Local ASA CA to failover
people
I has implemented a vpn ssl on an asa 5540 (8.2), but cannot establish the local authority of ca
its a pair of active failover / standby
I knew that this was not enabled on active/active, but I didn't know that it was not also enabled on active/passive
has one came across this or know if it can be activated?
Hello
Unfortunately it is also not supported in Active script / standby.
There is an enhancement request to have this feature implemented so I would advise you to contact your account team if this feature is important to you, so that they can have it prioritized accordingly: CSCsm17487 CA Local: failover / load balancing Support.
Kind regards
Nicolas
Tags: Cisco Security
Similar Questions
-
Local unit is active failover but is not active.
Impossible to run IPSEC sessions... This is a debugging... any idea?
# Debug ASA5520 cry isa 1
ASA5520 # 14 August at 11:06:59 [IKEv1]: IKE initiator: local unit is active failover but is not active.
August 14 at 11:07 [IKEv1]: IKE initiator: local unit is active failover but is not active.
August 14 at 11:07:02 [IKEv1]: receiver IKE: local unit is active failover but does not
currently active.
August 14 at 11:07:04 [IKEv1]: IKE initiator: local unit is active failover but is not active.
August 14 at 11:07:04 [IKEv1]: IKE initiator: local unit is active failover but is not active.
Try to restart the PIX.
Referring URL:
http://www.Cisco.com/en/us/products/HW/vpndevc/ps2030/products_tech_note09186a0080094ea7.shtml
-
ASA status interface failover: Normal (pending)
I've been struggling with this, I have two ASA running 8.6 that show the interfaces being monitored as well.
I'm under 9.2 on these and tell waiting interfaces. Also can I disable SPI monitored? I ask only the cause at the time where the IPS is a module of the SAA, if I had to restart, the units would be tipping. I don't know if it's the same now with the IPS is a software based inside the ASA running on a separate hard drive.
ASA5515-01 # show failover
Failover on
Unit of primary failover
Failover LAN interface: FAILOVER of GigabitEthernet0/5 (top)
Frequency of survey unit 1 seconds, 15 seconds holding time
Survey frequency interface 5 seconds, 25 seconds hold time
1 political interface
Watched 3 114 maximum Interfaces
MAC address move Notification not defined interval
Version: Our 9.2 (2) 4, Mate 4 9.2 (2)
Last failover at: 03:55:44 CDT October 21, 2014
This host: primary: enabled
Activity time: 507514 (s)
slot 0: ASA5515 rev hw/sw (1.0/9.2(2)4 State) (upward (Sys)
Interface to the outside (4.35.7.90): Normal (pending)
Interface inside (172.20.16.30): Normal (pending)
Interface Mgmt (172.20.17.10): Normal (pending)
Slot 1: IPS5515 rev hw/sw (N/A 7.1 (4) E4) State (to the top/to the top)
IPS, 7.1 (4) E4, upward
Another host: secondary - ready Standby
Activity time: 0 (s)
slot 0: ASA5515 rev hw/sw (1.0/9.2(2)4 State) (upward (Sys)
Interface (0.0.0.0) outdoors: Normal (pending)
Interface (0.0.0.0) inside: Normal (pending)
Interface (0.0.0.0) Mgmt: Normal (pending)
Slot 1: IPS5515 rev hw/sw (N/A 7.1 (4) E4) State (to the top/to the top)
IPS, 7.1 (4) E4, upwardFailover stateful logical Update Statistics
Relationship: unconfigured.ASA5515-01 # poster run | failover Inc.
failover
primary failover lan unit
LAN failover FAILOVER GigabitEthernet0/5 interface
failover interface ip FAILOVER 10.10.1.1 255.255.255.252 ensures 10.10.1.2
ASA5515-01 # ping 10.10.1.2
Type to abort escape sequence.
Send 5, echoes ICMP 100 bytes to 10.10.1.2, time-out is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = ms 02/01/10
# ASA5515-01------------
I read also not to use a design where a cable is directly connected to each unit, and instead each interface must connect on a downstream switch port so that the status of the link is still up to a firewall interface if the other firewall interface fails. Otherwise, the two units detects a link down condition and assume that their own interface is down. Never really thought about it in that sense. Anyone use a direct attached cable and have problems?
Hello
I rarely troubleshoot failover configurations so I am little rusty with associated with these problems.
First thing that comes to mind is that configurations under interfaces has "standby" configured IP address? I wondered as the changeover seems to be configured and the link between the units is fine but the unit ready standby shows just 0.0.0.0 for each interface.
-Jouni
-
ASA with different failover module IPS
Hi all
Is it possible to configure the failover of the ASA with different IPS module configuration because we have: ASA 5585-X with firepower PHC-10 and ASA 5585-X with IPS SSP-10
Thank you
N °
Inventories of material (basic unit, memory and optional modules) must be the same in a pair of failover ASA.
-
Hello
I didn't send a CX module before. We are about to deploy firewalls 2xASA5585-X with CX (for STROKE and WSE) modules.
