Proxy HTTPS without an SSL certificate
Is it possible to configure the proxy HTTPS WSA without an SSL certificate? If so, what would be the features available? Other web and URL filtering reputations, I can't think of anything.
You can't configure the HTTPS proxy without using a cert... This certificate may be the demo one delivered with the box or one of your friends, but it must have a cert. Your desktops have either themselves trust manually or you will need to deploy some how so his confidence (if you do not they will always have cert warnings).
If you do not use the HTTPS proxy, so yes, all you get is the base url, web reputation filtering for https traffic category. HTTP traffic you will get again STROKE, Anti Malware, etc...
Tags: Cisco Security
Similar Questions
-
UTL_HTTPS on HTTPS without certificates (like the curl - insecurity)
UTL_HTTPS can be used for connections to HTPPS without having a certificate stored in a portfolio? Otherwise I get ORA-29024: certificate validation to fail.
Something like curl has the option to ignore the validation of certificate by using paratemer - unsecure.
Thank you!
This should not be possible; you will need to use a portfolio:
http://docs.Oracle.com/CD/B19306_01/AppDev.102/b14258/u_http.htm#i998681
An Oracle wallet is required to perform an HTTPS request.
see you soon
-
HTTPS without certificates / portfolio?
Hello
is this possible in Oracle 9i, 11i or 11r2 to connect to SSL sites without requiring a certificate chain filled on Oracle wallet?
Thank you
Robert.You can test your solution using a test certificate, you can request to verisign to provide.
VeriSign will provide you with a certificate of the trial which will be valid for 15 days and you can use it in your test instance.
-
Pre complains about SSL certificate on the exchange server
Hello. I just got a pre and tries to set up to communicate with an exchnage server. Pre complains and will not set up the connection with this error message: «"SSL certificate error.» Is the date and time correct? ». The date and time are correct, but the server is running a self signed certificate. This causes no problems with iPhones that use a lot of people here.
How can I fix it? It is not all parameters for this problem.
I spent the weekend trying to test and understand what was going on. I found that if I nominated the e-mail server (name after HTTPS: / / in Setup) the same as the name of certificate displayed in the Certificate Manager (Launcher > Device Info > more info > Menu > Certificate Manager), the error should disappear. The problem for me was that the name of cert in cert Manager was different from address of mail server (in my case server. [domain .local] instead of mail. ([Domain_name] .com). The transformation it seems to use is:
(1) find the certificate...
(2) CN is HTTPS: / / in the installer?
(3) If no, use error 'Verify the certificate, date and time not correct' (or whatever it is) - If Yes, go to HTTPS: / /.
(4) Exchange requires safety pin? If no, proceed to synchronize - if so, use error "unsupported of security policies.
So I looked more closely CERT and it held several common names (CN) for the cert. It seems that ANY OTHER DEVICE can filter through the list of common names, and use the one that works. The Pre uses only (whether first or last, I don't know).
So, there are two options for the certificate problem (I guess the 3rd is that you can return the phone):
FIRST SOLUTION
=====================
(1) check the name of cert in cert Manager.
(2) if it is a name that can be resolved DNS (i.e. [mail]. [mywebsite]. [com]) then change this setting in your exchange installation program in the mail server field beside the HTTPS: / /.
This will only fix it if your COMPUTER administrator has with permissions on the used field. It is possible that an alias is used on other areas
SECOND SOLUTION (as I have done)
=================================
(1) ensure that your Certification Authority is installed. You can do it by clicking START > ADMINISTRATIVE TOOLS > CERTIFICATION AUTHORITY - OR - on a computer on your network using IE/Safari/Firefox and typing http://server/certsrv. If the page is found, then you are installed, if not, then you will need to have installed.
