How to restrict multicast traffic to specific ports on GS716Tv3?
I can not find specific instructions to limit traffic of multicast on the smart switch GS715Tv3.
I need to force all multicast traffic to travel on a specific set of interfaces, or at least stay within a given virtual LAN on the switch to which it is native. All the changes you want multicast servers and listeners will be on these interfaces in their separate vLAN.
We have several GS715Tv3 switches configured identically, but multicast traffic does not pass between the switches.
Topology:
Eight GS716Tv3 smart switches, each configured with three VLANS identical.
No traffic should pass between these VLANS on the switch or pass between the switches
In other words, even if all the 8 switches each have a vLAN named "IOSubsystem", I do not considered the same vLAN.
.
vLAN 4 is corresponding to the hosts of Linux to address major
vLAN 5 is for the audio subsystem
vLAN 6 is for the IO subsystem
VLAN each switch 4 has two active ports, a session to the external interface of the main Linux host and the other to a central switch of 9th GS716Tv3 where a system of software development is also linked.
VLAN each 5 switch connects to the components of the audio subsystems (not shown).
VLAN each switch 6 has two active ports, a going inward a lead Linux host interface and one for the IO subsystem.
-> [vLAN4 | g10]---> [Switch #9]-+.
-> [vLAN4 | g9]-> [Linux host #1: eth0] |
[Switch #1]-> [vLAN6: g1]-> [Linux host #1 | eth1] |
-> [vLAN6: g2]-> [e/s 1 subsystem] |
|
-> [vLAN4 | g10]---> [Switch #9]- +---> [software Dev host]
-> [vLAN4 | g9]-> [Linux host #2: eth0] |
[Switch #2]-> [vLAN6: g1]-> [Linux host #2 | eth1] |
-> [vLAN6: g2]-> [subsystem/o 2] |
... ~
|
-> [vLAN4 | g10]---> [Switch #9]-+.
-> [vLAN4 | g9]-> [Linux host #8: eth0]
[Switch #8]-> [vLAN6: g1]-> [Linux host #8 | eth1]
-> [vLAN6: g2]-> [i/o subsystem #8]
We get multicast traffic unwanted between each of these systems, causing corruption of our stream. We limit the multicast traffic on vLAN6 of each switch to stay on the vLAN6 of this specific switch.
Thanks for any help.
To switch the management VLAN to 4.
Make sure you have 2-way switch, one in VLAN4 in a VLAN1.
4 and apply the value of the system you use to a static IP address to the switch and confirm the access to the web configuration and then change "management VLAN ID. then pass the system that you use on the port or any VLAN 4, then you should have access, otherwise, wait about 60-90sec and try again, because you might have PLEASE and it will block anything on the port for just under its set to "Enabled" 'Fast Link '.
Then under "IP Configuration" value switches other IP address in IP range of VLAN4.
For the love of Simplisicty, unmarked ports should never be in 1 VLAN simultaneously.
And instead of using the point and click, goto "Port PVID Configuration" and just create the VLAN it.
Member of the PVID and VLAN the same thing for a port, on what VLAN, it must be in the database
And to confirm, you have a cable from switch to each VLAN? You can cut down on cables and ports if you tag/trunk ports to the next switch. then all VLAN 3 just 1 cable between each pair of switches, saving you at least 4 ports on each switch.
