ports (vulnerability analysis)
I ran a scan of vulnerability on a switch 2960 and certain "ports" (I don't even know if it's the right way to call them) showed an opening or which needed to be considered. I really need to know what they are and if I have to keep or have to get rid of them. How do you disable "ports" (I do not speak on the real ports on the switch such as gig1/0/1) on a cisco switch? The ports are 4786 tcp, udp 67, udp 161, 162 udp, udp udp 1975, 2228 and 49688 udp.
UDP/67 is bootp (used by DHCP). The switch to listening on this port if it is a DHCP itself or is configured to provide the 'ip assistance' service which is used to translate local segment to the end users of programming a unicast packet, which is then transmitted to your DHCP server also.
UDP 161 and 162 are used by SNMP. Best practice a SNMP limited to SNMP v3 (with authentication and encryption or privacy) and an access list applied to set your authorized SNMP servers.
The high numbered ports are usually a sign that the device (or a user on it session) is connected to something remotely and it's random port is selected in the > range 1024 (sometimes called 'ephemeral' ports as they come and go a bit random) to use as its source port. As long as the session is open, features "listen" on this port for responses.
Good link for port number reference.
Tags: Cisco Security
Similar Questions
-
Port vulnerability 32764 Linksys RVS4000
I have the Linksys RVS4000 router with firmware 1.3.3.5 version. I see that Cisco has released an update (http://software.cisco.com/download/release.html?mdfid=282414013&softwareid=282465789&release=2.0.3.2... to address the vulnerability port 32764 but it's only for the RVS4000 v2.) Does anyone know if there will be an update of the older RVS4000 router?
Thank you
Jim
Hello.
These products are handled by the Cisco Small Business Support community.
* If my post answered your question, please mark it as "acceptable Solution".
Thank you!
-
Result of vulnerability analysis shows Sun Java JDK / JRE / SDK Multiple Vulnerabilities
Analysis of vulnerabilities by Kaspersky Anti Virus showed Sun Java JDK / JRE / SDK Multiple vulnerabilities in my laptop Vista Home Basic 32-bit computer. Looking for solutions for
In Kaspersky, if you click on the little details, it will bring up a full description of the possibility. It may look technically daunting, but generally if you scroll down there is a statement of how to fix the vulnerability. In most cases, it simply means updated the web browser plugin or program. In your case, it may simply mean Java update by visiting www.java.com and get the free update.
Note that a vulnerability detected is not to say that your PC is infected with malware. It simply means that a security breach has been detected that could potentially be exploited by a person in certain circumstances.
-
It seems that whenever a mail server connects a mass mailing to clients I see this fire GIS.
I also see the SIG fires when "some" users surf to websites with rejected (DoubleClick, Akamai, etc..)
According to the DB, GIS to MySDN, this GIS is benign, as long as the traffic seen is internal.
Is this the case?
Do you mean the scan TCP SYN host (3030-0)? I never really found to be a useful signature, especially because it doesn't relate ports under analysis. It is prone to false positives as well because it fires on the return circulation (as a HTTP proxy, for example). Filtering can fix this if you are so inclined.
see these threads:
-
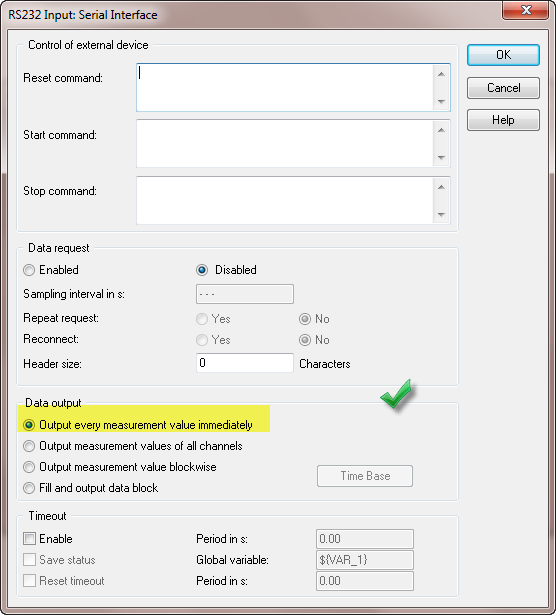
I can collect data from a hygrometer in a text file using the RS232 port with the following T75.2F:H17.0% format, these data are collected using a data logger software. I was wondering if I can collect this data for later analysis using Dasylab. Any help is appreciated.