I'm sure I know the answer to this (I've deployed a lot of old OLD ASA with CSC modules in them, and I'm guessing that the CX module has the same).
1 will be the failure of the module CX trigger a failover event (fail-over active standby)? My guess is not?
2. If it is not and policy service is set to 'closed' this means that the client should perform a manual failover to the secondary/sleep to restore access, web - this correct?
Pete
Hi Pete,.
1 will be the failure of the module CX trigger a failover event (fail-over active standby)? My guess is not.?
Yes he custom of tipping your ASA, depends on configuration either will be allowed or close the traffic
In the area if ASA CX card fails, click permit traffic or close traffic. The narrow traffic option defines the ASA to block all traffic if the ASA CX module is not available. Permits for movement option sets the ASA to allow all traffic through, if not inspected, the ASA CX module is not available.
2 if it is not and the service policy is set to 'closed' this means that the client should perform a manual failover to the secondary/sleep to restore access, web - this correct? .When set to allow traffic CX failure, there is no need to manually failover your ASA firewall between HA
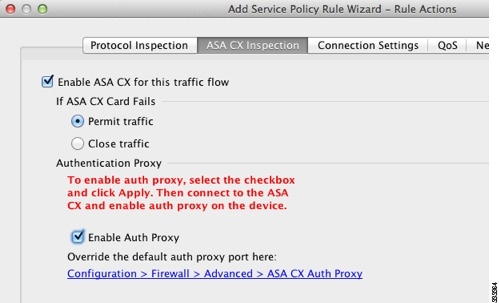
Step 8
 check the ASA CX check this box traffic flow.
check the ASA CX check this box traffic flow.http://www.Cisco.com/c/en/us/TD/docs/security/ASA/Quick_Start/CX/cx_qsg.html#wp49530
-
ASA 5540 Stateful failover routing errors
Hello
Having two 5540's configuration in a failover scenario. Make the LAN failover and failover state. * See attachment *.
Failover LAN use 192.168.2.1 as active and 192.168.2.2 as before, with the subnet mask of 30. On both LAN failover use G0/2 and there is a crossover cable connecting them.
The failover of the State uses 192.168.3.1 as active and 192.168.3.2 as before, with the subnet mask of 30. With "enable HTTP replication" checked in ASDM. On both devices State failover uses G0/3 and there is a crossover cable connecting them.
The ASDM syslog connects errors every 10 seconds or so to say that:
SOURCE IP ADDRESS: 192.168.3.1
DESTINATION IP: 192.168.3.2
Description:
"Routing could not locate the next hop for igrp NP identity 192.168.3.1/0 in statefull:192.168.3.2/0".
The ASA use static routes to meet the network, these roads, there are two, and both are in the 10.x.x.x network. No routing protocol is in use.
I don't know why these errors are "spamming" my syslog and would like to get rid of them.
Glad to hear that it works, that's the most important thing. I don't mean to preach, but Cisco does not recommend using ADJUSTABLE wires to fail on. Devices cannot always say that the captain should be and usually causes questions more than a simple link to the bottom.
-
block access to the local asa firewall vpn accounts
I'm looking for the local accounts on the firewall and would like to make sure that users who have local accounts for vpn do not have for the firewall itself through asdm, telnet, ssh to the management.
Is the only aaa on the firewall command
the ssh LOCAL console AAA authentication
With this command, if I change the local account setting to 'NO ASDM, SSH, Telnet or access Console' (see attached screenshot) will that still allow users to vpn in and access the network because they have to take off but any what potential access to the firewall?
Thank you
Hello
Yes, if you select the option "No., ASDM, SSH, TELNET or Console access" allows to block only the admin access to the firewall. Here's the equivalent CLI for this option:
myASA(config-username) # type of service?
the user mode options/controls:
Admin user is authorized to access the configuration prompt.
NAS-prompt user is allowed access to the exec prompt.
remote user has access to the network.If you use this option you will be on the third option in the above list that is remote access. Users will have the option of VPN in but no admin (asdm, ssh, telnet or console)
Thank you
Waris Hussain.
-
I have two firewalls autonomous asa5525-x,
on two of them, the command show version shows as active/active failover license. Can I use these two to make a pair of active failover / standby?
ASA what are failover license types? Is this different from PIX?
Active/active failover is available only for ASAs in multiple context mode. In an active/active failover configuration, the two ASAs can pass network traffic.
Active failover / standby allows you to use an ASA helps to support the features of a failed unit. When the active unit fails, it changes sleep state while the rescue unit moves to the active state.
For Active hybrid in multiple context mode, the ASA can switch the entire unit (including all contexts) but cannot switch on different contexts separately.
In an active/active couple, amounts of license (if any) are merged. For example, the two 5510 s seats in a pair/active every 100 Premium SSL. The licenses will merge to have a total of 200 SSL VPN has helped the pair. The total number should be below the limit of the platform. If the number exceeds the limit of the platform (e.g. 250 SSL VPN connection on a 5510) the limit of the platform will be used on each.
You can use the active / standby for you.
