The 5.5 SSL certificate installation device Orchestrator
Need for additional documents and advice on installing the Orchestrator's SSL certificate. My approach resulted in a failure to download error. Method: keystore file downloaded using selection in Configuration Orchestrator interface. Removed the embedded free signed certificate and key private using commands in the key tool. Issues for a new original keystore certificate using the keytool command. Treaty of applicantst on a windows certification authority. Installed at root, intermediate, and new machine cert in original keystore, checked the chain and tried to install the key file using the GUI with a download error received.
See the following resources:
- http://mighty-virtualization.blogspot.de/2012/09/VCO-51-appliance-how-to-fix.html
- http://www.vcoteam.info/articles/learn-VCO/181-work-with-VCO-over-SSL.html
- http://KB.VMware.com/kb/2007032
Also, could you give more information about the error, you receive (for example, trace error stack in the log files)?
Tags: VMware
Similar Questions
-
The existing migration ssl certificate win 4.2 device acs acs 3.2
Hello
We have the acs server that has the ssl running certficate(certifcate authority) in the acs 3.2 for eap - tls user authentication windows version.
We want the same be migrated to application 4.2 (appliance) acs. I tried in different ways to push the certificate but I couldn't.
I tried the System Configuration Thru--> ACS certificate--> certificate installation to install ACS--> download the certificate file
As I mentioned the FTP server IP address, identification information, name and path
But if I submit the application sound giving the directory not found or incorrect credentials.
In FTP records its showing like this
April 15, 2011 19:41:55 Session 4, Peer 10.190.249.40 PASS welcome2acs
April 15, 2011 19:41:55 Session 4, Peer 10.190.249.40 230 user logged
April 15, 2011 19:41:55 Session 4, Peer 10.190.249.40 FTP: successful connection
April 15, 2011 19:41:55 Session 4, Peer 10.190.249.40 CWD D:\FTP-ACS-AU
April 15, 2011 19:41:55 Session 4, Peer 10.190.249.40 D:\FTP-ACS-AU 550: no such file or directory.
April 15, 2011 19:41:55 Session 4, Peer 10.190.249.40 FTP: connection is closed.
April 15, 2011 19:41:55 Session 4, Peer 10.190.249.40 Session closed by peer
April 15, 2011 19:44:47 Session 5, Peer 10.190.249.40 the FTP Server session
April 15, 2011 19:44:47 Session 5, Peer 10.190.249.40 the FTP Server session
April 15, 2011 19:44:47 Session 5, Peer 10.190.249.40 USER ftpadmin
April 15, 2011 19:44:47 Session 5, Peer 10.249.40 331 ok, need password username
April 15, 2011 19:44:47 Session 5, Peer 10.190.249.40 FTP: connection attempt by: ftpadmin
April 15, 2011 19:44:48 Session 5, Peer 10.190.249.40 PASS welcome2acs
April 15, 2011 19:44:48 Session 5, Peer 10.190.249.40 230 user logged
April 15, 2011 19:44:48 Session 5, Peer 10.190.249.40 FTP: successful connection
April 15, 2011 19:44:48 Session 5, Peer 10.190.249.40 DLG FTP - ACS - to THE
April 15, 2011 19:44:48 Session 5, Peer 10.190.249.40 550 FTP - ACS - to THE: no such file or directory.
April 15, 2011 19:44:48 Session 5, Peer 10.190.249.40 FTP: connection is closed.
April 15, 2011 19:44:48 Session 5, Peer 10.190.249.40 Session closed by peerCan anyone please suggest me what could be the problem in this... is my method won't?
Hello
Directory just enter ' / '.
Just browse for the file field, and shared folder opens automatically.
I hope this helps.
Kind regards
Anisha
P.S.: Please mark this thread as answered if you feel that your query is resolved. Note the useful messages.
-
CA-signed SSL certificates on vCenter 5.1 installation (server or device)
I recently updated my 5.0 to 5.1 ESXi ESXi hosts and they all kept CA-signed SSL certificates that I installed previously. I did a new install of vCenter 5.1 server where the box even ran SSO, inventory, vCenter Server and Manager Update Services. After installing, everything worked perfectly except that none of the vCenter services used my CA-signed SSL certificate - only 5.1 ESXi hosts had these.
So, I followed the instructions in replacing default vCenter 5.1 and ESXi certificates PDF found at http://www.vmware.com/resources/techresources/10318. The document is terrible. For example, page 10 lists the locations by three default certificates SSL on Windows 2008. None of these paths are correct. The first a typo of extra space between "Program" and "Data" and the other two say "Program Files" when they should have been "ProgramData". This is just the beginning of the problems.
If you follow the instructions to the letter, you'll break vCenter. I got frustrated and thought I'd give the vCenter 5.1 device a shot. With regard to the Certificates SSL signed by CA, it was worse. The vCenter 5.1 device can even automatically generate a new SSL certificate if you change the host name (turn on generation auto-certificat, change of hostname and restart). It gives an error 653 during the boot process and keeps the original of the certificate. Even bother trying the steps on page 18 of the above-mentioned guide - you will get just the same mistake 653.
It seems to me that VMware did not all tests around the CA-signed SSL certificate on vCenter 5.1 installation. It's amazing to me that the installation of the SSL certificate is so tedious for ESXi and vCenter when vShield Manager 5.1 has a very simple process that works well (and is similar to the installation procedure for Certificate SSL on the DRAC, ASR, breeding various firewalls, etc.).
