Renewal of certificates Cisco ISE Admin and EAP
Hi on board,
Maybe I'm asking a rather stupid question here, but anyway :)
Currently, I think about how renew a certificate admin/EAP on a node of the ISE and the effect on the endpoint authentication.
Here's the thing that I do when I install initially an ISE node
1.) creation of CSR on ISE (PAN) - CN = $FQDN$ and SAN = 'name of FQDN as well. "
2.) sign CSR and certificate of bind on the ISE node - done
Now, after 10 months or two (if the certificate is valid for one year) I want to renew the certificate of admin/EAP ISE.
Creation of CSR: I can't use the $FQDN$ like CN, because there is still the current certificate (CN must be unique in the store, right?)
So what to do now? I really need to create a temporary SSC and make the admin/EAP certificate, remove the current certificate, and then create a new CSR? There must be a way better and more important to do nondisruptive.
How you guys do this in your deployments?
Thanks again in advance, and sorry if this is a silly question.
Johannes
You can install a new certificate on the ISE until he's active, Cisco recommends to install the new certificate before the expiry of the old certificate. This period of overlap between the former certificate expiration date and the new certificate start date gives you time to renew certificates and to plan their installation with little or no downtime. Once the new certificate enters its valid date range, select the EAP or HTTPS protocol. Remember, if you turn on HTTPS, there will be a restart of the service
Renewal of certificate on Cisco Identity Services Engine Configuration Guide
Tags: Cisco Security
Similar Questions
-
Access VPN ASA and cisco ISE Admin
Hello
Currently I'm deployment anyconnect VPN Solution for my client on ASA 9.2 (3). We use the ISE 1.3 to authenticate remote users.
In the policy stipulates the conditions, I put the condition as below.
Policy name: Anyconnect
Condition: DEVICE: Device Type Device Type #All Device Types #Dial - in access EQUALS AND
RADIUS: NAS-Port-Type is equal to virtualI'm authenticating users against the AD.
I am also restrict users based on group membership in authorization policies by using the OU attributes.
This works as expected for remote users.
We also use the ISE to authenticate administrators to connect to the firewall. Now what happens is, Cisco ASA valid also against policy, administrators and their default name Anyconnect.
Now the question is, how to set up different political requirement for access network admin and users the same Firewall VPN.
Any suggestions on this would be a great help.
See you soon,.
Sri
You can get some ideas from this article of mine:
http://ltlnetworker.WordPress.com/2014/08/31/using-Cisco-ISE-as-a-generic-RADIUS-server/
-
Cisco ISE CLI and GUI password expires
I got Cisco ISE version 1.1 I am facing a problem with the password CLI and GUI, it expires and I can not connect, I do password reset using the DVD of the ISE.
I naviguer navigate to the CLI of ISE, then perform the following commands:
conf t
password policy
no password-expiration-enable
and reset the password of admin GUI, using the command:
# reset-passwd ise admin request
from the interface of ISE I delete option for the devil admin account after 45 days.
but after 60 days, the password expire again.
kindly advise what to check for this question expires.
Hello Mostafa,
Yes, the last answer was more towards past-mgmt GUI because in the majority of cases, it happens with the administrator account on the user interface. I need to know if you've restarted the ISE after disabling the expiration of the CLI, because what I read a few weeks in an internal fault which password policy settings are not preserved on cli after restart so just to check could please check current on CLI w settings / help to see the race. in the password policy.
~ BR
Jatin kone* Does the rate of useful messages *.
-
Renew the certificate - Cisco VPN (the router)
Hello!
I have to renew my certificate and I need to do this, generate a new CSR.
My doubt is if I generate a new CSR my current certificate will be lost or not.
The command I use to generate a new CSR is:
# crypto ca enroll XXX
Thank you.
Hi Anderson,
If you create the CSR in a different trustpoint, you will not lose the current certificate.
It may be useful
-Randy-
-
Cisco ISE synchronization and NTP server
I am currently implementing Cisco ISE to our customer.
But having a little problem Cisco ISE cannot synchronize with NTP server.
Keep in mind, NTP servers in AD.
Currently, Cisco ISE synchronize just at the local level.
Cisco ISE implemented distributed mode, when there are two Cisco ISE installed on VMware (Administration & monitoring primary & secondary node), and another is the device (political Service node).