NOTE: SBS 2003 WILL AWARD A CERT TO THE IIS WITHOUT THE ROOT CA. THIS SEEMS TO BE THE PROBLEM WITH THE AUTO CERTS GENERATED I HAD
(2) If you have not installed it, go to this topic, it is well written to get step by step instructions how to install, create demand for cert, create the cert and install the cert (it took me about 30 min). http://www.MSExchange.org/tutorials/SSL_Enabling_OWA_2003.html
NOTE: IF YOU ALREADY HAVE A CERT ON IIS, YOU NEED TO REMOVE IT AS IT IS "DEFECTIVE" CERT BEFORE YOU CAN REQUEST A NEW CERTIFICATE. YOU MAY BE ABLE TO REINSTALL OVER THE NEW CERT, BUT I DON'T KNOW
(3) open https://mail.domain.com/exchange on your computer - display details of the cert and save the file on your desktop - if you are using a laptop, you can also install it on your laptop to use for use outside the Office (this is also a good back-up that you can use to get more later if needed again).
(4) plug your pre in USB mode.
(5) slide the cert and unplug the USB cable
(6) go to cert Manager
7) tap on the icon of "Sun" at the bottom left
(8) press on the new file cert that you save in USB mode
(9) to confirm that the new cert appears with the name of the correct mail server
10) go to the e-mail program and configure the exchange account
The above will create a REAL root cert (not IIS domain root Cert) that the Pre can work with.
Really, I don't know that how/why Palm overlooked this possibility because they claimed so-called does not want to sell to companies who need strict security requirements. For me, it means a small / medium company that has limited IT supports (according to the needs, pay as you or green guy with limited knowledge). Then, why they test the GER in this environment, I'm not sure. I bet they were tested on their own network, which has all the correct methods, best practices for the management of cert. I guess it's like the developers that they have offended and almost lost their support until turned it over and said: 'sorry, we really want make you programs for our platform WebOS. ". We've just been paranoid for so long salivate us when the bell rings. "They just didn't beta test this well enough. The sad result of this is that Sprint will have to address all of the sheets because this certificate simple reading process was given only minimal recognition capabilities.
But having said that - I'm now completely in love with my pre!

I'm happy to try to help if you need it. I found a lot of the forum of solutions were not enough detailed, so do not hesitate to contact.
-
So I come back on an interesting question that can cause significant problems, unless I can find a reasonable solution.
Until yesterday a number of software programs that run in a number of remote sites were running all fortunately accessing a database. This database is accessible via the HTTPS POST and screw HTTPCLIENT, and for the past two years, everything worked fine while having the true flag to check server, the database is part of a site that is all signed and certified.
However, as of yesterday, they all decide to stop, investigate the server itself it seems that the SSL certificate has switched from the previous period. While browsing the forums of LAVA, I managed to find the reference to the problem with which a LabVIEW ca - bundle.crt file making the obsolete object so not check the validity of the new certificate.
Now, while there is here a workaround which the server verify the Pavilion from true to FALSE switching, I can do all programs work again, there's the issue of having to update and rebuild several years worth of programs. So I was expecting something that I could do outside of LabVIEW to try to solve the problem, I had considered to replace ca - bundle.crt, but I'm not sure of the validity of this idea.
So, any ideas are likely to be accepted if they mean that I don't have to go to several versions of LabVIEW.
TLDR:
I can do something with it to solve the problem?
Welll the good news is that I found a solution. The problem is that I don't know to what extent this solution will get me, it should mean at least I can reach the single database I'm targeting.
Subsequently to the rear since the database certificate (COMODO) provider I found they provide CA bundle which when used to replace the LabVIEW supplied ca - bundle.crt allows the system HTTP access the database without problem.
For remote computers, it's probably fine as it is guaranteed to have the only secure site SSL they will try to access the database that I know the data are compatible with. For my development system however it may still remain a problem that I don't know when I'll have to try to access another site certified and whether or not the new authority will work. Although in all fairness for the moment I don't know if the LabVIEW provided one or the other will work.
I might have to come back to this thread at a later date and to make the point about how everything worked.
-
ACS 3.3 invalid or corrupted SSL certificate installed
Hello
I installed a new SSL certificate to replace the old one which was about to expire. After this update of cert, I can access is no longer the ACS server for admin purposes. I get the error "cannot establish connection cifered because the certificate presented by
is invalid or damaged. Error code:-8101 "or something similar that the message is in Spanish. I tried to restart the CSAdmin service without success. I also watched ath the different CS tools but none of them does this nor is the Guide to GBA.
Is there a way to remove the certificate from the command line or other?
