Recovery site - redundant VPN peers
Hello all, thank you in advance for your expertise.
We put in place a recovery site disaster that will host the redundant copies of our servers and critical data in Kansas City. When disaster strikes, our headquarters site would be totally gone.
We currently have 7 locations that communicate to our HQ via VPN tunnels (whether on a circuit of the Internet or on a circuit of Cox Communications Ethernet WAN). Branch sites each can an ISR of Cisco 2821 router. At Headquarters and on the DR site, we use a Cisco ASA 5510 to terminate VPN tunnels and do everything that our column spinal routing. Routing on the ASA and branch routers is all static, using a routing protocol would be a nice update in the future... any ideas? We use IPSEC VPN lan lan tunnels 2, no GRE/VPN is used because it is not terminated by the ASA.
What is the best way to configure my routers for branch to automatically or manually failover to connect to one ASA different site of DR?
In addition, if my seat is still in place, but either my Internet or Cox headquarters ethernet circuit breaks down. How can I re - route all traffic in a loop to the seat on the right remains a circuit?
Is there a better way to do what I want to accomplish? BGP is not an option at this point due to its complexity.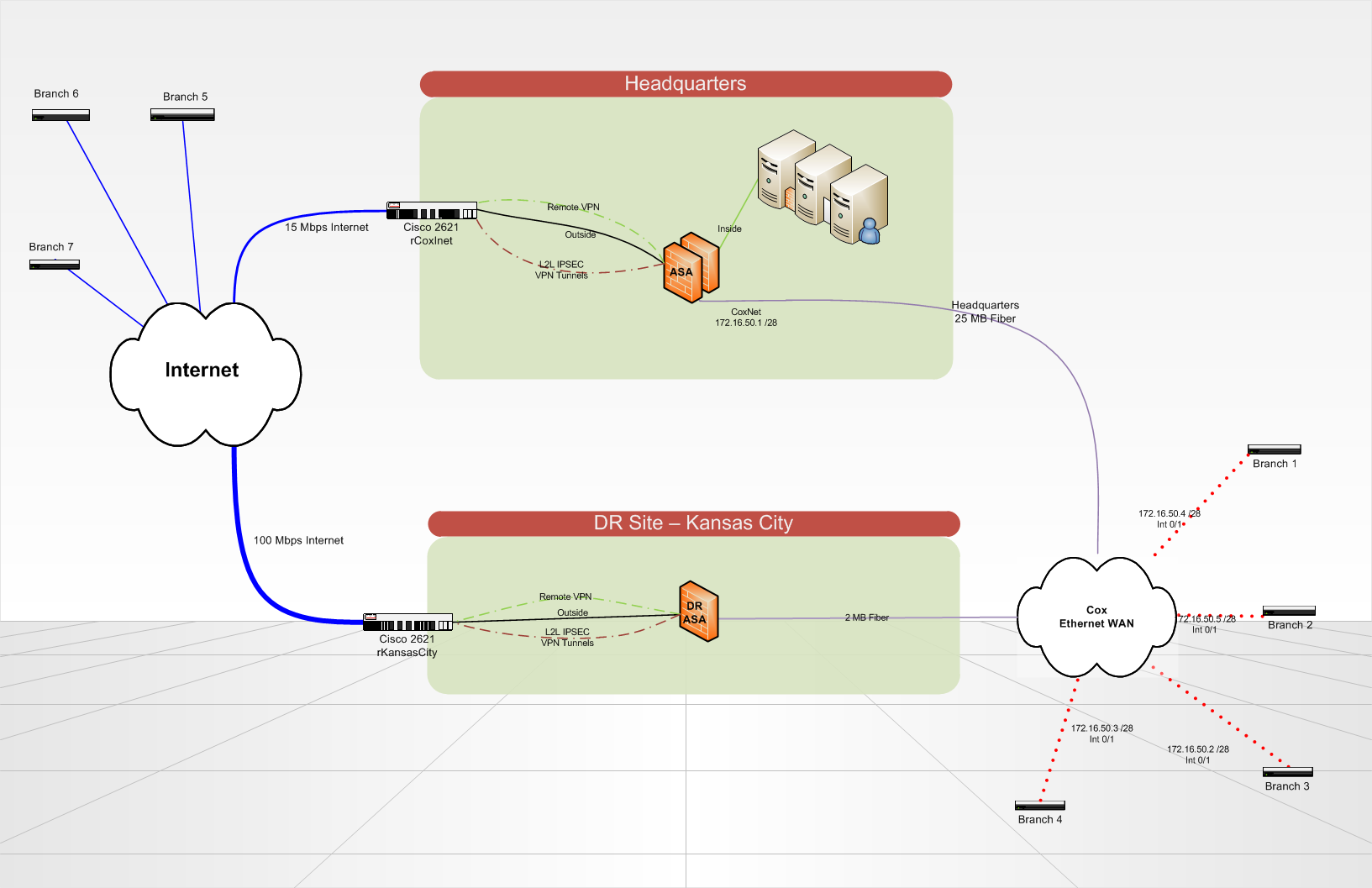
Lucas,
To circumvent the two point separately.
