Cisco ISE 1.1.2.145 Admin authentication via the LDAP protocol
I have configured the LDAP protocol and able to retrieve our LDAP directory structure. Now, I'm trying to point authentication "Admin Access" Source 'External identity', which is the new LDAP IS I created. But I couldn't find an option to authenticate locally if for some reason the LDAP configuration does not work. I learned that the ISE can automatically return to local auth as external sources Idenitity are inaccessible. How can I test the LDAP authentication with breaking them our Admin Access? I thought to open two parallel sessions, one with Super Admin account Local and one with the domain account. But I noticed that ISE communication is smart enough for the closing session/connection no matter what other sessions in different browsers so, basically, I can't open two parallel sessions the same machine to test. Suggestions? or am I missing something here?
Thanks in advance.
Hi Srinivas,
Even if you configure LDAP as a source of external identity of admin access, you can always internal relief without having locked. According to the ISE user guide:
During the operation, Cisco ISE is designed to "fall back" and try to perform the internal identity database authentication, if the communication with the external identity store has not been established, or if it fails. In addition, whenever an administrator for which you have configured external authentication launches a browser and initiates a logon session, the administrator must still the option authentication of demand through the local Cisco ISE database by choosing 'Internal' to the Selector drop-down storage of identity in the Connect dialog box.
http://www.Cisco.com/en/us/docs/security/ISE/1.1/user_guide/ise_man_identities.html#wp1351543
Please see the attached screenshot by my lab ISE:
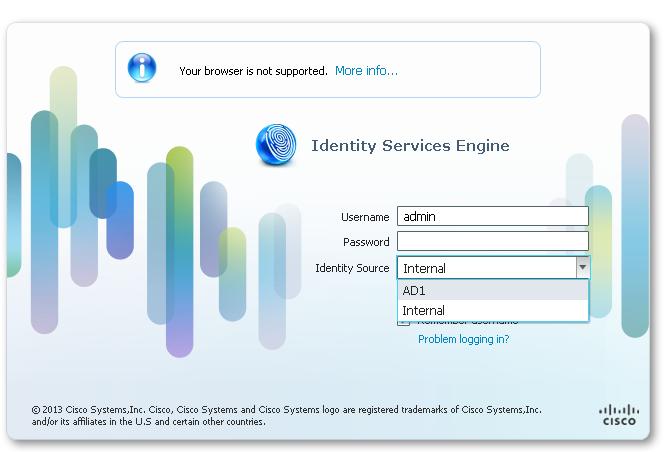
I configured the admin authentication against AD, but I still see both 'Internal' and 'AD' at the time of the connection.
I hope this helps.
Thank you
Aastha
Tags: Cisco Security
Similar Questions
-
Hello
I m currently looking for a document that specify the number of MAC addresses can be stored and authenticated via a GBA (1120)? I prefer to use the identity store internal AD or LDAP for authentication of the MAB for 802.1 X project.
I would like to know what impact the GBA? CPU/MEM?
What is the impact on the user authentication? delay, delay, etc.
Please specify any other restrictions or side effect.
Thanks for your comments
Concerning
Torsten Hello,
I have confirmed on our database as well as this community and the answer is the same
Refer to:
https://supportforums.Cisco.com/thread/2101657
Added additional information:
Internal Users : 300000 Internal Hosts : 50000
Best regards.
-
External authentication via the PHP script failed
I'm not a PHP genius - in fact I'm not a backend coder so I'm kinda struggeling with the sample scripts - I still hope for a sample of CF....
I'm trying to run and connect to the CAA via the command line (Terminal). I'm not sure what I'm doing wrong - this is what I'm passing:
PHP f /Applications/MAMP/htdocs/afcs.php args - debug - host = my_pass, http://connectnow.acrobat.com, fcguru, my_login
The username and password I spend are correct. However, I get this response:
Error: message exception 'AFCSError' with ' < State response 'error' = >
< error code = "AUTH_FAILED" >
< msg > failed authorization < / msg >
< / error >
< / answer >
' in /Applications/MAMP/htdocs/afcs.php:86
Really struggeling with this. Once again I get this working from the command line, I don't know how to call it from a script instead. I use CF on the backend, no PHP.
