Split tunnel with ASA 5510 and PIX506.
Hello
I have the production between Asa 5510 (main office) and Pix 506 VPN tunnel. It is configured so that all traffic is encrypted and moves through the tunnel. This includes remote users behind Pix Internet traffic. I would like to use split tunnel and direct Internet traffic hitting the web directly from Pix instead of going through the tunnel. How can I do this safely? Please see current config Pix below:
:
6.3 (5) PIX version
interface ethernet0 car
interface ethernet1 10baset
ethernet0 nameif outside security0
nameif ethernet1 inside the security100
clock timezone EDT - 5
clock to summer time EDT recurring 2 Sun Mar 2:00 1 Sun Nov 02:00
No fixup protocol dns
fixup protocol ftp 21
fixup protocol h323 h225 1720
fixup protocol h323 ras 1718-1719
fixup protocol http 80
fixup protocol they 389
fixup protocol rsh 514
fixup protocol rtsp 554
fixup protocol sip 5060
No fixup protocol sip udp 5060
fixup protocol 2000 skinny
fixup protocol smtp 25
fixup protocol sqlnet 1521
no correction protocol tftp 69
names of
allow VPN 192.x.x.x 255.255.255.0 ip access list one
LocalNet ip access list allow a whole
pager lines 20
opening of session
monitor debug logging
logging warnings put in buffered memory
logging trap warnings
Outside 1500 MTU
Within 1500 MTU
IP address outside 24.x.x.x 255.255.255.0
IP address inside192.x.x.x 255.255.255.0
IP audit name Outside_Attack attack action alarm down reset
IP audit name Outside_Recon info action alarm down reset
interface IP outside the Outside_Recon check
interface IP outside the Outside_Attack check
alarm action IP verification of information
reset the IP audit attack alarm drop action
disable signing verification IP 2000
disable signing verification IP 2001
disable signing verification IP 2004
disable signing verification IP 2005
disable signing verification IP 2150
PDM logging 100 information
history of PDM activate
ARP timeout 14400
Global 1 interface (outside)
NAT (inside) 0 access-list LocalNet
Route outside 0.0.0.0 0.0.0.0 24.x.x.x
Timeout xlate 03:00
Timeout conn 01:00 half-closed 0:10:00 udp 0: CPP 02:00 0:10:00 01:00 h225
H323 timeout 0:05:00 mgcp 0: sip from 05:00 0:30:00 sip_media 0:02:00
Sip timeout - disconnect 0:02:00 prompt Protocol sip-0: 03:00
Timeout, uauth 0:05:00 absolute
GANYMEDE + Protocol Ganymede + AAA-server
AAA-server GANYMEDE + 3 max-failed-attempts
AAA-server GANYMEDE + deadtime 10
RADIUS Protocol RADIUS AAA server
AAA-server RADIUS 3 max-failed-attempts
AAA-RADIUS deadtime 10 Server
AAA-server local LOCAL Protocol
Enable http server
enable floodguard
Permitted connection ipsec sysopt
Crypto ipsec transform-set esp-3des esp-md5-hmac AMC
map UrgentCare 10 ipsec-isakmp crypto
card crypto UrgentCare 10 corresponds to the VPN address
card crypto UrgentCare 10 set counterpart x.x.x.x
card crypto UrgentCare 10 value transform-set AMC
UrgentCare interface card crypto outside
ISAKMP allows outside
ISAKMP key * address x.x.x.x 255.255.255.255 netmask
ISAKMP identity address
part of pre authentication ISAKMP policy 20
ISAKMP policy 20 3des encryption
ISAKMP policy 20 md5 hash
20 2 ISAKMP policy group
ISAKMP duration strategy of life 20 86400
SSH timeout 15
Console timeout 0
Terminal width 80
Cryptochecksum:9701c306b05151471c437f29695ffdbd
: end
I would do something by changing the acl that applies to your crypto card. You want to know what you want to support above the tunnel and then deny other networks.
If you have:
192.168.3.0/24
192.168.4.0/24
10.10.10.0/24
172.16.0.0/16
Do something like:
VPN access list allow 192.x.x.x ip 255.255.255.0 192.168.3.0 255.255.255.0
VPN access list allow 192.x.x.x ip 255.255.255.0 192.168.4.0 255.255.255.0
VPN access list allow 192.x.x.x ip 255.255.255.0 10.10.10.0 255.255.255.0
VPN access list allow 192.x.x.x 255.255.255.0 ip 172.16.0.0 255.255.0.0
Then when the traffic is destined for something other than these networks, it will go not to the ISP instead of the tunnel.
HTH,
John
Tags: Cisco Security
Similar Questions
-
Help with a VPN tunnel between ASA 5510 and Juniper SSG20
Hello
We have a customer wanting to configure a VPN Site to Site tunnel between a new purchased 5510 of ASA located in his direction with its Juniper SSG20 Office, located in the main office. We contacted HP and they send us a Cisco professional to do the job.
After 2 days from 16:00 to 22:00 and error and countless hours of research online and nunerous calls, we are still unable to get traffic from the network of agencies to enter the tunnel.
Main branch
1.1.1.2 1.1.1.1
----- -----------
192.168.8.0/24 | ASA|-----------------------------------| Juniper | 192.168.1.0/24
----- -----------
192.168.8.254 192.168.1.254According to Cisco professionals, the tunnel is now in place but no traffic through. We are unable to ping anything on the network on the other side (192.168.1.0/24). We receive timeout ping all the time. The Cisco professional told us it's a routing or NAT problem and he's working on a solution!
Through research, I came across a post on Experts-Exchange (here) [the 1st comment on the original post] which States "...". that both sides of the VPN must have a different class of LAN for the VPN to work... " Would that be our problem?