The best way to provide active / standby time of reundancy is preferred peer in cryptographic cards (on the ISR routers).
You can choose to establish VPN to HQ and only if HQ is not aid you to DR, when HQ is you will EVENTUALLY return to it.
The answer to share of your questions may also be the preferred option by peers (and several counterparts in a crypto map entry).
This being said, you can try to send OSPF traffic to IPsec tunnel (and using the neighbor command to avoid the manipulation of mcast in pure IPsec).
Docs:
HTH,
Marcin
P. S.
If you want my personal opion, chaning ASAs in HQ and DR sites and put you in routers could make DMVPN or DVTI-ASIT scenario which gives you a lot more features ;-)
Tags: Cisco Security
Similar Questions
-
Disater recovery site main VPN, OSPF
I am trying to find a solution for our site recovery. We have 13 websites with VPN tunnles back to the main site with OSPF and GRE tunnels for routing. I need to make a site separate from the main site mirror (ip addresses, VIRTUAL LANs, etc.). How can I switch the VPN sites on the site automatically using the GRE and OSPF network disaster recovery using the same model of IP address?
The stateless failover is used when primary network edge platform fails, IPsec sessions can failover and reconnect to the edge network backup platform, thereby reducing downtime of connection.
-
Hi all
I need a solution for this implementation:
2 sites
2 internet connections each site (different suppliers)
1 ASA in each site
I need a config that allows me to have redundant VPN connections from one site to the other. I need to have a VPN using the, say, internet connection A of site 1 and internet connection from site 2 and if the internet connection A of site 1 goes down the VPN connect by using the internet connection B from site 1 to site 2 A internet connection. This must be done without user intervention.
If I can't do it with the ASA which can use to achieve this scenario? Another router (2900), a kind of load balancing?
I would like to use the ASA because I have a lot of inbound NAT configured and keeping addresses public IP on the SAA outside interface would be great.
Thank you, best regards.
Yes.
You can apply the same card encryption on both interfaces.
Also... If you have multiple VPN peers, they end on the same card encryption as well.
If you for example need many VPN Site to Site tunnels, you create a single card encryption with sequence numbers different to accept VPN connections.
Federico.
-
Should what license I for 25 SSL VPN peers
Hi all
I want to implement cluster active / standby with a pair of ASAs 5550 and I have a licensing question. Here's the "sh - key retail activation" leave two output devices...
ASA1:
SH - activation in detail key:
Serial number: XXXXX
No temporary key assets.
Activation key running: XXXXX XXXXX XXXXX XXXXX XXXXX
The devices allowed for this platform:
The maximum physical Interfaces: unlimited
VLAN maximum: 250
Internal hosts: unlimited
Failover: Active/active
VPN - A: enabled
VPN-3DES-AES: enabled
Security contexts: 2
GTP/GPRS: disabled
SSL VPN peers: 2
Total of the VPN peers: 5000
Sharing license: disabled
AnyConnect for Mobile: disabled
AnyConnect Cisco VPN phone: disabled
AnyConnect Essentials: disabled
Assessment of Advanced endpoint: disabled
Proxy sessions for the UC phone: 2
Total number of Sessions of Proxy UC: 2
Botnet traffic filter: disabled
This platform includes an ASA 5550 VPN Premium license.