AY help would be appreciated because I don't want to reinstall/rebuild the server.
Thank you
Niels
If the EC is 3.3.4 or below then it can be disabled through the registry. 4.x do not have registry settings to tweak.
For 4.x
A possible workaround we have is that if a GBA backup taken prior to activation of the HTTPS is there, we can restore the same and work around the problem.
For 3.3.x
To restore access using http on your server, you must change the registry setting
to disable the https. Here's the location of the key "reg":
HKEY_LOCAL_MACHINE \SOFTWARE \Cisco \CiscoAAAv3.2 \CSAdmin \Config \HTTPSSupport
Change this value from 2 to 1.
Kind regards
~ JG
Note the useful messages
-
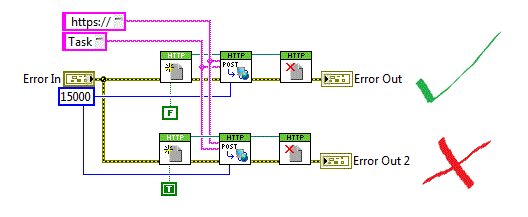
I run a Setup with SSL unpack - aka the HTTPS proxy
I'm starting to see websites giving warnings, such as:the Setup is WSA S360 version 7.7.0 - 761-latest and CAP file for parameters to customers
This PAC file is GPO'ed to windows clients. CERT of internal PKI are imported on WSA and works on many many siteshttps://registration.preemptive.com
-Use a GoDaddy Certhttps://support.Logitech.com/
-Using a DigiCert GlobalI see weak encryption (128-bit) in a self-contained outside the PC, in the two URLS, and I see warning in chrome
But above all, I see the WSA giving warnings in the client browser, and I have a few tools that uses the proxy settings in the App, but omits simply theses apps.
I guess they can't manage warnings and then just exsist...I have a category/policy work around, but I want to really just unpack to work and not to work around.
What can we do?
The WSA HTTPS proxy sometimes fails on intermediary certificates. If you download
On a box that is not behind the WSA (net by example separate, bypass, etc.) go to the web pages that you are experiencing this issue with. Click on the "lock" icon in the address box and download each of the certificates.
Then on the WSA, go Security Services/HTTPS Proxy. Click on the "managed trust roots" near the bottom. Import the certificates that you have downloaded... Usually you can just do the intermediaries and not the roots as the WSA already has them (eg. "On the list of Cisco" = yes). For some reason, I had to keep the MS one 2011...
Here is what mine looks like.
-
The SSO authentication: the SSL certificate is unknown
Hello
I'm trying to configure orchestrator solution to use SSO for authentication. Although the vCenter certificate is installed and displayed in the trust to SSL Manager, I get the following error:
The SSL certificate is unknown. You can fix this in the SSL Certificate tab.
Tried to reinstall the certificate, restart the device - without success. Username and password are correct.
I use Version of the device: 5.5.0.0 build 1282845, vCenter 5.5.0, 1476327.
How can I solve this problem?
By "vCenter certificate is installed," do you mean Certificate SSL VC (imported from https://[vc-ip]:443)?
For SSO authentication, you must also import the UNIQUE https://[sso-ip]:7444 authentication certificate
-
Discover 5.1 upgrade issue SSL certificates
So I heard that the SSL stuff in 5.1 is different from previous versions and by reading the upgrade guide, I think I'll be ok as I am now however, it is always nice to get confirmation currently we lack 5.0 on all pieces of our environment in mind, we have a Secure Gateway in our DMZ for external access and the main connection inside our LAN Server. Both servers use a CA signed SSL cert (generic) and both decide the same DNS name (on the outside using the public DNS records inside using internal DNS records). For example, if on an iPad, the connection to the server is configured as view.mydomain.com with the same DNS name resolved to our external public IP address that points to the gateway secure in the demilitarized zone. Inside, I have a DNS entry that points "display" then inside of the connection to the server. Everything works well and we don't get the guests of SSL certificate. My question is that, if I understand although it for upgrading view must import existing certificates because they are without my intervention, see below:
NOTE: If your original discovers servers already have SSL certificates signed by a CA, the upgrade.View important your signed certificate CA in Windows Server certificate store.So in that spirit I'm ok to proceed with the upgrade, as I normally would or do I need to set up an internal CA authority etc.?Thank you!I think your ok to continue, but I would go ahead and have the facility ready guide in case you have problems. Just saw a blog post by Jason Boche onto the upgrade of his laboratory experience.