Kind regards
Stefan
Thank you, this is very useful. It seems that I can now connect from the Terminal so that's a good start. Also, I did not see external authentication in PHP for example - I must have been blind.
I'll see how far I get with that. What I'm trying to do is spawn new rooms based on a template on the fly, and I have some doubts, I'll be able to understand this myself. -
I am very new to Cisco ISE and Meraki. I try to get the Radius configuration for wireless authentication. When I do a test of the Meraki to ISE, it passes.
When I try to connect from my laptop, I look at the logs of the Radius and it passes; However, it does not connect me to good policy. I keep hitting the default policy. I have my Meraki police above the default policy in the strategy defined in article. I have attached what looks like my strategy game.
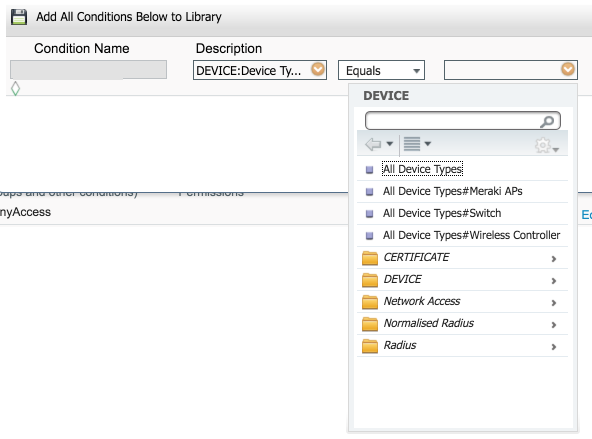
Devices does not really matter. Here is what I see when I create a device group (where you add the access point to this group), and then create the condition:
And here is where I create the condition of strategy game and you should be able to select the Meraki access points:
This will give you the condition similar to what I posted above. This is perhaps why you aren't hit that is not matching the condition for this game.
-
Hello!
Is anyone know about Cisco ISE?
I have a problem with the respect of the Posture. I installed the NAC Agent on PC, Catalyst 2950, and ISE. Authentication is great, but the Posture of compliance does not. I'll send you information if you want to help me.
Thank you!
Catalyst 2950 does not support costs (RADIUS permission change) which is required for enforcement to work: http://www.cisco.com/en/US/docs/security/ise/1.0.4/compatibility/ise104_sdt.html#wp55038
-
I'm working on our implementation of the ISE, and these are my two goals.
1. one SSID to BYOD users and systems businesses managed.
- Connection to the NAC agent if it is not part of the domain (EX: computer laptop windows is not part of the joined field the SSID, passes through the self-service, agent NAC downloads portal, must connect on NAC agent each time that join network with AD credentials)
- AD connection must adhere to this SSID, no guests not allowed
2 comments SSID
- Comments connection requires only - sponsor
- Agent required for Web windows machine
- Required AV
- Current AV definitions required
These objectives are achievable or I'm better to go in a different direction is my first question.
Secondly, using the Guide of Smart Solution from Cisco BYOD (link at the bottom of post), he mentions the unique as SSID not being is not complicated but something it does work thanks to the double solution SSID, which parameters are necessary for one SSID? I use Open + MAC filtering but when the supplicant trying to connect it does not work because it is looking for a WPA2 network with the same SSID name.
http://www.Cisco.com/en/us/docs/solutions/Enterprise/Borderless_Networks/Unified_Access/byoddg.html
One SSID is specifically mentioned here:
David,
What makes the documentation, is that it created a State that performs the check for the ssid in the access-request packet:
Guest_Authz is a condition of simple permission set by the user for customers accessing the Internet through Web authentication via the WIFI network at the open prompt SSID. It corresponds to the next pair of RADIUS AV of the Airespace dictionary:
Airespace-Wlan-Id - [1] EQUALS 1
So that when the user connects to the network, they connect through the ssid of comments in which he has the id of wlan of the 1. Either you can do that in your right authorization rule in the screenshot, or you can create this condition under the tab elements of strategy.
