Problem setting up VPN
MY problem is that when the vpn is configured, and I try to run a tracert to one of my remote PC across the VPN, the VPN router sends information from the internet and do not attempt to open the tunnel. what I am doing wrong?
I use a cisco router 1700 and connect to a vpn concentrator 3030 Cisco
Current configuration: 1522 bytes
!
version 12.3
horodateurs service debug datetime msec
Log service timestamps datetime msec
encryption password service
!
router host name
!
boot-start-marker
boot-end-marker
!
enable secret 5
!
MMI-60 polling interval
No mmi self-configuring
No pvc mmi
MMI snmp-timeout 180
No aaa new-model
IP subnet zero
!
!
!
IP cef
Max-events of po verification IP 100
!
!
crypto ISAKMP policy 9
BA 3des
md5 hash
preshared authentication
Group 2
ISAKMP crypto key (shared key) (peer IP address)
!
86400 seconds, duration of life crypto ipsec security association
!
Crypto ipsec transform-set esp-3des esp-md5-hmac TS1
!
crypmap 1 ipsec-isakmp crypto map
defined peer (IP ADDRESS of the peer)
game of transformation-TS1
match address 101
!
!
!
interface Ethernet0
IP (IP ADDRESS)
NAT outside IP
Half duplex
crypmap card crypto
!
interface FastEthernet0
IP (IP ADDRESS)
IP nat inside
automatic speed
!
the IP nat inside source 1 interface Ethernet0 overload list
IP classless
IP route 0.0.0.0 0.0.0.0 (default router)
no ip address of the http server
no ip http secure server
!
!
access-list 1 permit one
access-list 101 permit ip host (LOCALHOST using NAT) host (the remote host 1)
access-list 101 permit ip host (LOCALHOST using NAT) host (remote host 2)
access-list 101 permit ip host (LOCALHOST using NAT) host (the remote host 3)
access-list 101 permit ip host (LOCALHOST using NAT) host (the remote host 4)
!
!
Line con 0
line to 0
line vty 0 4
7 PASSWORD password
opening of session
!
end
Hi Jim
You must change the access list statement also the declaration of overloaded nat...
You must deny traffic between 2 vpn networks is natted...
You can check the below link configuration to the top of the same...
http://www.Cisco.com/en/us/Tech/tk583/TK372/technologies_configuration_example09186a008009448f.shtml
regds
Tags: Cisco Security
Similar Questions
-
Hello
I use a software called TheGreenbow IPSec VPN Client to create a VPN to my RVS4000 tunnel. I have used this software for a long time with my old BEFSX41 router with no problems. My settings are almost identical to the parameters of the site Web of TheGreenbow: Guide of Config .
My problem is the following...
I have successfully created a tunnel. I can ping my devices on network without the drama. If I close that tunnel and attempt to open another, my client tells me that the tunnel is open, even if the router says it's down. I can't ping my network and my logs tell me I have an INVALID COOKIE error. I understand that this means that one of my endpoints using a SA which is no longer in use. Seems that the router is 'pending' on an old SA document. The only way I can solve this is to make a change (no change) to the router so that I have to press the button to save the changes. This seems to reset the router endpoint and the next tunnel I opened works correctly. It of fine when I'm at home and testing and may reset the router but impossible to deal with when I am on the road and actually use the tunnel.
Someone knows a problem like this before and have any advice on settings I can adjust to the problem?
Thanks in advance.
Milster
Sorry people I could have solved.
The router is new, so I checked the firmware version and there had been a number of updates to version my router supplied with. Improved v1.1.11 to v1.2.11 and initial test seems solid.
See you soon
Milster
-
Problem setting up vpn l2tp/ipsec
I tried to configure an ASA5505 with a l2tp/ipsec vpn which I can connect to with Windows Vista vpn client. I had connection problems. When I try to connect, watch windows vpn client tell an error message "error 789: the L2TP connection attempt failed because the security layer detected a processing error during initial negotiations with the remote computer." The newspaper on the SAA is errors saying "Phase 1 failure: incompatibility of the types of attributes of class Group Description: RRs would be: unknown Cfg was: Group 2.
It seems that the ASA does not like windows vpn client IKE proposal but I do not know if I interpret correctly this error message.
I was wondering if anyone has seen this problem or have had success with this type of installation. I have the setup of device OK so that I can connect with the Cisco VPN client, but get l2tp/ipsec Setup to work with the windows vpn client turns out to be problematic.