The setting below causes the error. Change for the second selection, output values of all channels.
-
BlackBerry App BlackBerry App analysis of vulnerability
Hello
I'm looking for a way to perform an analysis of the vulnerability on the applications of the BlackBerry World public.
Currently, we use a variety of tools including NowSecure Lab (for ios and android) to analyize of specific applications for security vulnerabilities that are present. This includes the binary app static analysis and dynamic analysis of the application running on the device.
Is there a similar tool to the NowSecure laboratory which can be used for applications BlackBerry World?
Thank you
Change Yes I know app BlackBerry vetting of treatment with the help of guardian and their relationship with Trend Micro.
Two copies. Please see here: http://supportforums.blackberry.com/t5/BlackBerry-World-Development/BlackBerry-App-Vulnerability-Ana...
-
Hi all
We have properly installed and configured Hyperion Reporting and analysis 11.1.2.4 in windows 2012 server however when I try to logint to the workspace, I get an error like "start-up of the specified document does not exist in the repository." "Select a new start under the General Preferences tab document" monitoring of "could not find a server reports and analysis hyperion running on localhost at port 6800. Please check your connection string server and verify that the server is up '.
HyS9RaFramework_epmsystem2-syserr:
GsmNotFound
com.brio.one.services.globalservicemanager.GSMException: GsmNotFound
at com.brio.one.services.globalservicemanager.GSMFactory.getGSM (unknown Source)
to com.brio.one.client.ClientFactory. < init >(Unknown Source)
to com.brio.one.client.ClientFactory. < init >(Unknown Source)
to com.brio.one.client.ClientFactory$ ClientFactoryInitializer.connect (unknown Source)
at com.brio.one.client.ClientFactory.getClientFactoryConnect (unknown Source)
at com.brio.one.client.ClientFactory.getDefaultGSM (unknown Source)
at com.brio.one.web.properties.ApplicationProperties.getDefaultGSM (unknown Source)
at com.brio.one.web.properties.ApplicationProperties.getDefaultGSMContext (unknown Source)
at com.sqribe.WS.WSBaseServlet.setDefaultGSMContext (unknown Source)
at com.sqribe.WS.WSBaseServlet.initLogging (unknown Source)
at com.sqribe.WS.WSBaseServlet.loadConfiguration (unknown Source)
at com.sqribe.WS.WSBaseServlet.init (unknown Source)
to weblogic.servlet.internal.StubSecurityHelper$ ServletInitAction.run (StubSecurityHelper.java:283)
at weblogic.security.acl.internal.AuthenticatedSubject.doAs(AuthenticatedSubject.java:321)
at weblogic.security.service.SecurityManager.runAs(SecurityManager.java:120)
at weblogic.servlet.internal.StubSecurityHelper.createServlet(StubSecurityHelper.java:64)
at weblogic.servlet.internal.StubLifecycleHelper.createOneInstance(StubLifecycleHelper.java:58)
to weblogic.servlet.internal.StubLifecycleHelper. < init > (StubLifecycleHelper.java:48)
at weblogic.servlet.internal.ServletStubImpl.prepareServlet(ServletStubImpl.java:539)
at weblogic.servlet.internal.WebAppServletContext.preloadServlet(WebAppServletContext.java:1981)
at weblogic.servlet.internal.WebAppServletContext.loadServletsOnStartup(WebAppServletContext.java:1955)
at weblogic.servlet.internal.WebAppServletContext.preloadResources(WebAppServletContext.java:1874)
at weblogic.servlet.internal.WebAppServletContext.start(WebAppServletContext.java:3155)
at weblogic.servlet.internal.WebAppModule.startContexts(WebAppModule.java:1518)
at weblogic.servlet.internal.WebAppModule.start(WebAppModule.java:487)
to weblogic.application.internal.flow.ModuleStateDriver$ 3.next(ModuleStateDriver.java:427)
at weblogic.application.utils.StateMachineDriver.nextState(StateMachineDriver.java:52)