Flash activation key is the SAME as the key running.
ASA2:
SH - activation in detail key:
Serial number: XXXXX
No temporary key assets.
Activation key running: XXXXX XXXXX XXXXX XXXXX XXXXX
The devices allowed for this platform:
The maximum physical Interfaces: unlimited
VLAN maximum: 250
Internal hosts: unlimited
Failover: Active/active
VPN - A: enabled
VPN-3DES-AES: enabled
Security contexts: 2
GTP/GPRS: disabled
VPN SSL counterparts: 25
Total of the VPN peers: 5000
Sharing license: disabled
AnyConnect for Mobile: disabled
AnyConnect Cisco VPN phone: disabled
AnyConnect Essentials: disabled
Assessment of Advanced endpoint: disabled
Proxy sessions for the UC phone: 2
Total number of Sessions of Proxy UC: 2
Botnet traffic filter: disabled
This platform includes an ASA 5550 VPN Premium license.
Flash activation key is the SAME as the key running.
--------------------------------------------------------------
It seems so obvious that I have to upgrade the first ASA to support 25 SSL VPN peers in order to create the cluster HA, right?
Now, I want to know do I need the license "ASA5505-SSL25-K9" or something else.
Thank you very much in advance for any help!
Ah OK I see - right then: upgading pole will allow the license to share.
Re the version target, I would recommend going directly to 8.4 (4.1). I have it deployed on several sites without problem.
-
Question of redundancy VPN l2l using 2811 as endpoint devices
I have a new implementation of VPN L2L passes using two 2811 s than VPN terminal devices. I'll try to use the HSRP address between the public interfaces of both routers as VPN peer address. The problem that I found during the test is that the tunnel will become active and debugs watch the HSRP address as an invalid address to form the tunnel. Have a work-around, or a better plan for redundancy on peering address using similar devices? Thanks in advance.
Take a look at this doc about IOS IPSec HA.
-
Hi, I currently have a site to site vpn upward and running and it works fine. I try to put the other two online and just cannot make them work. I used the same configuration of one operation but I cannot get the next tunnel. I saw several errors when debugging isakmp and ipsec and they are at the end of my configs. Anyone have any ideas? Thank you
Main site - a vpn clients connecting too it and pt to pt vpn to 3 endpoints
Cisco PIX Firewall Version 6.3 (3)
* Main Site Config *.
client_vpn 10.10.0.0 ip access list allow 255.255.0.0 192.168.0.0 255.255.255.0
VPN_to_Site2 10.10.0.0 ip access list allow 255.255.0.0 192.168.0.0 255.255.255.0
NAT (inside) 0-list of access client_vpn
Permitted connection ipsec sysopt
Crypto ipsec transform-set esp-3des esp-md5-hmac fws_encry_set
outside_map 60 ipsec-isakmp crypto map
address for correspondence card crypto outside_map 60 VPN_to_Site2
crypto outside_map 60 peer 64.X.X.19 card game
card crypto outside_map 60 transform-set fws_encry_set
outside_map interface card crypto outside
ISAKMP allows outside
ISAKMP key * address 64.X.X.19 netmask 255.255.255.255 No.-xauth-no-config-mode
ISAKMP identity address
ISAKMP nat-traversal 20
part of pre authentication ISAKMP policy 10
ISAKMP policy 10 3des encryption
ISAKMP policy 10 md5 hash
10 2 ISAKMP policy group
ISAKMP life duration strategy 10 86400
Site 2 config
* only because the pt to pt does not work I have it set up to allow vpn clients to cross to connect to the main site.