Can you post the Config of your ASA. Did you check the following link:
http://www.Cisco.com/en/us/products/ps6120/products_configuration_example09186a00807213a7.shtml
-
problem setting up vpn site-to-site between asa and 1811 router
I get the following error.
3. January 8, 2008 | 15: 47:31 | 710003 | 192.168.0.45 | 192.168.0.50. TCP access denied by ACL to 192.168.0.45/3698 to LAN:192.168.0.50/80
3. January 8, 2008 | 15:47:28 | 710003 | 192.168.0.45 | 192.168.0.50. TCP access denied by ACL to 192.168.0.45/3698 to LAN:192.168.0.50/80
6. January 8, 2008 | 15:47:28 | 302021 | 192.168.0.45 | 192.168.0.50. Connection of disassembly for faddr gaddr laddr 192.168.0.50/0 192.168.0.50/0 192.168.0.45/1024 ICMP
6. January 8, 2008 | 15:47:28 | 302020 | 192.168.0.45 | 192.168.0.50. Built of ICMP incoming connections for faddr gaddr laddr 192.168.0.50/0 192.168.0.50/0 192.168.0.45/1024
5. January 8, 2008 | 15: 47:03 | 713904 | IP = public IP address, encrypted packet received with any HIS correspondent, drop
4. January 8, 2008 | 15: 47:03 | 113019 | Group = public IP address, Username = public IP address, IP = IP address public, disconnected Session. Session type: IPSecLAN2LAN, duration: 0 h: 00 m: 00s, xmt bytes: 0, RRs bytes: 0, right: Phase 2 Mismatch
3. January 8, 2008 | 15: 47:03 | 713902 | Group = public IP address, IP = public IP address, peer table correlator withdrawal failed, no match!
3. January 8, 2008 | 15: 47:03 | 713902 | Group = public IP address, IP = IP address public, error QM WSF (P2 struct & 0x4969c90, mess id 0xf3d044e8).
5. January 8, 2008 | 15: 47:03 | 713904 | Group = public IP address, IP = IP proposals public, IPSec Security Association all found unacceptable.
3. January 8, 2008 | 15: 47:03 | 713119 | Group = public IP address, IP = IP address public, PHASE 1 COMPLETED
6. January 8, 2008 | 15: 47:03 | 113009 | AAA recovered in group policy by default (DfltGrpPolicy) to the user = public IP address
4. January 8, 2008 | 15: 47:03 | 713903 | Group = public IP address, IP = IP address public, previously allocated memory release for authorization-dn-attributes
I do not think that because of the incompatibility of encryption. Any help is appreciated.
Thank you
Nilesh
You have PFS (Perfect Forward Secrecy) configured on the ASA and not the router. This could be one of the reasons why the tunnel fails in Phase 2.
If you do not need a PFS, can you not make a 'no encryption card WAN_map 1 set pfs' the configuration of the ASA and make appear the tunnel.
Kind regards
Arul
-
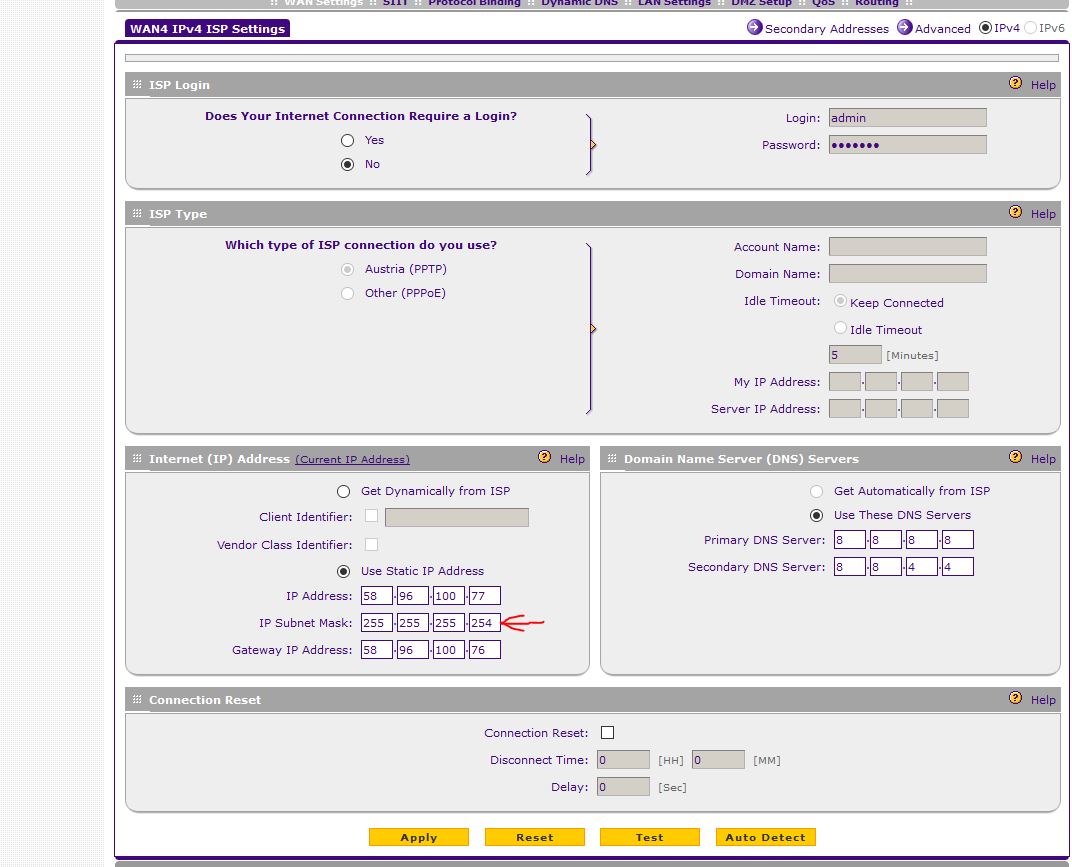
I can't add/subnet mask 31 255.255.255.254 ISP WAN > static IP setting in VPN Firewall SRX5308
Hello
I can't add/subnet mask 31 255.255.255.254 ISP WAN > static IP setting in VPN Firewall SRX5308. When I try to apply it, I get the popup error message like "invalid IP subnet mask. Please enter 0/128/192/224/240/248/252 for octet 4 ". I try to add provider NTU fiber optic internet service in one of the 4 WAN settings. The vendor gave me a 31 block IP and the subnet as 255.255.255.254 mask. It is a limitation in this firewall? I have to ask the provider to give me a 30 block the IP instead? With 30 block IP subnet mask will be 255.255.255.252 who is authorized by this firewall setting. I tried this on another (SnapGear SG560) firewall and it works without any problem. See the screenshots below. Can someone please?