It has become a critical issue to the point that he had to replace the Cisco ASA with a temporary Juniper SSG5 on another subnet (192.168.7.0/24) to get the tunnel upward and through traffic until the ASA VPN issue is resolved and I didn't need to say that the client is killing us!
Help is very appreciated.
Thank you
1. Yes, ping package from the interface of the ASA is considered valuable traffic to the LAN of Juniper.
SAA, need you traffic from the interface source ASA's private, because interesting to determine by crypto ACL MYLIST traffic between 192.168.8.0/24 and 192.168.1.0/24.
You will also need to add the following configuration to be able to get the ping of the interface of the ASA:
management-private access
To initiate the ping of the private interface ASA:
ping 192.168.1.254 private
2. the default time before the next generation of new key is normally 28800 seconds, and if there is no interesting traffic flowing between 2 subnets, he'll tear the VPN tunnel down. As soon as there is interesting traffic, the VPN tunnel will be built automatically into the next generation of new key. However, if there is traffic before generating a new key, the new tunnel will be established, and VPN tunnel will remain standing and continue encrypt and decrypt traffic.
Currently, your configuration has been defined with ITS lifetime of 3600 seconds GOLD / 4608000 kilobytes of traffic before the next generate a new key (it will be either 3600 seconds, or 4608000 kilobytes period expires first). You can certainly change it by default to 28800 seconds without configuring kilobytes. SA life is negotiated between the ASA and Juniper, and whatever is the lowest value will be used.
Hope that helps.
-
Remote access VPN with ASA 5510 by using the DHCP server
Hello
Can someone please share your knowledge to help me find out why I'm not able to receive an IP address on the remote access VPN connection so that I can get an IP local pool DHCP?
I'm trying to set up remote access VPN with ASA 5510. It works with dhcp local pool but does not seem to work when I tried to use an existing DHCP server. It is tested in an internal network as follows:
!
ASA Version 8.2 (5)
!
interface Ethernet0/1
nameif inside
security-level 100
IP 10.6.0.12 255.255.254.0
!
IP local pool testpool 10.6.240.150 - 10.6.240.159 a mask of 255.255.248.0. (worked with it)
!
Route inside 0.0.0.0 0.0.0.0 10.6.0.1 1
!
Crypto ipsec transform-set esp-3des esp-md5-hmac FirstSet
life crypto ipsec security association seconds 28800
Crypto ipsec kilobytes of life - safety 4608000 association
Crypto-map dynamic dyn1 1jeu transform-set FirstSet
dynamic mymap 1 dyn1 ipsec-isakmp crypto map
mymap map crypto inside interface
crypto ISAKMP allow inside
crypto ISAKMP policy 1
preshared authentication
3des encryption
sha hash
Group 2
life 43200
!
VPN-addr-assign aaa
VPN-addr-assign dhcp
!
internal group testgroup strategy
testgroup group policy attributes
DHCP-network-scope 10.6.192.1
enable IPSec-udp
IPSec-udp-port 10000
!
username testlay password * encrypted
!
tunnel-group testgroup type remote access
tunnel-group testgroup General attributes
strategy-group-by default testgroup
DHCP-server 10.6.20.3
testgroup group tunnel ipsec-attributes
pre-shared key *.
!
I got following output when I test connect to the ASA with Cisco VPN client 5.0
Jan 16 15:39:21 [IKEv1]: IP = 10.15.200.108, IKE_DECODE RECEIPT Message (msgid = 0) with payloads: (4) SA (1) + KE + NUNCIO (10) + ID (5), HDR + VENDO
4024 bytesR copied in 3,41 0 seconds (1341 by(tes/sec) 13) of the SELLER (13) seller (13) + the SELLER (13), as well as the SELLER (13) ++ (0) NONE total length: 853
Jan 16 15:39:21 [IKEv1 DEBUG]: IP = 10.15.200.108, SA payload processing
Jan 16 15:39:21 [IKEv1 DEBUG]: IP = 10.15.200.108, processing ke payload
Jan 16 15:39:21 [IKEv1 DEBUG]: IP = 10.15.200.108, payload processing ISA_KE
Jan 16 15:39:21 [IKEv1 DEBUG]: IP = 10.15.200.108, nonce payload processing
Jan 16 15:39:21 [IKEv1 DEBUG]: IP = 10.15.200.108, payload processing ID
Jan 16 15:39:21 [IKEv1 DEBUG]: IP = 10.15.200.108, payload processing VID
Jan 16 15:39:21 [IKEv1 DEBUG]: IP = 10.15.200.108, received xauth V6 VID
Jan 16 15:39:21 [IKEv1 DEBUG]: IP = 10.15.200.108, payload processing VID
Jan 16 15:39:21 [IKEv1 DEBUG]: IP = 10.15.200.108, DPD received VID
Jan 16 15:39:21 [IKEv1 DEBUG]: IP = 10.15.200.108, payload processing VID
Jan 16 15:39:21 [IKEv1 DEBUG]: IP = 10.15.200.108, received Fragmentation VID
Jan 16 15:39:21 [IKEv1 DEBUG]: IP = 10.15.200.108, IKE Peer included IKE fragmentation capability flags: Main Mode: real aggressive Mode: false
Jan 16 15:39:21 [IKEv1 DEBUG]: IP = 10.15.200.108, payload processing VID
Jan 16 15:39:21 [IKEv1 DEBUG]: IP = 10.15.200.108, received NAT-Traversal worm 02 VID
Jan 16 15:39:21 [IKEv1 DEBUG]: IP = 10.15.200.108, payload processing VID
Jan 16 15:39:21 [IKEv1 DEBUG]: IP = 10.15.200.108, the customer has received Cisco Unity VID
Jan 16 15:39:21 [IKEv1]: IP = 10.15.200.108, connection landed on tunnel_group testgroup
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, IKE SA payload processing
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, IKE SA proposal # 1, turn # 9 entry overall IKE acceptable matches # 1
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, build the payloads of ISAKMP security
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, building ke payload
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, building nonce payload
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, Generating keys for answering machine...