You can check your information to license under the 'show version' and 'show activation key '. Here is an example:
The devices allowed for this platform:<-----------------FEATURES which="" are="" available="" by="" your="">
The maximum physical Interfaces: 8
VLAN: 20, unrestricted DMZ
Internal hosts: unlimited
Failover: Active / standby
VPN - A: enabled
VPN-3DES-AES: enabled
SSL VPN peers: 2
The VPN peers total: 25
Two Internet service providers: enabled
VLAN Trunk Ports: 8
Sharing license: disabled
AnyConnect for Mobile: disabled
AnyConnect VPN phone Cisco: enabled
AnyConnect Essentials: disabled
Assessment of Advanced endpoint: disabled
Proxy sessions for the UC phone: 2
Total number of Sessions of Proxy UC: 2
Botnet traffic filter: disabled
This platform includes an ASA 5505 Security Plus license.<--------------------- type="" of="" your="">
Serial number: JMX00000000<------------------SERIAL>
Activation key running: 0 x... 0x........ 0x........ 0x........ 0 x...<--------- activation="">
ASA # display the keySerial activation number: JMX00000000Running activation key permanent: 0 x - 0 x - 0 x - 0 x - 0 x - x 0.
Activation key running time: 0 x "' 0 x" ' 0 x "' 0 x" ' 0 x "' 0 x" 'Licenses required for active/active failover
The following table shows the licenses required for this function:
# Model
# Condition of licence
# ASA 5505
# No support.
# ASA 5510 ASA 5512-X
# Security Plus license.
# All other models
# Base license.
Conditions of licence for an active failover / standby
The following table shows the licenses required for this function:
# Model
# Condition of licence
# ASA 5505
# Security Plus license. (Dynamic failover is not supported).
# ASA 5510 ASA 5512-X
# Security Plus license.
# All other models
# Base license.
Active/active failover
You cannot use the active/active failover and VPN; If you want to use VPN, use active failover / standby.
Please note!
Post edited by: sachin gelin
-
ASA 5500 SSL VPN Failover license
Hello
I have a partner who request assistance with SSL VPN licenses on the ASA 5500 firewall sharing:
His question is:
Both SSL, provided with the firewall of the SAA, licenses can be shared across a couple active / standby? I would therefore have a total of (4) licenses of SSL VPN to use?
This would also be true for two security contexts that are included with the firewall?
For example, I buy two base ASA 5520 firewall, running active / standby, that each machine is supplied with SSL VPN licenses (2) and (2) licensing of security contexts? In version 8.3, the licenses are cumulative by failover pairs, so I should a total SSL VPN (4) and (4) security contexts?
Here is my response to his request:
Based on this link (http://www.cisco.com/en/US/partner/docs/security/asa/asa83/license_standalone/license_management/license.html#wp1449664)
It was mentioned that:
"You can have one active license type, either the AnyConnect Essentials license or the AnyConnect Premium license. By default, the Adaptive security apparatus includes an AnyConnect Premium license for 2 sessions. If you install the AnyConnect Essentials license, it is used by default. See not anyconnect-essentials control or in ASDM Configuration > remote access VPN > network (Client) access > advanced > component AnyConnect Essentials to activate the Premium license instead. »
It will be able to share the included license on the ASA 5500 4. It will be able to share these licenses, but I'm not sure the security context. My answer would be, it can use only 2 context Security licenses since only the VPN licenses are shared on the version 8.3 and other licenses not characteristic. My understanding is correct? or there are other explanations on my customer survey?
Thanks in advance!
Ice Flancia
Cisco partner Helpline Tier 2 team
Only from ASA 8.3 version and following, the license can be combined on a failover pair active / standby.
2 SSL included license on SAA in failover pair is combined as 4 license SSL.
2 license of background on ASA in failover pair is combined as license frame 4.
Here's the URL on ASA combined license failover:
Hope that helps.
-
ASA 5505 as internet gateway (must reverse NAT)
Hi all the Cisco guru
I have this diet:
Office-> Cisco 877-> Internet-> ASA 5505-> remote network
Office network: 192.168.10.0/24
Cisco 877 IP internal: 192.168.10.200
Cisco 877 external IP: a.a.a.a
ASA 5505 external IP: b.b.b.b
ASA 5505 internal IP: 192.168.1.3 and 192.168.17.3
Remote network: 192.168.17.0/24 and 192.168.1.0/24
VPN tunnel is OK and more. I have the Office Access to the remote network and the remote network access to the bureau by the tunnel.
But when I try to access the network remotely (there are 2 VLANS: management and OLD-private) to the internet, ASA answer me:
305013 *. * NAT rules asymetrique.64.9 matched 53 for flows forward and backward; Connection for udp src OLD-Private:192.168.17.138/59949 dst WAN:*.*.64.9/53 refused due to path failure reverse that of NAT
Ping of OLD-private interface to google result:
110003 192.168.17.2 0 66.102.7.104 0 routing cannot locate the next hop for icmp NP identity Ifc:192.168.17.2/0 to OLD-Private:66.102.7.104/0
Result of traceroute
How can I fix reverse NAT and make ASA as internet gateway?