-
the service of Proxy HTTPS url conversion
Hello
Based proxy wsdl based service is accessible via http://nomh get: port/ProxyServiceName I wan t to my proxy service to host a url https://hostname:port / ProxyServiceName and wsdl for this power of Attorney must also be accessible using https://hostname:port / ProxyServiceName? WSDL, I checked the required checkbox HTTPS and when I type the url https://hostname:port / ProxyServiceName it does not open, but the port is changed to https://hostname:7002 / ProxyServiceName can someone help me as well as I can also change HTTPS without changing the port.
Rgds,
RahulRahul,
Enable SSL on your Weblogic Server and set the value of the port SSL listening the current value of the listening port and change the value in the listening Port.
http://docs.Oracle.com/CD/E17904_01/Web.1111/e13707/SSL.htm#i1200848
Kind regards
Anuj -
Firefox for Mac does not recognize a valid SSL certificate
Firefox for Mac does not recognize the SSL certificate that is valid for this site, I got: https://www.georgeglazer.com. It gives a warning "not reliable." However, the Firefox for Windows does not give a warning. This happens even if I clear the cache and it happens in the Mavericks and OS of Yosemite. The certificate is up-to-date and with Comodo. Firefox for Mac is now the only browser producing these errors (v. 39, put updated) - Internet Explorer, Safari and Chrome are not. Our hosting provider has said it's probably a browser issue, perhaps having to do with intermediate certificates in Firefox being obsolete. I really hope you'll solve the problem, as it's annoying for us when we're going to do right by our customers and pay for the SSL certificate. I have attached a picture of the warning and the other from what you see on a PC: a pop-up that says it is a verified SSL certificate and gives details about the issuer, the period of validity, etc.
COMODO should you sent a link to download the file 'bundle' containing the intermediate certificates. Who needs to go in the same directory as the certificate of your site. If you are using a control panel, your host can probably help with this process. And if you bought through them, shame on them for not taking care of this for you already!
-
How to accept a new ssl certificate in Thunderbird?
7.15.15
I can't get or send emails on my cell phone two days ago.
- Neither the "Configuration Options for certificates" worked to bring in the certificate that I use that allows you to send and receive e-mail. Under the "Digital Signature" or "Encryption" when I press "Select" to select a certificate, I get the pop-up message "Certificate Manager cannot locate a valid certificate... ». When I press 'View certificates' certificate that I use is listed under 'Servers' and the 'authorities' and is up to date.
-In addition, under Tools - Options - Advanced - certificates for: "when a server requests my personal certificate", I selected "Ask Me every time" and left "query OSCP responder servers to confirm...". ', the box is checked.I think that this problem is bound to accept a new ssl certificate has been recently renewed. I've never had this problem before. How to start accepting a new certificate?
Thank you.
No you can not communicate with the server using a common product of Mozilla. In a short while you will not be able to co interact with it with any product. The operator/administrator of the server needs to fix their server to issue certificates 1024-bit or better. Or stop using TLS.
The best explanation of this change and it's because I've seen is here https://weakdh.org/
(right at the bottom of the page is what you need to do stuff)In essence, that the server does not have a security flaw serious patched and Mozilla products have been modified to not interact with servers that have not corrected the vulnerability. Vulnerability leaves you open to man in the middle attack on piracy.
-
Repeated errors of SSL certificate after upgrade to FF36
It seems as if all the sites that I visit that uses the https protocol requires a certificate exception. This is not correct. I'm a developer with 5 different browsers installed on my dev machine. Only FF has this problem.
Worse still, if I create an exception (I have not to keep doing this), I lose all the CSS and images on the site, which makes them unusable. And if the sites I need to see are unusable so FF.
I much prefer the user interface of FF and I find generally more sensitive than Chrome. But now I have to use Chrome. Visit this page.
