ISE and AAA configuration
Hi guys,.
I use that one server as primary and cisco ISE says there (ACS + NAC) features. I want to activate the AAA on the box rightnow ISE services.
I used the ACS earlier and you want to configure the same functions in this regard.
Authentication of devices in ISE when remote login for switch/router/firewall.
Authorization of the form controls what ISE based on the user login
Posting the details of command and connection and disconnection from the user.
I have very basic knowledge of ISE but I used ACS througly.
Please help in the question above.
Thanks in advance
Concerning
You've probably used GANYMEDE + with your ACS; You cannot migrate this functionality to ISE does not support the ISE GANYMEDE +. You must take the device admin stuff on GBA.
Tags: Cisco Security
Similar Questions
-
Hi all
I have a problem to install ISE and ACS on VM server. Linux Redhat Enterprise is detected by the system when the iso file is selected.
But some dependencies of the package are noticed as openssl kernel-devel or cisco...
The installation will stop from print virtual daemon.
Any help!
OK, I recommend:
1. check that all the VM gusts are configured to meet the required specifications (RAM, CPU, disk space, etc.)
2 re - download the ISO file and try the installation again
3. download and try OVA
Let us know how it goes :)
Thank you for evaluating useful messages!
-
I am very new to Cisco ISE and Meraki. I try to get the Radius configuration for wireless authentication. When I do a test of the Meraki to ISE, it passes.
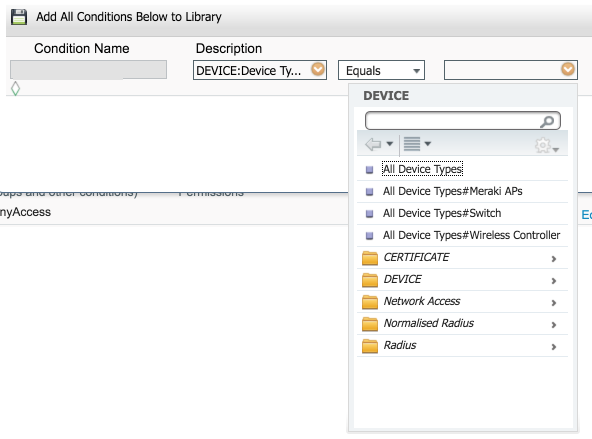
When I try to connect from my laptop, I look at the logs of the Radius and it passes; However, it does not connect me to good policy. I keep hitting the default policy. I have my Meraki police above the default policy in the strategy defined in article. I have attached what looks like my strategy game.
Devices does not really matter. Here is what I see when I create a device group (where you add the access point to this group), and then create the condition:
And here is where I create the condition of strategy game and you should be able to select the Meraki access points:
This will give you the condition similar to what I posted above. This is perhaps why you aren't hit that is not matching the condition for this game.
-
1.2 of the ISE and made maximum PSN supported in my Persona config
Hello people, I am setting up a way large-scale distributed of ISE and I was wondering if anyone could tell me what the maximum number of PSN is allowed in this configuration. I was reading through an older training document with version 1.1 and suggested 5, that's why I wonder if the specs changed on 1.2 but I can't find them anywhere to practice.
I have a large virtual machine running the MAIN admin character who is also secondary to my report & follow-up in my main data centre.
In another State (bound to 10G) is another large VM acting as my character high school admin with primary oversight & reports.
Across several States I want to have multiple Ssnp through geographic patterns of each State, but I don't know if I can put across enough with my current version of 1.2 and my persona config Ssnp listed above. I need about 12 to 15 Ssnp.
I was wondering if I need two VMs more out of my control as a node in DC1 and secondary surveillance in DC2 for more extensibility PSN.
Any help would be greatly appreciated.
-Thank you
As Marvin suggested, I would look at using 1.3 at this point, unless you have any specific concerns of this version and I really want to stay with 1.2. That being said, here are my recommendations/comments:
-Two v1.2 and v1.3 fits in fact up to 40 knots PSN
-If none of the nodes of your PSN will be put in the same place and are layer 2 adjacent I recommend putting them in a group node and behind a load balancer. If you do not have a load balancer, I would always put them in a node group. At this time a node group can have up to 10 PSN
-If you have 10-15 knots PSN then you should spend 2 nodes for specifically for the character of monitoring
-The period of maximum round trip between all nodes must not exceed 200 ms
For more information, you can always reference the "Network deployment" section in the installation guide material for ISE:
v1.3
v1.2
http://www.Cisco.com/c/en/us/TD/docs/security/ISE/1-2/installation_guide/ise_ig/ise_deploy.html
Thank you for evaluating useful messages!
