headquarters and on the DR site, we use a Cisco ASA 5510 to terminate VPN tunnels and do everything that our column spinal routing. Routing on the ASA and branch routers is all static, using a routing protocol would be a nice update in the future... any ideas? We use IPSEC VPN lan lan tunnels 2, no GRE/VPN is used because it is not terminated by the ASA.
What is the best way to configure my routers for branch to automatically or manually failover to connect to one ASA different site of DR?
In addition, if my seat is still in place, but either my Internet or Cox headquarters ethernet circuit breaks down. How can I re - route all traffic in a loop to the seat on the right remains a circuit?
Is there a better way to do what I want to accomplish? BGP is not an option at this point due to its complexity.
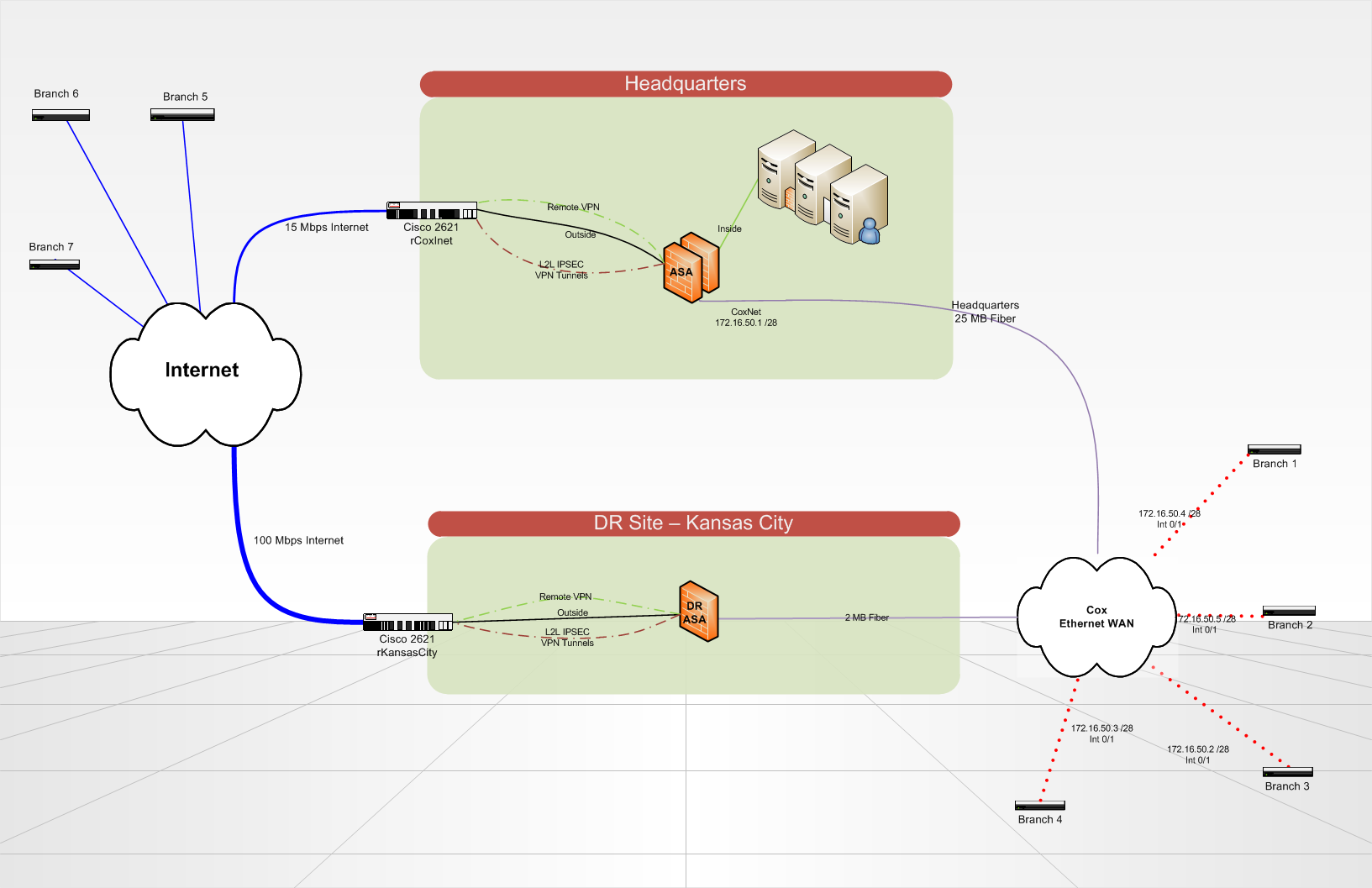
Lucas,
To circumvent the two point separately.
The best way to provide active / standby time of reundancy is preferred peer in cryptographic cards (on the ISR routers).
You can choose to establish VPN to HQ and only if HQ is not aid you to DR, when HQ is you will EVENTUALLY return to it.
The answer to share of your questions may also be the preferred option by peers (and several counterparts in a crypto map entry).
This being said, you can try to send OSPF traffic to IPsec tunnel (and using the neighbor command to avoid the manipulation of mcast in pure IPsec).