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, construction of payload ID
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, build payloads of hash
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, calculation of hash for ISAKMP
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, build payloads of Cisco Unity VID
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, constructing payload V6 VID xauth
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, building dpd vid payload
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, constructing the payload of the NAT-Traversal VID ver 02
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, NAT-discovery payload construction
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, calculation of hash discovered NAT
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, NAT-discovery payload construction
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, calculation of hash discovered NAT
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, construction of Fragmentation VID + load useful functionality
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, build payloads VID
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, send Altiga/Cisco VPN3000/Cisco ASA GW VID
Jan 16 15:39:21 [IKEv1]: IP = 10.15.200.108, IKE_DECODE SEND Message (msgid = 0) with payloads: HDR SA (1) KE (4) NUNCIO (10) + ID (5) + HASH (8) + SELLER (13) + the SELLER (13) + the SELLER (13) + the SELLER (13) NAT - D (130) + NAT - D (130) of the SELLER (13) + the seller (13) + NONE (0) total length: 440
Jan 16 15:39:21 [IKEv1]: IP = 10.15.200.108, IKE_DECODE RECEIPT Message (msgid = 0) with payloads: HDR + HASH (8) + NOTIFY (11) + NAT - D (130) + NAT - D (130) of the SELLER (13) + the seller (13) + NONE (0) overall length: 168
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, processing hash payload
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, calculation of hash for ISAKMP
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, processing notify payload
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, payload NAT-discovery of treatment
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, calculation of hash discovered NAT
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, payload NAT-discovery of treatment
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, calculation of hash discovered NAT
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, payload processing VID
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, useful treatment IOS/PIX Vendor ID (version: 1.0.0 capabilities: 00000408)
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, payload processing VID
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, the customer has received Cisco Unity VID
Jan 16 15:39:21 [IKEv1]: Group = testgroup, I
[OK]
KenS-mgmt-012 # P = 10.15.200.108, status of automatic NAT detection: remote end is NOT behind a NAT device this end is NOT behind a NAT device
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, empty building hash payload
Jan 16 15:39:21 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, build payloads of hash qm
Jan 16 15:39:21 [IKEv1]: IP = 10.15.200.108, IKE_DECODE SEND Message (msgid = d4ca48e4) with payloads: HDR + HASH (8) + ATTR (14) + (0) NONE total length: 72
Jan 16 15:39:26 [IKEv1]: IP = 10.15.200.108, IKE_DECODE RECEIPT Message (msgid = d4ca48e4) with payloads: HDR + HASH (8) + ATTR (14) + (0) NONE total length: 87
Jan 16 15:39:26 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, process_attr(): enter!
Jan 16 15:39:26 [IKEv1 DEBUG]: Group = testgroup, IP = 10.15.200.108, transformation MODE_CFG response attributes.
Jan 16 15:39:26 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, IKEGetUserAttributes: primary DNS = authorized
Jan 16 15:39:26 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, IKEGetUserAttributes: secondary DNS = authorized
Jan 16 15:39:26 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, IKEGetUserAttributes: = authorized primary WINS
Jan 16 15:39:26 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, IKEGetUserAttributes: = authorized secondary WINS
Jan 16 15:39:26 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, IKEGetUserAttributes: Compression IP = disabled
Jan 16 15:39:26 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, IKEGetUserAttributes: Split Tunneling political = disabled
Jan 16 15:39:26 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, IKEGetUserAttributes: setting Proxy browser = no - modify
Jan 16 15:39:26 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, IKEGetUserAttributes: browser Local Proxy bypass = disable
Jan 16 15:39:26 [IKEv1]: Group = testgroup, Username = testlay, IP = 10.15.200.108, (testlay) the authenticated user.
Jan 16 15:39:26 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, empty building hash payload
Jan 16 15:39:26 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, build payloads of hash qm
Jan 16 15:39:26 [IKEv1]: IP = 10.15.200.108, IKE_DECODE SEND Message (msgid = 6b1b471) with payloads: HDR + HASH (8) + ATTR (14) + (0) NONE total length: 64
Jan 16 15:39:26 [IKEv1]: IP = 10.15.200.108, IKE_DECODE RECEIPT Message (msgid = 6b1b471) with payloads: HDR + HASH (8) + ATTR (14) + NONE (0) overall length: 60
Jan 16 15:39:26 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, process_attr(): enter!
Jan 16 15:39:26 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, cfg ACK processing attributes
Jan 16 15:39:27 [IKEv1]: IP = 10.15.200.108, IKE_DECODE RECEIPT Message (msgid = 49ae1bb8) with payloads: HDR + HASH (8) + ATTR (14) + (0) NONE total length: 182
Jan 16 15:39:27 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, process_attr(): enter!
Jan 16 15:39:27 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, treatment cfg request attributes
Jan 16 15:39:27 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, MODE_CFG: application received for the IPV4 address!
Jan 16 15:39:27 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, MODE_CFG: application received for the IPV4 network mask!
Jan 16 15:39:27 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, MODE_CFG: application received for DNS server address.
Jan 16 15:39:27 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, MODE_CFG: application received for the address of the WINS server.