at weblogic.application.internal.flow.ModuleStateDriver.start(ModuleStateDriver.java:119)
at weblogic.application.internal.flow.ScopedModuleDriver.start(ScopedModuleDriver.java:201)
at weblogic.application.internal.flow.ModuleListenerInvoker.start(ModuleListenerInvoker.java:249)
to weblogic.application.internal.flow.ModuleStateDriver$ 3.next(ModuleStateDriver.java:427)
at weblogic.application.utils.StateMachineDriver.nextState(StateMachineDriver.java:52)
at weblogic.application.internal.flow.ModuleStateDriver.start(ModuleStateDriver.java:119)
at weblogic.application.internal.flow.StartModulesFlow.activate(StartModulesFlow.java:28)
to weblogic.application.internal.BaseDeployment$ 2.next(BaseDeployment.java:672)
at weblogic.application.utils.StateMachineDriver.nextState(StateMachineDriver.java:52)
at weblogic.application.internal.BaseDeployment.activate(BaseDeployment.java:212)
at weblogic.application.internal.EarDeployment.activate(EarDeployment.java:59)
at weblogic.application.internal.DeploymentStateChecker.activate(DeploymentStateChecker.java:161)
at weblogic.deploy.internal.targetserver.AppContainerInvoker.activate(AppContainerInvoker.java:79)
at weblogic.deploy.internal.targetserver.BasicDeployment.activate(BasicDeployment.java:184)
at weblogic.deploy.internal.targetserver.BasicDeployment.activateFromServerLifecycle(BasicDeployment.java:361)
to weblogic.management.deploy.internal.DeploymentAdapter$ 1.doActivate(DeploymentAdapter.java:52)
at weblogic.management.deploy.internal.DeploymentAdapter.activate(DeploymentAdapter.java:200)
to weblogic.management.deploy.internal.AppTransition$ 2.transitionApp(AppTransition.java:31)
at weblogic.management.deploy.internal.ConfiguredDeployments.transitionApps(ConfiguredDeployments.java:261)
at weblogic.management.deploy.internal.ConfiguredDeployments.transitionApps(ConfiguredDeployments.java:246)
at weblogic.management.deploy.internal.ConfiguredDeployments.activate(ConfiguredDeployments.java:170)
at weblogic.management.deploy.internal.ConfiguredDeployments.deploy(ConfiguredDeployments.java:124)
at weblogic.management.deploy.internal.DeploymentServerService.resume(DeploymentServerService.java:181)
at weblogic.management.deploy.internal.DeploymentServerService.start(DeploymentServerService.java:97)
at weblogic.t3.srvr.SubsystemRequest.run(SubsystemRequest.java:64)
at weblogic.work.ExecuteThread.execute(ExecuteThread.java:256)
at weblogic.work.ExecuteThread.run(ExecuteThread.java:221)
In the workspace, it shows that the Service is pending.
EMP Diagnostic Report:
Can help kindly out how should I solve this problem.
I restarted the services and rebooted the Machine but still getting the same error.
Kind regards
VJ
Hello
I've reconfigured the Reporting, analysis, and everything by, I chose "Drop table" and the issue was resolved.
Kind regards
VJ
-
vulnerability, right tools of analysis for DB beyond basic configurations. »
Someone is using external tools for analysis of vulnerability DB as well as any recommendation?
I'm looking for external suppliers and ANALYSIS tool. I don't mean to Oracle security (links you posted). Thank you.
-
analysis of the chain of the serial port to retrieve data
Hi all
It is a problem of beginner. I have two sensors sending data to a same wireless serial port. In order to distinguish which is which. I coded each sensor to send data with a unique address UoL 000 X, then followed by two values, I want to read. These two values are in the float with format fixed impression (decimal fixed after the third bit). The format string of the first sensor should looks like UoL 0001 123,45678 876.54321. I use the Scan of the String function, unfortunately, it doesn't work that way. Could you please check the VI for me? Or a better solution for this application. Thank you very much.