There is my full config
!
ASA Version 8.2 (2)
!
hostname ASA2
domain default.domain.invalid
activate the encrypted password password
encrypted passwd password
names of
!
interface Vlan1
Description INTERNET
1234.5678.0002 Mac address
nameif WAN
security-level 100
IP address b.b.b.b 255.255.248.0
OSPF cost 10
!
interface Vlan2
OLD-PRIVATE description
1234.5678.0202 Mac address
nameif OLD-private
security-level 0
IP 192.168.17.3 255.255.255.0
OSPF cost 10
!
interface Vlan6
Description MANAGEMENT
1234.5678.0206 Mac address
nameif management
security-level 0
192.168.1.3 IP address 255.255.255.0
OSPF cost 10
!
interface Ethernet0/0
!
interface Ethernet0/1
Shutdown
!
interface Ethernet0/2
Shutdown
!
interface Ethernet0/3
Shutdown
!
interface Ethernet0/4
Shutdown
!
interface Ethernet0/5
Shutdown
!
interface Ethernet0/6
switchport trunk allowed vlan 2.6
switchport mode trunk
!
interface Ethernet0/7
Shutdown
!
connection of the banner * W A R N I N G *.
banner connect unauthorized access prohibited. All access is
connection banner monitored, and intruders will be prosecuted
connection banner to the extent of the law.
Banner motd * W A R N I N G *.
Banner motd unauthorised access prohibited. All access is
Banner motd monitored and trespassers will be prosecuted
Banner motd to the extent of the law.
boot system Disk0: / asa822 - k8.bin
passive FTP mode
DNS domain-lookup WAN
DNS server-group DefaultDNS
Server name dns.dns.dns.dns
domain default.domain.invalid
permit same-security-traffic intra-interface
object-group Protocol TCPUDP
object-protocol udp
object-tcp protocol
object-group service RDP - tcp
RDP description
EQ port 3389 object
Access extensive list ip 192.168.17.0 LAN_nat0_outbound allow 255.255.255.0 192.168.10.0 255.255.255.0
Standard access list LAN_IP allow 192.168.17.0 255.255.255.0
WAN_access_in list of allowed ip extended access all any debug log
WAN_access_in list extended access permitted ip OLD-private interface WAN newspaper inactive debugging interface
WAN_access_in list extended access permit tcp any object-group RDP any RDP log debugging object-group
MANAGEMENT_access_in list of allowed ip extended access all any debug log
access-list extended OLD-PRIVATE_access_in any allowed ip no matter what debug log
access-list OLD-PRIVATE_access_in extended permit ip 192.168.10.0 255.255.255.0 192.168.17.0 255.255.255.0 inactive debug log
OLD-PRIVATE_access_in allowed extended object-group TCPUDP host 192.168.10.7 access-list no matter how inactive debug log
access-list OLD-PRIVATE_access_in allowed extended icmp host 192.168.10.254 interface private OLD newspaper inactive debugging
access-list OLD-PRIVATE_access_in allowed extended icmp host 192.168.17.155 interface private OLD newspaper debugging
access-list 101 extended allow host tcp 192.168.10.7 any eq 3389 debug log
Access extensive list ip 192.168.17.0 WAN_1_cryptomap allow 255.255.255.0 192.168.10.0 255.255.255.0
WAN_1_cryptomap to access ip 192.168.1.0 scope list allow 255.255.255.0 192.168.10.0 255.255.255.0
WAN_cryptomap_2 to access ip 192.168.1.0 scope list allow 255.255.255.0 192.168.10.0 255.255.255.0
Capin list extended access permit ip host 192.18.17.155 192.168.10.7
Capin list extended access permit ip host 192.168.10.7 192.168.17.155
LAN_access_in list of allowed ip extended access all any debug log
Access extensive list ip 192.168.17.0 WAN_nat0_outbound allow 255.255.255.0 192.168.10.0 255.255.255.0
Access extensive list ip 192.168.17.0 WAN_2_cryptomap allow 255.255.255.0 192.168.10.0 255.255.255.0permit inside_nat0_outbound to access extended list ip 192.168.10.0 255.255.255.0 192.168.17.0 255.255.255.0
pager lines 24
Enable logging
recording of debug trap
logging of debug asdm
Debugging trace record
Debug class auth record trap
MTU 1500 WAN
MTU 1500 OLD-private
MTU 1500 management
mask 192.168.1.150 - 192.168.1.199 255.255.255.0 IP local pool VPN_Admin_IP
no failover
ICMP unreachable rate-limit 1 burst-size 1
ICMP permitted host a.a.a.a WAN
ICMP deny any WAN
ICMP permitted host 192.168.10.7 WAN
ICMP permitted host b.b.b.b WAN
ASDM image disk0: / asdm - 631.bin
don't allow no asdm history
ARP timeout 14400
Global (OLD-private) 1 interface
Global interface (management) 1
NAT (WAN) 1 0.0.0.0 0.0.0.0inside_nat0_outbound (WAN) NAT 0 access list
WAN_access_in access to the WAN interface group
Access-group interface private-OLD OLD-PRIVATE_access_in
Access-group MANAGEMENT_access_in in the management interface
Route WAN 0.0.0.0 0.0.0.0 b.b.b.185 1
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-registration DfltAccessPolicy
the ssh LOCAL console AAA authentication
local AAA authentication attempts 10 max in case of failure