Jan 16 15:39:27 [IKEv1]: Group = testgroup, Username = testlay, IP = 10.15.200.108, transaction mode attribute unhandled received: 5
Jan 16 15:39:27 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, MODE_CFG: application received for the banner!
Jan 16 15:39:27 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, MODE_CFG: application received for setting save PW!
Jan 16 15:39:27 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, MODE_CFG: receipt of request for default domain name!
Jan 16 15:39:27 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, MODE_CFG: application received for Split-Tunnel list!
Jan 16 15:39:27 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, MODE_CFG: application received for split DNS!
Jan 16 15:39:27 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, MODE_CFG: application received for PFS setting!
Jan 16 15:39:27 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, MODE_CFG: application received for the Proxy Client browser setting!
Jan 16 15:39:27 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, MODE_CFG: application received for the list of backup peer ip - sec!
Jan 16 15:39:27 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, MODE_CFG: application received for setting disconnect from the Client Smartcard Removal!
Jan 16 15:39:27 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, MODE_CFG: application received for the Version of the Application.
Jan 16 15:39:27 [IKEv1]: Group = testgroup, Username = testlay, IP = 10.15.200.108, Type of Client: Windows NT Client Application Version: 5.0.07.0440
Jan 16 15:39:27 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, MODE_CFG: application received for FWTYPE!
Jan 16 15:39:27 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, MODE_CFG: request received for the DHCP for DDNS hostname is: DEC20128!
Jan 16 15:39:27 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, MODE_CFG: application received for the UDP Port!
Jan 16 15:39:32 [IKEv1]: Group = testgroup, Username = testlay, IP = 10.15.200.108, in double Phase 2 detected packets. No last packet retransmit.
Jan 16 15:39:37 [IKEv1]: IP = 10.15.200.108, IKE_DECODE RECEIPT Message (msgid = b04e830f) with payloads: HDR + HASH (8) + NOTIFY (11) + (0) NONE total length: 84
Jan 16 15:39:37 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, processing hash payload
Jan 16 15:39:37 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, processing notify payload
Jan 16 15:39:37 [IKEv1]: Group = testgroup, Username = testlay, IP = 10.15.200.108, in double Phase 2 detected packets. No last packet retransmit.
Jan 16 15:39:39 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, IKE has received the response from type [] at the request of the utility of IP address
Jan 16 15:39:39 [IKEv1]: Group = testgroup, Username = testlay, IP = 10.15.200.108, cannot get an IP address for the remote peer
Jan 16 15:39:39 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, case of mistaken IKE TM V6 WSF (struct & 0xd8030048)
, : TM_DONE, EV_ERROR--> TM_BLD_REPLY, EV_IP_FAIL--> TM_BLD_REPLY NullEvent--> TM_BLD_REPLY, EV_GET_IP--> TM_BLD_REPLY, EV_NEED_IP--> TM_WAIT_REQ, EV_PROC_MSG--> TM_WAIT_REQ, EV_HASH_OK--> TM_WAIT_REQ, NullEvent Jan 16 15:39:39 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, case of mistaken IKE AM Responder WSF (struct & 0xd82b6740)
, : AM_DONE, EV_ERROR--> AM_TM_INIT_MODECFG_V6H, EV_TM_FAIL--> AM_TM_INIT_MODECFG_V6H NullEvent--> AM_TM_INIT_MODECFG, EV_WAIT--> AM_TM_INIT_XAUTH_V6H, EV_CHECK_QM_MSG--> AM_TM_INIT_XAUTH_V6H, EV_TM_XAUTH_OK--> AM_TM_INIT_XAUTH_V6H NullEvent--> AM_TM_INIT_XAUTH_V6H, EV_ACTIVATE_NEW_SA Jan 16 15:39:39 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, IKE SA AM:bd3a9a4b ending: 0x0945c001, refcnt flags 0, tuncnt 0
Jan 16 15:39:39 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, sending clear/delete with the message of reason
Jan 16 15:39:39 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, empty building hash payload
Jan 16 15:39:39 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, constructing the payload to delete IKE
Jan 16 15:39:39 [IKEv1 DEBUG]: Group = testgroup, Username = testlay, IP = 10.15.200.108, build payloads of hash qm
Jan 16 15:39:39 [IKEv1]: IP = 10.15.200.108, IKE_DECODE SEND Message (msgid = 9de30522) with payloads: HDR HASH (8) + DELETE (12) + (0) NONE total length: 80
Kind regards
Lay
For the RADIUS, you need a definition of server-aaa:
Protocol AAA - NPS RADIUS server RADIUS
AAA-server RADIUS NPS (inside) host 10.10.18.12
key *.
authentication port 1812
accounting-port 1813
and tell your tunnel-group for this server:
General-attributes of VPN Tunnel-group
Group-NPS LOCAL RADIUS authentication server
--
Don't stop once you have upgraded your network! Improve the world by lending money to low-income workers:
http://www.Kiva.org/invitedBy/karsteni -
VPN site to Site ASA 5510 and 871 w / dynamic IP
What is the best method of creating a VPN site-to site between an ASA 5510 and a router 871 where the 5510 has a static IP address and has 871, a dynamic IP address?
My ASA is running ASA software version 7.0 (5) and I can't find how to create a tunnel for a dynamic IP address via the ASDM. I have currently a tunnel between these two arrangements in place, but it was done by specifying the remote IP address, even if it is dynamic.
Any suggestions or pointers would be * very * appreciated.
-Adam
This can help but it does not show ASDM.
-
unexpected behavior with vpn, clientless ssl and smart tunnels on ASA 5510
Hi there, hope someone can help
I am able to set up a smart tunnel for an application and everything works fine, however...