S.G
It does not because what you have set is not different from what you have joined earlier. Have you tried something?
See this amendment attached to your VI. The format strings work with the examples you gave, and sends the data to the appropriate indicator.
Also, I cleaned up the mess that the inner loop where you were waiting for 1 or more bytes. Which means most of the time that you would probably get an incomplete message.
-
After the analysis of my PC - WARNING vulnerability ID: NON-2015-0211, help please
The report says that my firmware is out of date and that it upgraded. So, as any reasonable computer geek I checked out your site and found the upgrade you suggested to other people with the same problem... download to v1.1.2.12. I downloaded and followed the instructions, there is no download, several times. I watched my router on your site and went to his specific download page and there the last update was the he version to what I have installed on it (v1.0.0.48), so I don't know if there is an update, you can direct me. Any help greatly appreciated ywould.
Sincerely,
Sethos099
Unfortunately, there will be no update future firmware for the router.
This is because the router is already EOL.
Consider getting a newer model.
-
MyHP3070 deskjet will scan and print via USB link, but don't scan the network, printing is authorized via netowrk. Used to work but not anymor. I have windows XP laptop. I tried HP doctor but in vain. It says that it cannot connect with the driver. Tried to uninstall and reinstall from the CD and also downloaded driver via HP web page but does not. Any ideas what to try next? Also have Norton 360 software virsus and tried extinction of firewalls, etc., but it doesn't seem to help. What is confusing, is that it is used to work but now is intermittened, it won't work at all.
I managed to uninstall with REVO Uninstaller. This removed the driver original from the Add/REMOVE program possibly a result. This then allowed me to install the driver that you recommended to your link above. I ran out of time yesterday to test if the printer has worked with the new download, so I'll have to try again later today to see if it works. I would grab with result.
Thanks a mil
-
WRT54GS - how stealth ports 135-139
Hello
The WRT54GS router has been very, very good to me... But I'm digging the safety and find that the 135-139 ports are considered to be closed and not Steathed. I tried dumping of traffic to ports to a non-existent LAN machine, but it does not work. Is it possible to achieve stealth?
Thank you
p.
paul1149 says:
You are seen. If you weren't there (or actually camouflaged) and then to the router closest to your IP address (for example the router that needs to deliver packages to your IP) would yield a unreachable ICMP to the sender. Of course, he doesn't not because the router knows that you are connected. So 'stealth' means only you are there but do not meet certain demands.
If the router again that I do not answer, then undercover under a router is a joke. I guess that's what you're saying. I am amazed by this.
Fix. The whole 'stealth' is a joke. As I've written before, which is implemented in many firewalls and routers is "I do not answer an incoming unsolicited connection queries" (instead of answer "closed port"). But not answering, it's not what would happen if an IP was not in use, because the IP protocol requires unreachable ICMP message from the nearest router to your ISP to be returned if an IP address is not used... So 'stealth' of port scans is not the same thing as 'invisible '.
paul1149 says:
I doubt whether they will really be worth if a port is "stealth"
My thought was that if they don't see you down, they would not search further for vulnerable ports. Is this bad?
Lol what would be the purpose of this, unless you do not want to make intensive checks of some computers. But it would be very inefficient. In addition, scans ports more than a single IP address is relatively easy to detect by the firewall. Many firewalls (such as those used by ISPS) scans ports IP addresses to detect and block once.
Instead a worm that exploits a vulnerability on port 135 will scan open ports 135. If it's a Trojan horse using port 12345 it will scan for port 12345. Although it was a malware that is able to exploit some dozend vulnerablitiies, it would be just scan for ports that expose vulnerable services and not all. All malware has to do is to send the connection requests and wait for those who succeed. If there is a "closed port" returned or anything not really made a difference.
