Method to identify the user isuing ALTER SYSTEM
Hi allWe have a database of test in which APPS (a power user) access is given to all developers. We had kept TIMED_STATISTIC to false in this case, so that the load is reduced to the minimum. From these last days, we change this value at the level of the system, and we are unable to identify the person.
Is there a way I can write a database trigger to capture this specific ALTER SYSTEM event? Any help in this regard is highly appreciated.
Kind regards
Lucette
Lucette wrote:
Hi Keita,
My mistake, I do not pay attention on behalf of the author. Forgive me for my doubts; they may be stupid - I'm not a DBA, but I'm a preparer SQL.If I use audit_sys_operations - he will capture all ALTER SYSTEM orders by any user. Then narrow it down us to the test user by issuing ALTER AUDIT test SYSTEM. Please correct me if I'm wrong.
In my PB, there are at least 300 developers work at the moment - is possible to limit this information to a specific event to ALTER SYSTEM? In addition, we are in a WINDOWs environment. If cron does not work. It would be much better if I could device a method to write the details of the session incriminated at a table.
Do you think below would work?
create or replace TRIGGER UNI. USYSTEM_B_ALTER_SYS_AUDIT_TRIG
FRONT
CREATE OR CHANGE OR DROP OR TRUNCATE
ON THE SYSTEM. SCHEMA
declare
......Kind regards
LucettePublished by: lollipop on October 12, 2009 12:18
You don't need to set the parameter audit_sys_operations . What you need is that one specific user to AUDIT
Tags: Database
Similar Questions
-
Is it possible to connect in LR as a user to identify the user who did it change?
Hey there,
Is it possible to connect in LR as a user to identify the user who did it change?
LR is a single-user system. It has no user information that I see in the catalogue or xmp files that are associated each edit change.
-
can watch it identify the user?
Hey,.
I'm curious to know if the Apple Watch is able to identify the user who wears.
I try to explain what I mean
Scenario would be: I bought and use the watch, everything is set up and works great. Then for example my sister puts the watch.
The device includes is not carry me over (e.g. a sensor or whatever it is)?
I hope that you understand what my question is
Good day
Sarah
Hi Sarah
Your watch can be protected by a password, you should keep private.
You may want to try these settings:
-On your iPhone, in the application of Eve, go to: My Watch (low left tab) > General > wrist Detection - this turns on.
-On your iPhone, in the application of Eve, go to: Watch My > Passcode > Passcode turn on (choose a password Simple or more complex).
-If you wish: also on the password settings screen, select Unlock with iPhone.
Your watch will be defined when it was placed on your wrist - or someone else.
After putting on it, it will only be then unlock if you unlock your watch manually (by entering the access code) or unlock your iPhone. Then, it will remain unlocked until you remove it from your wrist, when that it locks automatically.
If someone else puts your watch on, they will not be able to unlock or use it unless they also know the access code (or, if you have enabled the unlock iPhone option with code, you are in the Bluetooth range and unlock your iPhone).
-
I opened gpedit and navigated to the Configuration\Adminstrative administration\systeme user. Then under setting I clicked on "run only the Applications Windows specified, set it to on, then in the section show Options clicked the button next to the"list of authorized applications. I typed in a few apps clicked ok and closed gpedit
When I tried to come back in gpedit, he gave me the following message: "this operation has been cancelled due to restrictions if effect on this computer. Please contact your system adiminstrator. »
I am an administrator on this pc, but it won't let me do anything.
Help, please!
You yourself locked out. A restore from a previous backup (you do not have a right) or a repair installation of the operating system dvd can fix this.
-
Using the copy Flash "alter system suspend '"
Hello friends,
I just had the opportunity to have the IBM/Tivoli to present a new feature called Advanced Copy Services.
This feature offers the possibility to take a copy of 'flash' very fast to a database (hot water), and then copy it to another partition of HDD or on SAN or network server, and then allows us to use RMAN to perform a normal "flashcopied" database copy The time it takes to make a copy of 'flash' is expressed in only a few minutes. In fact, I would like to know precisely how long it takes for a real database about 300 GB.