-
Cisco ISE and WLC Access-List Design/scalability
Hello
I have a scenario that wireless clients are authenticated by the ISE and different ACL is applied depending on the rules in the ISE. The problem I have seen is due to the limitation on the Cisco WLC that limit only 64 input access list. As the installer has only a few IVR/interfaces and several different access lists are applied to the same base on user groups interface; I was wondering if there may be an evolutionary design / approach according to which the access list entries can evolve next to create a vlan for each group of users and apply the access list on the interface of layer 3 instead? I illustrated the configuration below for reference:
Group of users 1 - apply ACL 1 - on Vlan 1
User 2 group - apply ACL 2 - on the Vlan 1
3 user group - apply ACL 3 - on the Vlan 1
The problem appears only for wireless users, he does not see on wired users as the ACLs can be applied successfully without restriction as to the switches.
Any suggestion is appreciated.
Thank you.
In fact, you have limitations on the side of the switch as well. Long ACL can deplete resources AAGR of the switch. Take a look at this link:
The new WLCs based on IOS XE and not the old OS Wireless/Aironet will provide the best experience in these matters.
Overall, I see three ways to overcome your current number:
1. reduce the ACL by making them less specific
2 use L3 interfaces on a switch L3 or FW and the ACL is applied to them
3. use the SGT/SGA
I hope this helps!
Thank you for evaluating useful messages!
-
I am AAA configuration. I'm setting up a router so that when users access using the vty line, they must be authenticated by Active Directory. I configured AAA on the router and on Microsoft Windows Server 2003 IAS. But when I type 'test group aaa AUTH administrator legacy xxxxxxx' it gives the following error
Test of authentication attempting AUTH server group using RADIUS
* 01:01:04.991 Mar 1: AAA: analyze IDB name =
type =-1 ATS = - 1 * 01:01:04.991 Mar 1: AAA/MEMORY: create_user (0x6417FF80) = user tweak "Administrator" = "NULL" ds0 = 0 port = "rem_addr = 'NULL' = ASCII service CONNECTION priv = authen_type = 1 initial_task_id = '0', vrf = (id = 0) no answer authoritative of any server.
RTR #.
* 01:01:23.647 Mar 1: RADIUS-4-RADIUS_DEAD %: 172.16.1.243:1812, 1813 RADIUS server does not respond.
* 01:01:23.655 Mar 1: AAA/MEMORY: free_user (0x6417FF80) = user tweak "Administrator" = "NULL" port = "rem_addr = 'NULL' = ASCII service CONNECTION priv = authen_type = 1 vrf = (id = 0)
* 01:01:23.655 Mar 1: RADIUS-4-RADIUS_ALIVE %: 172.16.1.243:1812, 1813 RADIUS server is marked in life.
I also used the default ports for authentication, but still no use. I am able to ping router radius server and can ping router of the radius server.
The Radius in VMWARE Server installed on and the router is emulated in Dynampis.
Here is the configuration of the router
RTR #sh run
Building configuration...
Current configuration: 863 bytes
!
version 12.4
horodateurs service debug datetime msec
Log service timestamps datetime msec
no password encryption service
!
hostname RTR
!
boot-start-marker
boot-end-marker
!
!
AAA new-model
!
!
RADIUS AAA server AUTH group
ACCT-port of the server 172.16.1.243 auth-port 1812 1813
!
RADIUS authentication AUTH of AAA connection group.
!
AAA - the id of the joint session
memory iomem size 5
!
!
IP cef
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
!
interface Loopback1
no ip address
!
interface FastEthernet0/0
IP 172.16.1.241 255.255.255.0
automatic duplex
automatic speed
!
IP http server
no ip http secure server
IP route 0.0.0.0 0.0.0.0 172.16.1.1
!
!
!
radius of the IP source interface FastEthernet0/0
!
!
RADIUS-server host 172.16.1.243 auth-port 1812 acct-port 1813 key xxxxx
!
control plan
!
!
!
!
!
!
!
!
!
!
Line con 0
line to 0
line vty 0 4
authentication of connection AUTH
!
!
end
Do you see any hits on the 2003 event logs? If no request is not the RADIUS.
Do not forget that dynampis some time shows abnormal behavior. Since you are able to ping, then connectivity seems to be just fine here.
Check the shared secret key and make sure that the radius ports are open, check to see if there is a firewall between the two.
Kind regards
~ JG
-
Hi all
Im trying to get my head around the use of 3d party certificates with the ISE and I think that I need advice here.
I have a setup of 6 knots ISE, 2xAdmin, 2xMonitoring and 2xPolicy.
All the these have the abc.local domain name.
I want to use MS-CHAPv2 and customer service without certificate error.
So I register all my six knots with some 3d CA? Or only the nodes 2xPolicy?
I know that the best solution would be the six, but just to know if it is possible.
How to work around the problem with .local? I don't think that it is possible to get a certificate with .local as a domain in the FULL domain name.
Is that useful here of SAN certificates? How would look (even .local in CN..?)