Enable http server
http 192.168.1.0 255.255.255.0 WAN
http 0.0.0.0 0.0.0.0 WAN
http b.b.b.b 255.255.255.255 WAN
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
Service resetoutside
Crypto ipsec transform-set ESP-DES-SHA esp - esp-sha-hmac
Crypto ipsec transform-set esp-SHA-ESP-3DES-3des esp-sha-hmac
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
card crypto WAN_map 1 corresponds to the address WAN_1_cryptomap
card crypto WAN_map 1 set peer a.a.a.a
WAN_map 1 transform-set ESP-DES-SHA crypto card game
card crypto WAN_map WAN interface
ISAKMP crypto enable WAN
crypto ISAKMP policy 10
preshared authentication
3des encryption
sha hash
Group 2
life 86400
crypto ISAKMP policy 30
preshared authentication
the Encryption
sha hash
Group 1
life 86400
Telnet timeout 5
SSH a.a.a.a 255.255.255.255 WAN
SSH timeout 30
SSH version 2
Console timeout 0
dhcpd auto_config management
!a basic threat threat detection
host of statistical threat detection
Statistics-list of access threat detection
a statistical threat detection tcp-interception rate-interval 30 burst-400-rate average rate 200
NTP server 129.6.15.28 source WAN prefer
WebVPN
attributes of Group Policy DfltGrpPolicy
Protocol-tunnel-VPN IPSec l2tp ipsec svc webvpn
internal admin group strategy
group admin policy attributes
DNS.DNS.DNS.DNS value of DNS server
Protocol-tunnel-VPN IPSec
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list LAN_IP
privilege of encrypted password password username administrator 15
type tunnel-group admin remote access
tunnel-group admin general attributes
address pool VPN_Admin_IP
strategy-group-by default admin
tunnel-group a.a.a.a type ipsec-l2l
tunnel-group a.a.a.a general-attributes
strategy-group-by default admin
a.a.a.a group of tunnel ipsec-attributes
pre-shared-key *.
NOCHECK Peer-id-validate
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
maximum message length automatic of customer
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the rsh
inspect the rtsp
inspect esmtp
inspect sqlnet
inspect the skinny
inspect sunrpc
inspect xdmcp
inspect the sip
inspect the netbios
inspect the tftp
Review the ip options
!Thank you for your time and help
Why you use this NAT type?
Access extensive list ip 192.168.17.0 WAN_nat0_outbound allow 255.255.255.0 any
NAT (OLD-private) 0-list of access WAN_nat0_outboundYou are basically saying the ASA not NAT traffic. This private IP address range is not routed on the Internet. This traffic is destined to be sent over the Internet? If so, that LAC should then not be there.
If you want NAT traffic to one IP public outside the ASA, you must remove this line and let the NAT and GLOBAL work:
NAT (OLD-private) 1 0.0.0.0 0.0.0.0
Global (WAN) 1 interface
-
Cannot access a local network of off Site 2 Site VPN
I have cisco ASA 5515-X and 8818 cisco router device
I configured vpn site-to-site. the cisco ASA is a new device but the router is a device in another location and contain several tunnel work, now the tunnel is up but I can't ping LAN on the site of the ASA firewall and some time tunnel at the end of the asa will disappear while it will show again at the end of the router
Here is the config of the SAA.
# show running-config
: Saved
:
ASA 9.1 Version 2
!
CITGroup hostname
activate the encrypted password of V9WHcFD3Zaeul5Lr
names of!
interface GigabitEthernet0/0
nameif outside
security-level 0
address IP A.A.A.A 0.0.0.0
!
interface GigabitEthernet0/1
nameif inside
security-level 100
address IP B.B.B.B 0.0.0.0
!
interface GigabitEthernet0/2
Shutdown
No nameif
no level of security
no ip address
!
interface GigabitEthernet0/3
Shutdown
No nameif
no level of security
no ip address
!
interface GigabitEthernet0/4
Shutdown
No nameif
no level of security
no ip address
!
interface GigabitEthernet0/5
Shutdown
No nameif
no level of security
no ip address
!
interface Management0/0
management only
nameif management
security-level 100
IP 192.168.1.1 255.255.255.0
!
boot system Disk0: / asa912-smp - k8.bin
passive FTP mode
network obj_any object
subnet 0.0.0.0 0.0.0.0OFFICE of extended access list permit ip (IP local ASA) (local IP of the router)
outside extended access list permit tcp any any eq ssh
outside allowed extended access list tcp any host (local IP address of ASA) eq ssh
outside extended access list permit icmp any one
outside extended access list permit tcp host (the router's local IP) host (local IP address of ASA) eq sshpager lines 24
asdm of logging of information
Outside 1500 MTU
Within 1500 MTU
management of MTU 1500
no failover
ICMP unreachable rate-limit 1 burst-size 1
ASDM image disk0: / asdm - 713.bin
don't allow no asdm history
ARP timeout 14400
no permit-nonconnected arp
!