It's like spammers: they really not worth that an email address exists or not. Once they have found an address they sent spam there. They check even returned undeliverable messages. Why bother?
paul1149 says:
Re my router config, I have no port triggering, DMZ or UPnP. The only transmission I did was earlier, in the 139 infiltration attempt. But my attempts to transfer to a non-existent customer made no difference in the analysis.
Get a stealth, you must forward a port on a computer running a software firewall, which "hides" a port. Redirect to a non-existent customer does not necessarily (because the router must still declare an ICMP unreachable, it may or may not do).
In any case, I recommend to ask your ISP if they are blocking ports 135-139 or not. The only other way to find out would be to use a computer connected to the internet port of the router (with static IP on the computer and the router) and see if the computer detects the same result or if it is reported he 135-139 ports then camouflaged.
-
Certificate/Protocol 4172 PCoIP gateway port problems
Just received my quarterly security scans back, and while I thought I had my security server set up correctly, apparently I still have problems with the port of PCoIP/cert.
The analyses show the PCoIP gateway on 4172 answering the SSLv3 and by not providing a valid certificate. I have double and triple checked the registry settings and files locked.properties to be sure I'm not serving SSLv3 and present a valid certificate, and all these settings seem to be correct. Check the ports 443 or 8443 shows the protocols/cert are working properly, but the same analysis on 4172 shows that he respond to SSLV3 and issue a certificate of PCoIP self-signed (default).
Looks like my locked.properties file in C:\Program VMware View\Server\sslgateway\conf:
secureProtocols.1 = TLSv1.2
secureProtocols.2 = TLSv1.1
secureProtocols.3 = TLSv1
preferredSecureProtocol = TLSv1.2
enabledCipherSuite.1 = TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
TLS_DHE_DSS_WITH_AES_128_CBC_SHA = enabledCipherSuite.2
enabledCipherSuite.3 = TLS_RSA_WITH_AES_128_CBC_SHA
enabledCipherSuite.4 = TLS_RSA_WITH_AES_256_CBC_SHA
enabledCipherSuite.5 = TLS_DHE_DSS_WITH_AES_256_CBC_SHA
enabledCipherSuite.6 = SSL_RSA_WITH_RC4_128_MD5
enabledCipherSuite.7 = SSL_RSA_WITH_RC4_128_SHA
enabledCipherSuite.8 = SSL_RSA_WITH_3DES_EDE_CBC_SHA
enabledCipherSuite.9 = SSL_DHE_DSS_WITH_3DES_EDE_CBC_SHA
And here are registry settings that PCoIP gateway should use for the cert (SSLCertPSGNI the key is correctly set to the public fqdn of the Security Server):
The friendly name on the cert in the Windows certificate store is vdm, and there is a private key associated with the cert. As I said, it's only to default on 4172-443 and 8443 work as expected. No idea where to start looking for why the PCoIP gateway isn't follow these settings on 4172?
Thank you
Geoff
Just got the phone with support. TL; DR version: it works.
More explanation in the case where you need please Commissioners to the accounts:
Apparently most of the scanning (in this case, Qualys) services fail to do one very important thing when they probe port 4172, and who has send a SNI. Without this crucial little of info Security Server will return the cert (self-signed) by default, not the one you want. To see this in action, openssl is your friend:
c:\OpenSSL-Win32\bin>OpenSSL s_client-connect "vcs.XXXXXXX.com:4172" - showcerts
Loading 'screen' into random State - done
CONNECTED (000001CC)
depth = 1 O = PCoIP Root, CN = PCoIP Root CA
Verify error: num = 19:self certificate of certificate chain
Verify return: 0
---
Certificate chain
0 s/O = PCoIP Device/CN=1.1.1.1
i: / O = PCoIP root/CN = PCoIP Root CA
...
Now try the same connection by sending a SNI (servername argument)-:
c:\OpenSSL-Win32\bin>OpenSSL s_client - servername vcs. XXXXXXXX.com - connect "vcs.XXXXXXX.com:4172" - showcerts
Loading 'screen' into random State - done
CONNECTED (000001CC)
...