concerning
Ridwan
/ 31 would be used in specific scenarios where you * really * need to keep the address space and on links only point to point. To be honest I've never met anyone, or any ISP that uses it. It works on point to point, because, well, there no need to broadcast address because there are only two devices on the link (one on each side of the cable)... IP address ranges would be;. 0-. 1,.2-. 3, etc.
Most (if not all) Netgear devices will prevent you from setting 31, but you will probably be able to use without problem in all 30 cases, according to the setup of the ISP I do not think that it would cause you problems really. But if you can, I would certainly ask a 30 instead.
-
Problem with Tunnel VPN L2L between 2 ASA´s
Hi guys,.
I have some problems with my VPN Site to site tunnel between 2 ASA (5520/5505).
I watched a lot of videos on youtube, but I can't find out why the tunnel does not...
Both devices can ping eachothers WAN IP address (outside interfaces), but I don't see any traffic between the 2 sites. It seems that the tunnel is not open to everyone. When i PING from the local to the Remote LAN (which should be an interesting traffic for the tunnel...), the its IKEv1 remains empty...
Am I missing something? I can't understand it more why same phase 1 is not engaged.
You NAT won't. In your config file traffic is NATted initially and then does not match any more crypto ACL. You must move the rule dynamic NAT/PAT until the end of the table on two ASAs NAT:
no nat (INSIDE,OUTSIDE) source dynamic any interface nat (INSIDE,OUTSIDE) after-auto source dynamic any interface
-
Problem Set - up blackBerry Smartphones Email
Hey guys,.
I'm having a problem setting up my accounts e-mail and access to internet on my 8830 Verizon Wireless. Sorry I'm kinda a n00b this is my first blackberry. Thus, everytime I try to put something it says I have to create a blackberry account which is fine and dandy, but it won't let me because it says that my PIN is already activated, now I buy this phone. How can I do accept my new account and letme registry?
I will also upgrade the operating system on it (even if my thinkpad comes to die what numbers) which version of desktop software works best?
Good so I called Verizon and they were confused at first but after being on the phone for a while with a very useful technology, they understood him out and set up my email for me. It turns out that I have to use the user name that is already registered on the phone, so the guy that I bought username. They wiped out its old email (I hope, you just don't lose all your emails wherever you are) accounts and set mine to and let me change the password. Everything works now, just waiting to get my thinkpad broke stupid of the STI in order to update and sync with my outlook calendar.