As a result of it might not sync server NTP and the ISE of Cisco, Cisco ISE often OUT-OF-SYN.
Is there a solution for this problem?
Gandhi,
This is a known issue, I have crossed upwards and have not read that you use AD as your NTP server, there have been problems with integration of the ISE and ACS with AD as their ntp source, please use another device like sources ntp, for example a router.
Thank you
Tarik Admani
* Please note the useful messages *. -
Cisco ISE 1.3 using 802.1 x authentication for wireless clients
Hello
I fell into a strange question attempts to authenticate a user more wireless. I use as PEAP authentication protocol. I have configured my strategy of authentication and authorization, but when I come to authenticate the selected authorization policy are by default that denies access.
I used the 802. 1 x conditions made up to match the computer authentication, then the user authentication
AUTHENTICATION OF THE COMPUTER
football match
Box
Wireless
Group of ads (machine)
AUTHENTICATING USERS
football match
Box
Wireless
Ad (USER) group
has been authenticated = true
Here are the measures taken to authenticate any ideas would be great.
Request for access received RADIUS 11001
11017 RADIUS creates a new session
15049 evaluating Policy Group
Service evaluation 15008 selection policy
15048 questioned PIP
15048 questioned PIP
15048 questioned PIP
15006 set default mapping rule
11507 extract EAP-response/identity
12300 prepared EAP-request with PEAP with challenge
11006 returned Challenge RADIUS access
Request for access received RADIUS 11001
11018 RADIUS re - use an existing session
12302 extracted EAP-response containing PEAP challenge-response and accepting as negotiated PEAP
12318 has successfully PEAP version 0
12800 first extract TLS record; TLS handshake began
12805 extracted TLS ClientHello message
12806 prepared TLS ServerHello message
12807 prepared the TLS certificate message
12810 prepared TLS ServerDone message
prepared 12305 EAP-request another challenge PEAP
11006 returned Challenge RADIUS access
Request for access received RADIUS 11001
11018 RADIUS re - use an existing session
12304 extract EAP-response containing PEAP stimulus / response
prepared 12305 EAP-request another challenge PEAP
11006 returned Challenge RADIUS access
Request for access received RADIUS 11001
11018 RADIUS re - use an existing session
12304 extract EAP-response containing PEAP stimulus / response
prepared 12305 EAP-request another challenge PEAP
11006 returned Challenge RADIUS access
Request for access received RADIUS 11001
11018 RADIUS re - use an existing session
12304 extract EAP-response containing PEAP stimulus / response
12318 has successfully PEAP version 0
12812 extracted TLS ClientKeyExchange message
12804 message retrieved over TLS
12801 prepared TLS ChangeCipherSpec message
12802 completed TLS prepared message
12816 TLS handshake succeeded
12310 full handshake PEAP completed successfully
prepared 12305 EAP-request another challenge PEAP
11006 returned Challenge RADIUS access
Request for access received RADIUS 11001
11018 RADIUS re - use an existing session
12304 extract EAP-response containing PEAP stimulus / response
12313 PEAP inner method started
11521 prepared EAP-request/identity for inner EAP method
prepared 12305 EAP-request another challenge PEAP
11006 returned Challenge RADIUS access
Request for access received RADIUS 11001
11018 RADIUS re - use an existing session
12304 extract EAP-response containing PEAP stimulus / response
11522 extract EAP-Response/Identity for EAP method internal
11806 prepared EAP-internal method call offering EAP-MSCHAP VERSION challenge
prepared 12305 EAP-request another challenge PEAP
11006 returned Challenge RADIUS access
Request for access received RADIUS 11001
11018 RADIUS re - use an existing session
12304 extract EAP-response containing PEAP stimulus / response
11808 extracted EAP-response containing EAP - MSCHAP VERSION challenge response to the internal method and accepting of EAP - MSCHAP VERSION such as negotiated
15041 assessment political identity
15006 set default mapping rule
Source sequence 22072 Selected identity
15013 selected identity Source - AD1
24430 Authenticating user in Active Directory
Identity resolution 24325
24313 is looking to match accounts at the junction
24315 account in the domain
24323 identity resolution detected single correspondent account
Application for CPP 24343 successful logon
24402 user Active Directory authentication succeeded
Authentication 22037 spent