Docs:
HTH,
Marcin
P. S.
If you want my personal opion, chaning ASAs in HQ and DR sites and put you in routers could make DMVPN or DVTI-ASIT scenario which gives you a lot more features ;-)
-
Cisco ASA and dynamic VPN L2L Fortigate configuration
I met a problem recently with an ASA 5510 (7.0) and a bunch of Fortigate 50 (3.0 MR7). The ASA is the hub and Fortigates are rays with a dynamic public IP.
I followed this document on the site Web of Cisco (http://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a00805733df.shtml) to set up my ASA and the parameters passed to my counterparts to set up their Fortigates.
However, the ASA journal reveals that attemtps Fortigate connection always tried with DefaultRAGroup before falling back to DefaultL2LGroup and finally died. Experience with putting in place a dynamic VPN between Cisco and Fortigate someone? Which could not fail at each end? Here's a typical piece of error log ASA. The ASA is currently having a static VPN tunnel and a site-2-client VPN in two groups by default.
6. January 10, 2011 20:58:45 | 713905: Group DefaultL2LGroup, IP = 116.230.243.205, P1 = relay msg sent to the WSF MM
5. January 10, 2011 20:58:45 | 713201: Group = DefaultL2LGroup, IP = 116.230.243.205, in double Phase 1 detected package. Retransmit the last packet.
6. January 10, 2011 20:58:45 | 713905: Group DefaultL2LGroup, IP = 116.230.243.205, P1 = relay msg sent to the WSF MM
5. January 10, 2011 20:58:45 | 713201: Group = DefaultL2LGroup, IP = 116.230.243.205, in double Phase 1 detected package. Retransmit the last packet.
6. January 10, 2011 20:58:41 | 713905: Group DefaultL2LGroup, IP = 116.230.243.205, P1 = relay msg sent to the WSF MM
5. January 10, 2011 20:58:41 | 713201: Group = DefaultL2LGroup, IP = 116.230.243.205, in double Phase 1 detected package. Retransmit the last packet.
4. January 10, 2011 20:58:39 | 713903: Group = DefaultL2LGroup, IP = 116.230.243.205, ERROR, had decrypt packets, probably due to problems not match pre-shared key. Abandonment
5. January 10, 2011 20:58:39 | 713904: Group = DefaultL2LGroup, IP = 116.230.243.205, received the package of Mode main Oakley encrypted with invalid payloads, MessID = 0
6. January 10, 2011 20:58:39 | 713905: Group = DefaultRAGroup, IP = 116.230.243.205, WARNING, had decrypt packets, probably due to problems not match pre-shared key. User switching to the tunnel-group: DefaultL2LGroup
5. January 10, 2011 20:58:39 | 713904: Group = DefaultRAGroup, IP = 116.230.243.205, received the package of Mode main Oakley encrypted with invalid payloads, MessID = 0
4. January 10, 2011 20:58:33 | 713903: Group = DefaultRAGroup, IP = 116.230.243.205, error: cannot delete PeerTblEntry
3. January 10, 2011 20:58:33 | 713902: Group = DefaultRAGroup, IP = 116.230.243.205, Removing peer to peer table has no, no match!
6. January 10, 2011 20:58:33 | 713905: Group DefaultRAGroup, IP = 116.230.243.205, P1 = relay msg sent to the WSF MM
5. January 10, 2011 20:58:33 | 713201: Group = DefaultRAGroup, IP = 116.230.243.205, in double Phase 1 detected package. Retransmit the last packet.
6. January 10, 2011 20:58:25 | 713905: Group DefaultRAGroup, IP = 116.230.243.205, P1 = relay msg sent to the WSF MM
5. January 10, 2011 20:58:25 | 713201: Group = DefaultRAGroup, IP = 116.230.243.205, in double Phase 1 detected package. Retransmit the last packet.
6. January 10, 2011 20:58:21 | 713905: Group DefaultRAGroup, IP = 116.230.243.205, P1 = relay msg sent to the WSF MM
5. January 10, 2011 20:58:21 | 713201: Group = DefaultRAGroup, IP = 116.230.243.205, in double Phase 1 detected package. Retransmit the last packet.
5. January 10, 2011 20:58:19 | 713904: IP = 116.230.243.205, encrypted packet received with any HIS correspondent, dropYes, sounds about right. He will try to match with the DefaultRAGroup first, and when you know that it's a dynamic IPSec in LAN-to-LAN, it will be
then back to the DefaultL2LGroup, because he doesn't know if the VPN Client or L2L again when he is contacted fist as they are connecting from dynamic IP peer.
You must ensure that your L2L tunnel-group by default has been configured with the corresponding pre-shared key.
Assuming that you have configured the dynamic map and assign to the card encryption.
Here is an example of configuration where ASA has a static and peripheral ip address pair has dynamic IP:
Hope that helps.
-
Using to relay DHCP on LAN remote IPSec VPN WRVS4400N
Hello
I have a WRVS4400N. I want to know if it is possible to configure the remote relay DHCP WRVS4400N to find a DHCP server on the local network. The local network is 192.168.2.0/24, and the Remote LAN is 192.168.1.0/24. I am entered the field of relay DHCP server 192.168.1.100 but my local PC does not get an IP address. So, I would like to than the local PC to get an IP from DHCP address 192.168.2.x server remote (LAN) through the IPSec VPN tunnel. Is this possible?