Without smart tunnel, the user must navigate the portal interface (because of how he encapsulates urls and basically acts as a proxy), it is too beautiful and good and expected behavior. If a user does not enter a URL in the portal URL entry (only enters the normal address bar) she takes them outside the clientless ssl vpn portal.
Now too the point to start a smart tunnel, URL, the user types in the normal address bar is not encapsulated in the device URL, although they are still placed through our network (and note, the intelligent application of tunnel is not the browser, which is be IE). How can I know it? sites that would be blocked by a web filter are blocked with smart on but not PVD tunnels with smart tunnel.
I need to know if this is intended behavior or not and how and why this is happening?
Thanks in advance
In my view, this is how it works. If you are referring to this doc:
https://supportforums.Cisco.com/docs/doc-6172
Smart tunnel is functioning all or nothing. Which means once you turn it on for a specific process or a specific bookmark, all your traffic for this process (and the browser you are using to open the SSL Clientless session ) will pass through the ASA.
Example: Enable option ST for a process or bookmark #1 (which connected IE used to login). Opening a separate instance of the IE browser will be all traffic through the ASA, tunnel, if the new browser window belongs to the same process. All tabs on the movement of this browser browser will be smart tunnel, even to Favorites (ie. #2 favorite) are not specifically the chip in the tunnel. You must use a different browser (ie. (FireFox) in this case, if you want some of your traffic (ie. #2 favorite) is not to be smart tunnelees.
I hope this helps.
-
Between asa 5510 and router VPN
Hello
I configured ASA 5510 to vpn LAN to LAN with router 17 857. and between the routers.
between vpn routers works very well.
from the local network behind the ASA I can ping the computers behind routers.
but computers behind routers, I cannot ping PSC behind ASA.
I have configured the remote access with vpn cisco 4.X client, it works well with routers, but cannot work with asa.
the asa is connected to the wan via zoom router (adsl)
Are you telnet in the firewall?
Follow these steps to display the debug output:
monitor terminal
farm forestry monitor 7 (type this config mode)
Otherwise if its console, do "logging console 7'.
can do
Debug crypto ISAKMP
Debug crypto ipsec
and then generate a ping from one device to the back of the ASA having 192.168.200.0 address towards one of the VPN subnets... and then paste the result here
Concerning
Farrukh
-
What is is it possible to use the acl extended for split tunneling on ASA?
I'm setting up VPN IPSEC RA on SAA and I would like to know if it is possible to use the ACL extended as part of the split tunneling?
Thank you!
Yes, you can use the extended ACL. See this example:http://www.cisco.com/c/en/us/support/docs/security/asa-5500-x-series-nex...
Kind regards
Averroès.
-
LAN to Lan tunnel between ASA 5505 and 3030.
I am unable to build a tunnel vpn site-to-site between an ASA 5505 and our Cisco 3030. I tried all possible combinations except one that will work. I am able to ping each peer on the other site. Someone at - it a config between two tunnels of Lan to Lan to work between a 5505 and 3030 that works. Thank you
Hello
Please visit this link using config:
http://www.Cisco.com/c/en/us/support/docs/security/VPN-3000-series-conce...
Kind regards
Aditya
Please evaluate the useful messages.
-
Split DNS on ASA 5510 access remote vpn works not
I connect successfully to the tunnel and can ping hosts remotely by IP but am unable to browse the internet from the VPN client. Also, the resolution of host name on the remote end does not work... can only connect through the IP address. Ideas? Thanks again!
Your group policy will SUFFER a good split tunneling and divide the dns settings. But I think that you are awarded the DfltGrpPolicy rather than your group policy will SUFFER because group policy is not set in your group of tunnel, nor be transmitted from authentication.
Make a vpn-sessiondb distance 'show' to confirm what group policy is assigned to fix it, assign your group policy will BE to your group of tunnel as follows:
global-tunnel-group attributes
Will BE by default-group-policy
-heather
-
Split string with regular model and expression(10g)
Hello world
Could I ask you, your opinion on this query (tuning)?
SQL * more: version 10.1.0.4.2 - Production on Tue October 21 10:40:07 2008
Copyright (c) 1982, 2005, Oracle. All rights reserved.
Connected to:
Oracle Database 10g Enterprise Edition Release 10.2.0.3.0 - 64 bit Production
With partitioning, OLAP and Data Mining options
SQL > select * from test_1;
NR X
---------- -----------------------------------------------------------------------------------------
1 F01
2 F02
3 D01:D02
4 F03:G45:D34
5 G56:Y45:U89:E56
SQL > SELECT NR, STRING
2 FROM TEST_1
MODEL 3
4 RETURN THE UPDATED LINES
5 PARTITION BY (NR)
6 DIMENSION (POSITION 0)
MEASURES 7 (CAST (' ' AS VARCHAR2 (50)) AS STRING, X, LENGTH (REGEXP_REPLACE (X,'[^:] + ",")) + 1 NB_MOT)
8 RULES
9 (STRING [FOR POSITION 1 TO INCREMENT 1 NVL(NB_MOT[0],1)] =
10 CASES WHERE NB_MOT [0] IS NULL THEN X [0] ELSE REGEXP_SUBSTR (X [0], "[^:] +', 1, CV (POSITION)") END)
11 ORDER BY 1;
STRING OF NR
---------- --------------------------------------------------
1 F01
2 F02
3 D01
3 D02
4 G45
4 F03
4 D34
5 G56
5 Y45
U89 5
5 E56
11 row (s) selected (s).