Cisco PIX Firewall Version 6.3 (5) *.
permit access ip 192.168.0.0 list VPN_to_Main 255.255.255.0 10.10.0.0 255.255.0.0
NAT (inside) 0-list of access VPN_to_Main
Permitted connection ipsec sysopt
Crypto ipsec transform-set esp-3des esp-md5-hmac fws_encry_set
outside_map 10 ipsec-isakmp crypto map
outside_map card crypto 10 corresponds to the address VPN_to_Main
crypto outside_map 10 peer 207.X.X.13 card game
card crypto outside_map 10 transform-set fws_encry_set
outside_map interface card crypto outside
ISAKMP allows outside
ISAKMP key * address 207.X.X.13 netmask 255.255.255.255 No.-xauth-no-config-mode
ISAKMP identity address
ISAKMP nat-traversal 20
part of pre authentication ISAKMP policy 10
ISAKMP policy 10 3des encryption
ISAKMP policy 10 md5 hash
10 2 ISAKMP policy group
ISAKMP life duration strategy 10 86400
Errors
PIX (config) # IPSEC (sa_initiate): ACL = deny; No its created
authenticator is HMAC-MD5IPSEC (validate_proposal): invalid local address
I have a link that works very well. I have copied the config from there, changed the ip info and it does not work. The only differences in the configs are no sysopt route dnat and it's on Version 6.2 (2)
IPSec (sa_initiate): ACL = deny; No its created
I think that you have configured a VPN tunnel without removing the cryptographic card of the external interface. The message above is the error we get in such situation.
I suggest the following solution:
-remove the external interface (the two pix) cryptographic card
-Cree claire isa his and trendy clear ipsec his (the two pix)
-Reapply the card encryption on external interfaces.
If this doesn't solve the problem, restart the equipment.
Kind regards
Ajit
-
How to get the ID of externsión SRM in an environment shared recovery sites
I am setting up a new site and I want to get this protected site and point to the existing shared recovery site.
I have no idea what is the ID extension SRM used the previous seller
Is anyway to extract the extension of MRS. ID?
Connect to the SRM at-> Solutions and Applications, go to the Sites-> Summary tab and you will see the ID of SRM as in this picture:
-
Protection and recovery Site ESX versions
All,
Not sure if this has been asked before, but is there a compatibility issue if my protected site is running vCenter 4.1, ESXi 4.1, 4.1.1 SRM and my recovery site is running vCenter 4.1, ESX 4.0 Update1 and SRM 4.1.1? Basically it is based, and I will have issues if my ESX version is higher on the protected site.
Thank you!
Hello
Although it is important to keep all versions ESX and vCenter the same, the difference in ESX versions directly will not affect SRM or the recovering site as long as controllers (vCenter) are the same at all levels. Most of that depends on SRM is databases.
-rp
-
Question of shared recovery Site
Here's my scenario. I need to test VMware View and SRM. I plan to use scripts provided by EMC to help with view and SRM because the view was not really made to be able to test in a DR scenario.
I have two vCenters in a production data center. One is used for my normal "servers" and is vCenter 4.1 x 64. The other vCenter is used for VMware View host computers, I have this vCenter (called "VDI") because I use View Composer and it is not compatible with x 64 servers.
On the site of DR, I have a vCenter. It is currently running vCenter 4.0. Now, I know that I can have a shared with MRS recovery site, but virtual machines can also be shared?
For example, should I perform a test of SRM which includes a production vCenter my "Server" domain controller and also include the view virtual machines that are part of the other 'VDI' vCenter in my production?
Thank you!
First of all, what version of MRS. you plan to use? You mentioned the two vCenter 4.1 and 4.0. SRM 4.1 is not compatible with vCenter 4.0 and SRM 4.0.x is not compatible with vCenter 4.1 (SRM versions must be the same at all sites).
Regarding your question, I have not implemented recovery shared functionality, but as far as I know, even in this configuration you can still pair site independently, i.e. protected satellite site SRM and SRM instance of its corresponding recoverysite instance. So I don't think that the associations for the Protection of several sites will be available to include in the unique recovery plan.
Please correct me if I'm wrong.