I did a lot of research on Google and found various articles on the installation of the SSL certificate, but most were based on GA pre - 5.1 products. If you have any installation of certificates SSL CA-signed success with vCenter Server or device 5.1 GA, let me know how you got around some of these issues. Please indicate if your vCenter Server or device will run on a 5.1 GA ESXi host as well. Please do not answer about vCenter 5.0 - I had no problem with SSL certificates (other than it was more painful to be).
Thanks in advance,
Nate
Finally I managed to install giving him to 127.0.0.1 instead of the period of INVESTIGATION, accessible from the outside of the vCenter server, it's very well in my case the vCenter and VUM server are on the same VM but its not exactly ideal for deployments of more large.
-
http://wiki.DreamHost.com/Certificate_Domain_Mismatch_Error
Certificate SSL of Dreamhost for their mail servers only at one level of subdomain while many of their clusters of e-mail exist on a second level subdomain. In my view, this translates into an error message 'bad security' of the e-mail application.
I contacted DreamHost and they say they are unable to solve this problem, or that they will allow me to install an SSL certificate on my virtual domain pointing to my cluster e-mail (even if I had to buy a).
I understand, it is possible to manually add certificates via adb in a way similar to this: http://www.pending.io/add-cacert-root-certificate-to-firefox-os/
However what I read this: 1. does not work on the ZTE Open 2. Can only fix only navigation not the web mail client.
Is there any option that is available to me short of switching hosts?
Fabian,
Are you familiar with Firefox OS? The reason why I say this is because the e-mail client cannot create an excaption certificate. In fact, it's design. It's design: https://wiki.mozilla.org/Gaia/Email/Features#Security
This request for support to Mozilla was placed specifically for the product Firefox OS, for which there is only a single mail client.
That said many people in the Mozilla Bugzilla, have been able to show me how to find another alias for those servers that actually works and in fact corresponds to SSL certificates. Although Dreamhost support could not provide me with any such information, and such information is not actually in the DreamHost wiki.
I have a repeated insistence of Dreamhost possibility I should just live with the exceptions of SSL certificate, when there is real existing valid server names to match the certificates in question, silly.
The fact that you post this solution for one product, so that it is not yet applicable beyond useless. It serves to muddy waters.
-
replace the SSL certificate in Dell OMSA 7.2
My University is compels me to replace the Dell's SSL certificate in OMSA with a certificate from a certification authority. We use InCommon.
I generated a certificate using Microsoft IIS request. InCommon generated the certificate and got sent back links to a variety of formats.
as PKCS#7 Base64 encoded: Other available formats: as PKCS#7 Bin encoded: as X509, Base64 encoded: as X509 Certificate only, Base64 encoded: as X509 Intermediates/root only, Base64 encoded: as X509 Intermediates/root only Reverse, Base64 encoded Does anyone know what kind of certificate I need, and exactly how to install it in the apache server that runs Dell OMSA.Ok. I have an answer.
As far as I know, the interface Dell OMSA itself does not have to import the intermediate certificates (returns an error) and cannot be used to create a useful CSR (signature request) because you can't specify your own institutional settings. Our CA would not authenticate the CSR request generated by the Dell OMSA interface, even if it would incorporate new certificates (which she seems to fail at the).
The simplest approach is to generate a CSR in Windows IIS, the authenticated certificate back from your CA, and then to export to a .pfx file (private, final, intermediate entity certificate and certificates root key, extended attributes).
Use IBM tool called keyman (download www.ibm.com/developerworks). Use the version of Windows.
It can convert a .pfx file in a keystore apache in 3 easy steps. 1. create a new key file
2 import the .pfx file 3. Save the key file.
Tips on the internet suggest keeping all the passwords the same - pfx export, keystore, key, etc.
Edit the server.xml file in the apache server to use your new password.
Only downside is that your password will be readable text in the server.xml file. In the original file server.xml file Dell used system tools or java to hide passwords.
-
Error update vcenter SSL certificate?
Hello people,
I've recently upgraded to vcenter 5.1 U1a successfully.
I'm following VMware articles and a popular blog to prepare and run the certificate VMware 1.0 automation tool.
http://www.derekseaman.com/2012/09/VMware-vCenter-51-installation-part-2.html
http://www.derekseaman.com/2013/04/using-VMware-vCenter-certificate.html
Everything was pretty smooth up until I have to replace the the vcenter Server SSL certificate. Option 2 vcenter update ssl. See the attached photo.
After the error, my vcenter service will not start.
I tried to reset the password of database using vpxd.exe - p, but vcenter still does not start.
I also checked that the correct service ID is matched between vpxd.cfg and LS_ServiceID.prop.
Stuck at this point. I have since went instant return, but try to see if anyone has any suggestions?
Could this be type a bad password?
Thank you!
You mentioned the KB as well?
Concerning
Girish
-
SSL certificate tool Automation error level 3?
So I'm working out KB 2041600. I'm trying to update the certificates on two servers separate vCenter and I get the same error "can not determine if the inventory Service is registered with Single Sign-On - errorlevel is 3" while improving my certificate inventory. "." See full changelog below *.
I am 100% positive that my certificates are correct. I used Derek Seamons scripts in the past to generate my certificates and it has worked for other vCenter servers. I have completed step 1 and replace the certificate for the SSO. I'm just stuck in the service of the inventory now. I opened a case of pension as well.