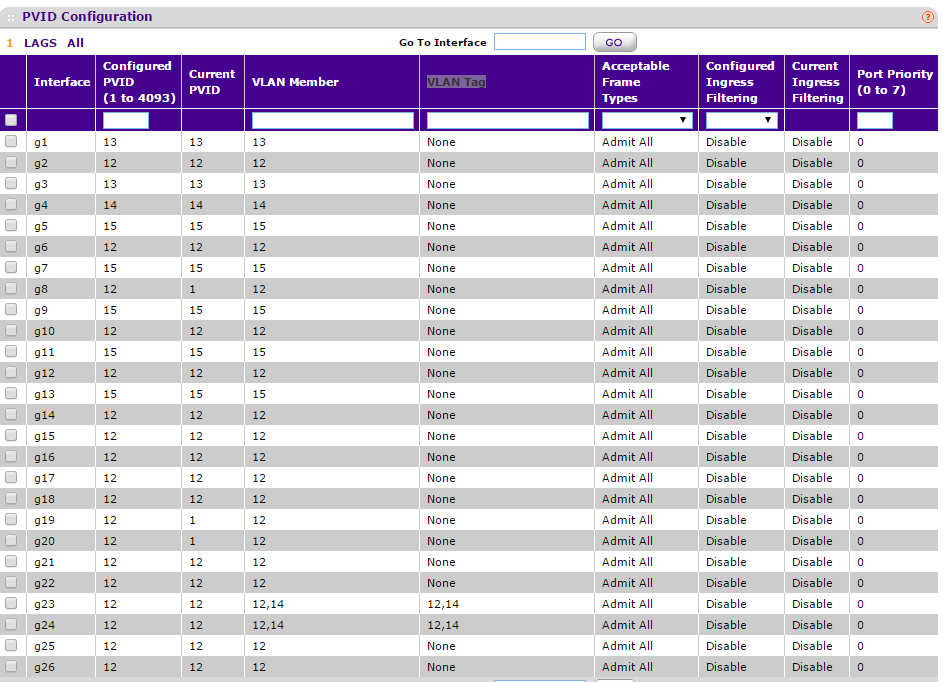
Just an example of my GS724T (ignore ports g8 and g-19-20, their current PVID is because of something else you do not, LACP and Span/Monitoring):
All ports are configured to a single VLAN, my 'LAN hand' is VLAN12, that the management VLAN is set for, g23-24 ports VLAN trunks, they are set on tagg VLAN12 and 14 when the traffic is out of these ports, then switch to the other side reads the consequence tagg and acts, that way I don't need 2 cables/port for each of them.
Tags: Netgear
Similar Questions
-
Specific customer VPN - how to restrict to host/port?
Hello
I have a PIX-515 performer 6.3.5 code using Firewall/VPN device. I have a lot from site to site and VPN client works well. However, I'm looking for a way to split tunnel to the port grannularity level.
for example, vpn profile Fabricant2, limit access to the 192.168.100.210 on port 80 and 81 only. Here is my config.
object-group service tcp tcp-80-81
Beach of port-object www 81
object-group network consultant-vpn2-dst
host of the object-Network 192.168.100.210
object-group network vpn-clientpool-2
network-object 192.168.101.64 255.255.255.224
!
access-list consultant-vpn2 permitted tcp object-group consultant-vpn2-dst object-group tcp-80-81 object-group vpn-clientpool-2
access-list no. - nat permitted tcp object-group consultant-vpn2-dst object-group tcp-80-81 object-group vpn-clientpool-2
!
192.168.101.64 - 192.168.101.95 pool2-vpn IP local pool
!
NAT (inside) - access list 0 no - nat
!
vpngroup address vpn-pool2 pool Fabricant2
vpngroup Fabricant2 by default-domain mydomain.com
vpngroup split Fabricant2 consultant-vpn2 tunnel
vpngroup idle time 1800 Fabricant2
Fabricant2 vpngroup password *.
This config works fine but when connecting, I see the split tunnel which passes on the IP level. I am able to ping or pass another type of traffic to the host, even if the ACL is extended and only port 80/81.
Is there a way to limit the VPN client to a specific port only?
One solution would be to...
1. remove the allowed sysopt connection ipsec
2. write access you want in your list of outside access.
No ipsec sysopt connection permit
outside_access_in tcp object-group allowed access list vpn-clientpool-2-object-group consultant-vpn2-dst eq 80
outside_access_in tcp object-group allowed access list vpn-clientpool-2-object-group consultant-vpn2-dst eq 81
Access-group outside_access_in in interface outside
Note: the actual acl may vary depending on what you already have. Also if you have other virtual private networks, these subnets access should be allowed since the removal of the sysopt command block access.
-
How to create and assign a VLAN to specific ports
In our ISA550W, create the VLANS for different subnets and assigning them to specific ports are a piece of cake and self explanitory.