Michael
-
RAC replication environment in a disaster recovery Site
Hi all, in my environment I must reproduce the main site on a recovery site disaster. I use the network at high speed between the two sites and the data on file systems shared on two of SEM (one on the primary) and one on the site of the disaster related synchronously.
My environment's RAC ORACLE 11 g 2, with AIX 6.1 and clusters of twins between the primary recovery and disaster sites.
Recovery site servers have IP addresses and different IP names and names of main site.
I mean, I installed my first ORACLE RAC, but I don't know how to install ORACLE RAC in the Dr site after a disaster.
I have a few questions:
(1) how should install ORACLE RAC in the recovering site, based on SAN storage that is constantly in overrided by replication of the primary storage to the storage of physical recovery? of course, the recovering site, ORACLE RAC is usually kept off-line, but I don't know how to organize the alignment between the two (primary and recovery) ORACLE environments and how to make the process of taking control.
Please, can you tell me?
Thank you
MarcoHi Marco,.
I think you should be able to start.Have you implemented this or being implemented?
I don't know about the behavior of replication SAN disk OCR/vote. But we use it for the database unique instance and it works fine.
I also suggest you open SR with oracle support on this subject.
Concerning
Rajesh -
Another scenario of test - isolate the recovery Site
Question for the gurus out there:
Installation: We have a simple configuration with a single restore site protected and unique. The configuration of the network is stretched VLAN. All the tests to bubble networks works as advertised, and we are very pleased with the solution so far. In addition to virtual infrastructure, there is a certain physical systems that make up the environment, and the goal is to make a complete failure on the test of the site in the coming weeks.
Test case: the proposed solution is to drop the link between sites protected-recovery and turn the entire failover datacenter in a bubble (only accessible through VPN links). Once the test is completed, we would have back then all the changes on the recovering site, so that it protects once more the main site.
Question: Would it be possible to rotate part SRM to the test in 'Test' mode only - that she set up the whole environment attached to the VLAN direct (who are now isolated from production by dropping the link of the site) and once finished, reset the recovery by the normal site (i.e. "Test recovery finished, press on continue clean...") ») ? I don't see why it wouldn't work, unless for some reason, the test procedure requires communication between the sites that the effective recovery process does not.
Thanks for any comments.
Hello
Recovery test requires no connection to the protected site as far as I know.
About the networking part of your question, when you change a recovery plan, on the network management screen you have an option to configure the test networks. These networks is used during the trial instead of bubble networks (default).
SRM will be cleaning the virtual environment, but how do you cleaning physical servers?
For how long you plan to run on the recovering site? You have sufficient capacity for snapshots on your storage array?
Michael.
-
ISA500 site by site ipsec VPN with Cisco IGR
Hello
I tried a VPN site by site work with Openswan and Cisco 2821 router configuration an Ipsec tunnel to site by site with Cisco 2821 and ISA550.
But without success.
my config for openswan, just FYI, maybe not importand for this problem
installation of config
protostack = netkey
nat_traversal = yes
virtual_private=%v4:10.0.0.0/8,%v4:192.168.0.0/16,%v4:172.16.0.0/12,%4:!$RIGHT_SUBNET
nhelpers = 0
Conn rz1
IKEv2 = no
type = tunnel
left = % all
leftsubnet=192.168.5.0/24
right =.
rightsourceip = 192.168.1.2
rightsubnet=192.168.1.0/24
Keylife 28800 = s
ikelifetime 28800 = s
keyingtries = 3
AUTH = esp
ESP = aes128-sha1
KeyExchange = ike
authby secret =
start = auto
IKE = aes128-sha1; modp1536
dpdaction = redΘmarrer
dpddelay = 30
dpdtimeout = 60
PFS = No.
aggrmode = no
Config Cisco 2821 for dynamic dialin:
crypto ISAKMP policy 1
BA aes
sha hash
preshared authentication
Group 5
lifetime 28800
!
card crypto CMAP_1 1-isakmp dynamic ipsec DYNMAP_1
!
access-list 102 permit ip 192.168.1.0 0.0.0.255 192.168.5.0 0.0.0.255
!