network obj_any object
NAT dynamic interface (indoor, outdoor)
Route outside 0.0.0.0 0.0.0.0 D.D.D.D 1
Timeout xlate 03:00
Pat-xlate timeout 0:00:30
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
Floating conn timeout 0:00:00
dynamic-access-policy-registration DfltAccessPolicy
identity of the user by default-domain LOCAL
the ssh LOCAL console AAA authentication
Enable http server
http 192.168.1.0 255.255.255.0 management
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown warmstart of cold start
Crypto ipsec transform-set esp-aes-256 TEST esp-sha-hmac ikev1
Crypto ipsec pmtu aging infinite - the security association
crypto map outside_map 1 is the OFFICE address
card crypto outside_map 1 set k.k.k.k counterpart
outside_map 1 set transform-set TEST ikev1 crypto card
outside_map interface card crypto outside
trustpool crypto ca policy
Crypto ikev1 allow outside
IKEv1 crypto policy 1
preshared authentication
3des encryption
sha hash
Group 2
life 86400
IKEv1 crypto policy 2
preshared authentication
3des encryption
md5 hash
Group 2
lifetime 28800
Telnet timeout 5
SSH 0.0.0.0 0.0.0.0 outdoors
SSH 0.0.0.0 0.0.0.0 inside
SSH timeout 5
SSH group dh-Group1-sha1 key exchange
Console timeout 0
management of 192.168.1.2 - dhcpd address 192.168.1.254
enable dhcpd management
!
a basic threat threat detection
Statistics-list of access threat detection
no statistical threat detection tcp-interception
username admin password encrypted JtdUVwNnMzvEjPfJ
nairtime Fyp1BJjsayu55viz username encrypted password
tunnel-group k.k.k.k type ipsec-l2l
k.k.k.k group of tunnel ipsec-attributes
IKEv1 pre-shared-key *.
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
maximum message length automatic of customer
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the rsh
inspect the rtsp
inspect esmtp
inspect sqlnet
inspect the skinny
inspect sunrpc
inspect xdmcp
inspect the sip
inspect the netbios
inspect the tftp
Review the ip options
inspect the icmp
!
global service-policy global_policy
context of prompt hostname
no remote anonymous reporting call
Cryptochecksum:e658de2652c6702c61a0cc854a47415f
: endYou are missing a nat exemption, follow the example below, replace IP subnet object-group, depending on your environment.
object-group network local-ASA-lan
object-network 10.10.1.0 255.255.255.0object-group network remote-router-lan
object-network 10.200.0.0 255.255.255.0NAT source (indoor, outdoor) static local-ASA-lan lan-ASA-local destination distance-router-lan lan-router-remote control no-proxy-arp static
Thank you
Rizwan James
-
Cisco ASA with Microsoft CA but arrive CRL
Hi all
I'm going through the old VPN IPsec of Cisco AnyConnect VPN. We want to keep two-factor authentication, so I install a Microsoft stand-alone certification authority (cannot use local ASA CA as we have two units of the SAA in failover). MS it works very well, I delivered the of CA root certificate to the ASA and not issued certificates of the certification authority for client computers that connect using AnyConnect no problem.
My problem is that everything I try I can not get the ASA to retrieve the Revocation list. Many guides, I followed the State that you just add the CRL to the certificate root, then the SAA should pick this up by using the option "use CRL Distribution Point certificate." I tried also manually add LDAP url and try recovery like that (although I don't know about the url I used) and I always get just "cannot retrieve or check the Revocation list. Does anyone have any experience with this or know what I'm doing wrong?
Thank you
Rob
You have the right URL in the certificate? I have seen so many times that the CDP has been incorrectly configured with only a host name instead of a FULL domain name that does not able to solve the modem-router VPN.
-
ASA 5505 Split Tunneling configured but still all traffic Tunneling
Hello
I installed an ASA 5505 running 8.3.2 and Cisco AnyConnect Client 2.5.2017.
There are the DefaultRAGroup and a newly configured Group called SplitTunnelNets.
I have 1 internal subnet (192.168.223.0/24) which has a matching ACL/AS configured on the DefaultRAGroup and the custom group policy called SSLClientPolicy.
When I start the VPN with the ASA, I can indeed reach internal resources, but when I look at the routing table, I see a new default gateway route 0.0.0.0 / 0-> 192.168.25.2 (that is in the IP pool) with a metric of 2. The default route before the start of the session AnyConnect now has a higher metric, so the 192.168.25.2 next hop is a priority.
I don't see the routes in the routing table for 192.168.223.0/24 as I expect to see. In the diagnosis of AnyConnect, I see that 0.0.0.0/0 is the policy applied to the client.
Here's my setup. Please tell me if you see something that I'm missing.
