ISE Corp. Internet access static user authentication
Hello gentlemen,
I have a small question on the type of authentication that I can use for the CORP users who want to access Internet & some in-house applications on their Android devices and they should not be re - authenticate when they move between sites to connect to the same SSID when they film in different sites.
The configuration looks like below: -.
USER (needs static auth to move between sites)--> SSID--> WLC--> ISE (common to all sites)
Please can you suggest the best way for users to type Android with name of user and password similar authentication when they move in different sites.
Thank you
D
Hello
you have 2 choices:
-users log on SSID using their Active Directory/LDAP credentials. Once they connect, credentials are stored on their devices, and they will be able to reconnect without repeating the authentication.
-make BYOD, this means you force, was the first connection, users to enroll a certificate. More secure solution. In reality, they authenticate the 1st time with their powers AD/LDAP and before obtaining access, they will be popup to a web portal to register their devices.
the 1st solution requires only basic licenses and 2nd requires MORE licenses. Basic license, have to buy you them once that's all. As well, it is the licence renewal (1y, 3y and I think more than 5 years).
on deployments, than I do today, companies prefer the use of certificates from the user/password and the server certificate is ISE. In this case, you are not related to the systems guys, and if something is compromised, you can manage the revocation of certificate directly to the LSE instead of ask a person to system to disable the user account on AD.
hope this is clear.
Thank you
PS: Please do not forget to rate and score as good response if this solves your problem
Tags: Cisco Security
Similar Questions
-
How to give a limitation of internet access to users via gpedit.msc?
How to give a limitation of internet access to users via gpedit.msc
Hello
Follow the below mentioned article:
How to use the Group Policy Editor to manage the Local computer policy in Windows XP: http://support.microsoft.com/kb/307882
-
How to block internet access to users on the local computer. The machine is sub domain control.
How to block internet access to users on the local computer and the machine is in sub domain control.
Hello
Thanks for posting your query in Microsoft Community.
Your question is beyond the scope of what is generally answered in this forum of consumer and would be better suited for the IT Pro TechNet public.
Please post your question in the TechNet Forums.
-
ASA 5505 - order Internet access for users
Hi all
I have a Cisco ASA 5505 connect my LAN over the internet using NAT/PAT. I want to restrict access to the internet on ports 80 and 443 on a per user basis.
That is to say access to management staff while limiting the general staff.
I understand how this on a per device level by creating an access list to block certain IP addresses to the internet, but I would limit some users.
I guess they will have to authenticate to the ASA some how.
Pointers?
TIA.
You need to set up the Cup via proxy in ASA.
Here is the configuration that we add on ASA:-
access-list WEBAUTH permit tcp any any eq 80
access-list WEBAUTH permit tcp any any eq 443
AAA authentication WEBAUTH indoor soccer match
AAA authentication secure-http-client
AAA authentication listener http inside port www redirect
Redirect the AAA authentication listener https within the https port
http://www.Cisco.com/en/us/docs/security/ASA/asa72/configuration/guide/fwaaa.html#wp1043431
http://www.Cisco.com/en/us/docs/security/ASA/asa72/command/reference/a1_72.html#wp1437427
Kind regards
~ JG
Note the useful messages
-
Separation of monitor only and Admin for Cisco ASDM (ASA) access for users authenticated via LDAP
Hello
We have two groups of ads on network Admins, one for the system administrators group. The network Admins will get Priv lvl 15 the other Priv lvl 3.
This is the setup I use:
TestASA # sh run ldap-attribute-map of test4
Comment by card privileged-level name
map-value comment fw - ro 5
map-value comment fw - rw 15
memberOf IETF Radius-Service-Type card name
map-value memberOf "cn = s-FW-Admin, OR = security groups, DC = 802101, DC = local" 6
map-value memberOf "cn = s-fw-ro, OR = security groups, DC = 802101, DC = local" 5The user in both groups can connect ssh and asdm but all users get the same rights priv lvl 15.
Someone at - it an idea?
You must visit the listed link below to configure ASA to only read access and access admin. not sure, if you have already been there.
https://supportforums.Cisco.com/docs/doc-33843
~ BR
Jatin kone* Does the rate of useful messages *.