==================================================================
4 update the inventory Service SSL certificate
1. update the confidence of the inventory of Single Sign-On Service
2. update the Service of Trust inventory to vCenter Server
3 update the inventory Service SSL certificate
4. back to the old inventory SSL Certificate Service
5. return to the main menu to update other services
The service chosen is: 1
[Thursday June 26, 2014 - 14:51:26.61]: services that are delivered to market as part of thi
operation s are: vCenter Inventory Service.
[Thursday June 26, 2014 - 14:51:57.01]: update of the last confidence Inventory Service operation to
Single Sign-On completed successfully.
[Thursday June 26, 2014 - 14:51:57.01]: go to the next step in the plan, which was received
Scheduler of update steps d.
==================================================================
4 update the inventory Service SSL certificate
1. update the confidence of the inventory of Single Sign-On Service
2. update the Service of Trust inventory to vCenter Server
3 update the inventory Service SSL certificate
4. back to the old inventory SSL Certificate Service
5. return to the main menu to update other services
The service chosen is: 2
[Thursday June 26, 2014 - 14:53:50.92]: services that are delivered to market as part of thi
operation s are: vCenter Inventory Service.
[Thursday June 26, 2014 - 14:54:23.93]: update of the last confidence Inventory Service operation to
vCenter Server completed successfully.
[Thursday June 26, 2014 - 14:54:23.95]: go to the next step in the plan, which was received
Scheduler of update steps d.
==================================================================
4 update the inventory Service SSL certificate
1. update the confidence of the inventory of Single Sign-On Service
2. update the Service of Trust inventory to vCenter Server
3 update the inventory Service SSL certificate
4. back to the old inventory SSL Certificate Service
5. return to the main menu to update other services
The service chosen is: 3
[Thursday June 26, 2014 - 14:54:47.90]: services that are delivered to market as part of thi
operation s are: vCenter Inventory Service.
Enter the location of the new stock Service SSL cert file (default is):
C:\Certs\Inventory\chain. (MEP):
Enter the location of the new private key of Service inventory (default is: C)
(: \Certs\Inventory\rui.key):
Enter the SSO administrator user (default value is: admin@system-doma)
in):
Enter the SSO administrator password (not displayed):
[.] WARNING: Certificate ' CN = vcenter01.burdweiser.com, OU = vCenterInventoryService,.
O = Burdweiser, L = Houston, TX, C = ST = US signature uses low one-way hash (SHA
(- 1). In a secure environment, it is recommended to use SHA2 256 or higher has
algorithm of h.
[.] The supplied certificate string is valid.
[Thursday June 26, 2014 - 14:55:14.12]: last update of functioning inventory Service SSL cert
ificatsanitai re has failed:
[Thursday June 26, 2014 - 14:55:14.14]: unable to determine if the inventory Service is registe
Red with Single Sign-On - errorlevel is 3
In my case, I was trying to replace the certificates before an upgrade from 5.1 to 5.5. The easiest route taken was to uninstall SSO and the inventory service and then proceed to the upgrade to 5.5. After that, replace the certificates.
-
VCenter Server 5.1 SSL certificate update - error
Hi all
We set up a new Windows 2008 R2 server as a vCenter Server 5.1
Now, I try to install the new certificates for all parts of vCenter (server, inventory, web client service,...) with the Windows certification authority.
I'm stuck at the update server certificate SSL vCenter with the 'Certificate SSL Automation Tool'.
This is part 5. in this guide (5. the cmd screen shot):
All credentials are correct, but I still get the same error (vc-update - ssl.log):
[26.04.2013 - 10:42:54, 99]: copy the new certificates and keys 'C:\ProgramData\VMware\VMware VirtualCenter\SSL. '... »[26.04.2013 - 10:42:55: 00]: creating the PKCS certificate file...Could not reload vCenter SSL certificates[26.04.2013 - 10:42:56: 22]: ""cannot reload the server vCenter SSL certificates. " The certificate could not be unique. » »[26.04.2013 - 10:42:56, 24]: new certificates and keys deleting...[26.04.2013 - 10:42:56: 25]: restoration of the certificates and the original keys...1 Datei () kopiert.1 Datei () kopiert.1 Datei () kopiert.[26.04.2013 - 10:42:56: 25]: attempt to restore...Could not reload vCenter SSL certificates[26.04.2013 - 10:42:57, 08]: ""cannot reload the server vCenter SSL certificates. " The certificate could not be unique. » »[26.04.2013 - 10:42:57: 10]: new certificates and keys deleting...[26.04.2013 - 10:42:57: 10]: restoration of the certificates and the original keys...1 Datei () kopiert.1 Datei () kopiert.1 Datei () kopiert.[10: 42:57, 13 - 26.04.2013]: failure of the update of the certificate of vCenter.So I tried the manual way, as it is mentioned in this guide:I'm stuck here too, get a 'result of Method Invocation: vpx.fault.SecurityConfigFault ' after ""Invoke method ': "
- Go to https://localhost/mob/?moid=vpxd-securitymanager & vmodl = 1 on the server vCenter Server and load the certificates for the configuration using the managed object browser.
- Click continue if you are prompted with a warning on this certificate.
- Enter a vCenter Server administrator user name and password when prompted.
- Click reloadSslCertificate.