The IPSec tunnel works. I ping the 192.168.1.100 remote DHCP server, if the local PC, a static IP address 192.168.2.x I have the configuration of the DHCP server with an IP of 192.168.2.x/24 range.
The remote VPN router is a Netgear FVS114.
Thank you
NIC
The wrvs4400n, you cannot do the dhcp relay in the vpn tunnel. You may need to get a business for which solution or a connection point to point for both networks on the same local network configuration.
-
ASA 5505 IPSec client-to-site any LAN access?
Hello
Like many others, I have problems get ipsec vpn clients can communicate with my LAN.
I have configure ipsec with the wizard, I have also to add an ACL to allow the network to pool for the vpn client to connect to the local network, but with little success.
Many of the responses I've seen includes changes in the NAT table, I tried a lot of them, but without success.
There must be something really simple, that it's so frustrating because I guess it is supposed to be a relatively simple thing to get running.
VPN client (Linux, iptables rules no) get 10.80.80.100 address, but cannot connect to a TCP service on a machine of LAN (no firewall on computer LAN) and can not ping LAN.
The VPN client routing table:
Kernel IP routing table
Destination Gateway Genmask Flags metric Ref use Iface
85.24.249.35 212.112.31.254 UGH 255.255.255.255 0 0 0 eth0
10.80.80.0 0.0.0.0 255.255.255.0 U 0 0 0 tun0
212.112.31.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0
0.0.0.0 0.0.0.0 0.0.0.0 U 0 0 0 tun0: Saved
:
ASA Version 7.2(4)
!
hostname ciscoasa
domain-name default.domain.invalid
enable password xxx encrypted
passwd xxx encrypted
names
!
interface Vlan1
nameif inside
security-level 100
ip address 192.168.0.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
ip address dhcp setroute
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
ftp mode passive
dns server-group DefaultDNS
domain-name default.domain.invalid
same-security-traffic permit inter-interface
access-list tictac_splitTunnelAcl remark allow vpn tunnel users to LAN
access-list tictac_splitTunnelAcl standard permit 192.168.0.0 255.255.255.0
access-list inside_nat0_outbound extended permit ip any 10.80.80.0 255.255.255.0
access-list inside_access_in extended permit ip any any log disable
access-list outside_access_out extended permit ip any any
pager lines 24
logging enable
logging asdm informational
mtu outside 1500
mtu inside 1500
ip local pool vpnpool 10.80.80.100-10.80.80.120 mask 255.255.255.0
icmp unreachable rate-limit 1 burst-size 1
asdm image disk0:/asdm-524.bin
no asdm history enable
arp timeout 14400
global (outside) 1 interface
nat (inside) 0 access-list inside_nat0_outbound
nat (inside) 1 0.0.0.0 0.0.0.0
access-group outside_access_out out interface outside
access-group inside_access_in in interface inside
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
http server enable
http 192.168.0.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto dynamic-map outside_dyn_map 20 set pfs group1
crypto dynamic-map outside_dyn_map 20 set transform-set ESP-3DES-SHA
crypto map outside_map 65535 ipsec-isakmp dynamic outside_dyn_map
crypto map outside_map interface outside
crypto isakmp enable outside
crypto isakmp policy 10
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
telnet 192.168.0.0 255.255.255.0 inside
telnet timeout 5
ssh timeout 5
console timeout 0
dhcpd auto_config outside
!
dhcpd address 192.168.0.2-192.168.0.33 inside
dhcpd dns 8.8.8.8 4.2.2.2 interface inside
dhcpd enable inside
!group-policy tictac internal
group-policy tictac attributes
dns-server value 8.8.8.8 4.2.2.2
vpn-tunnel-protocol IPSec
split-tunnel-policy tunnelspecified
split-tunnel-network-list none
username mattiasb password SVCZv/HMkykG.ikA encrypted privilege 0
username mattiasb attributes
vpn-group-policy tictac
tunnel-group tictac type ipsec-ra
tunnel-group tictac general-attributes
address-pool vpnpool
default-group-policy tictac
tunnel-group tictac ipsec-attributes
pre-shared-key *
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
!
service-policy global_policy global
prompt hostname context
Cryptochecksum:6e456ab21d08182ca41ed0f1be031797
: end
asdm image disk0:/asdm-524.bin
no asdm history enable
The list of split tunnel network was put on 'none' in your configuration:
group-policy tictac attributes
dns-server value 8.8.8.8 4.2.2.2
vpn-tunnel-protocol IPSec
split-tunnel-policy tunnelspecified
split-tunnel-network-list none
Please configure the tunnel list to reference the split tunnel ACL as follows:group-policy tictac attributes
split-tunnel-network-list value tictac_splitTunnelAclHope that helps.
-
IPSec tunnels between duplicate LAN subnets
Hi all
Please help to connect three sites with our Central site has all the resources for users, including internet access.
The three sites will be the ASA 5505 like their WAN device.
We need to know is - it possible, allowing to configure an IPsec Tunnel between the three ASA with duplicate LAN subnets.
Central site two networks 192.168.1.x 24, 192.168.100.x 24
Distance a 24 192.168.1.x subnet
Two remote a subnet 192.168.100.x 24
If it is possible we also do hair distance one ping, above two remote to the Central Site to access internet, what sites need are on the Central Site, including e-mail, network, other resource also records.
