ISE 1.2 defined strategy
Just had a quick/easy question about activation of the ISE political sets.
We have a current work ISE environment, and I wanted to just make sure when to activate the strategy games, that he's not kidding anything upwards when I turn it on. Thought I'd ask someone who did it before. I wanted no surprises. Have not found this insurance in the docs.
Thank you!!
Activation of strategy sets, everything leaves you just rules in the game of strategy by default, so no change there. Be aware, though, that once you start to create your rules and strategy games, there is no easy way to return to policy unsettled depending on configuration
Tags: Cisco Security
Similar Questions
-
ISE: Change of lifestyle politics
Hello
I want to move on to political games of our current compex set of rules, anyone has done this and if so what happens to your existing rules?
I looked through the documentation and all it says is that you can change the policy mode, but not what is happening to your existing policy.
Thank you
Hi Martin,
- After you do a new installation of ISE 1.2 or Cisco ISE upgrade, version 1.1 to version 1.2 ISE, the Simple Mode strategy template is selected by default.
- If you choose to enter the Simple Mode defined political mode, authentication policies and authorization are migrated to the default strategy game.
- If you choose to switch to Mode Simple of POLICYMODE set, authentication and authorization of the whole of the default policy are migrated to be authentication and authorization strategies. All other strategy game policies are deleted.
For more information on the overall assessment of the policy, please refer to the User Guide 1.2 ISE.
Here is the link for the same thing.
http://www.Cisco.com/c/en/us/TD/docs/security/ISE/1-2/user_guide/ise_use...
-
ISE GANYMEDE authentication - connect before you decide if you should have access
I'm away Cisco ACS to ISE Cisco version 2.1 to control GANYMEDE of my network devices. I opened a proof with TAC but the answer, I seem to fly intuitive and hope for verification of this is now the way that Cisco or I just need to set up my policy defines differently.
For a switch using ACS for the administration, a user will be SSH to the machine and if they are not in good AD security group, the user will receive a response from denial of access
With ISE GANYMEDE to the administration, the user will be SSH to the machine and because they are a member of the AD domain they authenticate and connect the device actually get a command prompt. Now this same user if they are not in the right group of safety AD that they will not be allowed to do anything on the switch.
According to my TAC, ISE needs to identify the user, before he can decide if that user is allowed to access the device. It is not fine with me because basically, anyone in my company can now connect on these devices. Outside put ACLs on the switches that allow access only from certain computers, what are others doing to mitigate this risk?
Thank you
Hi Ken,
In the event that you have configured your ISE with a new 2.1 installation, follow these steps:To the "device Admin defined strategy", leave the part "Authentication" of a rule as it is.
In the "Authorization" section, add your security AD as conditions groups (select the box on the right under the conditions of-> create new condition-> to 'select attribute': 'AD login name'-> ExternalGroups-> 'equal'-> name of group to choose AD) and the right set of commands and the Shell profile for each security group.Now the importand part: the last rule is the default rule that will be used if the user is not a member of a security group that was the condition of an old rule.
Here, you should make sure that the profile ' refuse of all Shell "is selected, it means that if this rule should be used, the user will be blocked from access.In case you went from 2.0 to 2.1, you may be suffering from this bug here:
https://BST.cloudapps.Cisco.com/bugsearch/bug/CSCva04654/?referring_site=bugquickviewredir Then you simply do not have a profile ' refuse of all Shell "as an option.
I'm building a work around for my system:
I created a new profile of shell, which has a "disconnect" as command 0 privielege max level and auto.
I loaded this profile of shell in the default rules.
Maybe this isn't the best solution, but it does what it should do.Let me know if it worked and it please note useful responses!
Greetings,
MaxEdit: spelling mistakes
-
ISE 1.4 and access for guests with distinct SMS providers
Could someone please help with the installation of the guest access. I am trying to perform an establishing a unique SSID prompted with two central WISN and a pair of ISE 1.4 to manage a building containing different companies. Installation work good with a sponsor (company) chooses just the customer who registered but at the end of the implementation the handover raised a question that left me speechless. Every company wants to have their own account SMS provider. How can I configure so that the end-user location defines the SMS provider?
Hello
There are 2 different stand-alone ise or there are members of the same deployment?
You can add gateways sms on the parameters of the ise. So if there are 2 different deployment, simply choose the sms gateway that you created in a configuration Portal comments.
If you have only 2 servers ise 1 deployment, you can create 2 comments portal on each one you set the right sms gateway.
If you have 1 deployment and have the same ssid comments:
-divide PSA between 2 companies using the AP group
-to the ise, you can use the defined strategy (simpler and more readable).