Execution plan
----------------------------------------------------------
0 SELECT STATEMENT Optimizer = ALL_ROWS (cost = 5 card = 5 bytes = 325
)
1 0 SORTING (ORDER BY) (cost = 5 card = 5 bytes = 325)
2 1 MODEL (ORDERED) SQL (cost = 5 card = 5 bytes = 325)
3 2 TABLE ACCESS (FULL) 'TEST_1' (TABLE) (cost = 4 = 5 bytes map = 325)
Kind regards
Salim.Why?
How long takes now?
Can you explain?
Kind regards.
LOULOU.
-
VPN split tunnel with 1811W and IAS RADIUS problems
I am very new to the implementation of a VPN IPSEC with a Cisco router. I know very well on the way to do it with a PIX / ASA, but the controls are a bit different in IOS, where my questions. Here is what is happening, I can connect to the VPN with the Cisco VPN Client. I would assign it an address of my ip pool that I created, but when I try to access the remote network somehow, I can't. I ran a tracert and what is really weird, is that I get the external IP address of the 1811W as my first jump when I list an internal IP address of the remote network (it also fixes the device FULL domain name, so I know that my DNS configuration is correct). I will list my config to the 1811W as well as the screenshot of the tracert. I've removed all the passwords that are encrypted, but they are there in the router config and I am able to connect to the network and click the IAS server behind it. Please excuse the config as we took it during another TI provider so that it can have a few additional entries that may not be necessary that I have not yet cleaned.
Tracert:
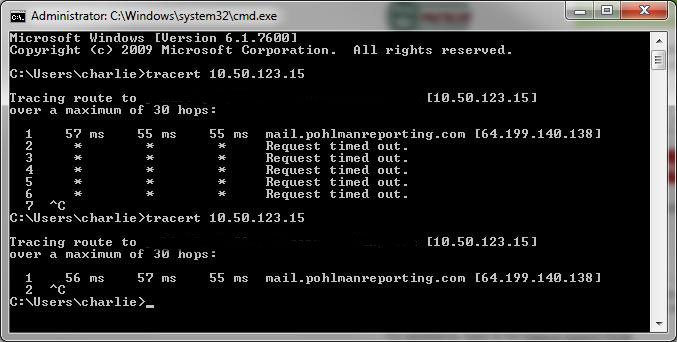
And here's the full config:
Building configuration...
Current configuration: 9320 bytes
!
version 12.4
no service button
horodateurs service debug datetime msec
Log service timestamps datetime localtime show-time zone
encryption password service
!
hostname RTR01
!
boot-start-marker
boot-end-marker
!
logging buffered 8192
enable password 7
!
AAA new-model
!
!
AAA authentication login userauthen local radius group
AAA authorization groupauthor LAN
!
!
AAA - the id of the joint session
clock TimeZone Central - 6
!
SSID dot11 internal
VLAN 5
open authentication
authentication wpa key management
Comments-mode
WPA - psk ascii 7
!
dot11 ssid public access
VLAN 10
open authentication
!
!
!
IP cef
No dhcp use connected vrf ip
DHCP excluded-address 192.168.1.1 IP 192.168.1.10
DHCP excluded-address IP 192.168.1.20 192.168.1.254
!
public IP dhcp pool
import all
network 192.168.1.0 255.255.255.0
default router 192.168.1.1
DNS-server 10.50.123.15 207.69.188.186
!
!
no ip domain search
IP domain name pohlmanreporting.com
!
Authenticated MultiLink bundle-name Panel
!
Crypto pki trustpoint TP-self-signed-3986412950
enrollment selfsigned
name of the object cn = IOS - Self - signed - certificate - 3986412950
revocation checking no
rsakeypair TP-self-signed-3986412950
!
!
TP-self-signed-3986412950 crypto pki certificate chain
certificate self-signed 01
quit smoking
!
!
password username admin privilege 15 7
username cisco password 7
username secret privilege 15 ssetech 5
Archives
The config log
!
!
!
!
crypto ISAKMP policy 1
BA 3des
md5 hash
preshared authentication
Group 2
!
crypto ISAKMP policy 10
BA 3des
preshared authentication
Group 2
!
Configuration group VPNGROUP crypto isakmp client
me?
DNS 10.50.123.15
domain domain.com
pool VPNPOOL
ACL 110
include-local-lan!
!
Crypto ipsec transform-set esp-3des-md5 esp-3des esp-md5-hmac
Crypto ipsec transform-set esp-des-md5 esp - esp-md5-hmac
Crypto ipsec transform-set esp-3des esp-sha-hmac TRANS_3DES_SHA
Crypto ipsec transform-set esp-3des esp-sha-hmac RIGHT
!
crypto dynamic-map EXA_DYNAMIC_MAP 10
Set transform-set RIGHT
market arriere-route
!
!
card crypto client EXT_MAP of authentication list userauthen
card crypto isakmp authorization list groupauthor EXT_MAP
crypto card for the EXT_MAP client configuration address respond
card crypto EXT_MAP 10-isakmp dynamic ipsec EXA_DYNAMIC_MAP
!
!
!
Bridge IRB
!
!
!
interface FastEthernet0
IP 64.199.140.138 255.255.255.248
IP access-group denied-hack-attack in
no ip redirection
no ip unreachable
no ip proxy-arp
NAT outside IP
IP virtual-reassembly
route IP cache flow
automatic duplex
automatic speed
No cdp enable
card crypto EXT_MAP
!
interface FastEthernet1
REDUNDANT INET CONNECTION description
no ip address
automatic duplex
automatic speed
!
interface FastEthernet2
!
interface FastEthernet3
!
interface FastEthernet4
!
interface FastEthernet5
!
FastEthernet6 interface
!
interface FastEthernet7
!
interface FastEthernet8
!
interface FastEthernet9
!
interface Dot11Radio0
Description 802. 11B / G interface
no ip address
!
encryption vlan 5 tkip encryption mode
!
