Traffic LLC,(2)
I have install a PIX 501 in a net that has a SNA Server. The external interface of the PIX is connected in e0 interface of the router.
Is it possible the LLC,(2) packages pass for firewall and I continue to protect IP traffic?
If not, I thought to connect another router interface (e1) in the internal net for only the LLC,(2) traffic only (not via the firewall) but I don't know about the configuration of the interface of the router.
The PIX only manages the IP traffic, so unless tyou can encapsulate your traffic IP LLC, the PIX won't touch it. I guess you can bypass the PIX and connect a LLC,(2) interface that is only on the router in your home network, depends on how secure you want to be. Make sure that you do not configure an IP address on the router interface, otherwise you will run the risk of someone circumvent security of PIX.
Tags: Cisco Security
Similar Questions
-
I need to install a PIX 501 in a network. The internal interface is connected to my local network and that the external interface is connected to e0 interface of the router.
The LAN have LLC,(2) and IP traffic. Is possible to LLC,(2) traffic through the firewall without tunnel? Can I connected another interface on the router in the local network only to traffic ll2?
Thank you
The PIX only manages the IP traffic, so unless tyou can encapsulate your traffic IP LLC, the PIX won't touch it. I guess you can bypass the PIX and connect a LLC,(2) interface that is only on the router in your home network, depends on how secure you want to be. Make sure that you do not configure an IP address on the router interface, otherwise you will run the risk of someone circumvent security of PIX.
-
Traffic Inspectorate and the respect of security
I am looking at options invovling traffic inspection using duplication of port on the server virtual networking within ESXi to help with things like intrusion detection and identify anomalies in network traffic indicating potential security events.
The question is, if I deploy a solution that does this by becoming a destination port of a traffic of mirroring session, which are the gains that I receive by identifying anomalies and intrusion detection is worth, given the increased risk of the collector receives all the images in the output of virtual machines in my environment?
Thoughts / opinion welcome.
Thank you
Hello
I think that it is worth IDS, analytical, but if your system is enough big enough, then you can to deliver these items via a virtual device of Gigamon to be handled by other cool tools.
The real question will be if you do that, you have a fairly large SIEM to analyze all the possible events and correlate all your networks. If your intention is to analyze the traffic to determine what is wrong and what is not, then what is the tool that you will use for this and how does fit in your network to provide the best response times. If your answer is too slow then something reaches you. An active response is essential, but having the data to do is even more.
If you don't have a tool, then design what you want and then choose a tool which will work according to your specifications.
Best regards
Edward L. Haletky
VMware communities user moderator, VMware vExpert 2009-2015Author of the books ' VMWare ESX and ESXi in the business: Planning Server Virtualization Deployment, Copyright 2011 Pearson Education. ' Of VMware VSphere and Virtual Infrastructure Security: securing the virtual environment ', Copyright 2009 Pearson Education.
Virtualization and Cloud Security Analyst: The Practice of virtualization, LLC - vSphere Upgrade Saga - virtualization security Table round Podcast
-
How can I calculate the amount of download and upload traffic within a single session?
Hi, I would like to calculate how much the traffic of data (in bytes) that I use a session (time).
Mind you, I speak not of connection speed.
I guess I have sum download traffic to forward traffic, but I don't know where I can find it in my Firefox or my OS, and Linux.
Can you help me?This is due to the use of a provider with a download bandwidth limits?
There is an Extension Point called 'Net use'
https://addons.Mozilla.org/firefox/addon/NET-usage-item/
http://netusage.iau5.com/ -
How stop imagies to record traffic.
How stop imagies to record traffic. I have only 200 MB per month. This is 38.0.1 version.
Sorry for my languige? I'm not American.- Image block: https://addons.mozilla.org/firefox/addon/image-block/
- ImgLikeOpera: https://addons.mozilla.org/firefox/addon/imglikeopera/
-
Turning on links sends the traffic to the address
OS Mavericks, 38.0.1 Firefox.
When I roll over any link on a page Web Little Snitch throws an alert that Firefox attempts to send traffic to the address associated with the link. This is the new behavior in the last month.
I don't have this problem with the Safari browser.
Hello, please see the section "read-ahead" How to stop Firefox to make automatic connections
-
All the world began to see traffic outbrain appearing in Safari on their iPhone? When I click a link on a site of newspapers I see momentarily otraffic outbrain are contained in the URL. What I've read, I don't want it on my phone and discussed ways to eliminate, but nothing is there for phones. Any thoughts?