-
PSE10 - how to get help online on PC without Internet access?
Hello
Our company bought several licenses of Photoshop Elements 10 and I would like the installation of packages in order to be able to install it with SCCM (formelly named SMS) on PC.
The question we have is that the PC in our society do not have Internet access, so users cannot, after the installation, download the online help... and since there is currently not out included help, it means that they have no help at all.
Can you let us know where the aid in question is copied when it is downloaded, so that our packaging team will be able to download these files from a PC with Internet access, then add them together, so that our users will be able to read the help (F1), even if they have no Internet access?
Thanks a lot for your answer
Yes you can do so by changing the settings in the Adobe help Manager
Open Adobe Help.exe location: c:\program files (x 86) \Adobe\Adobe help
Then in the prefrences download section, you can select the products you want to get offline help
In the update section select manually
In the section "local content": select the product, and then click UPDATE
When using offline is downloaded, and then in the general section, select Yes (this will make the default value of local aid)
Now if you can switch to offline mode and press F1 in the program, it will open local help
It could be useful!
-
Unable to share internet access among the accounts of users in the same computer
Hello
I have bsnl connection broadband through beetel 110tc1 adsl2 modem + router connected through administrator account. the computer has also other user accounts of my son, but he is not able to connect because the computer does not display this connection. BSNL engineers are of no use to solve the problem - please help. the accounts were created as it contributes to the protection of the computer, but the purpose is defeated if the internet is accessible from the admin account.
Thank you
Hi Johanna,.
I understand that some user accounts on the PC has no Internet connection. Please correct me if I'm wrong.
1. What is the exact error message you get when you try to access Internet from your son's account?
2. what exactly do you mean by "sharing internet acsess between user accounts?
3. the other user accounts appear under a Standard account?
Please create a new user account and let us know if you are able to connect to the Internet.
Create a user account
http://Windows.Microsoft.com/en-in/Windows/create-user-account#create-user-account=Windows-7Let us know the result, we will be happy to help you.
-
No internet access through VPN
Hi, I have the router Cisco 881 (MPC8300) with c880data-universalk9 - mz.153 - 3.M4.bin when users establish a VPN connection to the corporate network, had access to all the resources but no internet access, please help me what else I need to configure to achieve my goal. I don't want to split the tunnel, internet via VPN, users must have. In my opinion, I have put an additional configuration for NAT, but my router not recognize u-Turn and NAT commands on the object on the network.
My config:
Building configuration...
Current configuration: 13562 bytes
!
! Last configuration change at 09:52:38 PCTime Saturday, May 16, 2015, by admin
version 15.3
no service button
horodateurs service debug datetime msec
Log service timestamps datetime msec
no password encryption service
!
XXX host name
!
boot-start-marker
start the flash system: c880data-universalk9 - mz.153 - 3.M4.bin
boot-end-marker
!
!
logging buffered 51200 warnings
!
AAA new-model
!
!
AAA authentication login default local
AAA authentication login ciscocp_vpn_xauth_ml_1 local
AAA authentication login ciscocp_vpn_xauth_ml_2 local
AAA authorization exec default local
AAA authorization ciscocp_vpn_group_ml_1 LAN
AAA authorization ciscocp_vpn_group_ml_2 LAN
!
!
!
!
!
AAA - the id of the joint session
iomem 10 memory size
clock timezone PCTime 1 0
PCTime of summer time clock day March 30, 2003 02:00 October 26, 2003 03:00
!
Crypto pki trustpoint TP-self-signed-1751279470
enrollment selfsigned
name of the object cn = IOS - Self - signed - certificate - 1751279470
revocation checking no
rsakeypair TP-self-signed-1751279470
!
!
TP-self-signed-1751279470 crypto pki certificate chain
certificate self-signed 01
XXXX
!
!
Protocol-IP port-map user - 2 tcp 8443 port
user-Protocol IP port-map - 1 tcp 3389 port
!!
!
!
IP domain name dmn.local
8.8.8.8 IP name-server
IP-server names 8.8.4.4
IP cef
No ipv6 cef
!
!
license udi pid CISCO881-K9 sn FCZ174992C8
!
!
username privilege 15 secret 5 xxxx xxxx
username secret VPNUSER 5 xxxx
!