However on a SG300-10MP, I am totally lost lol. I just want to make ports 7 & 8 set to a sous-reseau.10 instead of un.6 as the rest of the switch. I need these ports to be totally independent from the rest and not to communicate with others at all.
How can I do this?
Thank you!
Hi Alex,
Under management of VLANS, go into settings of the interface. Change the interfaces that you use to access the ports by choosing the way you want by clicking on change.
Once they are access ports back to Port for page VLAN and assign the port desired as one not marked in this interface.
This should be everything you need, let me know if you have any other questions.
-Good Trent
* Please note the useful messages! **
-
How to restrict the tunnel VPN Site to site traffic thrue
Hello
I have a tunnel from site to site, where Site 1 is the local site and main site. and 2 the site is the remote site.
How to limit the traffic of site 2, so that they can only reach a few IPS on the lokal site.
But since the lokal site all IP addresses must be able to reach all of the IP addresses to site 2 (remotely).
an access list to the 'inside' interface does not work, since all the acl is bypassed for the interfaces for IPSEC traffic.
Then, I tried to make a political group where I only allow traffic to servers specifik, but site 2 can still reach everything on the lokal site.
Am I missing here?
Best regards
Erik
Hi Erik,
Unfortunately, the only options that we have are VPN filters that are two-way and disabling the sysopt feature.
If you have a core switch/router we can block traffic on this device by using the access list or null routes.
See you soon,.
Nash.
-
Multicast traffic stops flowing after a while when using IGMP snooping
Hi all
I have the following configuration:
:

Where host 1 is a multicast traffic source and host 2 is a customer of multicast traffic. IGMP snooping is configured on both switches.
Host 2 boots and sends an IGMP report, in order to join the multicast host group 1. Given that SW2 does not know where the mrouter from the group, adds port Eth1/1 to the Group of snooping and removes the package, the IGMP packet. Once host 1 starts, it sends an IGMP query (which is flooded by the port channel), and multicast traffic starts to flow to host 2.
When I ran 'show ip Mattia snooping groups' I've seen the same result on both switches: on the two switches of the groups the Eth1/1 and the channel port, but after a while, the switch connected to the host 2 deleted the channel of the port of the group.
After consultation with the switch logs and sniff traffic on one of the channel port on SW1 interfaces, I came to the conclusion that happens since SW1 ceases to send queries generated by host 1 and responding to them locally (some proxy or something). I also noticed that IGMP reports generated by host 2 stop arriving on SW1 (since SW2 do not know that there a connected mrouter more across the channel of the port).My questions are:
1. How does SW1 knows he should keep the channel port as part of the group, if it does not IGMP reports coming from SW2 more?
2. what happens if the host 2 is not interested in multicast traffic, but do not send and IGMP leave message (a behavior that is supported according to the Protocol, to my knowledge)? How SW1 knows he should cease to IGMP sent from host 1 query response?
Thanks in advance,
Omer.
Hello
The problem is because you have not mrouter port sw1. It is well documented by virtue
http://www.Cisco.com/c/en/us/support/docs/switches/Catalyst-6500-Series-...
There are 3 ways you can solve this problem.
1. enable Pim on Sw1.
Or
2. enable ip igmp snooping interrogator on Sw2
Or
3. create staitc mrouter port on sw2.
ip igmp snooping vlan 1 mrouter interface PoX
-
inter esxi host ipv6 multicast traffic are not detected by the destination VM
Hello
Warning, I do not have in-depth knowledge of vmware, so please excuse the bad wording, misconception and ignorance in the post below.
The current topology is:
Each esxi 4.1 update 3 (DL380 G8) host is to connect both layer 2 switch.
on each host, the vswitch has two network cards configured as active/active, with the default NIC cluster approach (route based on the original virtual port code).
Everything else is default.