We have no other way to make this network, as all security is on our Central Site, website filtering, Application filtering, filtering of network traffic all.
We understand that we can change two remote sites to a different subnet from the Central Site, but we have so many host devices, it will take weeks or months, so to change the MS AD domain for all users, servers too.
We really need your expertise to do this in a laboratory and then in production.
Thank you
Hello Stephen,
You can check the following links for the subnets overlap talk to each other:-
1 LAN-to-LAN IPsec VPN with overlapping networks
http://www.Cisco.com/en/us/products/ps6120/products_configuration_example09186a0080b37d0b.shtml
2 IPsec between two IOS routers with overlapping of private networks
http://www.Cisco.com/en/us/products/ps5855/products_configuration_example09186a0080a0ece4.shtml
Important point is local network must connect to the remote network via the translated addresses.
for example, you won't be ablt to use real IP of the communication.
For haripinning or turning U:
http://www.Cisco.com/en/us/products/ps6120/products_configuration_example09186a00805734ae.shtml
Hope that helps.
Kind regards
Dinesh Moudgil
-
Cisco ipsec Vpn connects but cannot communicate with lan
I have a version of cisco 1921 15.2 (4) M3 I install vpn ipsec and may have customers to connect but cannot ping anything inside. A glimpse of what could be wrong with my config would be greatly appreciated. I posted the configuration as well as running a few outings of ipsec. I also tried with multiple operating systems using cisco vpn client and shrewsoft. I am able to connect to the other VPN ipsec running 1921 both of these computers by using a client.
Thanks for any assistance
SH run
!
AAA new-model
!
!
AAA authentication login radius_auth local radius group
connection of AAA VPN_AUTHEN group local RADIUS authentication
AAA authorization network_vpn_author LAN
!
!
!
!
!
AAA - the id of the joint session
clock timezone PST - 8 0
clock to summer time recurring PST
!
no ip source route
decline of the IP options
IP cef
!
!
!
!
!
!
no ip bootp Server
no ip domain search
domain IP XXX.local
inspect the high IP 3000 max-incomplete
inspect the low IP 2800 max-incomplete
IP inspect a low minute 2800
IP inspect a high minute 3000
inspect the IP icmp SDM_LOW name
inspect the IP name SDM_LOW esmtp
inspect the tcp IP SDM_LOW name
inspect the IP udp SDM_LOW name
IP inspect name SDM_LOW ssh
No ipv6 cef
!
Authenticated MultiLink bundle-name Panel
!
!
Crypto pki trustpoint TP-self-signed-2909270577
enrollment selfsigned
name of the object cn = IOS - Self - signed - certificate - 2909270577
revocation checking no
rsakeypair TP-self-signed-2909270577
!
!
TP-self-signed-2909270577 crypto pki certificate chain
certificate self-signed 01
license udi pid CISCO1921/K9 sn FTX1715818R
!
!
Archives
The config log
Enable logging
size of logging 1000
notify the contenttype in clear syslog
the ADMIN_HOSTS object-group network
71.X.X.X 71.X.X.X range
!
name of user name1 secret privilege 15 4 XXXXXXX!
redundancy
!
!
!
!
!
property intellectual ssh time 60
property intellectual ssh authentication-2 retries
property intellectual ssh event logging
property intellectual ssh version 2
!
!
crypto ISAKMP policy 1
BA 3des
preshared authentication
Group 2
!
ISAKMP crypto client configuration group roaming_vpn
key XXXXX
DNS 192.168.10.10 10.1.1.1
XXX.local field
pool VPN_POOL_1
ACL client_vpn_traffic
netmask 255.255.255.0
!
!
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
tunnel mode
!
!
!
crypto dynamic-map VPN_DYNMAP_1 1
Set the security association idle time 1800
game of transformation-ESP-3DES-SHA
market arriere-route
!
!
list of authentication of card crypto SDM_CMAP_1 client VPN_AUTHEN
map SDM_CMAP_1 isakmp authorization list network_vpn_author crypto
client configuration address map SDM_CMAP_1 crypto answer
map SDM_CMAP_1 65535-isakmp dynamic VPN_DYNMAP_1 ipsec crypto
!
!
!
!
!
the Embedded-Service-Engine0/0 interface
no ip address
Shutdown
!
interface GigabitEthernet0/0
IP 76.W.E.R 255.255.255.248
IP access-group ATT_Outside_In in
no ip redirection
no ip unreachable
no ip proxy-arp
NAT outside IP
inspect the SDM_LOW over IP
IP virtual-reassembly in
load-interval 30
automatic duplex
automatic speed
No cdp enable
No mop enabled
map SDM_CMAP_1 crypto
!
interface GigabitEthernet0/1
no ip address
load-interval 30
automatic duplex
automatic speed
!
interface GigabitEthernet0/1.10
encapsulation dot1Q 1 native
IP 192.168.10.1 255.255.255.0
no ip redirection
no ip unreachable
no ip proxy-arp
property intellectual accounting-access violations
IP nat inside
IP virtual-reassembly in
!
interface GigabitEthernet0/1.100
encapsulation dot1Q 100
10.1.1.254 IP address 255.255.255.0
no ip redirection
no ip unreachable
no ip proxy-arp
IP nat inside
IP virtual-reassembly in
!
interface GigabitEthernet0/1,200
encapsulation dot1Q 200
IP 10.1.2.254 255.255.255.0
no ip redirection
no ip unreachable
no ip proxy-arp
IP nat inside
IP virtual-reassembly in
IP tcp adjust-mss 1452
!
local IP VPN_POOL_1 192.168.168.193 pool 192.168.168.254
IP forward-Protocol ND
!