Certificate chain
s:/0C = US / ST = Texas/L = Houston/O = XXXXXXXX/CN = *. XXXXXXX.com
i: / C = US / O = DigiCert Inc./CN = DigiCert SHA2 Secure Server CA
The PCoIP Gateway sends the cert right when you connect with the customer to view or with a browser, but if another program (such as openssl) connects without sending a NIS, you will get the default cert (or nothing at all if disable CERT legacy with the key "reg").
Hope this helps for others who have to explain why 4172 appears vulnerable according to audit reports.
Geoff
-
My system administrator told me to take down my Apple Airport Extreme because of a vulnerability. Administrator says:
"The remote host is an airport Apple Wireless Access Point.
can be administered on port TCP 5009.
There is a design flaw in the administrative protocol that makes
clients that connect to this port to send the password
clear (though slightly obsfuscated).
An attacker who has the ability to intercept data this will
device can use this flaw to get his administrative password and
its gain setting. From the airport to the base station does not keep all
Journal, it will be difficult to determine administrative access
has been stolen.
Solution:
Block incoming port traffic and administer only
This base station when connected using a cross-over ethernet
cable. »
I am brought to believe that Airport Extreme is not blocking ports, and to forward port 5900 to a non-existent address.
Can someone on this and perhaps provide clear instructions on how to forward a port to a non-existent address?
By default, as a NAT router, all incoming ports on the airport base stations are blocked. Has no way to specifically block ports (incoming or outgoing) through the AirPort Utility limit.
Your suggestion of redirecting from one port to a non-existent address should work.
For port mapping/forwarding, check out this Tip to the user for more details. As for the IP address to use, I suggest that take you a from outside the DHCP scope by default on the base... which is 10.0.1.2 - 10.0.1.200. So, 10.0.1.201 should do.
-
Why is ssl3 is disabled in firefox 35.01 on my pc, I have test and it's vulnerable to ssl3
I have the latest version of Firefox installed on one of my PC, not this one, Windows 7 Professional. When I ran the test SSL3 he returned my Firefox browser is vulnerable. I looked everywhere to find a solution for this and cannot. Please help me with this.
Thank you
From Firefox 34.0 vulnerable SSL 3.0 has been disable and TLS 1.0 is used by default. https://blog.Mozilla.org/security/2014/10/14/the-poodle-attack-and-the-end-of-SSL-3-0/
The security.tls.version.min about: config must be set to 1 by default which means TLS 1.0 is the minim, uh and not SSL 3.0 which is set to 0 on the preference.
You have Avast? as the analysis of https in Avast can actually make your less secure connection in some cases and cause problems of this kind. So if you have Avast disable https analysis in Avast. Some other antivirus scanners may have an effect on this also.
Maybe you are looking for
-
In some forms of web (e.g. What strikes a new note in Evernote Web), I can't type the numbers 1, 2, 6, 9, or 0. Typing '1' or '2' jumps out to an another changes in typing "9" or "0" tab open the font size. Type '6' does nothing I can see easily. I u
-
Satellite Pro L870-149 - query Toshiba Blu - Ray player
Good afternoon. I bought the laptop above a month ago and have just tried playing a Bluray disc for the first time using its built-in Bluray player, but nothing plays. By default the autoruns drive the integrated Toshiba Blu - Ray player, which is lo
-
How to restore Toshiba NB250 to out of the box?
I have a laptop Toshiba NB250-108, is a German keyboard layout if it makes a difference. I have no CD drive or the DVD software.I tried the system restore to out of the box several times with no luck, hold 0 (zero) button on start up, but only takes
-
event for broadcasting images of TCP/IP
Hi all My request has currently 2 devices using TCP/IP on stream of framework to 100ms and 50ms data refresh to a PC. I would like to change the polling for data to generate an event when the data arrives, but I'm not sure how to proceed. I have curr
-
HP Color Laserjet pro mf m177f: stuck on Intializing
Hello from the Germany, Unfortunately my new printer is stuck on initializing. I read a few solutions but they didn't work (hard rest) and I also turn around the cartridges for example black on the front but the printer was still saying that I should