-According to the AP group, you can Portal popup comments 1 to 1 group AP and another portal of comments for another group of AP. In order to make this work, you need to change the type of id station call on the Security tab, on the wlc himself.
hope this is clear.
If you have deployed MSE, you can set your rules and popup portal based on the physical location without the use of the AP group
-
Updates to Windows does not and Administrator error Message.
I had a problem with my windows updates. It won't work and I get a message that reads: administrator defined strategy than refusing you the right to perform this action. I am the owner of this computor. However, he belonged to a leasing company before I buy it. I created the property with my computer manufacturer. What should I do?
Hi Ann K.
Step: We can try to activate the default Administrator profile.
http://support.Microsoft.com/default.aspx/KB/555910
Step 2: Now fix your corrupted user profile
You will need to create a new profile and then copy the files from the existing to the new profile.
http://Windows.Microsoft.com/en-us/Windows-Vista/fix-a-corrupted-user-profile
Now connect to your new profile and check if everything is working properly.
NOTE: Disable the default Administrator account again. Follow the steps in the Article and on this line at the command prompt, type net user administrator / active: No.and then press ENTER. (change the Yes by not)
After back and let us know if it helped to solve your problem.
Thank you and best regards,
R uma - Microsoft technical support.
Visit our Microsoft answers feedback Forum and let us know what you think.
-
Are there recommendations regarding when you choose to open a session at the beginning or end? I know in some circumstances, the only option is to immediately because of the packet dropped, but what about in other situations?
For example, I have an access control rule that has balanced security and a defined strategy for IPS connectivity and a custom policy file. The action is set on allow which should still block bad things, if it goes through. Is it better to open a session at the beginning or end?
My default action for this policy has the network discovery. Is it better to open a session at the beginning or end?
The only other place that I have enabled logging is in SSL policies and you can only connect at the end.
The problem is that I came across a problem where CME seems to have very few events (like maybe an hours value), whereas before, I had days worth so I feel that I now have too many records enabled. The virtual appliance that resembles it culminates at connection of 10 M running events.
If you want see what happens on the network and keep track, you have logging enabled.
I suggest to use end-of-connection in there also.
Political SSL you can have it with end of connection as the political SSL must decide and then open a session that will be better.
Rate if helps.
Yogesh
-
AnyConnect and DAP does not not on ASA 8.3.2?
Hello
I encountered a problem using the AnyConnect client after upgrade ASA5510 to 8.3.2 (from 8.3.1). After entering the username and password in the browser, the error message "connection refused. Your environment does not meet the conditions of access defined by your administrator. "appears.
Some of the results:
1 connect to the ASA 8.3.1 and 8.2.3 works very well with dynamic access policies (RAP) defined
2 connection to ASA 8.3.2 fails when political DAP are defined
3. connect to ASA 8.3.2 works well when no DAP (except DfltAccessPolicy) policy is defined
4. error in the syslog file messages are "% ASA-3-734004: DAP: processing error: Code 2358" and "% ASA-3-734004: DAP: processing error: Code 3626".
5 cisco Secure Desktop is enabled, but not conduct audits host Scan.Versions of the software in use:
-Secure desktop cisco 3.5.1077
-AnyConnect 2.5.0217
-Used for testing clients are running Windows XP and VistaIt doesn't seem to matter what the DAP policy contains, just that it exists. I tried to add a new policy to a single "Application = IPsec' (which he must jump and move to DfltAccessPolicy) and the other with a single"Application = AnyConnect"(that he must match and be allowed access). IPsec clients corresponding to the first and continue as usual, but the AnyConnect client stops as long as there is at least a defined strategy. The problem exists even if the DfltAccessPolicy is set to "continue".
I see this problem on two different ASA5510s. Is this a known issue?
More than likely you are running in the CSCth56065bug. If you open a case with TAC, we can provide you the 8.3.2.1 Provisional which includes the fix.
-
Problem with application MyPolicy "permission denied."
Hi all
Apply policies to PDFs using LiveCycle web services! We
first tried with the API and we had the same problem with both
approach:(to make it easier, I'll post the code API)
When we use the example it works just fine:
strategy game: the overall strategy defined
policy name: restrict to all majorDocument protectPDF = documentManager.applyPolicy)
inPDF,
"LoanPDF,"
"Global policy set."
"Restrict to all major."
NULL, null);so, we've created custom with the LC Gui (EDC) policies
and when we try to use them with our customer we get this error:Document protectPDF = documentManager.applyPolicy)
inPDF,
"LoanPDF,"
"MyPolicies."