- Click the calling method. If successful, the window displays this message: result of Invocation of method: Sub.
I tried to fix this, but there is not really a solution for this:
http://communities.VMware.com/thread/429035
so, I need help with this question
SOLVED!
Steps to follow:
1. stop the vCenter service
2. search for your ID in LS_ServiceID.prop in the folder C:\ProgramData\VMware\VMware VirtualCenter
3. copy this ID (e.g. {C4672589-9258-42B1-90E2-1EF268BBD402}: 5 )
4. change your vpxd.cfg in the same folder and replace
vCenterService with
your ID 5. start vCenter Service
Then, the SSL automation tool works!
You need to undo changes.
-
Discover 5.1 upgrade issue SSL certificates
So I heard that the SSL stuff in 5.1 is different from previous versions and by reading the upgrade guide, I think I'll be ok as I am now however, it is always nice to get confirmation currently we lack 5.0 on all pieces of our environment in mind, we have a Secure Gateway in our DMZ for external access and the main connection inside our LAN Server. Both servers use a CA signed SSL cert (generic) and both decide the same DNS name (on the outside using the public DNS records inside using internal DNS records). For example, if on an iPad, the connection to the server is configured as view.mydomain.com with the same DNS name resolved to our external public IP address that points to the gateway secure in the demilitarized zone. Inside, I have a DNS entry that points "display" then inside of the connection to the server. Everything works well and we don't get the guests of SSL certificate. My question is that, if I understand although it for upgrading view must import existing certificates because they are without my intervention, see below:
NOTE: If your original discovers servers already have SSL certificates signed by a CA, the upgrade.View important your signed certificate CA in Windows Server certificate store.So in that spirit I'm ok to proceed with the upgrade, as I normally would or do I need to set up an internal CA authority etc.?Thank you!I think your ok to continue, but I would go ahead and have the facility ready guide in case you have problems. Just saw a blog post by Jason Boche onto the upgrade of his laboratory experience.
-
Hello
I config the view to connect the server of ssl certificate, I have config ssl with the kb certificate
but when I configed the ssl certificate, I opened IE, open connect with https server.
certificate is issued is not disabled certificate.how do?
When I use the customer display to connect the server to connect, he invites "the host name in the certificate is invalid or does not match to.
My way
1. Add keytool for the path of the system:
a. in your host server view connection or security, right-click workstation, and then click Properties.
b. click on the Advanced tab.
c. click on Environment Variables.
d. in the Group of system variables, select path and click on modify.
e. type the path to the JRE directory in the Variable value text box. For example,.
< install_directory > \VMware\VMware View\Server\jre\bin.2. open a command prompt and run this command using keytool to generate a key file:
keytool - genkeypair - keyalg 'RSA' - keysize 2048 - keystore keys.jks - storepass secret
keytool - certreq-file certificate.csr - keystore keys.jks - storepass secret
3. I asked the certificate with my CA certsrv in the field. I asked for the advanced certificate and copy the text file
for example
-----BEGIN NEW CERTIFICATE REQUEST-
MIICrDCCAZQCAQAwZzELMAkGA1UEBhMCY24xCzAJBgNVBAgTAnNoMQswCQYDVQQHEwJzaDEQMA4G
A1UEChMHdm1jbG91ZDEQMA4GA1UECxMHdm1jbG91ZDEaMBgGA1UEAxMRVk1DT04udm1jbG91ZC5j
b20wggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCNEbwcZeW + 5PNsRgk65lB4NQ1AMMTb
HbtGRwQIbaBLgvUxZlfNucu7nckC6bdg3brXDRIbZp3vjQCpZLsHjNPmRGkoVRhwikEaOoou9UWA
b + 0HScCMFZShkULCrAJV2nKuPuUl5JO3lRBecRBKiRm37yf53c9HYmh + nexQaz0dX + jfOm4M3fcg
Ujfl + UAky9KOjMrHQ5MJjoTqZCV2uMpiGOaG8h/8kruEyISiSn89KOAgmA90Iq32SItA09pJG/V5
GWbIUXSE5JUF70ZemdXN31dajmwXH0ML + SLEQfUjQeH1vGZ/v0nG51wIf5QOJTJ7pJ2aKEsaNcBz
6PvjWcdpAgMBAAGgADANBgkqhkiG9w0BAQUFAAOCAQEABnjFSmKYINAvBJ4S1Hy5rnPdunaVcsQA
y5WkVf7ouRIm7Zew2tjzr4KN2Xt41alJlLUtfpGfw5xqGSvZBxuxVltW5dEYRitf84trysdeQAuB
t103qAchdBpziPAOumu2mk/PjW + kt/t0o5CuZ81vCD8/KB9KX94YW9vB83Q9B7Mkg3g3G7Clzyim
Ogwq/VVErAu0udbW30Bp0RuSkj9CBwofpYsC + sdcVeduXV1vjpl4 + Fo + BWt1JkrT2aLkAJ4uhvzw
V7vPmYlqpuauS79iZowU + uXir3F75GBxKYsWRXia5D/AiDRd/xLS9K62o2QnVjV7qpshIlv6IIzN
MOLDzA is
-NEW APPLICATION FOR CERTIFICATE OF END-I copyed the text in my ca server asked for the catificate
4. when the certificate was requested, I download the certificate chain and export the certificate and the ssl certificate
5 keytool - keystore viewcs1.jks - storepass password - importcert-alias rootca-folder rootca.der.cer
6 keytool - importcert - keystore viewcs1.jks - storepass password - keyalg 'RSA' - trustcacerts-alias viewcs1-file viewcs1.der.cer
7 copy the jks and the certificate of "\VMware\VMware View\Server\sslgateway\conf".