Try resetting Safari. Close Safari completely from the window of the selector app by double clicking the Home button and slide up the preview pane of Safari until it disappears from the display. Then go to settings > Safari > clear the history and data from the Web site. Then perform a forced reboot. Hold down the home and Sleep/Wake buttons simultaneously for about 15-20 seconds , until the Apple logo appears.
-
BitDefender traffic light not working not not in the Firefox browser
I just started using the Firefox browser and have noticed that my Bitdefender traffic light function no longer works (it worked with I.E. and Opera browsers). This function checks Web sites when you perform a search and displays a green checkmark if Bitdefender thinks that the site is safe to access. I really like it and would like to know how to run in Firefox or Firefox does not support this?
Download and use Bitdefender fires Addon
-
Unable to access SSL Web site when company proxy use man-in-the-middle attack to scan SSL traffic
Our company uses a proxy server that analyzes the SSL traffic on web sites. This is done via man-in-the-middle attack. The proxy generates a new certificate on the fly that it sends to the client, impersonate a secure server.
After upgrading from Firefox 10.0, I always get error:
Error HTTP Status: 400 Bad Request
After the confirmation of a security exception.Maybe this is related to the difficulties of the attack of the BEAST bug (browser exploit against SSL/TLS)
- bug 702111 - intolerant servers to record split of 1: n-1. "The connection was reset" (see also the comment 60)
-
Web error: traffic blocked due to exceed the quota of session
I have a problem with access to the internet. I don't know if I am posting this in the category right forum or not.
Since last week I have been sporadically do the following random error message when going online. It will come when trying to access a Web page, but he seems to have nothing to do with the page itself. He rides on a wide variety of Web pages.
"Blocked traffic due to exceed quota of session IP shaper. Please contact the system administrator. Your session quota is: 512, more traffic will be blocked. »
I get this message on both my computer and on the iPad for my husband. Usually, if I refresh the page, the Web page originally, I was trying to go to load. But sometimes this error message will just continue to flow to the top when I try to reload the page.
I use a MacBook Pro of the retina, OS X El Capitan, 10.11.4, Safari 9.1 version. IPad for my husband is a Mini iPad start (I don't know exactly what we) running latest iOS, I think 9.3.1 and Atomic web browser.
I tried to do a search online for other people with this same problem and I found a lot of different complaints, but they were all in different languages from around the world. And none of them had real fixes. The only English and even made any sense is here: ause-of-exceed-per-ip-shaper-session http://superuser.com/questions/550362/http-requests-met-with-traffic-blocked-bec. But it doesn't really say how to solve this problem.
I plan to call my ISP tomorrow morning, but I really don't see how this problem would be on their part I use Dish internet Network satellite. She has a monthly quota of data, but I have access to my use, and is not the problem. Indeed, my fair use reset for the month yesterday, but I still get this message. In addition, the grammar is odd in this error message, and it does not resemble a flat view. Something to suggest in my internet connection. And it is on many devices in my home and disrupts the use of the internet for my and my family.
Trying to Resti.
I'd appreciate really any ideas on what it is and how to fix it. Thank you.
So, I called dish, my ISP, Friday, and no one there had heard of this problem. Their only suggestion was to connect my modem directly to my computer without going through the router and see if I have the problem persists, in order to see if the problem with my AirPort Extreme. Unfortunately, my computer, a MacBook Pro of the retina, lacks an ethernet port.
I'm at a complete loss what to do about it, it's getting slowly worse and come more often. Does anyone have any suggestions?
-
DNS server records to monitor traffic.
I do not understand much about it so I hope someone can explain to me.
I have a server configured with a DNS server running successfully on my mac mini (dns primary server for the House).
I was wondering if there is a way to capture the DNS server logs and monitor visited Web sites of specific host ips/name?
I don't have an example to make immediately available, and I expect that it will be the analysis or an output channel created manually or otherwise searching the DNS server connects.
If your firewall blocks all outgoing DNS traffic except for DNS queries on the server (this is to avoid without entering the DNS server, register via VPN or other), you can turn on extra logging through the command line, and then check the DNS server logs.
This configuration is probably more commonly implemented with either a network sniffer I look for DNS queries arriving at your server, or perhaps a web proxy server, as this proxy server gets you the customer information and the target host information, as it won't be all kinds of activities related to the web-is in the DNS for a typical client newspapers.
Activity network Apps, app updates (various which may seem HTTPS traffic, too), multiple streams of data, etc.
HTTPS and VPN can throw a key in these listening and data collection activities, unfortunately. They can hide the access or hide the DNS query, according to the monitored computers.