IP http server
IP http authentication aaa-authentication of connection ADMIN_AUTHEN
IP http secure server
IP http timeout policy slowed down 60 life 86400 request 10000
!
IP nat inside source map route ATT_NAT_LIST interface GigabitEthernet0/0 overload
IP nat inside source static tcp 192.168.10.10 25 expandable 25 76.W.E.R
IP nat inside source static tcp 192.168.10.10 80 76.W.E.R 80 extensible
IP nat inside source static tcp 192.168.10.10 76.W.E.R expandable 443 443
IP nat inside source static tcp 192.168.10.10 76.W.E.R expandable 987 987
IP route 0.0.0.0 0.0.0.0 76.W.E.F
!
ATT_Outside_In extended IP access list
permit tcp object-group ADMIN_HOSTS any eq 22
allow any host 76.W.E.R eq www tcp
allow any host 76.W.E.R eq 443 tcp
allow 987 tcp any host 76.W.E.R eq
allow any host 76.W.E.R eq tcp smtp
permit any any icmp echo response
allow icmp a whole
allow udp any any eq isakmp
allow an esp
allow a whole ahp
permit any any eq non500-isakmp udp
deny ip 10.0.0.0 0.255.255.255 everything
deny ip 172.16.0.0 0.15.255.255 all
deny ip 192.168.0.0 0.0.255.255 everything
deny ip 127.0.0.0 0.255.255.255 everything
refuse the ip 255.255.255.255 host everything
refuse the host ip 0.0.0.0 everything
NAT_LIST extended IP access list
IP 10.1.0.0 allow 0.0.255.255 everything
permit ip 192.168.10.0 0.0.0.255 any
deny ip 192.168.10.0 0.0.0.255 192.168.168.192 0.0.0.63
refuse the 10.1.1.0 ip 0.0.0.255 192.168.168.192 0.0.0.63
deny ip 10.1.2.0 0.0.0.255 192.168.168.192 0.0.0.63
client_vpn_traffic extended IP access list
permit ip 192.168.10.0 0.0.0.255 192.168.168.192 0.0.0.63
ip licensing 10.1.1.0 0.0.0.255 192.168.168.192 0.0.0.63
IP 10.1.2.0 allow 0.0.0.255 10.1.1.0 0.0.0.255
!
radius of the IP source-interface GigabitEthernet0/1.10
Logging trap errors
logging source hostname id
logging source-interface GigabitEthernet0/1.10
!
ATT_NAT_LIST allowed 20 route map
corresponds to the IP NAT_LIST
is the interface GigabitEthernet0/0
!
!
SNMP-server community [email protected] / * /! s RO
Server enable SNMP traps snmp authentication linkdown, linkup warmstart cold start
Server enable SNMP traps vrrp
Server SNMP enable transceiver traps all the
Server enable SNMP traps ds1
Enable SNMP-Server intercepts the message-send-call failed remote server failure
Enable SNMP-Server intercepts ATS
Server enable SNMP traps eigrp
Server enable SNMP traps ospf-change of State
Enable SNMP-Server intercepts ospf errors
SNMP Server enable ospf retransmit traps
Server enable SNMP traps ospf lsa
Server enable SNMP traps ospf nssa-trans-changes state cisco-change specific
SNMP server activate interface specific cisco-ospf traps shamlink state change
SNMP Server enable neighbor traps cisco-specific ospf to the State shamlink change
Enable SNMP-Server intercepts specific to cisco ospf errors
SNMP server activate specific cisco ospf retransmit traps
Server enable SNMP traps ospf cisco specific lsa
SNMP server activate license traps
Server enable SNMP traps envmon
traps to enable SNMP-Server ethernet cfm cc mep-top low-mep Dispatcher loop config
Enable SNMP-Server intercepts ethernet cfm overlap missing mep mep-unknown service-up
Server enable SNMP traps auth framework sec-violation
Server enable SNMP traps c3g
entity-sensor threshold traps SNMP-server enable
Server enable SNMP traps adslline
Server enable SNMP traps vdsl2line
Server enable SNMP traps icsudsu
Server enable SNMP traps ISDN call-information
Server enable SNMP traps ISDN layer2
Server enable SNMP traps ISDN chan-not-available
Server enable SNMP traps ISDN ietf
Server enable SNMP traps ds0-busyout
Server enable SNMP traps ds1-loopback
SNMP-Server enable traps energywise
Server enable SNMP traps vstack
SNMP traps enable mac-notification server
Server enable SNMP traps bgp cbgp2
Enable SNMP-Server intercepts isis
Server enable SNMP traps ospfv3-change of State
Enable SNMP-Server intercepts ospfv3 errors
Server enable SNMP traps aaa_server
Server enable SNMP traps atm subif
Server enable SNMP traps cef resources-failure-change of State peer peer-fib-state-change inconsistency
Server enable SNMP traps memory bufferpeak
Server enable SNMP traps cnpd
Server enable SNMP traps config-copy
config SNMP-server enable traps
Server enable SNMP traps config-ctid