The switches are connected by a link to trunk (not bunk)
I have two Windows Server 2008 R2 VM in the same subnet and you have enabled ipv6 on them (by default)
When two virtual machines are on the same physical host, ping-6 destination_ipv6_address works (I just use the link local address)
When two virtual machines are on different hosts, ping fails with the "destination unreachable" message, which usually means the neighbor discovery process fails (similar to arp in ipv4 where source VM cannot get mac address of the destination virtual machine)
When two virtual machines are on the same physical host, the the packet capture shows that Neighbor Solicitation message is sent via an ipv6 multicast address
When they are not on the same physical hosts, packet capture on the VM shows that the destination virtual machine will ever get the destination ipv6 multicast packets.
I then connect two DL380 G8 in a similar way to the switches and install windows Server2008 R2 directly without virtualization on them and ping-6 works perfectly.
My questions are:
-I missed somewhere, a configuration to allow ipv6 multicast to work? Or even to remove any 'logic' and treat it simply as a show?
On network switches, you can do this by disabling IGMP who will then deal with multicast as broadcast packets.
Although I can't find a similar setting under esxi anywhere.
-J' saw an option "Enable ipv6" on esxi, but I guess it's only useful if the host itself to participate in ipv6 and therefore not applicable to my case?
The only similar question I found the research is on the link below, which suggest to hardcode the next table on virtual machines, which is not ideal.
I can confirm however, hard coding the table nearby on two virtual machines to work. This problem seems to be on how esxi vswitches manage ipv6 multicast traffic
Ideas, points of view are very appreciated
Ed
I don't know if this will really solve your problem, but it is worth trying to update the firmware of the NETWORK adapter and the driver.
Looks like it's a HP NC 331FLR NIC (gen8 DL by default NETWORK 4 ports with the BCM5719 chip card).
There is no binary updates that you can run from the 4.1, but you can update all the components of the firmware with the current Service Pack HP for Proliant image:
Or start the server in a live Linux of your choice and use the Linux binary update:
http://www.HP.com/swpublishing/MTX-ec0e18db6a8e4d978b57aa95d1
These will update the NIC 331FLR to the Boot Code version 1.37/NCSI 1.2.37.
Then update the tg3 driver in ESXi with this set to 3.129d.v40.1 offline:
You need the file bundle offline (BCM - tg3 - 3.129d.v40.1 - offline_bundle - 1033618.zip) in this package. You can import in the vCenter update manager for easier deployment or install it (probably) ESXi shell with esxupdate--bundle=/tmp/BCM-tg3-3.129d.v40.1-offline_bundle-1033618.zip
I'm a little rusty in the Department of ESXi 4.1 CLI however, you may need to use the vihostupdate utility or with PowerCLI Install-VMHostPatch remote:
-
LRT224 Port forwarding of specific Port
Is it possible with this router to do port forwarding on a specific port to a pc?
I have a basic need:
Transfer the incoming request to WAN port 37777 to RDP port 3389 to the local server xxx.xxx.xxx.xxx.
I try to do a formward configured like this:
Service: 37777 (custom)-37777
IP address: XXX.XXX.XXX.XXX:3389
But I can't save this configuration (wghite page is displayed).
How can I access with RDP on my public IP address on a specific (not the standard 3389), the port of my business and be sent to a specific server?
for example: RDP at yyy.yyy.yyy.yyy:37777 connects to the server local xxx.xxx.xxx.xxx
So far, I can only access this server with rdp standard port on the public ip address.
Thank you
The LRT224 supports the translation of address of Port (PAT). With PAT, each computer on the LAN is translated at the same IP address, but with a different port number assignment.
-
How can I assign an IP address and a specific port on a powerconnect switch 6224?
Thanks for the explanation.
When you connect two layer 3 devices, you need a network isolated between devices. The process is similar between Cisco and PowerConnect. The difference is, as you said, you cannot set an ip address on the port itself with Powerconnect. As you would with Layer 3 devices Cisco.
Are the switch A and switch B of PowerConnect? Or is a Cisco and the other Powerconnect.
If both are PowerConnect. You will need to create a VLAN to be only used to one port on each of the 2 devices.