There are approaches especially here, including the firewall of filtering (or notation) and the mechanisms of OS X such as Parental controls, depending on the specific details of your needs here. There are examples posted around the network to use Wireshark or tcpdump to acquire the DNS of your network data, as well.
Details on the management of the BIND 9 command line - i.e. when there is hair - are available in the ISC BIND documentation, such as 9.10. Find statement grammar and record the setting up an output channel, as a starting point.
For recent versions of OS X Server, BIND configuration files are under/Library/Server. (See this discussion, as well.)
Changes to the configuration files can sometimes fail.app, unfortunately. Close.app, make the changes to a copy of the file, then restart.app (and I hope Server.app don't spill or undo your changes).
-
ConfigFree network traffic meter - what do the bars?
What does the bars up and down the network traffic meter in the configfree SP2 version?
Hello
Unfortunately, I m not sure what bar do you mean but the ConfigFree includes a feature to help clean with lots of useful information and helpful tips.
Please start the Configfree and press F1. Now, aid should start. -
Is there a way in which I can see if Apple firewall blocks the traffic to a certain IP address?
Connection to my e-mail domain seems to be blocked by a body between my home network (via Apple AirPort) and my mail server to an external service provider. I can connect to this fine through my mobile operator, but not from my home network. This leads me to believe it may have something to do with the Apple firewall, blocking traffic to. Where can I see if this is the case? Other possibilities or what to check?
I agree that it seems that the Apple router blocking communication (Support Apple says that is not possible, is said by the way)... but please read this thread for another angle that you would not have thought:
-
How remove adware 'alwaysnewsoft' point 'traffic-portal' point 'net '?
I accidentally contaminated my Mac Pro with the 'alwaysnewsoft' dot "traffic-portal" dot "net" adware/malware, which prevents me from using Safari, unless I click OK on a warning that I am not ready to touch. Does anyone know how to remove it? Googling the issue is only for Windows solutions, and almost all of them are apparently shady malware movers.
You have two options; You can download and run Malwarebytes' Anti-Malware for Mac, which was developed by a respected contributor and confidence here and therefore is not shaded, or you can remove it manually. I'd personally go with Malwarebytes because it's tidy, fast and only removes the malware/adware software from your hard drive, nothing else.
-
How to restrict multicast traffic to specific ports on GS716Tv3?
I can not find specific instructions to limit traffic of multicast on the smart switch GS715Tv3.
I need to force all multicast traffic to travel on a specific set of interfaces, or at least stay within a given virtual LAN on the switch to which it is native. All the changes you want multicast servers and listeners will be on these interfaces in their separate vLAN.
We have several GS715Tv3 switches configured identically, but multicast traffic does not pass between the switches.
Topology:
Eight GS716Tv3 smart switches, each configured with three VLANS identical.
No traffic should pass between these VLANS on the switch or pass between the switches
In other words, even if all the 8 switches each have a vLAN named "IOSubsystem", I do not considered the same vLAN.
.
vLAN 4 is corresponding to the hosts of Linux to address major
vLAN 5 is for the audio subsystem
vLAN 6 is for the IO subsystem
VLAN each switch 4 has two active ports, a session to the external interface of the main Linux host and the other to a central switch of 9th GS716Tv3 where a system of software development is also linked.
VLAN each 5 switch connects to the components of the audio subsystems (not shown).
VLAN each switch 6 has two active ports, a going inward a lead Linux host interface and one for the IO subsystem.
-> [vLAN4 | g10]---> [Switch #9]-+.
-> [vLAN4 | g9]-> [Linux host #1: eth0] |
[Switch #1]-> [vLAN6: g1]-> [Linux host #1 | eth1] |
-> [vLAN6: g2]-> [e/s 1 subsystem] |
|
-> [vLAN4 | g10]---> [Switch #9]- +---> [software Dev host]
-> [vLAN4 | g9]-> [Linux host #2: eth0] |
[Switch #2]-> [vLAN6: g1]-> [Linux host #2 | eth1] |
-> [vLAN6: g2]-> [subsystem/o 2] |
... ~
|
-> [vLAN4 | g10]---> [Switch #9]-+.
-> [vLAN4 | g9]-> [Linux host #8: eth0]
[Switch #8]-> [vLAN6: g1]-> [Linux host #8 | eth1]
-> [vLAN6: g2]-> [i/o subsystem #8]We get multicast traffic unwanted between each of these systems, causing corruption of our stream. We limit the multicast traffic on vLAN6 of each switch to stay on the vLAN6 of this specific switch.