entity of traps activate SNMP Server
Server enable SNMP traps fru-ctrl
SNMP traps-policy resources enable server
Server SNMP enable traps-Manager of event
Server enable SNMP traps frames multi-links bundle-incompatibility
SNMP traps-frame relay enable server
Server enable SNMP traps subif frame relay
Server enable SNMP traps hsrp
Server enable SNMP traps ipmulticast
Server enable SNMP traps msdp
Server enable SNMP traps mvpn
Server enable SNMP traps PNDH nhs
Server enable SNMP traps PNDH nhc
Server enable SNMP traps PNDH PSN
Server enable SNMP traps PNDH exceeded quota
Server enable SNMP traps pim neighbor-rp-mapping-change invalid-pim-message of change
Server enable SNMP traps pppoe
Enable SNMP-server holds the CPU threshold
SNMP Server enable rsvp traps
Server enable SNMP traps syslog
Server enable SNMP traps l2tun session
Server enable SNMP traps l2tun pseudowire status
Server enable SNMP traps vtp
Enable SNMP-Server intercepts waas
Server enable SNMP traps ipsla
Server enable SNMP traps bfd
Server enable SNMP traps gdoi gm-early-registration
Server enable SNMP traps gdoi full-save-gm
Server enable SNMP traps gdoi gm-re-register
Server enable SNMP traps gdoi gm - generate a new key-rcvd
Server enable SNMP traps gdoi gm - generate a new key-fail
Server enable SNMP traps gdoi ks - generate a new key-pushed
Enable SNMP traps gdoi gm-incomplete-cfg Server
Enable SNMP-Server intercepts gdoi ks-No.-rsa-keys
Server enable SNMP traps gdoi ks-new-registration
Server enable SNMP traps gdoi ks-reg-complete
Enable SNMP-Server Firewall state of traps
SNMP-Server enable traps ike policy add
Enable SNMP-Server intercepts removal of ike policy
Enable SNMP-Server intercepts start ike tunnel
Enable SNMP-Server intercepts stop ike tunnel
SNMP server activate ipsec cryptomap add traps
SNMP server activate ipsec cryptomap remove traps
SNMP server activate ipsec cryptomap attach traps
SNMP server activate ipsec cryptomap detach traps
Server SNMP traps enable ipsec tunnel beginning
SNMP-Server enable traps stop ipsec tunnel
Enable SNMP-server holds too many associations of ipsec security
Enable SNMP-Server intercepts alarm ethernet cfm
Enable SNMP-Server intercepts rf
Server enable SNMP traps vrfmib vrf - up low-vrf vnet-trunk-up low-trunk-vnet
Server RADIUS dead-criteria life 2
RADIUS-server host 192.168.10.10
Server RADIUS 2 timeout
Server RADIUS XXXXXXX key
!
!
!
control plan
!
!Line con 0
privilege level 15
connection of authentication radius_auth
line to 0
line 2
no activation-character
No exec
preferred no transport
transport of entry all
transport output pad rlogin lapb - your MOP v120 udptn ssh telnet
StopBits 1
line vty 0 4
privilege level 15
connection of authentication radius_auth
entry ssh transport
line vty 5 15
privilege level 15
connection of authentication radius_auth
entry ssh transport
!
Scheduler allocate 20000 1000
NTP-Calendar Update
Server NTP 192.168.10.10
NTP 64.250.229.100 Server
!
endRouter ipsec crypto #sh her
Interface: GigabitEthernet0/0
Tag crypto map: SDM_CMAP_1, local addr 76.W.E.Rprotégé of the vrf: (none)
local ident (addr, mask, prot, port): (0.0.0.0/0.0.0.0/0/0)
Remote ident (addr, mask, prot, port): (192.168.168.213/255.255.255.255/0/0)
current_peer 75.X.X.X port 2642
LICENCE, flags is {}
#pkts program: 1953, #pkts encrypt: 1953, #pkts digest: 1953
#pkts decaps: 1963, #pkts decrypt: 1963, #pkts check: 1963
compressed #pkts: 0, unzipped #pkts: 0
#pkts uncompressed: 0, #pkts compr. has failed: 0
#pkts not unpacked: 0, #pkts decompress failed: 0
Errors #send 0, #recv 0 errorslocal crypto endpt. : 76.W.E.R, remote Start crypto. : 75.X.X.X
Path mtu 1500, mtu 1500 ip, ip mtu IDB GigabitEthernet0/0
current outbound SPI: 0x5D423270 (1564619376)
PFS (Y/N): N, Diffie-Hellman group: noSAS of the esp on arrival:
SPI: 0x2A5177DD (709982173)
transform: esp-3des esp-sha-hmac.
running parameters = {Tunnel UDP-program}
Conn ID: 2115, flow_id: VPN:115 on board, sibling_flags 80000040, crypto card: SDM_CMAP_1
calendar of his: service life remaining (k/s) key: (4301748/2809)
Size IV: 8 bytes
support for replay detection: Y
Status: ACTIVE (ACTIVE)the arrival ah sas:
SAS of the CFP on arrival:
outgoing esp sas:
SPI: 0x5D423270 (1564619376)
transform: esp-3des esp-sha-hmac.