"antoinetest,"
"PCW", "antoine.blanchard");= > adobe.edc.sdk.SDKException: failure of politics
[MyPolicies:antoinetest] - permission denied (error code bin: 1296,)
hex: 0 x 510)anyone has a solution, explanation or something else?
Thanks for your helpJust a thought... try to leave the setting for the whole of the policy (where you "MyPolicies") with the null value
Didn't call it via the API only used in an orchestration and I know that this parameter is optional in general... required if policy is in a defined strategy and optional if it isn't.
-
Cisco ise 1.3 How to import an exported strategy game
Hi all
How can be imported a strategy that I exported in the past of the export strategy page? I can't find a solution.
any help appeciated.
You can not, this export function is only intended to be used for sending to TAC
-
We want to create a set of policies that strikes on a group of identity of the endpoint. A group of identity of endpoint contains a bunge mac address which we can filter with match user name of RADIUS that work very well for a shot of the seller.
Done, someone has an idea of possible?
You cannot create a matching condition "Strategy" based on a group of identity of the endpoint. You must choose one of the available attributes. For example, you can match against a group of n or WLAN ID. Once inside the 'strategy', you can create different authentication and authorization rules that may refer to a group of endpoint.
I hope this helps!
Thank you for evaluating useful messages!
-
Redirect WLC Web Auth URL point to a strategy ISE only NŒUD?
Hi all
I was wondering if the Auth Web configured in the WLC redirect URL can only point to a knot of ISE Persona in politics so the portal (see below) in the ISE is active only when the device of ISE is this active political figure.

It is called
Political character of Services
and the node is called
Policy Services node (PSN) (if there is no other character set on the node).
I would say that your assumption is right. The character of the Administration and supervisory personnel are not able to host the portal my devices.
-
Strategy of the ISE, DACL and VLAN change together
So I had a hard time finding consistency in a policy that changes the VLAN and applies to a DACL. Originally, I discovered that the remarks were causing to ruin. But I can't find any consistency. Can I use vanilla ' oermit all ' DACL to ISE, as well as a change VLAN and it just doesn't work. My AuthZ is very simple... If you are wired_MAB and your point of endpoints in a particular group, then apply a policy that changes the VLAN and applies to a DACL. This seems like it was originally what ISE is supposed to do, but it seems so buggy. Strange thing is that if I change VLAN by itself, it works. But when I add to the DACL does not work either. Anyone have any ideas why this is?
Your main problem, will probably be with assignment of DACL, which requires the switch to know the ip address of the client, before any list DACL will apply, at least in host multi-auth mode, I know a "bug", where analysis of device does not work yet once you change your local network virtual access initial port to another virtual LAN and try to apply a DACL using the validation of the MAB When this fails, try to check your schedule of ip device, and see if you hit the same "bug" is I've touched before. You should see this device analysis think that your device still has the original investigation period vlan or none at all. Remember that DHCP Snooping is also used to fill the device-tracking table, so make sure you use it also. Other than that, you could try mode closed, but that if them run could not be suitable for your environment.
-
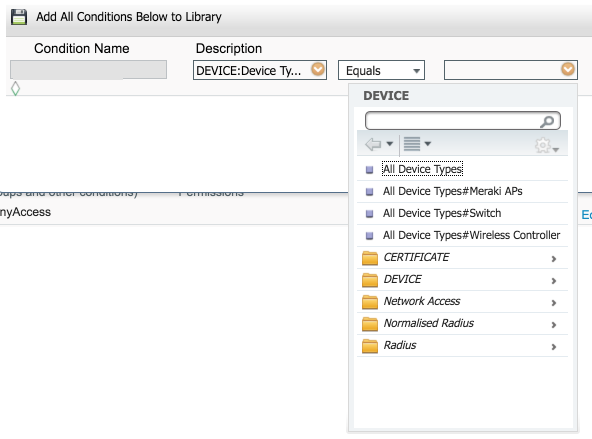
I am very new to Cisco ISE and Meraki. I try to get the Radius configuration for wireless authentication. When I do a test of the Meraki to ISE, it passes.
When I try to connect from my laptop, I look at the logs of the Radius and it passes; However, it does not connect me to good policy. I keep hitting the default policy. I have my Meraki police above the default policy in the strategy defined in article. I have attached what looks like my strategy game.
Devices does not really matter. Here is what I see when I create a device group (where you add the access point to this group), and then create the condition:
And here is where I create the condition of strategy game and you should be able to select the Meraki access points:
This will give you the condition similar to what I posted above. This is perhaps why you aren't hit that is not matching the condition for this game.