8. create locked.properties and set the keyfile property
keyfile = Keys.P12
KeyPass = MY_PASSshops = jks
9 restart connect services
What is the problem? I'm doing this. I don't know the step that I did wrong.
pls help me solve the problem.
thansks much
This problem is puzzle me long.
I hope someone can provide the video
My email: [email protected]
When you created the certificate did you use namesake who would use people accessing VDI? For example, if people acecss VDI with https://vdi.blank.com , then you would have to create your certificate using the same.
-
Sefl-signed ssl certificate is not possible?
 Hi all
Hi all
the ILO is not yet possible to let flex' webservice or httpservice to connect to a
WebService https secured by a self-signed certificate? There is absolutely no reason
for me to buy a 'real' certificate just for encryption purposes.
I installed crossdomain.xml on the target server, the Web service works well when pasting
the URL in the browser and I have installed the certificate in IE (which I use here), then
is no error and shows the OWL small lock in the address bar. But Flex refuses to work,
except for run the application locally (means by clicking on "run" in flex builder).
I'm using Flex 2.01 so important.
So, could someone help me? Or Flex so ignorant for self-signed webservices?
Good bye
sysForHi sysfor,
I am using the appropriate production and development self-signed SSL certificates in & don't test, no problems so far.
Flex/Flash is not the authentication of SSL certificates - this task is delegated to the browser.So I suppose you are faced with a different type of problem - your crossdomain.xml is not configured correctly.
Have you checked the log of policyfiles.txt?
Another point, you're probably doing is called direct URL (https://myhost/path). Instead, you must use a relative path. For example if your swf file has been downloaded from the server myhost, then he should just make the calls in / path.See you soon,.
Dmitri. -
Pre complains about SSL certificate on the exchange server
Hello. I just got a pre and tries to set up to communicate with an exchnage server. Pre complains and will not set up the connection with this error message: «"SSL certificate error.» Is the date and time correct? ». The date and time are correct, but the server is running a self signed certificate. This causes no problems with iPhones that use a lot of people here.
How can I fix it? It is not all parameters for this problem.
I spent the weekend trying to test and understand what was going on. I found that if I nominated the e-mail server (name after HTTPS: / / in Setup) the same as the name of certificate displayed in the Certificate Manager (Launcher > Device Info > more info > Menu > Certificate Manager), the error should disappear. The problem for me was that the name of cert in cert Manager was different from address of mail server (in my case server. [domain .local] instead of mail. ([Domain_name] .com). The transformation it seems to use is:
(1) find the certificate...
(2) CN is HTTPS: / / in the installer?
(3) If no, use error 'Verify the certificate, date and time not correct' (or whatever it is) - If Yes, go to HTTPS: / /.
(4) Exchange requires safety pin? If no, proceed to synchronize - if so, use error "unsupported of security policies.
So I looked more closely CERT and it held several common names (CN) for the cert. It seems that ANY OTHER DEVICE can filter through the list of common names, and use the one that works. The Pre uses only (whether first or last, I don't know).
So, there are two options for the certificate problem (I guess the 3rd is that you can return the phone):
FIRST SOLUTION
=====================
(1) check the name of cert in cert Manager.
(2) if it is a name that can be resolved DNS (i.e. [mail]. [mywebsite]. [com]) then change this setting in your exchange installation program in the mail server field beside the HTTPS: / /.
This will only fix it if your COMPUTER administrator has with permissions on the used field. It is possible that an alias is used on other areas
SECOND SOLUTION (as I have done)
=================================
(1) ensure that your Certification Authority is installed. You can do it by clicking START > ADMINISTRATIVE TOOLS > CERTIFICATION AUTHORITY - OR - on a computer on your network using IE/Safari/Firefox and typing http://server/certsrv. If the page is found, then you are installed, if not, then you will need to have installed.
NOTE: SBS 2003 WILL AWARD A CERT TO THE IIS WITHOUT THE ROOT CA. THIS SEEMS TO BE THE PROBLEM WITH THE AUTO CERTS GENERATED I HAD
(2) If you have not installed it, go to this topic, it is well written to get step by step instructions how to install, create demand for cert, create the cert and install the cert (it took me about 30 min). http://www.MSExchange.org/tutorials/SSL_Enabling_OWA_2003.html
NOTE: IF YOU ALREADY HAVE A CERT ON IIS, YOU NEED TO REMOVE IT AS IT IS "DEFECTIVE" CERT BEFORE YOU CAN REQUEST A NEW CERTIFICATE. YOU MAY BE ABLE TO REINSTALL OVER THE NEW CERT, BUT I DON'T KNOW
(3) open https://mail.domain.com/exchange on your computer - display details of the cert and save the file on your desktop - if you are using a laptop, you can also install it on your laptop to use for use outside the Office (this is also a good back-up that you can use to get more later if needed again).
(4) plug your pre in USB mode.
(5) slide the cert and unplug the USB cable
(6) go to cert Manager
7) tap on the icon of "Sun" at the bottom left
(8) press on the new file cert that you save in USB mode
(9) to confirm that the new cert appears with the name of the correct mail server
10) go to the e-mail program and configure the exchange account
The above will create a REAL root cert (not IIS domain root Cert) that the Pre can work with.