Switch to # config
Switch database has (config) # vlan
A(config-vlan) switch # vlan 2
Switch A(config-vlan) # exit
Switch to (config) # interface vlan 2
A (config-if) # name of the L3 switch connect switch
Switch # 192.168.1.1 ip address A(config-if) 255.255.255.0
Switch A(config-if) # exit
Switch to (config) # interface ethernet xxx
Switch A(config-if) # switchport mode access
Switch A(config-if) # switchport access vlan 2
--------------------
The B switch configuration:
B # config switch
Database switch B (config) # vlan
B(config-vlan) switch # vlan 2
Switch B(config-vlan) # exit
Switch B (config) # interface vlan 2
B (config-if) # name of the L3 switch connect switch
Switch B (config-if) # ip 192.168.1.2 address 255.255.255.0
Switch B (config-if) # exit
Switch B (config) # interface ethernet xxx
Switch B (config-if) # switchport mode access
Switch B (config-if) # switchport access vlan 2
Next, you will want to check to make sure IP routing table that's list a path to all networks on both sides.
You will probably need a specific static route defined for networks or by default.
-
How to determine if ASA is blocking port or not?
Hello world
I support the ASA according to the customer. I'm new to the world of the SAA.
Users especially to check whether or not ASA allows specfic port.
I don't know how I can check that.
Is it possible that I can determine if ASA is blocking port or not?
If ASA is blocking port what steps I must take to allow ASA allow specific port?
concerning
Mahesh
Hello
You can use the command packet--draw to get the results you're after... that is to say if a 10.1.1.10 client attempts to access google dns, you can use the following syntax:
plotter of entrance inside the 10.1.1.10 udp packets 53 8.8.8.8 53 detailed (I may have the syntax a bit but you can tab your way through this).
Thank you
Sent by Cisco Support technique iPad App
-
Why IPSec does not support multicast traffic?
If IPSec is a tunnel, why can't set you the multicast traffic in an ACL to protect?
IPSec is a standard, and there is nothing in the standard that allows for multicast or broadcast traffic to go through it.
Specifically, the IPSec RFC (ftp://ftp.isi.edu/in-notes/rfc2401.txt) says things like:
A security association is identified by a triple compound
a security parameter Index (SPI), Destination IP address, and a
identifier (AH or ESP) security protocol. In principle, the
Destination address may be a unicast, broadcast IP address
address or multicast group address. However, the IPsec Security Association Management
Currently, the mechanisms are defined only for unicast SAs.
and
The receiver-orientation of the Security Association implies that, in
the case of unicast traffic, the destination system will normally be
Select the SPI value. Making the destination select the SPI
value, there is no risk for manually configured security
Associations to conflict with automatically configured (e.g., via a)
The key management protocol security associations) or safety
Associations from several sources in conflict between them. For
multicast traffic, there are multiple destination systems by
Multicast group. If some system or person will need to coordinate
Among all the multicast groups to select an SPI or SPIs on behalf of each
multicast group and communicate the IPsec group information to
all legitimate members of this group of multicast through mechanisms
not defined here.
Several transmitters to a multicast group SHOULD use a single title
Association (and therefore Security Parameter Index) for all traffic to
This group when a symmetric key encryption or authentication
algorithm is used. In such circumstances, the receiver knows only
that the message is from a system with the key for this
Multicast group. In such circumstances, a receiver will be generally
not be able to authenticate which system sent the multicast traffic.
Specifications for other, more general multicast cases are postponed
for later IPsec documents.
Sorry to quote RFC from you, but we just follow the standard and the standard does not support this. You can bypass it by setting a GRE/IPSec connection, but what really is encapsulating the broadcast/multicast in a package of volition unicast first, then encrypt this unicast packet.
-
PIX Site to Site VPN to aid to specific port
Good day to all!
I know that to have establish a site to site VPN using 2 PIX firewall, it should be noted the interesting traffic on both sides. Usually, we make the following statement:
accessList AllowedTraffic ip 192.168.2.1 allow 192.168.3.1
But I thought what happens if specify us specific ports on the
The ACL that is used for interesting VPN as HTTPS traffic? Like the one below:
Acccess-list AllowedTraffic tcp 192.168.2.1 192.168.3.1 eq 443
Comments would be nice...
Thank you...
Chris
Here are my configs when I tested it. I hope this helps! If Yes, please rate.