!
!
!
!
!
type of class-card inspect sdm-nat-user-protocol--2-1 correspondence
game group-access 105
corresponds to the user-Protocol - 2
type of class-card inspect entire game SDM_AH
match the name of group-access SDM_AH
type of class-card inspect entire game PAC-skinny-inspect
Skinny Protocol game
type of class-card inspect entire game SDM_IP
match the name of group-access SDM_IP
type of class-card inspect entire game PAC-h323nxg-inspect
match Protocol h323-nxg
type of class-card inspect entire game PAC-cls-icmp-access
match icmp Protocol
tcp protocol match
udp Protocol game
type of class-card inspect entire game PAC-h225ras-inspect
match Protocol h225ras
type of class-card inspect entire game SDM_ESP
match the name of group-access SDM_ESP
type of class-card inspect entire game PAC-h323annexe-inspect
match Protocol h323-annex
type of class-card inspect entire game PAC-cls-insp-traffic
match Protocol pptp
dns protocol game
ftp protocol game
https protocol game
match icmp Protocol
match the imap Protocol
pop3 Protocol game
netshow Protocol game
Protocol shell game
match Protocol realmedia
match rtsp Protocol
smtp Protocol game
sql-net Protocol game
streamworks Protocol game
tftp Protocol game
vdolive Protocol game
tcp protocol match
udp Protocol game
type of class-card inspect the correspondence SDM_GRE
match the name of group-access SDM_GRE
type of class-card inspect entire game PAC-h323-inspect
h323 Protocol game
type of class-card inspect correspondence ccp-invalid-src
game group-access 103
type of class-card inspect entire game PAC-sip-inspect
sip protocol game
type of class-card inspect correspondence sdm-nat-https-1
game group-access 104
https protocol game
type of class-card inspect all match mysql
match the mysql Protocol
type of class-card inspect correspondence ccp-Protocol-http
http protocol game
type of class-card inspect entire game CCP_PPTP
corresponds to the SDM_GRE class-map
inspect the class-map match PAC-insp-traffic type
corresponds to the class-map PAC-cls-insp-traffic
type of class-card inspect entire game SDM_EASY_VPN_SERVER_TRAFFIC
match Protocol isakmp
match Protocol ipsec-msft
corresponds to the SDM_AH class-map
corresponds to the SDM_ESP class-map
type of class-card inspect correspondence ccp-icmp-access
corresponds to the class-ccp-cls-icmp-access card
type of class-card inspect the correspondence SDM_EASY_VPN_SERVER_PT
corresponds to the SDM_EASY_VPN_SERVER_TRAFFIC class-map
!
type of policy-map inspect PCB - inspect
class type inspect PCB-invalid-src
Drop newspaper
class type inspect mysql
inspect
class type inspect PCB-Protocol-http
inspect
class type inspect PCB-insp-traffic
inspect
class type inspect PCB-sip-inspect
inspect
class type inspect PCB-h323-inspect
inspect
class type inspect ccp-h323annexe-inspect
inspect
class type inspect ccp-h225ras-inspect
inspect
class type inspect ccp-h323nxg-inspect
inspect
class type inspect PCB-skinny-inspect
inspect
class class by default
drop
type of policy-card inspect sdm-license-ip
class type inspect SDM_IP
Pass
class class by default
Drop newspaper
type of policy-card inspect sdm-pol-NATOutsideToInside-1
class type inspect sdm-nat-https-1
inspect
class type inspect sdm-nat-user-protocol--2-1
inspect
class type inspect CCP_PPTP
Pass
class class by default
Drop newspaper
type of policy-card inspect PCB-enabled
class type inspect SDM_EASY_VPN_SERVER_PT
Pass
class class by default
drop
type of policy-card inspect PCB-permits-icmpreply
class type inspect PCB-icmp-access
inspect
class class by default
Pass
!