Thank you
Tarik Admani
* Please note the useful messages *. -
Hello guys,.
I have Cisco ISE Cli access, but I do not know the admin password. I mean, password is saved in SecureCRT and I am automatically.
I decided to add another cli user account, login with this user and reset the admin password.
Strangely, I can't connect with the second user.
How can I add and connect with the second user of cli?
Can I use both at the same time?What command did you use to create the second user?
It should be "username
password admin role plain. Jan
-
Cisco first 2.1 / 2.2 support for Cisco ise 1.3?
Hi, I just tried to connect cisco IP 2.1 to cisco ISE 1.3, but fails.
I read the Release Notes, only 1.2 ISE ist supported.
But I was wondering that the ssl negotiation fails (I made a packet capture).
So PI 2.1 has not tried to connect to the ise 1.3 via api, because of the connection fails during the ssl handshake.Anyway, does anyone know if ISE 1.3 will be supported with a PI or PI 2.2 version 2.1.x?
ICC 2.1.2 supports up to 1.2 ISE. ICC 2.2 release date is scheduled for December 2014. Read below.
Table 4 The Infrastructure first, Cisco and Cisco wireless version compatibility matrix
-
Access VPN ASA and cisco ISE Admin
Hello
Currently I'm deployment anyconnect VPN Solution for my client on ASA 9.2 (3). We use the ISE 1.3 to authenticate remote users.
In the policy stipulates the conditions, I put the condition as below.
Policy name: Anyconnect
Condition: DEVICE: Device Type Device Type #All Device Types #Dial - in access EQUALS AND
RADIUS: NAS-Port-Type is equal to virtualI'm authenticating users against the AD.
I am also restrict users based on group membership in authorization policies by using the OU attributes.
This works as expected for remote users.
We also use the ISE to authenticate administrators to connect to the firewall. Now what happens is, Cisco ASA valid also against policy, administrators and their default name Anyconnect.
Now the question is, how to set up different political requirement for access network admin and users the same Firewall VPN.
Any suggestions on this would be a great help.
See you soon,.
Sri
You can get some ideas from this article of mine:
http://ltlnetworker.WordPress.com/2014/08/31/using-Cisco-ISE-as-a-generic-RADIUS-server/
-
Authentication (Windows Server 2013) AD Cisco ISE problem
Background:
Has deployed two Cisco ISE 1.1.3. ISE will be used to authenticate users wireless access admin WLC and switches. Database backend is Microsoft running on Windows Server 2012 AD. Existing Cisco ACS 4.2 still running and authenticate users. There are two Cisco WLCs version 7.2.111.3.
Wireless users authenticates to AD, through works of GBA 4.2. Access admin WLC and switches to the announcement through ISE works. Authentication with PEAP-MSCHAPv2 access and admin PAP/ASCII wireless.
Problem:
Wireless users cannot authenticate to the announcement through ISE. This is the error message '11051 RADIUS packet contains invalid state attribute' & '24444 Active Directory failed because of an error that is not specified in the ISE'.