The whole point of the software is to eliminate the need for long time for backups.
This sounds good, and I'm trying to understand how this can be done.
Apparently, Oracle has a (fairly new) modifies the system suspend and resume command that makes this possible.
Someone at - he used these change orders in the system for this purpose (flashcopy and backups)? Is it really possible to run for this purpose?
I found a few sites with information on this subject and it seems that this can be done as the seller says.
When Oracle offer this new feature? I wasn't aware of this.
NOTE: When I did a few tests, I "suspended" the database, yet I could still select tables, but I could not perform any DDL and DML. Apparently suspends performs a form of locking transaction on all objects in the database.
Thank you.
JI LiIs your goal to a backup or a copy of the database?
I used flash for both, but the Services of integrated advanced copy the Flashcopy and Tivoli Storage Manager with the Protection of data for instant capture devices. I never wanted to integrate Flash copy with Tivoli, my main goal was a brief overview of the database for backup or duplication. I always once a flash for backup just manually send the Flash files to TSM. If there are a few advanages it to integrate Flash and TSM, I have never done.
I've never used suspends alter system as part of the copy of flash, because it suspends all I/o operations and for copy makes flash a recovery managed on the other end eliminates this need however if your database is large enough with enough file Flash with the suspension systems may not be all that practice because I had a database that took almost 5 minutes to get the flash has started on all of its volumes and the suspension for that length of time I'd be against. However Metro Mirror (PPRC) I think requires suspends, so, according to the technology behind the presences for advanced copy Services may be required esp if the wish is to leave the boundaries of the San to copy/backup however documentation is really taking only about copy flash.
I would like to ask the question how long will be my database must be in a sleep state? As I have indicated that if the database has a large number of volumes that need to be flashed this might take a bit so if you have a busy database that could be a factor to consider.
One thing I wonder is if you need to maintain the drive around because the flash back for quick restoration why not only run a physical standby and run backup from it with PDT it will serve the purpse even unloading the backup to another server, and when you re-instantiate the day before use flash for this not to mention some of the other benefits you get to have physics of the day before.
Then, look carefully the benefits and disadventages of the use of GBA in your environment based on your needs and your requirements.
Just some thoughts
-
How to identify the Local user in the BI Publisher?
Hi Experts,
Can we identify the language of the User Login in the editor of BI 11 g?
As we identify the user at the time of the report(:xdo_user_name)
Please mark helpful or appropriate so that others may find useful.
-
Customization of the user for users of the data base and without security ADF
JDeveloper version - 11.1.1.7.0
I want to implement personalization by the user on the database of users and without ADF security. I followed the link in storing the repository in a file system but its same showing below the user interface for all users.
http://Sameh-Nassar.blogspot.IE/2012/03/apply-MDS-to-Oracle-ADF-application.html
Please guide me on how to do this for users of the database. Please share any other useful links, as appropriate.
Customization of the user (SDM) does not care the security of applications. You can also apply to the MDS in your ADF application if you use the ADF security or custom security. The main idea is the class of customization (like MyUserCC) has the method call getValue this method should return the user name. When the user login stores the user id in the session and the method getValue returns the user session ID as:
public String[] getValue(RestrictedSession restrictedSession, MetadataObject metadataObject) { try { String user = (String)FacesContext.getCurrentInstance().getExternalContext().getSessionMap().get("userId"); // userId is the session variable that store the login user id if(user == null) { return new String[]{""}; } return new String[]{user}; } catch (Exception e) { e.printStackTrace(); } return new String[]{""}; } -
the user of the simultaneous listing licenses
Hello
We have 5 tiara concurrent license. Now is mounted in use and I find myself being frequent "who uses licenses" so as to address users who may have checked out a license but are not needing more. Or not as desperately as another user.
I tried to read the log file, but it contains a long list of mixed entries. Screening on the licenses that have been checked, but not yet once, it is almost impossible.