Other things to consider in the present?
concerning
Mikael
That's right, that you must issue the CSR based on the currently configured for ise host name that corresponds to the fqdn.
Your problem is that the public certificate authorities will not issue you a cert because you use a .local and not a public domain such as .com, .edu or .org to name a few.
The only way to solve your problem is to use a Microsoft private certification authority that is simple to configure. Or change your area om ise and use the public domain of your company name.
Thank you
Sent by Cisco Support technique iPad App
-
Where can I find the 'graphic moment and trigger Configuration vi '?
Where can I find the professional tool #5: NOR-DAQmx graphic timing and trigger Configuration vi. It is discussed here http://www.ni.com/white-paper/3697/en/ but the link for download is broken.
Is that what you are looking for?
http://www.NI.com/example/28285/en/
Check out the docs llb and Word attached on the left.
-
Backup and managing configurations on ONS 15454 devices
We have a lot of ONS 15454 and CiscoWorks LMS 4 apparently does not support these devices (I can't pick the cards ML1000 configurations or configs of chassis).
Can I save the configurations of the STC cards/chassis using the CTC? I see a backup option of database under maintenance contract, but I'm not entirely of this make. Basically, I want to assure you that if one of these devices suffers a hardware failure, I have backups of the way in which the circuits are provided.
Is there a better tool to use?
Any advice would be great
For nodes to backup through the CTC, the Cisco ONS 15454 procedure Guides describe the steps to be taken to save the nodes (section below the latest version is:)
Cisco Transport Manager is a management system of item available for the largest optical networks and has features to back up the databases of several nodes.
=========
NTP-A108 back up the database
Goal
This procedure saves a backup version of the TCC2/TCC2P (software) database on the workstation running Cisco transport (CTC) controller or a network server.
Tools/equipment
None
Pre-trial proceedings
None
Required / have required
Mandatory. Cisco recommends to perform a backup of database at intervals of about a week and before and after configuration changes.
Onsite / remote
On-site or remotely
Security level
Maintenance or higher

Note
 You need to back up and restore the database for each node on a path of the circuit in order to maintain a complete circuit.
You need to back up and restore the database for each node on a path of the circuit in order to maintain a complete circuit.
Note
 The following settings are not backed up and restored: node name and Internet Inter - ORB Protocol (IIOP) port. If you change the name of the node and restore a backup of a database with a different node name, the circuits map to the new node name. Cisco recommends keeping a record of the old and new node names.
The following settings are not backed up and restored: node name and Internet Inter - ORB Protocol (IIOP) port. If you change the name of the node and restore a backup of a database with a different node name, the circuits map to the new node name. Cisco recommends keeping a record of the old and new node names.Step 1
 Complete the "DLP-A60 Log into CTC" task at the node that you want to back up. If you are already connected, go to step 2.
Complete the "DLP-A60 Log into CTC" task at the node that you want to back up. If you are already connected, go to step 2.Step 2
 Click it maintenance > Database tabs.
Click it maintenance > Database tabs.Step 3
 Click on backup.
Click on backup.Step 4
 Save the database on the hard drive of the workstation or network storage. Use a file name with the extension of .db file. for example, database.db.
Save the database on the hard drive of the workstation or network storage. Use a file name with the extension of .db file. for example, database.db.Step 5
 Click Save.
Click Save.Step 6
 Click OK in the confirmation dialog box.
Click OK in the confirmation dialog box.Stop. You have completed this procedure.
-
ISE and AirWatch MDM integration
I have been using ISE with the integration of AirWatch for over a year. Recently, it seems that AirWatch has updated their certificates and now I can't get ISE and AirWatch to communicate. I can access the AirWatch API URL through a browser, and I see that the browser uses TLS 1.2. According to TAC, Cisco, ISE does not support TLS 1.2. I have cases open with two TACS, but have yet to find a resolution.
Someone at - it ISE / Airwatch integration currently work?
Wes,
I have a client who had what sounds like the same issue. It came down to AirWatch change the host he was using. It was a long journey to get to the right answer but when AirWatch changed host, things started working again. It took several calls with AirWatch until someone had the idea to make this change.
Hope that helps.
Tim
-
I have a client that 5508 WLCs runs through the area, and I'm catching IEEE802.1x authentication for the enterprise WLAN and WebAuth for WLAN of comments... they PSK now :(
They have ad and ISE and NAC great interest, so my immediate thoughts are to integrate ISE AD and use ISE as RADIUS server for .1x on the WLC. Then use the WLC and ISE do WebAuth for comments... It's all of the standard stuff, but it gives the background.
Now, we come to the interesting bit... they want to run BYOD. They are involved in the financial markets, so the BYOD must be tightly controlled. They ask on ISE coupled with the NAC, but I am not convinced that I need the NAC since the arrival of the ISE1.3. Of course, I will examine three (min) SSID, corporate knowledge, comments and BYOD, just logically distinct. I have nothing that ISE 1.2 cannot press the company and comments but BYOD must full profiling and reclamation prohibition or device before access to the net.