safety zone-to-zone
security of the area outside the area
ezvpn-safe area of zone
zone-pair security PAC-zp-self-out source destination outside zone auto
type of service-strategy inspect PCB-permits-icmpreply
zone-pair security PAC-zp-in-out source in the area of destination outside the area
type of service-strategy inspect PCB - inspect
source of PAC-zp-out-auto security area outside zone destination auto pair
type of service-strategy inspect PCB-enabled
sdm-zp-NATOutsideToInside-1 zone-pair security source outside the area of destination in the area
type of service-strategy inspect sdm-pol-NATOutsideToInside-1
in the destination box source sdm-zp-in-ezvpn1 ezvpn-pairs area security
type of service-strategy inspect sdm-license-ip
source of sdm-zp-out-ezpn1 of security area outside zone ezvpn-zone time pair of destination
type of service-strategy inspect sdm-license-ip
safety zone-pair sdm-zp-ezvpn-out1-source ezvpn-zone of destination outside the area
type of service-strategy inspect sdm-license-ip
safety zone-pair source sdm-zp-ezvpn-in1 ezvpn-area destination in the area
type of service-strategy inspect sdm-license-ip
!
!
crypto ISAKMP policy 1
BA 3des
preshared authentication
Group 2
!
crypto ISAKMP policy 2
BA aes 256
preshared authentication
Group 2
!
Configuration group customer crypto isakmp Domena
key XXXXXX
DNS 192.168.1.2
Dmn.local field
pool SDM_POOL_1
Save-password
Max-users 90
netmask 255.255.255.0
banner ^ Cwelcome ^ C
ISAKMP crypto ciscocp-ike-profile-1 profile
match of group identity Domena
client authentication list ciscocp_vpn_xauth_ml_2
ISAKMP authorization list ciscocp_vpn_group_ml_2
client configuration address respond
virtual-model 1
!
!
Crypto ipsec transform-set esp - aes 256 esp-sha-hmac ESP_AES-256_SHA
tunnel mode
!
Profile of crypto ipsec CiscoCP_Profile1
game of transformation-ESP_AES-256_SHA
set of isakmp - profile ciscocp-ike-profile-1
!
!
!
!
!
!
!
interface Loopback0
IP 192.168.9.1 255.255.255.0
!
interface FastEthernet0
no ip address
!
interface FastEthernet1
no ip address
!
interface FastEthernet2
no ip address
!
interface FastEthernet3
no ip address
!
interface FastEthernet4
Description $ETH - WAN$ $FW_OUTSIDE$
IP x.x.x.x 255.255.255.248
NAT outside IP
IP virtual-reassembly in
outside the area of security of Member's area
automatic duplex
automatic speed
!
type of interface virtual-Template1 tunnel
IP unnumbered Loopback0
ezvpn-safe area of Member's area
ipv4 ipsec tunnel mode
Tunnel CiscoCP_Profile1 ipsec protection profile
!
interface Vlan1
Description $ETH_LAN$ $FW_INSIDE$
IP 192.168.1.1 255.255.255.0
IP access-group 100 to
IP nat inside
IP virtual-reassembly in
Security members in the box area
IP tcp adjust-mss 1452
!
local IP SDM_POOL_1 192.168.10.10 pool 192.168.10.100
IP forward-Protocol ND
IP http server
23 class IP http access
local IP http authentication
IP http secure server
IP http timeout policy slowed down 60 life 86400 request 10000
!
The dns server IP
IP nat inside source list 3 interface FastEthernet4 overload
IP nat inside source static tcp 192.168.1.3 interface FastEthernet4 443 443
IP nat inside source static tcp 192.168.1.2 8443 interface FastEthernet4 8443
IP route 0.0.0.0 0.0.0.0 X.x.x.x
!
SDM_AH extended IP access list
Note the category CCP_ACL = 1
allow a whole ahp
SDM_ESP extended IP access list
Note the category CCP_ACL = 1
allow an esp
SDM_GRE extended IP access list
Note the category CCP_ACL = 1
allow a gre
SDM_IP extended IP access list
Note the category CCP_ACL = 1
allow an ip
!
not run cdp
!