Crypto ipsec transform-set ESP-AES-SHA1 esp - aes esp-sha-hmac
crypto dynamic-map DYNMAP_1 1
game of transformation-ESP-AES-SHA1
match address 102
!
ISAKMP crypto key
address 0.0.0.0 0.0.0.0 ISAKMP crypto keepalive 30 periodicals
!
life crypto ipsec security association seconds 28800
!
interface GigabitEthernet0/0.4002
card crypto CMAP_1
!
I tried ISA550 a config with the same constelations, but without suggesting.
Anyone has the same problem?
And had anyone has a tip for me, or has someone expirense with a site-by-site with ISA550 and Cisco 2821 ipsec tunnel?
I can successfully establish a tunnel between openswan linux server and the isa550.
Patrick,
as you can see on newspapers, the software behind ISA is also OpenSWAN
I have a facility with a 892 SRI running which should be the same as your 29erxx.
Use your IOS Config dynmap, penny, you are on the average nomad. If you don't have any RW customer you shoul go on IOS "No.-xauth" after the isakmp encryption key.
Here is my setup, with roardwarrior AND 2, site 2 site.
session of crypto consignment
logging crypto ezvpn
!
crypto ISAKMP policy 1
BA 3des
preshared authentication
Group 2
lifetime 28800
!
crypto ISAKMP policy 2
BA 3des
md5 hash
preshared authentication
Group 2
lifetime 28800
!
crypto ISAKMP policy 3
BA 3des
preshared authentication
Group 2
!
crypto ISAKMP policy 4
BA 3des
md5 hash
preshared authentication
Group 2
!
crypto ISAKMP policy 5
BA 3des
preshared authentication
Group 2
life 7200
ISAKMP crypto address XXXX XXXXX No.-xauth key
XXXX XXXX No.-xauth address isakmp encryption key
!
ISAKMP crypto client configuration group by default
key XXXX
DNS XXXX
default pool
ACL easyvpn_client_routes
PFS
!
!
Crypto ipsec transform-set esp-3des esp-sha-hmac FEAT
!
dynamic-map crypto VPN 20
game of transformation-FEAT
market arriere-route
!
!
card crypto client VPN authentication list by default
card crypto VPN isakmp authorization list by default
crypto map VPN client configuration address respond
10 VPN ipsec-isakmp crypto map
Description of VPN - 1
defined peer XXX
game of transformation-FEAT
match the address internal_networks_ipsec
11 VPN ipsec-isakmp crypto map
VPN-2 description
defined peer XXX
game of transformation-FEAT
PFS group2 Set
match the address internal_networks_ipsec2
card crypto 20-isakmp dynamic VPN ipsec VPN
!
!
Michael
Please note all useful posts
-
Hi guys,.
I'm trying to get the Site working on two 5505 VPN of Site I have in my lab.
Attached image...
I used the Setup Assistant, and I think that sounds good. However, this does not work when I run the following command:
Community-Site # sh ipsec his
There is no ipsec security associations
I think I generate traffic, then I tried to ping and access IIS from one laptop to the other without a bit of luck.
Ping between ASAs works very well.
ASAs are 5505 8.2 (5)
Config is:
Community site
interface Ethernet0/0
Outside description
switchport access vlan 2
!
interface Ethernet0/1
Inside description
!
interface Ethernet0/2
!!