-
Problem setting transition duration first pro cs4. Is this a bug?
Hello world
I have made a project of first pro cs4 and I'm having problems setting the duration of transitions between clips. I have my default transion set to cross dissolve them and 15 frames in length. When I try to lengthen, it seems that first makes two transitions in instead of a longer one. So, if for example I got a clip with a dip to black when I extend more than 15 default images to say 30 images I get two separate transitions one after the other instead of a long. I know it's difficult to understand so I downloaded the video on youtube. If fast forward you to the minute 01:20, you will see the latest bland given away with a dip to black transition and the you'll be right flash a bit after the last light disappears. I hope someone can help me solve this problem, as I'm completaly lost. Thank you :-)
Work waaay too hard at this, dude. Just use the default chained. It gives you good fade to the top using all 24 images, no adjustment necessary.
-
Problem setting out by ASA 5505 VPN
While inside a network secured by an ASA 5505, I can't establish a PPTP VPN on. The ASA will connect the following:
09-2009 20:50:09 creating 305006 24.13.209.125 regular translation failed for the internal protocol 47 src: 192.168.132.108 dst outside:xxx.xxx.xxx.125
I looked at the msg of error in line, but for some reason, I'm just not understand what he says. How can I fix it? Let me know if you have any questions... Thank you guys!
Colombia-British
Hello
Enable pptp inspection
pixfirewall (config) #policy - map global_policy
pixfirewall(config-pmap) #class inspection_default
pixfirewall (config-pmap-c) #inspect pptp
Go to this link for the use of pptp/gre info background detail under various codes.
Concerning
-
Routing problem between the VPN Client and the router's Ethernet device
Hello
I have a Cisco 1721 in a test environment.
A net 172.16.0.0/19 simulates the Internet and a net 192.168.1.0/24 simulates the net, the VPN tunnel must go to (intranet).
The net 172.16.0.0 depends on the router 0 FastEthernet, Intranet (VPN) hangs on Ethernet 0.
The configuration was inspired form the sample Configuration
"Configuring the Client VPN Cisco 3.x for Windows to IOS using Local extended authentication"
and the output of the ConfigMaker configuration.
Authentication and logon works. Client receives an IP address from the pool. But there's a routing problem
side of routers. Ping client-side - do not work (the VPN client statistics that count encrypt them packets, but not to decrypt).
Ping the router works too, but decrypt and encrypt customer statistics in VPN packets count progressive
(customer has a correct route and return ICMP packets to the router).
The question now is:
How to route packets between the Tunnel and an Ethernet device (Ethernet 0)?
conf of the router is attached - hope that's not too...
Thanks & cordially
Thomas Schmidt
-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.- snipp .-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.
!
version 12.2
horodateurs service debug uptime
Log service timestamps uptime
encryption password service
!
!
host name * moderator edit *.
!
enable secret 5 * moderator edit *.
!
!
AAA new-model
AAA authentication login userauthen local
AAA authorization groupauthor LAN
!
! only for the test...
!
username cisco password 0 * moderator edit *.
!
IP subnet zero
!
audit of IP notify Journal
Max-events of po verification IP 100
!
crypto ISAKMP policy 3
3des encryption
preshared authentication
Group 2
!
ISAKMP crypto client configuration group 3000client
key cisco123
pool ippool
!
! We do not want to divide the tunnel
! ACL 108
!
Crypto ipsec transform-set esp-3des esp-sha-hmac RIGHT
!
Crypto-map dynamic dynmap 10
Set transform-set RIGHT
!
map clientmap client to authenticate crypto list userauthen
card crypto clientmap isakmp authorization list groupauthor
client configuration address map clientmap crypto answer
10 ipsec-isakmp crypto map clientmap Dynamics dynmap
!
interface Ethernet0
no downtime
Description connected to VPN
IP 192.168.1.1 255.255.255.0
full-duplex
IP access-group 101 in
IP access-group 101 out
KeepAlive 10
No cdp enable
!
interface Ethernet1
no downtime
address 192.168.3.1 IP 255.255.255.0
IP access-group 101 in
IP access-group 101 out
full-duplex
KeepAlive 10
No cdp enable
!
interface FastEthernet0
no downtime
Description connected to the Internet
IP 172.16.12.20 255.255.224.0
automatic speed
KeepAlive 10
No cdp enable
!
! This access group is also only for test cases!
!
no access list 101
access list 101 ip allow a whole
!
local pool IP 192.168.10.1 ippool 192.168.10.10
IP classless
IP route 0.0.0.0 0.0.0.0 172.16.12.20
enable IP pim Bennett
!