EAP-MSCHAP VERSION 11824 passed authentication attempt
prepared 12305 EAP-request another challenge PEAP
11006 returned Challenge RADIUS access
Request for access received RADIUS 11001
11018 RADIUS re - use an existing session
12304 extract EAP-response containing PEAP stimulus / response
11810 extract EAP-response to the internal method containing MSCHAP stimulus / response
11814 inner EAP-MSCHAP VERSION successful authentication
11519 prepared EAP-success for the inner EAP method
12314 PEAP inner method completed successfully
prepared 12305 EAP-request another challenge PEAP
11006 returned Challenge RADIUS access
Request for access received RADIUS 11001
11018 RADIUS re - use an existing session
12304 extract EAP-response containing PEAP stimulus / response
ISE 24423 was not able to confirm the successful previous machine authentication
15036 assessment authorization policy
15048 questioned PIP
15048 questioned PIP
Looking 24432 user in Active Directory - xxx\zzz Support
24355 fetch LDAP succeeded
Recovery of user 24416 of Active Directory groups succeeded
15048 questioned PIP
15048 questioned PIP
15004 Matched rule - default
15016 selected the authorization - DenyAccess profile
15039 rejected by authorization profile
12306 successful PEAP authentication
11503 prepared EAP-success
11003 returned RADIUS Access-Reject
Endpoint 5434 conducted several failed authentications of the same scenarioWindows will only be machine authentication when you start, then test you can't just disconnect/connect the pc, you will need to restart. The solution is called cisco anyconnect nam and eap-chaining.
-
Can someone please recommend a good book on ISE 2.0... again 2.0
IMHO there is no good book on ISE 2.0 because there is no book of ISE 2.0 at all.
IM aware of only three books on ISE:
- CiscoPress: Unified Cisco ISE BYOD and blocked access
- CiscoPress: CCNP security SISAS 300-208 official Cert Guide
- Syngress: Practical deployment of Cisco Identity Services Engine (ISE): concrete examples of deployments AAA
I did the first and also know each other. They n 't ISE 2.0 coverage. And looking at the table of contents of the third, it looks no better.
Not a book at all, but the best documentation for ISE is ISE product page design guides: http://www.cisco.com/c/en/us/support/security/identity-services-engine/products-implementation-design-guides-list.html
-
Hello!!
We are working on a mapping between a promoter Cisco ISE group and a user group in Active Directory, but the customer wants the mapping through a RADIUS SERVER, to avoid the ISE by querying directly activate Directory.
I know it is possible to use a RADIUS SERVER as source of external identity for ISE... but, is possible to use this RADIUS SERVER for this sponsor group manages?
Thank you and best regards!
Hi Rodrigo,
The answer is no. There is no way to integrate the portal Sponsor config with a RADIUS server. Your DB for authentication Portal Sponsor options;
AD
LDAP
User internal ISE DBSent by Cisco Support technique iPhone App
-
Renewal certificate HTTPS in Cisco ISE
Hello
A few months ago a renewed our certificate for eap. Now, I must renew the HTTPS certificate. ISE said that there will be a 'significant' downtime, the renewal of the certificate.
What exactly is this judgment? Cannot authenticatie users through EAP / RADIUS? Or is that what the web interface? I can't find any documentation on this topic.
Kind regards
Michael Trip
The only downtime, you can expect the renewal of the HTTPS certificate is:
1. for changes to HTTPS protocols, a restart of the ISE services is required, which creates a few minutes of downtime. You will not be able to access the GUI round 10-15 minutes.
2. If you are using a self-signed certificates in a distributed deployment, the primary self-signed certificate must be installed in the approved certificate of the secondary server ISE store. Similarly, the secondary self-signed certificate must be installed in the approved certificate of the server main ISE store. This allows the ISE server to mutually authenticate each other. The deployment might break. If you renew certificates from a third-party certification authority, check if the root certificate chain has been changed and update the store of certificates approved in the ISE as a result.
Here is the document containing the same steps. I have highlighted for your convenience.
Rgds,
Jousset
~ Make rate of useful messages.
-
Cisco ISE 1.2 and the ad group
Hello
I have Cisco ISE installed on my EXSi server for my test pilot. I added several ad groups at ISE as well.