Conducted a detailed test of the AD of the ISE. The test was a success and the result seems fine except for the below:
xxdc01.XX.com (10.21.3.1)
Ping: 0 Mins Ago
Status: down
xxdc02.XX.com (10.21.3.2)
Ping: 0 Mins Ago
Status: down
xxdc01.XX.com
Last success: Thu Jan 1 10:00 1970
March 11 failure: read 11:18:04 2013
Success: 0
Chess: 11006
xxdc02.XX.com
Last success: Fri Mar 11 09:43:31 2013
March 11 failure: read 11:18:04 2013
Success: 25
Chess: 11006
Domain controller: xxdc02.xx.com:389
Domain controller type: unknown functional level DC: 5
Domain name: xx.COM
IsGlobalCatalogReady: TRUE
DomainFunctionality: 2 = (DS_BEHAVIOR_WIN2003)
ForestFunctionality: 2 = (DS_BEHAVIOR_WIN2003)
Action taken:
Log Cisco ISE and WLC by using the credentials of the AD. This excludes the connection AD, clock and AAA shared secret as the problem.
(2) wireless authentication tested using EAP-FAST, but same problem occurs.
(3) detailed error message shows below. This excludes any authentication and authorization policies. Even before hitting the authentication policy, the AD search fails.
12304 extract EAP-response containing PEAP stimulus / response
11808 extracted EAP-response containing EAP - MSCHAP VERSION challenge response to the internal method and accepting of EAP - MSCHAP VERSION such as negotiated
Evaluate the politics of identity
15006 set default mapping rule
15013 selected identity Store - AD1
24430 Authenticating user in Active Directory
24444 active Directory operation failed because of an error that is not specified in the ISE
(4) enabled the registration of debugging AD and had a look at the logging. Nothing significant, and no clue about the problem.
(5) wireless tested on different mobile phones with the same error and laptos
(6) delete and add new customer/features of AAA Cisco ISE and WLC
(7) ISE services restarted
(8) join domain on Cisco ISE
(9) notes of verified version of ISE 1.1.3 and WLC 7.2.111.3 for any open caveats. Find anything related to this problem.
10) there are two ISE and two deployed WLC. Tested a different combination of ISE1 to WLC1, ISE1 to WLC2, etc. This excludes a hardware problem of WLC.
Other possibilities/action:
1) test it on another version WLC. Will have to wait for approval of the failure to upgrade the WLC software.
(2) incompatibility between Cisco ISE and AD running on Microsoft Windows Server 2012
Did he experienced something similar to have ideas on why what is happening?
Thank you.
Update:
(1) built an another Cisco ISE 1.1.3 sever in another data center that uses the same domain but other domain controller. Thai domain controller running Windows Server 2008. This work and successful authentication.
(2) my colleague tested in a lab environment Cisco ISE 1.1.2 with Windows Server 2012. He has had the same problem as described.
This leads me to think that there is a compatibility issue of Cisco ISE with Windows Server 2012.
Yes, it seems that 1.1.3 doesn't support Server 2012 as of yet.
External identity Source OS/Version
Microsoft Windows Active Directory 2003 R2 32-bit and 64-bit
Active Directory Microsoft Windows 2008 32-bit and 64-bit
Microsoft Windows Active Directory 2008 R2 64-bit only
Microsoft Windows Active Directory 2003 32-bit only
http://www.Cisco.com/en/us/docs/security/ISE/1.1/compatibility/ise_sdt.PDF
-
Cisco ISE 1.3 using 802.1 x authentication for wireless clients
Hello
I fell into a strange question attempts to authenticate a user more wireless. I use as PEAP authentication protocol. I have configured my strategy of authentication and authorization, but when I come to authenticate the selected authorization policy are by default that denies access.
I used the 802. 1 x conditions made up to match the computer authentication, then the user authentication
AUTHENTICATION OF THE COMPUTER
football match
Box
Wireless
Group of ads (machine)
AUTHENTICATING USERS
football match
Box
Wireless
Ad (USER) group
has been authenticated = true
Here are the measures taken to authenticate any ideas would be great.