Line con 0
exec-timeout 0 0
password 7 * edit from moderator *.
line to 0
line vty 0 4
!
end
^-^-^-^-^-^-^-^-^-^-^-^-^- snapp ^-^-^-^-^-^-^-^-^-^-^-^-^-^-
Thomas,
Can't wait to show something that might be there, but I don't see here. You do not have the card encryption applied to one of the interfaces, perhaps it was not copied. Assuming your description you do it, or should it be, applied to the fa0 and you are connected. Try how you ping? Since the router or a device located on E0? If you ping the router, you will need to do an extended ping of E0 to the ip address of the client has been assigned. If your just ping the router without the extension, you will get sales and decrypts that you declare on the client. Have you tried to ping from the client to interface E0? Your default route on the router is pointing to fa0? You have a next hop to affect? You have several NIC on the client pc? Turn off your other network cards to check that you don't have a problem with routing on the client if you have more than one.
Kurtis Durrett
-
Problem creating a VPN IPSec with SRP527W
Hello.
I have a Setup like this:
192.168.15.0/24 SRP527W <->internet <->ROUTER [172.16.16.1] <1:1 nat="">pfSense (raccoon vpn server) [172.16.16.2] 192.168.55.0/24
I set up a VPN between the SRP and pfsense connection but the connection is not established because that timeout of the phase 1. According to racoon on the remote side does not.
Before that, I've properly established a VPN between the SRP and another box of pfsense, but with a public IP address. The same host, I have an another vpn to the pfsense box (172.16.16.1) works correctly.
These parameters of the PRS:
IKE policy:
Exchange mode: aggressive
Permit ID: manual
Remote ID: 172.16.16.2
Encryption: 3DES
Authentication: MD5
DH: Group 2
PSK: mysharedkey
DPD: disabled
IPSec policy:
Policy type: police car
Remote end point: IP ADDRESS
IP: 172.16.16.2
Life expectancy: 7800
Set local subnet and remote according to the above (192.168.x.x) Network Setup.
How can I check what is the problem? I struggled for several hours now and have failed to go out again! Any help really welcome!
Thank you
Lorenzo,
The router to 172.16.16.1 allows all traffic to the pfsense VPN server when specific NAT is enabled or you have create access rules? My guess is that the router is blocking the traffic.
-Marty
-
Problem with IPsec VPN between ASA and router Cisco - ping is not response
Hello
I don't know because the IPsec VPN does not work. This is my setup (IPsec VPN between ASA and R2):
my network topology data:
LAN 1 connect ASA - 1 (inside the LAN)
PC - 10.0.1.3 255.255.255.0 10.0.1.1
ASA - GigabitEthernet 1: 10.0.1.1 255.255.255.0
-----------------------------------------------------------------
ASA - 1 Connect (LAN outide) R1
ASA - GigabitEthernet 0: 172.30.1.2 255.255.255.252
R1 - FastEthernet 0/0: 172.30.1.1 255.255.255.252
---------------------------------------------------------------------
R1 R2 to connect
R1 - FastEthernet 0/1: 172.30.2.1 255.255.255.252
R2 - FastEthernet 0/1: 172.30.2.2 255.255.255.252
R2 for lan connection 2
--------------------------------------------------------------------
R2 to connect LAN2
R2 - FastEthernet 0/0: 10.0.2.1 255.255.255.0
PC - 10.0.2.3 255.255.255.0 10.0.2.1
ASA configuration:
1 GigabitEthernet interface
nameif inside
security-level 100
IP 10.0.1.1 255.255.255.0
no downtime
interface GigabitEthernet 0
nameif outside
security-level 0
IP 172.30.1.2 255.255.255.252
no downtime
Route outside 0.0.0.0 0.0.0.0 172.30.1.1------------------------------------------------------------
access-list scope LAN1 to LAN2 ip 10.0.1.0 allow 255.255.255.0 10.0.2.0 255.255.255.0
object obj LAN
subnet 10.0.1.0 255.255.255.0
object obj remote network
10.0.2.0 subnet 255.255.255.0
NAT (inside, outside) 1 static source obj-local obj-local destination obj-remote control remote obj non-proxy-arp static-----------------------------------------------------------
IKEv1 crypto policy 10
preshared authentication
aes encryption
sha hash
Group 2
life 3600
Crypto ikev1 allow outside
crypto isakmp identity address------------------------------------------------------------
tunnel-group 172.30.2.2 type ipsec-l2l
tunnel-group 172.30.2.2 ipsec-attributes
IKEv1 pre-shared-key cisco123
Crypto ipsec transform-set esp-aes-192 ASA1TS, esp-sha-hmac ikev1-------------------------------------------------------------