Note access-list 3 INSIDE_IF = Vlan1
Note CCP_ACL category in the list to access 3 = 2
access-list 3 Let 192.168.1.0 0.0.0.255
Note access-list 23 category CCP_ACL = 17
access-list 23 permit 192.168.1.0 0.0.0.255
access-list 23 allow 10.10.10.0 0.0.0.7
Note access-list 100 Auto generated by SDM management access feature
Note access-list 100 category CCP_ACL = 1
access-list 100 permit tcp 192.168.1.0 0.0.0.255 host 192.168.1.1 eq 22
access-list 100 permit tcp 192.168.1.0 0.0.0.255 host 192.168.1.1 eq www
access-list 100 permit tcp 192.168.1.0 0.0.0.255 host 192.168.1.1 eq 443
access-list 100 permit tcp 192.168.1.0 0.0.0.255 host 192.168.1.1 eq cmd
access-list 100 tcp refuse any host 192.168.1.1 eq telnet
access-list 100 tcp refuse any host 192.168.1.1 eq 22
access-list 100 tcp refuse any host 192.168.1.1 eq www
access-list 100 tcp refuse any host 192.168.1.1 eq 443
access-list 100 tcp refuse any host 192.168.1.1 eq cmd
access-list 100 deny udp any host 192.168.1.1 eq snmp
access ip-list 100 permit a whole
Note access-list 101 category CCP_ACL = 1
access-list 101 permit ip 192.168.1.0 0.0.0.255 any
Note access-list 102 CCP_ACL category = 1
access-list 102 permit ip 192.168.1.0 0.0.0.255 any
Note access-list 103 CCP_ACL category = 128
access-list 103 allow the ip 255.255.255.255 host everything
access-list 103 allow ip 127.0.0.0 0.255.255.255 everything
access-list 103 allow ip 93.179.203.160 0.0.0.7 everything
Note 104 CCP_ACL category = 0 access-list
IP access-list 104 allow any host 192.168.1.3
Note access-list 105 CCP_ACL category = 0
IP access-list 105 allow any host 192.168.1.2-----------------------------------------------------------------------
^ C
!
Line con 0
no activation of the modem
line to 0
line vty 0 4
access-class 102 in
transport input telnet ssh
line vty 5 15
access class 101 in
transport input telnet ssh
!
!
endI'd be grateful for help
concerning
Hello
Enter the subnet pool VPN to access-list 3 for source NAT
You may need to check the firewall also rules to allow the connection based on areas you
HTH,
Averroès
-
Cisco ISE 1.1.2.145 Admin authentication via the LDAP protocol
I have configured the LDAP protocol and able to retrieve our LDAP directory structure. Now, I'm trying to point authentication "Admin Access" Source 'External identity', which is the new LDAP IS I created. But I couldn't find an option to authenticate locally if for some reason the LDAP configuration does not work. I learned that the ISE can automatically return to local auth as external sources Idenitity are inaccessible. How can I test the LDAP authentication with breaking them our Admin Access? I thought to open two parallel sessions, one with Super Admin account Local and one with the domain account. But I noticed that ISE communication is smart enough for the closing session/connection no matter what other sessions in different browsers so, basically, I can't open two parallel sessions the same machine to test. Suggestions? or am I missing something here?
Thanks in advance.
Hi Srinivas,
Even if you configure LDAP as a source of external identity of admin access, you can always internal relief without having locked. According to the ISE user guide:
During the operation, Cisco ISE is designed to "fall back" and try to perform the internal identity database authentication, if the communication with the external identity store has not been established, or if it fails. In addition, whenever an administrator for which you have configured external authentication launches a browser and initiates a logon session, the administrator must still the option authentication of demand through the local Cisco ISE database by choosing 'Internal' to the Selector drop-down storage of identity in the Connect dialog box.
http://www.Cisco.com/en/us/docs/security/ISE/1.1/user_guide/ise_man_identities.html#wp1351543
Please see the attached screenshot by my lab ISE:
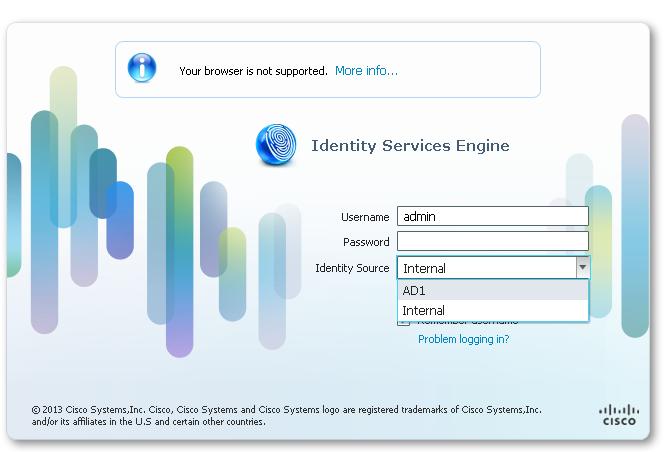
I configured the admin authentication against AD, but I still see both 'Internal' and 'AD' at the time of the connection.