Request for access received RADIUS 11001
11017 RADIUS creates a new session
15049 evaluating Policy Group
Service evaluation 15008 selection policy
15048 questioned PIP
15048 questioned PIP
15048 questioned PIP
15006 set default mapping rule
11507 extract EAP-response/identity
12300 prepared EAP-request with PEAP with challenge
11006 returned Challenge RADIUS access
Request for access received RADIUS 11001
11018 RADIUS re - use an existing session
12302 extracted EAP-response containing PEAP challenge-response and accepting as negotiated PEAP
12318 has successfully PEAP version 0
12800 first extract TLS record; TLS handshake began
12805 extracted TLS ClientHello message
12806 prepared TLS ServerHello message
12807 prepared the TLS certificate message
12810 prepared TLS ServerDone message
prepared 12305 EAP-request another challenge PEAP
11006 returned Challenge RADIUS access
Request for access received RADIUS 11001
11018 RADIUS re - use an existing session
12304 extract EAP-response containing PEAP stimulus / response
prepared 12305 EAP-request another challenge PEAP
11006 returned Challenge RADIUS access
Request for access received RADIUS 11001
11018 RADIUS re - use an existing session
12304 extract EAP-response containing PEAP stimulus / response
prepared 12305 EAP-request another challenge PEAP
11006 returned Challenge RADIUS access
Request for access received RADIUS 11001
11018 RADIUS re - use an existing session
12304 extract EAP-response containing PEAP stimulus / response
12318 has successfully PEAP version 0
12812 extracted TLS ClientKeyExchange message
12804 message retrieved over TLS
12801 prepared TLS ChangeCipherSpec message
12802 completed TLS prepared message
12816 TLS handshake succeeded
12310 full handshake PEAP completed successfully
prepared 12305 EAP-request another challenge PEAP
11006 returned Challenge RADIUS access
Request for access received RADIUS 11001
11018 RADIUS re - use an existing session
12304 extract EAP-response containing PEAP stimulus / response
12313 PEAP inner method started
11521 prepared EAP-request/identity for inner EAP method
prepared 12305 EAP-request another challenge PEAP
11006 returned Challenge RADIUS access
Request for access received RADIUS 11001
11018 RADIUS re - use an existing session
12304 extract EAP-response containing PEAP stimulus / response
11522 extract EAP-Response/Identity for EAP method internal
11806 prepared EAP-internal method call offering EAP-MSCHAP VERSION challenge
prepared 12305 EAP-request another challenge PEAP
11006 returned Challenge RADIUS access
Request for access received RADIUS 11001
11018 RADIUS re - use an existing session
12304 extract EAP-response containing PEAP stimulus / response
11808 extracted EAP-response containing EAP - MSCHAP VERSION challenge response to the internal method and accepting of EAP - MSCHAP VERSION such as negotiated
15041 assessment political identity
15006 set default mapping rule
Source sequence 22072 Selected identity
15013 selected identity Source - AD1
24430 Authenticating user in Active Directory
Identity resolution 24325
24313 is looking to match accounts at the junction
24315 account in the domain
24323 identity resolution detected single correspondent account
Application for CPP 24343 successful logon
24402 user Active Directory authentication succeeded
Authentication 22037 spent
EAP-MSCHAP VERSION 11824 passed authentication attempt
prepared 12305 EAP-request another challenge PEAP
11006 returned Challenge RADIUS access
Request for access received RADIUS 11001
11018 RADIUS re - use an existing session
12304 extract EAP-response containing PEAP stimulus / response
11810 extract EAP-response to the internal method containing MSCHAP stimulus / response
11814 inner EAP-MSCHAP VERSION successful authentication
11519 prepared EAP-success for the inner EAP method
12314 PEAP inner method completed successfully
prepared 12305 EAP-request another challenge PEAP
11006 returned Challenge RADIUS access
Request for access received RADIUS 11001
11018 RADIUS re - use an existing session
12304 extract EAP-response containing PEAP stimulus / response
ISE 24423 was not able to confirm the successful previous machine authentication
15036 assessment authorization policy
15048 questioned PIP
15048 questioned PIP
Looking 24432 user in Active Directory - xxx\zzz Support
24355 fetch LDAP succeeded
Recovery of user 24416 of Active Directory groups succeeded
15048 questioned PIP
15048 questioned PIP
15004 Matched rule - default
15016 selected the authorization - DenyAccess profile
15039 rejected by authorization profile
12306 successful PEAP authentication
11503 prepared EAP-success
11003 returned RADIUS Access-Reject
Endpoint 5434 conducted several failed authentications of the same scenarioWindows will only be machine authentication when you start, then test you can't just disconnect/connect the pc, you will need to restart. The solution is called cisco anyconnect nam and eap-chaining.