SSID internal
!
public access SSID
!
Base speed - 1.0 2.0 basic basic-5, 5 6.0 9.0 basic-11, 0 12.0 18.0 24.0 36.0 48.0
channel 2462
root of station-role
!
interface Dot11Radio0.5
encapsulation dot1Q 5
No cdp enable
Bridge-Group 1
Bridge-group subscriber-loop-control 1
Bridge-Group 1 covering-disabled people
Bridge-Group 1 block-unknown-source
No source of bridge-Group 1-learning
unicast bridge-Group 1-floods
!
interface Dot11Radio0.10
encapsulation dot1Q 10
IP 192.168.1.1 255.255.255.0
IP access-group 130 to
IP nat inside
IP virtual-reassembly
No cdp enable
!
interface Dot11Radio1
description of the 802 interface. 11A
no ip address
Shutdown
Speed - Basic6.0 9.0 basic - 12.0 18.0 basic-24, 0-36.0 48.0 54.0
root of station-role
!
interface Vlan1
no ip address
Bridge-Group 1
!
interface Async1
no ip address
encapsulation sheet
!
interface BVI1
IP 10.50.123.1 255.255.255.0
IP access-group 105 to
IP nat inside
IP virtual-reassembly
IP tcp adjust-mss 1452
!
local IP VPNPOOL 192.168.130.1 pool 192.168.130.50
IP route 0.0.0.0 0.0.0.0 64.199.140.137
IP route 10.60.52.0 255.255.255.0 10.50.123.2
!
!
IP http server
local IP http authentication
IP http secure server
IP http timeout policy inactive 600 life 86400 request 10000
IP nat POOL 64.199.140.138 pool 64.199.140.142 netmask 255.255.255.248
overload of IP nat inside source list 120 interface FastEthernet0
IP nat inside source map of route-nat interface FastEthernet0 overload
IP nat inside source static tcp 10.50.123.14 21 64.199.140.138 21 expandable
IP nat inside source static tcp 10.50.123.11 25 64.199.140.138 25 expandable
IP nat inside source static tcp 10.50.123.11 80 64.199.140.138 80 extensible
IP nat inside source static tcp 10.50.123.11 143 64.199.140.138 143 extensible
IP nat inside source static tcp 10.50.123.11 443 64.199.140.138 443 extensible
IP nat inside source static tcp 10.50.123.10 64.199.140.138 1723 1723 extensible
IP nat inside source static tcp 10.50.123.14 21 64.199.140.139 21 expandable
IP nat inside source static tcp 10.50.123.18 80 64.199.140.139 80 extensible
IP nat inside source static tcp 10.50.123.18 443 64.199.140.139 443 extensible
IP nat inside source static tcp 10.50.123.18 64.199.140.139 3389 3389 extensible
IP nat inside source static tcp 10.50.123.14 80 64.199.140.141 80 extensible
IP nat inside source static tcp 10.50.123.14 443 64.199.140.141 443 extensible
IP nat inside source static 10.50.123.40 expandable 64.199.140.142
!
deny-hack-attack extended IP access list
permit udp 10.0.0.0 0.255.255.255 any eq snmp
deny udp any any eq snmp
deny udp any any eq tftp
deny udp any any eq bootpc
deny udp any any eq bootps
deny ip 172.16.0.0 0.15.255.255 all
deny ip 192.168.0.0 0.0.255.255 everything
allow an ip
!
recording of debug trap
record 10.50.123.15
access-list 99 allow 10.0.0.0 0.255.255.255
access-list 99 allow 69.63.100.0 0.0.1.255
access-list 102 permit ip 10.50.123.0 0.0.0.255 10.60.52.0 0.0.0.255
access-list 105 deny ip any host 69.63.101.225
105 ip access list allow a whole
access-list 110 permit ip 10.50.123.0 0.0.0.255 192.168.130.0 0.0.0.255
access-list 111 deny ip 10.50.123.0 0.0.0.255 10.10.0.0 0.0.255.255
access-list 111 deny ip 10.50.123.0 0.0.0.255 10.60.52.0 0.0.0.255
access-list 111 allow ip 10.50.123.0 0.0.0.255 any
access-list 112 deny ip 10.50.123.0 0.0.0.255 172.0.0.0 0.0.0.255
access ip-list 112 allow a whole
access-list 120 allow ip 192.168.1.0 0.0.0.255 any
access-list 130 allow udp 192.168.1.0 0.0.0.255 host 10.50.123.10 eq field
access list 130 permit tcp 192.168.1.0 0.0.0.255 host 10.50.123.10 eq field
access list 130 permit tcp 192.168.1.0 0.0.0.255 host 10.50.123.16 eq www
access list 130 permit tcp 192.168.1.0 0.0.0.255 host 10.50.123.16 eq 443
access-list 130 deny ip any 10.0.0.0 0.255.255.255
access-list 130 ip allow a whole
SNMP-server community no RO
!
!
!
map of route-nat allowed 10
corresponds to the IP 111
!
!
!
RADIUS-server host 10.50.123.13 auth-port 1645 acct-port 1646 hits 7
!
control plan
!
Bridge Protocol ieee 1
1 channel ip bridge
!
Line con 0
exec-timeout 120 0
line 1
Modem InOut
StopBits 1
Speed 115200
FlowControl hardware
line to 0
line vty 0 4
location * Access Virtual Terminal allowed only from internal network *.
access-class 99 in
exec-timeout 0 0
connection of authentication userauthen
transport input telnet ssh
!
max-task-time 5000 Planner!
WebVPN cef
!