card crypto ASA1VPN 10 is the LAN1 to LAN2 address
card crypto ASA1VPN 10 set peer 172.30.2.2
card crypto ASA1VPN 10 set transform-set ASA1TS ikev1
card crypto ASA1VPN set 10 security-association life seconds 3600
ASA1VPN interface card crypto outsideR2 configuration:
interface fastEthernet 0/0
IP 10.0.2.1 255.255.255.0
no downtime
interface fastEthernet 0/1
IP 172.30.2.2 255.255.255.252
no downtime-----------------------------------------------------
router RIP
version 2
Network 10.0.2.0
network 172.30.2.0------------------------------------------------------
access-list 102 permit ahp 172.30.1.2 host 172.30.2.2
access-list 102 permit esp 172.30.1.2 host 172.30.2.2
access-list 102 permit udp host 172.30.1.2 host 172.30.2.2 eq isakmp
interface fastEthernet 0/1
IP access-group 102 to------------------------------------------------------
crypto ISAKMP policy 110
preshared authentication
aes encryption
sha hash
Group 2
life 42300------------------------------------------------------
ISAKMP crypto key cisco123 address 172.30.1.2-----------------------------------------------------
Crypto ipsec transform-set esp - aes 128 R2TS------------------------------------------------------
access-list 101 permit tcp 10.0.2.0 0.0.0.255 10.0.1.0 0.0.0.255
------------------------------------------------------
R2VPN 10 ipsec-isakmp crypto map
match address 101
defined by peer 172.30.1.2
PFS Group1 Set
R2TS transformation game
86400 seconds, life of security association set
interface fastEthernet 0/1
card crypto R2VPNI don't know what the problem
Thank you
If the RIP is not absolutely necessary for you, try adding the default route to R2:
IP route 0.0.0.0 0.0.0.0 172.16.2.1
If you want to use RIP much, add permissions ACL 102:
access-list 102 permit udp any any eq 520
-
How to set up VPN on the router via ASA5505 2811
Hello everyone
I apologize for the possible triviality of my question. The current configuration of our society considers appropriate for the edge, two ASA5505 below that are installed two routers configured with the CCME 2811 Express. When the two AS5505 is configured a VPN connection for the transmission of data in our network traffic. Given the presence of several public addresses available on our two sites, I was wondering if you could (and if so, how) to set up a VPN between two routers 2811, except that when existing data traffic, dedicated exclusively to the voice traffic. It give me a document that teach me how can I solve my problem?
Thank you very much
Damiano,
If you want an IPsec VPN for only separate voice and termination traffic on routers, there are several possibilities. Especially if you have a spare IP addresses:
IPsec VPN endpoints on the routers.
GRE over IPsec routers ending (gives you that soften what and where can be routed, in particular, identify voice traffic)
Termination of free WILL on the routers and unloading IPsec to ASAs. (Benefit of the foregoing + ASAs making encryption).
There is no problem to close the tunnels through the ASA, the only warning is that even in the case of static NAT you should probably use NAT-Traversal.
Marcin
-
Problem with ping VPN cisco 877
Hi all!
I have a working VPN between a fortigate and a Cisco.
I have a problem with ping network behind the cisco of the network behind the forti.
When I ping to vlan2 cisco without problem (192.168.252.1) interface, but I can't ping a server in the vlan2 (192.168.252.2) behind the cisco.
However the Cisco I can ping the server. In the forti, I see that ping to the interface vlan2 and server in vlan2 take in the same way, and I can see package.
I post my config could see it it as blocking the ping from 10.41.2.36 to 192.168.252.2 while 192.168.252.1 ping is OK?
IPSEC #show run
Building configuration...Current configuration: 3302 bytes
!
! Last modification of the configuration at 14:42:17 CEDT Friday, June 25, 2010
! NVRAM config update at 14:42:23 CEDT Friday, June 25, 2010
!
version 12.4
no service button
horodateurs service debug datetime msec
Log service timestamps datetime localtime show-time zone
encryption password service
!
IPSEC host name
!
boot-start-marker
boot-end-marker
!
logging buffered 1000000
enable secret 5 abdellah
!
No aaa new-model
clock timezone GMT 1
clock to summer time CEDT recurring last Sun Mar 02:00 last Sun Oct 03:00
!