Any suggestions to solve this problem I found does not work. It is a problem for a long time with Firefox and I've seen the problem before manifest in many versions of FF but this time he isn't going away and became so bad as to make me change my browser.
Please someone respond with a serious answer - not about confirming or accept exceptions. There must be a root to this and what cause whether it's FF unusable upward.
Philip you were bang on! I didn't know that FF was its own proxy settings. A lot of software takes parameters of Internet Explorer in Windows. I should guess, although I still do feel unfamiliar with the new UI options in FF (which feels like an improvement but I'm still a little lost with it, is seems!).
Now, I guess my next question is what changed the proxy setting. After thinking about this subject for a short period while I realize a violin does.
It would be nice to see this information displayed on error pages certs, as well as the issue of the time. I think it would help a lot of people and save time!
Boy, I was upset with FF the other day. Thanks for fixing that. It has not been caused by the FF and there was an underlying reason caused by other software.
Thanks again.
Rob -
Thunderbird does not recognize a self-signed SSL certificate
Dear support,
I have a very strange problem that I don't understand.
I run a server ISP offering IMAP and TLS/SSL HTTPS encryption. Both services use the same SSL certificate issued by RapidSSL/GeoTrust Server edward.ennabe.de
When I open an https connection to the server, Firefox correctly solves the certificate chain and use the certification authority root Equifax (which is correct).
However, when I try to connect to a mailbox via Thunderbird, all I get in the hierarchy of certificates is my server edward.ennabe.de. I don't think that it's "working as intended", or is it?Is something wrong with my Thunderbird or My Dovecot configuration? What is really strange that firefox recognizes it correctly.
Thanks in advance
Kind regards
ZeroEnna
In Thunderbird, click the 'Détails' tab in the display of the certificate.
See all certificates of CA listed in the field "Certificate hierarchy" also installed in your Thunderbird certificate store?
When checking this look for the tab 'authorities '.
If there are no certificates listed in the missing chain in the Thunderbird certificate store (for some reason any), you can try to export it in Firefox and import them into Thunderbird. -
SSL certificate not used for Admin Server connections
I have a GoDaddy SSL certificate installed on OS X Server 10.11.4. It works very well for the web server (https). Connection via Server.app off-site, produces a warning SSL and self-signed certificate. There is a related error regularly in newspapers:
[[servermgr_certs]:-[CertsRequestHandler(KeychainOpenSSLExport) exportIdentity:]: SecKeychainItemExport (certificateChain) no certificate string available, defaulting to a cert leaves only
Any suggestions? I reinstalled the cert...
You must raise the.app of 3rd party certificate. Follow these steps:
1: Open Keychain Access.
2: select the system Keychain in the keychains list.
3: find the preference of identity com.apple.servermgrd and double click it.
4: select your SSL certificate 3rd party in the contextual menu of preferred certificate.
5: Press the button Save changes. You will be asked to authenticate.
6: restart the server or restart the process of servermgrd to activate the changes.
Now when you connect to the server from a remote device using.app, sign in using your valid 3rd party SSL certificate and avoid mistakes.
Reid
Apple Consultants Network
Author - "El Capitan Server - Foundation Services.
Author - "El Capitan Server - Collaboration & control»
Author - "El Capitan Server - Advanced Services '.
: IBooks exclusively available in Apple store
Maybe you are looking for
-
Can't find where to turn off LTE / 4G on the airwaves of the ipad 2
-
After trying a story custom in the Section for the protection of personal information (not security as the first mentioned section), I went back to "remember history" but now, there are NO button to click to prevent the 3rd party cookies to enter com
-
Satellite Pro M70 recovery disk - where can I get a new one?
Hi all. I'm trying to help my friend to untangle its M70 that was severely marred by many pieces of adware, malware, trojans... you name it. It has very little installed or stored on it so a complete reinstallation seems to be the easiest option. How
-
Programmatically change the selected cell/line of control multi-column listbox
I want to programmatically change the selected cell of a multicolumn list box whose selection Mode is set to highlight the whole line. I would use this to highlight the line whatever the list box, I chose to. It would work the same way if the user
-
How can I remove the password block that will appear when the signature in windows xp?
When I turn on my computer there is a block of password that appears. I don't want to.