interface Vlan1
Description Community Site
nameif inside
security-level 100
address 192.168.20.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 50
IP 10.181.10.2 255.255.255.0the obj_any object-group network
inside_access_in list extended access permit icmp any one
inside_access_in of access allowed any ip an extended list
outside_access_in of access allowed any ip an extended list
outside_access_in list extended access permit icmp any one
outside_1_cryptomap to access extended list ip 192.168.20.0 allow 255.255.255.0 255.255.255.0 network-remote control
inside_nat0_outbound to access extended list ip 192.168.20.0 allow 255.255.255.0 255.255.255.0 network-remote controlGlobal 1 interface (outside)
NAT (inside) 0-list of access inside_nat0_outbound
NAT (inside) 1 0.0.0.0 0.0.0.0inside_access_in access to the interface inside group
Access-group outside_access_in in interface outside
Route outside 0.0.0.0 0.0.0.0 10.181.10.1 1Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
card crypto outside_map 1 match address outside_1_cryptomap
card crypto outside_map 1 set pfs Group1
peer set card crypto outside_map 1 10.181.1.1
card crypto outside_map 1 set of transformation-ESP-3DES-SHA
outside_map interface card crypto outside
crypto ISAKMP allow outside
crypto ISAKMP policy 10
preshared authentication
3des encryption
sha hash
Group 2tunnel-group 10.181.1.1 type ipsec-l2l
IPSec-attributes tunnel-group 10.181.1.1Config on the other side is:
Corporate
description of remote control-network name 192.168.20.0 Community Network
!
interface Ethernet0/0
Outside description
switchport access vlan 2
!
interface Ethernet0/1
Inside description
!
interface Ethernet0/2
!!
interface Vlan1
Torbay Corp description
nameif inside
security-level 100
IP 192.168.10.1 255.255.255.0
!
interface Vlan2
nameif outside
security-level 50
IP 10.181.10.1 255.255.0.0
!
passive FTP mode
outside_access_in_1 of access allowed any ip an extended list
outside_access_in_1 list extended access permit icmp any one
inside_access_in_1 of access allowed any ip an extended list
inside_access_in_1 list extended access permit icmp any one
permit outside_1_cryptomap to access extended list ip 192.168.10.0 255.255.255.0 255.255.255.0 network-remote control
permit inside_nat0_outbound to access extended list ip 192.168.10.0 255.255.255.0 255.255.255.0 network-remote control
pager lines 24Access-group outside_access_in_1 in interface outside
inside_access_in_1 access to the interface inside group
Route outside 0.0.0.0 0.0.0.0 10.181.10.2 1Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
card crypto outside_map 1 match address outside_1_cryptomap
card crypto outside_map 1 set pfs Group1
peer set card crypto outside_map 1 10.181.10.2
card crypto outside_map 1 set of transformation-ESP-3DES-SHA
outside_map interface card crypto outside
crypto ISAKMP allow outside
crypto ISAKMP policy 10
preshared authentication
3des encryption
sha hash
Group 2
life 86400
tunnel-group 10.181.10.2 type ipsec-l2l
IPSec-attributes tunnel-group 10.181.10.2
pre-shared key *.
!Hi haidar_alm,
After a quick glance to the configuration, I found an error with the vpn peer on the Community Site:
peer set card crypto outside_map 1 10.181.1.1
tunnel-group 10.181.1.1 type ipsec-l2l
IPSec-attributes tunnel-group 10.181.1.1The public ip address of morality is 10.181.10.1.
Correct configuration:
peer set card crypto outside_map 1 10.181.10.1
tunnel-group 10.181.10.1 type ipsec-l2l
IPSec-attributes tunnel-group 10.181.10.1-JP-
-
Site configuration VPN Multi site.
I currently can do a site VPN between two routers, but I need a little help on how to add another site to the config. Sites remote only need to talk to the router base so I shouldn't need free WILL, but I'm not sure what is the right way to add additional hosts. It seems that I can only add a card encryption to a physical interface so, how do you add the other site?
It's all the orders I have run to get the top of the site to another and going to what else do I need to add? Sorry to be a newb.
Router (config) #crypto isakmp policy 9
Router (config-isakmp) #hash sha
Router (config-isakmp) #authentication pre action
Router (config) #crypto isakmp key address
Router (config) #crypto ipsec - the association of safety to life seconds 86400
Router (config) #access - list 110 permit ip any one
Router (config) #crypto ipsec transform-set esp-3des esp-sha-hmac Test
Router (config) #crypto map Test 1 ipsec-isakmp
Peer Router (config-crypto-map) #set
Router (config-crypto-map) #set transform-set Test
Address of the router (config-crypto-map) #match 110
Router (Config-if) #crypto map Test * \run command on the int of the VPN
Hi Chris,
You can do it. Source peer ip address is an address that corresponds to your address outside. But you can have several pairs of destination and policies that can be assigned to the same router.
http://www.Cisco.com/en/us/Tech/tk583/TK372/technologies_configuration_example09186a008009463b.shtml
This document helps you to be better. It's a basic documentation. But this will give you an idea.