!
dot11 syslog
IP cef
No dhcp use connected vrf ip
DHCP excluded-address IP 192.168.254.0 192.168.254.99
DHCP excluded-address IP 192.168.254.128 192.168.254.255
!
IP dhcp DHCP pool
network 192.168.254.0 255.255.255.0
router by default - 192.168.254.254
Server DNS A.A.A.A B.B.B.B
!
!
no ip domain search
name of the IP-server A.A.A.A
name of the IP-server B.B.B.B
!
!
!
!
!
crypto ISAKMP policy 1
BA aes 256
preshared authentication
Group 5
ISAKMP crypto key ciscokey address IP_forti
!
!
Crypto ipsec transform-set esp - aes 256 esp-sha-hmac vpntest
!
myvpn 10 ipsec-isakmp crypto map
defined by peer IP_forti
Set transform-set vpntest
match address 101
!
Archives
The config log
hidekeys
!
!
!
!
!
interface Tunnel0
IP 2.2.2.1 255.255.255.252
source of Dialer0 tunnel
destination of IP_forti tunnel
myvpn card crypto
!
ATM0 interface
bandwidth 320
no ip address
load-interval 30
No atm ilmi-keepalive
DSL-automatic operation mode
!
point-to-point interface ATM0.1
MTU 1492
bandwidth 160
PVC 8/35
VBR - nrt 160 160
PPPoE-client dial-pool-number 1
!
!
interface FastEthernet0
switchport access vlan 2
!
interface FastEthernet1
!
interface FastEthernet2
!
interface FastEthernet3
switchport access vlan 2
!
interface Vlan1
IP 192.168.20.253 255.255.255.0
IP nat inside
no ip virtual-reassembly
!
interface Vlan2
IP 192.168.252.1 255.255.255.0
IP nat inside
IP virtual-reassembly
!
interface Dialer0
bandwidth 128
the negotiated IP address
NAT outside IP
no ip virtual-reassembly
encapsulation ppp
load-interval 30
Dialer pool 1
Dialer-Group 1
KeepAlive 1 2
Authentication callin PPP chap Protocol
PPP chap hostname [email protected] / * /
PPP chap password 7 abdelkrim
myvpn card crypto
!
IP forward-Protocol ND
IP route 0.0.0.0 0.0.0.0 Dialer0
IP route 10.41.2.32 Tunnel0 255.255.255.240
!
no ip address of the http server
no ip http secure server
The dns server IP
translation of nat IP tcp-timeout 5400
no ip nat service sip 5060 udp port
overload of IP nat inside source list NAT interface Dialer0
!
IP access-list standard BROADCAST
permit of 0.0.0.0
deny all
!
NAT extended IP access list
IP enable any host IP_cisco
deny ip 192.168.252.0 0.0.0.255 10.41.2.32 0.0.0.31
!
access-list 101 permit ip 192.168.252.0 0.0.0.255 10.41.2.32 0.0.0.31
public RO SNMP-server community
3 RW 99 SNMP-server community
SNMP-server community a RO
SNMP-Server RO community oneCommunityRead
not run cdp
!
!
!
control plan
!
!
Line con 0
password 7 abdelkrim
opening of session
no activation of the modem
line to 0
line vty 0 4
password 7 aaaaa
opening of session
escape character 5
!
max-task-time 5000 Planner
NTP-period clock 17175037
Server NTP B.B.B.B
Server NTP A.A.A.Aend
Alex,
It's your GRE tunnel:
interface Tunnel0
IP 2.2.2.1 255.255.255.252
source of Dialer0 tunnel
destination of IP_forti tunnel
myvpn card cryptoYou also have routing set by it.
You don't need a GRE tunnel, nor do you need the road to tunnel if you want just IPsec tunnel.
-
I'm tring to define you Site IPSEC to a VPN of Site connection a md seem to run into problems. Can someone look over my setup and lead me in the right direction:

#sh ROUTER1 card crypto
'TOWIFE' 1-isakmp ipsec crypto map
Peer = 10.2.2.1
Expand the access list IP HusbandToWife
HusbandToWife 192.168.1.0 ip access list allow 0.0.0.255 192.168.3.0 0.0.0.255
Current counterpart: 10.2.2.1
Life safety association: 4608000 Kbytes / 3600 seconds
PFS (Y/N): N
Transform sets = {}
3DESHMAC,
}
Interfaces using crypto card TOWIFE:
FastEthernet0/0ROUTER1 #sh running-config
Building configuration...Current configuration: 1027 bytes
!
version 12.4
horodateurs service debug datetime msec
Log service timestamps datetime msec
no password encryption service
!