WebVPN context Default_context
SSL authentication check all
!
no go
!
!
endYou must also create NAT exemption for traffic between your internal network to the VPN Client pool.
You have the following NAT 2 instructions:
overload of IP nat inside source list 120 interface FastEthernet0
IP nat inside source map of route-nat interface FastEthernet0 overloadFor the 120 access list, please add the following:
120 extended IP access list
1 refuse the ip 10.50.123.0 0.0.0.255 192.168.130.0 0.0.0.255
Uses of "-nat ' ACL 111 route map, please also add the following:
111 extended IP access list
1 refuse the ip 10.50.123.0 0.0.0.255 192.168.130.0 0.0.0.255
Then ' delete ip nat trans * "after the above changes and try to connect again.
Hope that helps.
-
VPN, Internet and a Split Tunnels traffic
Please attached photo because I hope that explains what I really want to do, but here's the break down.
When a VPN Client connects to remote access to 1-ASA5510 I want all Internet traffic to send to 2 - ASA5510 instead of back to the default route. When it comes out 2-ASA5510, it passes through the content filter. 2 - ASA5510 has Split Tunnel put in place and we are trying to do away with Tunnel from SPlit.
I hope this is clear enough.
Any ideas would be helpful
Dan
Dan,
Difficult but doable! First of all, there is a nice feature in the ASA that allows configuration of remote proxy based on VPN profile by: -.
Group Policy <> attributes
use a MSIE-proxy-server method
Internet Explorer-proxy server value x.x.x.x
activate Internet Explorer-proxy local-bypass
Well Yes you guessed it - works only on Microsoft Internet Explorer.
I don't think that any policy based routing would work for you - bad luck.
But you can try another feature - traffic through the tunnel, which is normally used in the topllogy of EasyVPN: -.
Configuration of the ASA at the bottom, I probably would test this with the IP address of the 2651 router!
HTH.
-
Hello support,
Probably a simple question and can be buried in these forums (but I'm not).
I am trying to replace one 5510 with another 5510 and have all kinds of difficulties. Devices the PAT against the external interface have no problem out, but anything with a 1:1 NAT cannot. Cries of an ARP issue; However, to restart the switch and firewall are without effect. Is there something else I could potentially be missing. Configurations are completely reversed. And the firewall, that the I'm replacing has no problem going out with NAT (static) 1-to-1. Any ideas?
Hello
I assume you mean a L3 switch that you begin with the ASA?
If this isn't the case, then where is the gateway of your ASA L3 and who manages this device?
One thing that comes to mind associated with ARP is that if you use several public subnets on your ASA. For example 30 for network connection between your site and the ISP and some 28 as a public subnet for purposes of NAT static. Then you may experience problems IF your software has changed to 8.4 (3) or something higher.
If ARP is the problem then it is of course the option that makes you check the original interfaces of ASAs (connected to the ISP) MAC address and configure this same MAC address to the new WAN ASAs interface to the ISP.
You can actually go under the interface and deliver MAC address with the command
0000.1111.2222 Mac address
In addition, naturally when it comes to configurations and firewall rules you can always use the command "packet - trace" to simulate the packets from your local network for the EXTENDED or WAN network to the local network and see the race passes through completely.
-Jouni
-
Automatic update AIP-SSM-10 and ASA 5510 (Beginner)
I see that it is possible to automate the updates of the ASA 5510 and AIP SSM via FTP on my own server. Is it possible to automate the download directly from Cisco.com?
Thank you!
Jeremy
Jeremy, the answer to your question is correct, as far as the Cisco products are concerned. So I wrote a PERL app that does exactly that, and I published an article about it in the June 2007 issue of Sys Admin magazine. Here's the article online: http://www.samag.com/documents/s=10128/sam0706a/0706a.htm
And it is also on my site, with a tar of scripts to:
http://www.LHB-consulting.com/pages/apps/index.html
Good luck.
-Lisa
-
ASA 5510 to Sonicwall TZ205 - ASA 9.1.6 upgrade breaks Tunnel VPN
After reclassification of 8.4.5 to 9.1.6 my tunnel from site to site between an ASA 5510 and a Sonicwall TZ 205 is 'up' and I can ping the external interface of the other but I can't ping LAN to LAN.
Hey Kevin,
They should not be a difference on the config VPN between these versions, can you try to run a packet - trace on the SAA or place a screenshot inside while sending traffic.
Example:
entry Packet-trace within the icmp < src="" ip=""> 8 0
Capture the vpn inside the match ip host
host interface It may be useful
-Randy-
Maybe you are looking for
-
I can't change my security questions, I have many attempts, how do I fix? Also, I forgot my phone code where I'm trying to change my security questions... help please!
-
Lost with upgrade to El Capitan photos
I upgraded to El Capitan and moved photos to iphoto to Photos and lots of photos were lost. I have photos on an external hard drive. Is it possible to take pictures in iphoto and copy them on dropbox and stop using iphoto? I'm tired of the problems
-
Touch screen does more to 22 degrees.
ENVY TouchSmart j051ea 15 HP I noticed that my touch unresponsive to the touch when the temperature exceeds 22 ° C. To be clear, that the laptop isn't hot, the laptop is at room temperature. Nothing to do with the fan or the computer laptop cooling.
-
Several programs, I can't uninstall
I have several programs, I would like to get rid of that. When I try to uninstall it, I get a message that says "the system administrator has set policies to prevent this installation. When I click on this box, another box says "you don't have suffic
-
Arrival blackBerry Smartphones Facebook does not work
Check Facebook... close places, etc., does not work. He has in the past, but with the recent update of FB is no longer. I checked everything on the phone and FB - everything looks good. Any ideas? Tom