running parameters = {Tunnel UDP-program}
Conn ID: 2116, flow_id: VPN:116 on board, sibling_flags 80000040, crypto card: SDM_CMAP_1
calendar of his: service life remaining (k/s) key: (4301637/2809)
Size IV: 8 bytes
support for replay detection: Y
Status: ACTIVE (ACTIVE)outgoing ah sas:
outgoing CFP sas:
Routing crypto isakmp #sh its
IPv4 Crypto ISAKMP Security Association
DST CBC conn-State id
76.W.E.R 75.X.X.X QM_IDLE 1055 ACTIVEIPv6 Crypto ISAKMP Security Association
In your acl, nat, you will need to refuse your VPN traffic before you allow the subnet at all. Just put all the declarations of refusal before the declarations of licence.
Sent by Cisco Support technique iPhone App
-
Ping LAN internal via the IPSec VPN Client
It's my scenario.
Software Version 7.2 (1)
I activated the VPN in the external Interface. The IPSec Client pool is in the range 192.168.98.150 - 192.168.98.175.
- Allowed "a whole icmp" out Interface access both within the Interface.
- ICMP & ICMP error inspection is enabled.
- NAT-control is disabled.
Clients are unable to ping any IP within the LAN 'inside' but at the same time, they are able to access the devices in the LAN using HTTP, HTTPS, SSH & TELNET.
CASE 1:
access-list SHEEP extended permits all ip 192.168.98.0 255.255.255.0
NAT (Inside) 0 access-list SHEEP
I get the following log "translation portmap creation failed for CBC icmp outdoors"
CASE 2:
If I add a static 192.168.98.0 public (exterior, Interior) 192.168.98.0 netmask 255.255.255.0
I am able to Ping and the problem is solved.
Could someone explain please this behavior?
- Why ICMP only needs a NAT device when TCP & UDP traffic works very well.
- Why a portmap translation error? Why not dynamic identity NAT?
Hello
So he was correspondent to a configuration 'nat' on the 'outside' interface that had no configuration corresponding 'global' for the destination (probably inside) interface which caused problems and produces the 'portmap' error.
Please do not forget to mark an answer as the correct answer, if she answered your question or useful rate responses
-Jouni
-
IPSec tunnel and join a LAN router
I have to tunnel MikroTik IPSec Cisco ASA.
Cisco WAN: xxx.xxx.xxx.xxx
Cisco LAN: 172.27.0.0/20
MikroTik WAN: .yyy
MikroTik LAN: 172.27.128.0/20
This acts to Cisco configuration:
access extensive list ip 172.27.0.0 acl_encrypt allow 255.255.240.0 172.27.128.0 255.255.240.0
access extensive list ip 172.27.0.0 acl_no_nat_inside allow 255.255.240.0 172.27.128.0 255.255.240.0
NAT-control
Global 1 interface (outside)
NAT (inside) 0-list of access acl_no_nat_inside
NAT (inside) 1 0.0.0.0 0.0.0.0Crypto ipsec transform-set esp-aes-256 ts_esp_aes_256_sha, esp-sha-hmac
card crypto cm_outside 10 correspondence address acl_encrypt
card crypto cm_outside pfs set 10 group5
card crypto cm_outside 10 peers set.yyy
card crypto cm_outside 10 transform-set ts_esp_aes_256_sha
3600 seconds, duration of life card crypto cm_outside 10 set - the security association
card crypto cm_outside 10 set security-association life 1048576 kilobytescm_outside interface card crypto outside
crypto ISAKMP policy 10
preshared authentication
aes-256 encryption
sha hash
Group 5
life 3600tunnel - group.yyy type ipsec-l2l
tunnel - group.yyy ipsec-attributes
pre-shared-key *.Tunnel works fine, when I try to ping from a PC behind Cisco to another PC behind MikroTik.
(e.g. 172.27.1.1 to 172.27.129.1), it works fine (except the first two lost packages which is OK
due to the delay of its ISAKMP/IPsec negotiation).But I need to be able to access a PC behind Cisco's MikroTik.
If I try for example
ping 172.27.129.1
Cisco, all packets are lost.
I guess that Cisco does not use its LAN interface but the WAN interface.
What can I do to make it work?
Not sure why you want to do.
Yes, ASA use the IP address on the outgoing interface as source IP address. So when you ping the remote of the SAA, it will WAN IP.
You can add the following entry in your ACL to see if it works
access-list allowed acl_encrypt ip xxx.xxx.xxx.xxx host 172.27.129.1
Make the changes to the ACL on the remote site as well.
You may or may not add a NAT 0 as well. I don't know because this traffic is started from ASA itself. You can check the log to see what's happening and then make the decision.
-
Hi guys,.
I'm trying to connect 2 1841 routers using ipsec/gre.
the situation is as below:
router a router - Internet - b
router config:
crypto ISAKMP policy 1
BA 3des
preshared authentication
Group 2
ISAKMP crypto key cisco address bb.bb.bb.bbCrypto ipsec transform-set esp-3des esp-md5-hmac TFMset
!
Profile of crypto ipsec ToB
game of transformation-TFMset!
interface Tunnel0
Description * to B *.