ASA 8.3 Version (2)
!
host name asanames of
!
interface Vlan1
nameif inside
security-level 100
IP 192.168.223.254 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
IP x.x.x.x 255.255.255.240
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
boot system Disk0: / asa832 - k8.bin
passive FTP mode
clock timezone IS - 5
clock to summer time EDT recurring
DNS lookup field inside
DNS server-group DefaultDNS
Server name 192.168.223.41
domain Labs.com
network obj_any object
subnet 0.0.0.0 0.0.0.0
vpn-client-net network object
255.255.255.0 subnet 192.168.25.0
network of the internal net object
192.168.223.0 subnet 255.255.255.0
the DM_INLINE_NETWORK_1 object-group network
internal-net network object
network-vpn-client-net object
the DM_INLINE_NETWORK_2 object-group network
internal-net network object
network-vpn-client-net object
SplitTunnelNets to access extensive ip list allow any 192.168.223.0 255.255.255.0
pager lines 24
Enable logging
asdm of logging of information
Within 1500 MTU
Outside 1500 MTU
mask 192.168.25.1 - 192.168.25.50 255.255.255.0 IP local pool SSLClientPool
no failover
ICMP unreachable rate-limit 1 burst-size 1
ICMP allow any inside
ASDM image disk0: / asdm - 635.bin
don't allow no asdm history
ARP timeout 14400
NAT (inside, all) static source internal-net net internal static destination vpn client vpn client-Net
!
network obj_any object
NAT dynamic interface (indoor, outdoor)
Route outside 0.0.0.0 0.0.0.0 x.x.x.x 1
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
Sunrpc timeout 0:10:00 h323 0:05:00 h225 mgcp from 01:00 0:05:00 mgcp-pat 0:05:00
Sip timeout 0:30:00 sip_media 0:02:00 prompt Protocol sip-0: 03:00 sip - disconnect 0:02:00
Timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
dynamic-access-policy-registration DfltAccessPolicy
Labs-AAA protocol ldap LDAP-server
AAA-server Lab-LDAP (inside) host 192.168.223.41
Server-port 636
LDAP-base-dn dc = labs, dc = com
LDAP-scope subtree
LDAP-naming-attribute sAMAccountName
LDAP-login-password *.
LDAP-connection-dn [email protected] / * /
enable LDAP over ssl
microsoft server type
Enable http server
http 192.168.223.0 255.255.255.0 inside
No snmp server location
No snmp Server contact
Server enable SNMP traps snmp authentication linkup, linkdown cold start
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
Crypto ca trustpoint ASDM_TrustPoint0
registration autosslvpnkeypair key pair
Configure CRL
Crypto ca trustpoint ASDM_TrustPoint1
ASDM_TrustPoint1 key pair
Configure CRL
string encryption ca ASDM_TrustPoint0 certificatesTelnet 192.168.223.0 255.255.255.0 inside
Telnet timeout 5
SSH 192.168.223.0 255.255.255.0 inside
SSH timeout 5
Console timeout 0
dhcpd outside auto_config
!a basic threat threat detection
Statistics-list of access threat detection
no statistical threat detection tcp-interception
NTP 192.5.41.41 Server
NTP 192.5.41.40 Server
SSL-trust outside ASDM_TrustPoint1 point
WebVPN
allow outside
No anyconnect essentials
SVC disk0:/anyconnect-win-2.5.2017-k9.pkg 1 image
SVC disk0:/anyconnect-macosx-i386-3.0.0629-k9.pkg 2 image
Picture disk0:/anyconnect-linux-3.0.0629-k9.pkg 3 SVC
enable SVC
tunnel-group-list activate
internal SSLClientPolicy group strategy
attributes of Group Policy SSLClientPolicy
value of server DNS 192.168.223.41
VPN-tunnel-Protocol svc
Split-tunnel-policy tunnelspecifiedvalue of Split-tunnel-network-list SplitTunnelNets
field default value Labs
split dns value Labs.com
the address value SSLClientPool pools
WebVPN
SVC Dungeon-Installer installed
attributes of Group Policy DfltGrpPolicy
value of server DNS 192.168.223.41
Split-tunnel-policy tunnelspecified
value of Split-tunnel-network-list SplitTunnelNets
coyotelabs.com value by default-field
type of remote access service
type tunnel-group SSLClientProfile remote access
attributes global-tunnel-group SSLClientProfile
CoyoteLabs-LDAP authentication-server-group
Group Policy - by default-SSLClientPolicy
tunnel-group SSLClientProfile webvpn-attributes
allow group-alias CoyoteLabs
!
class-map inspection_default
match default-inspection-traffic
!
!
type of policy-card inspect dns preset_dns_map
parameters
maximum message length automatic of customer
message-length maximum 512
Policy-map global_policy
class inspection_default
inspect the preset_dns_map dns
inspect the ftp
inspect h323 h225
inspect the h323 ras
inspect the rsh
inspect the rtsp
inspect esmtp
inspect sqlnet
inspect the skinny
inspect sunrpc
inspect xdmcp
inspect the sip
inspect the netbios
inspect the tftp
Review the ip options
!
global service-policy global_policy
context of prompt hostname
Cryptochecksum:95b7ff58b54e02948a14b225eec1a990
: endThe split tunnel access list must be standard access-list, not extended access list.