-
Cisco ISE and question Admin CLI
Hello.
I have a strange problem with my installation of ISE. First of all, I use AD users for authentication. It works very well on HTTPS. I can connect with my admin AD by HTTPS.
The problem starts when I try to log in via the CLI (SSH). I got login prompt. When I type my credentials AD that he said "Login Incorrect" and I got the same result if I try it with the local administrator account.
I tried to reset the password for the local administrator over HTTPS to check this kind of wrong password. But no effect.
My ISE is installed VMware.
Experiences with it?
ARM
CLI authentication which is the base Linux OS is not / cannot be bound to AD to the admin authentication. Only, you integrate the application on top of Linux, which in this case is ISE, to AD. So, if you want to connect to the cli shell, you will need to use the username/password you configured during installation. If you do not remember those you need to perform a rest of password via the installation CD / ISO
Thank you for evaluating useful messages!
-
Applicant is not pop up on Win XP during authentication wth Cisco ISE
Hello!
I'm trying to set up authentication for 802. 1 X with Cisco native ISE, Win XP SP3 and begging.
Problem is that when the workstation connects to the network, it uses the hostname as a username and sapplicant is not pop up to ask me the user name and password. Someone knows how to fix this? MB to install a patch on Win XP?
Thank you!
ARO
Max
You are able to get their hands on another machine to test? I think Russian settings, it is causing confusion with me in order to understand the begging parameters. I don't have my hands on a XP client but see if you can use the authentication of the user or the machine and see if it changes your luck?
Tarik Admani
* Please note the useful messages *. -
Authentication for 802.1 x and Cisco ISE printer
Hello
What is the best practice to authenticate a 802 printer. 1 x in Cisco ISE?
The printer can store a certificate for authentication and support EAP - TLS.
Thanks for the reply.
Marco
Please refer to the rules of authentication
www.Cisco.com/c/en/US/TD/docs/Security/ISE/1-2/user_guide/ise_user_guide...
-
Cisco ISE machine has no machine authentication
Hey, since we migrated to ISE 1.2 patch 7 we have problems with our company SSID.
We have a rule that essentially says:
The user is a domain user.
The machine is in the field.
But for some reason, some workstations are is denied by this:
ISE 24423 was not able to confirm the previous machine successfully authentication of user in Active Directory
I was wondering if I could force a sync?
Hmm, you when you restart the machine you should see an entry of authentication which starts by "host /" Let's try this:
1 uncheck the box 'Remove' repeated successful authentications and the "suppress abnormal customers'
2. wait 10 minutes
3. restart the computer and try again and let us know what happens
Maybe you are looking for
-
can I have a watch for my youtube channle review
-
How to clear the drop-down list choice when signing into hotmail etc.
past when signing errors appear below as possible choices how to clear this list
-
I don't like where the HOME icon now (right of the screen) and you want to move elsewhere. I am able to do?
-
dynamically selecting active at TS2012
TS2012 I have several configured reports (all different displayable reports), and they all generate very well (they are all on the disc where I think they should be) At the end of the run, I get the default visible displayed report showing, and top r
-
I lost my disc for Windows XP. Where can I get another?
LOST INSTALLATION DISC I lost my installer of xp, where to get a copy of the windows xp Setup program? I have a certificate of authenticity! Thank youversion of my installer of operating system is WINDOWS XP HOME EDITION!