Please assess whether the information provided is useful.
By
Knockaert
-
Router 886VA Site to site ipsec vpn fqdn
Hello
I would like to create a vpn site-to site with a crypto fqdn on the side of the branch.
The reason is in our head office in the wan IP will be hungry for change, and I want the branch office router to reconnect as soon as they get the new ip address.
How could a which?
Here is my Config:
ip domain lookup source-interface Dialer0 crypto isakmp policy 10 encr aes authentication pre-share group 2 lifetime 14400 crypto isakmp key MyKey address 22.22.22.22 crypto ipsec transform-set MySET esp-3des esp-md5-hmac crypto map BranchMap 10 ipsec-isakmp description HDG set peer 22.22.22.22 set transform-set MySET match address 110 int Dialer 0 ip access-group 101 in cryptop map BranchMap access-list 101 remark INT DIALER0 INCOMING access-list 101 permit udp host 62.2.24.162 eq domain host 11.11.11.11 access-list 101 permit udp host 62.2.17.60 eq domain host 11.11.11.11 access-list 101 permit udp host 22.22.22.22 host 11.11.11.11 eq non500-isakmp access-list 101 permit udp host 22.22.22.22 host 11.11.11.11 eq isakmp access-list 101 permit esp host 22.22.22.22 host 11.11.11.11 access-list 101 permit ahp host 22.22.22.22 host 11.11.11.11 access-list 101 permit tcp any any established access-list 101 permit udp host 129.132.2.21 eq ntp host 11.11.11.11 eq ntp access-list 101 permit udp host 130.60.75.52 eq ntp host 11.11.11.11 eq ntp access-list 101 permit udp host 8.8.8.8 eq domain host 11.11.11.11 access-list 101 remark INT DIALER0 INCOMING
11.11.11.11 = > local WAN IP Branch
22.22.22.22-online distance seat WAN IP
Thank you
If your HQ has a (rare) dynamic IP address, you must do 3 things:
1. set up a dynamic DNS host name for your HQ VPN peer (dyndns.org, etc..)
2. your counterpart dynamic crypto map using "dynamic peer hqddns.company.com defined".
3. your isakmp for the peer key a wildcard character ("crypto isakmp key addr 0.0.0.0")
If you say that it is an IP change single opposite HQ, then maybe:
1 Add the new IP address to your 'access-list 101' ACL (remember to use a name instead of ACL numbered for readability)
2. Add another encryption with the new IP address isakmp key
3. Add the new IP address as secondary peer:
map BranchMap 10 ipsec-isakmp crypto
the default peer 22.22.22.22
defined peer 3.3.3.3
Maybe you are looking for
-
Need driver for my hp 15 r-033tx USB bus controller... Not fint in site...
-
On Qosmio G30 black screen after installing Windows XP
Hello worldI want you help me solve my problem.I have a Qosmio G30E - 148 and when you install a new program, the BSOD had been posted. prevents me from having access to windows fromnormal mode and safe mode.Then I installed a new Win XP manually and
-
Automation of absolute or relative mode on graphs
Hello I want to do a control triggers an event on my Panel frontal vi, which makes alternate time graphics mode to absolute relative in x mode. I can't find the property or method where I can access this mode. When right-clicking on the chart contr
-
Disable energy Mode on HP OfficeJet 6700 Premium economy
Not seeing a way to do it on the front or in the SAP. Anyone know if this is possible? I'm guessing that probably not but I would check. Printing from ePrint seems stifling once the printer goes into power saving mode.
-
Print on paper with HP Photosmart 7510
I have a HP Photosmart 7510 and need to print on custom size paper. Is anyway to do this with the printer HP Photosmart 7510?