IP 100.100.100.1 255.255.255.252
tunnel source aa.aa.aa.aa
destination bb.bb.bb.bb tunnel
ipv4 ipsec tunnel mode
Profile of tunnel ToB ipsec protectioninterface FastEthernet0/0
IP address aa.aa.aa.aa 255.255.255.252
NAT outside IP
!
interface FastEthernet0/1
11.11.11.11 IP address 255.255.255.0
IP nat insideIP route 0.0.0.0 0.0.0.0 FastEthernet0/0
IP nat inside source map route SHEEP interface FastEthernet0/0 overload
IPNAT extended IP access list
deny ip 11.11.11.0 0.0.0.255 22.22.22.0 0.0.0.255
IP 11.11.11.0 allow 0.0.0.255 any
!
SHEEP allowed 10 route map
corresponds to the IP IPNATConfig router B:
crypto ISAKMP policy 1
BA 3des
preshared authentication
Group 2
ISAKMP crypto key cisco address aa.aa.aa.aaCrypto ipsec transform-set esp-3des esp-md5-hmac TFMset
!
Profile of crypto ipsec ToA
game of transformation-TFMset!
interface Tunnel0
Description * to A *.
IP 100.100.100.1 255.255.255.252
tunnel source bb.bb.bb.bb
destination aa.aa.aa.aa tunnel
ipv4 ipsec tunnel mode
Profile of tunnel ToA ipsec protectioninterface FastEthernet0/0
IP address bb.bb.bb.bb 255.255.255.252
NAT outside IP
!
interface FastEthernet0/1
IP 22.22.22.22 255.255.255.0
IP nat insideIP route 0.0.0.0 0.0.0.0 FastEthernet0/0
IP nat inside source map route SHEEP interface FastEthernet0/0 overload
IPNAT extended IP access list
deny ip 22.22.22.0 0.0.0.255 11.11.11.0 0.0.0.255
IP 22.22.22.0 allow 0.0.0.255 any
!
SHEEP allowed 10 route map
corresponds to the IP IPNAT
I managed to see the crypto isakmp and tunnel upward, but I'm not able to ping to the Remote LAN ip...
have you guys any idea on this?
Thank you...
Hello
Try to create a static route on a router for remote network pointing to the source of the tunnel as its front door.
Here is a useful link: -.
https://learningnetwork.Cisco.com/docs/doc-2457
Thank you
Shilpa
-
Hi all
I need to change my actual lan-to-LAN vpn configuration in host-to-lan, and I have a few questions. Maybe someone here can help me.
Current configuration:
SITE A:
-cisco 892
-subnet: 192.168.1.0/24
SITE B:
-hub cisco 3000
-subnet 192.168.2.0/24
I have access to only the site router.
Currently, all clients in the site one can reached site B and vice versa.
Here are my ACLs of the SITE a router:
ip permit 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
Now, I need to change the vpn config in:
-vpn ipsec must be configured between 192.168.2.0/24 (SITE B) and 10.1.1.1/32 (ip protocol used for the nat all clients from SITE A to SITE B)
SITE A router ACL shoul become:
permit host 10.1.1.1 ip 192.168.2.0 0.0.0.255.
All SITE A clients who want to join the SITE B are nat - ed by 10.1.1.1. SITE B cannot reach subnet A SITE, only 10.1.1.1
Now the questions:
IP address 10.1.1.1 shoul be configured on a loopback interface?
How the nat configuration?
Thank you very much.
Hello Richard,.
10.1.1.1 will be configured on loopback interaface. Here's the basic config->
interface Loopback0
10.1.1.1 IP address 255.255.255.255
NAT outside IP
!
interface FastEthernet0/0
IP 192.168.1.1 255.255.255.0
IP nat inside
!
interface FastEthernet0/1
IP 23.0.0.2 255.255.255.0
NAT outside IP
card crypto WCPA
!
overload of IP nat inside source list VPN_NAT_ACL interface Loopback0
!
VPN_NAT_ACL extended IP access list
ip permit 192.168.1.0 0.0.0.255 192.168.2.0 0.0.0.255
VPN_TRAFFIC_ENCRYPT extended IP access list
permit host 10.1.1.1 ip 192.168.2.0 0.0.0.255
Best regards
Please note all useful messages and close issues resolved
Maybe you are looking for
-
Separated from this thread. I do not understand why a BIOS update would fix it. Other people have this same problem. Nevertheless, I will not ask someone from asus to help me install a BIOS update, because I don't have the time, money or patience, an
-
Recycle Office 2007 spam filter on each update?
Why does keep the junk of office e-mail filter whenever there is an update? That must cost white collar and manufacturers a tidy sum small in a fiscal year.
-
I have Microsoft .NET Framework 2.0 service pak, I also Microsoft NET Framework 3.0 installed service pak. My question is can I remove Microsoft .NET Framework 2.0 service pak and just let Microsoft .NET Framework 3.0 service pak? Thanks for your tim
-
Where can I find my passwods for POP3 and STMP.live to receive mail from my PC to my iphone 3 g?
Where can I find my passwods for POP3 and STMP.live to receive mail from my PC to my iphone 3 g?
-
How do I save or burn photos to a CD as taken
the pictures are alphatetized. Date taken no. Every time I have to try and make a CD or put my photos in a folder, it will come out in alphabetical order. Can I check in date taken, but he will not enter a folder this way. Help!