Thanks for any help.
To switch the management VLAN to 4.
Make sure you have 2-way switch, one in VLAN4 in a VLAN1.
4 and apply the value of the system you use to a static IP address to the switch and confirm the access to the web configuration and then change "management VLAN ID. then pass the system that you use on the port or any VLAN 4, then you should have access, otherwise, wait about 60-90sec and try again, because you might have PLEASE and it will block anything on the port for just under its set to "Enabled" 'Fast Link '.
Then under "IP Configuration" value switches other IP address in IP range of VLAN4.
For the love of Simplisicty, unmarked ports should never be in 1 VLAN simultaneously.
And instead of using the point and click, goto "Port PVID Configuration" and just create the VLAN it.
Member of the PVID and VLAN the same thing for a port, on what VLAN, it must be in the database
And to confirm, you have a cable from switch to each VLAN? You can cut down on cables and ports if you tag/trunk ports to the next switch. then all VLAN 3 just 1 cable between each pair of switches, saving you at least 4 ports on each switch.
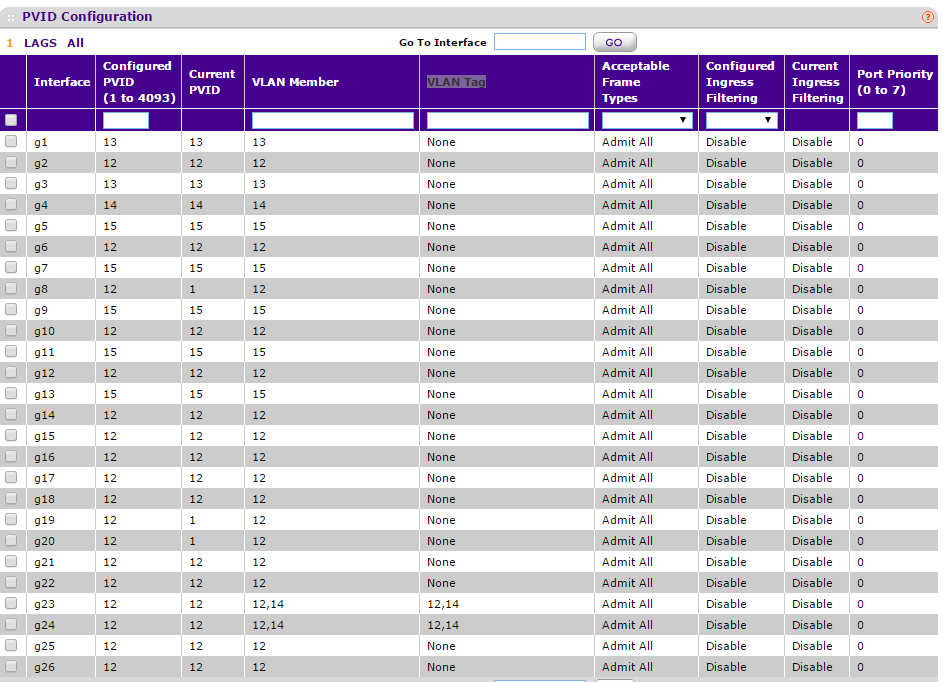
Just an example of my GS724T (ignore ports g8 and g-19-20, their current PVID is because of something else you do not, LACP and Span/Monitoring):
All ports are configured to a single VLAN, my 'LAN hand' is VLAN12, that the management VLAN is set for, g23-24 ports VLAN trunks, they are set on tagg VLAN12 and 14 when the traffic is out of these ports, then switch to the other side reads the consequence tagg and acts, that way I don't need 2 cables/port for each of them.
Maybe you are looking for
-
How can I restore my emails that they don't?
My emails aren't coming since 09:00 this am and it is simply not possible. Don't know if I did something that I have or what is happening. Can you help me?
-
I am looking for a VI which registers all controls, pressed by a user on a front panel and can be read without having to press the controls again. Thank you in advance for your help. Best regards.
-
I start my computer and it tells me that I need an update for my new processor because there an 1801 error such that it has a firmware problem and I need to support my progress. I went online to get and my manufacturer isn't an i have the update of d
-
network cards, teredo tunneling pseudo-interface. device cannot start (code 10)
error code 10
-
Cannot install update KB968930 or KB970158, error code 800F0900
I have a problem installing these updates. They don't will not install and I believe that there are other problems with my computer. I constantly receive a security message that will then shut down the computer, also my McAfee will not scan it stops