Really, I don't know that how/why Palm overlooked this possibility because they claimed so-called does not want to sell to companies who need strict security requirements. For me, it means a small / medium company that has limited IT supports (according to the needs, pay as you or green guy with limited knowledge). Then, why they test the GER in this environment, I'm not sure. I bet they were tested on their own network, which has all the correct methods, best practices for the management of cert. I guess it's like the developers that they have offended and almost lost their support until turned it over and said: 'sorry, we really want make you programs for our platform WebOS. ". We've just been paranoid for so long salivate us when the bell rings. "They just didn't beta test this well enough. The sad result of this is that Sprint will have to address all of the sheets because this certificate simple reading process was given only minimal recognition capabilities.
But having said that - I'm now completely in love with my pre!

I'm happy to try to help if you need it. I found a lot of the forum of solutions were not enough detailed, so do not hesitate to contact.
-
The SSO authentication: the SSL certificate is unknown
Hello
I'm trying to configure orchestrator solution to use SSO for authentication. Although the vCenter certificate is installed and displayed in the trust to SSL Manager, I get the following error:
The SSL certificate is unknown. You can fix this in the SSL Certificate tab.
Tried to reinstall the certificate, restart the device - without success. Username and password are correct.
I use Version of the device: 5.5.0.0 build 1282845, vCenter 5.5.0, 1476327.
How can I solve this problem?
By "vCenter certificate is installed," do you mean Certificate SSL VC (imported from https://[vc-ip]:443)?
For SSO authentication, you must also import the UNIQUE https://[sso-ip]:7444 authentication certificate
-
How to install the ssl certificate in windows server 2008?
Hello
Can someone give me the steps to install the SSL certificate on my application hosted on windows server 2008 R2?
Hello
Although technet.microsoft.com should be the best forum for the problems of server below is a guide on how to install an SSL certificate.
It will be useful.
To install your newly acquired in IIS 7 SSL certificate, first copy the file somewhere on the server and then follow these instructions:
- Click on the start menu, go to administrativetools and click on Manager of Services Internet (IIS).
- Click the server name in the links on the left column. Double-click server certificates.
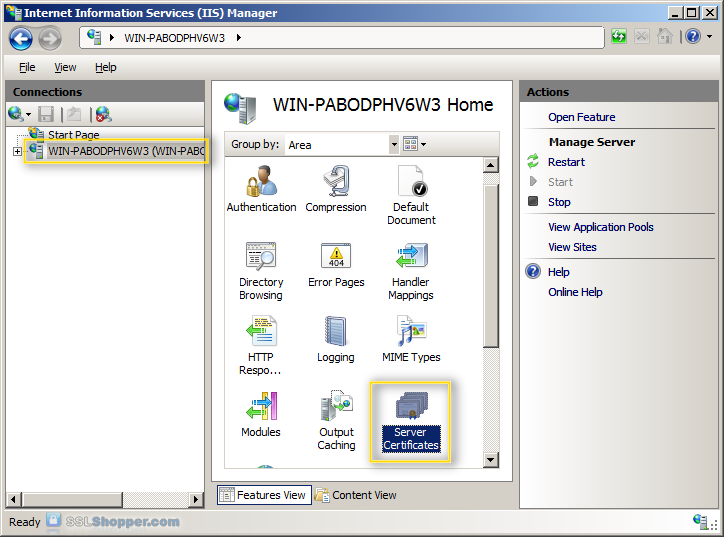
- In the Actions column to the right, click Complète Certificate Request...
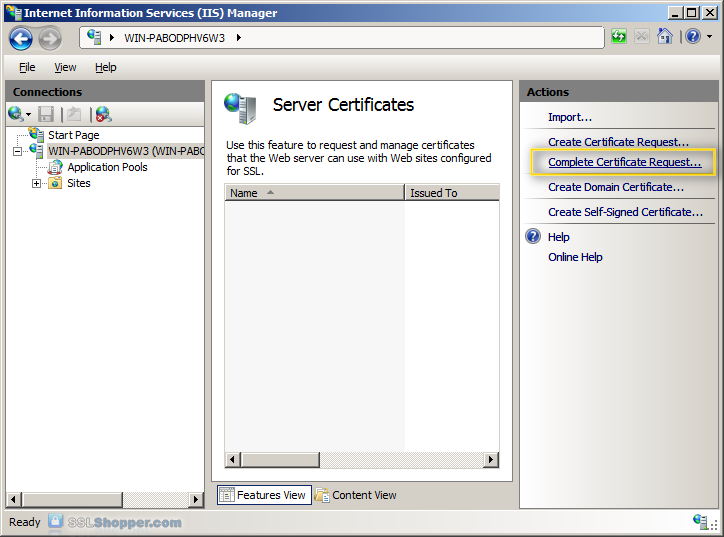
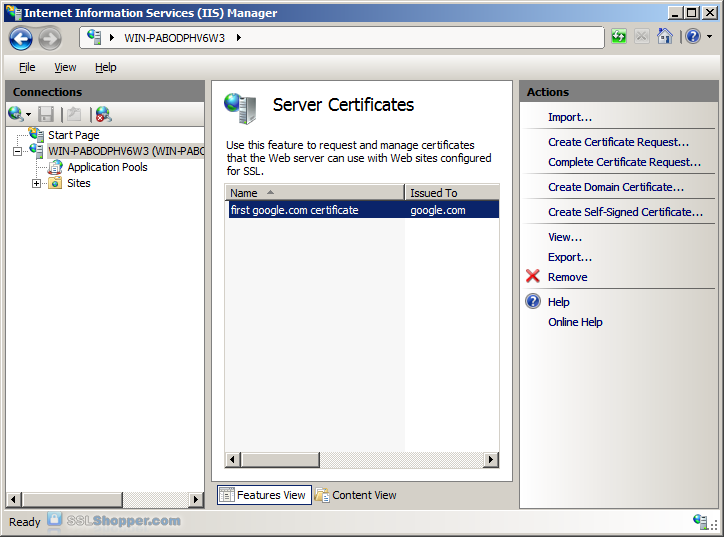
- Click on the button with the three points, and then select the server certificate that you received from the certificate authority. If the certificate does not have a .cer file extension, select this option to display all types. Enter a friendly name that you can keep track of certificate on this server. Click OK.