Y at - it a simple method to see the users or IP addresses or computer names are at this time using the licenses?
In addition, a monitor of operating time would be of great help to decide if and how many new licenses.
Thank you.
Michael
Hi Michael,
You use Volume License Manager OR? NEITHER Volume License Manager 3.1 was released recently and it has some new features that will help you answer such questions.
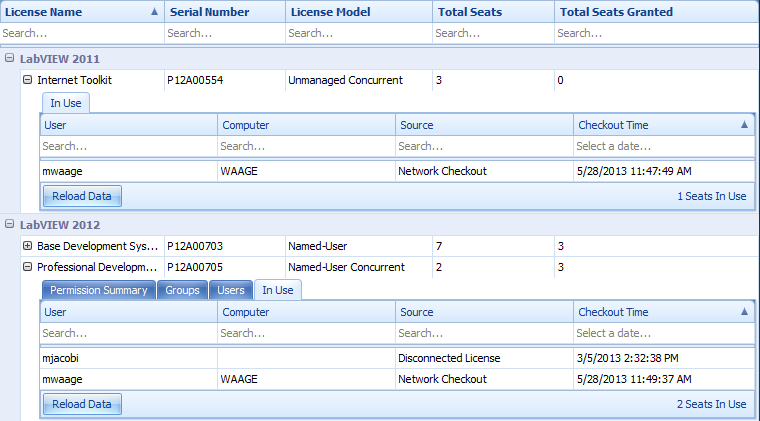
We have improved the ability of the administrator to see which licenses are used with the new tab in use:
This gives you a clear vision of the common use for each license. In order to obtain the most recent data, you can click the button reload.
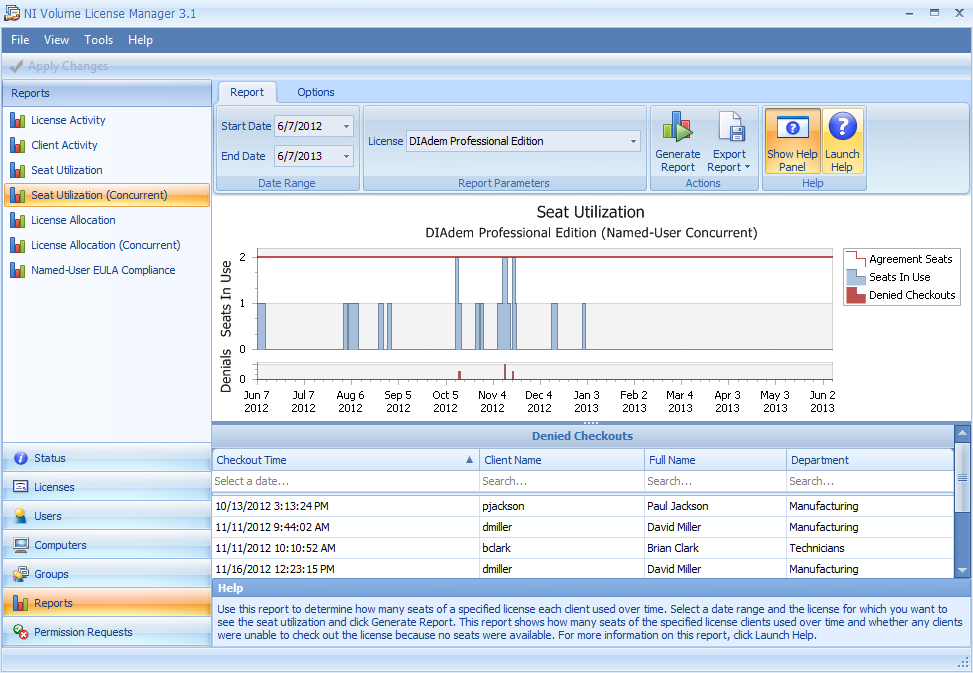
We have also added 3.1 VLM reports. Seat utilization reports are designed to answer your question of how many new licenses to acquire.