ROUTER1 hostname
!
boot-start-marker
boot-end-marker
!
!
No aaa new-model
memory iomem size 5
IP cef
!
!
!
!
!
Authenticated MultiLink bundle-name Panel
!
!
!
!
!
Archives
The config log
hidekeys
!
!
crypto ISAKMP policy 1
preshared authentication
address of spike key crypto isakmp 10.2.2.1
!
!
Crypto ipsec transform-set esp-3des esp-sha-hmac 3DESHMAC
!
TOWIFE 1 ipsec-isakmp crypto map
defined peer 10.2.2.1
Set transform-set 3DESHMAC
match address HusbandToWife
!
!
!
!
!
!
interface FastEthernet0/0
10.1.1.1 IP address 255.255.255.0
automatic duplex
automatic speed
card crypto TOWIFE
!
interface FastEthernet0/1
IP 192.168.1.1 255.255.255.0
automatic duplex
automatic speed
!
IP forward-Protocol ND
!
!
IP http server
no ip http secure server
!
HusbandToWife extended IP access list
ip permit 192.168.1.0 0.0.0.255 192.168.3.0 0.0.0.255
!
!
!
!
!
control plan
!
!
Line con 0
line to 0
line vty 0 4
!
!
endRouter3 #sh card crypto
'TOHUSBAND' 1-isakmp ipsec crypto map
Peer = 10.1.1.1
Expand the access list IP WifeToHusband
WifeToHusband 192.168.3.0 ip access list allow 0.0.0.255 192.168.1.0 0.0.0.255
Current counterpart: 10.1.1.1
Life safety association: 4608000 Kbytes / 3600 seconds
PFS (Y/N): N
Transform sets = {}
3DESHMAC,
}
Interfaces using crypto card TOHUSBAND:
FastEthernet0/0Router3 #sh running-config
Building configuration...Current configuration: 1033 bytes
!
version 12.4
horodateurs service debug datetime msec
Log service timestamps datetime msec
no password encryption service
!
name of host Router3
!
boot-start-marker
boot-end-marker
!
!
No aaa new-model
memory iomem size 5
IP cef
!
!
!
!
!
Authenticated MultiLink bundle-name Panel
!
!
!
!
!
Archives
The config log
hidekeys
!
!
crypto ISAKMP policy 1
preshared authentication
spike key crypto isakmp 10.1.1.1 address
!
!
Crypto ipsec transform-set esp-3des esp-sha-hmac 3DESHMAC
!
TOHUSBAND 1 ipsec-isakmp crypto map
defined peer 10.1.1.1
Set transform-set 3DESHMAC
match address WifeToHusband
!
!
!
!
!
!
interface FastEthernet0/0
address 192.168.3.1 IP 255.255.255.0
automatic duplex
automatic speed
card crypto TOHUSBAND
!
interface FastEthernet0/1
10.2.2.1 IP address 255.255.255.0
automatic duplex
automatic speed
!
IP forward-Protocol ND
!
!
IP http server
no ip http secure server
!
WifeToHusband extended IP access list
ip licensing 192.168.3.0 0.0.0.255 192.168.1.0 0.0.0.255
!
!
!
!
!
control plan
!
!
Line con 0
line to 0
line vty 0 4
!
!
endPlease provide us with 'see the crypto isakmp peer', ' show crypto ipsec his ' and 'show ip access-list' output of these two routers site2site. Y at - it all matches in ACL? Can you ping peers of each other?
---
HTH. Please rate this post if this has been helpful. If it solves your problem, please mark this message as "right answer".
Maybe you are looking for
-
The operation cannot be performed because the "Firefox" element is in use.
Whenever I try to download the latest version of Firefox on my mac, I get the following error: "The operation cannot be performed because the"Firefox"element is in use." I close Firefox and still get this error. I tried this guy 100 times and may not
-
How can I prevent my downloads to iCloud of too much space on my hard drive? I have a plan of storage iCloud, but I am doing something bad for my all 100G disk to be full! Help!
-
Why isn't my computer stay in mode 'sleep'
After a few minutes, when I put my computer in mode 'sleep' my screen saver turns on
-
Acer 1640Z crashed XP to restore aid.
Laptop spare as above Windows XP. Three days ago, I configured the Acer e parameters and inadvertently pressed a wrong button. He began to wipe everything. I turned off after 6-7 seconds, and restarting the laptop wouldn't start. 1 message: NTLDR is
-
How to restore a Windows Calendar deleted by error. Thank you very much.