I hope this helps.
Thank you
Aastha
-
How to restrict Internet access by using the RADIUS server via switch Catalyst 3560
Dear all,
I need a configuration using any. I have a small network of 15 users a 3560, which is in turn connected to a router ISR 2811. Interface fastethernet 0/24 switch 3560 I intend to connect to a unix based server RADIUS. ISP is connected on the opposite side of the 2811 to the fa0/0 interface.
I want to make is that if someone among the 15 users tries to access the internet, they must be validated in the RADIUS server by their pre-configured user credentials. (I'm going to store 15 user credentials here). If someone else tries to connect (except those 15) he or she should be denied internet access.
The RADIUS server will be having a login page to type the name of user and password.
Please guide based on what commands I should inject into the 3560 or what specifically, I need to have to run this task.
Thanks in advance!
Samrat.
I only did this in a very long time, but you probably want to do is activate the web authentication.
-
No Internet access after the connection of the cisco vpn client
Hi Experts,
Please check below config.the problem is vpn is connected but no internet access
on the computer after the vpn connection
ASA Version 8.0 (2)
!
ciscoasa hostname
activate 8Ry2YjIyt7RRXU24 encrypted password
names of
!
interface Ethernet0/0
nameif outside
security-level 0
IP 192.168.10.10 255.255.255.0
!
interface Ethernet0/1
nameif inside
security-level 100
IP 192.168.14.12 255.255.255.0
!
interface Ethernet0/2
Shutdown
No nameif
no level of security
no ip address
!
interface Ethernet0/3
Shutdown
No nameif
no level of security
no ip address
!
interface Management0/0
Shutdown
No nameif
no level of security
no ip address
!
2KFQnbNIdI.2KYOU encrypted passwd
passive FTP mode
standard access list dubai_splitTunnelAcl allow 192.168.14.0 255.255.255.0
INSIDE_nat0_outbound list of allowed ip extended access all 192.168.14.240 255.255.2
55.240
pager lines 24
Within 1500 MTU
Outside 1500 MTU
IP local pool testpool 192.168.14.240 - 192.168.14.250
no failover
ICMP unreachable rate-limit 1 burst-size 1
don't allow no asdm history
ARP timeout 14400
Global 1 interface (outside)
NAT (inside) 0-list of access INSIDE_nat0_outbound
NAT (inside) 1 0.0.0.0 0.0.0.0
Route outside 0.0.0.0 0.0.0.0 192.168.10.12 1
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout, uauth 0:05:00 absolute
dynamic-access-policy-registration DfltAccessPolicy
Enable http server
http 192.168.14.0 255.255.255.0 inside
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Crypto ipsec transform-set esp-3des esp-md5-hmac setFirstSet
Crypto-map dynamic dyn1 1 set transform-set setFirstSet
Crypto-map dynamic dyn1 1jeu reverse-road
dynamic mymap 1 dyn1 ipsec-isakmp crypto map
mymap outside crypto map interface
crypto ISAKMP allow outside
crypto ISAKMP policy 1
preshared authentication
3des encryption
sha hash
Group 2
life 43200
crypto ISAKMP policy 65535
preshared authentication
3des encryption
sha hash
Group 2
life 86400
Telnet timeout 5
SSH timeout 5
Console timeout 0
a basic threat threat detection
Statistics-list of access threat detection
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the netbios
inspect the rsh
inspect the rtsp
inspect the skinny
inspect esmtp
inspect sqlnet
inspect sunrpc
inspect the tftp
inspect the sip
inspect xdmcp
!
global service-policy global_policy
password encrypted user testuser IqY6lTColo8VIF24 name
username password khans X5bLOVudYKsK1JS / encrypted privilege 15
tunnel-group mphone type remote access
tunnel-group mphone General attributes
address testpool pool
tunnel-group ipsec-attributes mphone
pre-shared-key *.
context of prompt hostname
Cryptochecksum:059363cdf78583da4e3324e8dfcefbf0
: end
ciscoasa #.Hello
Large. Try adding the below to make it work
vpn-sheep access list extended permits all ip 192.168.15.0 255.255.255.0
NAT (inside) 0-list of access vpn-sheep
Harish
-
User authentication with AD Director
Hey!