This screenshot shows the use of licensed competitor of tiara more than a year. The report will indicate how many licenses were in use and display how many users have been denied. This information will help you determine how many licenses you need.
If you already use VLM 3.0, you can Download NI VLM 3.1 and use your existing license file. If you are using an older version of VLM or FlexNet Publisher, contact [email protected] and let them know that you need a new license file.
Please let me know if you have any additional questions!
-
Need help with this code to update the user interface example
I'm triying to understand the differences between the three methods to manage UI interactions.
I'm really confused with these three terms when triying them figure out in a real case.
Basically, I know that I should use invokeLater, invokeAndWat, or getEventLock() to avoid
This exception: java.lang.illegalStateException: engine access UI without holding the lock on the eventThe code below illustrates the function of the invokeAndWait method, but if I replace it with
invokeLater or getEventLock() the program will work exactly the same way.
Could you please change the code to show the differences between the three
methods of updating the user interface?/ public final class HelloWorldMainScreen extends form {}
private LabelField labelField;
public HelloWorldMainScreen() {}
labelField = new LabelField ("Hello World");
Add (labelField);
Thread MainScreenUpdaterThread = new MainScreenUpdaterThread (this);
thread. Start();
}{} public void appendLabelText (String text)
labelField.setText(labelField.getText()+"\n"+text);
}}
SerializableAttribute public class MainScreenUpdaterThread extends Thread {}
HelloWorldMainScreen screen;public MainScreenUpdaterThread (screen HelloWorldMainScreen) {}
this.mainScreen = screen;
}public void run() {}
for (int i = 0; i)< 10;="" i++)="">
try {}
Thread.Sleep (5000);
} catch (InterruptedException ex) {};
UiApplication.getUiApplication () .invokeAndWait (new Runnable() {}
public void run() {}
mainScreen.appendLabelText ("Update");
}
});}
}
}These three concepts are very confusing for a lot from people so all explanatory source code
describing their functions will be highly useful for everyone, I think.Thanks in advance!
With respect to the effect, there is no difference between methods. The difference is the way in which the result is achieved. So we can't change the code to show you the difference.
As we are unable to demonstrate the difference, you have to do with an explanation. To understand the explanation, you'll need to understand the thread of events, so if you have not already, please consider this:
http://supportforums.BlackBerry.com/T5/Java-development/what-is-the-event-thread/Ta-p/446865
If the three options are differentiated by the processing order:
(a) invokeLater executes the update on the thread of events. The transformation takes place at a later stage and the code which is in order after the invokeLater will actually run before the code within the invokeLater.
(b) invokeAndWait also manages the update on the thread of events, which means that all other events that await on the thread of events will be run before this code. But any code after the invokeAndWait will not be executed.
(c) the synchronized option, like invokeAndWait, runs the update of the UI before moving on to the following code. The difference is that the code to run on the event Thread is not executed before code in the synchronized block.
If this is meaningless, so that probably does not matter too much. in general, you should use invokeLater, except if you need to update the user interface occur in the order with your background processing. If so, use invokeAndWait. It has synced are very few occasions where you must use the block, and it should be very small updates to the user interface and you should understand the implications this could have on the wire events.
-
The driver INF file: identify the OS Architecture of the driver inf file supported
I'm trying to analyze the drivers INF file to identify the architecture of operating system supported by them. For this, I am referring to the MSDN ' SECTION MANUFACTURER INF ' link:
http://msdn.Microsoft.com/en-us/library/Windows/hardware/ff547454 (v = vs. 85) .aspx
I have an inf driver that includes a section of manufacturer as:
[Manufacturer]
HSD % = HSD, NTAMD64
According to section manufacturer documentation given in the link above, the model INF Section name must be decorated with architecture support and therefore, "NTAMD64" suggests that the driver is valid for a Windows 64-bit operating system. But, which suggests "HSD" ?
What operating system doesn't make it references to? How to identify with this? It only supports 32-bit OS or 32 and 64 bit OS.