- If successful, you will see your newly installed in the list certificate. If you receive an error indicating that the request or the private key is not found, make sure that you use the correct certificate and you install it on the same server that you generated the CSR on. If you are sure these two things, you just create a new certificate and reissue or replace the certificate. If you have problems with this, contact your certification authority.
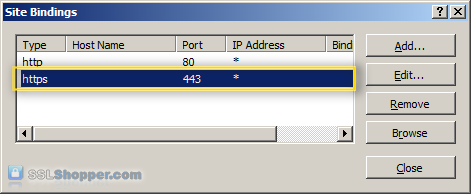
Bind the certificate to a Web site
- In the column of links on the left, expand the sites folder, and click the Web site that you want to bind the certificate to click links... in the right column.

- Click the Add... button.

- Change the Type to https , and then select the SSL certificate that you just installed. Click OK.
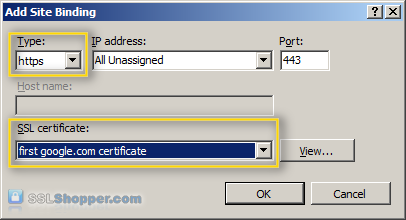
- You will now see the listed link for port 443. Click close.
Install all the intermediate certificates
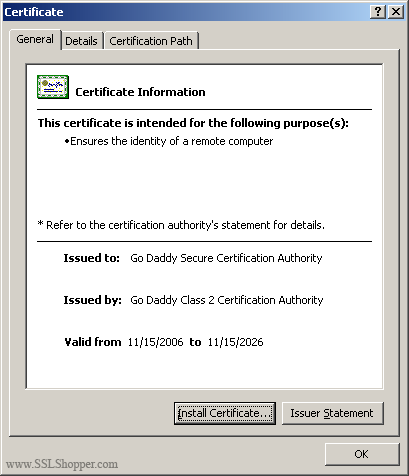
Most of the SSL providers issue certificates of server out of an intermediate certificate so you will need to install the intermediate certificate on the server as well or your visitors will receive a certificate error not approved. You can install each intermediate certificate (sometimes there are more than one) by following these instructions:
- Download the intermediate certificate in a folder on the server.
- Double-click the certificate to open the certificate information.
- At the bottom of the general tab, click the install Certificate button to start the Certificate Import Wizard. Click Next.
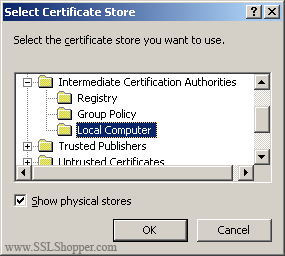
- Select place all certificates in the following store , and then click Browse.

- Select the Show physical stores checkbox, then expand the Intermediate certificate authorities folder, select the below folder on the Local computer . Click OK. Click Next, and then click Finish to complete the installation of the intermediate certificate.
You may need to restart IIS so that it starts the new certificate to give. You can verify that the certificate is installed correctly by visiting the site in your web browser using https rather than http.
Links
- Move or copy an SSL certificate on a Windows Server to another Windows Server
- How to disable SSL 2.0 in IIS 7
- How to configure the SSL in IIS 7.0
- Video tutorials to install an SSL certificate in IIS 7 to NetoMeter
Kind regards
Joel
-
EDIT: Posted KB poorly in the subject line and below (KB fixed the link shown below, was not able to change the field of the object above).
I try to follow KB 2109074 - VMware KB: vCenter server certificate validation error or a service platform for the VMware Solutions external... controller
My steps relate to the 2 k linked to in the main article: 2109074
Everything went very well in order to run the final order as get the old footprint certificate, obtain the new certificate file, etc..
When you try to run the actual command in Windows (tmore successful version that it the command I am running as follows):
"C:\Program Files\VMware\vCenter Server\python\python.exe" ls_update_certs.py - url https://vcenter.domain.local/lookupservice/sdk -fingerprints b1:35:c1:9 c: a5:59:dd:ab:3d:c2:50:e7:92:79:82:f0:b6:85:7 d: c8 - FichierCert C:\certificates\ [email protected]' user password ' Passw0rd & '
BTW, the VMware KB says:
"Note: on Windows systems, place the password in double quotes."