You must change the following:
FROM: SplitTunnelNets access-list extended ip to allow all 192.168.223.0 255.255.255.0
To: SplitTunnelNets standard access list allows 192.168.223.0 255.255.255.0You should be able to reconnect again and will be able to access the Internet after you set up the standard access-list split tunnel.
Hope that helps.
-
Hi all
I have a little problem concerning ASA and syslogs. I have a tunnel from site to site between a local ASA and ASA distance. Behind the ASA local, I have a central syslog server (which has no ASA as default gateway) which collects messages from all network devices and I want to get messages from the ASA remote as well.
The tunnel protects traffic between local networks behind each ASA, which includes ASA inside remote interface as well. The problem is that if I specify on the SAA distance my syslog server it does not pass through the VPN tunnel. The ASA remote sees my server syslog as being 'outside' so he's using the external IP address as the source-interface for the syslog message. Which of course does not pass through the tunnel. As much as I know there is no way to configure the interface source for logging under the SAA, that you can do on a normal IOS router.
I've found a few documents explaining this Setup on CCO, but they all imply I have extend the list for interesting traffic to access allow remote UDP/514 of the PIX traffic outside my local syslog server interface. This isn't something I want to do what I would get in routing complication in my LAN with a public IP address of the ASA remote.
Any suggestions? I thought I could use some sort of NAT on the ASA remote so that all traffic for my local network a source the remote PIX is translated on the inside interface, which in theory should pass the package via the tunnel. I did not go so far.
Any help is appreciated.
Best regards
Stefan
You can define the interface that the ASA will use to send the newspapers "syslog_ip host record.
Make sure you also do "access management".
Then the SAA should source the syslogs from inside the interface, which is probably encrypted with the crypto ACL.
I hope it helps.
PK
-
ASA Site to not tunnel no transmission of traffic for some subnets after awhile
Hello
We have a question really strange tunnel from site to site on several ASAs.
We organize VPN tunnels between a small site and three largest.
The den has an ASA 5505, the other three principles are ASA 5510.
One of the tunnels working for months without problems.
Each tunnel has several class C network.
example Site:
-192.168.50.0/24 (named A1)
-192.168.51.0/24 (called A2)
Site b:
-192.168.60.0/24 (named B1)
-192.168.61.0/24 (called B2)
On two faulty tunnels, all is well at the beginning. After a few days (1-14) some networks to cease to work. So I can ping both A1 and A2 B1 network networks, but only from A2 B2 network. Pings from A1 to B2 doesn't expire. The ASA site showed tx = 0 traffic for <=>A1, B2, but progressive count rx traffic. ASA b it shows rx = 0 to B2<=>A1 and tx counties upward.
This happens unexpected after different periods. Sometimes he hits ASA on site B, where tx = 0, it is sometimes ASA on A site.
I tried to fix it as a result of orders:
ISAKMP crypto claire his
clear crypto ipsec his
clear xlatebut nothing has worked. The only solution for now is to restart the ASA where tx County indicates 0. After restarting, everything goes well for a while.
On one of the affected sites, we have a failover configuration - ASA. A failover of the active device also solves the problem. But if you change your prior back restart the old principal question will return immediately.
I think that there is no configuration because:
-All tunnels are configured in the same way, and one of them is running for moths without any problem
-Tunnels work for all combinations of subnet after a reboot
-The problem occurs after different and long periods of time. So I think that the period between failures is long to be caused by tunnel a.s.o. timeouts.
All ASA are running 9.1. (5) 21.
I updated the firmware of several releases these past few months and had the same problem with any version I tested.
So I hope that someone else has also had this problem and found a solution.
Christian Hey!
Hopefully, solve or find the root cause?
Thank you
Maybe you are looking for
-
I will be able to uninstall the update of the ios 10.0.1 software
I don't really like the new update for my iphone 6 s. I will be able to uninstall it?
-
I use the Blackboard with my USF School, and I can't, especially with copy and paste the Word document in the 'white' space on the Blackboard, which is class school forum online. People SHE told me to be sure that I use Firefox version 3.6 as they ha
-
Satellite A300-1J1 - where to find the drivers for Windows 7?
Could you please indicate the expected availability of the Windows 7 drivers for the laptop A300-1J1 (PSAG0E)? Thank you for your help.
-
Upgrade memory of 2800 satellite
HelloI have a satellite 2800 series model PS280L FQQL3CSS. When I bought this machine the PIII 700 Mhz, 128 MB of RAM seemed a lot, but now Windows 2000 Prof, the machine really creeps! I tried to find an expansion of 256 MB but the last 2 I got, a t
-
OfficeJet Pro 8620: No Internet connection / Proxy request
The screen has a yellow triangle with a! on the first icon on the bottom row. When I click it, I get an error message saying: no Internet connection and asking if I have a Proxy, which I did not. The problem started about a month when I noticed the p