HelloThe question you posted would be better suited in the MSDN Forums. I would recommend posting your query in the MSDN Forums: -
How to retrieve the id and the password of the user for a Windows service credentials?
Hello
Is it possible to recover a user credential and password in which runs a one-stop service
When I created a one-stop service and set to networkservice / Local user of the Service, later for another service to stop, I want to use this information to identify the user (stop service). How can I retrieve these credentials of the user?
Give more details... My question, if you go to control Panel\All Control Panel Items\Administrative Tools\Service \Properties, you get a tab for login
You can check the user credentials here.
How can be recover through c# code? (.net)
Hi Nandakumarpb,
Thanks for posting the request in the Microsoft Community.
I understand from the description of the issue, you want to know about the recovery of the username and passowrd through c# .net Windows service.
It is better suited for the IT audience Pro on MSDN. Please ask your question in the MSDN Support Forum. You can follow the link to your question:
I hope it helps. If you have problems in the future, please let us know. We will be happy to help you. -
Hi all
I have a strange type of need that must discuss and solution...
I just want to know how to lock the user when the user currently using application...?
Thanks and greetings877432 wrote:
On urgent basis I get my boss to lock user immediately order and I entered the end date on user sysdate but yet he uses to close connection...Kill user session and expiration date of the user account (set to an earlier date).
How to kill Sessions inactive, based on the information in the form of user monitor [ID 103516.1]
11i: how to identify the user for a Session of forms [185762.1 ID]Thank you
Hussein -
Validate the user connected to the database or not
Hi all
I am looking of the view or table to see if the user were connected to the database once the user has been created with all the privileges with on the activation of the audit.
Thank you
RAM.sb92075 wrote:
Girish Sharma wrote:
Another way is the logging listener to get the info if the user has been connected or not.
Listener.log has NOT identify the USER. only hostname / IP #.
Yes you're right Sb, I just got confused words 'Audit Trail' in the context of exploitation forest listener at the bottom of the link:
http://docs.Oracle.com/CD/A57673_01/doc/net/doc/NWTR23/ch2log.htm#audit2Thanks for correcting me.
Concerning
Girish Sharma -
How to identify the Source of Table in a schema star
Hello
We have a star schema with an intermediate table (with fact, as data on sales data) and two tables of dimension (such as by location and product data). In the model, we have specified an intermediate table to have a FK relationship with these two dimension tables.
Two questions:
-How can I select staging table and the foreign key columns in a KM. There are a few options available to the general public as: FK_PK_TABLE_NAME which helps me get my dimension of array, CT_NAME, ERR_NAME, but I can not find a method to identify the intermediate table that is one of the source tables in my interface.
-Is it possible to use the function getsrctableslist() somehow? For example we can use like I_TABLE or TABLE_ORD fields to identify the source table by using this function.
-On the 'Control' of my interface tab, I see the constraints that have been on the target table, is it possible to check the constraints on the source table. For example I can check if the source table contains all the entries valid product by referring to the product as the forign key relationship dimension table.
Pointers, advice, solutions are appreciated.
Thank youIt's Ok now...
follow these steps...
(1) at IKM (not ckm) create a new step.
technology: the same to the table in step
Logical schema: that of the table in stepCode:
<%=odiRef.getSrcTablesList( "","/*\n Will be used the table (and its alias): \n*/","","")%>(2) move this step just before the stage of "Flow Control".
(3) to sewing, the same stage where is the code that you sent change me all code at 'FROM' to
It will work.