Thank you
-
How to block all traffic except vpn traffic and traffic bureau HQ
Hello
Someone please advise me how to block all traffic except inbound traffic through the VPN and traffic from the IP of the HQ Office.
My router is 881/K9 Cisco router. Currently, I have blocked all IP addresses with the exception of the IP Office HQ using access-list on the brance office website.
I put the IP list allowed according to IP location of the VPN user. But now the VPN user become more and more and thus be difficult to block the IPs based on their current location. Sometimes not possible to know their WAN ip address.
Thanks in advance.
Have you considered allowing the IPSEC IP Protocol, TCP port, intellectual property all UDP ports and then by blocking all other traffic?
-
E1000/E1000e receive multicast traffic all
Hello
I used E1000/E1000e as NIC in Linux and I found out that all multicast traffic network interface which meant vSwitch passed all multicast traffic to these interfaces.
I don't want the network interface to see all multicast traffic because it does not affect the performance of vSwitch. How can I do?
I knew also VMXNET 3 can meet my needs, but for some reason, I have to use E1000/E1000e.
Gabriel
I knew what wrong with this case. I use tcpdump to view multicast traffic that has been approved to be unreliable. Tcpdump changed the E1000/E1000e configuration, if she could see the multicast traffic.
Right now, I've changed my method. I looked statistics packages based on order esxtop. In QNX 6.5.0, I did the following steps:
1. start of QNX, let interface upward. I don't see any esxtop, THAT VM has received all the packages.
2. start tcpdump. I saw tcpdump captured packets multicasts. Also of esxtop, I see VM received packets.
3 collapsed tcpdump. Of esxtop, VM has not received all packages.
To conclude, QNX with E1000/E1000e support multicast packets. And tcpdump couldn't be used to see the multicast traffic.
-
Network ACL two specific ports
As I know there is no way to set ACLs for network such that only two specific ports are available. I'm using Oracle 11 g 2.
I would like a HTTP and SMTP port opened for local loop address. These are ports 7777 and 25. It is my understanding that you can have only one of the ACL for each host. While it seems that you can create others, any additional ACL for the same host does not always work as expected. So does anyone have tips that how can I do this? I'd rather not have all ports between 7777 and 25 available but this is what I currently have...
DBMS_NETWORK_ACL_ADMIN. (ASSIGN_ACL)
ACL = > 'local_loopback.xml '.
, host = > "127.0.0.1"
lower_port = > 25
upper_port = > 7777
);Captain Egg wrote:
As I know there is no way to set ACLs for network such that only two specific ports are available. I'm using Oracle 11 g 2.Not the case in my experience. An ACL can be for a specific purpose, but contain multiple ports for this purpose.
For example I assign ports 80, 8080, 7777 and some others, in a single web - acl.xml, to a target of network (host or domain).
Read the usage notes in the PL/SQL package of database, Oracle®, and reference Types.
-
How will I know how many times I visited a specific Web site?
I need to know how many times I visited a specific Web site. How can I do in Safari? Thanks much for any help.
You could try your history unless you delete history after each session.
Command + Y should open Safari history or in the Safari menu bar, click on: history > view history
Otherwise, find how many times you have visited a site specific Web is impossible.
Maybe you are looking for
-
want to 4500 all-in-one series
I bought an envy4500 all in one series and after all tests and installation correctly, I had only one problem: when I print from excel files including 'grid' the printer will print all the lines in files. Sometimes jump the line grids, then print two
-
Purchase 2005, updated with HD and DVD but needs new CHIPSETS. HP it or repair shop?
-
Activate the floppy drive boot from
-How can I activate A floppy drive to boot from? Do I have to be an administrator?Thank you
-
Skype works only with windows vista
For the entire month past, whenever I open Skype, it immediately no longer works and I get a Windows message saying to download the latest version of Skype. I am running Windows Vista and I think I need some kind of patch from Microsoft. Anyone kno
-
Log in problems: "service user profile Service is a not the user profile cannot loaded e to logon.
After I typed the password Vista gives me an error screen... "The Service user profile service is a not the user profile cannot loaded e to logon. Any ideas? Someone has encountered this problem before?