-
ISE foreign CWA / deployment WLC - missing user of anchor names
I'm not sure if this belongs to the section mobility or security - I'll just give it a try here.
I've set up wireless access visitor with Cisco ISE 1.3 (patch 2) and a stranger WLC / anchor of deployment (7.6.130.0).
So far almost everything works fine - but I probably have a problem with logging Cisco ISE.In exploitation forest 'authentications Live', I see the authentication successful, but the identity of the column, it shows just the MAC address of endpoint.
If navigation to the identity store of endpoint endpoint of comments is in the right group (guestendpoints) and when you look at the details of the endpoint, I can see the "portalusername" who created the user.If I click on endpoints active view (see attachment), I can see all active clients (Authz profile "PermitAccess"). I guess the user name of the client must be filled out there as well, no?
Someone has an idea what is the cause for this? Or is the normal behavior?
My rules of authentication are:
If "wireless_mab" and "RADIUS: Called-Station-ID ENDS WITH comments-SSID" then use "endpoints internal" and continue if "user not found".My authorization rules are:
1.) if GuestEndpoints AND (Wireless_MAB AND RADIUS: Called-Station-ID ENDS_WITH Guest SSID) then PermitAccess
2.) if (Wireless_MAB AND RADIUS: Called-Station-ID ENDS_WITH Guest SSID) then GUEST_WEBAUTH
The profile GUEST_WEBAUTH Authz defined the CWA and preauthentication ACL for the WLCThe WLC I just configured the WLC foreign with the RADIUS (ISE) server and active authentication MAC the SSID.
All parameters such as aaa-override and RADIUS of the NAC are defined. The defined RADIUS is set on "settler" to comply with the ISEAccording to my experience, this is the expected behavior. The new workflow for the use case of comments starting at the point 1.3 of the ISE typically includes registration of endpoint, you're. Your strategy for authz for post-portail of authentication (after the certificate of authenticity) needs the MAC address to use as the identity for permissions invited, not the guest credentials used on the portal.
That being said, I would like to be able to see the username of the user portal whenever a registered endpoint point authenticates (until it is served using endpoint political purges, of course).
Tim
-
Change of ISE of the VLAN for wireless settings
Hello
I configured on ISE posture strategy for posture compliant and noncompliant to endpoints, such that endpoints compliant posture will fall in VLAN clean and not conform will fall in others.
Now, my question is, even if an end point is consistent, it is not in VLAN own posture. To get the ip address of VLAN, it requires enough ipconfig and ipconfig / renew to do manually.
How to solve the problem...
Kind regards
Aditya
If you assign a VLAN, the final step for the PC client to renew its IP address. This step is performed by the portal of reviews for Windows clients. If you have not defined a VLAN for the 2nd AUTH rule earlier, you can skip this step.
If you have assigned a VLAN, complete the following steps to enable the renewal of the IP:
- Click Administration, and then click comments.
- Click settings.
- Expand comments, and then expand Configuration multi-portail.
- Click DefaultGuestPortal or the name of a custom portal that you created.
- Click the DHCP Release VLAN check box.
Maybe you are looking for
-
Query data from computer network Analyzer RSZVB
Hello. Sorry for the inconvenience. I would like to ask u about the data. I have download RSZVB example of measurement in LABVIEW on site of Rohde & Schwarz. Then, data were not included in the graph. The connection that I used is the LAN cable. Or f
-
Have to use manual loading paper
ALL OF A SUDDEN A FEW WEEKS AGO, MY AUTOMATIC PAPER FEED WILL NOT WORK. WHEN I WANT TO PRINT, I HAVE TO PUSH THE MANUAL PAPER FEED. I TRIED TO RESTART, BUT IT WILL NOT WORK. WHAT SHOULD DO? THANKS, PEGGY
-
HP Officejet Pro 8600 N911a: HP Officejet Pro 8600 N911a - Print when Fax is not saved
Can I do so a fax is printed when it is not registered? I know that I can put to print and save every time, but I trust HP digital fax to save paper. If a fax is not registered, either because of a network error, or if the computer that logs usually
-
Play sounds simultaneously through internal and external speaker
I am using Windows 7 on my laptop. I want the sound to play through the computer laptop internal speakers but also external device to THE (such as headphones or additional speakers) to get some sort of effect surround sound. I know it's physically po
-
Impossible to reinstall silverlight
Original title: installation of silverlight Impossible to reinstall silverlight after uninstalling it. Tried to solve the problem through Microsoft's Web site (they offer to fix it automatically). Did not work.