Someone at - he comments or suggestions? Is ISE 1.3 enough NAC-like that I don't need more, or if this is not the case, what additional benefits does that ISE can support
Thanks for your advice/comments/experiences
Jim
Hi Jim -.
Version 1.3 offers an integrated PKI and a significantly improved services reviews experience. The internal PKI is nice if the customer does not have a PKI solution in place. Don't forget however that the PKI ISE internal can only issue certificates to BYOD devices which have boarded through the ISE BYOD "flow", you cannot use the ISE PKI to issue certificates to computers in the domain.
With regard to the NAC: you need to specify exactly what is needed here. If you were to make "posture assessment" then ISE can do for machines based on Windows and OSX. You can check for things like: A / V, a/s, status of the firewall, Windows hotfixes. If you want to make the posture on mobile devices, so you will need to integrate ISE with MDM (mobile device management) solution such as: Airwatch, Mobile, Extend360 iron, etc. ISE may question the MDM for things like: the device is protected with a PIN, is the rooted device, is the encrypted device, etc.
I hope this helps!
Thank you for evaluating useful messages!
-
Difference between ISE and NAC?
Dear all,
Can you please help to understand difference ISE and NAC?
Thank you
Eve.
ACS + NAC Profiler + comments the NAC + Manager = EHT NAC NAC Server
ISE does:
Centralized strategies
RADIUS server
Evaluation of posture
Guest access services
Profiling feature
MDM
Monitoring
Troubleshooting
Reporting -
Profilinh ISE and Thin Clients
I have 1.2 ISE and HP T610 customer light on the network
802.1 x authorization works correctly, but clients are looming as HP-devices generics or HP printers
I don't know how to create a strategy profiling custom for device "HP Thin Client.
What conditions YES to assign customers HP T610?
Thanks in advance,
Vice
Refer to the Profiler service to power down
Profile services food application for permit in advance
-
ISE and WLC for sanitation of the posture
Please can someone clarify a few things regarding the ISE and posture wireless.
(1) is the ACL-POSTURE-REDIRECT used for conversion, or is it just an ACL to redirect some of the posture of the kickoff checking traffic?
(2) can / a dACL/wACL list must be specified as a sanitation ACL?
(3) the WLC ACL should be written in long format (manually specify source and dest ports/doesny direction any job?)
(4) does anyone have working example ACL for redirect (CPC) posture and sanitation (dACL)?
(5) any other advice or pointers would be as useful as any docs I have found so far, what he TrustSec2, CiscoLive or anything else, do not seem to help me understand sanitation and WLC posture
Thank you
Nick
Yes,
This means that strategy available to your customer does not have a rule that will correspond to an entrepreneur who joined the network. Can you post a screenshot of the provisioning of customer policy?
Thank you
Tarik Admani
* Please note the useful messages *. -
Hello all - I'm working with a client on a deployment of the ISE and that they would like remote locations enjoy to dot1X. The potential problem I see is - what - they have ASA5505s for the tunnels to the main location, which is great, but they also use the integrated... switch I know there are problems with the largest ASAs requiring the IPN. I wonder if they will need a different switch to make it work? Don't think they plan on posture or whatever it is advanced. More just to lock the switchports and avoid problems when people plug random devices to keep them out of the network...
any suggestions are appreciated.
Scott J.
Scott,
If you are referring to the ports on the SAA, these are not supported dot1x. You will need a switch different in order to get this dot1x features you're looking for.
Thank you
Tarik Admani
* Please note the useful messages *.
Maybe you are looking for
-
[SOLVED] Impossible to uninstall TopArcadeHits extension?
I downloaded something download [dot] com (I'm not typing the address because I don't want anyone to link there without adequate warning). I looked and did * everything * I've found to remove this extension. MMFA, Spyware Terminator, Windows Defender
-
HP Envy 120: HP Envy 120 work removes
I have a printer HP Envy 120 - there is a print job in the queue that will delete not (even if the status shows deleting) and nothing that I send now will print. I restarted computer and printer, but nothing works.
-
'New' application iBooks will not transfer pdf to iPad files
OK, people, I'm just an order of jacked-up at McDonald's away from a stroke... When I went to sync my iPad this morning, I found adding .pdf files to my library on 'Books' iTunes no longer works, because Apple has placed all these reading materials i
-
[Help please] Intel AC radio went with the new driver.
Someone knows how to solve this problem: http://oi59.Tinypic.com/dwqcuh.jpg
-
Ive ripped songs show different work when transferred to a portable device
songs ripped from my own cd collection Ive see the same work from one of my CD not the one I recently ripped and then tried to sync