Am having a problem with the management groups.
I try to make external authentication with users of the AD but fails with one: user authentication failed: Eric: no group admin
Everything seems fine, political authorization, Menu access, liaison group AD with ISE Super Admin to access the data group
My user is ok on AD (not locked, expired, or anything)
Anyone had this problem before?
THX
Possibility of vice.
CSCud31796 ISE - External RBAC fails if Member user from the group containing the apostrophe
Symptom:
RBAC using a storage of external identity (AD, LDAP) group mapping fails for a correct user with the groups to access the GUI of the ISE. The following message will appear:
"User authentication failed: username: admin group.
Conditions:
The user is a member of a group that contains the apostrophe character.
Workaround solution:
There is no work around in ISE.
1 rename all groups in the external identity store such that they do not contain apostrophes
2 remove users participating in the administration of all external groups containing apostrophes ISE
Jatin kone
-Does the rate of useful messages- -
ASA VPN with ISE and different backends WBS for authentication
Hello
I have an AAA-problem I hope to have a few problems help.
The problem ultimately is: how the ASA via ISE send Radius Access requests to different given OTP backends provided a connection to a certain group of Tunnel.
BACKGROUND:
I'll try to give you a brief picture of the scenario, this is what I currently have.
A VPN system (ASA 8.4 (4)) where I let my users to choose among 3 different methods of authentication being
(1) certificate (on chip card)
(2) token - token of the OTP (One Time Password provided via the smartphone application: using pledge of Nordic OTP-Edge transport server)
(3) SMS - OTP token (Nordic OTP - Edge transport server SMS OTP)
The choice corresponds to different groups of profiles/Tunnel connection.
Today, all authentication requests go directly to the OTP server and authorization goes directly to the AD via LDAP.
THE PROBLEM:
The problem occurs when I try to put in the ISE in the mixture.
What I obviously (?) would like to do is have all the network authentication/authorization to go through my ISE platform to take advantage of a centralized administration, monitoring etc.
Again I would need to use data bases different backend such as AD and Nordic OTP - Edge server, but then mandated by ISE.
For me to be able to know what back-end AAA to the proxy system, to somehow be able to distinguish the incoming Radius Access-requests.
WHAT WE CALL:
At the time of the ASA 8.4.3 Radius access request contains 2 new attributes, the name of Group of Tunnel and the Type of customer, when a VPN user connects.
http://www.Cisco.com/en/us/docs/security/ASA/asa84/configuration/guide/ref_extserver.html#wp1802187
QUESTION:
The seams, that I can achieve what I want by looking at the access request attribute Radius "Tunnel Group Name" and forward my request to different backends OTP for the authentication part therefore in theory. But, how do I actually go ahead and set that up in ISE?
I don't see this attribute when I look at the details of Radius Authentication for an authentication AAA of the ASA at the ISE.
Best regards
/ Mattias
I think you can hit the following problem:
CSCtz49846: ISE does not match the condition with VPN 146 Tunnel-Group-Name attribute
This issue is not specific to this attribute, as shown in the solution shown in the accompanying note
Workaround
Ensure that the attribute name does not include a '.' character. This also applies to some of the existing attributes in the dictionary of Cisco-VPN300. Attribute names should be changed so that they do not include a "." character.
-
Windows 7 starter, no internet access, WPA2 Enterprise Network
I use an Asus EeePC for the first time to work. I replace my ibook apple that I had no problem with in the past. I entered the correct name for the network. has selected WPA2-Enterprise, AES encriptación. Using the PEAP authentication. After entering my user domain\username and password, I connect to the network, but when I look at the network he says no internet access. I can see my internal network and the computers.