-
Expiry of the password for user SYS and SYSTEM
My database 11g 2 on Redhat 5 has sys and system user password expired
But I can still connect the databsae with expired password t.SQL> select username,account_status,EXPIRY_DATE from dba_users where username like 'SYS%'; 2 USERNAME ACCOUNT_STATUS EXPIRY_DA ------------------------------ -------------------------------- --------- SYSMAN OPEN SYSTEM OPEN 15-FEB-11 SYS OPEN 15-FEB-11
Should I worry about the expiration of the password of the user these? For a normal user, I can not connect with expired passwordDear user13148231,
Here's an illustration;
SQL> alter user sys account lock; User altered. SQL> select username, account_status, lock_date, expiry_date from dba_users where USERNAME='SYS'; USERNAME ACCOUNT_STATUS LOCK_DATE EXPIRY_DA ------------------------------------------------------ SYS LOCKED 20-AUG-10 23-FEB-09 SQL> host sqlplus sys/password@opttest as sysdba SQL*Plus: Release 10.2.0.4.0 - Production on Fri Aug 20 12:25:43 2010 Copyright (c) 1982, 2007, Oracle. All Rights Reserved. Connected to: Oracle Database 10g Enterprise Edition Release 10.2.0.4.0 - 64bit Production With the Partitioning, OLAP, Data Mining and Real Application Testing options SQL> exit Disconnected from Oracle Database 10g Enterprise Edition Release 10.2.0.4.0 - 64bit Production With the Partitioning, OLAP, Data Mining and Real Application Testing options SQL> alter user sys identified by password password expire; User altered. SQL> select username, account_status, lock_date, expiry_date from dba_users where username='SYS'; USERNAME ACCOUNT_STATUS LOCK_DATE EXPIRY_DA ------------------------------------------------------ SYS EXPIRED & LOCKED 20-AUG-10 20-AUG-10 SQL> host sqlplus sys/password@opttest as sysdba SQL*Plus: Release 10.2.0.4.0 - Production on Fri Aug 20 12:27:02 2010 Copyright (c) 1982, 2007, Oracle. All Rights Reserved. Connected to: Oracle Database 10g Enterprise Edition Release 10.2.0.4.0 - 64bit Production With the Partitioning, OLAP, Data Mining and Real Application Testing options SQL> exit Disconnected from Oracle Database 10g Enterprise Edition Release 10.2.0.4.0 - 64bit Production With the Partitioning, OLAP, Data Mining and Real Application Testing options SQL> alter user sys identified by password account unlock; SQL> select username, account_status, lock_date, expiry_date from dba_users where username='SYS'; USERNAME ACCOUNT_STATUS LOCK_DATE EXPIRY_DA ------------------------------ -------------------------------- --------- --------- SYS OPENEven if the State expired and locked it's OK to connect to the database for the user SYS.
SQL> alter user ogan identified by password account lock password expire; User altered. SQL> select username, account_status, lock_date, expiry_date from dba_users where username='OGAN'; USERNAME ACCOUNT_STATUS LOCK_DATE EXPIRY_DA ------------------------------ -------------------------------- --------- --------- OGAN EXPIRED & LOCKED 20-AUG-10 20-AUG-10 SQL> conn ogan/password ERROR: ORA-28000: the account is locked Warning: You are no longer connected to ORACLE. SQL> conn / as sysdba Connected. SQL> alter user ogan account unlock; User altered. SQL> conn ogan/password@opttest ERROR: ORA-28001: the password has expired Changing password for ogan New password: Retype new password: Password changed Connected. SQL>Ogan
Maybe you are looking for
-
I have never had this problem before, but had to reinstall because it was not properly closing out.
-
Windows live mail (not hotmail)
I don't know how to sign out of wimdowa live mail. I can connect to hotmail, windows live mail get a box that requires password but if I enter her name and just X out of this area I can always get my windows mail without password
-
I tried to update the bios yesterday. First put into service after that, computer do not download the fan running noise. Nothing on the screen. Also tried to use recovery, but computer disks even not spin the dvd. Help?
-
HelloI have a table like this:IdentPKrankA201B302C403D403E504I have an accumulation of PK with distinct values in the order of ranking. Like this:IdentPKrankrun_sumA20120B30250C40390D40390E504140I appreciate your help.
-
I have a question about generator program that I could use certainly responded.Currently, we work a program to help us clean up our data and want to unsubscribe automatically people who do not respond to our contact inactive campaign.I would like to