I have this error is (fgarlic on get-site-id):
----------------------------------------------------------------------------------------------------------
Traceback (most recent call changed):
File "ls_update_certs.py", line 19, < module >
args. Password)
File "C:\Program Files\VMware\vCenter Server\VMware identity Services\lstool\s
cripts\lstoolutil.py', line 79, modify_svc_ep_certs
raise exception ("'get-site-id lstool' failed: %d"% rc ')
Exception: "lstool get-site-id" failed: 1
----------------------------------------------------------------------------------------------------------
I tried this on 2 different vCenter servers (both 6.0u2) and get the same behavior, I have tried every combo of passwords for the PSC/SSO as Passw0rd. Pass-w0rd P@ssw0rd W34df * fdc4... etc and tried with or without quotes (2 citations, 4 citations), tried bash escape after the password like:-... and nothing works. I do not know if it is a problem of password. A few lines above I see things showing this:
----------------------------------------------------------------------------------------------------------
Caused by: com.vmware.vim.vmomi.core.exception.CertificateValidationException: Sserver certificate chain not verified
Caused by: javax.net.ssl.SSLPeerUnverifiedException: peer not authenticated at sun.security.ssl.SSLSessionImpl.getPeerCertificates (SSLSessionImpl.jagoes: 421) to com.vmware.vim.vmomi.client.http.impl.ThumbprintTrustManager$ Hostname Verifier.verify (ThumbprintTrustManager.java:296)
----------------------------------------------------------------------------------------------------------
However, I can run this command (which does not require a password) successfully:
"C:\Program Files\VMware\vCenter Server\python\python.exe" 'C:\Program Files\VMware\vCenter Server\VMware identity Services\lstool\scripts\lstool.py' get-site-id - url https://vcenter.domain.local/lookupservice/sdk" " " " "
.. It works very well and shows the SSO sso-site-default name.
Has he's other aspects of the signed certificate installation succeeded except the Search Service of that is causing my NSX Manager install to connect do not back up the Search Service...
I also get the error on the Web Client showing this:
"Error during processing of the application. Check logs WebClient vSphere for more details". (Refer to KB: https://kb.vmware.com/kb/2129053 ) ).. .caused by the same issue as well:
Anyone see this problem or knows anyway possible to recover from it without having to re - install? How to debug the .py scripts better? Is there a better documentation of VMware on the operation of these scripts? If the Search Service can be re-installed?
Any help is greatly appreciated!
Ahhhh-hah... I found the problem.
If I manually run the command:
""C:\Program Files\VMware\vCenter Server\python\python.exe"'C:\Program Files\VMware\vCenter Server\VMware identity Services\lstool\scripts\lstool.py' list - url https://vcenter.domain.local/lookupservice/sdk"
Can I get good output... The command works great.
But just as a hunch, I had to check something, I decided to see what happens when I run the same command with the '-non-cocher-cert' put it as as follows:
""C:\Program Files\VMware\vCenter Server\python\python.exe"'C:\Program Files\VMware\vCenter Server\VMware identity Services\lstool\scripts\lstool.py' list - no-check-cert - url https://vcenter.domain.local/lookupservice/sdk"
.. .and guess what? I got the SAME java error as in all the other scripts: "peer not authenticated."
So I went to the folder of scripts for VMware lstool (C:\Program Files\VMware\vCenter Server\VMware identity Services\lstool\scripts\): open lstool.py with Notepad and see that he simply calls another script in the same folder called: lstoolutil.py
I then opened that lstoolutil.py script in Notepad and did a search for the string:-non-cocher-cert... .and there has been 5 cases where different commands called this switch. I have placed in the comment (#) 5 lines composing this switch, saved the file and re-run the original script: ls_update_certs.py... .and WHAH-LABRIQUE Hooray!
Line 52: # "-non-cocher-cert."
Line 74: # "-non-cocher-cert."
Line 85: # "-non-cocher-cert."
Line 121: # "-non-cocher-cert."
Line 139: # "-non-cocher-cert."
"Then just to check I relaunch:"C:\Program Files\VMware\vCenter Server\python\python.exe"'C:\Program Files\VMware\vCenter Server\VMware identity Services\lstool\scripts\lstool.py' list - url https://vcenter.domain.local/lookupservice/sdk"
.. and can confirm that all records of service have the field "SSL trust" with the new certificate key.
Problem solved... That just leaves one a review to follow in case they encounter the same problem...
Maybe you are looking for
-
Numbers gives an error of syntax for all equations
I don't know what is happening, but I keep getting errors in syntax for multiple equations and no matter where I put it or how, he always gives the syntax error. Example B2 has 500 in there. Enter B3 B2x2 and it gives an error of syntax instead of 10
-
How can I unsubscribe from apple's music?
Looking to get out of the free after three months, who is now in charge.
-
I can't open my main email application and it will crash after opening
When I open my mail application it crash and close quickly and I can't use it
-
problem with the hp pavilion dv7 1195eo
Hello I buy Pavilion dv7 1195eo in Sweden. Reinstal Windows and now I have little problem. I can't find drivers for Ethernet controller. Now I have six unknow devices. I found the drivers on the Hp page but I can't install it. I have procesor AMD Tur
-
How the neck down width of track?
I am relatively new to the map layout (which means most of my drawings so far have been fairly simple). I'm working on my first layout of the USB and examples of manufacturer all have a width of little trace leaving the IC pad, then growing to the ~