Any advice would be greatly appreciated.
Thank you
Hi Kbpipes,
First check the edition of Windows 7 installed on your computer, since you mentioned that you use the Windows 7 starter edition. Windows 7 starter edition will not be able to join the domain network. To join the domain network, you will need to install either Windows 7 Professional, ultimate edition.
Access the link below to learn more about the field of Assembly.
http://Windows.Microsoft.com/en-us/Windows7/products/features/domain-join
To verify which edition of Windows 7 is installed on your computer, follow the steps below.
- Click Start.
- Right-click on computer and click Properties.
- Check the information on your computer.
However, you try to run the troubleshooter from network built into windows 7 and check if it can help solve you the problem of connection to the Internet.
Access the link below and follow the steps.
http://Windows.Microsoft.com/en-us/Windows7/using-the-network-troubleshooter-in-Windows-7
You can also try to temporarily disable the security software of the computer and try to connect to the Internet. If you are able to connect to the Internet, you can contact the manufacturer of security software and check if you need to change the settings. Later, re-enable the security software.
Also, you can try to start the computer in safe mode with network and check if you can connect to the Internet. To boot to the desktop in safe mode with network keep tapping key F8 during restart. Once you see the option to start it in safe mode with select network and press ENTER.
Access the link to learn more about how to start the computer in safe mode: http://windows.microsoft.com/en-US/windows7/Start-your-computer-in-safe-mode
You can also contact your network administrator and check if there are settings that must be changed or configured to access the Internet.
Post back with the above information and let us know the result.
Thank you and best regards,
Srinivas R Microsoft support.
Visit our Microsoft answers feedback Forum and let us know what you think.
-
unidentified network - no internet access windows 7
Hi, I have a pavilion dv6 - windows 7 Home premium. everything was working fine until recently, but since this morning my wireless connection is coming as 'public network' with an error message "schooner - no internet access network. its connected to the router as usual with strong signals and other wireless computers work fine. I have not change whatsoever on my laptop but now I tried all the solutions mentioned on the internet. reboot/uninstall-install the drivers / updated drivers/called HP support/safemode network but nothing has worked so far. I use AVG Anti-virus if it's important. other ideas would be very appreciated. and how can I change a public network at my home netowrk in this case?
Thank you
Hello
It may be an idea to set up a static IP address to see if it will connect you.
Open windows control panel and open network and sharing Center. Click on change settings card and in the next window, right click on your wireless connection, and then select Properties. Left click on Internet Protocol Version 4 (TCP/IPv4) to highlight (click on the wording and not with the beat box) and then click the properties button. Click the radio button next to "use IP address, then enter the following values. following
IP 192.168.1.110
Subnet mask 255.255.255.0
Default gateway 192.168.1.1
In addition, assign the following DNS server address
Preferred DNS 208.67.222.222 Server (these belong to OpenDNS)
Auxiliary DNS 208.67.220.220 Server
After entering these values, don't forget to click OK for each open window, before restarting the laptop.
Kind regards
DP - K
Maybe you are looking for
-
Bug where the music would stop playing if app closed if listen to mail or online
I got the iPhone 5 s and I got an update where it would interrupt the music from the email app. Writing music and I use my phone to do this frequently. Basically one of my friends sent me a song that he wanted me to write, simple right? N ° before th
-
HP Pavilion model: dv7 - 3085dx
You help me find the correct supply for the dv7 - 3085dx who was just given to me by a parent? the adapter that I use now will only work the computer and will not charge the battery. I use a HP RN193 power supply now that is only turning off Watt 1
-
I forgot the password of login
Windows xp home edition. Am the administrator. I forgot my new log on password. I tried all the solutions for the past 12 hours. Help, please... Yhank you
-
4502 printer does not print full page
My printer 4502 feeds double intermittently leaving the lower third of the blank page. It occurs when you try to print multiple pages.
-
[HE JUST SEEMS TO BE PROBLEM AFTER PROBLEM WITH MY COMPUTER] the other day, Prevx a scanner my local drive very well! However, I don't have time to scan my local drive, and so I had to interrupt the scan. When I had to abandon it, it has already scan