I created a condition of authorization policy, that is WIRELESS_DOT1X_USERS (see screenshot)
Basically, I just replicate the default Wireless_802.1X and added Network Access: EapAuthentication, Equals, EAP - TLS.My problem is, I have been unable to join the wireless network, if I added my ad group to the authorization strategy (see screenshot). The user I is a member of WLAN USERS. If I removed the authorization policy group, the use is able to join the wireless network.
I have attached the screenshot of ISE newspapers as well. I checked the ISE, AD/NPS, WLC, laptop computer time and date, and they are all in sync.
I also have the WLC added as NPS client on my network.
I checked the newspaper AD and I found it, it was the local management user WLCs trying to authenticate. It is supposed to be my wireless user Credential is not the WLC.
It's the paper I received from the AD/NPS
Access denied to user network policy server.
Contact the server administrator to strategy network for more information.
User:
Security ID: NULL SID
Account name: admin
Domain account: AAENG
Account name: AAENG\admin
Client computer:
Security ID: NULL SID
Account name: -.
Full account name: -.
OS version: -.
Called Station identifier: -.
Calling the Station identifier: -.
NAS:
NAS IPv4 address: 172.28.255.42
NAS IPv6 address: -.
NAS identifier: RK3W5508-01
NAS Port Type: -.
NAS Port: -
RADIUS client:
Friendly name of client: RK3W5508-01
The client IP address: 172.28.255.42
Information about authentication:
Connection request policy name: Windows authentication for all users use
The network policy name: -.
Authentication provider: Windows
Authentication server: WIN - RSTMIMB7F45.aaeng.local
Authentication type: PAP
EAP Type: -
Identifier for account: -.
Results of logging: Accounting Information was written in the local log file.
Reason code: 16
Reason: Authentication failed due to incompatibility of user credentials. The provided username is not mapped to an existing user account or the password is incorrect.
Hello
The problem is with what ISE name, it's choosing to search of the AD. If you look in the ISE newspapers down, you'll see the username that use ISE (firstname, lastname) to search for the AD.
In your certificate template see what attribute containst name AD (possibly the dns name or email or the name of principle of RFC 822 NT), go to your profile to authenticate cerificate and use this attribute for the user name.
Thank you
Tarik Admani
* Please note the useful messages *. -
Authentication for 802.1 x and Cisco ISE printer
Hello
What is the best practice to authenticate a 802 printer. 1 x in Cisco ISE?
The printer can store a certificate for authentication and support EAP - TLS.
Thanks for the reply.
Marco
Please refer to the rules of authentication
www.Cisco.com/c/en/US/TD/docs/Security/ISE/1-2/user_guide/ise_user_guide...
-
Cisco ISE 1.1.2.145 Admin authentication via the LDAP protocol
I have configured the LDAP protocol and able to retrieve our LDAP directory structure. Now, I'm trying to point authentication "Admin Access" Source 'External identity', which is the new LDAP IS I created. But I couldn't find an option to authenticate locally if for some reason the LDAP configuration does not work. I learned that the ISE can automatically return to local auth as external sources Idenitity are inaccessible. How can I test the LDAP authentication with breaking them our Admin Access? I thought to open two parallel sessions, one with Super Admin account Local and one with the domain account. But I noticed that ISE communication is smart enough for the closing session/connection no matter what other sessions in different browsers so, basically, I can't open two parallel sessions the same machine to test. Suggestions? or am I missing something here?
Thanks in advance.
Hi Srinivas,
Even if you configure LDAP as a source of external identity of admin access, you can always internal relief without having locked. According to the ISE user guide:
During the operation, Cisco ISE is designed to "fall back" and try to perform the internal identity database authentication, if the communication with the external identity store has not been established, or if it fails. In addition, whenever an administrator for which you have configured external authentication launches a browser and initiates a logon session, the administrator must still the option authentication of demand through the local Cisco ISE database by choosing 'Internal' to the Selector drop-down storage of identity in the Connect dialog box.
http://www.Cisco.com/en/us/docs/security/ISE/1.1/user_guide/ise_man_identities.html#wp1351543
Please see the attached screenshot by my lab ISE:
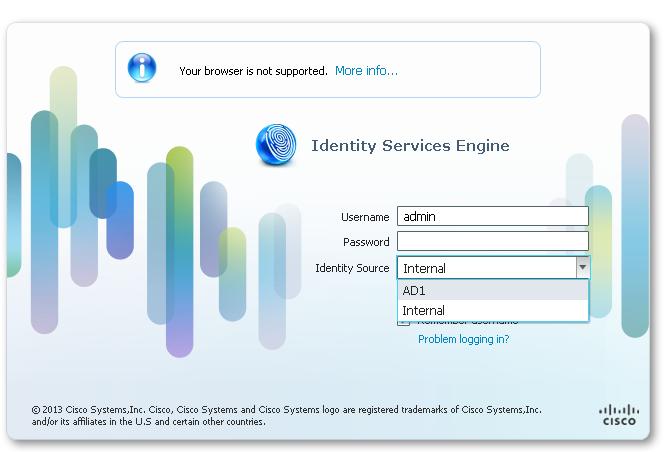
I configured the admin authentication against AD, but I still see both 'Internal' and 'AD' at the time of the connection.
I hope this helps.
Thank you
Aastha
-
Renew the certificate of identity on Cisco ASA 5505, do I have to renew all user certificates?
n00b questions.
I have to renew my SSL certificate of identity soon on my Cisco ASA 5505. I'll have to renew all my certificates for client on their devices, so they can establish a vpn tunnel?
Hi dsartoros,
If you encounter a self signed (generated locally) identity certificate renewed, then you will need to download this certificate on the clients so that they can connect without getting "untrusted server certificate error".
If you renew a certificate issued by a 3rd party CA (sending of CSR to CA) and certificate, then you will not need to make any changes on the client as they already trust the certification authority that issues the certificate first root.
Kind regards
Dinesh MoudgilPS Please rate helpful messages.
-
Renew the certificate in Cisco ACS for PEAP authentication
Hi, we installed in laptops wireless customer a certificate created by Cisco ACS to authenticate, but its about to expire.
How can I do to renew the certificate whithout affecting users.
(1) Yes, we can generate a new cert but install the latter.
(2) install generated new cert on the client.
(3) install the new cert in ACS.
Good plan and will probably work.
Kind regards
~ JG
Note the useful messages
-
Cisco ise 1.2 installation of certificates for the issue of cluster ise
Hello everyone I have a cluster ise 4 devices. 1 main admin/secondary monitor, admin of admin/primary secondary 1 and 2 knots of policy
I need to install the Cert CA public on them. can I generate 1 CSR on one of the nodes, which includes a San with all the nodes DNS names?
So get 1 single certificate by the CA and export and import the cert even in all other nodes?
or do I have to generate 1 CSR for each node and 4 certificates of purchase? Wildcard certificates is not an option. Thank you
Yes, you are right. The document was created before ISE 1.2. You can generate the CSR from the interface of ISE and add SAN.
Kind regards
Jatin kone
* Make the rate of useful messages *.
Maybe you are looking for
-
Photosmart C5180 driver for Windows 7 RC
Are there drivers (beta or not) available for this printer all-in-One on Windows 7? The Vista 64-bit driver should work on Windows 7 as well, but the installation program stops due to OS version control.
-
Apple ID disabled after that contact iTunes support for transaction cannot be complete
OK my thread before all my problem that I can't buy the itunes gift card... Now, a big problem happens. so my problem has been resolved and I can sent a gift to my friends, but then the error came again. I contact apple support chat and they even sai
-
Access to the eccentric camera and GPS problem
I love this phone and use it for a few weeks now. I know that the update just worked for T-mobile, and the biggest problem he treats is the camera. My question is if anyone knows if this update fixes other issues? One of them is how he takes the X bi
-
G4 HP 250: very weak wifi signal
today I bought hp 250 g4 with no windows installed .i 10 operating system but I have a very low two meters from the router wifi signal.im and I do not get signal.i must get exacly near router to get 2-3 bars. I plugged a USB wifi adapter, I had and I
-
How can I get rid of the Office 2007 trial and subsequent updates automatically downloaded Version
Hi all. I have a PC that came with the Trial Version of Office 2007. I was very happy with Office 2003, so I loaded it up. Now, my PC automatically downloaded the service pack 2007 and whenever I go to open any document it asks for a product key.